



Suspected Threat Actors: SideWinder (aka RattleSnake)
Researchers disclosed information on a recent campaign involving SideWinder that used a slightly different technique compared to previous campaigns. In the current campaign threat actor updated DLL side-loading technique using the legit control.exe executable to load a malicious DLL aimed at decrypting and executing a final implant in memory. Researchers believe the malicious attachment propagated via spear-phishing. Based on the sample observed, the researchers were able to conclude its origin as Rawalpindi. The lure used in the document also asks for payment related to the repair of board radars on two of the Pakistani Navy ships. In the first stage, a downloaded RTF file exploits CVE-2017-11882 (RCE in Microsoft Office) vulnerability and JavaScript snippet which acts as a dropper of the next stage. The next loader stage involves the use of a DLL to collect information about the victim system, set persistence, perform evasion from anti-virus solutions, and clear previous infection tracks. The final implant consisting of a DLL file is a well-known Remote Access Trojan (RAT) including a file decryption routine used has been attributed to SideWinder.
As per researchers SideWinder is an APT-tier threat actor group and believed to be working in the interest of the Indian Government. The motivations are suspected to be driven for stealing sensitive information and carry out espionage operations against different nation-states within South Asia. The activities have been observed in operations against defense and government sectors.
Given increased tensions at a geopolitical level or political, economic, or military interests in a particular geographical area, it is possible to observe notable growth of cyber operations aimed at collecting information between parties that are directly indirectly involved.
According to researchers, India’s interest in the region has notoriously been to mitigate the effects of the strong tensions between the various countries in Central Asia and to contain Pakistan as a potential threat. Researchers assert that the motivation of the operation analyzed finds its roots in a geopolitical and strategic context.
CTI observed Link Manufacturing (Link Mfg/ www.linkmfg.com) – a producer of motor vehicle parts and accessories – being impacted by the Cuba ransomware. It is suspected that the operators have exfiltrated a large amount of business-critical and sensitive data. At the time of CTI’s observation, the threat actor has not published any sensitive data in their data leak portal on the dark web, however, they are expected to release the data.
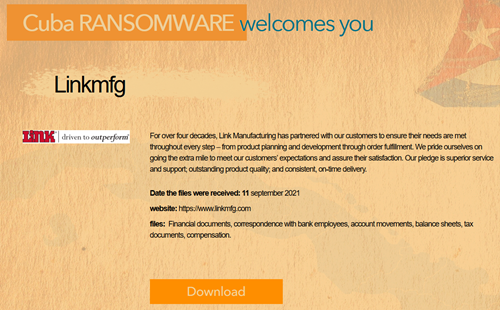

Source: Dark Web
Active since at least January 2020, the Cuba ransomware operator carry out double extortion techniques on their victims. The operators use their DLS site to publish exfiltrated data before encryption of those who refused to comply with their ransom demand. As per researchers, recently the Hancitor downloader joined Big Game Hunting and partnered with ransomware gangs to facilitate initial access to target networks. Researchers have found attackers are actively using Hancitor to deploy Cuba ransomware.
A typical Cuba ransomware kill chain involves the following:
-> Use of spam campaigns containing a link to malicious macro-laden Word documents that contains Hancitor as a payload.
-> When executed the Hancitor downloads several other additional tools via command-&-control (C2) server to aid lateral movement and data exfiltration before Cuba payload is executed on compromised systems.
-> Upon execution, Cuba terminates several SQL and Microsoft Exchange services and processes identified against a hardcoded list. Before initiating the encryption routine with a hybrid ChaCha20 and RSA encryption method and appending file extension “.cuba”, all files and directories on the compromised system are enumerated, compared against a hardcoded whitelist of files exempted from encryption.
As of the writing of this report on the current date, CTI has observed approximately 19 ransomware reported incidents affecting businesses operating in Automotive, Packaging, Legal, Furnishings, Utilities, Software, Industrial Products, Textile & Apparel, Financial Services, Aerospace & Defence Machinery, Transportation & Logistics, Real Estate, Government, Technology Services, Education, as well as the Construction industry, and spanned across multiple geographies.
Advance Fee Fraud: The Emergence of Elaborate Crypto Schemes
Researchers have disclosed an intriguing advance fee fraud scheme sending low-volume email campaigns leveraging advanced social engineering tactics to fool unsuspecting cryptocurrency users. The lures promise potential victims to withdraw hundreds of thousands of dollars worth of cryptocurrency from an already established account on a private Bitcoin investment platform. As per researchers, each email campaign is subject to hundreds of receipts worldwide and contains the same credential pairs (user ID and password) – which are subsequently changed as victims engage throughout the campaign – become unique to each victim. To entice potential victims, emails containing lures with the promise of a hefty amount of money are sent. They are prompted to login into the noted Bitcoin wallet website using the provided credentials. Immediately after the login, victims are prompted to change the password, set up recovery phone numbers, and OTP to enable additional security. Inside the website, victims are guided to take over the account from the alleged previous owner. In addition, messages from the previous owner are shown to provide reassurance that the account has been secured. The account also shows previous BTC transactions deposited and withdrawn in the past, showcasing as if the account is functional. To ensure everything works as expected the victims are required to withdraw 0.0001 BTC. Around this time, the platform prompts the victim the minimum amount to be withdrawn is 29.029 BTC – specified by the account owner at the time the account was created – meaning a transfer of at least 0.0291 BTC is be made to resolve the issue. Researchers, however, claim with high confidence the final transfer would not work, leaving victims at a loss of 0.029 BTC.
While the campaign is very similar to traditional advanced fee fraud scams, it is much more sophisticated from a technical standpoint. It is fully automated and requires extensive victim engagements.
In addition, the use of cryptocurrency is also notable due to the following reasons:
-> Anonymity is guaranteed to both the attacker and the victim. Especially the victim may find the whole setup more appealing.
-> The campaigns are aimed at tech-savvy individuals, who are likely to be skilled at handling their digital wallets.
The use of additional steps to set up a recovery phone number at the initial stage is a form of social engineering tactic to provide victims the false sense of security and intended to be a sign of legitimacy since multi-factor authentication account protection is considered one of the best security practices. Gullible users are prone to such tactics and follow along with their elaborate scams.