



Our investigation has unveiled the presence of critical vulnerabilities and exploits for sale on various dark forums and Telegram channels. These vulnerabilities encompass Elevation of Privilege, Authentication Bypass, SQL Injection, and Remote Code Execution, posing significant security risks. The affected platforms include Windows, JetBrains software, Microsoft Streaming Service Proxy, and Ubuntu kernels. One interesting finding is that Ransomware groups are actively searching for zero-day vulnerabilities in underground forums to compromise a large number of victims. To protect themselves, organizations must remain vigilant and prioritize security measures – including patch management and proactive threat monitoring – to safeguard against potential attacks.
Our analysis of various deep web forums revealed a concerning abundance of discussions and transactions related to a wide range of vulnerabilities and exploits. These forums have become breeding grounds for threat actors seeking to buy, sell, or exchange knowledge and tools that could compromise digital security. Our findings underscore the pressing need for robust cybersecurity measures, intelligence sharing, and law enforcement efforts to counter the proliferation of these underground markets and protect organizations and individuals from emerging threats.
In 2023, CISA added approximately 159 vulnerabilities to the Known Exploited Vulnerabilities list. Of that number, 21 are exploited by ransomware groups, highlighting the exploitation to gain initial access, as well as lateral movement.
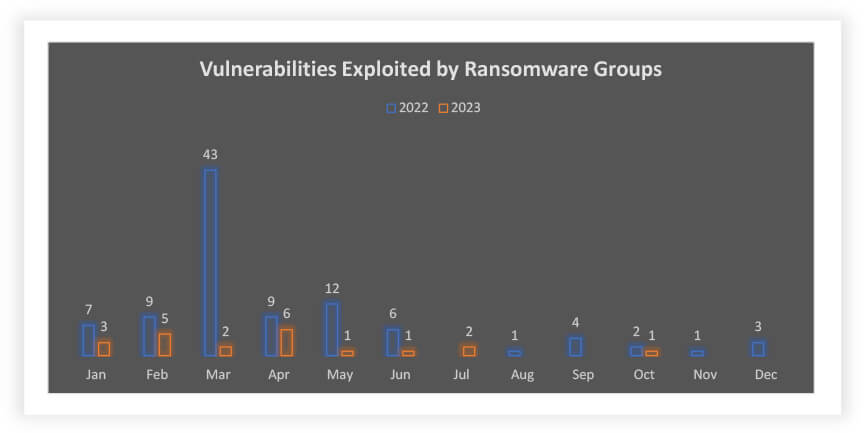
Even though the number of vulnerabilities exploited by ransomware groups in 2022 is less than 2023, they target vulnerabilities that can help them to exploit larger attack surfaces like MOVEit (CVE-2023-34362), PaperCut (CVE-2023-27350), and others.
Our investigation in this report will cover the following critical vulnerabilities and their correlated external threat landscape so that cyber defenders are better prepared to address any possible external threats and risks posed by these vulnerabilities.
| CVE-ID | CVE-Score | Product | NVD Published Date | Threat actor /Campaign |
| CVE-2023-28252 | 7.8 | Microsoft | 04/11/2023 | Nokoyawa Ransomware |
| CVE-2023-27350 | 9.8 | PaperCut | 04/20/2023 | Bl00dy Ransomware Gang/Cl0p ransomware |
| CVE-2023-34362 | 9.8 | MOVEit | 06/02/2023 | Cl0p ransomware group |
| CVE-2023-3519 | 9.8 | Citrix Systems | 07/19/2023 | Unknown |
| CVE-2023-2640 | 7.8 | Ubuntu | 07/25/2023 | Unknown |
| CVE-2023-38831 | 7.8 | WinRAR | 08/23/2023 | Konni APT |
| CVE-2023-36802 | 7.8 | Microsoft | 09/12/2023 | Unknown |
| CVE-2023-42793 | 9.8 | JetBrains | 09/19/2023 | North Korean threat actors |
| CVE-2023-40044 | 8.8 | WS_FTP Server | 09/27/2023 | Cl0p threat actors |
Affected Versions:
CVE-2023-28252 is a vulnerability found in the Windows Common Log File System (CLFS) that enables attackers to attain SYSTEM privileges on the target machines. This is a critical security issue as SYSTEM privileges provide the highest level of access and control on Windows systems.
Underground and Dark Web Forums
We observed a threat actor selling an exploit for a Microsoft Windows vulnerability (CVE-2023-2852) in an underground forum despite the patch being made available by Microsoft.
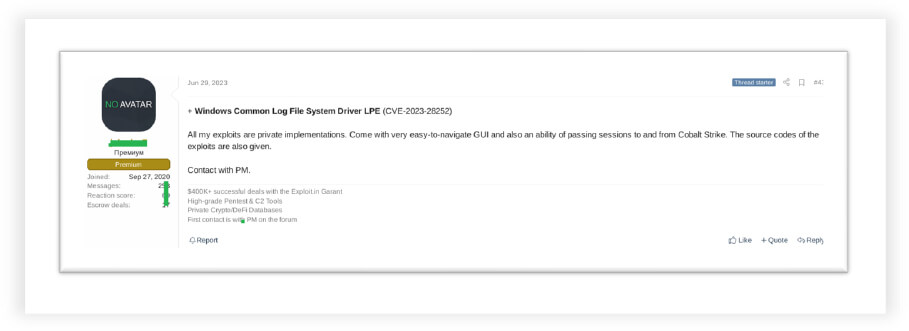
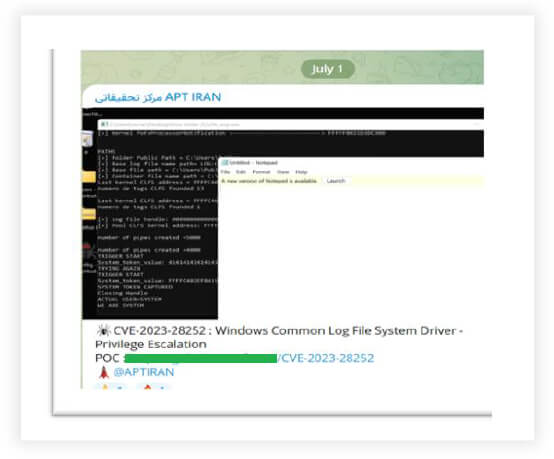
We observed Iranian threat actors discussing CVE-2023-2852 in a Telegram channel, highlighting their interest in active exploitation of the vulnerability.
Threat Actor
It was observed that the Nokoyawa ransomware group has been exploiting vulnerabilities in the CLFS driver since June 2022 (ahead of public availability in April 2023), using it to exploit retail, wholesale, energy, manufacturing, healthcare, software development and other sectors. Furthermore, exploit discussion in the underground forum and telegram channel highlights possible ongoing exploitation of unpatched servers.
Affected Versions:
This vulnerability arises from inadequate sanitization of user-provided data, enabling unauthenticated remote attackers to illicitly access the MOVEit application. If successfully exploited, this vulnerability could empower remote attackers to read, delete, or alter database information and assume full control over the affected application. The exploitation can take place through either HTTP or HTTPS, presenting a substantial security risk. Notably, threat actors including Cl0p and LockBit, have utilized this as a zero-day exploit to compromise numerous victims globally.
Underground and Dark Web Forums
Recently, vulnerability in the MOVEit application created chaos worldwide. At the same time, we have observed a threat actor actively selling MOVEit exploit even after its patch had been released by Progress Software.
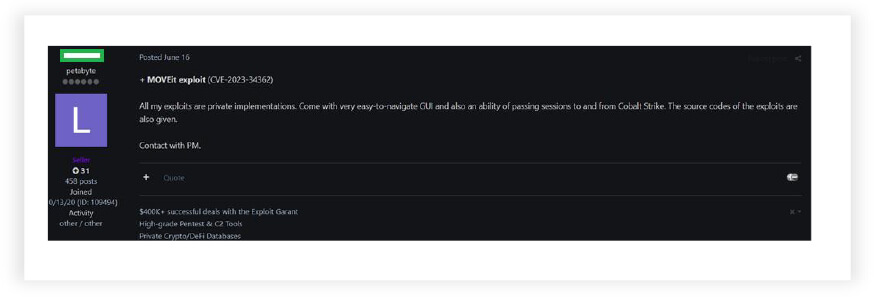
In Telegram channels, we found threads by threat actors discussing how to execute and compromise the victims’ systems.
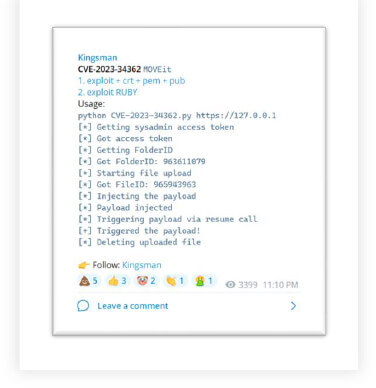
Threat Actor
The Cl0p ransomware group has used a zero-day vulnerability in the MOVEit application (CVE-2023-34362) to compromise numerous organizations around the world. Their ransom notes first appeared in May 2023, before Progress Software released a security advisory in June 2023. So far, Cl0p has targeted over 3,000 organizations in the US and 8,000 worldwide. Cl0p is a well-known RaaS (Ransomware-as-a-Service) operation with ties to Russia. Cl0p has a history of exploiting zero-day vulnerabilities, causing widespread damage in the ransomware landscape.
Affected Versions:
CVE-2023-3519 is a critical security vulnerability that affects Citrix ADC and Gateway products. This vulnerability permits attackers to execute malicious code remotely without requiring any form of authentication. In other words, attackers can compromise the targeted system, gain unauthorized access, and potentially steal sensitive information by exploiting this vulnerability.
Underground and Dark Web Forums
In our research on Citrix ADC and Gateway vulnerability, we observed that threat actors are not only marketing Citrix exploits but are also openly disseminating information on forums on identifying susceptible Citrix ADC systems by offering search engine filters.
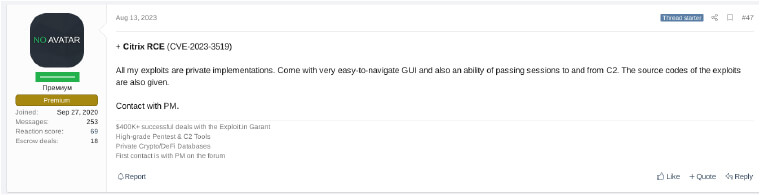
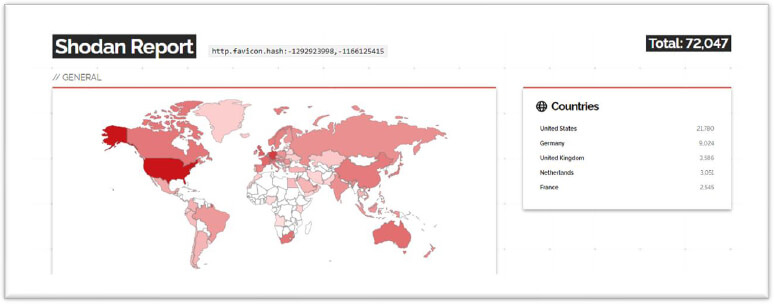
In our OSINT search, we found around, 72,000 devices Citrix systems publicly facing the internet, and this is a significant security concern, despite the patch being made available.
Threat Actors
It was observed that threat actors used this as a zero-day vulnerability for exploitation. The attack was first identified in June 2023, after which Citrix released a security advisory and the patch in July 2023. The largest number of impacted IP addresses associated with Citrix ADC and Gateway vulnerability (CVE-2023-3519) are based in Germany, followed by France, Switzerland, Italy, Sweden, Spain, Japan, China, Austria, and Brazil.
Affected Versions:
Microsoft Streaming Service Proxy vulnerability (CVE-2023-36802) allows attackers to gain SYSTEM privileges – once attackers have gained SYSTEM privileges, they can install, modify, or delete software and files without restrictions, as well as access sensitive system data.
Threat Actor
A well-known initial access broker “r1z” was engaged in the sale of an exploit for Microsoft Streaming Service Proxy (CVE-2023-36802) for a price ranging from USD 10,000 to USD 20,000. Previously threat actor was involved in selling exploits for various other vulnerabilities, such as those related to Atlassian Confluence Data Center, Microsoft SharePoint RCE Exploit CVE-2023-29357, and CVE-2023-40477 Winrar.
Underground and Dark Web Forums
CISA added a Microsoft Streaming Service Proxy vulnerability (CVE-2023-36802) in September 2023. On a dark forum, a well-known initial access broker was observed selling an exploit for the Microsoft Streaming Service Proxy vulnerability from February 2023. It had been actively sold on dark forums for seven months before Microsoft and CISA released an advisory on active exploitation.

Underground and Dark Web Forums
On the underground forum, the exploit for the PaperCut vulnerability continues to be sold, one month after the patch release, and threat actors are still actively using this exploit.
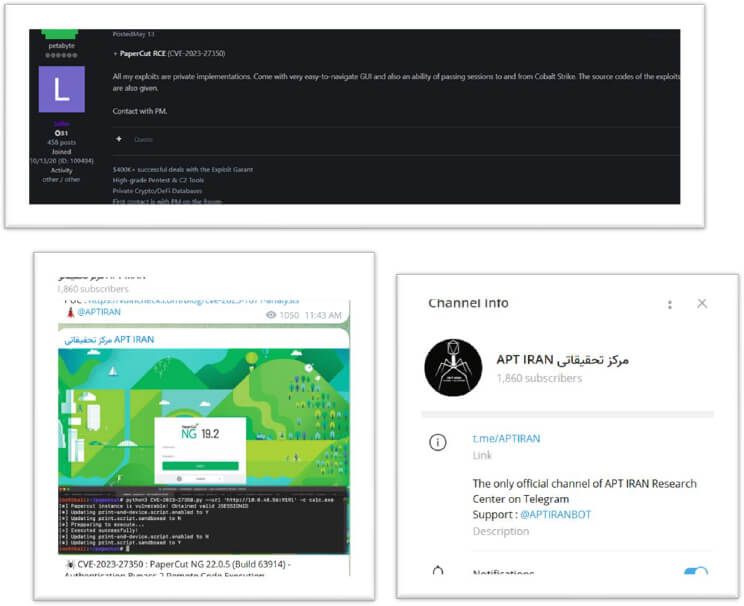
Affected Versions:
PaperCut is a print management software developed in Java, designed to support multi-server and multi-operating system environments. In a typical deployment, there is a primary server that acts as the main application server, and secondary servers that runs as a lightweight monitoring component.
Threat Actors
Multiple ransomware groups, including Cl0p, have been identified using this exploit. In May 2023, the Bl00dy ransomware gang specifically targeted vulnerable PaperCut servers in various sectors, including education, IT, and a range of small and large-scale industries. The company claims to have affected over 100 million users. Notably, we’ve observed that since the patch was released, the vulnerability has not been exploited.
Affected Versions: WinRAR before 6.23
This zero-day vulnerability (CVE-2023-38831) in WinRAR, allows hackers to install malware through manipulated archives, exposing users to hidden malicious scripts. The vulnerability enables attackers to execute arbitrary code when a user attempts to view what appears to be a harmless file, such as an ordinary PNG image file, within a ZIP archive.
Underground and Dark Web Forums
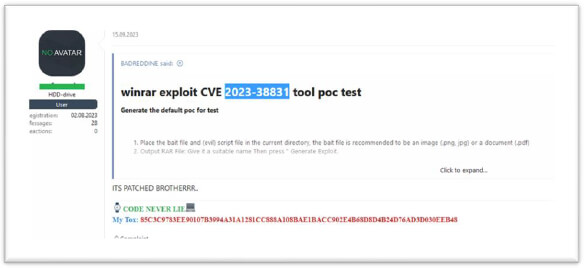
In an underground forum, we discovered that the WinRAR (CVE-2023-38831) vulnerability is actively being sold, even though a patch is available for it.
Threat Actors
The Konni APT; a North Korean state-sponsored cyber espionage group, as well as state-backed threat actors from Russia and China, have been exploiting a WinRAR vulnerability. Since April, threat actors have been using this vulnerability, potentially impacting over 500 million users worldwide. This exploitation has enabled the distribution of various malware families, including DarkMe, GuLoader, and Remcos RAT.
Affected Versions:
The vulnerability CVE-2023-2640 in certain Ubuntu kernels enables unprivileged users to set privileged extended attributes on mounted files without undergoing the necessary security checks. The GameOver(lay) vulnerabilities enable the crafting of an executable file with scoped file capabilities, tricking the Ubuntu Kernel into copying it to a different location with un-scoped capabilities. This grants anyone executing it root privileges.
Underground and Dark Web Forums
CVE-2023-2640; a vulnerability in the Ubuntu Kernel, has been observed for sale on the Dark forum. Threat actors continue to exploit this vulnerability even after a patch has become available.
Threat Actors
Threat actors continue to sell the exploits even after its patch was available. The Ubuntu Kernel vulnerability affects 40% of Ubuntu cloud workloads.
Affected Versions: JetBrains TeamCity Prior to 2023.05.4
The Jet Brains vulnerability (CVE-2023-42793) enables an unauthenticated attacker to gain access to a TeamCity server, allowing them to execute remote code and potentially leading to the compromise of source code and the potential for further supply chain attacks.
Underground and Dark Web Forums
While exploring various dark forums, we observed a trade involving an exploit for JetBrains software (CVE-2023-42793).
Threat Actors
Since early October 2023, Microsoft has observed North Korean nation-state threat actors Diamond Sleet and Onyx Sleet exploiting the Jet Brains TeamCity CVE-2023-42793 remote-code execution vulnerability. These nation-state threat actors use this vulnerability to install malware and backdoors.
Affected Versions: WS_FTP Server Versions Prior to 8.7.4 and 8.8.2
CVE-2023-40044 of the Transfer module is vulnerable to a .NET deserialization vulnerability that allows an unauthenticated attacker to execute remote commands on the WS_FTP Server operating system.
Underground and Dark Web Forums
CYFIRMA researchers discovered WS_FTP Server (CVE-2023-40044) for sale, after the patch was released.
Threat Actor
The Cl0p threat actor uses the WS_FTP Server (CVE-2023-40044) vulnerability to target organizations across various sectors, from IT, to legal, oil and gas, and healthcare.
These vulnerabilities can affect organizations across all aspects of society. Threat actors with knowledge of these vulnerabilities may selectively target industries based on the perceived value of the data, or services handled by these software instances. Organizations dealing with sensitive data or those heavily dependent on these tools may particularly be attractive targets.
To effectively manage the external threat landscape, organizations can benefit from cyber threat intelligence services. These services provide real-time information on emerging threats, vulnerabilities, and attack trends, allowing organizations to stay one step ahead of potential attackers.
This report highlights several critical vulnerabilities (CVEs) and their potential implications, covering a wide range of software and systems. Their criticality underscores the importance of prompt action and mitigation, making timely patching, upgrading, and vigilant security practices essential to prevent exploitation and mitigate risks.