



The Jenkins CVE-2024-23897 vulnerability poses a severe threat, allowing remote code execution (RCE) and arbitrary file read. Exploiting this flaw could lead to unauthorized access, data breaches, and compromise of the Jenkins automation environment. This requires immediate attention, and organizations utilizing Jenkins are strongly advised to implement mitigation measures swiftly.
The CYFIRMA Research team has conducted an in-depth analysis of a critical vulnerability affecting ‘Jenkins’; a popular open-source automation server widely used in software development. Tracked as CVE-2024-23897, the vulnerability was first identified on January 24 of this year and has since garnered significant attention from the cybersecurity community. This research aims to provide a comprehensive understanding of the Jenkins CVE-2024-23897 vulnerability, its implications, and effective mitigation strategies.
Key Takeaways:
Acknowledgements:
CYFIRMA Research acknowledges the collaborative efforts of security researchers and the cybersecurity community in identifying and addressing the CVE-2024-23897 vulnerability.
Vulnerability Type: Unauthenticated Remote Code Execution (RCE)
CVE ID: CVE-2024-23897
CVSS Severity Score: 9.8 (Critical)
Application: Jenkins
Impact: Allows unauthenticated attackers to execute arbitrary code and read arbitrary files by exploiting a critical remote code execution vulnerability.
Severity: Critical
Affected Versions: Multiple versions of Jenkins are impacted. Check here
Patch Available: Yes
Mitigation: Organizations are strongly advised to apply the latest security updates and patches promptly.
The CVE-2024-23897 vulnerability in Jenkins core is rooted in a flaw that allows attackers to execute arbitrary code remotely and read arbitrary files. The vulnerability arises from inadequate input validation in the Jenkins server, enabling malicious actors to exploit the system by crafting specifically designed inputs. An attacker could leverage this vulnerability to execute arbitrary commands and access sensitive information, leading to unauthorized data access and potential system compromise.
The potential impact of CVE-2024-23897 is significant. Successful exploitation could result in unauthorized access to Jenkins servers, compromise of sensitive data, and the execution of malicious code. This could have far-reaching consequences for organizations relying on Jenkins for their automation needs, affecting software development processes and the security of sensitive information.
Jenkins: 2.0 – 2.441 and Jenkins LTS: 2.7.1 – 2.426.2 are affected. The range of affected versions underscores the importance of a thorough review to ensure comprehensive protection. Check here.
Is there already an exploit tool to attack this vulnerability?
As of the latest available information, there is a known public exploit tool for CVE-2024-23897 targeting Jenkins.
Has this vulnerability already been used in an attack?
Regarding exploitation, there is no specific information confirming active exploitation of CVE-2024-23897 at the moment. Continuous monitoring is crucial to detect any emerging threats or exploitation activities.
Are hackers discussing this vulnerability in the Deep/Dark Web?
In terms of discussions in the Deep/Dark Web, CYFIRMA’s observations have not identified current discussions or potential exploitation of CVE-2024-23897 in these forums. The dynamic threat landscape emphasizes the importance of ongoing monitoring to promptly identify any evolving discussions or emerging threats.
What is the attack complexity level?
The attack complexity level for CVE-2024-23897 in Jenkins is assessed as LOW. Although there is currently a public exploit tool available, organizations should remain vigilant, prioritize mitigation efforts, and stay informed about the vulnerability’s status.
Historical trends and known Exploits:
As for historical trends and known exploits, there are limited known exploits or historical trends for Jenkins, however, organizations should recognize the potential risks associated with vulnerabilities by staying proactive in applying updates and implementing security measures to prevent unauthorized access, data breaches, or compromise of Jenkins environments. Regular updates and a proactive security stance are essential to safeguard against evolving cyber threats.
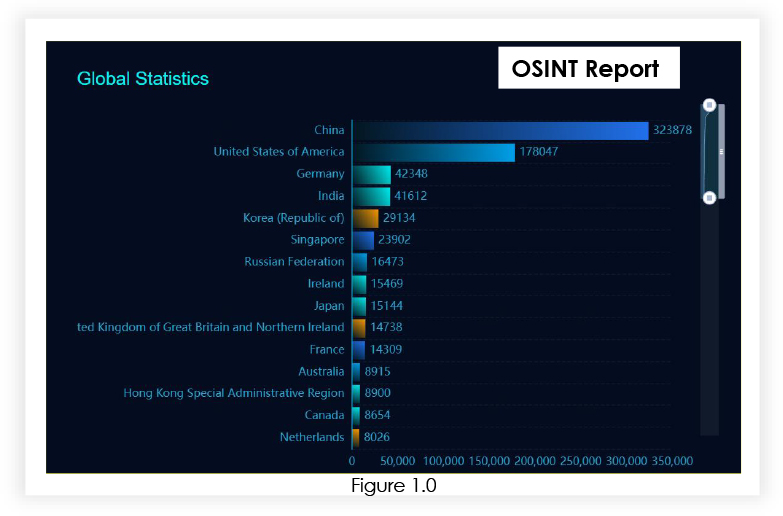
Our analysis found that more than 818,061+ Jenkins are public and can be vulnerable to CVE-2024-23897.
The vulnerability exposes a loophole, allowing unauthorized manipulation of file upload parameters, potentially resulting in remote code execution.
Utilizing threading and HTTP requests, the exploit executes concurrent download and upload operations on targeted Jenkins servers. This approach enhances the exploit’s efficiency, crucial for effective penetration testing.
A standout feature is the exploit’s adaptability in specifying target hosts. Supporting single IP addresses, IP ranges, lists of IPs, or CIDR blocks, it demonstrates versatility across diverse network configurations.
During execution, it dynamically generates unique session IDs for each target, contributing to stealth in exploitation. These session IDs play a pivotal role in both download and upload requests, providing a seamless tracking mechanism across multiple targets.
The download request, with session ID and specific headers, further demonstrates their nuanced approach. The upload request simultaneously integrates the session ID and uploads specific headers and a binary data payload. This payload, encoded as ‘data_bytes,’ emulates a file upload, replicating a realistic attacker scenario.
In addition to its intricate functionality, it prioritizes usability: handling potential errors gracefully, it provides informative error messages, and users can log these messages for post-exploitation analysis.
Immediate action is crucial to mitigate the risks associated with CVE-2024-23897. Organizations are advised to apply the latest Jenkins security updates and patches promptly. Additionally, implementing strong access controls, regularly monitoring Jenkins server activity, and employing network-based security measures can further reduce the risk of exploitation. Timely and comprehensive mitigation efforts are essential to safeguard against potential security breaches and ensure the continued secure operation of Jenkins environments.
Target Geography:
Organizations worldwide relying on Jenkins, encompassing the affected versions of CVE-2024-23897, face potential risks. The geographical impact of this vulnerability spans across regions such as North America, Central Europe, Asia, and other areas where Jenkins is prevalent. Organizations globally, irrespective of their location, may be exposed to the risk of exploitation if they utilize the impacted versions of Jenkins.
Target Industry:
The CVE-2024-23897 vulnerability in Jenkins poses a threat to organizations across various industries, including healthcare, finance, government, telecommunications, and others reliant on Jenkins for automation processes. Threat actors with knowledge of this vulnerability may selectively target industries based on the perceived value of the data or services facilitated by Jenkins. Industries handling sensitive information or heavily dependent on Jenkins for automation may become specific targets.
Target Technology:
The CVE-2024-23897 vulnerability specifically impacts Jenkins; a critical automation server widely used for software development. While the immediate impact is on Jenkins instances, successful exploitation may extend beyond, compromising interconnected systems, applications, and servers linked with Jenkins. This amplifies the potential impact on an organization’s technological infrastructure, emphasizing the need for comprehensive mitigation measures.
Understanding the potential impact across different geographic regions, industries, and technologies is imperative for organizations to assess their exposure to CVE-2024-23897. It underscores the urgent need for addressing the issue through prompt patching, proactive security measures, and continuous monitoring to mitigate the risks associated with this critical vulnerability.
Currently, there are ongoing discussions of this vulnerability, however, there is no mention or indication of the sale of any exploits on the forum.
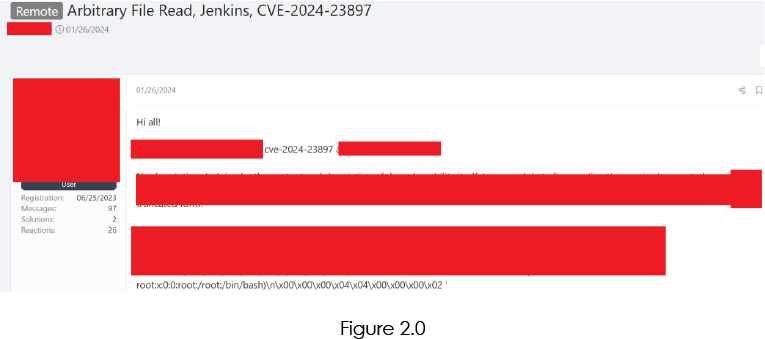
In conclusion, CVE-2024-23897 poses a critical threat to organizations globally, irrespective of industry or geographical location, due to its potential for unauthenticated remote code execution in Jenkins. Urgent mitigation measures, including prompt patching, proactive security measures, and continuous monitoring, are imperative to safeguard against potential unauthorized access, data breaches, and compromise of automation processes. Organizations should prioritize addressing this vulnerability to ensure the secure operation of their Jenkins environments.