



Being called one of the most ruthless and unreliable ransomware gangs by researchers, the Conti ransomware has now completed more than a year of attacking organizations. Unlike other successful ransomware operators who are particular about their reputation, Conti is known to be unreliable after receiving the ransom. The ransomware group continues to remain the top ransomware, affecting multiple businesses in the past week.
Bazar Backdoor a highly sophisticated backdoor trojan alleged to be operated by UNC1878 has been observed deploying Cobalt Strike beacons post initial stages of infection. Bazar Loader has recently been detected using DNS channels to accomplish an indirect way for the malware to connect with the attackers.
An ongoing worldwide campaign is pushing new malware dubbed MosaicLoader advertising camouflaged as cracked software via search engine results to infect wannabe software pirates’ systems.
TeaBot is run-of-the-mill Trojan software in multiple ways. It contains the usual functions that any info stealing trojan could have: the ability to steal data, including banking details, keylogging, taking screenshots, intercepting two-factor authentication (2FA) codes, SMS interception, and connecting to a C2 to transfer information, accept commands, and link the infected device to a botnet.
Various databases have been uploaded into the Dark Web forums. Here’s a snapshot:
1) +83.5M Phone numbers from JAPAN Clubhouse
Clubhouse imports the contacts and phone numbers of all its users into a secret database. This allows Clubhouse to map over 3 billion phone numbers. Phone numbers starting with the Japan area code were extracted from the directories of all clubhouse users.
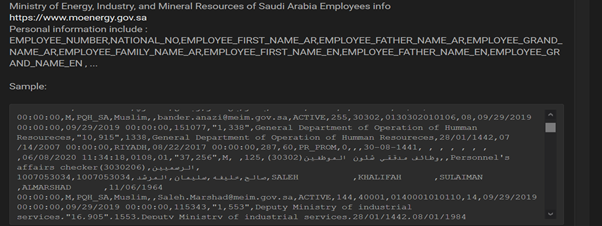
2) Saudia Arabia Ministry of Energy, Industry, and Mineral Resources.
EMPLOYEE_NUMBER,NATIONAL_NO,EMPLOYEE_FIRST_NAME_AR,EMPLOYEE_FATHER_NAME_AR,EMPLOYEE_GRAND_NAME_AR,EMPLOYEE_FAMILY_NAME_AR,EMPLOYEE_FIRST_NAME_EN,EMPLOYEE_FATHER_NAME_EN,EMPLOYEE_GRAND_NAME_EN, etc have been dumped online.
3) Russian defense contractor, Kronshtadt, documents have been hacked
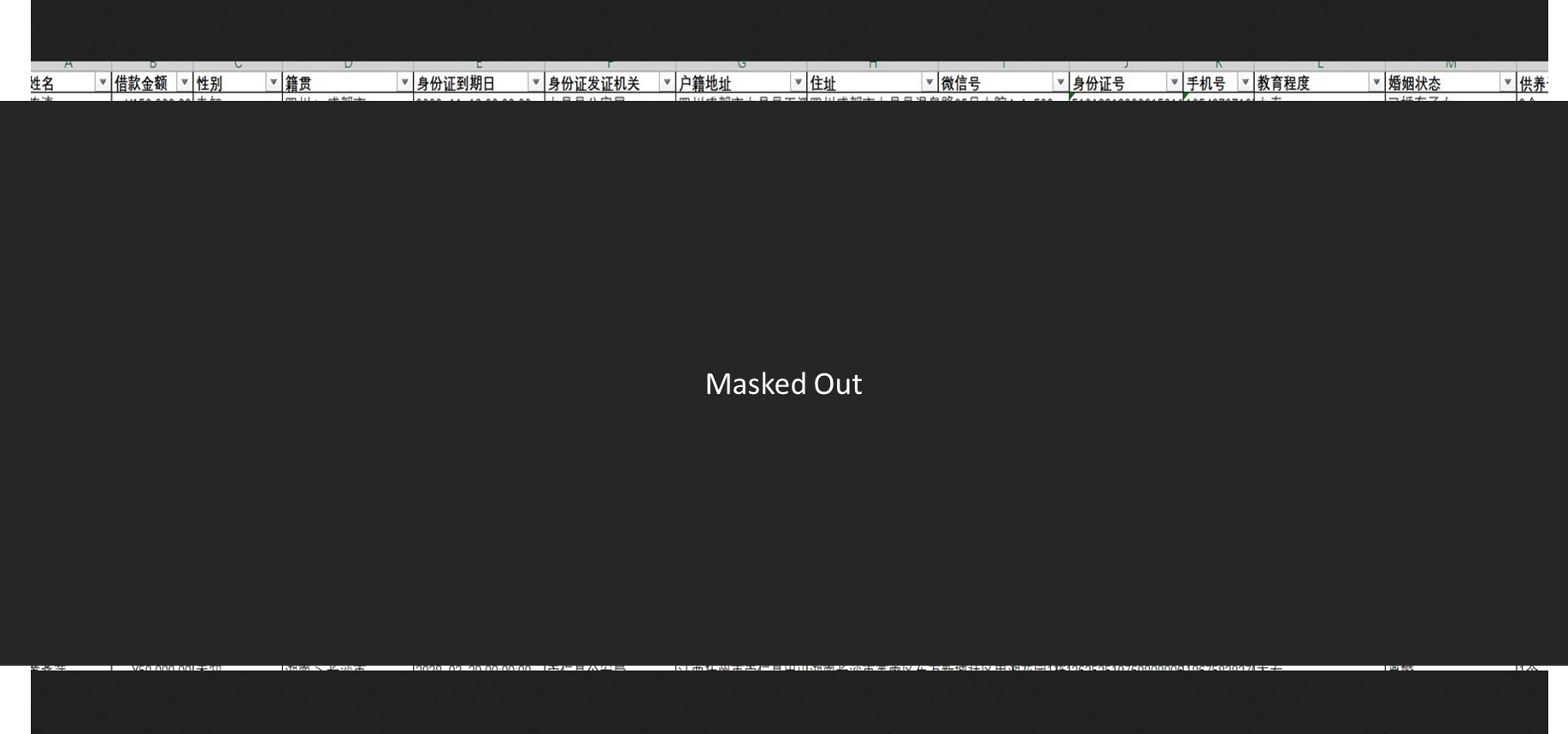
4) Loan data related to Chinese citizens has been compromised. The following data is now available in dark web marketplace:- Name, Loan Amount, Gender, Hometown, ID Card, Expiry Date, ID Card Issuing Authority, Registration Address, Home Address, WeChat ID, Phone Number, Education Level, Marital Status, Number of Dependent, Children, Residence, Type Name of Spouse, Spouse’s Mobile Number, Spouse Unit Name of Immediate Family, Members of Immediate Relations, Phone Number of Immediate Subordinates Address, unit name, department, position, current unit’s work start time, monthly payment new day, total monthly expenditure, total monthly income, working time, nature of the company.
Suspected Threat Actors: Leviathan (aka APT40)
Summary
A joint cybersecurity advisory was released by the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) providing information including TTPs and IOCs on the Chinese APT “Leviathan” to help cybersecurity practitioners. In a recent development, the U.S. Department of Justice unsealed an indictment against four APT40 threat actors for their computer network exploitation (CNE) via front company Hainan Xiandun Technology Development Company (Hainan Xiandun). The latter’s employees cooperated and carried out orders from PRC Ministry of State Security (MSS) Hainan State Security Department (HSSD) intelligence officers. The CNE activities resulted in the theft of trade secrets, intellectual property, and other high-value information from companies and organizations in the United States and abroad, as well as from multiple foreign governments.
Insights
Leviathan has used a variety of tactics and techniques including a large library of custom and open-source malware – the majority of which is shared with multiple other suspected Chinese threat actor groups. The threat actor used these malware to establish initial access via user and administrator credentials, enable lateral movement once inside the network, and locate high-value assets to exfiltrate data.
While this advisory was aimed towards providing information on APT40, the U.S. Governmental agencies have released several advisories describing malicious Chinese state-sponsored activity targeting U.S. and Allied entities including critical infrastructure organizations.
Summary
CTI observed Actiontec Electronics, Inc. – a major wireless and broadband solutions provider – impacted by the Conti ransomware. It is suspected that the operators have exfiltrated a large amount of business-critical and sensitive data. The threat actor has published approximately 33 gigabytes of suspectedly stolen data in their data leak portal on the dark web.
The following screenshots were observed published on the dark web:
Insights
The data is first made available for sale to potential buyers. As the ransom payment gets delayed the ransomware operators resort to publishing parts of the data as time goes on. Ultimately, if no ransom is paid and the data is not purchased, the data is released to the public for free for anyone to download.
While most ransomware providers often put a lot of effort to establish their reputation and attempt to maintain some level of integrity likely to encourage and facilitate ransomware payments, Conti has shown atypical behavior. In recent cases, Conti did not keep up the promise after ransom payments were received from victims.
Summary
Researchers highlight that an increasing number of ransomware groups are using virtual machines in a bid to evade detection. While encrypting files on the host computer the ransomware payload “hides” within a VM to avoid raising suspicions or triggering antivirus software.
Insights
Ransomware operators continue to refine their tactics to stay one step ahead of detection. Many ransomware groups are now heavily relying on legitimate tools to stage attacks on targeted networks. By hiding the ransomware payload in VM, it is expected that the attack may not be discovered since the ransomware payload itself is often the stage of the attack most likely to raise red flags.
The tactic also widens the scope of use of VMs to target Linux systems as well. Recently, researchers have spotted numerous Linux ELF64 versions of HelloKitty ransomware targeting ESXi servers running on Linux. The list also includes ransomware operators RansomExx/Defray, Babuk, GoGoogle, DarkSide, REvil, and Mespinoza who also have developed Linux encryptors targeting ESXi virtual machines.
Summary
The vulnerability in Juniper Networks SBR Carrier with EAP (Extensible Authentication Protocol) authentication configured, allows an attacker to send specific packets causing the radius daemon to crash resulting in Denial of Service (DoS) or leading to remote code execution (RCE). Juniper has not highlighted any malicious exploitation of this vulnerability. The vulnerability does not have a viable workaround; however, a patch has been issued by the vendor.
Insights
The bug is just one of many that the networking giant patched this week across its carrier and enterprise product lines, including several high-severity bugs that could be exploited to carry out DoS attacks. Another security flaw leading to RCE or DoS included an Out-of-bounds read vulnerability.
The CVE-2021-0276 can be exploited by attackers by continuously sending specific packets, repeatedly crashing the RADIUS daemon which may result in a sustained DoS attack.