



Being called one of the most ruthless and unreliable ransomware gangs by researchers, the Conti ransomware has now completed more than a year of attacking organizations. Last month, the ransomware was responsible for shutting down the entire IT infrastructure of Ireland’s healthcare system. Unlike other successful ransomware operators who are particular about their reputation, Conti is known to be unreliable after receiving the ransom.
Malspam remains the most common delivery method for Agent Tesla. The malware continues to be a consistent threat for many months and has managed to remain among the top families of malware. In the latest activity, the RAT was using COVID-19 vaccination as a lure to target Windows users. The campaign employed the most recent variant of Agent Tesla with better modules for evading detection and data theft.
sLoad (aka Starslord loader) functions as a downloader to collect and exfiltrate information from the infected systems, assess the target system, and drop a more significant payload. The malware is being actively developed and known to go through several iterations. Primary targeting Europe, the malware uses native Windows scripts such as VBS and PowerShell for an initial foothold. Recently, researchers observed SLoad infections originating from Italian endpoints which subsequently dropped Ramnit and Trickbot banking trojans.
The Joker Trojan was observed making its way on Google Play Store. The malware was spotted by researchers in 8 mobile applications which were later removed from the Play Store. The malware steals data such as SMS messages, Contact, and device information including interacting with advertisement websites and subscribing users to premium services without their knowledge.
Researchers identified a malware called LastConn distributed by Molerats (aka TA402, GazaHackerTeam). The Middle Eastern advanced persistent threat (APT) group is known to target entities in Israel and Palestine, in addition to other regions in the Middle East. The new and highly targeted campaign impacts government institutions in the Middle East and entities that have diplomatic relationships in the region. Researchers highlight that throughout the year 2021, the threat actor leveraged Middle Eastern geopolitical themes including the ongoing conflict in the Gaza Strip to carry out its operations. The threat actor used spearphishing emails containing malicious links or attachments. The activity observed in June had emails written in Arabic, containing a PDF document that embedded geofenced URLs to selectively redirect victims to a password-protected archive that contained the implant called LastConn. When first run, the malware displays a decoy document and relies on Dropbox API to download and execute files including running arbitrary commands and carrying out exfiltration back to Dropbox. Another initial access vector used Google Apps Script URLs directly inside the spearphishing email which eventually also redirected victims to password-protected archive and a decoy website based on the geofencing mechanism.
The threat actor deployed multiple mechanisms to avoid automated threat analysis including password protection and geofencing based on IP addresses. In addition, targeting systems with Arabic language packs and checking to determine the source IP address of targeted geographies, make the campaign highly targeted.
Molerats remains a highly effective and capable threat actor posing a serious threat to the government or other geopolitical entities working in the Middle East. Based on weekly activities observed, it is assessed that the threat actor is active and will continue to develop and modify customized malware implants.
A threat actor with suspected ties to Pakistan has been striking government and energy organizations in the South and Central Asia regions to deploy a remote access trojan on compromised Windows systems, according to new research.
Most of the organizations that exhibited signs of compromise were in India, and a small number were in Afghanistan. Some of the victims include a foreign government organization, a power transmission organization, and a power generation and transmission organization. The covert operation is said to have begun at least in January 2021.
The attack resulted in the victim downloading two agents; one resided in memory, while the second was side-loaded, granting threat actor persistence on the infected workstations.
The intrusions are notable for several reasons, in addition to its highly targeted nature, the tactics, techniques, and procedures (TTPs) adopted by the adversary rely on repurposed open-source code and the use of compromised domains in the same country as the targeted entity to host their malicious files.
At the same time, the group has been careful to hide their activity by modifying the registry keys, granting them the ability to surreptitiously maintain persistence on the target device without attracting attention.
American authorities seized a range of Iran’s state-linked news website domains they accused of spreading disinformation, the U.S. Justice Department said Tuesday, a move that appeared to be a far-reaching crackdown on Iranian media amid heightened tensions between the two countries.
Relations between Iran and the U.S. have deteriorated for years following former President Donald Trump’s withdrawal from Tehran’s nuclear deal and the return of devastating sanctions on the country.
The U.S. government also took over the domain name of the news website Palestine Today, which reflects the viewpoints of Gaza-based Islamic militant groups Hamas and Islamic Jihad, redirecting the site to the same takedown notice.
Most of the domains seized appeared to be “.net,” “.com” and “.tv” domains. The first two are generic top-level domains as opposed to country-specific domains, while “.tv” is owned by the Pacific Island nation of Tuvalu but administered by the U.S. company Verisign. Seizing a domain on a major country-specific top-level domain such as Iran’s “.ir” would be apt to produce widespread international condemnation as a violation of sovereignty.
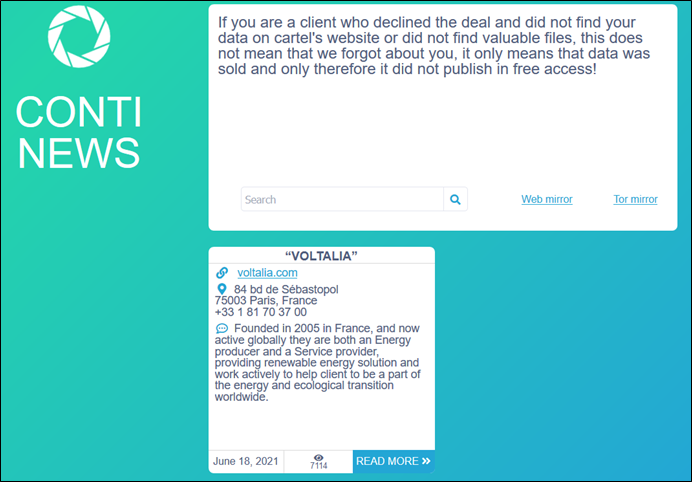
Researchers have observed Voltalia falling victim to Conti ransomware group. It is suspected that the operators have exfiltrated a large amount of business-critical and sensitive data.
Like the newly identified Lorenz group, the data is first made available for sale to potential buyers. As the ransom payment gets delayed, the ransomware operators resort to publishing parts of the data as time goes on. Ultimately, if no ransom is paid and the data is not purchased, the data is released to the public for free for anyone to download.
While most ransomware providers often put a lot of effort to establish their reputation and attempt to maintain some level of integrity to convince victims to make ransomware payments, Conti has shown atypical behavior. In recent cases, Conti did not keep up the promise of releasing decryption keys after ransom payments were received from victims.
The following screenshots was published in one of the dark web forums:
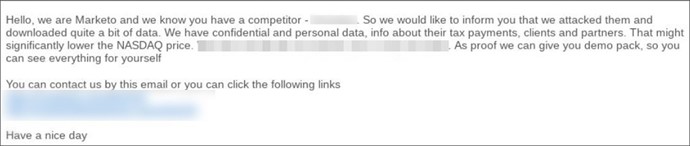
Data leak marketplaces, namely Marketo, were observed emailing competitors and offering samples of stolen data to maximize the pressure on victims. The dedicated data leak extortion marketplaces are built solely to sell stolen data from victims. The data is provided by other threat actors, collected from other ransomware or data leak sites, among other sources.
One of such marketplaces, Marketo, has started emailing victims’ competitors offering a “demo pack” of stolen data which they claimed to have breached.
The tactic of targeting victims’ competitors to extort money out of victims is not new. Like ransomware gangs, cybercriminals dealing in data leaks from both underground forums and the dark web are purely motivated by financial gains and adopt a range of extortion tactics. Notably, the Clop ransomware gang, after failing to receive ransom payments from victims also resorted to emailing competitors, journalists, and even customers with information about the cyberattack.
Further, the tactic of influencing stock prices of victim organizations has also been used by ransomware gangs. The Darkside ransomware was the first ransomware operator to put this into practice.
In a recent update, Google has addressed four security vulnerabilities, including one of the zero-day flaws that are being exploited in the wild. The critical severity flaw tracked as CVE-2021-30554 concerns a use-after-free vulnerability in WebGL (Web Graphics Library) component. A remote attacker may create a specially crafted web page, trick victims into visiting it, trigger a use-after-free error, and may execute arbitrary code on the vulnerable system. Successful exploitation of the vulnerability would allow an attacker to compromise the system. Google has acknowledged that an exploit exists for CVE-2021-30554 in the wild.
It is often the norm in such cases to limit technical details about the vulnerability until most users have updated to the latest and stable release. The update comes after just a few days of fixing another zero-day vulnerability exploited in active attacks tracked as CVE-2021-30551. CISA has also notified users and administrators to apply the necessary updates.