



In times of conflict, there are consequences of being an ally or an enemy of warring nations, either geopolitically, or in the cyber realm. Analyzing the Russia-Ukraine war and the Israel-Gaza conflict, it’s evident that hacktivists now play a significant role, launching attacks using custom-made DDoS tools, defacing websites, and mentoring others in how to disrupt organizations. This behavior arguably goes beyond the attacks themselves, involving a quasi-recruitment process, akin to a sleeper cell, where individuals are trained to act when needed. This dual strategy of cyber and ideological warfare poses huge challenges for governments and private organizations during times of escalating global tension.
The surge in DDoS attacks and other hacking activities extends beyond the Israel-Gaza war. In the past, hacktivists from Russia (such as NoName057(16) and Killnet) and ransomware gangs supporting pro-Russian causes have engaged in damaging actions against countries opposing their stance.
In the ongoing Israel-Palestine conflict, much is happening in the physical world and online. Previous reports have focused on the geopolitical and cyber aspects of the conflict, whereas this report explores the cybercriminal community in greater depth, including advanced persistent threats, hacktivists, and ‘script kiddies’ who are destroying servers, leaking sensitive information, defacing websites, and launching DDOS attacks. We’ve identified many in-house tools created by hackers and shared on platforms like Telegram and GitHub, and tutorials on how to launch cyber-attacks to contribute to the ongoing war.
Hackers Supporting Palestine
Hackers from Pakistan, Palestine, Turkey, Bangladesh, Iran, and Yemen target nations who are not only directly involved, but their supporters, too.
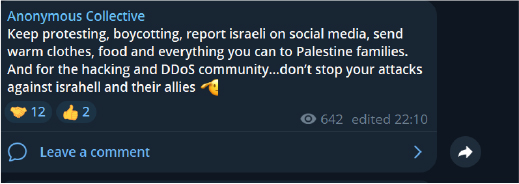
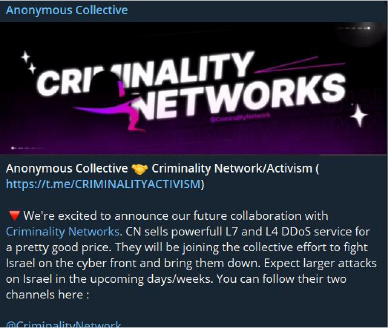
This Anonymous Collective message from Telegram calls for continued attacks against Israel and its supporters.
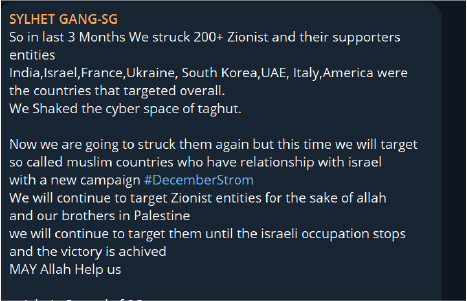
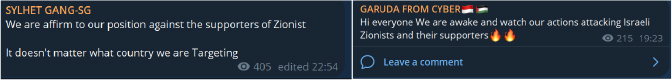
Whilst there are a large number of hacktivist groups supporting Palestine, there appears to be far fewer groups opposing Palestine.
Pro-Palestinian hacktivist groups have hacked billboards and displayed messages against Israel in Croatia and the West Indies.

Against India
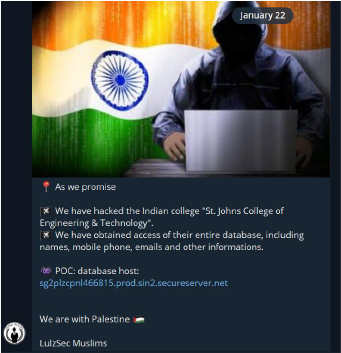
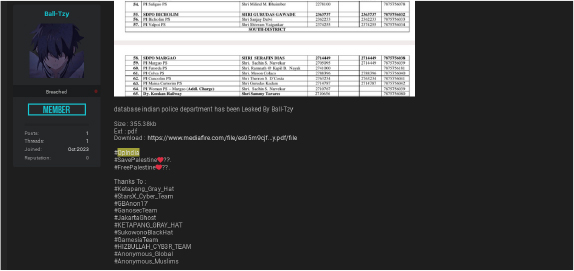
Groups like LulzSec Muslim and SystemadminBD are carrying out significant cyber-attacks against India as part of a wider pro-Palestine campaign. Recently, LulzSec Muslim gained access to the database and server of an Indian engineering college:
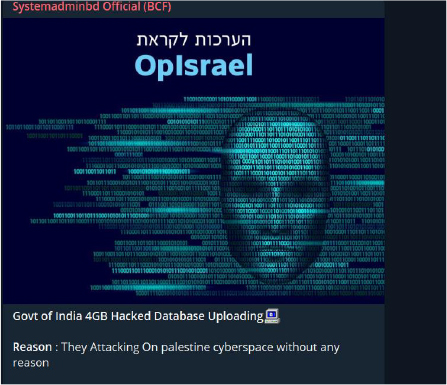
SystemadminBD, a group based in Bangladesh with a history of targeting Indian organizations, has recently attacked the Indian government by claiming to leak a database, stating that their actions were in retaliation to cyber-attacks from Indian hacktivists against the cyberspace of Palestine.
Additionally, we’ve observed instances of misinformation being spread by users in underground forums and Telegram groups, claiming to have breached or leaked data, but ultimately their claims didn’t stand up to scrutiny: for example, the assertion below, which our investigation debunked by revealing that the data in question had already been officially uploaded on the Goa government’s official website some time ago.
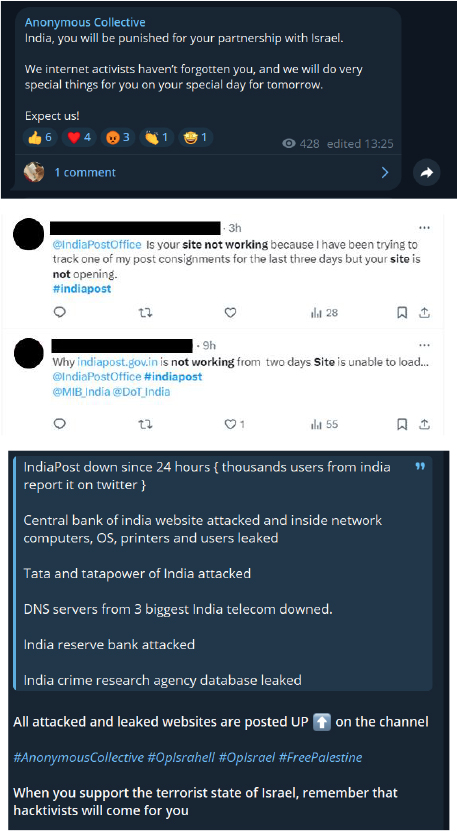
The Anonymous Collective initiated an attack on the Indian Post website, rending it inaccessible for four consecutive days and causing difficulties for many users.
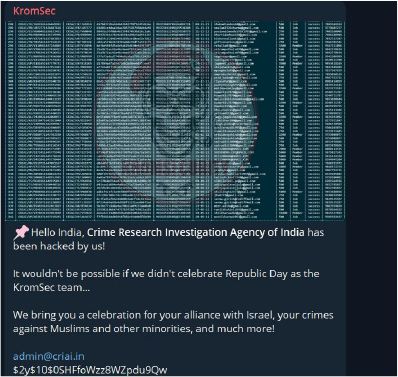
The Kromsec hacker group conducted a DDoS (Distributed Denial of Service) attack, and leaked data from the Central Bank of India and the India Crime Research Agency:
Upon investigating the data leaked by KromSec on ICRA, we ascertained that none of the data was confidential in nature, simply containing data from their web server to host the website. This is another example of how hacktivists tend to overemphasize their impact on the cyber threat landscape globally.
Against Saudi Arabia
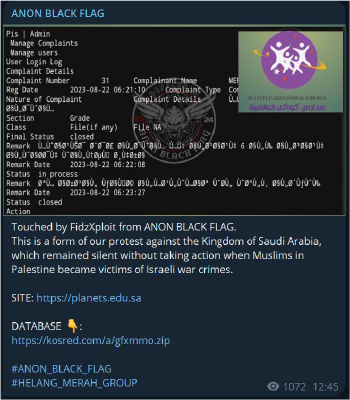
Several hacktivist groups are targeting multiple sectors within Saudi Arabia, for example, ‘Anon Black Flag’ which were found targeting education websites.
Against USA
The USA is a prominent target, with multiple websites defaced in response to the nation’s support of Israel.
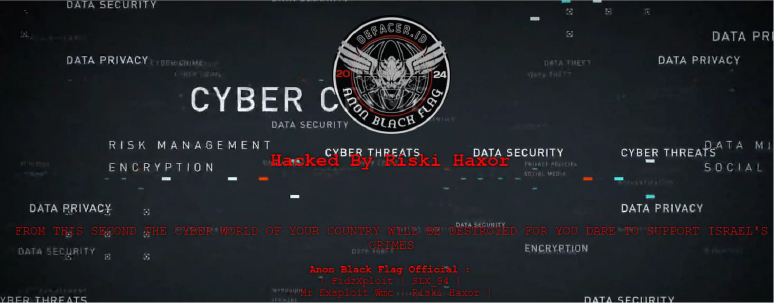
Website defacements are not a new occurrence, as this post from 2017 can attest. In this case, the Turkish-based group; ‘Turkhackteam’, targeted Mossad and websites associated with the USA, as part of a Free Palestine campaign.
Turkhackteam was established in 2002 by Arsenik and is one of the oldest hacking forums in Turkey, first gaining recognition by hacking a Microsoft MSN web portal subdomain and engaging in other high-profile activities.
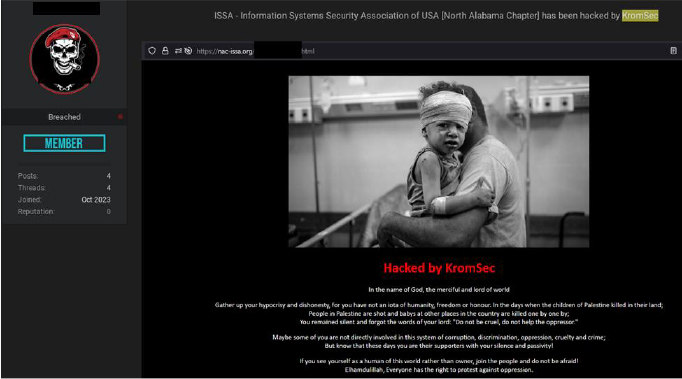
Kromsec successfully hacked and breached the data of AC-ISSA (Information Systems Security Association) North Alabama Chapter, claiming the attack on Beach forum. The compromised information includes email addresses, names, phone numbers, locations, and other related data.
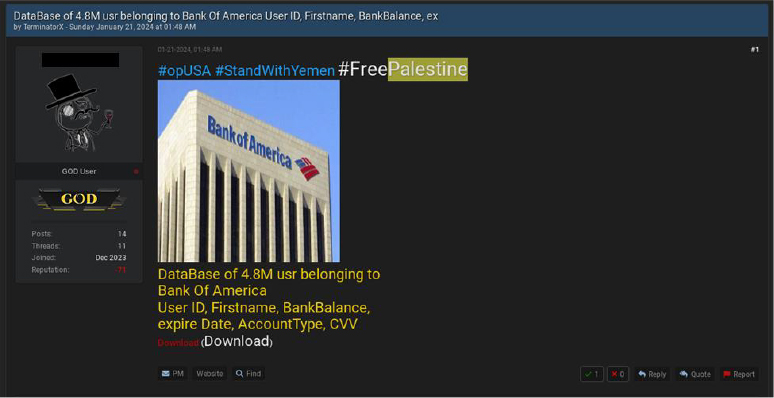
Since mid-October, there have been over 100 cyber-attacks on the United States. US defense officials report that more than 100 drones and missiles have been launched against vessels, targeting Israeli interests. In contrast to these kinetic events, a user on a Breach Forum leaked a database associated with Bank of America, purportedly as a response to the American stance on the Red Sea conflict.
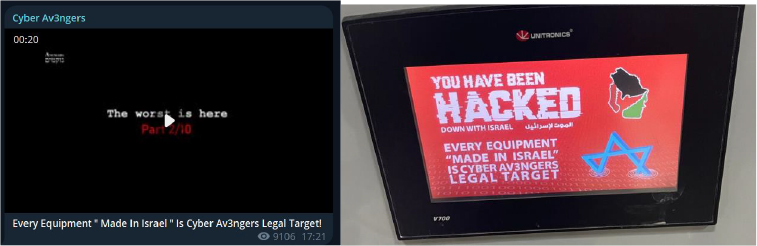
Cyber Av3ngers affiliated to Iran’s Islamic Revolutionary Guard Corps (IRGC) announced their intention to target any equipment made in Israel, and have attacked water systems in the United States, made by Unitronics, headquartered in Israel.
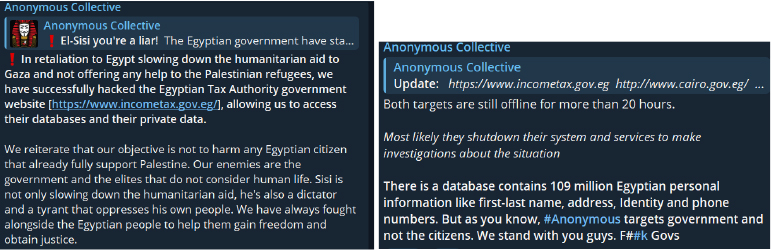
Against Egypt
Hacktivists have turned their attention to the Egyptian government for slowing down humanitarian aid to Palestinian refugees. In retaliation, the Anonymous Collective group executed a DDoS attack against the Cairo official website and the government income tax department, collecting a database of 109 million records containing sensitive data.
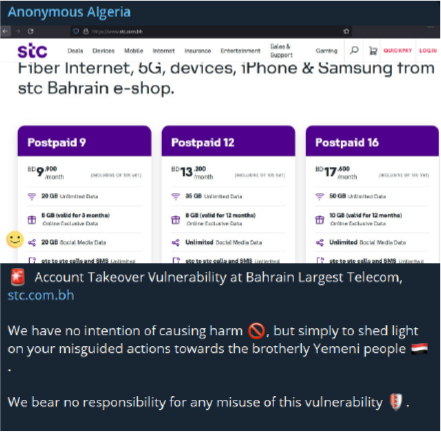
Against Bahrain
The US and the UK, along with other countries, conducted joint strikes on Houthi targets in Yemen. The strikes aimed to weaken the Iran-backed militia that has been targeting international ships in the Red Sea in response to the Israel-Hamas conflict. Bahrain’s silence on the matter has irked hacktivists.
Hackers Supporting Israel
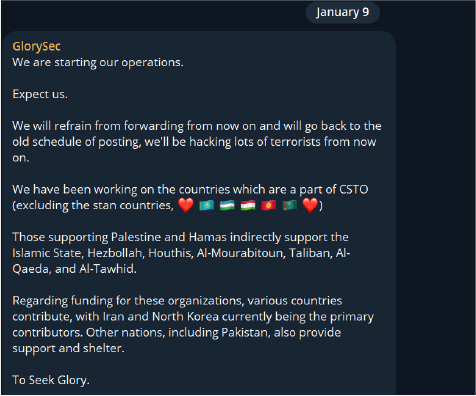
The hacktivist group Glorysec issued a warning, indirectly stating that countries supporting Hamas and other terrorist groups in Palestine will be heavily targeted.
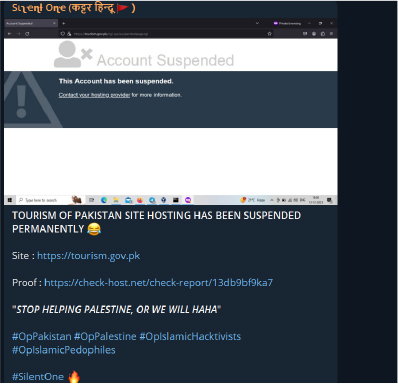
Hackers from India have also joined the fray, engaging in DDoS attacks and defacing websites of countries supporting Palestine in the conflict. Below is an image depicting an Indian group attacking a Pakistani website for backing Palestine.
Training and Tool Sharing
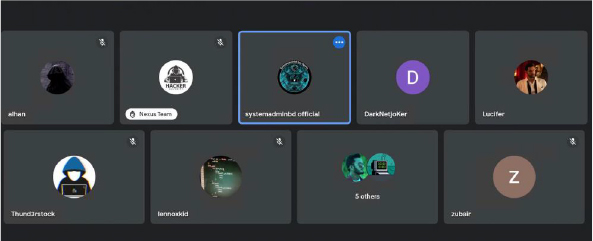
CYFIRMA researchers obtained covert access to a meeting organized by hacktivist group; SystemadminBD, addressing queries from its users, such as how to search for and exploit vulnerabilities.
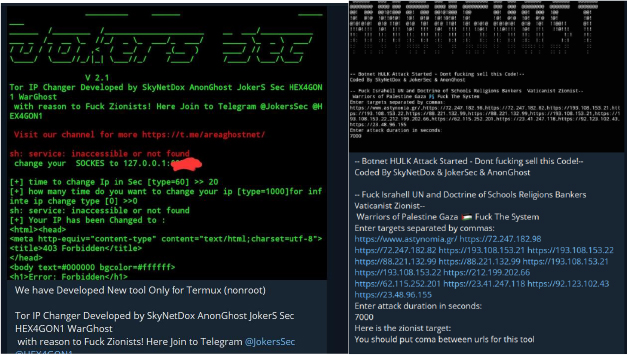
The team has also observed numerous in-house tools and DDoS software (both free and paid) created by hacktivists. These tools are shared on platforms like Telegram and GitHub, and they come in both command-line versions and versions compatible with Termux on Android devices. Since Termux is easily installable on any Android phone, and with step-by-step instructions provided, it enables users to participate in disruptive activities, causing slowdowns or disruptions to organizations.
While using an asset’s exposure tool and by conducting specific queries, it’s evident that hacktivist groups have launched cyber-attacks on numerous countries in support of – or in the guise of supporting – the Palestine conflict. It’s noteworthy that multiple sources are available to track websites defacement, providing a glimpse into the global cyber vandalism of websites around the world.
Body= ”hacked” && body=”savepalestine”
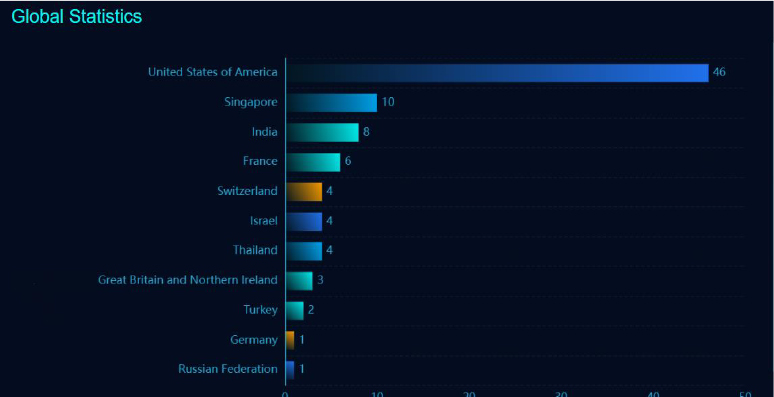
Recent Heat
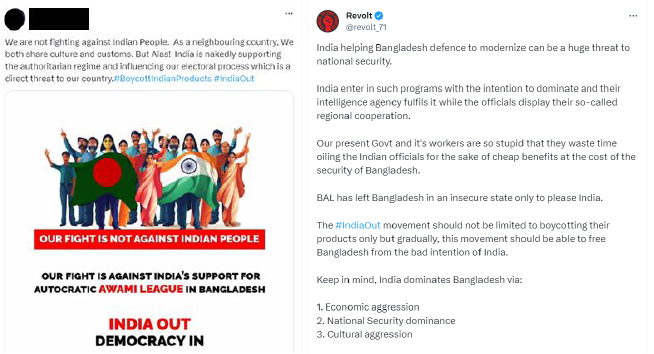
A campaign called “India Out” has come into force and is supported by opposition parties and some civilians within Bangladesh. They claim that the Indian government interfered in Bangladesh’s recent election, where Prime Minister Sheikh Hasina’s Awami League won a fourth term. The opposition party boycotted the polls, and now the hashtag #IndiaOut is trending, with hackers from Bangladesh and similar groups preparing to launch attacks against India as a response.
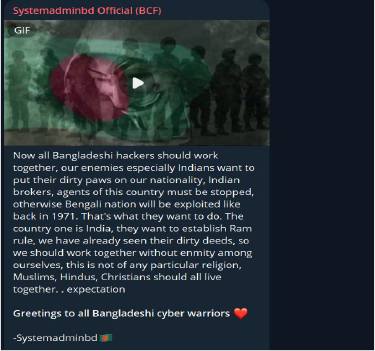
SystemadminBD and other hacktivist groups like Sylhet Gang-SG are actively preparing attacks against Indian targets, indeed SystemadminBD have recently leaked data from private organizations, and provide free access to Indian government portals as part of their campaign.
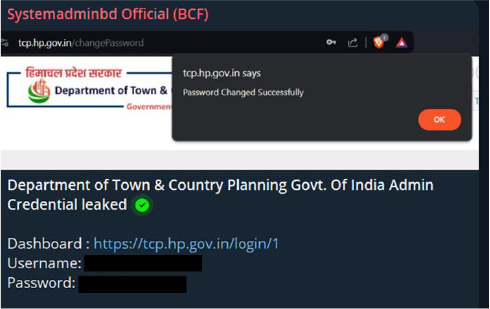
The admin credentials for the Town & Country Planning Department of the Himanchal Government are provided freely on SystemadminBD Telegram channel.
In a recent conversation with an alleged spokesperson of the hacktivist network; Sylhet Gang, we inquired about their views on India:
Sylhet Gang-SG Spokesperson: “the Indians are showing aggression along the Bangladeshi border, so our other admin moderators held a meeting, and we are waging a war against India now.”
As observed in this report, these hacktivists, who support Yemen and Palestine, might be preparing further attacks, having already targeted the USA, Bahrain, and the UK.
Below is a list of hacktivist groups known to be targeting Israel’s allies (please note that this is not an exhaustive list):
APT Groups
Attacking Palestine’s Allies
Whenever there are regional conflicts, we have seen hacker groups getting involved by attacking the websites of countries that oppose their agenda. For example, Indian hackers targeted countries like Bangladesh, Pakistan, and Turkey to support Israel, while hackers from Bangladesh, Pakistan, Turkey target the USA, UK, France, India, Bahrain, and other Israeli allies, providing training and tools to carry out attacks and reputational damage. Conflicts such as these highlight the importance of nations maintaining strong cybersecurity measures, especially if they have different geopolitical stances to those in their region.
Hacktivist attacks can lack sophistication, however, and don’t impact businesses unless a critical service in a major supply chain gets targeted for several days in a row, and defacement attacks are performed on websites of small businesses which lack basic cybersecurity hygiene. These attacks can be effective if carried out against entities like reservation websites or tracking consignment sites, for instance, we have observed a similar case regarding Indian post’s website, which was down for 3 days, resulting in widespread customer dissatisfaction.