



As part of CYFIRMA Research team’s continuous external threat landscape monitoring efforts, the team has identified the emergence of a threat actor group called “ARES”. This group is currently involved in the sale of corporate and government authority databases. Our analysis indicates that ARES has displayed characteristics, consistent with cartel-like behaviour, by actively seeking out affiliations with other threat actors and asserting connections with established hacking groups and ransomware operators. Our observations suggest that other cybercriminal groups have acknowledged this association. In recent developments, we have observed a significant increase in ARES Leaks activities, following the shutdown of the BreachedForum. This raise concerns that ARES may be intensifying its efforts to add more threat actors and leaks to its platform, to become one of the alternatives to the BreachedForum.
This report is a complete analysis of the Group’s operation, evolution, and capabilities.

Ares was the Greek god of war, known for his aggressive and impulsive nature and associated with the violent aspects of the battle. Ares was often depicted as a fierce and aggressive warrior, dressed in armour, and carrying a spear. There is no direct association between Ares, the god of war in Greek mythology, and cybercriminals. However, the name “Ares” has been used in the past, as a reference to a notorious Trojan malware called “Ares Rootkit,” which was used by cybercriminals to gain unauthorized access to computers and steal sensitive information.
Impact Assessment
From external threat landscape management viewpoint, data leak sites are a significant threat to data security. They serve as a platform for cybercriminals to monetize stolen data and enable an underground economy, worth billions of dollars. These sites can also facilitate targeted cyberattacks, resulting in significant financial and reputational damage. Moreover, data leak sites can compromise national security by publishing sensitive government data.
Victimology
ARES Leaks claim to target more than 65 countries, around the globe. Top 10 countries are the USA, India, Philippines, Mexico, Australia, Ukraine, Thailand, France, Spain, and Italy. Leaked data spans across all industries, but during the initial days most of the leaks were associated with government institutions, critical infrastructure, and defense/military and intelligence entities.

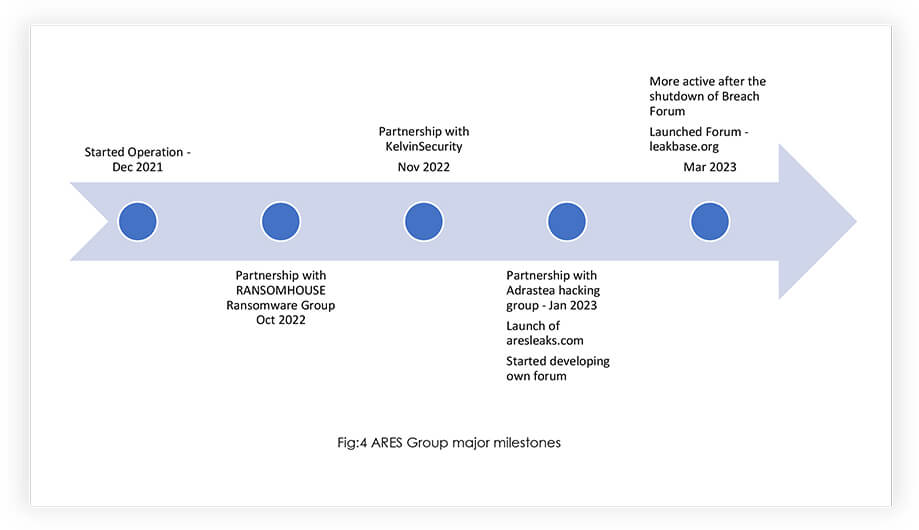
ARES Group started its operation in December 2021 through Telegram, like any other group of like-minded hackers. It started with selling fresh databases, and confidential information and engaged in re-publishing earlier leaked databases for free. During the initial phase, the group was trying to establish itself by adding more leaked databases to increase its subscribers, before enhancing its offerings. Looking at their footsteps, the group planned to evolve as a notorious cyber criminals’ cartel, by partnering with other specialized groups. The group operated predominantly using multiple telegram channels to accommodate multiple requirement streams.
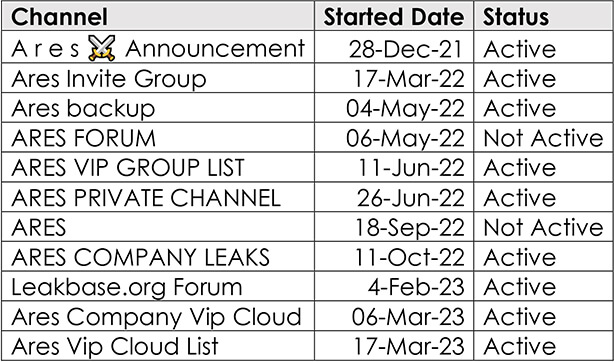
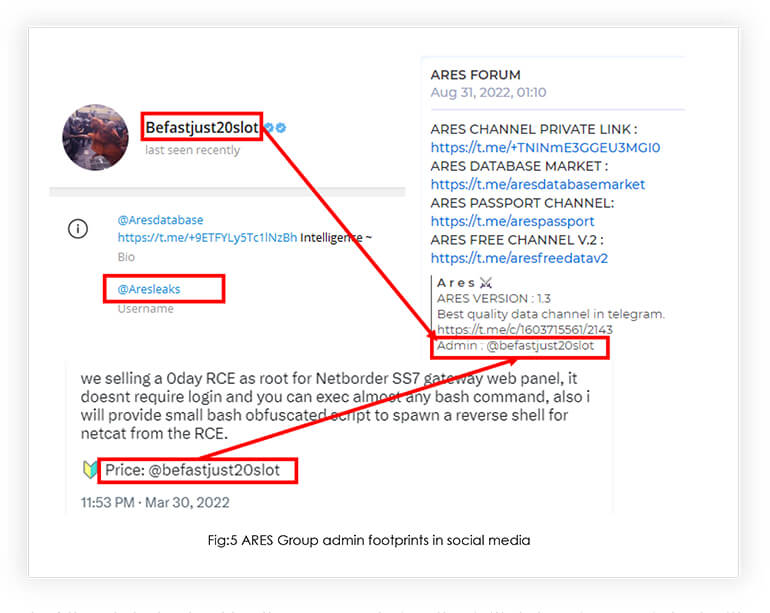
Only major announcements are advertised through the ‘A r e s Announcement’ channel, and databases are offered through other dedicated channels like ARES PRIVATE CHANNEL, VIP Channel, and company leaks. After getting started in Dec 2021, the group got more active in May 2022. For the discussion on the pricing of databases @Aresleaks and @befastjust20slot telegram channels are used. Our OSINT search found that the admin of ARES Group was also engaged in selling Zero-day vulnerabilities through a well-known social media platform, indicating the group is using vulnerabilities, especially zero-days to compromise systems.
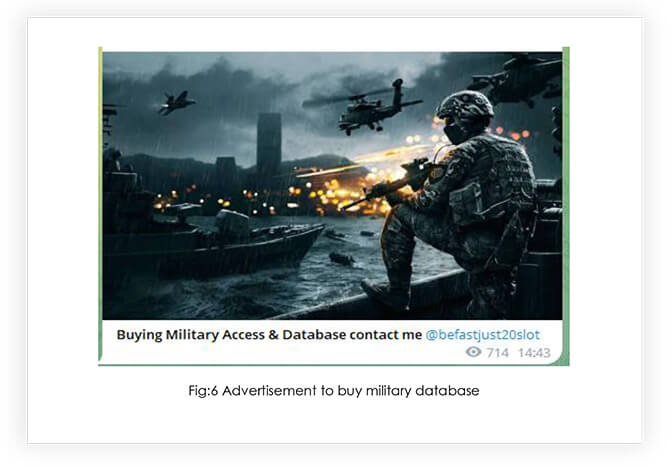
Most of the data leaked by the group, during the initial days is associated with government institutions, critical infrastructure, and defense/military and intelligence entities. We also noticed that the group is advertising to buy military entity access and databases, indicating the group’s interest in dealing with defence data leaks and demand for such data in the market.
Following the preliminary activities, it has been discovered that the ARES group has become increasingly active in the cybersecurity landscape, having established affiliations with both ransomware and other hacker groups. Specifically, in October 2022, the ARES group announced its collaboration with the RANSOMHOUSE Ransomware group, and in November 2022, they were found to be associated with KelvinSecurity. Furthermore, recently, the Adrastea hacker group has been added to the ARES group’s list of partners. These developments suggest that the ARES group is expanding its reach and influence within the data leak cyber threat landscape.
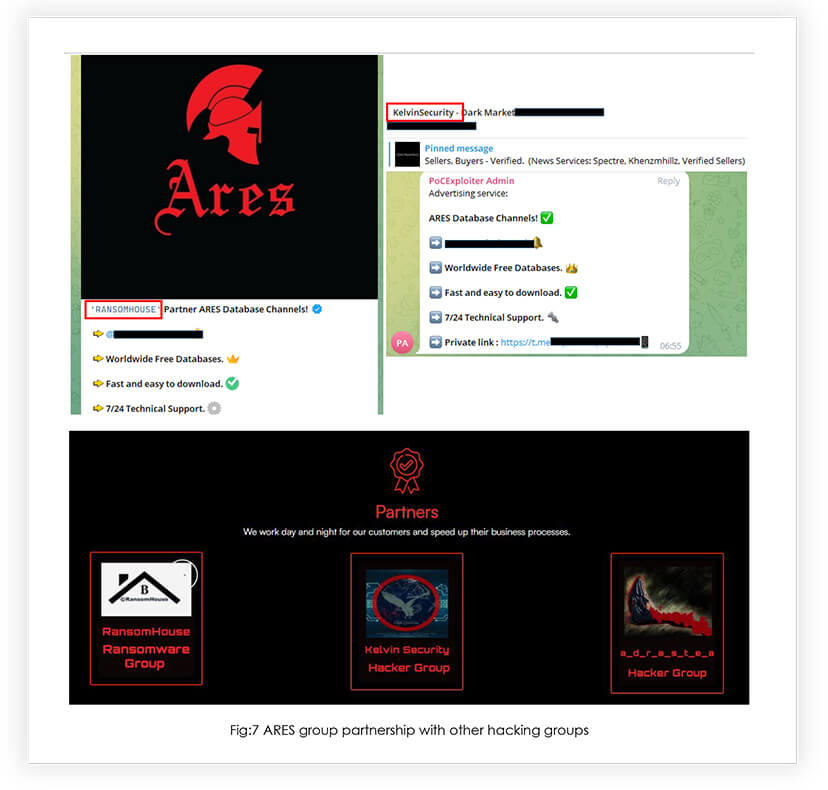
RansomHouse Ransomware Group: According to our knowledgebase, RansomHouse, a relatively new player in the cybercriminal landscape, is believed to have surfaced in December 2021. What sets this group apart from others is their approach to extorting money from their victims. Instead of relying solely on traditional online extortion tactics, they present themselves as penetration testers and bug bounty hunters. Once they have gained access to their target’s data, they offer to delete it and provide a comprehensive report, detailing the vulnerabilities they exploited and the methods they used to do so. These findings suggest that RansomHouse is employing sophisticated techniques to achieve its goals.
Kelvin Security Hacker Group: The KelvinSecurity Team is likely a Russian-based hacking organization with a significant presence on Deep and Dark Web forums, that are commonly frequented by hackers and cybercriminals.
Adrastea Hacker Group: Adrastea is a group of independent specialists and researchers in the field of cybersecurity. They try to find critical vulnerabilities in the victims’ networks and gain access to organizations’ files and confidential data. Adrastea is well known for hacking European missile maker MBDA.

As outlined in our “CYFIRMA 2023 Predictions,” the effectiveness of cyberattacks is expected to increase as threat actors forge partnerships with other like- minded cyber-criminal groups. The ARES group’s recent activities, including their leaked information and their affiliation with other hacker groups, serve as a prime example of this trend. By pooling their resources and expertise, these groups can leverage each other’s strengths and weaknesses to maximize their impact and potentially gain an advantage in the ongoing arms race between attackers and defenders.
Moreover, it is noteworthy that well-known threat actors are already utilizing the ARES platform to sell compromised data, indicating that the group is gaining popularity in the cybercriminal community.
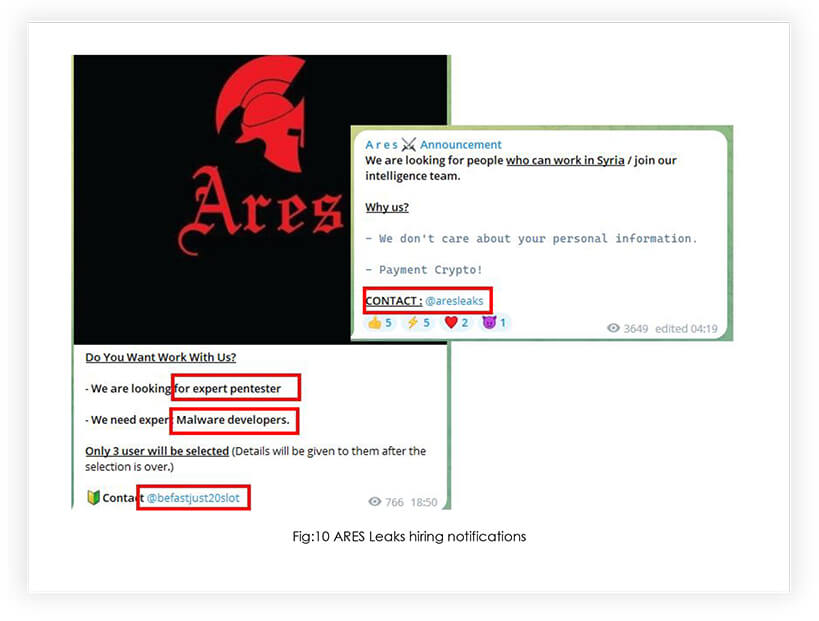
Additionally, we have observed that the ARES group is expanding its operations by hiring penetration testers, malware developers, and other expert resources. This growth is indicative of the increasing demand for the group’s services and suggests that the ARES group is positioning itself as a significant player in the cybercriminal landscape.
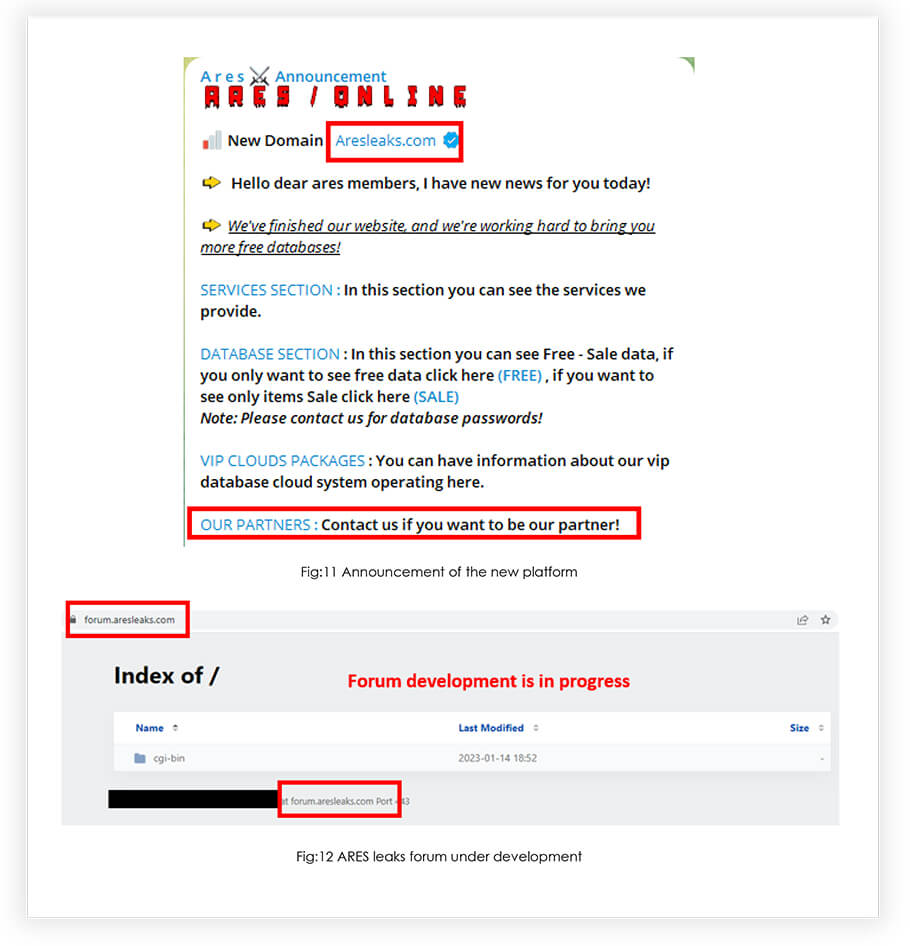
Over time, the ARES group has been growing its operations by incorporating new partners and expanding its workforce. In January 2023, the group took steps to further extend its reach and capabilities by launching its website. We have observed that the group has also been dedicated to constructing a forum, which was completed and launched on March 31st, 2023. This forum has the potential to serve as an effective platform for enhancing the group’s operational efficiency. After the shutdown of BreachedForum, we have noticed a surge in traffic directed toward ARES group’s new platform. This suggests that the group is becoming one of the potential alternatives, in the near future.
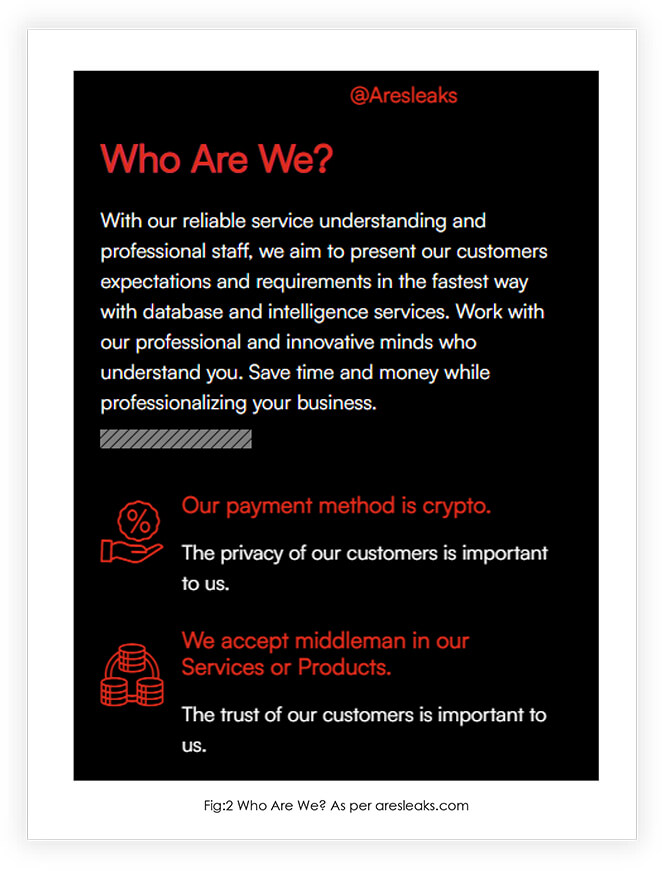
Group offers six services, all of them associated with data leak.
B2B Leads Services
This service claims to provide the latest B2B data to maximize profits for businesses. However, the provided data may attract hackers and competitors, who can exploit victims and competitors. The B2B Leads content includes Company Name, Address, City, State, Country, Phone, Fax, Website, Email Contact, Products Services, Business Type, Employees, and Income.
Strategic Intelligence Service
In this service, the group provides customers with strategic intelligence products, in line with their demands. The Group claims to offer up-to-date information, collected from their staff, around the world and in the field.
B2C Leads Services
The group claims to provide the most up to date B2C data, allowing users to maximize profits for their business or business model. Consumer Leads content consists of Name, Surname, Phone Numbers, Email Addresses, and Address Information.
Elasticsearch System Services
This service is a system that allows customers to manhunt around the world. The Group claims that their system, which is active worldwide, is a system that will provide customers with information such as the name, surname, phone number, and e-mail address of their targets.
Company Leak Services
ARES Group collects and offers specific data from ransomware groups and database markets. They purchase and offer company data sold on various forums and invite hackers to use their platform to sell compromised private databases. Advertised data leaks are from worldwide and include every industry.
VIP Cloud Services
This cloud contains company data from around the world, the oldest data is from 2021 and companies from every industry are offered.
These services tell that once an organization gets compromised, its data gets reused to compromise it again and aid in supply chain attacks. The importance of leaked data never goes down, it’s only a matter of time before “how”, “why” and “who” will use it to exploit the entities and personas associated with that data.
Our analysis of ARES Leaks’ activities indicates that the group is well-organized and recognizes the value of collaboration among like-minded cybercriminals, to sustain their operations. The group appears to have clear objectives to establish itself as a reliable data leak site and create a cybercriminal ecosystem for buyers and sellers of data and related services.
The ARES group’s progress from their initial telegram channel to building their own forum suggests that they are taking significant steps towards achieving their goals. Furthermore, the recent shutdown of Breached forum has created an opportunity for ARES Leaks to establish itself as a potential alternative platform for cybercriminals.
Overall, ARES Leaks’ activities present a serious threat to organizations’ cybersecurity. It is essential for organizations to implement comprehensive security measures to protect against potential attacks from this group and to remain vigilant against emerging cybercriminal ecosystems.
To manage this threat effectively, organizations must adopt a range of tools and strategies to detect and mitigate the impact of data breaches, including threat intelligence platforms, data loss prevention solutions, and incident response procedures. Vigilance and proactive measures are crucial to prevent sensitive information from falling into the wrong hands.