



This research conducted by the CYFIRMA Research team examines the critical privilege escalation vulnerability; CVE-2023-3460, present in the widely used Ultimate Member WordPress Plugin. With over 200,000 installations, the plugin was exploited by hackers through a zero-day vulnerability, posing a severe threat to WordPress sites worldwide. The flaw allows malicious actors to escalate their privileges, gaining unauthorized access to sensitive user data and potentially taking complete control over affected websites. Immediate action is required to mitigate this issue and safeguard online assets.
The vulnerability identified as CVE-2023-3460 poses a significant threat to websites utilizing the widely used Ultimate Member WordPress Plugin. With a severity score of 9.8, this critical privilege escalation vulnerability enables malicious actors to escalate their privileges, granting unauthorized access to sensitive user data and compromising the security of affected applications. The plugin, with over 200,000 installations, has become a popular choice for managing user profiles on WordPress sites. However, the versions below 2.6.7 are susceptible to this flaw, rendering websites at risk of complete compromise and unauthorized control.
Privilege escalation vulnerabilities present grave concerns for website administrators, as attackers can exploit these weaknesses to attain administrative access, allowing them to manipulate content, distribute malware, and potentially take full control of the entire website. This poses significant risks to user privacy, potentially leading to data breaches and identity theft. Additionally, the reputation of affected websites may suffer, and financial losses could ensue if customers lose trust in the platform’s security.
Key Takeaways:
Acknowledgements:
CYFIRMA Research teams acknowledge security researchers who responsibly disclosed the vulnerability.
Vulnerability type: Privilege Escalation
CVE ID: CVE-2023-3460
CVSS Severity Score: 9.8
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H Application: Ultimate Member WordPress Plugin
Impact: Complete compromise of website, unauthorized access to sensitive user data
Severity: CRITICAL
Affected Versions: < 2.6.7
Patched Available: YES Latest Version: 2.6.8
The Ultimate Member WordPress Plugin, a popular choice for user profile management, has been discovered to have a critical privilege escalation vulnerability, designated as CVE-2023-3460. The flaw enables bad actors to exploit a zero-day loophole, bypassing regular security measures, and escalate their privileges within the WordPress site.
By exploiting the vulnerability, attackers can attain administrative access, compromising user data, and gaining control over the website, which can ultimately lead to data breaches, unauthorized content modifications, and even complete website hijacking. As the plugin is widely used across diverse industries (from personal blogs to large-scale e-commerce platforms) the risk of exposure is large.
The CVE-2023-3460 vulnerability poses severe ramifications for affected websites. Malicious actors can exploit this flaw to compromise user data, leading to privacy violations and potential identity theft. Furthermore, unauthorized access to website administration can result in content manipulation, distribution of malware, and disruption of services. The reputation of compromised websites may suffer, leading to loss of trust and potential financial repercussions.
The vulnerability affects the Ultimate Member WordPress Plugin across versions below 2.6.7.
The CYFIRMA research team analysed a method to exploit the zero day in Ultimate Member Plugin version 2.6.5. We have setup our own lab for analysing the vulnerability.
1. Installation
We have installed Ultimate Member Plugin version 2.6.5, which was our scope for this research.
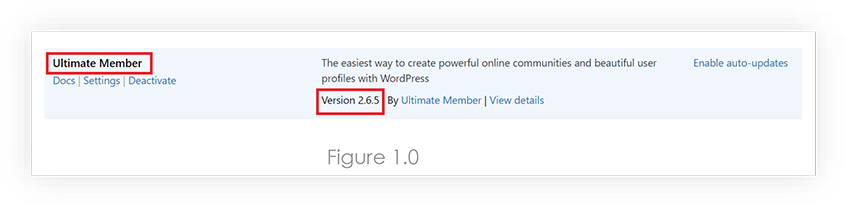
2. The Vulnerability
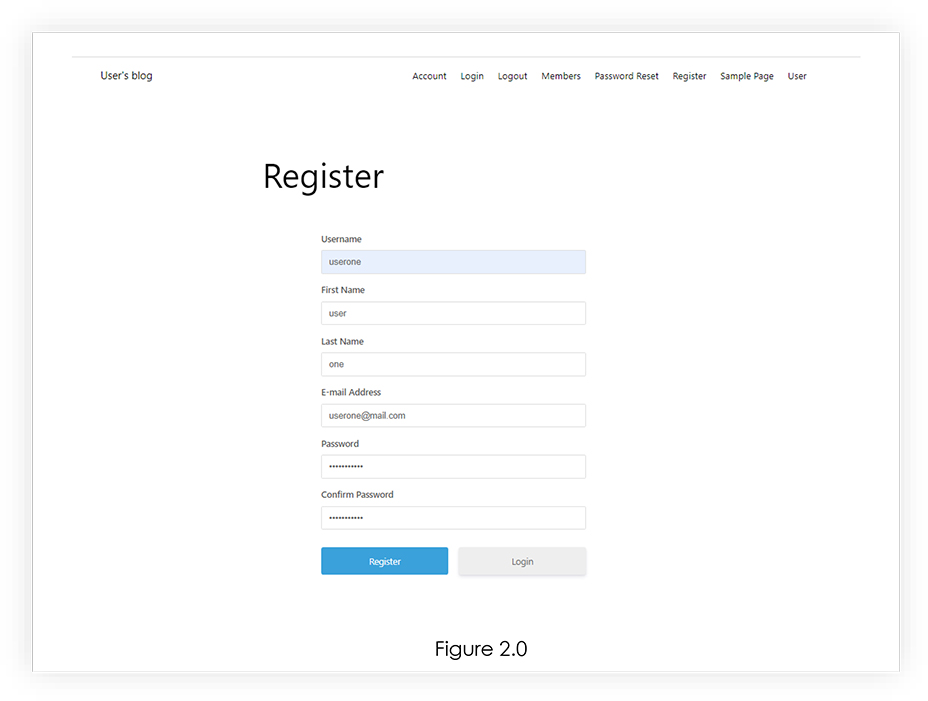
To Exploit this vulnerability, we visited the register page and filled in the details. Refer Figure 2.0
Next, upon filling in the details and intercepting the request in burp. We have concatenated the payload in the POST request. Refer 2.1
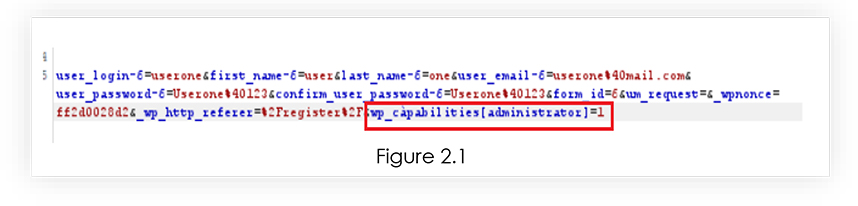
The payload takes advantage of WordPress’s built-in serialization to pass the value as an array. By manipulating the “wp_capabilities” field, the payload sets the administrator role to “1,” effectively granting the user escalated privileges. This serialized array allows attackers to exploit the vulnerability in the Ultimate Member plugin, enabling unauthorized access and compromising website security. Through this clever manipulation, the payload tricks WordPress into interpreting the input as a legitimate serialized array, bypassing regular input validation, and gaining control over user roles and capabilities.
3. Result
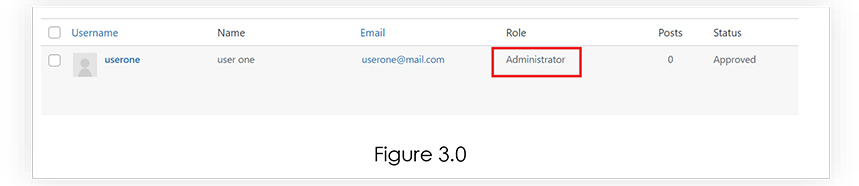
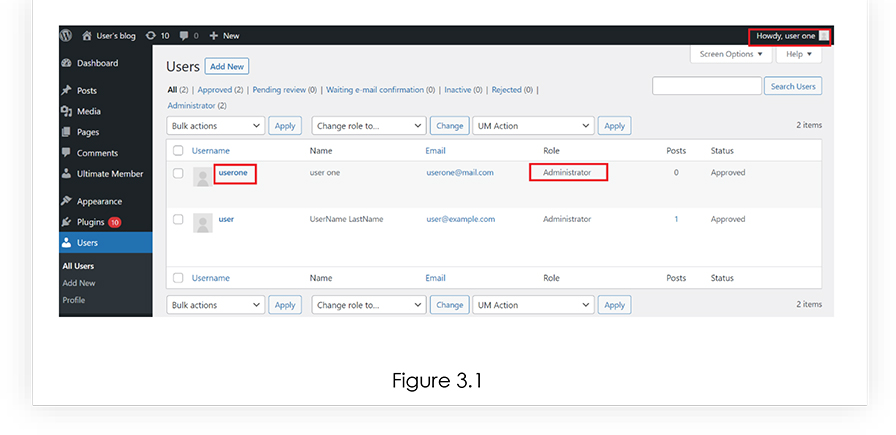
After injecting the payload, we can see from Figure 3.0 that the role for user “userone” has been changed to Administration.
We have also checked by logging into the “userone”, and it redirects to WordPress admin dashboard, where the user can make any changes to the website. Refer Figure 3.1.
Website administrators are strongly urged to take immediate action to mitigate the risk posed by CVE-2023-3460. CYFIRMA Research recommends the following steps:
Target Geography:
The Ultimate Member WordPress Plugin vulnerability (CVE-2023-3460) is a global concern, potentially impacting WordPress sites worldwide that have installed the plugin. While the vulnerability is not geographically limited, websites hosted in regions with a higher concentration of WordPress users, such as North America, Europe, and Asia-Pacific, may have a higher risk of exploitation. These regions typically have a larger number of WordPress installations, increasing the pool of potential targets for attackers, seeking to exploit the flaw.
Target Industry:
The Ultimate Member WordPress Plugin vulnerability can potentially impact websites across various industries that use the plugin for user profile management and community building. Industries that commonly rely on WordPress websites for their online presence, including personal blogs, corporate websites, e-commerce platforms, educational institutions, and non-profit organizations, may be at risk.
The plugin’s wide adoption in diverse industries makes it an attractive target for cyber attackers seeking to compromise user data or gain unauthorized access to websites with valuable content and resources.
Target Technology:
The Ultimate Member WordPress Plugin vulnerability is specific to the Ultimate Member plugin. However, it highlights the broader risks associated with using popular WordPress plugins. Since WordPress is a widely used content management system (CMS), websites using various plugins are potential targets for attackers.
The popularity of WordPress and its extensive plugin ecosystem provides cybercriminals with a large attack surface, making it crucial for website owners to prioritize security measures, regularly update plugins, and implement best practices to safeguard against potential vulnerabilities and attacks.
From underground forums, CYFIRMA Research team has observed that unknown hackers are selling WordPress accounts with wp-admin and wp-login access which could help the malicious actors to gain the vulnerable plugin.
Organizations and individuals using WordPress are advised to remain vigilant and take initiative-taking measures to protect their websites from potential attacks. This includes regularly updating WordPress and all associated plugins, using strong and unique passwords, and implementing additional security measures such as two-factor authentication and web application firewalls. It is also recommended to monitor underground forums and security news outlets to stay informed about emerging threats and vulnerabilities.
The CVE-2023-3460 privilege escalation vulnerability in the Ultimate Member WordPress Plugin presents a critical security risk to websites using the affected versions. The flaw allows attackers to escalate their privileges, gaining unauthorized access to sensitive user data and compromising website security.
Website administrators should prioritize immediate updates and monitoring to safeguard their online assets. Continuous vigilance and adherence to WordPress security best practices are essential to prevent potential exploitation. As a responsible and leading cybersecurity company, CYFIRMA remains committed to uncovering such vulnerabilities, contributing to a safer digital landscape for all.