Published On : 2023-09-20
EXECUTIVE SUMMARY
CYFIRMA team actively monitors ongoing cyber conflict between independent hacktivist groups unfolding in Asia and the Middle Eastern Regions. In this ongoing campaign discussed in this report, it seems to have no footprints associated with state-backed threat actors that engage in website defacements and DDoS attacks. While the attacks might not result in significant damage, they are impacting smaller businesses. In our analysis, we delve into this cyber conflict transpiring in the discreet corners of the internet.
INTRODUCTION
The escalating wave of cyber conflicts between hackers from Islamic countries and Indian counterparts has generated significant concerns within the global cybersecurity landscape. Initially perceived as virtual protests against alleged atrocities against Muslims in India, these attacks have taken an unexpected turn, inflicting unintended harm upon small Indian businesses as well as enterprises within the hackers’ home countries. The world has borne witness to a surge in cyber-attacks originating from Islamic countries such as Indonesia, Pakistan, Bangladesh, Afghanistan, and Malaysia. While these attacks have ostensibly been orchestrated against targets in India, hackers in India have also responded with defacements and DDoS attacks in retaliation.
KEY FINDINGS
- The entire cyber conflict doesn’t seem to be backed by governments. Instead, it involves independent hacktivist groups.
- The underlying motivation behind this cyber conflict stems from religious sentiments.
- The hackers primarily employed attack methods like – defacement and flooding websites with malicious traffic; and in a few cases has also resulted in data leaks.
- A noteworthy observation is hackers’ preference for targeting small and lesser- known websites owned by small businesses probably because they have weak security posture which makes them easy targets.
- The hackers have also released data; however, it remains unclear whether the hackers obtained this data through their own breaches or if they have accumulated older leaks from other forums.
- The choice of attack methods and the nature of targets challenge the initial narrative of a purely motivated virtual protest. The multifaceted nature of the attacks suggests that the motivations could extend beyond a singular cause, potentially involving a blend of geopolitical rivalry, competitive hacktivism, and criminal intent.
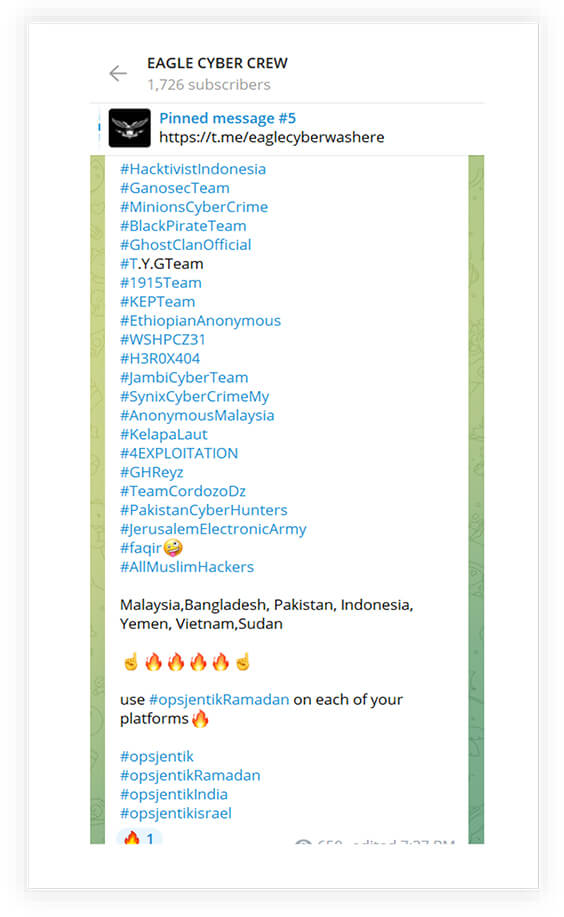
LIST OF THREAT ACTORS INVOLVED
Here is a list of key threat actors involved.
1. Team 1919
- Country: Afghanistan
- Date of Creation: (Date unspecified)
- Description: This threat actor claims to be Afghanistan’s premier cybersecurity team through their Telegram channel. In a recent incident, they defaced several websites.
2. Mysterious Team Bangladesh
- Country: Bangladesh
- Date of Creation: June 19, 2022
- Description: Since its inception, this group has been actively involved in defacing and leaking data. Initially targeting Indian and Israeli entities, they have since expanded their attacks to European countries like Denmark, Sweden, and the Netherlands. The group also operates a subgroup named Mysterious Silent Force, which communicates with followers about their attacks.
3. Indian Cyber Force
- Country: India
- Date of Creation: April 11, 2022
- Description: Initially focused on sharing hacking-related courses and Android RATs, this group has shifted its activities after a year to deface Pakistani and Chinese websites in response to threat actors attacking Indian websites.
4. 1915 Team
- Country: Kurdistan
- Date of Creation: January 19 (Year unspecified)
- Description: This threat actor primarily engages in defacing websites of various countries without disclosing a specific motive. The threat actor targeted Indian assets because of religious orientation.
5. BlackDragonSec
- Country: India
- Date of Creation: January 15, 2023
- Description: engaged in defacement, data leaks, and flooding malicious traffic on websites.
6. EAGLE CYBER CREW
- Country: Malaysia
- Date of Creation: December 3, 2022
- Description: Similar to other threat actors, Eagle Cyber Crew focuses on leaking data, defacement, and DDoS attacks. Their primary targets include India and Israel.
7. Khalifa Cyber Crew
- Country: Indonesia
- Date of Creation: June 19, 2022
- Description: Initially known for defacing Indian websites and leaking Israeli
data, this group has not launched an attack in the last few months. They are recognized for staging virtual protests against nations with anti-Islamic stances.
8. Team Insane PK Official
- Country: Pakistan
- Date of Creation: February 2, 2023
- Description: This group primarily targets countries with perceived anti-Islamic positions. They have attacked European nations and Indian cyber assets, playing a key role in uniting other Islamic threat actors against India, Israel, and Sweden.
9. Team Herox
- Country: Pakistan
- Date of Creation: March 15, 2023
- Description: Sharing the same ideology of targeting Israel and India, this group’s attacks are less frequent. They also engage in propaganda to maintain visibility around their cause.
10. GANOSEC TEAM
- Country: Indonesia
- Date of Creation: May 21, 2021
- Description: Originating from Indonesia, this threat actor initially targeted India and Israel. They continue to focus on defacing Israeli and Indian websites.
11. 177 Members Team
- Country: Indonesia
- Date of Creation: (Date unspecified)
- Description: Following a ban on their Telegram channel, this group recently created a new one.
12. Indian Cyber Mafia
- Country: India
- Date of Creation: March 30, 2023
- Description: Aligned with the Indian Cyber Force’s ideology, this group occasionally engages in defacement, including targeting Pakistani websites. They also provide support to other like-minded cybercriminal and threat actor groups, expressing support for the freedom of Baluchistan in one of their defacements.
13. Indian Cyber Troops
- Country: India
- Date of Creation: June 1, 2021
- Description: Initially sharing ethical hacking courses and political content, this group has recently been observed defacing Pakistani websites in retaliation to actions by other threat actors.
14. Team UCC Operations
- Country: India
- Date of Creation: July 27, 2022
- Description: Highly active in attacking the cyber infrastructure of Pakistan and Bangladesh, this threat actor employs DDoS attacks, data leaks, and website defacements extensively.
15. Anonymous Israel
- Country: Israel
- Date of Creation: April 20, 2023
- Description: Created in response to threat actors from Malaysia, Indonesia, and Pakistan, this group exclusively uses DDoS attacks to take down websites. Notably, individual members, rather than government sponsorship, drive their efforts to counterattacks against Israel.
16. TAF (Team Anon Force) ATTACK ZONE
- Country: Bangladesh
- Date of creation: 10th Sept 2023
- Description: This newly formed group has initiated its operations through a Telegram channel. Hailing from Bangladesh, they operate as a hacktivist group, launching attacks as a form of protest in support of their Muslim community.
ANALYSIS
To identify the threat actors involved in this small-scale cyber conflict, we analyzed the Telegram channels used by these threat actors to orchestrate cyberattacks against websites in different countries. We found that these independent hacktivist groups engage in trolling, abusive behavior, and communal accusations, which they use as a pretext for launching cyberattacks. Below is an analysis of a few attacks.
The below two screenshots show one of the threat actors threatening to attack India, Sweden, and Israel for insulting Islam.
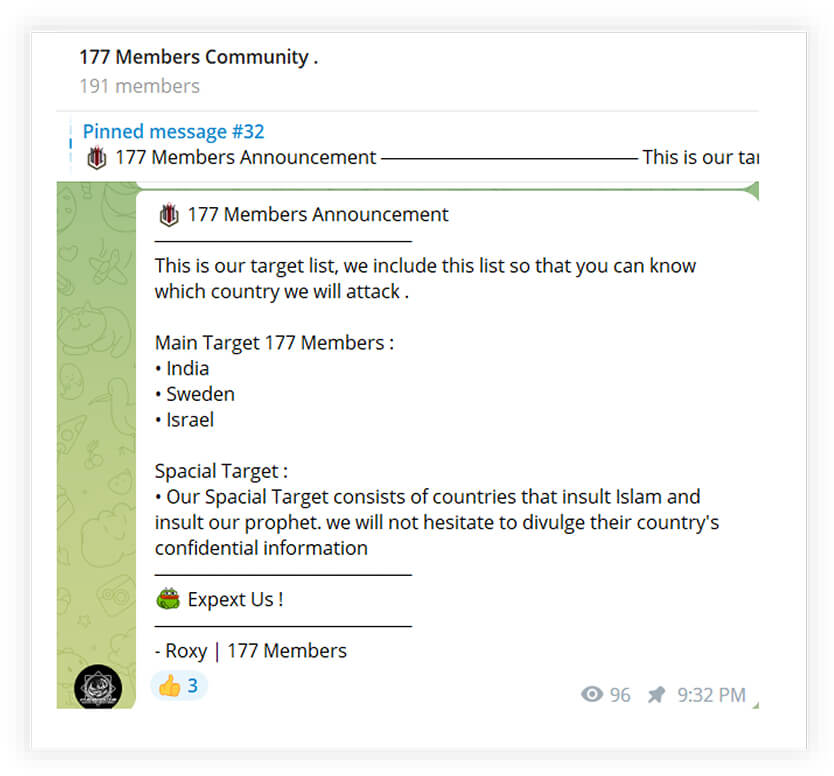
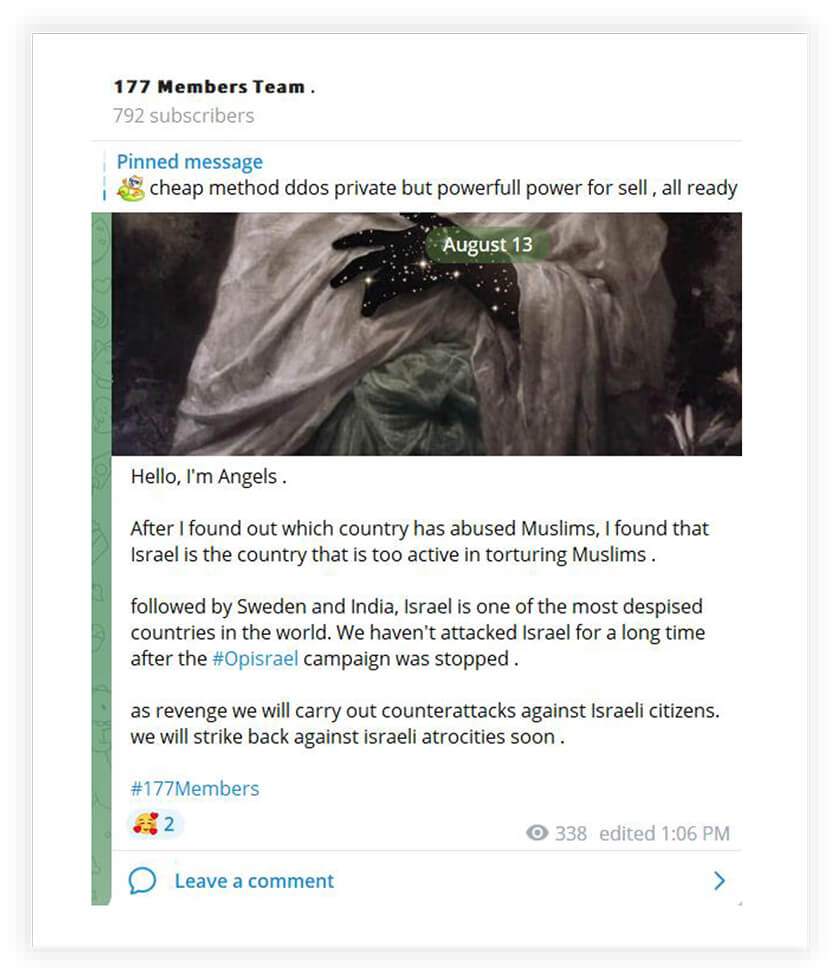
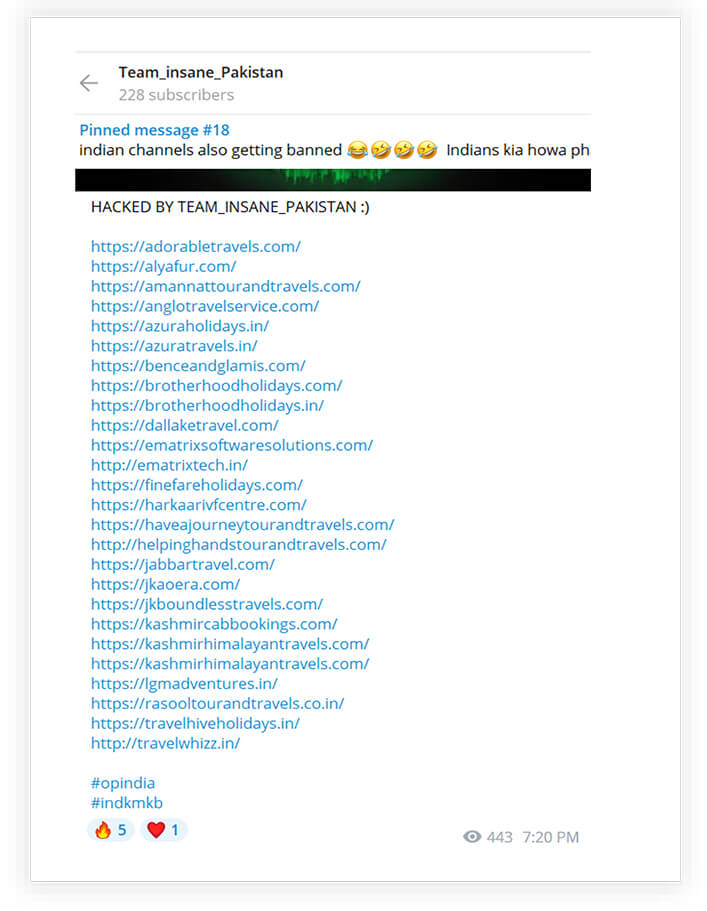
The below screenshot shows a telegram post of the threat actor named Team Insane that defaced websites from the Indian region. The threat actor has been defacing websites for a very long time, however, the websites targeted recently were part of #opIndia campaign that started before the G-20 meeting. The list of websites clearly indicates websites are part of a web server that hosts travel companies’ websites.
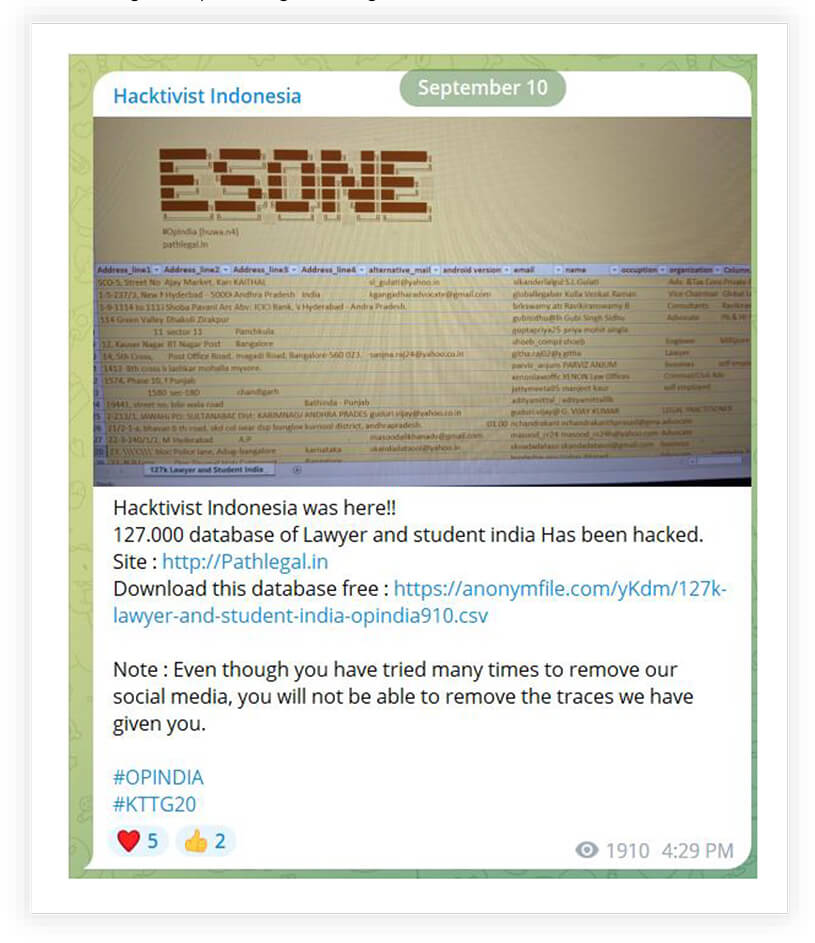
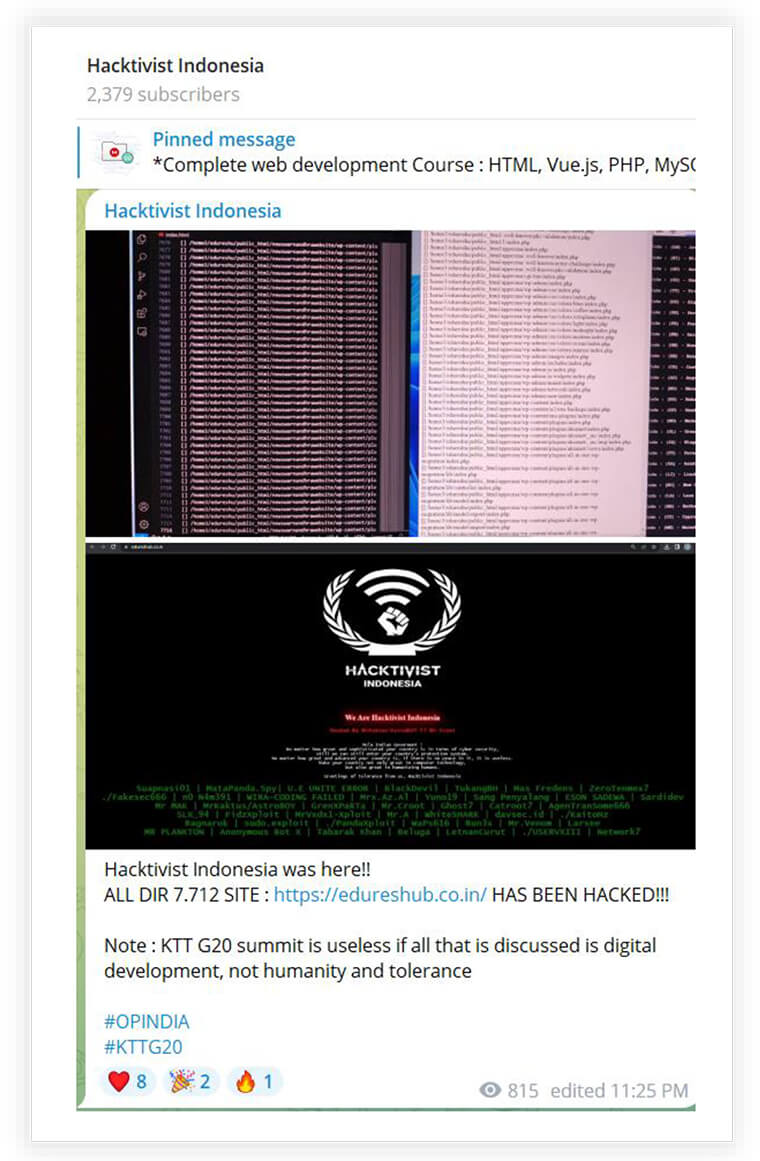
In the two screenshots below, the threat actor has leaked data and defaced a website during the G-20 summit. The threat actor belongs to Indonesia and executed these attacks to lodge their protest against alleged atrocities on Muslims.
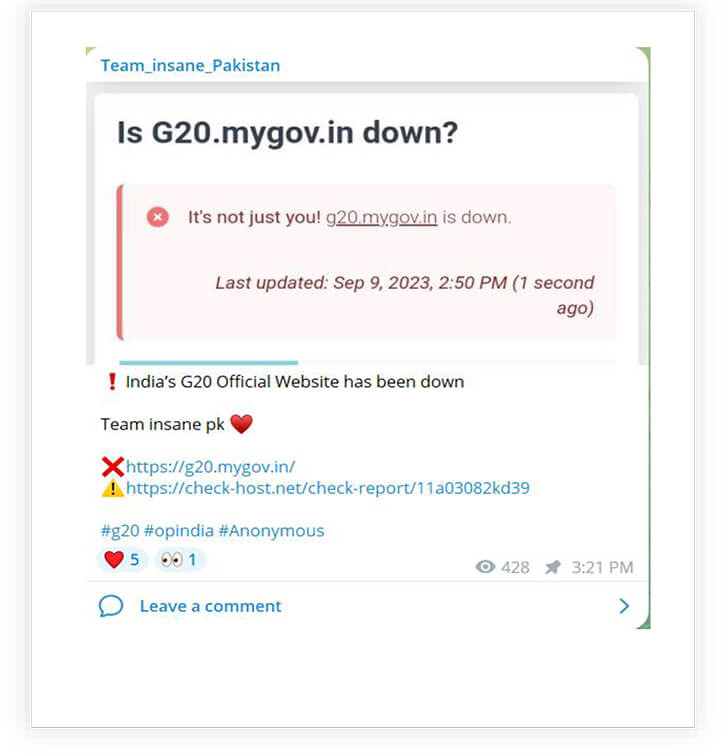
The below screenshot shows, a Pakistan-based hacktivist claiming to take down the official website for the G20 Summit after flooding malicious traffic for a DDoS attack.
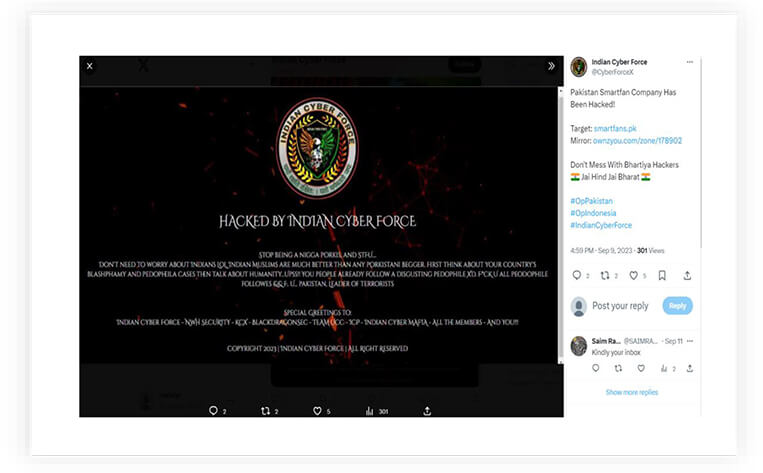
As seen in the screenshot below, it shows Indian threat actors defacing the Pakistani domain, where they are responding back to threat actors involved in attacking Indian cyber assets. The deface page warns the religiously backed group to stop worrying about the minority in India, instead asking them to focus on their country.
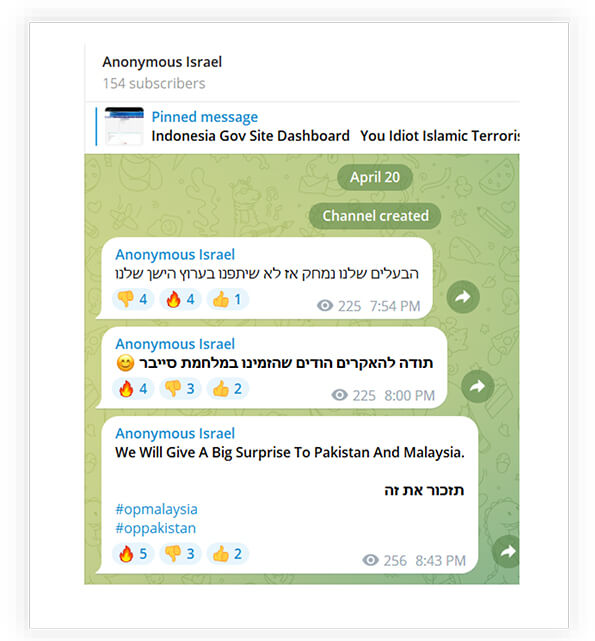
The screenshots below show Israeli hacktivists joining the mini-war and raising their voice against the attackers. It is rare to see Israeli-based groups involved in such attacks.
As seen below, it’s evident that one of the hacktivists is displaying a sign of unity with other threat actors, with the intention of targeting countries they believe are implicated in alleged atrocities against Muslims.
EXTERNAL THREAT LANDSCAPE MANAGEMENT (ETLM)
The conflict between Russia and Ukraine has led to the emergence of new cyber threat groups on both sides. These groups, which call themselves hacktivists, carry out cyberattacks, such as distributed denial-of-service (DDoS) attacks, against their adversaries. Hacktivism has proven to be a remarkably effective way to spread protests and opinions towards driving a pre-conceived agenda. Both Russia and Ukraine have used hacktivist groups to convey their messages and gain support or drive dissent. This approach has become a trend, with groups and individuals having political, religious, and protest motivations, using it as well. As a result, what began as isolated actions in the wake of the Russia-Ukraine war has evolved into smaller-scale cyber conflicts in other regions where the modus operandi has been used to adversely affect small businesses and disrupt their operations. This trend is likely to continue, potentially leading to the emergence of more groups using similar tactics to express their protest and support.
CONCLUSION
Our analysis shows that most of the cyberattacks have disproportionately affected small businesses that necessarily do not have any involvement whatsoever in religious disputes. Specifically, threat actors from Islamic nations have been targeting Indian and Israeli cyber assets and entities to protest alleged anti-Islamic sentiments.
Watch this space as the action will continue to heat up on this front.












