Published On : 2023-09-01
EXECUTIVE SUMMARY
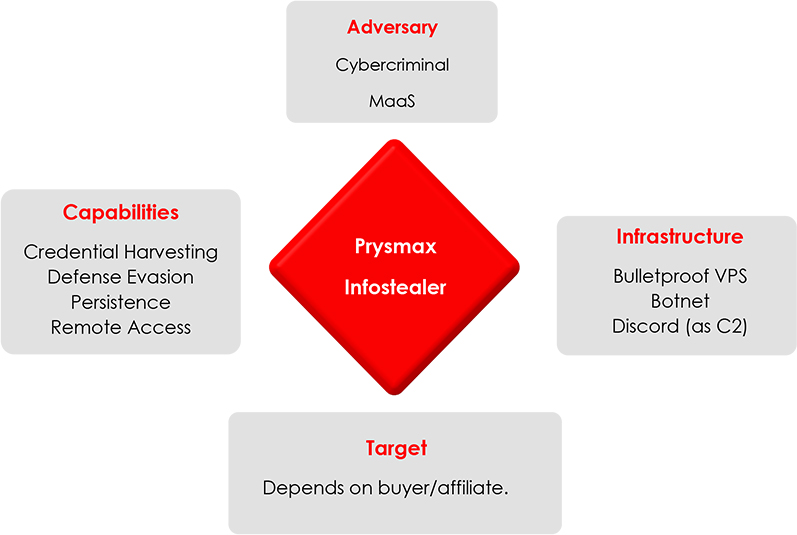
The CYFIRMA research team has discovered a new malware-as-a-service known as Prysmax. The developer behind Prysmax claims that their USP is FUD (fully undetectable) malware, be it their stealer or their RAT. They offer custom development services, along with subscriptions for a stealer, RAT, and botnet services. This report delves into their python-based information stealer known as Prysmax stealer, aimed at discreetly extracting sensitive data such as crypto wallets, passwords and cookies from a wide range of services. The malware is indeed fully undetectable by over 95% of signature-based detections commonly employed by antivirus solutions. By manipulating file associations and executing alongside legitimate .exe processes, Prysmax stealer maximizes its reach and impact. The malware’s extensive use of PowerShell enhances its capabilities for data exfiltration and stealthy actions. Employing proactive cybersecurity measures, including heuristics-based detection, is crucial to mitigate this evolving threat.
INTRODUCTION
In recent times, the proliferation of digital interconnectedness has paved the way for increasingly sophisticated cyber threats. Among these, the resurgence of infostealers stands out as a concerning trend. These malicious entities, designed with the intent to clandestinely pilfer sensitive data, have witnessed a concerning resurgence. This report delves into a specific instance of this growing threat landscape—an advanced infostealer that employs intricate techniques to evade detection, establish persistence, and compromise systems seamlessly.
CYFIRMA researchers came across the Telegram channel created for Prysmax promotion. Initially, from October 2022 to June 2023, the channel was meant for distributing botnet and RAT services. The TA most likely used the RAT to launch malware campaigns, to subsequently compromise a number of devices and using them as a botnet for further attacks/sale.
On 23rd June 2023, the release of Prysmax stealer was announced. The python-based malware is packed using Pyinstaller, which can be used to bundle the malicious code and all its dependencies into a single executable. The launch announcement came with the offer to activate licenses for old Prysmax customers, suggesting that the TA was involved in developing other types of malware in the past. CYFIRMA researchers believe that the developer of this infostealer is also selling a RAT, which is fully undetectable as well, but we’ll save the details for another piece.
KEY FINDINGS
- Anti-Detection Techniques: The infostealer is currently fully undetectable by over 95% of the antivirus vendors, as they are based on signature-based detection methods.
- File Association Manipulation: The infostealer strategically manipulates file associations, enabling it to execute whenever any .exe file is run. This technique ensures that the malware is triggered seamlessly, whenever legitimate executable files are opened, potentially leading to persistent infection.
- Security Software Disruption: To ensure uninterrupted operation, the infostealer takes steps to disable Windows Defender and the built-in firewall. By neutralizing these security measures, the malware gains the ability to execute its malicious activities and communicate with external servers without interference.
- Persistence Mechanism: The infostealer establishes persistence by integrating itself into the system’s startup process. This means that even if the infected system is rebooted, the malware will automatically launch alongside legitimate processes, maintaining its foothold for prolonged unauthorized access.
- PowerShell Exploitation: The infostealer makes extensive use of PowerShell, a scripting language native to Windows, to carry out its malicious actions. This approach allows the malware to perform various tasks, such as data exfiltration and communication with remote servers, while leveraging the legitimate functionality of PowerShell for covert operations.
These characteristics collectively highlight the sophisticated nature of the infostealer, showcasing its ability to adapt, evade, and exploit various aspects of the target system to achieve its objectives. Let us delve into the actions performed by the infostealer to get a better understanding of how it works.
STEALER BEHAVIOUR
- Initial Execution: The malware execution begins with the file located at “%SAMPLEPATH%\prysmax_file.exe.” This file serves as the core component of the malware.
- Network Configuration: The malware promptly disables the Windows firewall for all profiles using the command: C:\Windows\system32\netsh.exe advfirewall set allprofiles state off. This action may allow the malware to communicate with external servers without hindrance, facilitating data exfiltration.
- Exclusion and Configuration Changes: The malware then executes a series of commands to manipulate Windows Defender settings, aiming to lower the system’s security posture:
- It adds “.exe” and “.tmp” file extensions to the list of exclusions for Windows Defender scanning:
- C:\Windows\system32\cmd.exe /c “powershell.exe -command Add-MpPreference -ExclusionExtension .exe”
- C:\Windows\system32\cmd.exe /c “powershell.exe -command Add-MpPreference -ExclusionExtension .tmp”
- The malware disables archive scanning:
- C:\Windows\system32\cmd.exe /c “powershell.exe -command Set-MpPreference -DisableArchiveScanning $true”
- It configures Windows Defender to disable blocking on first seen:
- C:\Windows\system32\cmd.exe /c “powershell.exe -command Set-MpPreference -DisableBlockAtFirstSeen $true”
- The malware turns off I/O AV protection:
- C:\Windows\system32\cmd.exe /c “powershell.exe -command Set-MpPreference -DisableIOAVProtection $true”
- Intrusion Prevention System (IPS) is disabled:
- C:\Windows\system32\cmd.exe /c “powershell.exe -command Set-MpPreference -DisableIntrusionPreventionSystem $true”
- Privacy mode is disabled:
- C:\Windows\system32\cmd.exe /c “powershell.exe -command Set-MpPreference -DisablePrivacyMode $true”
- Script scanning is disabled:
- C:\Windows\system32\cmd.exe /c “powershell.exe -command Set-MpPreference -DisableScriptScanning $true”
- Controlled folder access is disabled:
- C:\Windows\system32\cmd.exe /c “powershell.exe -command Set-MpPreference -EnableControlledFolderAccess Disabled”
- Threat Response Configuration: The malware adjusts the default threat response actions to evade detection and removal:
- It sets high and low threat default actions to values that may allow it to persist:
- C:\Windows\system32\cmd.exe /c “powershell.exe -command Set-MpPreference -HighThreatDefaultAction 6 -Force”
- C:\Windows\system32\cmd.exe /c “powershell.exe -command Set-MpPreference -LowThreatDefaultAction 6”
- The malware disables the submission of threat data to Microsoft:
- C:\Windows\system32\cmd.exe /c “powershell.exe -command Set-MpPreference -MAPSReporting 0”
- Potentially Unwanted Application (PUA) protection is disabled:
- C:\Windows\system32\cmd.exe /c “powershell.exe -command Set-MpPreference -PUAProtection disable”
- Scanning schedule is configured to run on day 8 (possibly to reduce the chances of detection):
- C:\Windows\system32\cmd.exe /c “powershell.exe -command Set-MpPreference -ScanScheduleDay 8”
- Severe threat default action is set to 6, which will simply remove the malware in case a severe threat is detected:
- C:\Windows\system32\cmd.exe /c “powershell.exe -command Set-MpPreference -SevereThreatDefaultAction 6”
- Signature Updates and Reporting: The malware adjusts settings related to signature updates and reporting:
-
Signature updates on startup without engine are disabled:
- C:\Windows\system32\cmd.exe /c “powershell.exe -command Set-MpPreference -SignatureDisableUpdateOnStartupWithoutEngine $true”
-
The consent for submitting samples is set to 2, to turn off automatic sample submission to Microsoft:
- C:\Windows\system32\cmd.exe /c “powershell.exe -command Set-MpPreference -SubmitSamplesConsent 2”
- Further Network Configuration: The malware executes a command to disable the Windows firewall again, potentially reinforcing its network communication capabilities:
- powershell.exe -command netsh advfirewall set allprofiles state off
- System Information Gathering: The malware utilizes Windows Management Instrumentation (WMI) to retrieve the system’s UUID:
- Persistence and Concealment: The malware maintains persistence by running from various locations, including the user’s profile folder and temporary folders. This behaviour makes it challenging to locate and remove. Additionally, when a victim inserts any removable storage device onto the infected machine, all the files on the removable storage get exfiltrated anonymously.
- Command and Control: The TA currently uses a discord bot as the C2 for Prysmax Stealer. Additionally, TA is working on setting up a bulletproof VPS for C2, as discord proactively bans any bot being used for command-and-control activities without obfuscation.
REGISTRY ACTIONS
Persistence via Startup: The malware attempts to establish persistence by adding an entry to the user’s startup using the following registry key:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\NombreDescriptivo
This registry key is utilized to ensure that the malware is executed whenever the user logs into the system. By adding an entry here, the malware aims to maintain its presence and execute its malicious activities each time the user’s session starts.
Disrupting Network Services: The malware attempts to manipulate critical network-related services through changes in the registry. These changes are aimed at disabling specific services, potentially weakening the system’s network security.
- HKLM\System\CurrentControlSet\Services\IKEEXT\Start
- HKLM\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\DomainProfile\EnableFirewall
- HKLM\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\PublicProfile\EnableFirewall
- HKLM\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\EnableFirewall
The changes to these registry keys could lead to the disabling of the IKEEXT service, as well as the firewall functionality for different profiles, including domain, public, and standard. By doing so, the malware may be attempting to facilitate its outbound communication and data exfiltration, without the firewall acting as a barrier.
Manipulating File Associations: The malware attempts to manipulate the Windows file associations, specifically targeting the “.exe” file extension. It interacts with the following registry key to potentially associate itself with executable files:
- HKU\S-1-5-21-4270068108-2931534202-3907561125-1001\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.exe\OpenWithProgids\exefile
This manipulation could potentially lead to the malware being invoked whenever executable files are launched, effectively allowing the malware to execute its malicious code whenever the user launches an executable.
In addition to stealing information from the infected devices, the stealer provides the attacker with a number of options to interact with the infected device and use the stolen credentials to compromise the respective accounts.
EXTERNAL THREAT LANDSCAPE MANAGEMENT (ETLM) INSIGHTS
OPSEC101
The TA attempted to mask the file hash on their Github repository but forgot to remove the videos uploaded to YouTube.
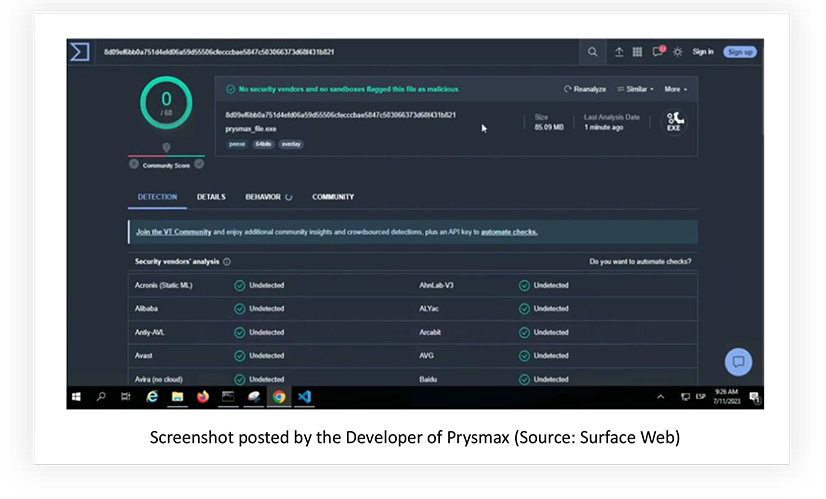
This led us to confirm the TA’s default system timezone, language and the time in UTC at which the sample was submitted to the online sandbox in question.
Based on the available artifacts, it can be concluded with medium confidence that the developer of Prysmax stealer is operating from Spain.
CONCLUSION
Our analysis reveals that the information stealing malware is focused on disabling Windows Defender, manipulating its settings, and configuring its own response to threats. It also attempts to reduce its traceability and maintain a foothold on the compromised system. The malware appears to be well-designed for data theft and exfiltration, while evading detection by security tools as well as dynamic analysis sandboxes. Most of the Prysmax stealer and RAT samples have between 0-2 detections on VT, showcasing a high probability of going undetected, if the victim is dependent on signature-based detections. By implementing the recommendations given below, organizations can enhance their defenses against this information stealer and similar malware threats, safeguarding their systems, data, and operations.
APPENDIX I
MITRE Mapping

IOCs
| No. |
Indicator |
Remarks |
| 1 |
16f902f7537f03d04d3ce308825a725734c028a57958a82f3ae6c8a837b7fd45 |
Prysmax Stealer SHA256 |
| 2 |
051508e80d56c787f50fa36e95b013484cb57db7cffa86fdf314749dcf69c02d |
Prysmax Stealer SHA256 |
| 3 |
17048488f601aa25d2d24b60960abcea22f7ad108b06da2657f4c8539af53d0b |
Prysmax Stealer SHA256 |
| 4 |
0918ec2719149bd59d058b70bf683775a4d39fa8d24614236062034558d1e0be |
Prysmax Stealer SHA256 |
| 5 |
8d09ef6bb0a751d4efd06a59d55506cfecccbae5847c503066373d68f431b821 |
Prysmax Stealer SHA256 |
| 6 |
lunarymc[.]xyz |
Command and Control Domain |
| 7 |
Jghghghgjjg[.]lunarymc[.]xyz |
Command and Control URL |
Sigma Rule for Detection
title: Detecting command-line activities performed by Prysmax Stealer
status: stable
description: CYFIRMA researchers discovered the Prysmax infostealer, aimed at discreetly extracting sensitive data such as crypto wallets, passwords and cookies from a wide range of services.
tags:
– attack.persistence
– attack.defense_evasion
– attack.execution
author: CYFIRMA RESEARCH
date: 2023/09/01
logsource:
category: process_creation
product: windows
detection:
selection:
CommandLine|contains:
– ‘csproduct get UUID ‘
– ‘netsh advfirewall set allprofiles state off ‘
– ‘Add-MpPreference ‘
– ‘Set-MpPreference ‘
– ‘ -SubmitSamplesConsent 2 ‘
– ‘ -SignatureDisableUpdateOnStartupWithoutEngine ‘
– ‘ -ExclusionExtension .exe ‘
– ‘ -ExclusionExtension .tmp ‘
condition: all of selection*
falsepositives:
– none
level: high
STRATEGIC RECOMMENDATIONS
- Network Segmentation: Implement network segmentation to isolate critical systems from less secure areas. This limits lateral movement and reduces the potential impact of a malware infection.
- Advanced Threat Detection: Invest in advanced threat detection solutions that use behavioural analytics and machine learning to identify abnormal activities indicative of malware. These tools can help catch sophisticated attacks that traditional methods might miss.
- Least Privilege Principle: Enforce the principle of least privilege by granting users only the permissions they need to perform their tasks. Limiting user privileges can significantly reduce the potential impact of a malware infection.
- Incident Response Plan: Develop a comprehensive incident response plan that outlines clear steps to be taken in the event of a malware attack. Regularly test and update the plan to ensure its effectiveness.
MANAGEMENT RECOMMENDATIONS
- Regular Security Audits: Conduct regular security audits and vulnerability assessments to identify weaknesses in the infrastructure. Address identified issues promptly to mitigate potential risks.
- Backup and Recovery: Implement a robust backup and disaster recovery strategy. Regularly back up critical data and systems to ensure business continuity in case of a malware-induced system compromise.
- Security Awareness Programs: Develop ongoing security awareness programs for all employees, emphasizing the importance of adhering to security policies, spotting potential threats, and reporting suspicious activities.
- Vendor Management: Review and assess the security practices of third-party vendors, who have access to your systems. Ensure they adhere to robust security standards to prevent potential vectors for malware.
- Threat Intelligence Sharing: Engage in threat intelligence sharing with industry peers, government agencies, and security organizations. Stay updated on the latest malware trends and threat vectors to enhance your defenses.
TACTICAL RECOMMENDATIONS
- Endpoint Security Solutions: Deploy robust endpoint security solutions that offer real-time protection against malware and can detect and block suspicious activities, files, and processes. Ensure these solutions are regularly updated to stay ahead of emerging threats.
- Patch Management: Implement a robust patch management strategy to keep operating systems and software up-to-date. Regularly apply security patches to mitigate vulnerabilities that malware could exploit.
- Firewall Configuration: Configure firewalls to only allow necessary inbound and outbound traffic. Disable unnecessary services and ports to minimize the attack surface and prevent malicious communication.
- Application Whitelisting: Enforce application whitelisting to allow only approved applications to run. This prevents unauthorized and potentially malicious executables from running on endpoints.
- User Training: Provide ongoing cybersecurity awareness training for users to recognize phishing emails, malicious attachments, and other social engineering tactics used by malware to gain access.







