



The team at CYFIRMA recently obtained advanced Android malware targeting individuals in the South Asia region. The suspicious Android malware is a dummy chatting app. Our initial technical analyses revealed that APT Bahamut is behind the attack. As technical analyses proceeded further, we also found footprints of tactics used by DoNot APT in the suspicious app belonging to APT Bahamut.
The malware that was acquired was specifically utilized to target individuals residing in South Asia. This particular malware exhibits a similar operational mechanism to the previously identified malware (distributed through the Google Play Store by the notorious APT group known as ‘DoNot’), however, this malware has more permissions, and thus presents a higher level of threat. The suspected Android malware, known initially as “CoverIm” was delivered to victims via WhatsApp, and was found to be disguised as a dummy chatting application named “SafeChat”. The user interface of this app successfully deceives users into believing its authenticity, allowing the threat actor to extract all the necessary information, before the victim realizes that the app is a dummy, the malware cleverly exploits unsuspecting Android Libraries to extract and transmit data to a command-and-control server. Our in-depth technical analysis will provide a comprehensive overview of this Android malware and shed light on the sophisticated methods employed by the threat actor to exploit Android Libraries for the purpose of data retrieval from victims’ mobile devices. Let’s dive into the technical analyses.
After installation, a suspected app with the name “Safe Chat” appears on the main menu.
After opening the app, the user is shown a landing page where the user is notified of operating a secure chatting app.

Upon opening the app, after fresh installation, the pop-up message instructs the user to allow permission.
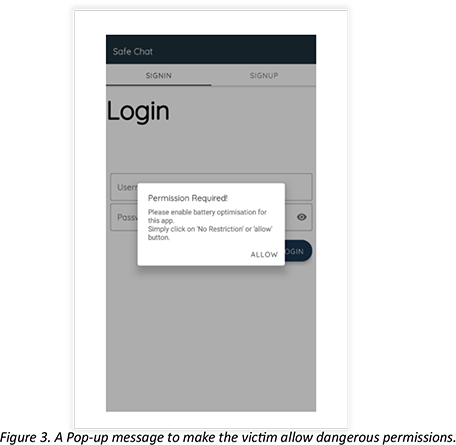
The below screenshot shows the app throwing another pop-up message and asking the user for permission to keep the app working in the background. Once allowed, the app will work even when the app is minimized or closed. This permission will let command and control seamlessly communicate with the app.
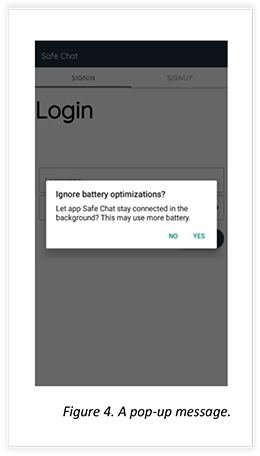
Once permission for ignoring battery optimization is allowed the user is allowed to sign in and sign-up.
The sign-up page:
After completion, the app signs you in, and then the user is shown another pop-up message for permission. This time it throws a pop-up showing the need for another permission app to work properly.
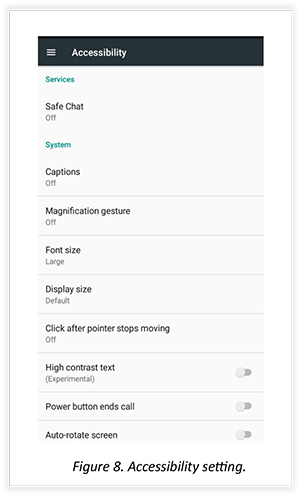
Once the user clicks on “Allow” as shown in the previous screenshot, the app takes the user to the accessibility page and asks the victim to enable accessibility for the Safe Chat app. Once the accessibility is on, then the malware will capture activity on screen including keystrokes. Until it is enabled, the app will throw a pop-up message again and again, as shown in the previous screenshot.
After enabling accessibility for the Safe Chat app, it works properly, showing a different dummy page like any other chatting app.
This excerpt is from the Android Manifest file that belongs to the suspicious Safe Chat Android app, showing permissions that are being employed by the app to perform malicious activity.
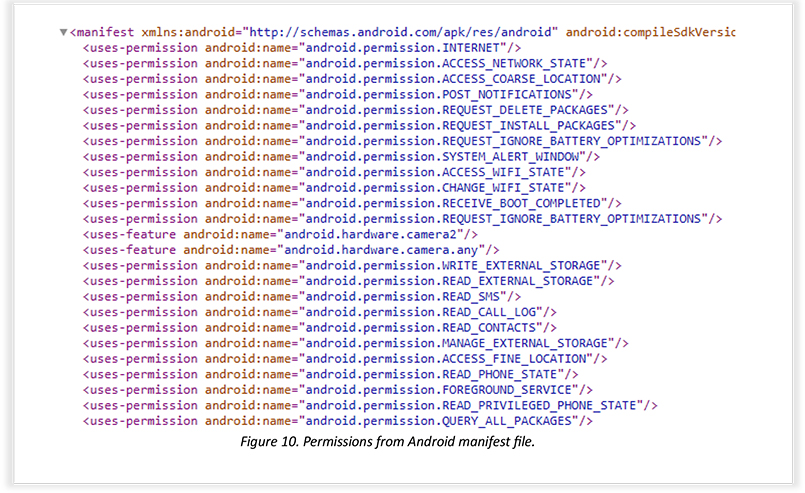
This table contains permissions that are dangerous if exploited for malicious activity:
| Sr.no | Permissions | Descriptions |
| 1 | ACESS_FINE_LOCATION | Allows the threat actor to fetch precise locations and track the live movement of mobile phones. |
| 2 | READ_CONTACTS | This permission allows TA to read and fetch contacts. |
| 3 | READ_EXTERNAL_STORAGE | This permission allows the threat actor to access the file storage of the mobile. |
| 4 | READ_SMS | This allows the threat actor to read all the SMSs of the device. |
| 5 | READ_CALL_LOG | This permission allows the threat actor to read call logs. |
| 6 | READ_CONTACTS | This permission allows the threat actor to read all the saved contacts in the device. |
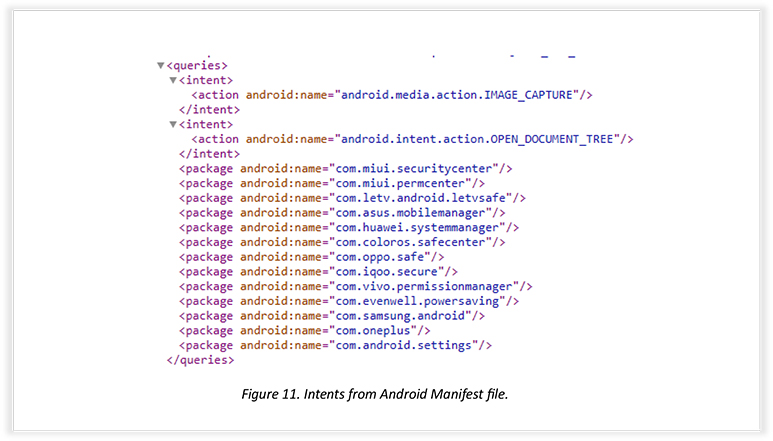
Another snippet from the Android Manifest file shows that the threat actor designed the app to interact with other already installed chat applications. The interaction will take place using intents, OPEN_DOCUMENT_TREE permission will select specific directories and access apps mentioned in intent.
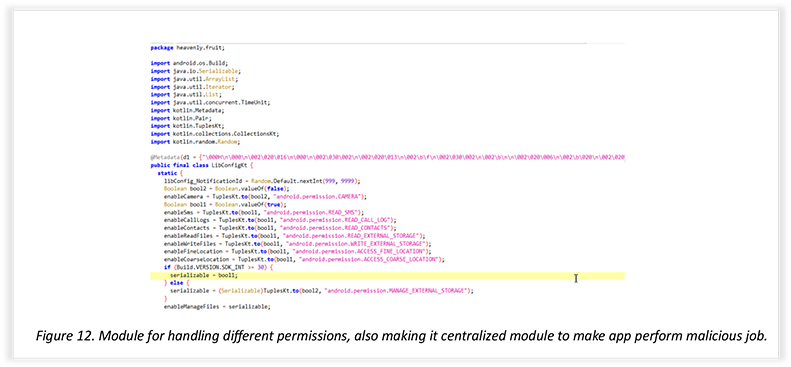
Part of the Kotlin code shows the exploitation of various permissions: the object “LibConfigKt” deals with the enabling and disabling of permissions, and the same object is called in different modules to exploit the permissions accessed by the suspicious App.
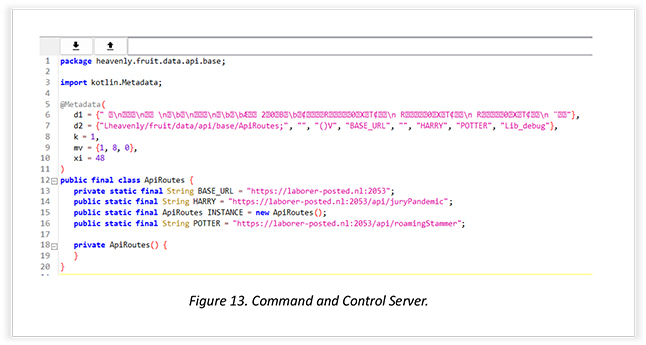
This excerpt shows the API module that is being used as a command-and-control server. Port 2053 is configured to the domain, where the transportation of data takes place.
The snippet below shows comments passed in one of the modules, revealing the use of the Ktor framework developed with Kotlin. Ktor is employed to establish communication between the command-and-control server and the app. Last month, our report exposed Android malware belonging to the DoNot APT, which had employed a similar library called retrofit for HTTP requests in their Android Malware, deployed on the Google Play Store. The malicious app has since been deleted.

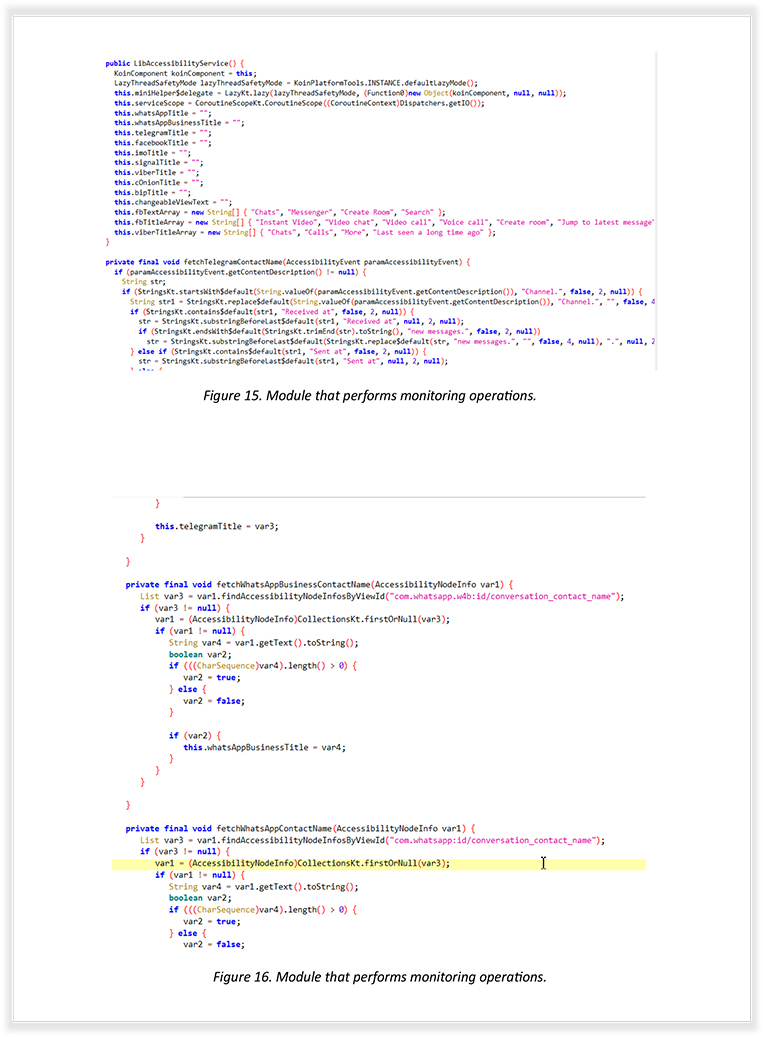
Here are some more out-takes from another module that interacts with the App, as part of monitoring different messenger apps like Telegram, Signal, Facebook Messenger, etc.
These snapshots are from a module that reveals the creation of JSON Object, which stores fetched information such as IMEI, Device ID, and SIM details, including location.
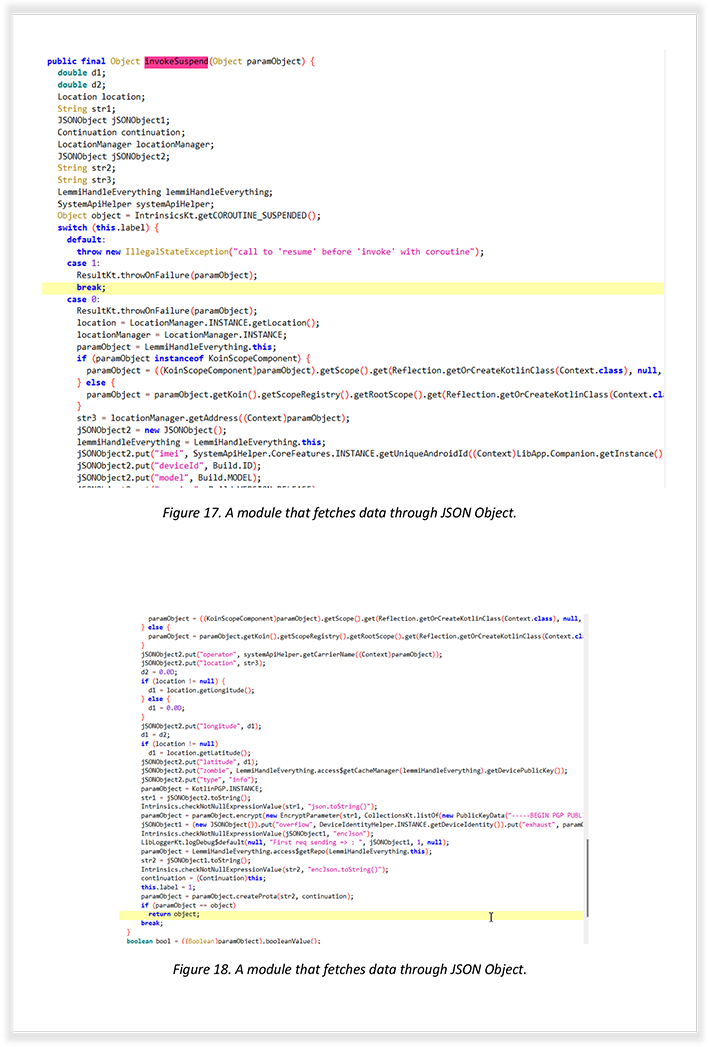
The following is from the module that performs RSA Encryption using the public key:

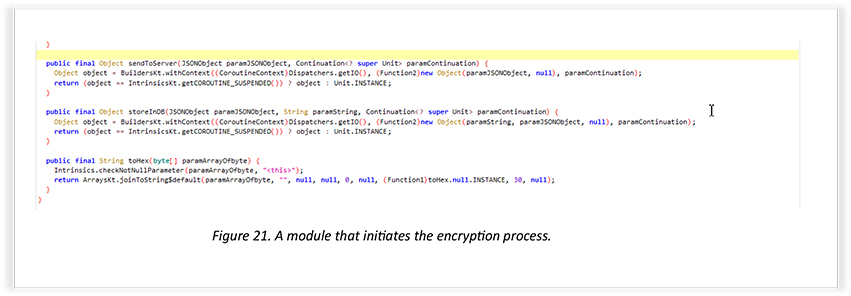
These module snapshots demonstrate the function of the encryption method to start the process of encrypting data. The analyses reveal that the threat actor is storing data in encrypted form using RSA/ECB/OAEPPadding.

The following demonstrates a captured Live HTTP request, which shows the letsencrypt certificate being used for encrypted communication between the app and server to dodge network interception.

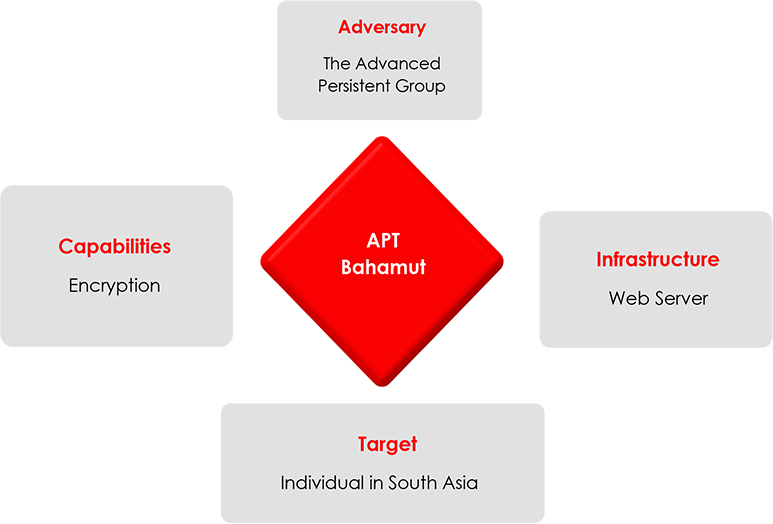
Through our technical analyses, we confidently attribute this attack to APT Bahamut. However, the tactics employed by this threat actor are similar to the tactics employed by APT DoNot, and it is also interesting to note that the target geography of both the threat actors is similar to each other.
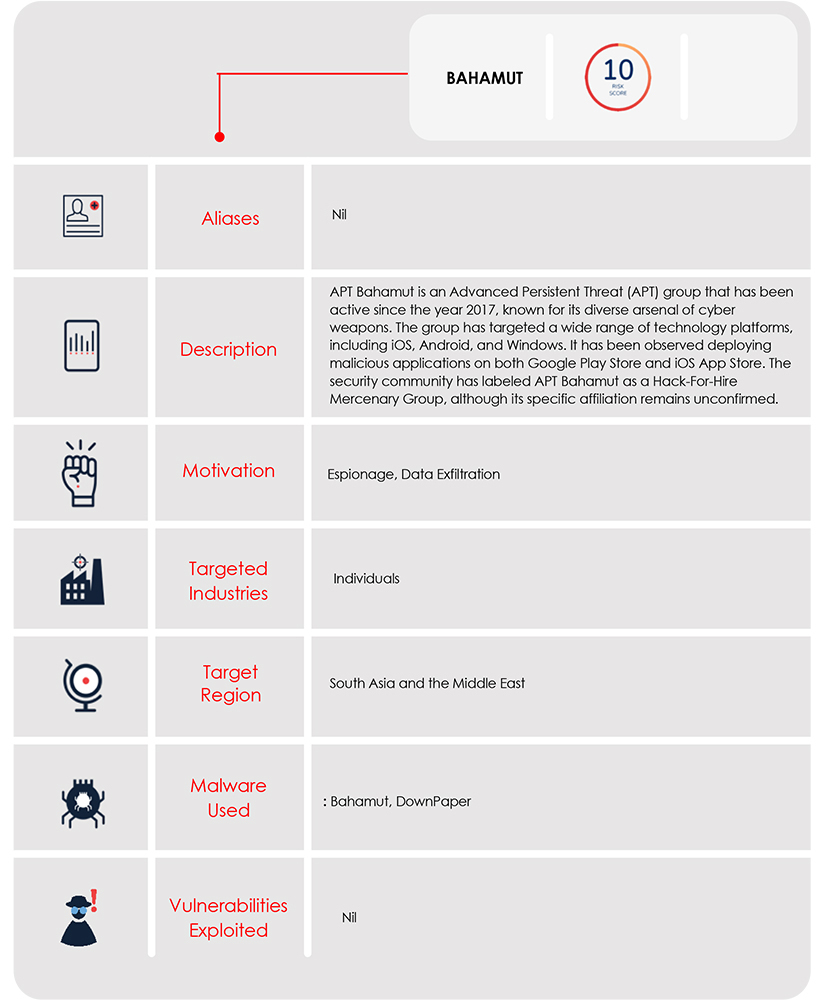
In this specific attack, the threat actor conducted targeted spear messaging attacks on WhatsApp Messenger, focusing on individuals in the South Asia region. The malicious payload was delivered directly through WhatsApp chat. The attack on the individual served the interest of one nation state government. The nature of this attack, along with previous incidents involving APT Bahamut, possibly indicate that it was carried out to serve the interests of one nation state government. Notably, APT Bahamut has previously targeted Khalistan supporters, advocating for a separate nation, posing an external threat to India. The threat actor has also aimed at military establishments in Pakistan and individuals in Kashmir, all aligning with the interests of one nation state government.
We are unable to disclose the specific target location of the sensitive cyber-attack, due to its sensitivity and security concerns. However, we can confirm that the target serves the interests of one nation state government. While some security organizations initially identified the threat as originating from a mercenary group, our own analysis indicates that it is, in fact, an Indian APT group acting on behalf of one nation state government. Several reasons support this conclusion.
Firstly, it is highly unlikely that the said nation state government will employ mercenary groups for hacking sensitive targets, unless the group is based within Indian territory. Based on past and present targets, it strongly suggests that the APT group operates within Indian territory. Furthermore, the threat actor utilized encryption techniques to secure the data and network traffic, using the same certificate authority as the DoNot APT group, which previously deployed Android Malware on the Google Play Store. Moreover, the APT actor employed the Ktor Library to efficiently fetch and transfer data to the command-and-control server, a tactic similar to how the DoNot APT group used retrofit for a similar data retrieval function.
Taking all these factors into account, our analysis strongly indicates that the APT group behind the attack has ties to the Indian territory and is acting in the interest of one nation state government.
| Indicator | Type | Remarks |
| 8A35D0B20B6F057FE42E606A124CB84D78FA95900A16B056269F1CC613853989 | Hash: SHA256 | Safe_Chat.apk |
| https://laborer-posted[.]nl:2053 | Domain and port | Command and control |
| Tactics | Technique ID | Description |
| TA0101 – Command and Control | T0869-Standard Application Layer Protocol | The threat actor uses a web service as a command-and-control server. |
| TA0035 – Collection | T1430-Location Tracking | Fetches precise Location as a part of information gathering. |
| TA0035 – Collection | T1532 – Archive Collected Data | The threat actor uses encryption over data transfer to the command and control. |
| TA0101 – Command and Control | T1521.002 Asymmetric Cryptography | The threat actor encrypts the fetched data using an asymmetric encryption method. |
| TA0035 – Collection | T1636.002 Call Log | The threat actor exploits Call log permission to access call logs |
| T1636.004 SMS Messages | The threat actor accesses SMSs by exploiting gained SMS permission. | |
| T1636.002 Contact List | The threat actor fetches Updated contact list. |