



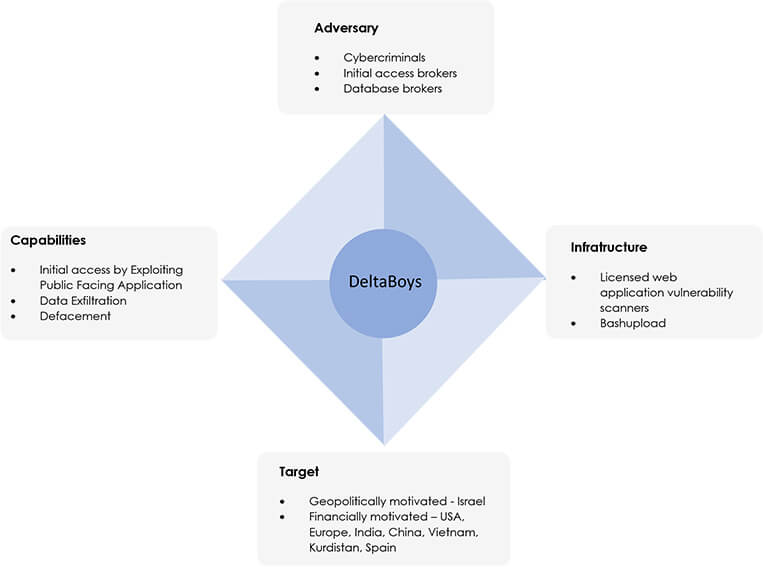
CYFIRMA research team has identified a new threat actor group on the rise with the moniker; DeltaBoys. We have assessed this unknown threat actor to be both financially and geopolitically motivated: they have targeted Israeli infrastructure for ideological purposes but will also indiscriminately attack other infrastructure for financial exploitation. Furthermore, they provide private hacker training sessions, which include access to zero-days, and a web-application vulnerability scanner license for the buyer. The rate at which they are defacing websites is accelerating rapidly, which shows that DeltaBoys are increasing their capacity, sophistication, and capability, and as such we highly recommend that organizations in Israel – particularly those in critical infrastructure sectors – implement enhanced security measures, including regular assessments, patch management, employee awareness training, and multi-factor authentication.
DeltaBoys have been operating since December 2021, initially starting out as database brokers and carders. However, in August 2022, their operation evolved into mass defacement and the ‘initial access’ broking market, providing webshells to sensitive websites. To fund their geopolitically motivated operations, they built a diverse catalogue of recently compromised databases, ‘zero-days’, ‘exploits to known vulnerabilities’, webshells, and leaked credit cards for sale.
DeltaBoys created their telegram channel on 1st December 2021 to monetize their hacking efforts.
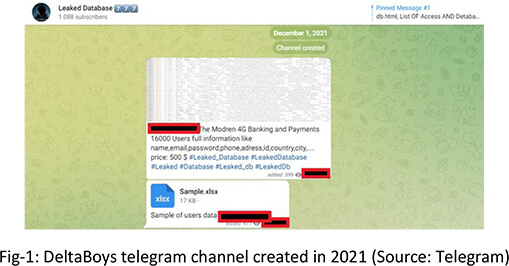

It soon became evident that the market for specific databases was smaller than that looking for initial domain access. The threat actors posted their first set of webshells for sale in August 2022.


Webshell access usually gets sold very quickly on the dark web: this is dependent on who finds the vulnerability/misconfiguration first, as naturally, threat actors do not want to share their victims.
In this case, the 170 webshells were sold within a minute, which highlights the demand of such data.

DeltaBoys launched with just 2 defacements in 2021, whereas in April 2023 alone DeltaBoys have defaced 59 websites, with majority of the victims from Israel, Taiwan, China and Spain.

Please note, the majority of domain hosting providers shown in Fig 4, are from the US.

DeltaBoys group is known to use the ‘bashupload’ utility, which allows a user to upload files for later access, and also facilitates data exfiltration. Further to that, only 3/88 antivirus vendors flagged this domain as malicious.


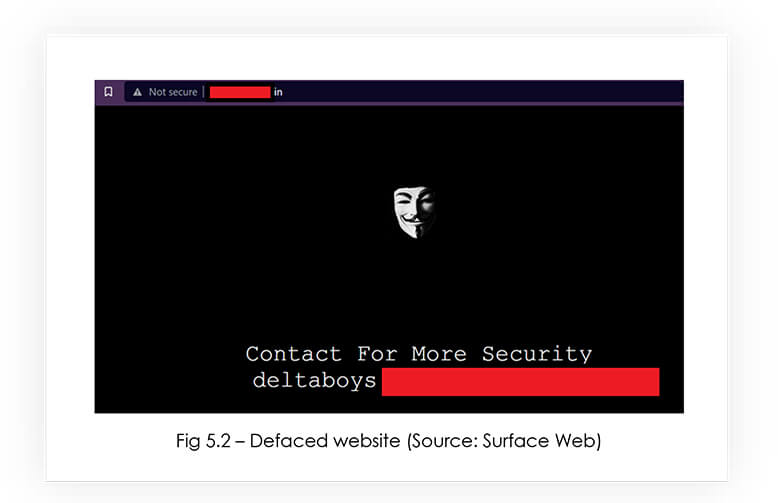
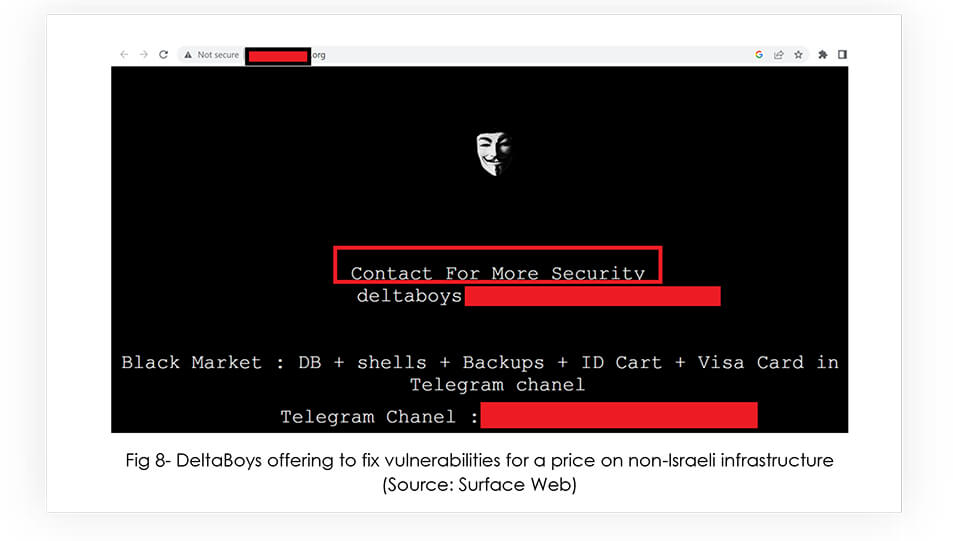
Please note that whenever DeltaBoys deface a non-Israeli infrastructure, they display the message “Contact for more security” – which implies that they want money to fix the vulnerabilities on the defaced infrastructure.
However, when DeltaBoys group defaces any infrastructure belonging to Israeli firms, they make sure to leave a strong message for the readers – which explains their DeltaBoys Black Hats on The Rise motivation behind the attack.

Threat Actor Profile: The members of DeltaBoys are seasoned black hat hackers, who have a wide variety of skills. DeltaBoys funds its activities by selling zero days, webshells and hacking tutorials to the black hat community.
Threat Landscape: Subscription models can be beneficial for threat actors, as it provides a steady source of income, which helps them plan their operations more effectively. DeltaBoys operators are moving to a subscription model, which equips the subscribers everyday with the latest exploits, zero days, tricks and bypasses, webshells, private databases, along with the methodologies and training to assist with the exploitation of latest vulnerabilities.
Victimology: Due to the geopolitical motivations, DeltaBoys has primarily targeted Israel’s infrastructure. However, other victims include the US, India, China, Vietnam, Kurdistan, Spain. The targeted industries by DeltaBoys are Government, Manufacturing and Financial Services. The threat actor group’s favorite targets are web applications running on Linux and FreeBSD environments.
Impact Assessment: DeltaBoys pose a significant threat to organizations, particularly those in critical infrastructure sectors, due to their advanced hacking skills and focus on financial and geopolitical motivations. Having access to a diverse range of exploits and methodologies makes them a formidable adversary, potentially leading to financial losses, due to stolen intellectual property, defacement, or compromised customer data.
In conclusion, DeltaBoys is a highly skilled threat actor group that poses a significant threat to organizations, particularly those in critical infrastructure sectors, due to their financial and geopolitical motivations. They have been observed accelerating their operations over the past year, expanding from database-brokering and carding to mass defacement and initial-access brokering. Their subscription model provides a steady source of income as well as access to a diverse range of exploits and methodologies. Organizations – particularly those in Israel – should implement enhanced security measures (such as regular security assessments, patch management, employee awareness training, and multi-factor authentication) to protect against potential attacks and mitigate risks from this growing, capable, and pernicious group.
| No. | Indicator | Type | Role |
| 1 | bashupload[.]com | URL | Data Exfiltration |
| No. | Tactic | Technique |
| 1 | Initial Access TA0001 | Exploit Public Facing Application T1190 |
To protect against the threat posed by DeltaBoys, organizations, particularly those in critical infrastructure sectors, should implement the following enhanced security measures:
Management Recommendations:
Strategic Recommendations:
Tactical Recommendations: