


Research team at CYFIRMA recently discovered a malicious sample in wild which pretends to be a ransomware named as ALC Ransomware. Our research team analysed and found it to be a scareware in actual, as it is not encrypting files on the victim machine.
On execution it disables the task manager, freezes or locks the screen and displays a ransom note on screen with instructions on how to decrypt/recover the data. The execution is very fast as it takes the malware couple of seconds to lock the victim’s screen. CYFIRMA research team constantly monitors and analyse such new malware strain and their behaviour.
The malware pretends to be a ransomware but is not fulfilling the basic criteria to encrypt the files. it simply disables the task manager and displays a ransom message on the locked screen, rendering the machine inaccessible to the user and causing chaos for the victim/organization.
ALC is suspected to be a scareware, pretending to be a ransomware. Scareware is a type of malware attack and a gateway to a sophisticated cyberattack and not an attack in and of itself. It is detected on a target device, directing the user to download or purchase the malicious software to resolve the issue.
The malware is poorly crafted and lacks sophistication, indicating that it may be in its early stages of development or created by less skilled and resourced authors, who may be affiliated with nations opposing Russia. These type of malware could be leveraged as low investment and big benefits type of scheme by the threat groups and cyber criminals.
The ransomware drops a ransom note named “RUS!.txt” on the desktop, stating that ALC ransomware is suspected to target Russia and its counterparts. This suggests that the threat group or attackers behind the malware could be from a nation that is opposing Russia and its allies.
Additionally, given the prolonged ongoing conflict between Russia and Ukraine, it is possible that the malware authors have some connection to the conflict and are using cyberattacks and scareware as tools to carry out cyberespionage or operational disruption.
CYFIRMA research team believes such type of malware with enhanced capabilities could be adopted and used in future as an attack method by threat groups from other nations such as Russia, China, Korea, Iran to target organizations in both public and private sectors. This scareware could cause fear and chaos in target victims, to comply to the potential demands and benefit the threat groups.
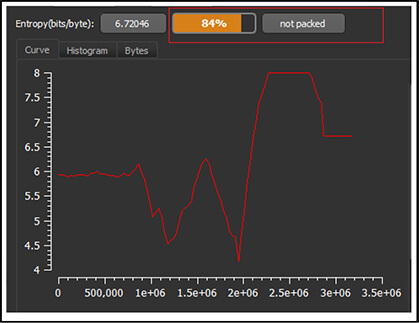
MD5: 3e6d52e151154065eb9da3da48dc7a7d
SHA256: 0ABE1AB9C75395A4CA829028D9C8C6530BD3BFDA49E4B856B6F3539B9AA36EA5
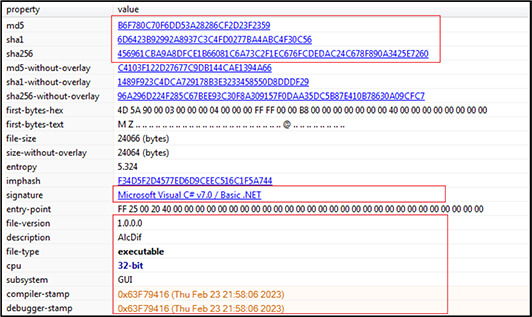
The binary is 64-bit PE executable having console subsystem. There is no information available regarding compilation time, as compilation timestamp is empty.
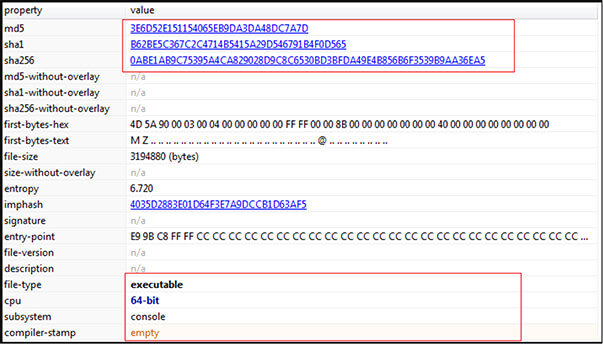
The binary is not packed.
Upon execution, the malware sample drops following files on the machine:
AlcDif.exe (Desktop): b6f780c70f6dd53a28286cf2d23f2359
RUS!.txt (Desktop): 79058D9B0FDFDADA59C18DF8AC026224
Pass (Desktop): 7384C4FCCF3818EF77C6188D7104A0B5
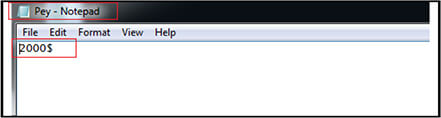
Pey (Desktop): 8D1C52CB4E6A5EA02275637D26F90F60
ALCKEY (Sample File Folder): 2B410375146A9BB550EDCA0BAE42A1CB
C.txt (Sample File Folder): 9A5E23DCC123B4B7526CE1D61DAB6CA4
Afterwards, it executes the file “AlcDlf.exe” and spawns the child with name “AlcDlf.exe” and deletes itself. The process tree corresponding to our sample execution is shown below.

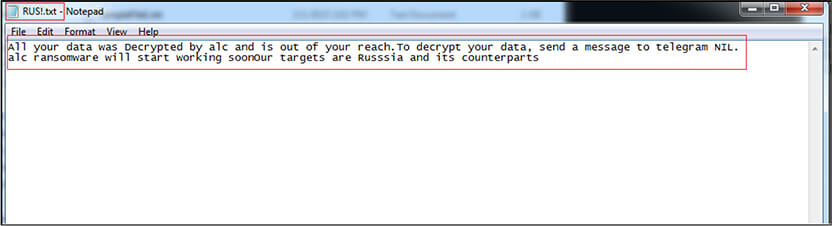
Before locking the screen, the malware drops the text file with name “RUS!.txt” on Desktop and displays the text. The text file contains following text as shown in below screen shot. The message is that all files on the machine are “Decrypted” (instead of Encrypted) and are out of reach of the owner of machine, and to decrypt the data the victims are instructed to connect with the attackers on Telegram; however, no Telegram address is provided. Finally, the malware authors have claimed that their targets are Russia and its allies. Based on the aforementioned indicators, it appears that the malware is poorly crafted and may be in its early stages of development, possibly created by less skilled authors. However, the authors’ targeting of Russia and its allies, suggests a clear motive behind their actions.
The dropped file “AlcDlf.exe” is the payload which further locks the screen and disables the task manager of the victim machine. The binary is 32-bit, written in .NET and having GUI subsystem. The compilation time stamp is latest of Feb-2023 which indicates that it is recently launched by malware authors.
On execution, within couple of seconds, the malware disables the task manager and locks the screen and display following ransom note on the screen with instructions how to recover the data, crypto wallet address, amount to be paid and other details. The ransom note also provides the QR code for payment, which on scanning directs to the same wallet address given on screen.

The ransom note wallpaper mentions that “All your files are encrypted”. Afterwards it provides the instructions to recover/decrypt data, the victim has to pay the amount “554 XMR” (which is equivalent to approx. $83,680 USD) into attackers crypto wallet “46yRW1YjGQUgZi2CrrX5ENj9boHWD8VqYJbGyv1f9QgvGuqJfUanwsfEEBuFhu4VqeaQVwqx2ctLPQbFbHjiRCja4cak53o” and afterwards have to send a message to attacker’s email-id “Alc@cock[.]li” that amount has been sent with the victim’s cvID, SuffID and PersonnelID. However, we ran multiple instances for the malware and these cvID, SuffID and PersonnelID remains same each time and is hardcoded.
The ransom note also mentioned that after the email from the victim, the attackers confirm that payment is received and later they will send instructions to decrypt the data. The attackers also warn that no decryption is possible after a week, the amount to be paid is doubled after two days and no decryption tools are able to decrypt the data. Further, at the end of ransom note, a textbox is provided, possibly to enter a password/key to unlock the system/screen and get access to the data.
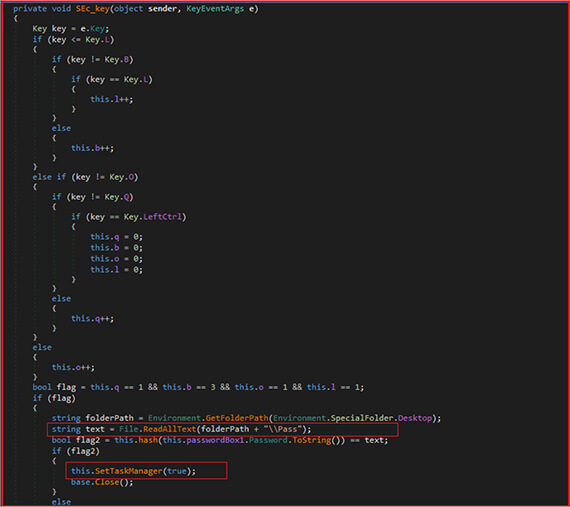
The screenshot below shows a snapshot of the code to handle the password provided by user on lock-screen. The code uses a specific combination of keystrokes to trigger the password check. The SEc_key function is a C# event handler for KeyEventArgs. This function is designed to detect a specific combination of keystrokes and execute a particular set of instructions if the keystrokes are detected. When user provides the password, the following function calculates hash and compares it with hash (2943a567bc05bc66ca6201dbc5f00bec3f774a47b1b94289a2ae8e79834c21a5) present in dropped file “Pass” on Desktop. If password hashes match then it enables the task manager, which was earlier disabled by the malware.
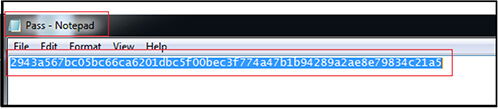
Dropped file “Pass” contents containing hash for the password:
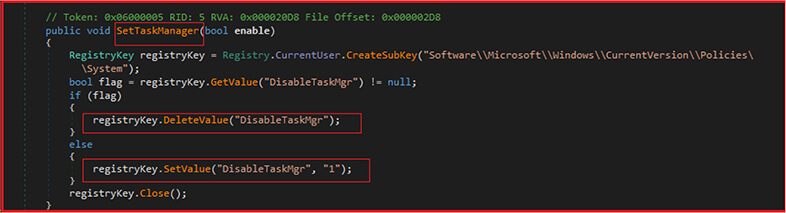
The code given below is used by malware to prevent the user from accessing the Task Manager and terminating the malicious process or identifying its presence. By disabling the Task Manager, the malware can run without interruption and continue to carry out its malicious activities.
First, the function creates a subkey called “Software\Microsoft\Windows\CurrentVersion\Policies\System” under the CurrentUser registry key. This subkey controls various system policies on the user’s computer. Next, the method checks if the value “DisableTaskMgr” exists in this subkey. If it exists, the method deletes the value by calling registryKey.DeleteValue(“DisableTaskMgr”). If it doesn’t exist, the method sets the value of “DisableTaskMgr” to “1” using the registryKey.SetValue method. This value disables the Windows Task Manager.
Below code shows, the malware creating a registry entry to gain persistence. This code is used by the malware to ensure that it runs automatically every time the user logs into their computer, allowing the malware to continue to operate even if the user attempts to remove it from their system.
The method Run which sets a registry value to run file “AlcDif.exe” located on the victim’s desktop when the computer starts up. It creates a subkey called “Software\Microsoft\Windows\CurrentVersion\Run” under the CurrentUser registry key. This subkey controls the programs that are launched when the user logs in. The code then sets the value of a registry entry called “Firfox” to the path of the “AlcDif.exe” file on the desktop.
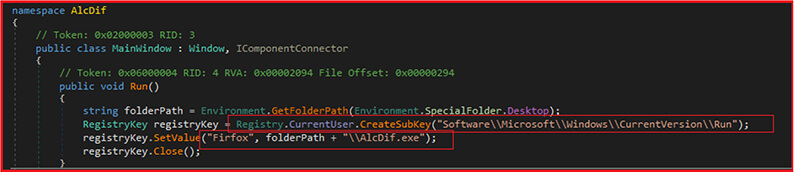
As shown below, the malware sets up to run on system startup (by calling “Run” function, explained above), disables the Task Manager (by calling “SetTaskManager” function, explained above), and displays the amount of ransom demanded by the malware to the user. The function gets the path of the user’s desktop folder, It then reads the contents of the “Pey” (dropped by the malware at desktop on execution) file on the desktop and displays the amount of ransom demanded by the malware to the user.
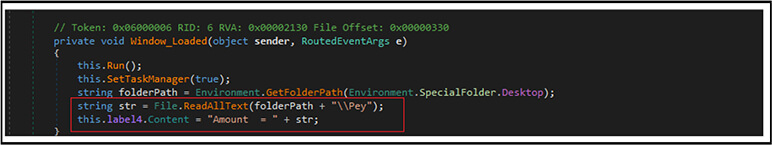
Below are the contents of the dropped file named “Pey” on the desktop, which shows a value of $2000 as the probable ransom amount. This value is different from the amount displayed on the lock screen, which is 554XMR (Monero currency).
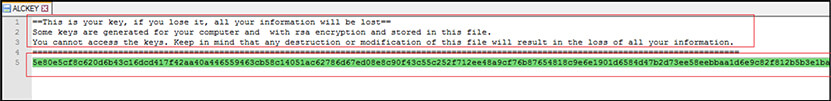
There is another file created “ALCKEY”. It is dropped in the same folder from where we are executing our main malicious sample (3e6d52e151154065eb9da3da48dc7a7d). The contents of the file states that it contains a key mentioned below:
“5e80e5cf8c620d6b43c16dcd417f42aa40a446559463cb58c14051ac62786d67ed08e8c90f43c55c252f712ee48a9cf76b87654818c9e6e1901d6584d47b2d73ee58eebbaa1d6e9c82f812b5b3e1ba15b69cfcdb2c776d6cb988da0fc3d8a959363ad5297de6798f4676cc7225a42fe14ad093f0a8d40c2ff1ac9eedb01ea4d1fc2e1fc93aa9e2cc5556c314ccd39680163d470b38d9f60f0e7ac7ab51a5ec3ace29dd1e248bfa168d3584015c72c41cef528948c6b50096ea296cba4948ff9c0f94609f812dc960ecb957cc28db57d6fe9465dc7132b40d95f23f1a4fe08299f4edbe79d4a03b30358c5ab0f42b1c3a79caf71fc3be0b3b3d919de9902bab1cffb75b92de7804c116bf49d5d8c6e1ac33ea5c3b80c9634bd7210bb65521a565fd69b65a7629c99e86c7c1200a7013f1a5ce7a256b98031d57b89fc7c84808453c4f54f1dbf556fbed912a2d7b045c61d44ed4442b3514df69eaf90caa8cce5761bbeac14f2a40ff3f0d322f48d594e181204cbaca487b”
And if the victim lose this key or modify it any way (which is generated with RSA encryption), it results in loss of all of the information/data of the victim.
CYFIRMA’s research team has identified a new strain of malware, named ALC Ransomware, which masquerades as ransomware but is a scareware. This malware does not encrypt files on the victim’s machine, but instead disables the task manager, locks the screen and displays a ransom note. The group or attackers deploying this malware may be affiliated with countries hostile to Russia, as indicated by the ransom note mentioning that ALC ransomware targets Russia and its counterparts. Although the malware lacks sophistication and is poorly crafted, it can still cause significant damage to victims and organizations. CYFIRMA’s research team constantly monitors and analyses such types of new malware strains and their behaviour to provide insights to cyber defenders and better protect their clients from attacks involving such malware.
| Sr.no | Indicator | Type | Remarks |
| 1 | 3e6d52e151154065eb9da3da48dc7a7d | MD5 File Hash | Sample File (ALC Ransomware) |
| 2 | b6f780c70f6dd53a28286cf2d23f2359 | MD5 File Hash | AlcDif.exe |
| 3 | 79058D9B0FDFDADA59C18DF8AC026224 | MD5 File Hash | RUS!.txt |
| 4 | 7384C4FCCF3818EF77C6188D7104A0B5 | MD5 File Hash | Pass |
| 5 | 8D1C52CB4E6A5EA02275637D26F90F60 | MD5 File Hash | Pey |
| 6 | 2B410375146A9BB550EDCA0BAE42A1CB | MD5 File Hash | ALCKEY |
| 7 | 9A5E23DCC123B4B7526CE1D61DAB6CA4 | MD5 File Hash | C.txt |
| 8 | 2943a567bc05bc66ca6201dbc5f00bec3f774a47b1b94289a2ae8e79834c21a5 | SHA256 Hash | Password Hash (contents of Pass File) |
| 9 | 5e80e5cf8c620d6b43c16dc d417f42aa40a446559463cb58c14051ac 62786d67ed08e8c90f43c55c252f712ee 48a9cf76b87654818c9e6e1901d6584d47b 2d73ee58eebbaa1d6e9c82f812b5b3e1ba15 b69cfcdb2c776d6cb988da0fc3d8 a959363ad5297de6798f4676cc7225a 42fe14ad093f0a8d40c2ff1ac9eedb01ea 4d1fc2e1fc93aa9e2cc5556c314ccd396801 63d470b38d9f60f0e7ac7ab51a5ec3ace29dd1e 248bfa168d3584015c72c41cef528948c6b50096e a296cba4948ff9c0f94609f812dc960ecb957cc28d b57d6fe9465dc7132b40d95f23f1a4fe08299f4edbe79 d4a03b30358c5ab0f42b1c3a79caf7 1fc3be0b3b3d919de9902bab1cf fb75b92de7804c116bf49d5d8c6e1ac 33ea5c3b80c9634bd7210bb65 521a565fd69b65a7629c99e86c 7c1200a7013f1a5ce7a256b98031d5 7b89fc7c84808453c4f54f1dbf556fbed91 2a2d7b045c61d44ed4442b3514df69eaf90caa8 cce5761bbeac14f2a40ff3f0d322f4 8d594e181204cbaca487b | Text/Key | Key Value (contents of ALCKEY File) |
| 10 | 46yRW1YjGQUgZi2CrrX5ENj9boHWD8VqYJbGyv1f9QgvGuq JfUanwsfEEBuFhu4VqeaQVwqx2ctLPQbFbHjiRCja4cak53o | Text/Address | Crypto Wallet Address |
| Sr.no | Tactics | Technique ID |
| 1 | Execution (TA0002) | T1129: Shared Modules |
| 2 | Persistence (TA0003) | T1547.001: Registry Run Keys |
| 3 | Defense Evasion (TA0005) | T1112: Modify Registry |
| 4 | Credential Access (TA0006) | T1056: Input Capture |
| 5 | Discovery (TA0007) | T1012: Query Registry T1082: System Information Discovery |
| 6 | Impact (TA0040) | T1490: Inhibit System Recovery |