



Anonymous and other hacktivist groups are engaging in online protests using tags such as #OpFukushima, #OpJapan, or #OpTEPCO to highlight and protest against the release of treated water from the Fukushima Daichi nuclear power plant. CYFIRMA discovered a suspected Chinese propaganda, claiming a 0-day RCE vulnerability, and the existence of backdoors allowing the Japanese government to spy on its citizens. This report analyses their claims in the context of the current political environment and breaks down why and how their assertions are false.
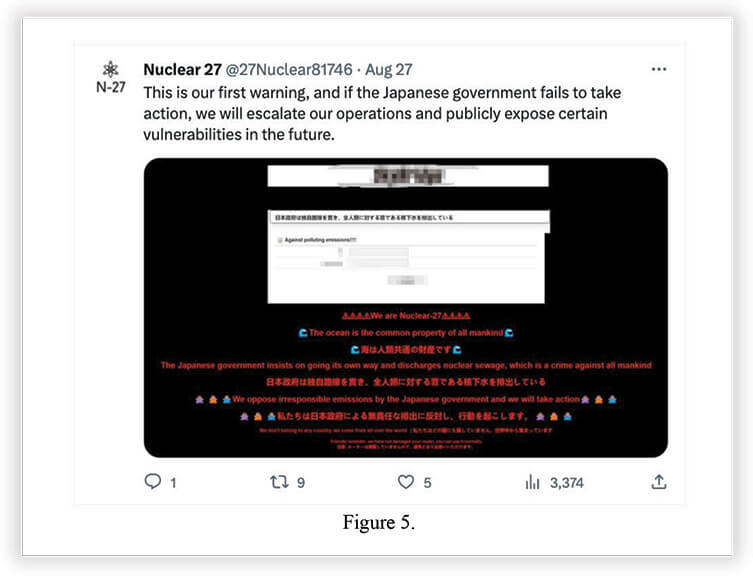
The CYFIRMA research team was alerted to an interesting Twitter account ‘Nuclear 27’, claiming attacks on Japanese network infrastructure using a 0-day RCE vulnerability in relation to the release of treated water from the Fukushima Daichi nuclear power plant.
At a glance, this looked like a potentially sophisticated threat actor with serious undisclosed vulnerability in their hands, warranting further analysis. Furthermore, Nuclear 27 claimed the discovery of a backdoor in Japanese network devices, “infringing upon the privacy of its citizens”.
However, basic due diligence quickly revealed evidence of using old and patched vulnerabilities on old IoT routers with hardcoded credentials, commonly used for servicing and maintenance during their release a decade ago. Threat actors were able to successfully identify remaining unpatched devices using Shodan, and exploit fairly straightforward vulnerabilities to change http.title and defaced WebUI login pages. This was subsequently used to give the impression of ongoing large-scale attacks to attract attention.
However, this attention never came, and the only other media mentioning this attack were the very suspicious Chinese gossip/propaganda news site; ‘iNEWS’.
This leads us to conclude with medium confidence that this was a propaganda stunt.
Nuclear 27 Twitter Activity
https://twitter.com/27Nuclear81746
The account was created in August 2023, just before sharing a handful of tweets between the 26th and 28th of August. Starting with a YouTube video in Anonymous style, claiming ongoing attacks on Japanese organizations. It is using stock footage and text-to-speech, leaving no real clues to explore. The YouTube account was created on 26th August 2023, seemingly to just post this video.
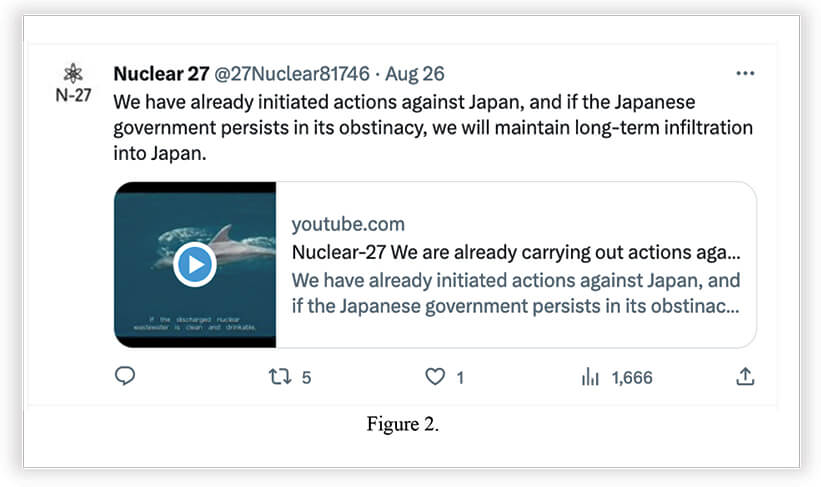
The next few tweets are claiming a 0-day vulnerability and alleged Japanese government backdoor accounts to spy on its own citizens.
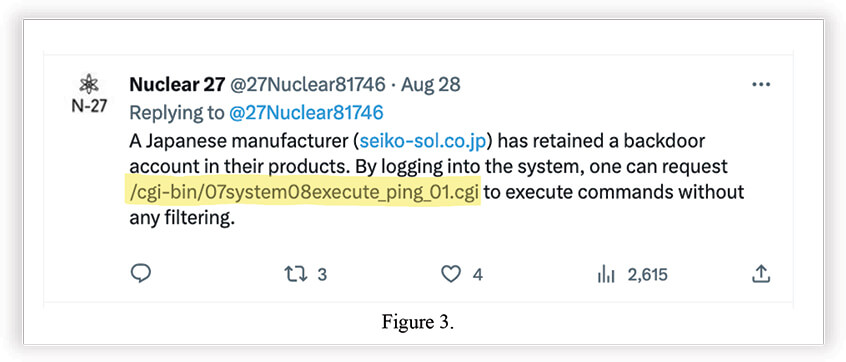
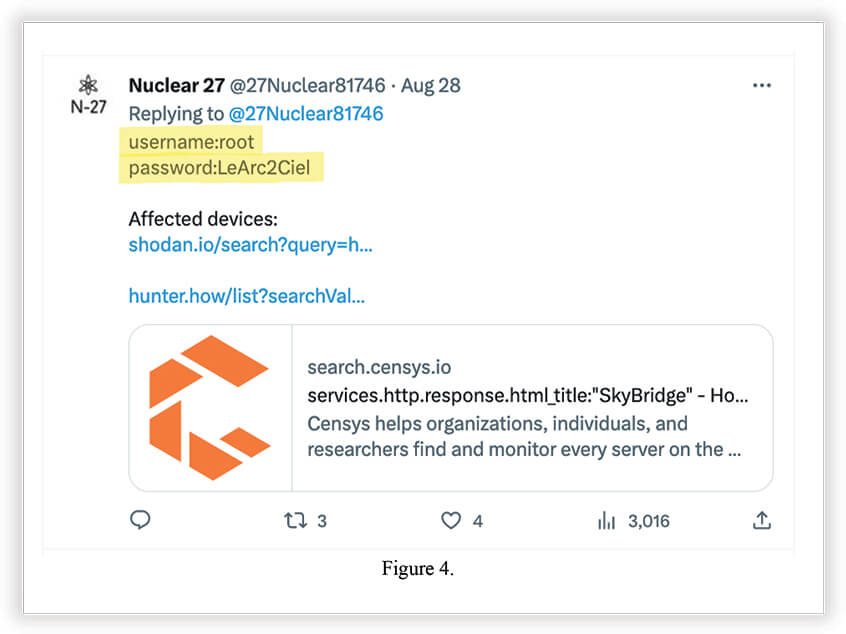
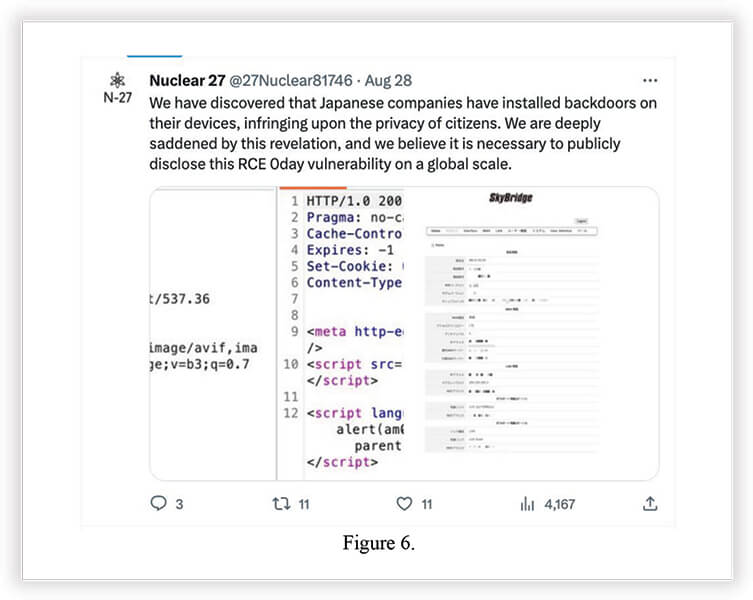
Below are screenshots from the last tweet above. Showing proof of discovered credentials and successful login into WebGUI.
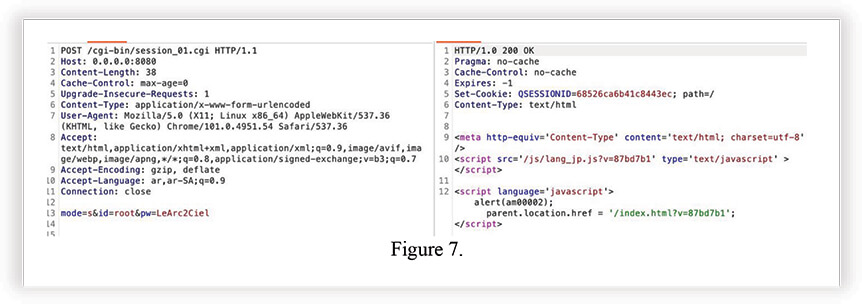
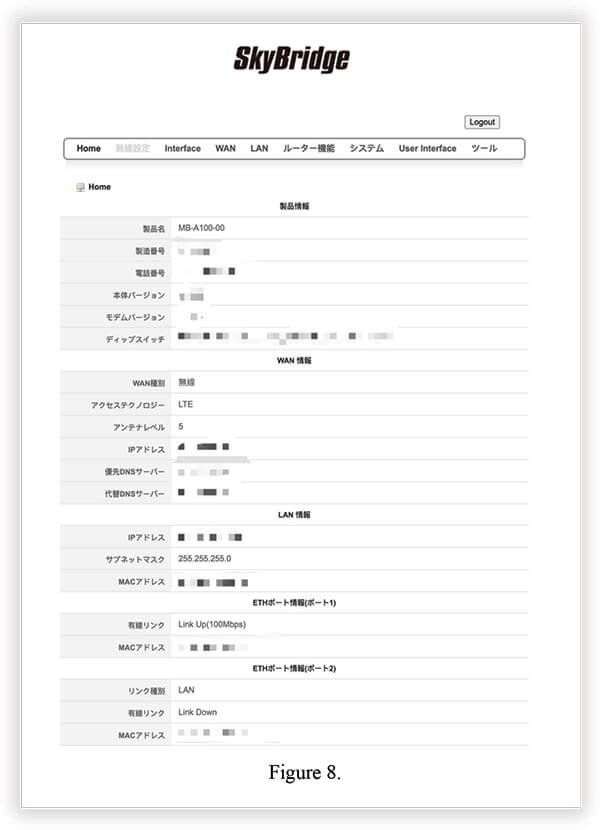
To verify the claims of Nuclear 27 and assess the potential threat, we asked some basic questions.
1. Which devices are vulnerable?
According to the screenshot in Figure 8. the threat actor was able to use the discovered credentials for successful login into the Seiko SkyBridge MB-A100 device. These are IoT M2M LTE/3G routers. In plain English; Machine-to-Machine routers for the Internet of Things, connected to the Internet using an NTT Docomo LTE/3G network.

These devices have been on the market at least since 2014 and are manufactured exclusively for the Japanese market (in fact, they don’t even function outside Japan, without a specific required connection).

2. Has this vulnerability been reported?
Having a quick look into vulnerability databases such as JVN and CVE, we were able to quickly find the exact same vulnerabilities that Nuclear 27 is describing.
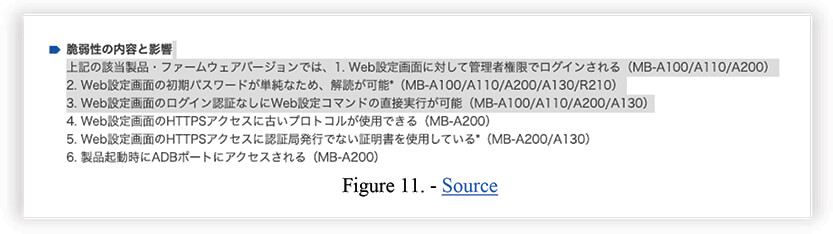
SkyBridge MB-A100/A110/A200/A130 SkySpider MB-R210 provided by Seiko Solutions Inc. contain multiple vulnerabilities listed below.
The developer states that attacks exploiting CVE-2022-36556 have been observed.
Source:
EN – https://jvndb.jvn.jp/en/contents/2023/JVNDB-2023-000029.html
JP – https://jvndb.jvn.jp/ja/contents/2023/JVNDB-2023-000029.html
Specifically, it appears to be a set of multiple related vulnerabilities, published on 10th May 2023.
https://www.cve.org/CVERecord?id=CVE-2023-25184
https://www.cve.org/CVERecord?id=CVE-2023-25072
“Use of weak credentials exists in Seiko Solutions SkyBridge and SkySpider series, which may allow a remote unauthenticated attacker to decrypt password for the WebUI of the product.”
https://www.cve.org/CVERecord?id=CVE-2023-25070
https://www.cve.org/CVERecord?id=CVE-2023-24586
“Cleartext storage of sensitive information exists in SkyBridge MB-A100/110 firmware Ver. 4.2.0 and earlier, which may allow a remote authenticated attacker to obtain an APN credential for the product.”
https://www.cve.org/CVERecord?id=CVE-2023-23906
“Missing authentication for critical function exists in SkyBridge MB-A100/110 firmware Ver. 4.2.0 and earlier, which may allow a remote unauthenticated attacker to execute some critical functions without authentication, e.g., rebooting the product.”
Nuclear 27 also mentioned “[vendor] has retained a backdoor account in their products”, which we believe is a reference to the existence of hardcoded credentials reported in CVE-2022-36560 and CVE-2022-36558. This is a old known and very bad practice of creating servicing admin accounts for maintenance purposes. Given the age of this product line since at least 2014, this is somewhat expected to exist. Most certainly they are not government backdoors for surveillance.
3. Is there a patch?
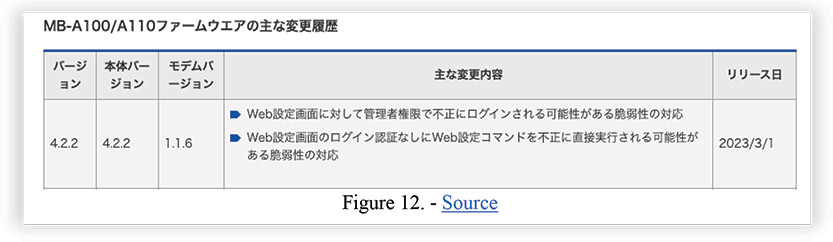
Yes, earlier on 28th February 2023, Seiko published a statement on their product website addressing these vulnerabilities.
And on 1st March 2023 released a patch 4.2.2 to fix these vulnerabilities.
4. How did Nuclear 27 breach devices if the patch existed?
Since these are internet-facing devices, in many cases, finding them using vulnerability scanners like Shodan is not too hard, if you know what to look for. And unfortunately, many devices (especially for machine-to-machine IoT deployment) are not actively managed and patched.
We assume Nuclear 27 created a simple script using the exposed credentials to log into unpatched devices, change their http.title and deface the WebUI login page to show off on Twitter via Shodan and Censys.
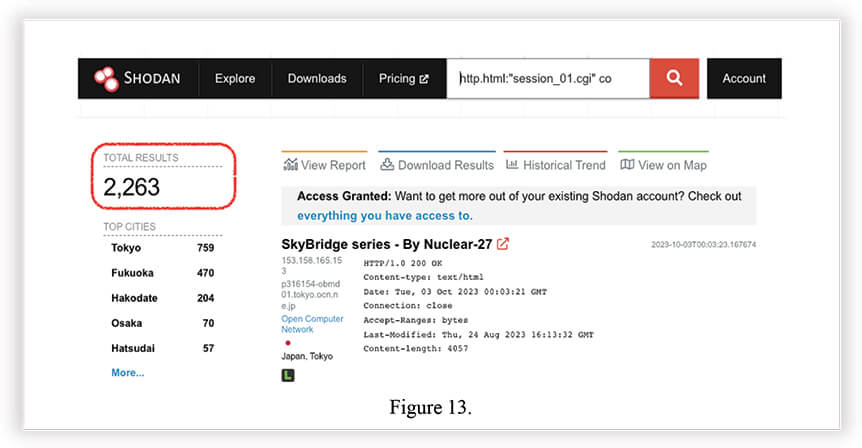
As shown in Figure 13., using the Shodan query provided by Nuclear 27, there are 2,263 results, some of which have their http.title changed to “SkyBridge series – By Nuclear-27” along with WebUI login screen defacement

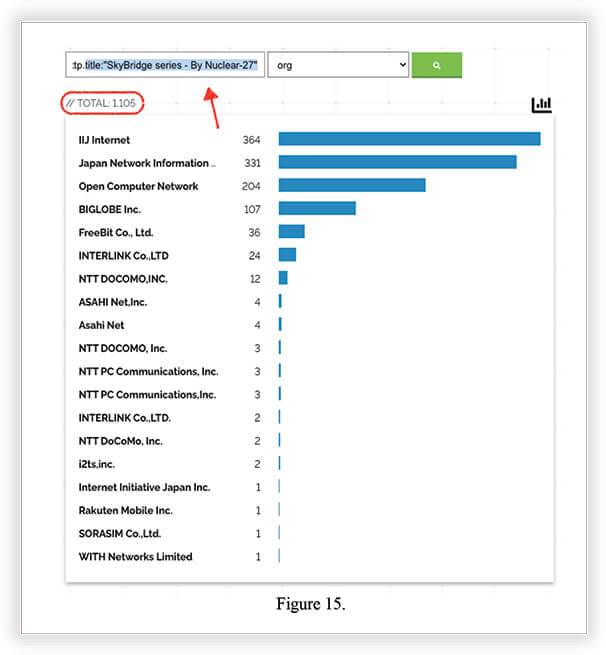
Specifying the query to search for changed titles only, we found Nuclear 27 managed to alter half of the devices – 1,105 found in Shodan. Results are grouped and sorted by Internet Provider Organization.
5. Did Nuclear 27 do any actual damage?
This is challenging to assess without more in-depth knowledge of what all SkyBridge devices are used for. At face value, it appears to be a significant attack on Japanese infrastructure, however, these devices were meant to provide a remote wireless internet connection for simple closed systems like CCTV, payment terminals in Taxi cars, or IPTV for truck cabins in 2014, before ubiquitous high-speed wireless connection. Most of such connections are encrypted, and even access to the router does not immediately present a significant threat beyond denial of service by reboot or shutdown of the device.
Furthermore, we assume most of these devices are old deployments, unlikely to run anything of importance. Threat actors would have to use significant resources on each single router to identify its use case and assess its value for potential lateral movement. This is why they most likely resorted to simple title changes and WebUI defacement for their Twitter posts.
Since the threat actor used a single-use burner account on Twitter and YouTube to send their message, any high-confidence attribution to specific actor is challenging.
With a reasonable degree of confidence, we can rule out Japanese native hacktivists as their primary interest would more likely be to alert fellow citizens about the government spying, however, they have chosen to use both English and Twitter as their platform.
Furthermore, the devices in question are quite niche and manufactured exclusively for the Japanese market, not even working outside Japan, implying threat actors have a long-term interest in and knowledge of Japanese digital infrastructure. This is not common for hacktivists, and understanding Japanese technology requires reading documentation in technical Japanese, which is among the most difficult written languages to learn. That said, however, Chinese and Japanese characters often have contextual overlap, facilitating the learning curve.
Admittedly, this is quite a reach, yet considering the context, the smoking gun appears to be pointing towards Chinese threat actors.
The only other mention beyond Nuclear 27’s own social media accounts is on a suspicious Chinese news website iNews – inf[.]news. Browsing the content of the website in both English and Chinese, it is clear that there are discrepancies with the content.
The article in question is written in a very sensational tone without any apparent understanding of cybersecurity, and the related context in which this activity of Nuclear 27 is being reported. A snippet of the article is shown below in Figure 16.
It appears the motivation for this Nuclear 27 stunt is propaganda, designed to both humiliate and expose the Japanese government for hypocrisy. The target audience is the citizens of the parent nation-state and the message appears to call out and juxtapose the overt surveillance and national pollution of China, with the covert surveillance and pollution via radioactive water allegedly occurring in Japan.
In conclusion, Nuclear 27 did not disclose 0-day RCE vulnerability, did not find government backdoors in Japanese network infrastructure, nor did they conduct a large-scale attack wreaking havoc on the Japanese government or organizations.
With medium confidence, we assess that Nuclear 27 is a nation-state threat actor and has conducted a hijacking of environmental hacktivists’ cause for nation-state propaganda purposes, arguably to highlight the ‘pious hypocrisy’ of the Japanese government. This was achieved using old and patched vulnerabilities to quickly deface WebUI login screens of old IoT routers with unpatched firmware, in order to present an illusion of large-scale attack.