



This report is a comprehensive analysis of the cybersecurity hurdles confronting Japan’s highly developed economy. Positioned as the world’s third-largest economy by nominal GDP and renowned for its innovation and technological prowess, Japan plays a pivotal role in global markets through critical sectors like automobile manufacturing, high-tech goods production, and robotics. These sectors are not only essential for domestic prosperity but also hold global significance.
While Japan’s advanced economy stands as a hallmark, it remains susceptible to the ever-evolving cyber threat panorama. The report accentuates the importance of Japan’s economy, underscoring its stature as the second-largest automobile manufacturer and a key player in high-tech manufacturing, integrated circuits, hybrid vehicles, electronic equipment, robotics, and precision goods. These sectors collectively underpin Japan’s economic prowess.
This report aligns Japan’s strides in technology with the increased attention of both state-sponsored and non-state cyber threat actors, with a notable focus on the escalating economic and technological competition from countries such as China and South Korea. Within this dynamic context, Japan grapples with cyber threats targeting its industrial and innovation sectors, threats that have grown increasingly sophisticated and persistent over time.
Manufacturing Mastery: Manufacturing contributes significantly to Japan’s GDP, accounting for approximately 20%. This includes automobiles and industrial robots, to semiconductors and machine tools. Tokyo-based startups have ventured into supplying robots and satellites to the burgeoning global space industry, poised to generate over US$1 trillion in revenue by 2040.
Driving Forces in Automotive: Japan’s automotive industry ranks among the world’s largest, consistently securing a spot in the top three car manufacturing countries since the 1960s, even surpassing Germany. An array of companies produces a wide range of vehicles and engines, with prominent manufacturers like Toyota, Honda, and Nissan. This industry, including its global subsidiaries, remains under constant surveillance by financially motivated and APT threat actors keen on monetary gain and intellectual property theft.
Aerospace Excellence: Renowned for its global leadership in aerospace research and development (R&D), Japan’s space program encompasses various government ministries, offices, and agencies. The wealth of data within this industry serves as a prime target for APT actors, holding immense value.
Steel’s Global Dominance: Japan’s steel industry boasts advanced technology, particularly in the production of high-grade steel, giving it a competitive edge over foreign counterparts. Ranking third globally in crude steel production, Japan produced 83.19 million tons in 2020. Operating on a global scale, the industry exports its domestically produced steel, particularly to rapidly developing Asian markets, while playing a pivotal role in supporting essential global infrastructure.
Thriving Fastener Industry: Japan’s fastener industry (i.e nuts, bolts, and screw manufacturing) is a formidable economic force, comprising approximately 3,000 manufacturers generating yielding roughly one trillion yen worth of fasteners annually, along with about 400 distributors and trading companies, yielding around 450 billion yen in annual revenue.
Japan’s diverse industrial sectors and cutting-edge technology products make it an appealing target for nation-state attackers and financially motivated threat actors. Furthermore, hacktivists have also been observed targeting Japanese industries alongside APT and other threat actors, reflecting the multifaceted cybersecurity challenges these sectors face.
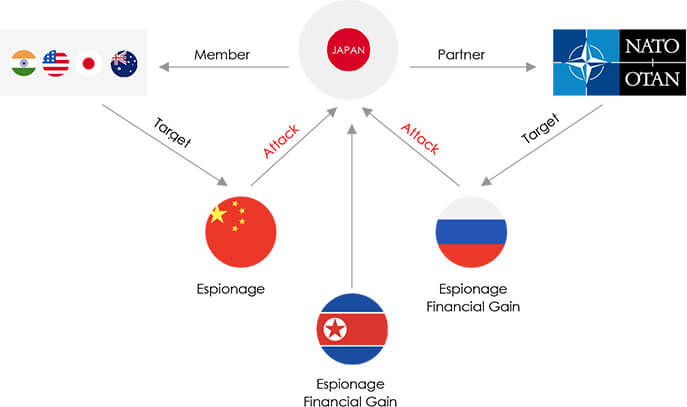
From a geopolitical standpoint, Japan confronts substantial challenges stemming from China, Russia, and North Korea. These challenges relate to regional dominance, its strategic alliances with QUAD and NATO, as well as ongoing territorial disputes.
Japan’s geopolitical risk factors in relation to China have shifted significantly in recent years. After World War II, Japan adopted a strong pacifist stance, prioritizing economic growth over military expenditure. However, the rise of China’s expansionist policies in the Indo-Pacific, particularly the looming threat of a Chinese invasion of Taiwan, has prompted Japan to reevaluate its security posture. Japanese Prime Minister Fumio Kishida’s announcement to double defense spending from one to two percent of GDP signifies a substantial departure from the country’s historical defense policy. This change, which builds upon the efforts of the previous Prime Minister Shinzo Abe, reflects Japan’s increasing focus on countering China and deepening military integration with the United States. As Japan strategically shifts military capabilities to its southwest islands, Taiwan emerges as a key flashpoint in its security considerations.
In essence, Japan’s evolving geopolitical risk factors with respect to China are characterized by a departure from decades of pacifism, a substantial increase in defense spending, a growing emphasis on countering Chinese influence, and a heightened awareness of Taiwan’s significance as a potential security flashpoint. These developments represent a significant transformation in Japanese security policy as it adapts to changing regional dynamics and challenges posed by China’s assertive posture in the Indo-Pacific.
During the Cold War, Japan primarily focused on the threat posed by the Soviet Union, positioning its limited military capabilities in the northern regions. However, with the end of the Cold War, Japan shifted its attention towards the threat emanating from North Korea in the east.
In recent years, North Korea has been escalating tensions through a series of missile tests and nuclear posturing on the Korean Peninsula. The year 2022 witnessed unprecedented missile tests, including intercontinental ballistic missiles fired over Japanese territory. Furthermore, North Korea has strengthened its alignment with Russia and China, pledging closer strategic and tactical cooperation, which enables North Korea to conduct more aggressive testing with relative impunity.
In addition to this, North Korea’s export of weapons to Russia for its war in Ukraine, possibly in exchange for cyber know-how and intelligence, raises concerns about the potential for North Korean cyber activities. Japan, along with South Korea and Australia, is among the most exposed geographies to North Korean cyber activities, however, North Korean threat actors are known for their opportunistic approach, engaging in criminal activities, such as ransomware-based operations to generate financial profit wherever opportunities arise.
Japan’s relationship with Russia has been strained due to a longstanding territorial dispute over the Kuril Islands, known as the Northern Territories in Japan. Recent developments indicate a significant change in Japan’s rhetoric concerning these disputed islands: Japanese Foreign Minister Yoshimasa Hayashi has accused Russia of occupying the Northern Territories without legal grounds, while Prime Minister Fumio Kishida asserted Japan’s sovereignty over them.
This shift in Japan’s stance follows Russia’s aggression in Ukraine and contrasts with the previous administration’s efforts to resolve the territorial dispute peacefully using softer language. While Russia’s current military capacity may not permit overt provocation, concerns have arisen about the use of cyberattacks to caution Japan not to overstep boundaries regarding the disputed islands.
Japan’s changing security posture is not occurring in isolation. It is part of a broader transformation in the U.S.-Japan alliance, involving South Korea, Australia, and the Philippines in defense alliances. This shift is in response to China’s assertive behavior in the region; a more capable North Korea, and Russia’s growing discontent, potentially leading to unpredictable actions against states with which it has territorial disputes.
These geopolitical factors require Japan to maintain a vigilant and adaptive approach to its national security and defense strategies.
We observed 73 campaigns targeting various industries in Japan during 2023. Chinese, Russian, and North Korean state-sponsored threat actors are behind most of these campaigns.
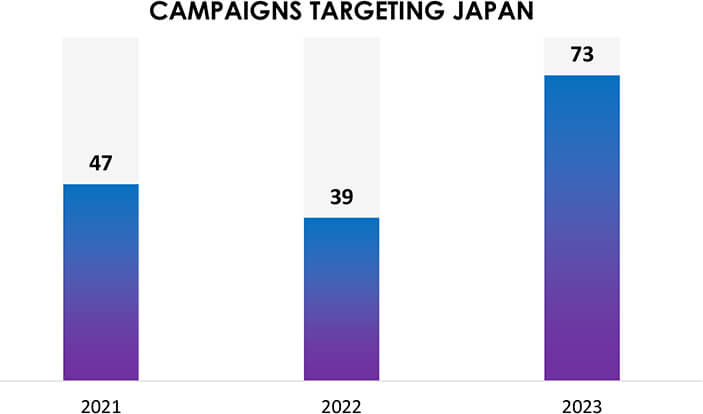
The number of observed campaigns significantly increased compared to the last two years, indicating threat actors’ interest in the economic and intellectual superpower; Japan.
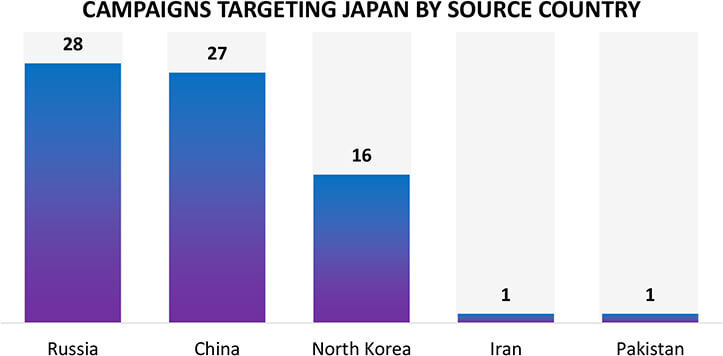
In 2023, both Russian and Chinese threat actors actively targeted Japan. Meanwhile, North Korean threat actors doubled their campaign compared to 2022 (8).
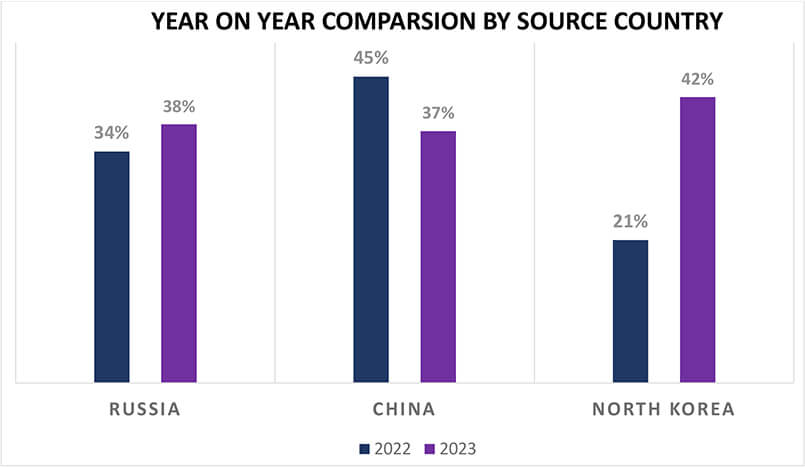
Year-on-year campaign comparisons highlighting geopolitical tensions, play a major role in cyber-attacks on Japan, especially due to Japan’s stand on the Russia-Ukraine war and Japan’s active involvement in global forums like QUAD and Asia Pacific matters.
Recent incidents of data breaches have come to light in Japan. Here are some notable cases:

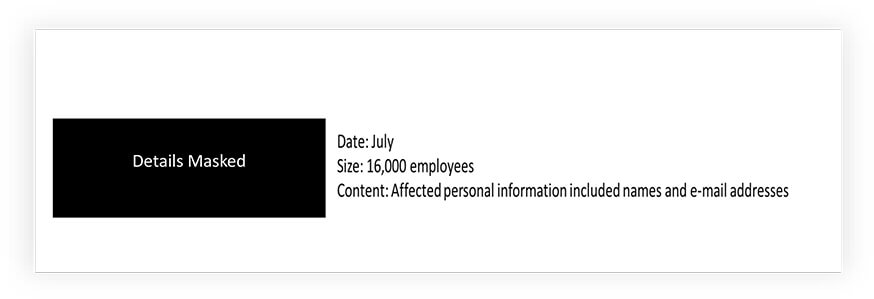
The research team observed a data leak associated with a Japanese org, which contains employees’ email, phone numbers, and administration panel credentials.
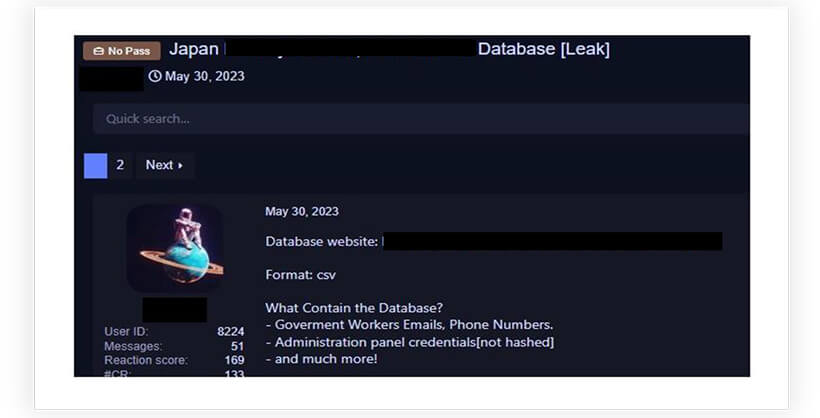
Japan’s foremost email platform experienced a data breach that subsequently became available for sale on a well-known hacking forum. This security incident led to the exposure of 1.3 million records, encompassing 580,000 distinct email addresses, as well as usernames, IP addresses, and MD5 password hashes.
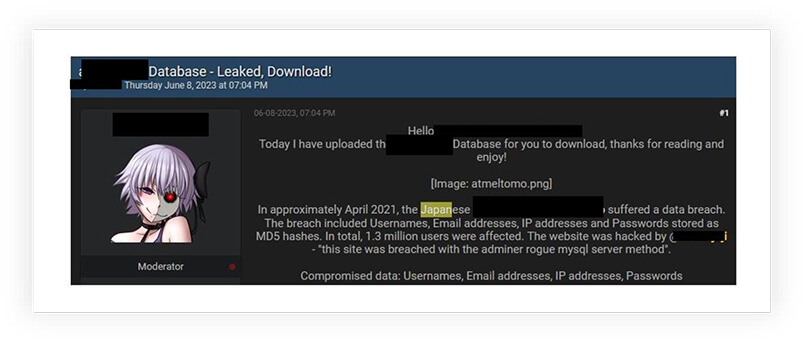
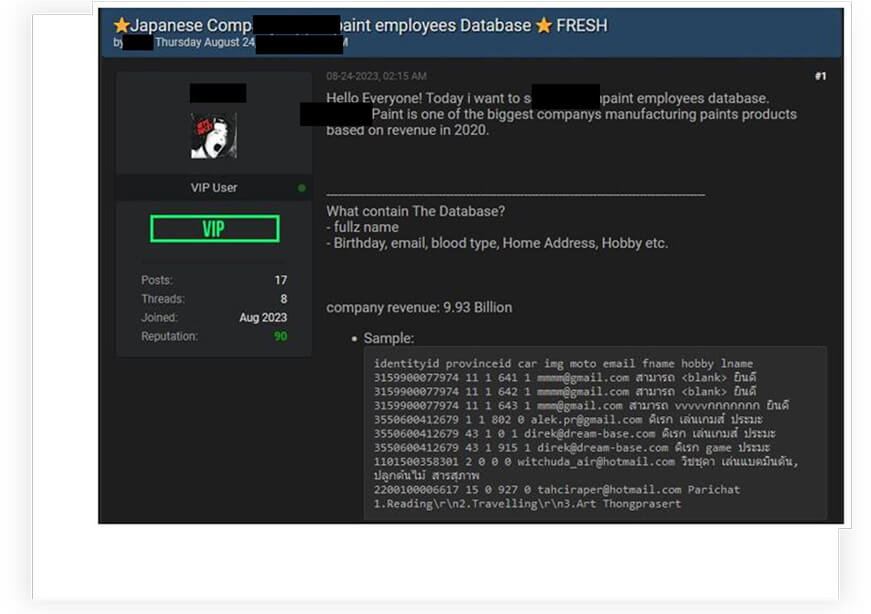
One of Japan’s largest manufacturers of paint products, fell victim to a data breach that was later made available for purchase on a widely recognized hacking forum. This cybersecurity incident resulted in the compromise of the company’s employee database, which included personal details such as names, birth dates, email addresses, blood types, addresses, hobbies, and more.
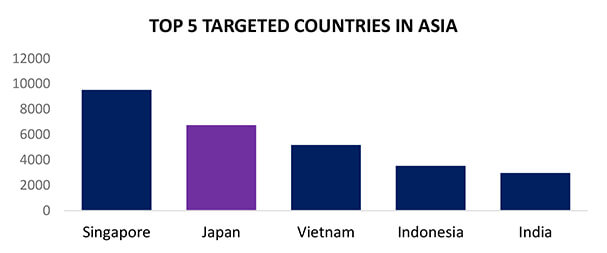
During the period spanning from January 1st to September 4th, CYFIRMA’s advanced telemetry systems meticulously detected a staggering total of 493,395 phishing campaigns. Within this extensive dataset, it’s noteworthy that Japan emerged as the second-most targeted geographic region in Asia.
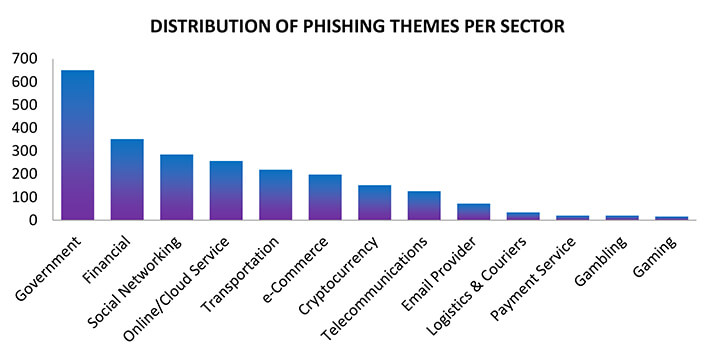
The observed campaign in Japan reveals several prominent themes exploited in phishing attacks. Among these, the sectors most frequently targeted include Government, Financial, Social Networking, Online/Cloud Services, and Transportation. These findings shed light on the diverse range of sectors that malicious actors are leveraging to carry out phishing attacks within Japan. Understanding these prevalent themes is crucial for enhancing cybersecurity measures and safeguarding against the evolving tactics employed by cybercriminals.

APT 29, Cozy Bear, The Dukes
APT 29 is a highly dedicated and organized cyberespionage group. This sophisticated group predominantly focuses its cyber operations on Western governments and affiliated entities, including governmental ministries and agencies, political think tanks, and contractors engaged in government-related activities.
APT 28, Fancy Bear
APT 28 is a Russian state-sponsored hacking group closely affiliated with the Russian intelligence service.

MISSION2025, APT 41
MISSION2025 is suspected to be a Chinese state-sponsored threat actor, possibly working for the Chinese government. This threat actor’s activities are believed to have been ongoing since at least 2012. Their operational scope encompasses a wide array of campaigns directed at organizations spanning diverse industries, including but not limited to Automotive, Retail, Healthcare, Energy, Hi-Tech, Media, Finance, Telecom, Supply Chain, and Travel. The focus of MISSION2025’s targeting aligns closely with China’s national strategies, notably exemplified by “Made in China 2025,” a comprehensive plan unveiled in 2015. This strategic initiative seeks to steer China’s economic landscape towards the production of higher-value goods and services, reflecting MISSION2025’s apparent objectives and the broader context of its cyber activities.
ChamelGang
ChamelGang is a recently identified APT group that has emerged with a distinct focus on infiltrating the fuel and energy sector and the aviation industry. This group employs various tactics, including the exploitation of well- known vulnerabilities like Microsoft Exchange Server’s ProxyShell. They also utilize a combination of both newly developed and pre-existing malware to breach network defenses and compromise targeted systems within these critical industries.

Kimsuky
Kimsuky, an advanced persistent threat (APT) group hailing from North Korea, has a well-documented history of conducting targeted attacks worldwide. Their primary mission revolves around collecting valuable information and engaging in espionage activities in the service of the North Korean government. Notably, Kimsuky’s recent campaigns have zeroed in on critical geopolitical issues, including nuclear agendas and conflicts. This showcases their remarkable adaptability and skill in leveraging contemporary events to advance their operations effectively.
Lazarus Group
The Lazarus Group, a cybercriminal organization of remarkable sophistication, maintains strong ties to the North Korean government. Their primary motivation revolves around achieving financial gains, a means of circumventing enduring sanctions imposed against the regime. Notably, they possess the capacity to swiftly develop, adapt, and refine existing exploits and malware within their specialized malware development unit. In their most recent endeavors, Lazarus Group has shifted their focus towards targeting cryptocurrency exchange companies.
Ransomware operators are continuously improving their techniques with the intent to intimidate and force victims to pay the ransom. At present, ransomware operators are suspected to follow a 4-layer approach to targeting organizations which includes:
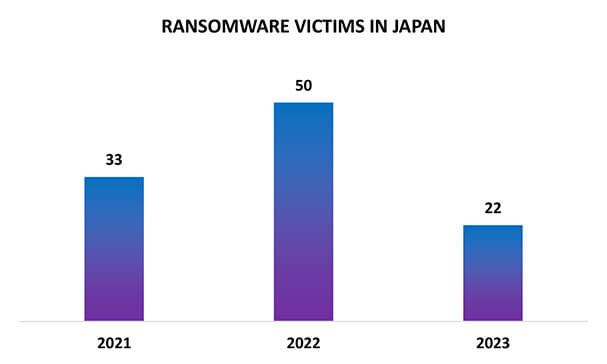
Japan stands out as one of the prominent targets of ransomware attacks in the Asia Pacific region. Among the sectors within Japan, the automotive, manufacturing, IT, and entertainment industries have experienced the most pronounced impact from these ransomware incidents. Notably, this threat landscape is influenced by formidable ransomware groups, including LockBit, BlackCat (Alphvm), and Cl0p, which feature prominently on the list of perpetrators targeting Japanese companies.
During our Open-Source Intelligence (OSINT) investigation, we discovered a substantial volume of internet-connected devices and systems linked to Japan. Specifically, our search revealed a staggering count of approximately 300,000 systems that exhibit vulnerabilities within the multiple versions of the Apache HTTP Server. These vulnerabilities span a spectrum from critical to medium severity, underscoring the potential risks associated with this widespread exposure.
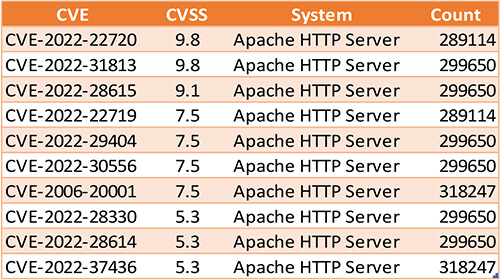
The exploitation of vulnerabilities, particularly zero-day vulnerabilities, serve as a favoured entry point for threat actors seeking to bypass detection mechanisms. Notably, both Chinese and Russian threat actors have gained notoriety for their adeptness in leveraging zero-day exploits as part of their espionage efforts. Moreover, these threat actors actively seek opportunities to launch supply chain attacks, aiming to compromise a wider attack surface. This multifaceted approach underscores the continually evolving tactics employed by these adversaries. Given Japan’s expansive industrial sectors and the significant shift toward industrial automation, it becomes paramount to emphasize the critical importance of effective vulnerability management. This approach is essential to secure various aspects of the technology landscape, including Operational Technology (OT), Industrial Control Systems (ICS), IoT devices, and all interconnected systems, ensuring the continued integrity and security of Japan’s critical infrastructure.
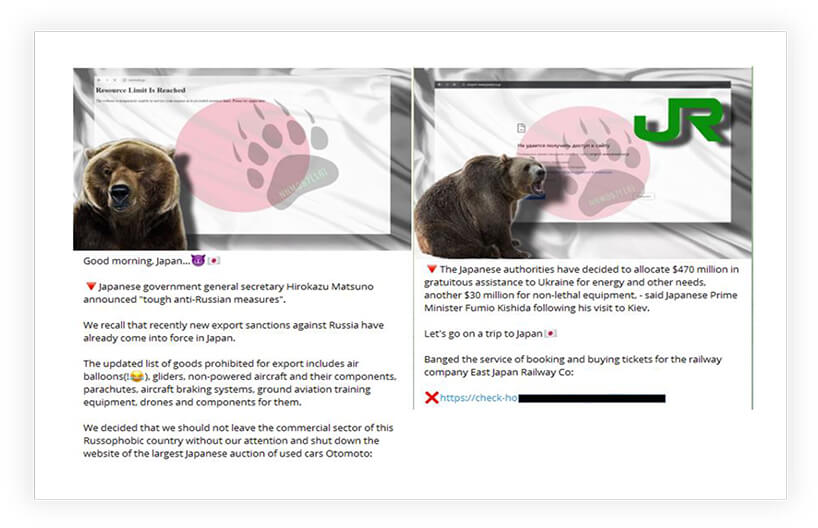
The Quantum of DDoS attacks increased globally after the start of the Russia-Ukraine war when pro-Russian and pro-Ukraine hacktivists started targeting each other with DDoS campaigns and they also started targeting alliance nations to show support to their respective country. Japan is the most targeted country in Asia by pro-Russian hacktivists. Recently we observed a Russian hacktivist group launching DDoS attacks on Japanese Organisations, after Japanese government general secretary Hirokazu Matsuno announced “tough anti-Russian measures”.
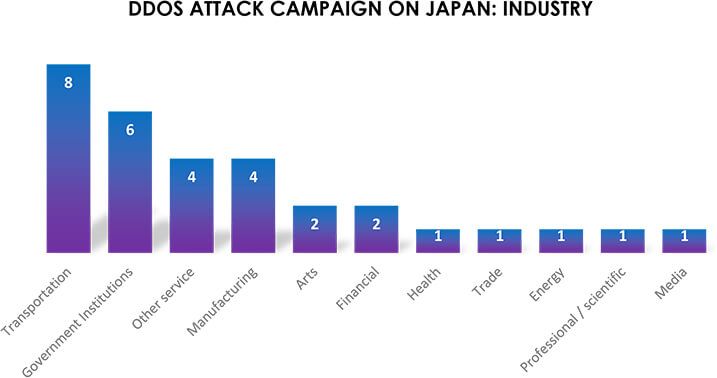
Overall, we observed 31 campaigns targeted against Japan. Government Institutions, Transportation, and Manufacturing are the most targeted industries by pro-Russian hacktivists.
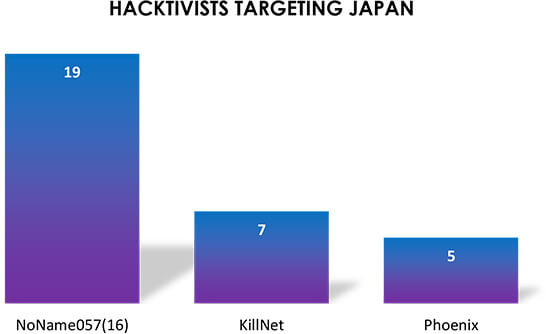
Along with the pro-Russian hacktivists threat, Anonymous Italy recently re-launched cyberattacks against nuclear power-linked groups in Japan as part of an operation called #OpFukushima, which was initiated earlier in April 2021. The campaign was launched to protest against the Government’s plan to release the treated radioactive water from the Fukushima nuclear plant into the sea. In the campaign, hacktivists started targeting the Japan Atomic Energy Agency, Japan Atomic Power Co. the Atomic Energy Society of Japan, and associated companies.
We suspect (with low to moderate confidence) that these DDoS hacktivists who gained knowledge of conducting DDoS operations eventually turn RDDoS campaigners once the purpose of the actual campaign is over or diluted. With learning and enhancements in DDoS tools, RDDoS will have devastating impacts on organizations globally in the coming days.
The cyber threat landscape extends beyond Japan’s geographical borders, with overseas subsidiaries and affiliated companies emerging as appealing targets for threat actors seeking access to global Japanese brands. In recent large-scale attacks on Japanese enterprises, adversaries have strategically chosen to compromise these overseas entities as a gateway into the networks of their Japanese counterparts. Several key factors contribute to this approach:
Varied Security Oversight: Overseas affiliates often exhibit varying levels of security oversight compared to their Japanese counterparts. This discrepancy can make them more vulnerable entry points for attackers.
Security Vulnerabilities via Acquisitions: The acquisition of overseas firms can introduce pre-existing security vulnerabilities into the parent company’s network. Additionally, it may lead to the development of separate security hierarchies that do not align with the security culture of the parent company, creating potential weak links in the overall defense.
Language Barriers: Language barriers can also play a role in this strategy. Attackers may exploit communication challenges to infiltrate Japanese companies through overseas partners, taking advantage of gaps in understanding and coordination.
Japan’s massive and globally integrated economy – encompassing advanced technology, automotive, manufacturing, technology, and financial sectors – presents a substantial attack surface for a diverse range of threat actors. The allure of Japanese product excellence attracts nation-state attackers, particularly from China, as well as financially motivated threat actors seeking to exploit the nation’s wealth. Moreover, Japan’s extensive network of overseas subsidiaries offers softer targets for cyber adversaries, further exacerbated by its proximity to cyber-capable neighbours like Russia, China, and North Korea. These threats encompass IP theft, customer data breaches, payment card fraud, personal information compromise, and cryptocurrency attacks. Japan stands out as a prominent target in the Asia Pacific region for cyberattacks by state-sponsored entities, financially motivated actors, and hacktivist groups. To safeguard its economic prosperity and valuable intellectual property, Japan must prioritize robust cybersecurity measures and proactive collaboration between public and private sectors to effectively counter evolving threats.