



In the third quarter of 2023, ransomware incidents surged, impacting organizations across the globe. This report thoroughly examines the major ransomware events, including high-profile breaches like Maximus and Port of Nagoya. We identify the top-targeted industries and nations, as well as also explore the evolving tactics of ransomware groups, new actors, and the vulnerabilities they exploit. This analysis aims to empower organizations to enhance their cybersecurity strategies and mitigate ransomware risks effectively.
Welcome to the Ransomware Report for the third quarter of 2023. As a persistent and evolving threat to organizations, ransomware continues to cause substantial financial losses and reputational damage. The third quarter of 2023 witnessed a notable surge in ransomware activity, emphasizing the critical need for enhanced cybersecurity measures. In this report, we delve into a comprehensive analysis of the ransomware landscape during this period, providing valuable insights into targeted regions, industries, threat actors, and emerging variants. Staying informed about these evolving trends is essential for organizations aiming to safeguard their valuable data and bolster their resilience against ever- changing cyber threats.
• The Manufacturing industry tops the list in reported incidents, emerging as the primary target for cyberattacks, with 209 recorded cases.
• The Cl0p ransomware group has risen as a significant threat, showcasing remarkable adaptability by novel techniques and tactics.
• In the third quarter of 2023, the United States ranked as the most heavily targeted region, with 639 victims.
• Newly emerged ransomware groups are actively exploiting a range of vulnerabilities, both old and new, posing a substantial cybersecurity threat to organizations.
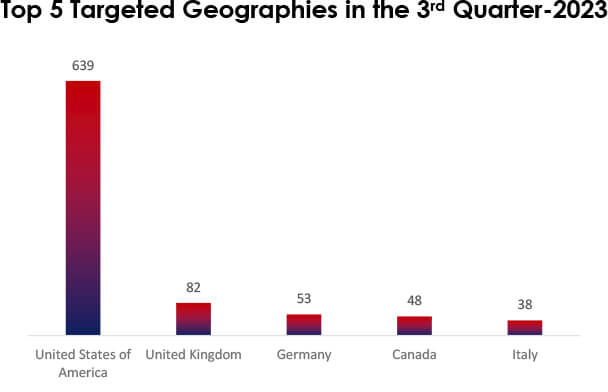
In Q3 2023, ransomware struck worldwide. The U.S. led with 639 victims, followed by the UK with 82, and Germany and Canada at 53 and 48 victims. Italy had 38 incidents. This emphasizes the global ransomware threat, demanding stronger cybersecurity and international collaboration. Ransomware attackers often target countries based on economic factors, including wealth and the presence of valuable data.
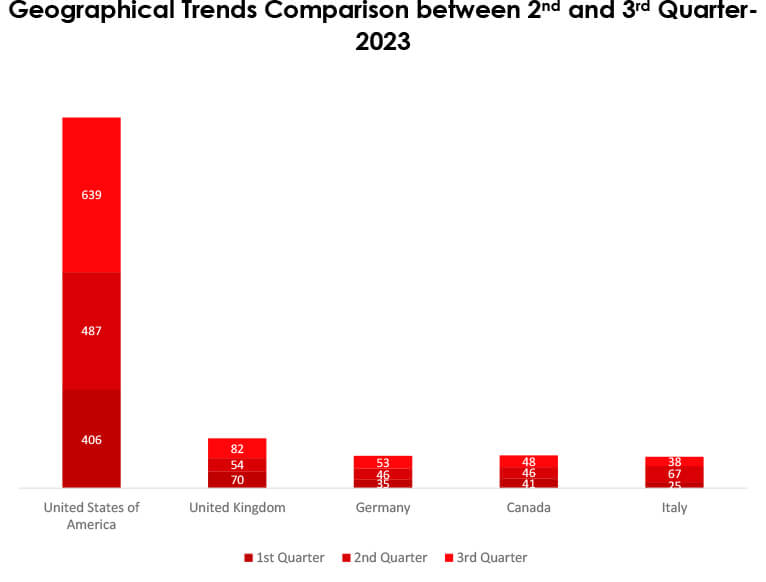
Analyzing the second and third quarters of 2023 reveals a substantial global surge in ransomware attacks. The United States reported 31% increase in victims, the United Kingdom saw a 52% rise, and Germany and Canada experienced 15% and 4% increases, respectively. Conversely, Italy witnessed a significant 43% decrease in victims.
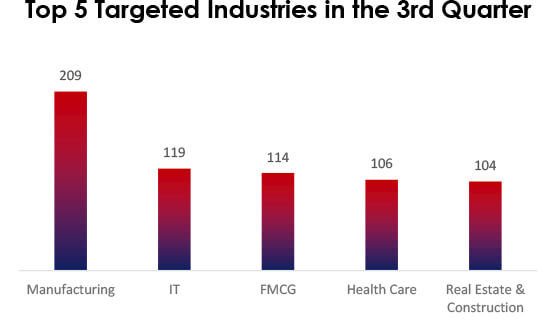
In Q3 2023, the top targeted industries were Manufacturing, IT, FMCG, Health Care, and Real Estate & Construction. They store valuable data, which is a magnet for cyberattacks, namely manufacturing for intellectual property, IT as a gateway, FMCG for customer data, Health Care for patients’ information, and Real Estate & Construction for financial data, all lucrative for cybercriminals.
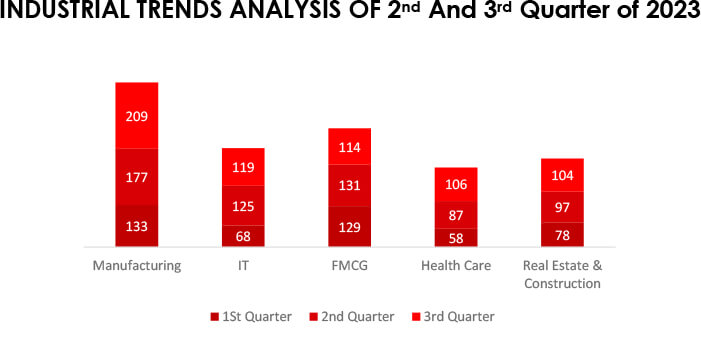
Analyzing industrial trends between the second and third quarters of 2023 reveals notable shifts in ransomware incidents. The Manufacturing sector notably increased by 18%, whereas IT experienced a slight 4% decrease. FMCG saw a 13% decline, while Health Care exhibited a substantial 22% increase. Real Estate & Construction witnessed a modest 7% rise.
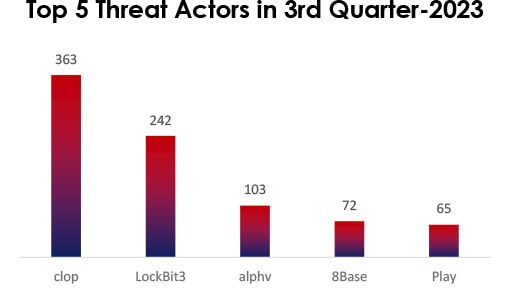
In the third quarter of 2023, threat actor activity was notably marked by several prominent groups. Cl0p stood out with 363 victims, followed by LockBit3 with 242 victims. Additionally, ALPHV, 8Base and Play impacted 103, 72, and 65 victims respectively, demonstrating a concerning trend of cyber threats during this period. This highlights the critical importance of cybersecurity measures and vigilance in safeguarding against these malicious actors.
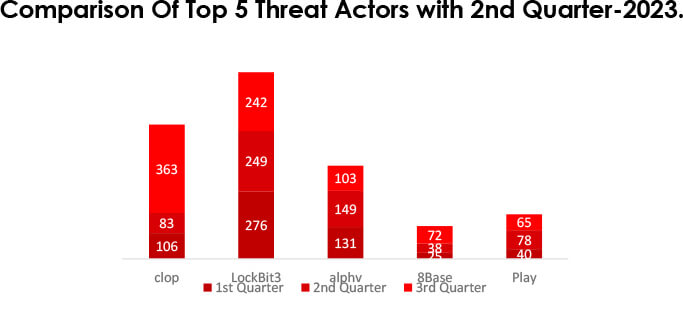
In the trend comparison of victims for the 3rd and 2nd quarters, there is a significant shift in the threat landscape. Cl0p victims increased substantially, with a 339% rise, while LockBit3 saw a decrease of 2%. ALPHV victims dropped by 31%, and 8Base experienced a 90% surge. Play victims declined by 16%. These percentage changes highlight the dynamic nature of cyber threats, requiring constant vigilance and adaptability in cybersecurity strategies.
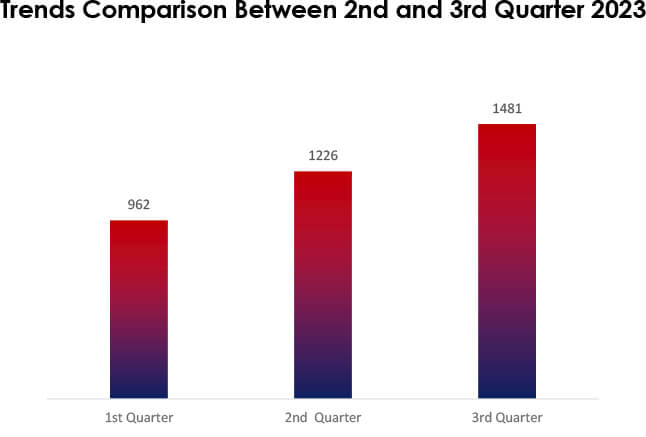
In the 3rd quarter of 2023, there was a noticeable increase in cyberattack victims compared to the previous quarter. The victim count surged from 1,226 in the 2nd quarter to 1,481 in the 3rd quarter, marking a significant 21% rise. This uptick suggests a heightened threat landscape and a more aggressive approach by threat actors. Organizations should remain vigilant, strengthen their cybersecurity posture, and prioritize proactive measures to mitigate evolving risks.
BlackCat’s Evolution shows a highly assertive behavior.
In July, BlackCat introduced a data leak API to rapidly share information about victims, increasing pressure for ransom compliance. In August, their Sphynx ransomware incorporated Impacket and RemCom for advanced lateral movement. By September, Sphynx encrypted Azure Storage, disabling security features and enhancing evasion techniques, making detection more challenging, marking an escalation in their attack tactics.
Cl0p Ransomware Group Adopts Clearweb Sites
In late July, the Cl0p ransomware gang adopted a tactic previously used by the ALPHV ransomware gang to intensify pressure on their victims. They started creating openly accessible clearweb websites, facilitating the leaking of stolen data by allowing indexing by search engines. Several of these sites were identified, focusing on companies such as PWC, Aon, EY (Ernst & Young), Kirkland, and TD Ameritrade. Unlike ALPHV’s advanced searchable database, Cl0p’s sites provide links for downloading the data. This approach enables ransomware groups to double-extort victims and enhances the likelihood of ransom payments.
An Overview of the Evolution of Akira
In July, the Akira ransomware group demonstrated persistence and adaptability, with some victims infected with a Linux variant. Despite a decryptor release in June, their extortion efforts continued. In August, they leveraged Cisco VPN vulnerabilities, possibly via authentication bypass, and exploited RustDesk for network traversal, showcasing increased sophistication and diversification in their techniques.
Monti ransomware hits ESXi servers with an advanced Linux locker.
In August, the Monti ransomware gang unveiled a new Linux locker aimed at VMware ESXi servers. This variant stands out from its predecessors, showcasing discreet ESXi VM termination, improved evasion techniques, and the utilization of AES-256-CTR encryption through OpenSSL, resulting in files marked with “.MONTI” extensions. Additionally, it includes ransom notes.
Yashma Ransomware Adapts Multilingual Approach.
Commencing in early August, a Yashma ransomware variant, potentially linked to Vietnamese threat actors, initiated a multilingual global attack campaign. This variant encrypts files, alters wallpapers, and doubles the ransom demand after three days. Notably, it retrieves its ransom note from GitHub, evading conventional detection methods. The resemblance to WannaCry serves as a stark reminder of the importance of robust response strategies.
A new version of DoDo Ransomware has emerged.
Researchers observed in the early days of August that a new version of DoDo, linked to Chaos Ransomware, emerged under the disguise of “Mercurial Grabber.” This variant targets users who unwittingly download this deceptive tool. Although ransom notes and extensions differ, both share Chaos Builder 3 as their origin and a common Bitcoin address. In this updated version, files are marked with the “.crypterdodo” extension, wallpapers are altered, and a contact email is provided.
FreeWorld- variant of Mimic Ransomware
In late August, a new variant of Mimic Ransomware, known as FreeWorld, emerged. This ransomware encrypts files and appends “.FreeWorldEncryption” to their filenames. Following encryption, it generates a ransom note named “FreeWorld-Contact.txt.”
Cuba came up with a Dangerous Backdoor
During the first week of September, the Cuba ransomware gang, recognized for data theft, displayed an evolution with new BurntCigar malware versions. An investigation unveiled a sophisticated backdoor termed BugHatch, functioning in process memory, establishing connections with a command-and-control server, and capable of downloading tools like Cobalt Strike Beacon and Metasploit. The involvement of Veeamp points to Cuba’s association in this event.
Collaboration Between Vice Society and Rhysida Ransomware
The Rhysida ransomware group has technical ties to Vice Society, both targeting education and healthcare sectors. Rhysida’s rise coincides with Vice Society’s decline. Shared Tactics, Techniques, and Procedures (TTPs) involve RDP, PowerShell, PsExec for lateral movement, log deletion for defense evasion, and data encryption. Focusing on TTPs leading to ransomware deployment is crucial. Monitoring remote management tools and attack techniques is key for prevention.
“Xollam Ransomware: An Evolution of the TargetCompany Strain”
Xollam, a modified version of TargetCompany ransomware, encrypts files with “.xollam” extensions and spreads via phishing emails with malicious OneNote attachments. It utilizes fileless techniques, targets Azure SQL servers, and employs various tools for evading antivirus software. Encryption methods include ChaCha20, Curve25519, and AES-128.
This section gives the details of newly emerged groups, along with some groups that recently published victims in Q3.
Cactus ransomware:
A new ransomware variant called CACTUS targets large commercial entities, encrypting files with .cts1 extensions. It employs various tactics and tools, including Chisel, Rclone, and Scheduled Tasks, to disable security software and gains initial access through VPN appliance exploits. Its activity peaked in July 2023.
Cyclops:
An emerging Ransomware-as-a-Service provider, in addition to traditional ransomware, has introduced a data theft tool. They actively promote their services on forums, seeking a share of profits from malicious use. They offer a user-friendly distribution panel for all major operating systems. They declared a new version, ‘Knight’, and shut down the old panel in July, marking an escalation in ransomware activities.
SophosEncrypt:
SophosEncrypt is a new Ransomware-as-a-Service (RaaS) model written in Rust. It shows traditional ransomware traits but with advanced capabilities, including RAT-like functions such as keystroke logging and system profiling. It exhibits a mix of traditional and sophisticated features, posing a unique and concerning threat. Encrypted files adopt a new format with the original filename, token, email, and the ‘Sophos’ extension after encryption.
Knight ransomware:
Knight ransomware, a rebrand of Cyclops Ransomware-as-a-Service, is spread through a spam campaign posing as TripAdvisor complaints. Emails contain ZIP attachments with executables, leading to fake TripAdvisor pages. Clicking ‘Read Complaint’ downloads Excel XLL files, triggering Knight Lite ransomware to encrypt files with .knight_l extension. Ransom notes demand $5,000 in Bitcoin.
INC ransomware
A new ransomware strain named INC is targeting large commercial entities, encrypting files with a “.INC” extension. The threat actor’s actions involve accessing different servers through compromised credentials and RDP. Data collection, exfiltration, and lateral movement were observed using tools like 7-Zip, native software, and MEGASync. Installation of Advanced IP Scanner, PuTTY, and credential access commands occurred, followed by file encryption execution via PSExec.
3AM ransomware:
3AM is a new ransomware that has been coded using the Rust programming language. Its primary objective is to encrypt files stored on a victim’s computer. In addition to encryption, 3AM alters the filenames of the encrypted files by adding the “.threeamtime” extension. To communicate with the victim and demand a ransom for file decryption, the ransomware creates a ransom note titled “RECOVER-FILES.txt.”
LostTrust:
LostTrust is a newly emerging ransomware that encrypts files and adds the “.losttrustencoded” extension to the names of the encrypted files. The ransomware generates ransom notes named “!LostTrustEncoded.txt” in every folder on the device. In these notes, the threat actors initially presented themselves as former white hat hackers, who had transitioned to cybercrime due to inadequate compensation.
Maximus Data Breach
U.S. government services contractor; Maximus, suffered a data breach affecting 11 million people, carried out by the Cl0p ransomware group. They exploited a zero-day vulnerability in the MOVEit file transfer app (CVE- 2023-34362, CVSS-9.8), compromising 169GB of sensitive data, including social security numbers and protected health records.
Port of Nagoya Ransomware
Japan’s largest port, the Port of Nagoya, experienced a disruptive ransomware attack affecting its container terminals. This critical facility, vital for major companies like Toyota, fell victim to the LockBit ransomware, suspected to be the work of Russian hackers.
Hawai’i Community College Ransom Payment
Hawai’i Community College operating in Education sector admitted to paying a ransom to the NoEscape ransomware gang to prevent the exposure of 28,000 individuals’ stolen data, totaling 65GB.
Estée Lauder’s Security Breach
Beauty giant Estée Lauder operating in FMCG industry, faced security breaches from ransomware actors, including ALPHV/BlackCat and Cl0p. The Cl0p gang exploited a vulnerability in the MOVEit Transfer platform. BlackCat taunted the company about its security measures, hinting at potential impacts on customers, employees, and suppliers.
Yamaha Cyberattack
Yamaha; a Japanese manufacturing giant, confirmed a cyberattack by the Black Byte ransomware gang, with data breaches reported in June and July.
Seiko Targeted by BlackCat
Seiko a company based in Japan and operating in manufacturing industry, fell victim to a cyberattack by the BlackCat/ALPHV ransomware gang. Stolen data included production plans, employee passport scans, new model releases, and confidential technical schematics.
South Africa’s Defense Department Hit by Snatch
The Snatch ransomware gang breached South Africa’s Department of Defense, claiming sensitive data, including military contracts, internal call signs, and personal information, totaling 1.6TB.
‘LockBit Locker’ Ransomware Phishing
The National Police of Spain issued a warning about a sophisticated ‘LockBit Locker’ ransomware campaign targeting architecture companies through deceptive phishing emails. The attackers posed as a photography store and engaged in detailed communication to build trust.
Rhysida Claims Prospect Medical Attack
The Rhysida ransomware gang admitted to infiltrating Prospect Medical Holdings, compromising 500,000 social security numbers, patient records, and demanding a $1.3 million ransom.
Mom’s Meals Data Breach
PurFoods, operating as ‘Mom’s Meals’ in the food industry, disclosed a data breach affecting 1.2 million customers and employees, due to a ransomware attack.
MGM Resorts Cyber Incident
MGM Resorts operating in the Hospitality industry, faced a widespread disruption caused by the ALPHV ransomware affiliate, impacting its internal networks and causing disruptions in its hotels and casinos.
Save the Children Ransomware Attack
The BianLian ransomware group targeted Save the Children International,
compromising 7TB of data, including financial records, human resources information, and personal data.
Auckland University of Technology Targeted by Monti
New Zealand’s Auckland University of Technology (Education sector), fell victim to a ransomware attack claimed by the Monti gang.
BORN Healthcare Data Breach
Canadian healthcare organization; BORN, suffered a Cl0p ransomware attack due to a zero-day vulnerability in Progress MOVEit Transfer software, compromising data of approximately 3.4 million individuals, primarily newborns and pregnancy care patients.
Johnson Controls Ransomware Attack
Major building automation company; Johnson Controls International, faced a significant ransomware attack by the Dark Angels gang, demanding $51 million for a decryptor and claiming to have stolen over 27TB of corporate data, impacting the company and its subsidiaries.
Ransomware is a severe menace, causing extensive harm to organizations and individuals. It results in substantial financial losses, data recovery expenses, business disruptions, downtime, and reduced productivity. Data breaches may occur, leading to regulatory compliance challenges and legal consequences. Reputation damage is significant, with loss of trust, public scrutiny, and market confidence.
Ransomware operators target organizations with high-value data, such as PII, financial records, and intellectual property. Industries like manufacturing, healthcare, finance, and technology are prime targets due to valuable data. They also focus on countries with robust economies, targeting their financial prosperity to demand substantial ransoms.
The report underscores the evolving ransomware landscape, requiring constant vigilance. New ransomware strains, like Cactus, LostTrust, INC, 3AM, and more pose fresh threats, while established groups, such as Cl0p and Akira, continue to adapt.
The Manufacturing industry’s continued vulnerability highlights the importance of securing critical sectors. Moreover, the global reach of the top 5 ransomware families emphasizes the widespread nature of these cyber threats. Organizations must remain vigilant to protect against ransomware’s evolving menace.
Robust cybersecurity measures, including employee training, proactive defense strategies, and rapid incident response, are essential to combat these persistent and potentially devastating attacks.