



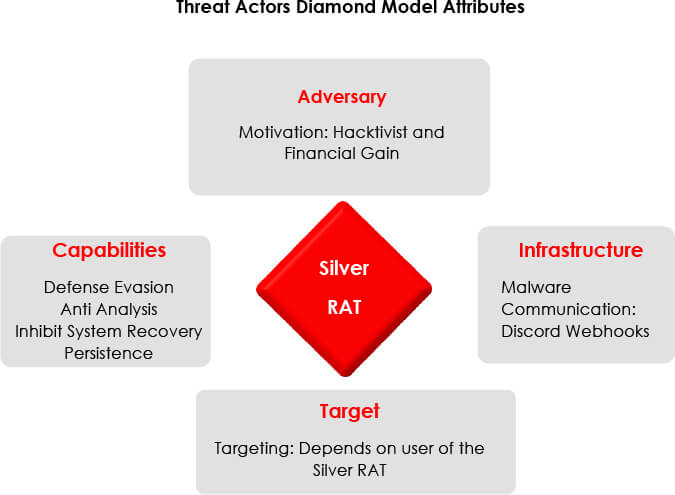
This report provides a glimpse into the evolving landscape of RAT development and malicious activities performed by threat actors working under name of ‘Anonymous Arabic’. Our team investigated the Silver RAT (written in C sharp) which has capabilities to bypass anti-viruses and covertly launch hidden applications, browsers, keyloggers, and other malicious activities. The developers operate on multiple hacker forums and social media platforms, showcasing an active and sophisticated presence, in addition to a Telegram channel offering a range of services including the distribution of cracked RATs, leaked databases, carding activities, and the sale of social media bots, which are employed to promote services by automatically engaging with and commenting on user content.
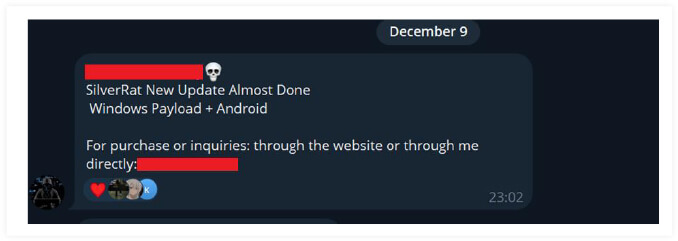
Silver RAT v1.0 was observed in the wild during November 2023. The authors of Silver RAT have also developed another product called S500 RAT. While Silver RAT is currently Windows-based, recent announcements indicate that the developers are planning to launch a new version with the ability to generate both Windows and Android payloads. Silver RAT v1.0 comes with destructive features such as a keylogger, UAC bypass, data encryption using ransomware, and functions to destroy system restore points.
The developer of Silver RAT is, known as ‘noradlb1,’ and is active on prominent hacking forums like XSS, Darkforum, TurkHackTeam, and others, with an arguably respected reputation. The RAT first appeared on their Telegram channel and later on Turkhackteam and 1877 forums. Silver RAT was cracked and leaked on Telegram around October, 2023, and now users on Telegram and GitHub are sharing cracked versions of Silver RAT v1.0 to users without the means to purchase RATs (however there is evidence from user conversations that this may not be as effective as other well-known RATs like xworm).
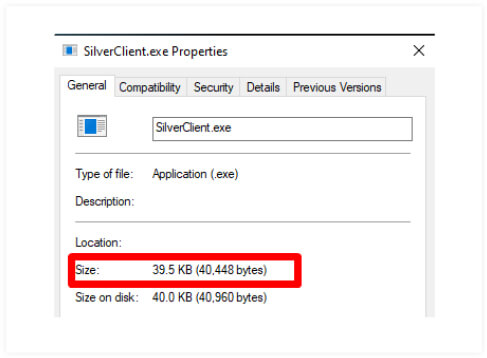
While generating a payload using Silver RAT’s builder, threat actors can select various options with a payload size up to a maximum of 50kb. Once connected, the victim appears on the attacker controlled Silver RAT panel, which displays the logs from the victim based on the functionalities chosen. The threat actor can hide processes under false headings, and the final payload can be generated in a Windows executable file, delivered through various social engineering methods.
The announcement about the sale of Silver RAT 1.0 initially appeared on the TurkHackTeam forum and later surfaced on 1877 and other underground hacking forums.
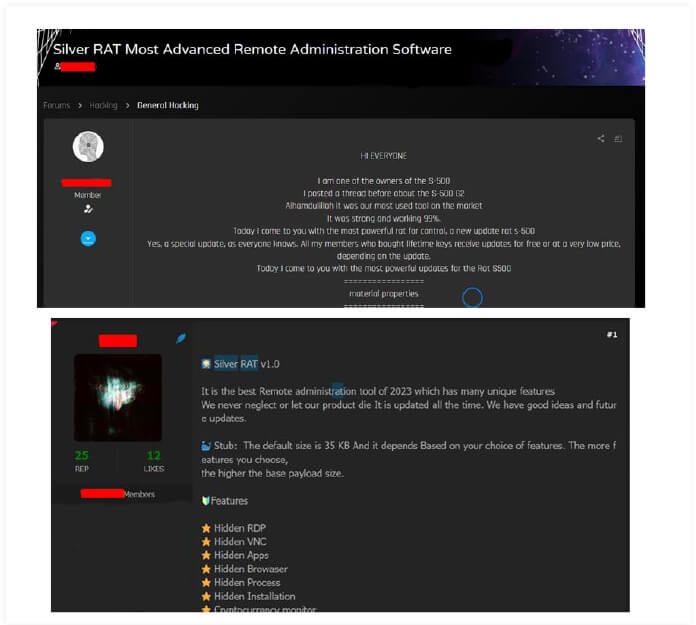
Our team found that the threat actor also posted in a well-known Russian forum, selling Silver RAT v1.0.
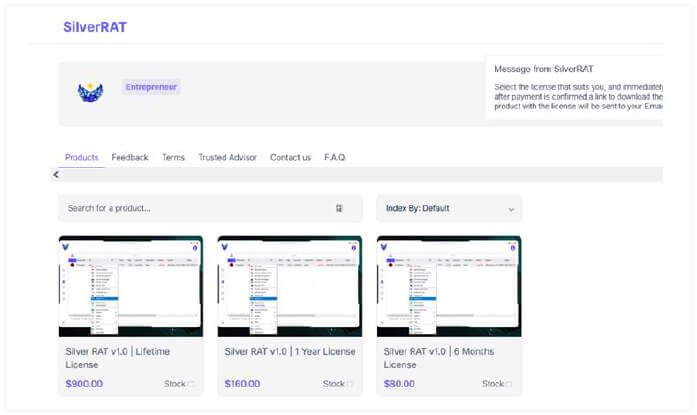
Additionally, they created a website under an e-commerce domain to facilitate the sale of Silver RAT v1.0.
The initial announcement regarding the release of Silver RAT V1.0 was made on October 19, 2022 on their Telegram channel. Subsequent to this, (November 19, 2022) the threat actor released the RAT on two hacker forums.
Silver RAT v1.0 written in C Sharp is a Window based RAT builder for windows systems, which has different features like Bypass AV, stealing browser cookies, keylogger, hidden browser, hidden RDP access and much more.
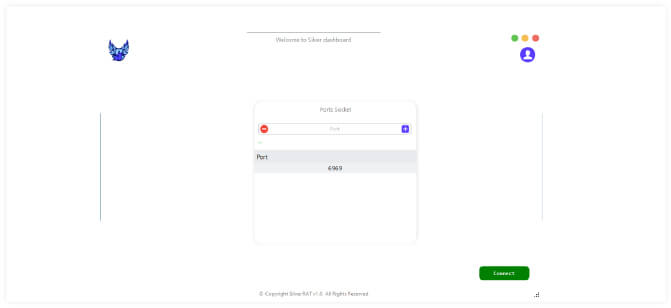
Our team have performed the analysis of the Silver RAT v1.0 builder in order to assess it’s capabilities: after executing, there is an initial prompt to request a port number on which Silver RAT will bind the IP, and port number for reverse shell.
This is the builder section of Silver RAT, where users will find numerous options. Some notable features include the ability to Bypass AV, conceal malicious processes by assigning custom process names, and specify the connection method. The user can choose between default connection settings by providing an IP for reverse connection or opt for a web HTML link.
Below is a list of the arguably most interesting functionalities of Silver RAT v1.0:
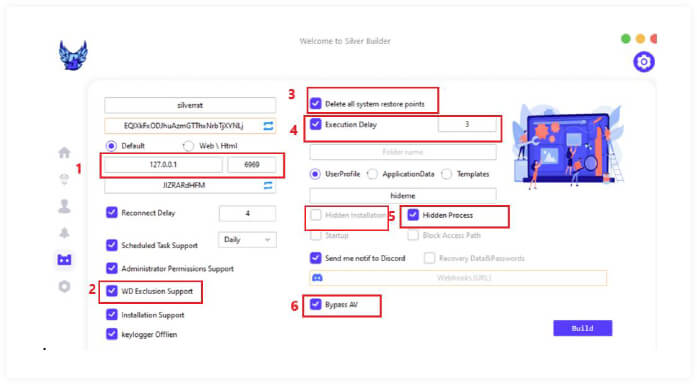
A point to note is that the payload size increases when users select more options, ranging from 40- 50KB.
In the execution process, the .Net executable payload can be delivered by using various social engineering tactics. Upon execution, an administrated permission prompt will appear, and it will run a CMD window that disappears in less than 2 seconds.
Following this, Silver RAT v1.0 establishes a connection, once connected the target will appear in the targets list.
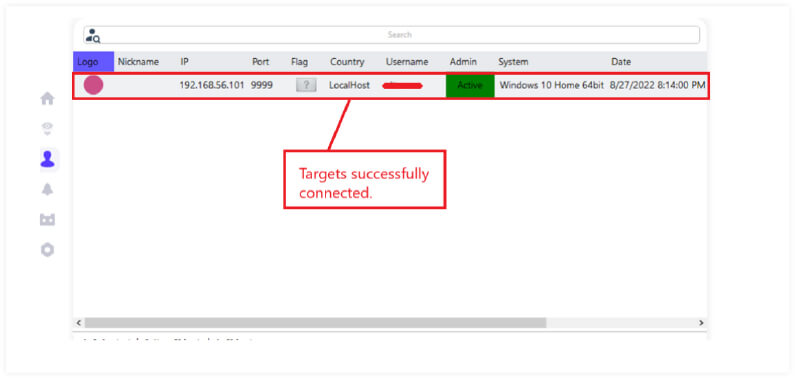
Upon successful connection, the attacker gains the ability to initiate various malicious activities on the target system, as seen in below snippet.
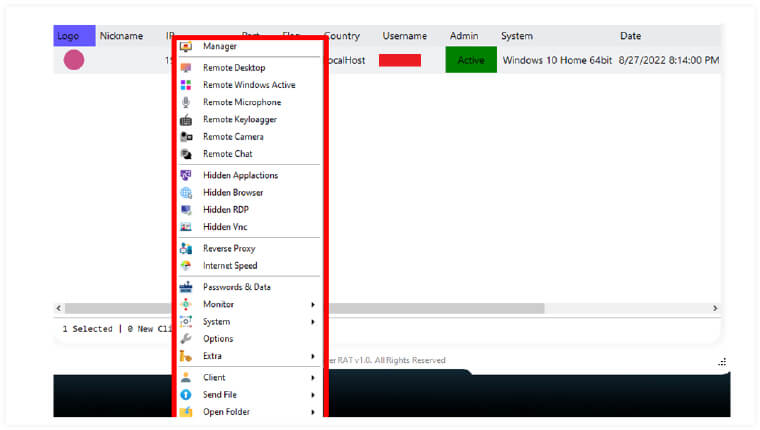
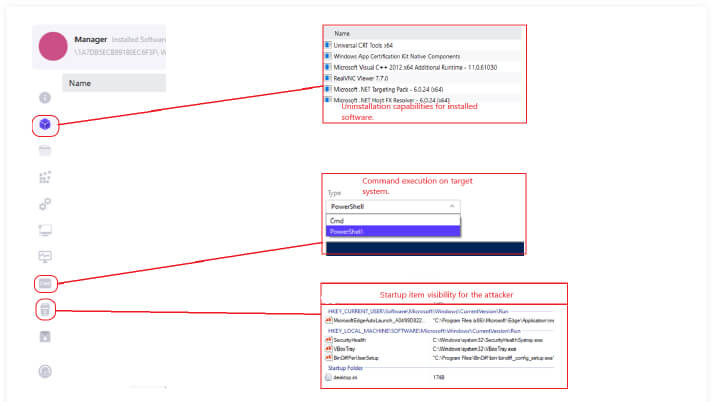
Beginning with the top option ‘Manager,’ the attacker can manage and control various aspects of the target system. This includes managing installed applications, navigating the file manager, modifying registry keys, checking startup items, and monitoring the performance of the target system.
Additionally, attackers can leverage other interesting malicious activities on target system such as:
Hidden Apps
– Attackers can control multiple applications on the client’s computer covertly, with various apps running concurrently.
Hidden Browsers
– Gives the ability to add client browsers to a hidden list.
– Enables the attacker and the victim to use the browser at the same time.
Hidden VNC
– Gives the attackers control of target system
– Attackers can control the client’s internet browsers.
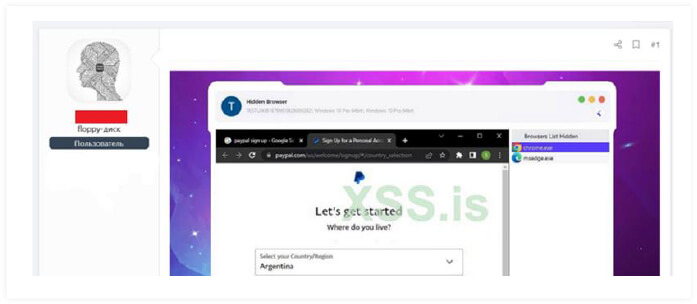
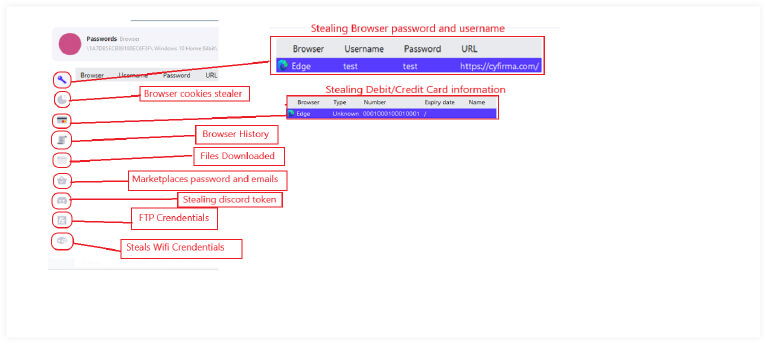
The image below illustrates specific stealing capabilities of Silver RAT v1.0.
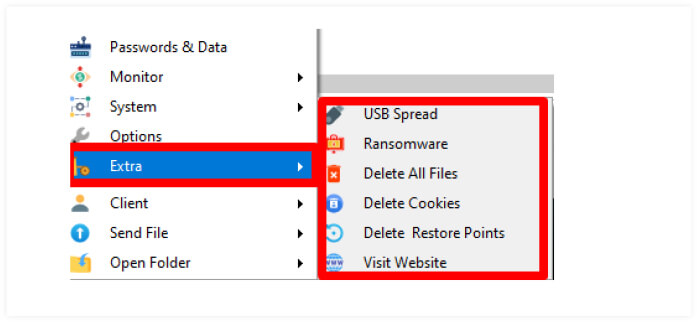
Additionally, an attacker can encrypt data on the victim’s computer using ransomware, delete data and browser cookies from the target computer remotely, propogate like worm through USB , and erase system restore points.
After analyzing the program file of the builder, there are some flags that warrant discussion:
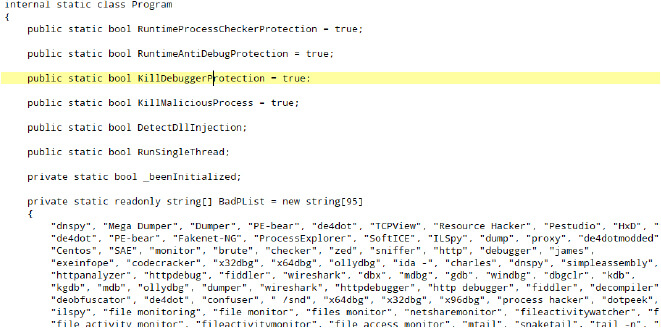
The below highlights boolean flags like ‘RuntimeProcessCheckerProtection’, ‘RuntimeAntiDebugProtection’, ‘KillDebuggerProtection’, ‘KillMaliciousProcess’, ‘DetectDllInjection’, and ‘RunSingleThread’.
These flags are used to protect the RAT from various debugging techniques, as well as protecting the program from being analyzed. If such activity is detected, the anti-analysis code will terminate the program’s execution.
In the snippet below this list called ‘BadPList’ containing different strings related to programs used by malware analysts. Each string represents the name of a process or tool that the RAT considers potentially bad or associated with debugging and analysis activities.
Threat Actor Profile:
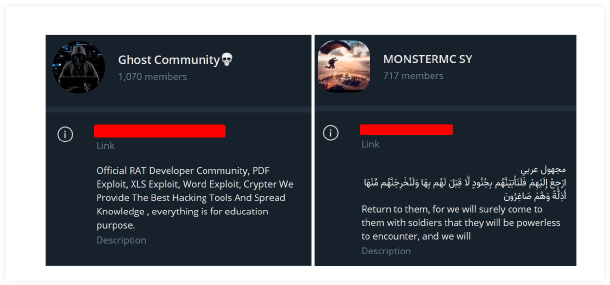
The Silver RAT developers have 2 different Telegram channels with 1k+ on one channel and 700+ users on another channel, indicating a high user engagement rate.
CYFIRMA researchers found out that the threat actor has been using a well-known Crypto wallet, employing different addresses for transactions, ranging from Bitcoin to Ethereum and USDT (Tether).
Their Bitcoin wallet appears to be empty, while their Ethereum wallet shows 8 transactions including 1 deposit and 7 transfers.
We note approximately 2,275.67 USD of transactions between December 24,2023 and December 25,2023 period, including potential cashing out activities.
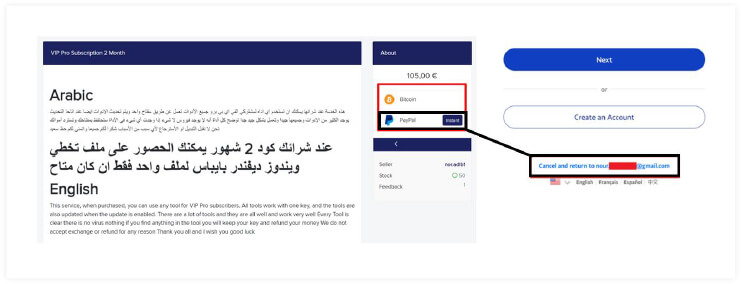
During the analysis, we backtracked to the PayPal purchase option, and upon exiting the page, we obtained the Gmail address used by threat actor for PayPal account.
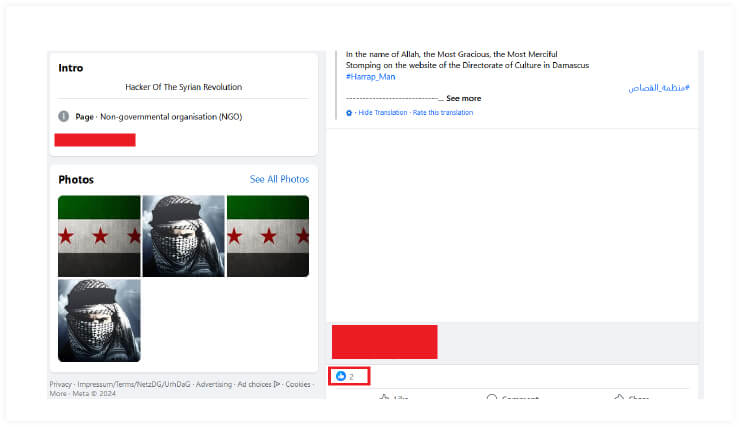
During our investigation, we discovered a Facebook account of a hacktivist group that supports the “Syrian Revolution”, with post engagement from a developer of Silver RAT based on multiple attribute matches. Reviewing the developer’s previous posts reveals a history of offering various first-person shooter (FPS) game hacks and mods.
Based on these observations, it can be ascertained with high confidence that the Silver RAT developer:
A threat actor using the moniker ‘Dangerous silver,’ and another using ‘Monstermc’, serve as developers for S500 RAT and Silver RAT. They operate a Telegram channel offering malware-as-a-service, distributing cracked RATs from various developers, leaked databases, carding services, fake pages, and the sale of Twitter/Facebook bots. They have blog website named as ‘Anonymous Arabic’ that is moderated by 2 other individuals, as well as groups named as Monstermc and Syria Pirates.
Following the leak, Silver RAT v1.0 is freely available over Telegram, as well as some underground forums and Github, complete with full instructions on its malicious use.
The threat actor is actively sharing information on various social media platforms, as well as development platforms like GitHub, where the threat actors shared different red teaming methods and cracked malware.
The threat actor’s YouTube channel where they shared details about Silver RAT was banned by the platform, but a new (and still active) channel shares tutorials about their malicious tools.
The threat actor Pastebin profile shows they pasted source code of builders as well as some bypass tricks.
We have discovered that the threat actor appears to have a good reputation on across various underground forums.
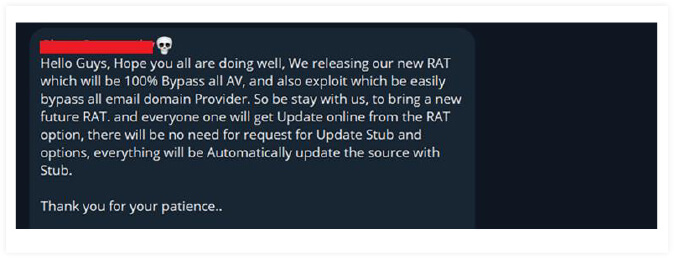
Silver RAT v1.0 generates a Windows executable, however Telegram chatter purports that the upcoming release of a new version of Silver RAT will be capable of generating payloads for both Android and Windows platforms.
| Tactics | Techniques |
| TA0002: Execution | T1059: Command and Scripting Interpreter T1053: Scheduled Task/Job |
| TA0003: Persistence | T1053: Scheduled Task/Job |
| TA0004: Privilege Escalation | T1055: Process Injection T1053: Scheduled Task/Job |
| TA0005: Defense Evasion | T1112: Modify Registry T1497: Virtualization/Sandbox Evasion T1055: Process Injection T1027: Obfuscated Files or Information |
| TA0006: Credential Access | T1056: Input Capture T1539: Steal Web Cookie T1552: Unsecured Credentials T1528: Steal Application Access Token |
| TA0007: Discovery | T1057: Process Discovery T1497: Virtualization/Sandbox Evasion T1083: File and Directory Discovery T1082: System Information Discovery |
| TA0009: Collection | T1056: Input Capture |
| TA0010: Exfiltration | T1041: Exfiltration over C2 Channel T1567: Exfiltration over Web Service |
| No | SHA256 Indicators | Remarks |
| 1 | 79a4605d24d32f992d8e144202e980bb6b52bf8c9925b1498a1da59e50ac51f9 | Silver RAT v1.0 Builder |
| 2 | a9fa8e14080792b67a12f682a336c0ea9ff463bbcb27955644c6fcaf80023641 | Silver RAT v1.0 Builder |
| 3 | 7a9aeea5e65a0966894710c1d9191ba4cbd6415cba5b10b3b75091237a70a5b8 | Silver RAT Payload |
| 4 | 0ace7ae35b7b44a3ec64667983ff9106df688c24b52f8fcb25729c70a00cc319 | Silver RAT Payload |
| 5 | 3b06b4aab7f6f590aeac5afb33bbe2c36191aeee724ec82e2a9661e34679af0a | Silver RAT Payload |
| 6 | 27b781269be3b0d2f16689a17245d82210f39531e3bcb88684b03ae620ac5007 | Silver RAT Payload |
| 7 | 0ace7ae35b7b44a3ec64667983ff9106df688c24b52f8fcb25729c70a00cc319 | Silver RAT Payload |
The developer of Silver RAT intends to release new versions of RAT following the leak of v1.0, which rends it freely accessible for malicious purposes. The developer, operating under the name “Anonymous Arabic,” appears is supportive of Palestine based on their Telegram posts, and members associated with this group are active across various arenas, including social media, development platforms, underground forums, and Clearnet websites, suggesting their involvement in distributing various malware. It is crucial for organizations to enhance their defense mechanisms in response to this potential threat.