



A Windows LSA Spoofing Vulnerability, CVE-2021-36942, dubbed PetitPotam was observed being exploited to distribute new ransomware tracked as LockFile. Along with this vulnerability, attackers were also using ProxyShell flaws in order to gain initial access to the target network. This file-encrypting ransomware scrambles only every alternate 16 bytes of a file, thereby giving it the ability to evade ransomware defenses.
Based on our research and analysis, few indicators were found associated with the CYFIRMA tracked campaign found in Dark Web dubbed GHlity. The campaign is suspected to be carried out by the Russian threat actor called FIN11 or affiliates. In the past, FIN11 has deployed other ransomware including CLOP, and threatened to publish exfiltrated data to pressure victims into paying the ransom demands.
The motives of the campaign appear to be Data Encryption, Defence Evasion, and Financial Gains.
Suspected Threat Actors: Black Axe
Summary
The FBI (Federal Bureau of Investigation) has arrested 33 individuals involved in cybercrime-related activities, including BEC and romance scams. The individuals are part of Black Axe – a transnational organized crime syndicate – linked to Nigeria and operate across the globe. As per the officials, the group has been active since at least 2017 carrying out a wide range of fraudulent activities including BEC, investor scams, and unemployment insurance fraud, online romance scams through site such as Match.com, ChistianMingle, JSwipe, and Plenty of Fish. As per the researchers, the group has stolen and laundered over USD17 million of funds from at least 100 victims.
Insights
Experts suggest the suspects were members of Black Axe, a known criminal syndicate linked to the Neo Black Movement (NBM). Since/ Established in 1970 to fight racism, the NBM has now evolved into a secret society, cult, and confraternity and spread across the world in recent years. As per the reports, the NBM’s Black Axe is currently believed to be involved in a range of criminal activities including cybercrimes which mainly centers around email fraud.
This is the second law enforcement crackdown against Black Axe groups’ cybercrime operations. The Italian police had, back in April 2021, also arrested 30 Black Axe members.
Summary
According to researchers, a new type of trojan sold on the dark web dubbed BloodyStealer is targeting gamer’s accounts on EA Origin, Steam, Epic Games, GOG, and other services. The malware can collect and exfiltrate a wide range of sensitive information. Researchers first observed the malware in March, advertised with capabilities of evading detection as well as protection against reverse engineering and malware analysis. The malware is available for sale in underground forums for less than USD 10 and USD 40 for one month and lifetime subscriptions respectively. The set of capabilities advertised by its developers includes:
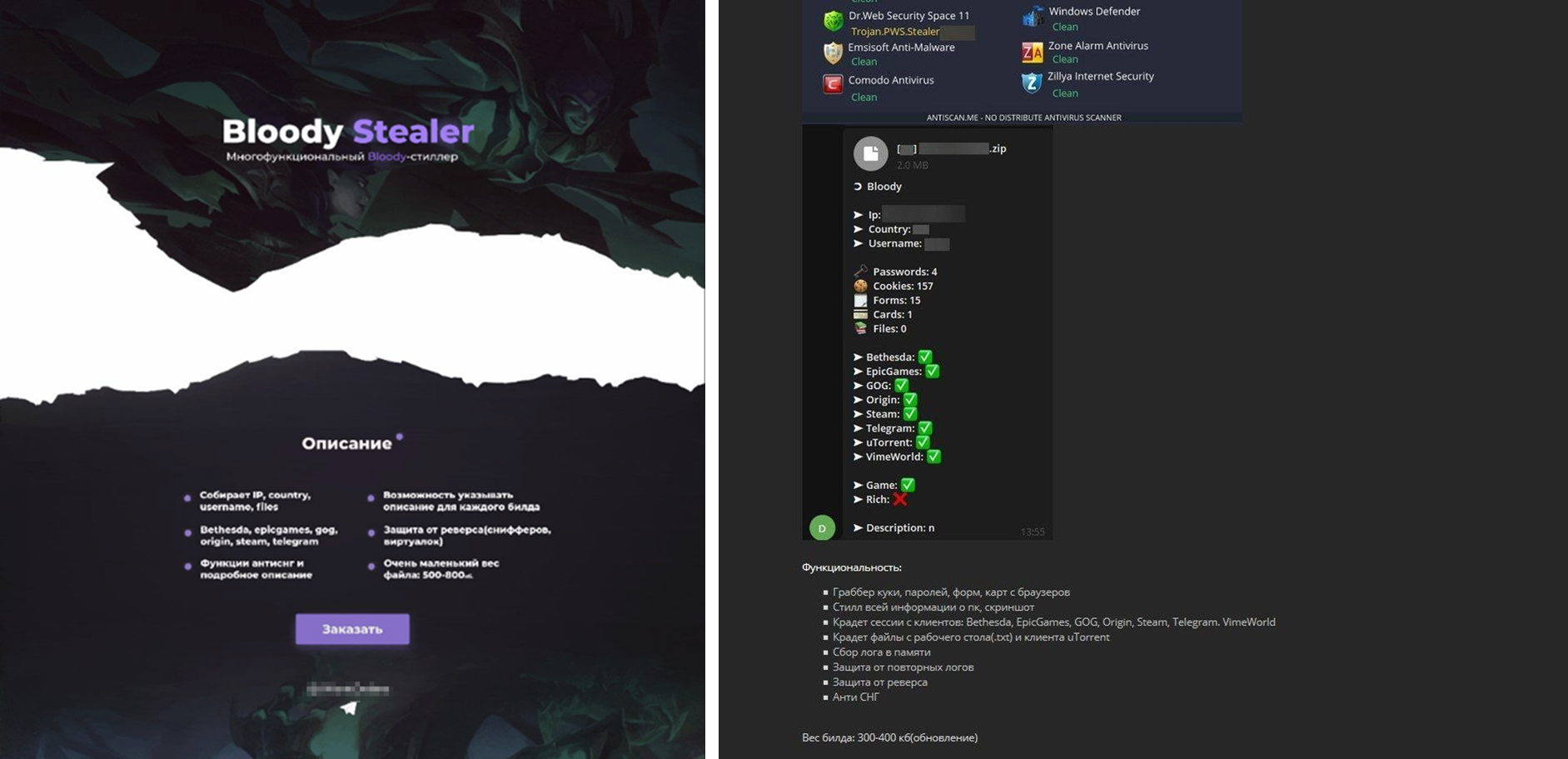
Source: Surface web
Insights
Researchers highlight that while BloodyStealer is not made exclusively for stealing game-related information, the platforms being targeted point to the demand for this type of data among cybercriminals. Logs, accounts, in-game goods, and other game-related products are sold on the darknet in bulk or individually for an attractive price.
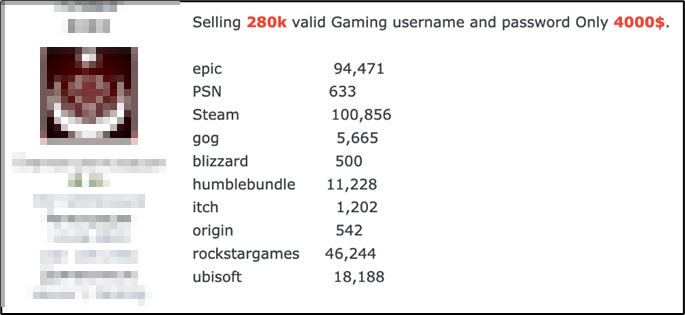
BloodyStealer is a prime example of an advanced tool used by cybercriminals to penetrate the gaming market. With its efficient anti-detection techniques and attractive pricing, researchers suspect the malware may be used in combination with other malware families soon.
Summary
The high severity bug tracked as CVE-2021-37973 is a UAF vulnerability in Portals API – a web page navigation system that helps in page transitions. The zero-day vulnerability has been reported to be actively exploited in the wild by attackers and marks the 11th zero-day exploit of the year for Google Chrome. The vulnerability was so severe that it necessitated an emergency update which was released last Friday, just days after the disclosure of vulnerability by in-house Google Threat Analysis Group (TAG) researchers.
Insights
Google has not revealed the details surrounding CVE-2021-37973, however, the vulnerability falls under the High severity ranking. Notably, the new zero-day vulnerability is yet another UAF vulnerability among 10 other similar issues disclosed in September alone. Given the timing of emergency patch, severity, and being classified as zero-day vulnerability by researchers makes it significantly more dangerous as attackers have been able to exploit the flaw before Google could release a patch.
Noticing this issue, the Cybersecurity and Infrastructure Security Agency (CISA) also issued a security advisory urging both users and system administrators to update their browsers and stated an exploit for this vulnerability exists in the wild.