



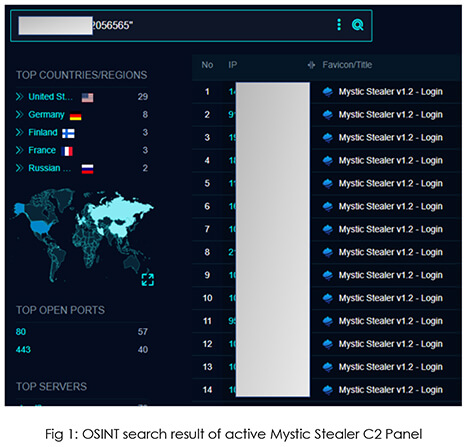
Information stealers pose an ongoing and dynamic threat to the security of both individuals and organizations. CYFIRMA’s Research team recently discovered an information stealer called “Mystic Stealer” being promoted in an underground forum, with the threat actor utilizing a Telegram channel for their operations. This threat actor continuously enhances the malware, incorporating new features to enhance its effectiveness and expand its user base. Our open-source intelligence (OSINT) investigation revealed the existence of over 50 active command and control (C2) servers, indicating the growing prevalence of this threat. Given the consistent demand for potent information stealers, “Mystic Stealer” emerges as a potential contender in this domain. This report provides comprehensive insights into Mystic Stealer’s capabilities and presents our OSINT findings.
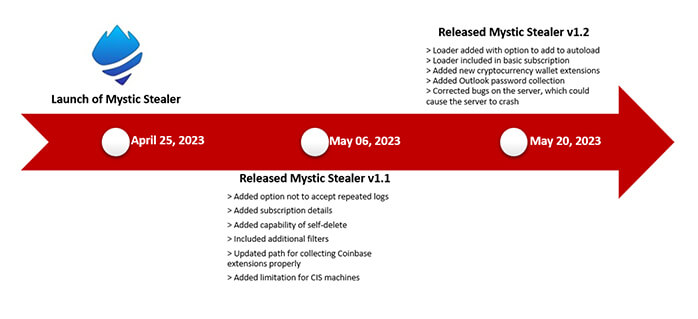
In late April 2023, Mystic Stealer made its debut in prominent underground forums, attracting attention with its advertised features, capabilities, and pricing. Over the subsequent weeks, the stealer was made available for testing to well-known veterans within the forum, who verified its effectiveness and provided valuable feedback for further enhancements. The threat actors diligently incorporated these recommendations into the stealer, resulting in ongoing updates and improvements. Consequently, Mystic Stealer has begun to establish a stronger foothold in the threat landscape, as evidenced by the rising number of command and control (C2) panels observed in the wild.
Well-known veterans in different underground forums have acknowledged the asserted proficiency of the stealer, offering constructive feedback to enhance its performance, resulting in regular updates, aimed at refining the product. Additionally, they have emphasized the threat actor’s friendly and accommodating behavior during the assessment of the builder and malware. Such commendations instill confidence in prospective buyers seeking a reliable stealer malware solution for their operational needs.
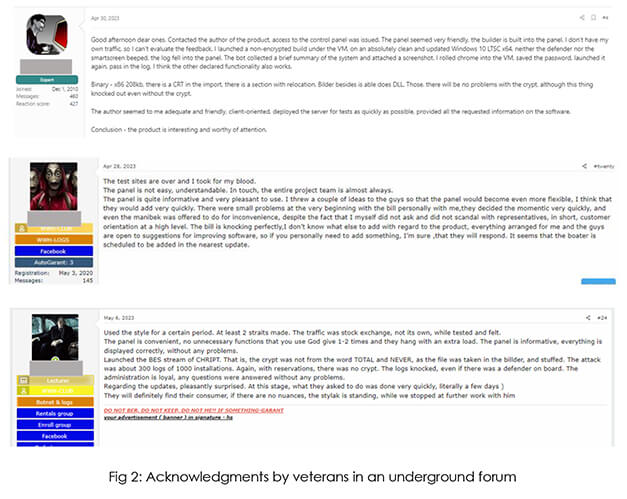
We also observed the threat actor using this positive feedback to gather attention and popularize the stealer in underground forums.
Mystic Stealer, a sophisticated and evolving malware, presents significant risks and potential impacts from the perspective of external threat landscape management. Impact includes data breaches, financial losses, operational disruptions, regulatory compliance challenges, and reputational damage. These sophisticated malware strains covertly infiltrate systems, extracting sensitive information and compromising personal identifiable data, financial records, and intellectual property. The consequences of such breaches include financial liabilities, loss of customer trust, reputational harm, and potential legal repercussions.
Companies that handle sensitive data, such as personally identifiable information (PII), financial records, or intellectual property, are attractive targets for Mystic Stealer. Industries such as healthcare, finance, and technology may be specifically targeted due to the potential value of the data they possess. Along with that, Mystic Stealer specifically targets individuals involved in cryptocurrency transactions. This includes users of cryptocurrency wallets, traders, and those engaged in mining activities. The malware aims to steal cryptocurrency wallets, private keys, or login credentials to gain unauthorized access to these assets.
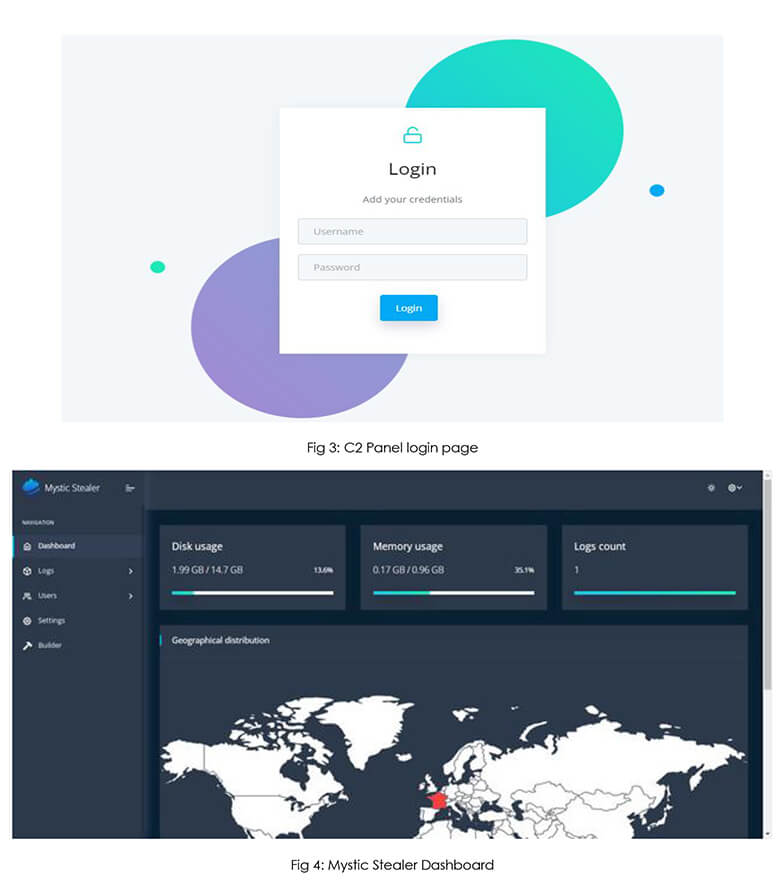
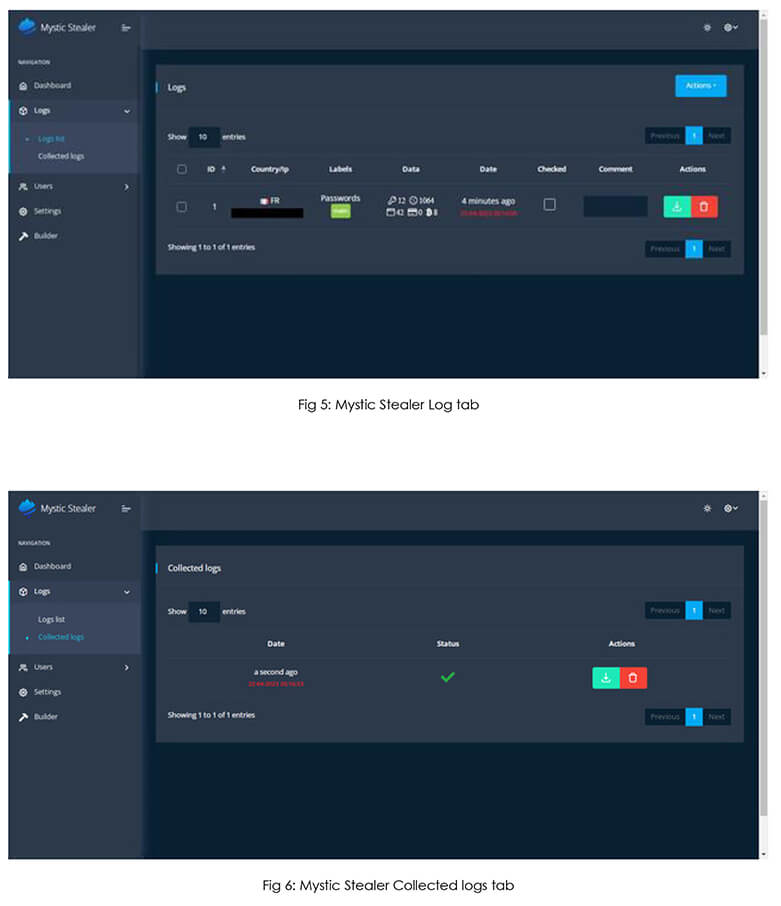
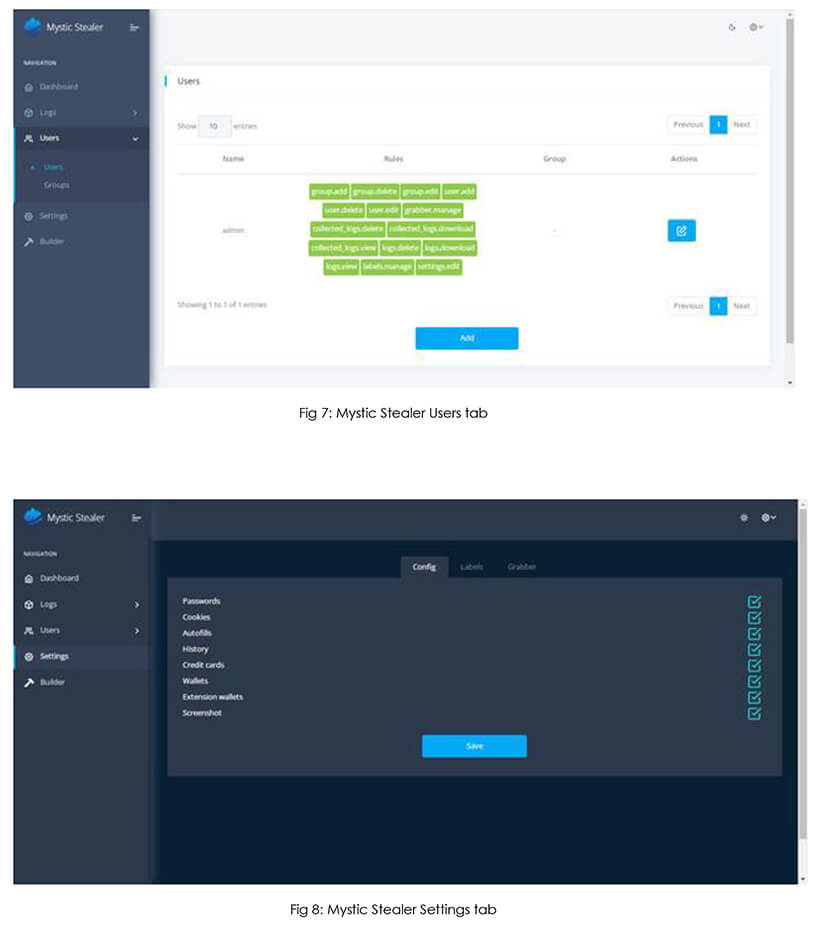
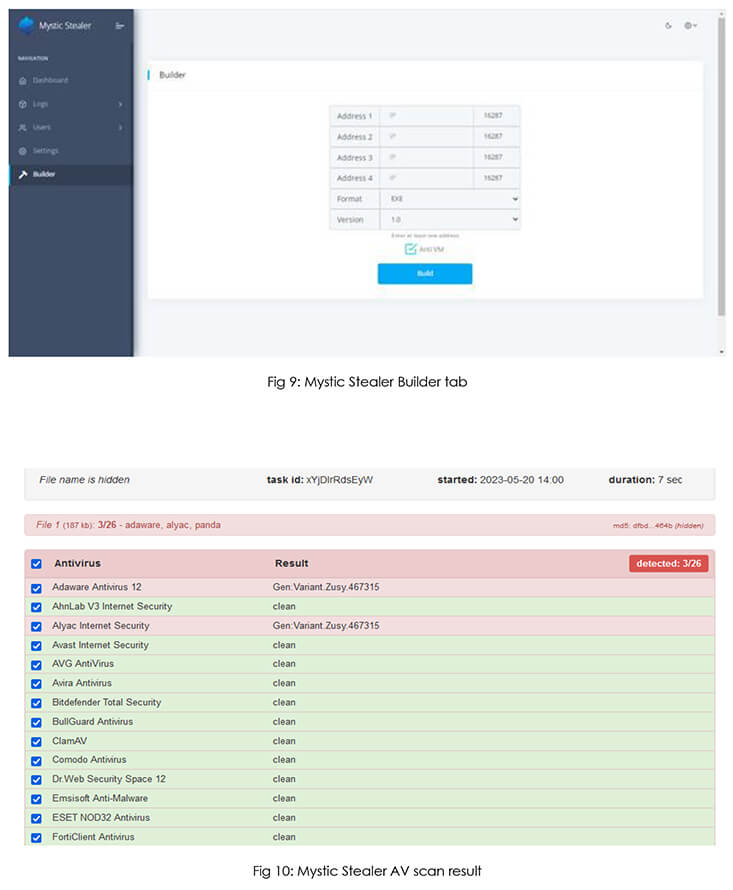
Mystic is an efficient stealer which continuously improves its capability in a short period of time, based on users’ upgrade needs, and provides complete control over data. It is equipped with an individually configurable panel, which is installed on the server, along with a powerful morpher that allows flexible morphing of sources. Additionally, it includes a convenient loader, featuring an autoload function. Mystic is capable of extracting data from browsers that are built on Chromium and Mozilla platforms. Furthermore, it can process information from more than 70 cryptocurrency extensions and Outlook. It is emphasized that all logs are securely stored and decrypted on the server to maximize security and transparency. These capabilities of Mystic Stealer and good reviews by veterans in the underground forum increase its presence in the threat landscape, posing a significant threat to organizations and individuals.
To effectively manage the impact of Mystic Stealer and similar threats, organizations should focus on proactive measures:
Mystic Stealer poses substantial risks and potential impacts from the perspective of external threat landscape management. By implementing a proactive approach to security, maintaining strong defenses, fostering employee awareness, and having effective incident response plans in place, organizations can minimize the impact of Mystic Stealer and enhance their resilience to emerging threats.
| Indicator | Type | Remarks |
| 104.21.27.68 | IP | Command Control |
| 104.21.38.108 | IP | Command Control |
| 104.21.52.152 | IP | Command Control |
| 104.21.60.13 | IP | Command Control |
| 104.21.63.115 | IP | Command Control |
| 104.21.72.247 | IP | Command Control |
| 104.21.74.252 | IP | Command Control |
| 104.21.76.230 | IP | Command Control |
| 104.21.87.169 | IP | Command Control |
| 104.21.88.238 | IP | Command Control |
| 116.202.233.49 | IP | Command Control |
| 142.132.201.228 | IP | Command Control |
| 167.235.34.144 | IP | Command Control |
| 172.67.144.196 | IP | Command Control |
| 172.67.145.114 | IP | Command Control |
| 172.67.154.57 | IP | Command Control |
| 172.67.155.235 | IP | Command Control |
| 172.67.169.8 | IP | Command Control |
| 172.67.184.175 | IP | Command Control |
| 172.67.201.239 | IP | Command Control |
| 172.67.209.76 | IP | Command Control |
| 188.40.116.251 | IP | Command Control |
| 194.169.175.123 | IP | Command Control |
| 194.50.153.21 | IP | Command Control |
| 213.142.147.235 | IP | Command Control |
| 5.42.94.125 | IP | Command Control |
| 89.23.107.241 | IP | Command Control |
| 91.121.118.80 | IP | Command Control |
| 94.130.164.47 | IP | Command Control |
| 95.216.32.74 | IP | Command Control |
| 7c185697d3d3a544ca0cef987c27e46b20997c7ef69959c720a8d2e8a03cd5dc | SHA256 | Sample |