



CYFIRMA researchers have recently observed similarities in two campaigns codenamed “Sixty Horses” and “Horn.” These campaigns have been monitored by CYFIRMA’s DeCYFIR platform and it revealed they have a common target industry, geography and TTPs (Tactics, Techniques, and Procedures). These two campaigns share infrastructure, malware and other indicators of compromise and attack. The N. Korean hacking group, Lazarus is suspected to be behind these activities.
Further analysis indicates there could also be a potential collaboration between Chinese and Russian cybercriminals groups. These are part of hacker-as-a-service (HaaS) and ransomware-as-a-service (RaaS) developments which are continuously evolving.
Another finding shows a Command Execution Vulnerability in NCR Command Center Agent.
A critical Command Execution Vulnerability (CVE-2021-3122) in NCR Command Center Agent has been found to have been exploited actively in the wild. Threat Actor has been seen using Living off the Land (LOLBins) including certutil to carry out malicious activities.
Based on our research and analysis, we suspect that a Chinese threat actor dubbed Rocke Group could be behind this campaign.
The primary motive of this campaign appears to be data exfiltration and financial gains.
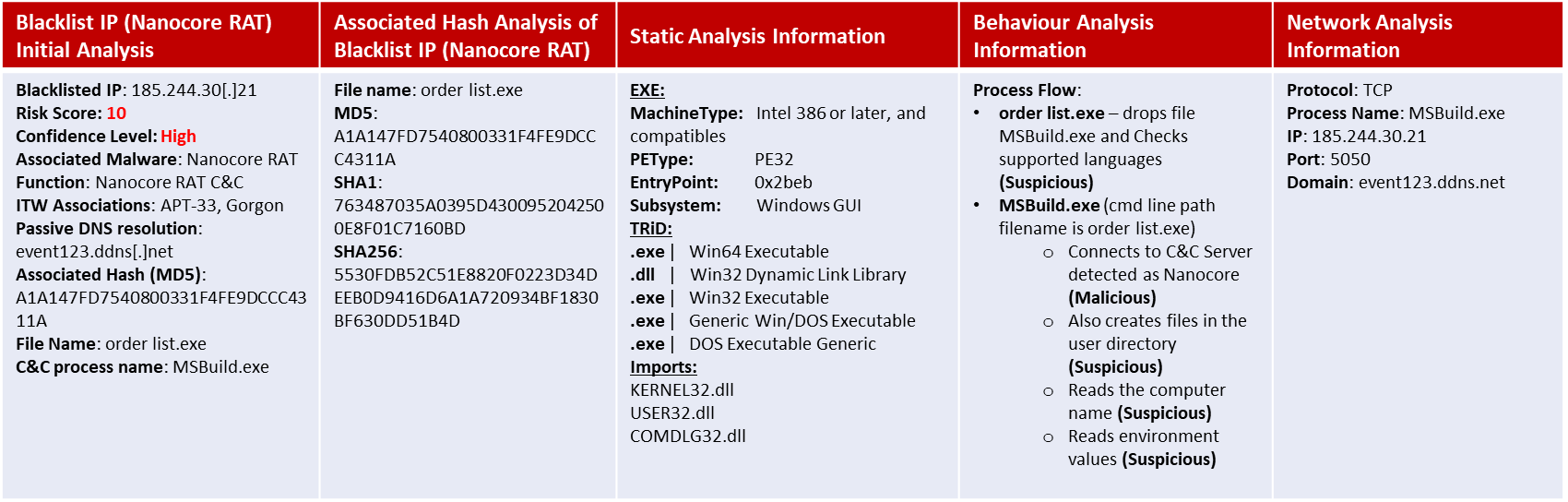
About Nanocore: NanoCore is a Remote Access Trojan (RAT). This malware is highly customizable with modular plugins which allow threat actors to modify its functionality to suit their needs. Nanocore is available for purchase for just USD25 from its “official” website. Technical details from CYFIRMA researchers are available here:
1) Vietnamese Cybersec Firm BKAV’s Source Code is Available for Sale
The attackers have hacked into their servers and have put the source code of their flagship product, BKAV Pro, up for sale.
2) 40k Gmail accounts and passwords in Vietnam are available in data leak site for sale. It includes information such as date of birth, phone number, IP address, and the operating system used.
Researchers have discovered a unique, long-running operation, called GhostEmperor. The campaign used Microsoft Exchange vulnerabilities to target high-profile victims with an advanced toolset and shown no similarity to any known threat actor. GhostEmperor is a Chinese-speaking threat actor which uses a formerly unknown Windows kernel-mode rootkit. To bypass the Windows Driver Signature Enforcement mechanism, the threat actor uses a loading scheme involving a component of an open-source project named “Cheat Engine”.
APT (Advanced Persistent Threat) actors are evolving with advances in detection and protection techniques. These threat actors typically refresh and update their toolset & tactics and GhostEmperor is one such example of how cybercriminals look for new techniques to use and new vulnerabilities to exploit.
Using a previously undocumented and sophisticated rootkit, the threat actor presents new challenges to defenders and joins the well-established trend of attacks targeting Microsoft Exchange.
Furthermore, by definition, rootkits are notoriously designed to provide continuous privileged access to the infected system while actively evading investigators and security solutions.
Researchers have recently observed the presence of a new remote access trojan (RAT) known as FatalRAT – which appears to be distributed via forums and Telegram channels – hidden in download links that attempt to lure the user via software or media articles. The malware is equipped with a wide set of capabilities that can be executed remotely by an attacker. It runs several tests before fully infecting a system including checking the existence of multiple virtual machine products, disk space, number of physical processors, and others. The malware disables users’ ability to lock the computer using CTRL+ALT+DELETE, after which the malware activates the keylogger. The malware maintains persistence either by way of modifying the registry or creating new services. Then it collects information such as external IP address, username, as well as other information from the infected machine and sends it to the Command & Control (C2) server.
Researchers highlight that the newly identified FatalRat malware uses techniques like obfuscation, anti-sandbox and antivirus evasion, encrypted configurations, logging user keystrokes, system persistence, login brute force, collection of system data, and encrypted communications with C2 server. In the past few months, multiple samples of this malware – with a slight dip in July – have been spotted. However, researchers expect to continue to see the presence of FatalRat and its variants.
In April, Telegram was increasingly used to spread ToxicEye malware. The threat actor realized that using the popular IM service as an integral part of their attacks can be very beneficial since Telegram is deemed a legitimate service and often is not blocked in enterprise environments. Further, attackers can remain anonymous and leverage their unique communications features to easily exfiltrate data or transfer new malicious files to infected machines.
Cisco recently announced that it has fixed a vulnerability in Cisco Firepower Device Manager (FDM) On-Box, which was discovered by researchers. This device manager is designed to locally configure Cisco Firepower NGFW firewalls. Tracked as CVE-2021-1518, the vulnerability is a flaw in REST API of Cisco FDM On-Box software. It would allow an authenticated remote attacker to execute arbitrary code in the operating system of an affected device.
To successfully exploit this vulnerability, the attackers need to obtain the credentials of a user with low privileges and send a specially crafted HTTP request.