Published On : 2023-12-08
Ransomware of the Week
CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
Introduction
CYFIRMA Research and Advisory Team has found a ransomware strain called Xaro while monitoring various underground forums as part of our Threat Discovery Process.
Xaro:
Researchers have found a variant of the DJVU ransomware, dubbed Xaro.DJVU is a variant of the STOP ransomware, often disguised as legitimate services.
Analysis Of Attack Involving Xaro
The infection initiates when a user unknowingly downloads an archive file named “install.7z” from a deceptive website posing as a legitimate freeware distributor. Upon extraction, the user executes the file “install.exe.” This 680MB binary, falsely identified as PDF writing software, conceals its true nature. Despite an unknown public threat intelligence hash, sandbox analysis identifies it as PrivateLoader—a pay-per-install downloader. PrivateLoader, prevalent since 2021, often lurks in freeware or cracked software sites. The executable communicates with command-and-control servers in Russia, Malaysia, and Denmark. This communication leads to the download and execution of various commodity malware such as RedLine Stealer, Vidar, Lumma Stealer, Amadey, SmokeLoader, Nymaim, and, in addition to dropping Xaro.
Xaro
The initial Xaro payload was observed running on the victim machine within three minutes of the first execution of the program install.exe. The payload undergoes multiple executions, with two distinct execution flows identified.
In the first flow, the process operates under a randomly generated name, consisting of four alphanumeric characters. It initiates a child process of itself, injecting code via process hollowing before terminating. This child process establishes runtime registry keys for persistence at the location \software\microsoft\windows\currentversion\run\syshelper.Additionally, it connects to command-and-control (C2) servers.
In line with observations in other DJVU-related samples, the Xaro process employs the Windows command line utility, icalcs.exe, to restrict access for the well-known SID S-1-1-0 (representing all users in the environment). It explicitly denies access to objects in its directory, utilizing delete commands applied to itself or its child processes.
Following these actions, the Xaro process proceeds to generate instances of the Vidar infostealer and Clipbanker within the protected directory, naming them build2.exe and build3.exe. In certain instances, this activity results in the creation of a scheduled task named Azure-Update-Task, designed to execute mstsca.exe—a file commonly associated with DJVU.
Second Flow
Approximately fifteen minutes following the initial infection, the second distinct execution unfolds, giving rise to a new process with a randomly generated name consisting of four alphanumeric characters. As previously observed, this process spawns a child of itself, employing process following before terminating—presumably to introduce complexity to investigations and circumvent security measures. This child process was noted to establish a connection with the command-and-control (C2) server api[.]2ip[.]ua. In contrast to the first flow, the second flow initiates the encryption of files within the C:\Users\User directory on the affected machine, utilizing the AES-256 algorithm.
Upon completion of the encryption process, Xaro deposits its ransom note as a text file named _readme.txt.
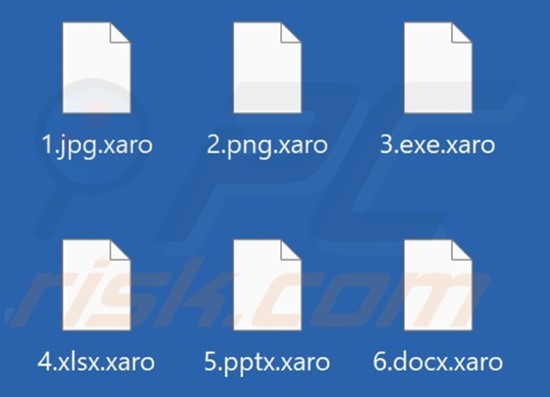
Screenshot of files encrypted by Xaro ransomware (Source: Surface web)
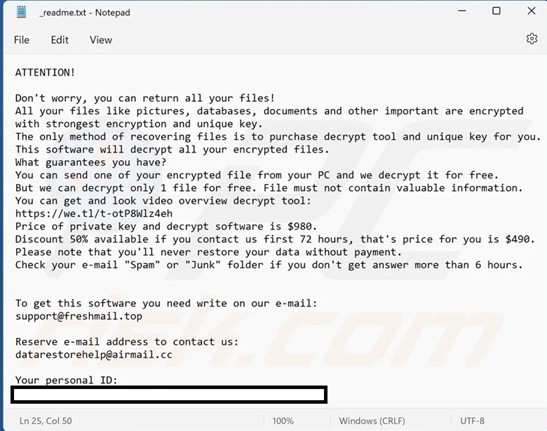
Screenshot of Xaro ransomware’s text file (Source: Surfaceweb)
Following are the TTPs based on the MITRE Attack Framework.
9TA0009: CollectionT1005: Data from Local System
T1560: Archive Collected Data
| Sr. No |
Tactics |
Techniques/ Sub-Techniques |
| 1 |
TA0002: Execution |
T1047: Windows Management Instrumentation
T1053: Scheduled Task/Job
T1106: Native API
T1129: Shared Modules |
| 3 |
TA0003: Persistence |
T1053: Scheduled Task/Job
T1547.001: Boot or Logon Autostart Execution:
Registry Run Keys / Startup Folder
T1574.010: Hijack Execution Flow: Services
File Permissions Weakness |
| 4 |
TA0004: Privilege Escalation |
T1053: Scheduled Task/Job
T1055: Process Injection
T1547.001: Boot or Logon Autostart Execution:
Registry Run Keys / Startup Folder
T1574.010: Hijack Execution Flow: Services
File Permissions Weakness |
| 5 |
TA0005: Defense Evasion |
T1027: Obfuscated Files or Information
T1027.002: Obfuscated Files or Information:
Software Packing
T1036: Masquerading
T1055: Process Injection
T1202: Indirect Command Execution
T1497: Virtualization/Sandbox Evasion
T1562.001: Impair Defenses: Disable or Modify
Tools
T1564.003: Hide Artifacts: Hidden Window
T1574.010: Hijack Execution Flow: Services
File Permissions Weakness |
| 6 |
TA0006: Credential Access |
T1003: OS Credential Dumping
T1552.002: Unsecured Credentials: Credentials
in Registry |
| 7 |
TA0007: Discovery |
T1018: Remote System Discovery
T1057: Process Discovery
T1082: System Information Discovery
T1083: File and Directory Discovery
T1497: Virtualization/Sandbox Evasion
T1518.001: Software Discovery: Security
Software Discovery |
| 10 |
TA0011: Command and Control |
T1071.001: Application Layer Protocol: Web
Protocols
T1095: Non-Application Layer Protocol
T1105: Ingress Tool Transfer
T1571: Non-Standard Port
T1573: Encrypted Channel |
| 11 |
TA0040: Impact |
T1486: Data Encrypted for Impact |
Relevancy and Insights:
- The ransomware specifically focuses on the extensively used Windows Operating System, which is widespread across a multitude of industries and organizations.
- By checking the CPU name, the ransomware can gather information about the victim’s computer hardware. This insight can help the attackers determine the system’s compatibility with specific exploit techniques or identify potential vulnerabilities to
- Detect-Debug-Environment: Debugging environments are used by developers to analyze and troubleshoot software. Ransomware that can detect debug environments may have implemented techniques to evade or disable debugging tools.
- Long sleep periods: The malware performs long sleep during execution, indicating that it may be designed to avoid detection or delay its actions on the compromised system.
- Calls to WMI: The ransomware is making calls to the Windows Management Instrumentation (WMI) framework. WMI is a powerful tool used by many legitimate applications and services, but it can also be exploited by malware to evade detection and gain access to sensitive information.
- Ransomware achieves persistence by adding a malicious executable to the registry key HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run. This manipulation ensures that the malware is automatically executed during the system startup, allowing it to maintain a presence on the infected system.
- Ransomware exploits HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree to manipulate scheduled tasks. By altering entries [in this case Time Trigger Task] within this registry key, the malware gains control over scheduled tasks, allowing it to execute malicious activities at predetermined This manipulation enhances persistence and ensures continued impact on the compromised system.
ETLM Assessment:
CYFIRMA’s assessment based on the available information suggests that Xaro ransomware may evolve to employ advanced evasion techniques, such as dynamic CPU analysis for tailored exploitation and enhanced detection avoidance. Future versions might incorporate more sophisticated anti-debugging mechanisms to thwart analysis efforts. Anticipated developments include refined sleep periods to prolong stealth and strategic usage of Windows Management Instrumentation (WMI) for increased system access. The ransomware may further diversify its persistence methods, potentially exploring new registry entries in innovative ways. Continuous adaptation to countermeasures is likely, with an emphasis on evading detection and maintaining resilience in the face of evolving cybersecurity measures.
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems. Sigma Rule:
title: Suspicious Schtasks From Env Var Folder tags:
– attack.execution
– attack.t1053.005
logsource:
product: windows
category: process_creation
detection:
selection1_create:
Image|endswith: ‘\schtasks.exe’
CommandLine|contains: ‘ /create ‘
selection1_all_folders:
CommandLine|contains:
- ‘%AppData%’
- ‘\AppData\Local\’
- ‘\AppData\Roaming\’
- ‘%Public%’
- ‘\Users\Public’
- ‘C:\Windows\Temp’
- ‘C:\Perflogs’
selection2_parent:
ParentCommandLine|endswith: ‘\svchost.exe -k netsvcs -p -s Schedule’
selection2_some_folders:
CommandLine|contains:
- ‘%Public%’
- ‘\Users\Public’
- ‘C:\Windows\Temp’
- ‘C:\Perflogs’
filter_mixed:
CommandLine|contains:
- ‘update_task.xml’
- ‘/Create /TN TVInstallRestore /TR’
- ParentCommandLine|contains: ‘unattended.ini’ filter_avira_install:
# Comment out this filter if you dont use AVIRA CommandLine|contains|all:
- ‘/Create /Xml “C:\Users\’
- ‘\AppData\Local\Temp\.CR.’
- ‘Avira_Security_Installation.xml’ filter_avira_other:
# Comment out this filter if you dont use AVIRA CommandLine|contains|all:
- ‘/Create /F /TN’
- ‘/Xml ‘
- ‘\AppData\Local\Temp\is-‘
- ‘Avira_’ CommandLine|contains:
- ‘.tmp\UpdateFallbackTask.xml’
- ‘.tmp\WatchdogServiceControlManagerTimeout.xml’
- ‘.tmp\SystrayAutostart.xml’
- ‘.tmp\MaintenanceTask.xml’ filter_klite_codec:
CommandLine|contains|all:
- ‘\AppData\Local\Temp\’
- ‘/Create /TN “klcp_update” /XML ‘
- ‘\klcp_update_task.xml’
condition: ( all of selection1* or all of selection2* ) and not 1 of filter* falsepositives:
- Benign scheduled tasks creations or executions that happen often during software installations
- Software that uses the AppData folder and scheduled tasks to update the software in the AppData folders
level: high
Source: Surface web
STRATEGIC RECOMMENDATIONS
- Implement competent security protocols and encryption, authentication, or access credentials configurations to access critical systems in your cloud and local
- Ensure that backups of critical systems are maintained which can be used to restore data in case a need arises.
MANAGEMENT RECOMMENDATIONS
- A data breach prevention plan must be developed considering, (a) the type of data being managed by the company; (b) the remediation process; (c) where and how the data is stored; (d) if there is an obligation to notify the local authority.
- Enable zero-trust architecture and multifactor authentication (MFA) to mitigate the compromise of credentials.
- Foster a culture of cybersecurity, where you encourage and invest in employee training so that security is an integral part of your organization.
TACTICAL RECOMMENDATIONS
- Update all applications/software regularly with the latest versions and security patches
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence provided.
- Add the Sigma rules for threat detection and monitoring which will help to detect anomalies in log events, identify and monitor suspicious activities.
Trending Malware of the Week
Type: Trojan
Objective: Steal Sensitive information, Monetary Deception Target Sectors: Banks
Target Technology: Android OS, Mobile banking
Target Geographies: Southeast Asia (Indonesia, Thailand, Vietnam, Singapore, and Malaysia)
Active Malware of the Week
This week “FjordPhantom” is trending.
FjordPhantom
Recently, researchers uncovered a new Android malware named FjordPhantom spreading in Southeast Asia, particularly in Indonesia, Thailand, and Vietnam, with reported activity in Singapore and Malaysia. This malware, discovered in early September, primarily utilizes messaging services to propagate and employs a combination of app-based malware and social engineering tactics to defraud banking customers.
The researchers acquired a sample of FjordPhantom from an affected end-customer’s device, revealing its focus on targeting a specific bank, although its code indicates potential capabilities to target other banking apps. Notably, FjordPhantom stands out for its use of virtualization to attack applications, a novel approach in the realm of Android banking malware. This technique, typically associated with reverse engineering, adds a layer of sophistication to the malware’s tactics. Despite efforts, additional samples of FjordPhantom and public information about the malware remain elusive, underscoring the ever-evolving nature of mobile security threats. A notable incident involves a customer being defrauded of 10 million Thai Baht (approximately $280,000) at the time of discovery.
Attack method
The FjordPhantom malware employs a multi-faceted attack method. It primarily spreads through email, SMS, and messaging apps, enticing users to download an app disguised as their bank’s legitimate application. While the downloaded app appears to be the authentic bank app, it actually runs within a virtual environment, featuring additional components that facilitate attacks on the app.
Following the download, users become targets of a social engineering attack orchestrated by an attack team, often operating from a call center. The attackers pose as bank customer service representatives, guiding users through steps to run the app. The malware allows the attackers to monitor and follow the user’s actions, enabling them to manipulate the user into performing transactions or extracting credentials. These stolen credentials can then be utilized for subsequent malicious activities, amplifying the potential impact of the attack.
FjordPhantom’s Use of Virtualization in Attacks
The malware, known as FjordPhantom, is constructed using open source/free projects available on Github. Key components include a virtualization solution and a hooking framework. Virtualization solutions, increasingly popular on Android, enable the installation and operation of apps within a virtual container. Google accepts these solutions, often available on the Google Play Store, for legitimate purposes, such as running the same app multiple times with different accounts—an operation not typically supported on Android.
In the case of FjordPhantom, the virtualization solution functions as an app capable of hosting various apps, installed into a virtual filesystem. When a hosted app is launched, the solution creates a new process, loading and launching the application. From the Android system’s viewpoint, only one app (the host) exists. However, this approach may cause issues with certain apps, as they expect to operate in specific environments. The virtualization solution heavily relies on hooking, modifying properties of the Android runtime environment, and proxying actions of hosted applications to enable normal execution within the virtualized environment. This intricate use of virtualization and hooking contributes to FjordPhantom’s unique attack methodology.
FjordPhantom’s Virtualization in Banking Attacks
FjordPhantom employs a unique virtualization approach by embedding the targeted banking app’s APK. Upon launch, it discreetly installs and runs the embedded app within a virtual container, concealing any visible traces of the virtualization process from the user. Notably, FjordPhantom autonomously invokes virtualization without the user’s knowledge, distinguishing it from previous virtualization attacks initiated by the device user. By hosting the target app in a virtual container, FjordPhantom opens avenues for multifaceted attacks. In this case, virtualization is primarily utilized to inject additional code into the hosted application’s process. This injected code comprises the actual malware and a hooking framework instrumental in the malware’s operations.
FjordPhantom’s modular design facilitates tailored attacks on various banking apps. While the analyzed malware sample targets a specific banking app, the underlying code reveals the potential to target seven other banking apps. The malware executes diverse attacks on the targeted apps, showcasing its adaptability and dynamic threat profile.
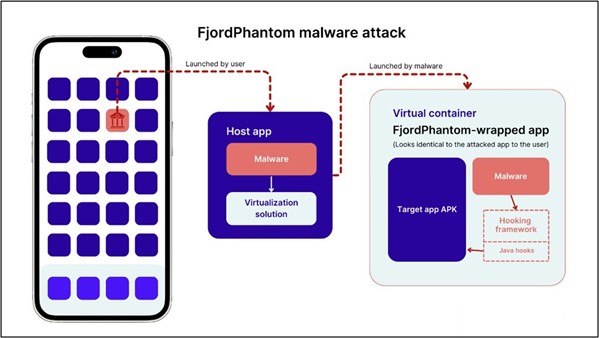
FjordPhantom’s Virtualization Breach in Android’s Sandbox
The utilization of virtualization by FjordPhantom poses a significant threat by breaking the conventional Android sandbox model. Normally, each app runs in isolation within its sandbox, but virtualization solutions enable multiple apps to operate within the same sandbox. This shared environment allows them to access each other’s files and memory, creating a favorable condition for attackers. Unlike traditional attacks requiring root access, virtualization-based attacks don’t necessitate rooting the device, making them more accessible and evading root detection measures, a common safeguard for critical apps.This ease of use has led to the popularity of virtualization solutions among attackers.
Furthermore, virtualization solutions, like the one employed by malware, can be exploited to inject code into applications. Unlike traditional methods involving repackaging, virtualization-based injection bypasses detection mechanisms since it doesn’t modify the original application. This makes FjordPhantom’s approach particularly potent in infiltrating security-critical apps, presenting a challenge for established security measures.
FjordPhantom’s Strategic Hooking Tactics in Android Attacks
FjordPhantom employs its embedded hooking framework to manipulate crucial APIs in targeted apps. By hooking into Accessibility services APIs and providing false information, the malware bypasses screenreader detection methods. This covert tactic enables attackers to utilize screenreaders to extract sensitive information from an app’s screen without the app’s awareness.
Additionally, the malware leverages its hooking framework to interfere with GooglePlayServices APIs, simulating unavailability. This deceitful tactic tricks apps into skipping SafetyNet checks commonly used to detect rooting. FjordPhantom strategically camouflages the presence of GooglePlayServices, undermining root detection mechanisms. In a more intricate approach, the malware hooks into UI functionality related to dialog boxes, automatically closing them if they contain specific text. Many of these dialog boxes warn users about potential malicious activity on their devices and are typically non-closable. By preventing users from seeing these warnings and allowing normal app usage, FjordPhantom discreetly enables further attacks without arousing suspicion.
Notably, the malware incorporates numerous hooks that log various activities of the targeted applications without altering their behavior. This likely serves as debugging functionality, indicating active development for evolving attacks on different apps.
FjordPhantom’s dynamic nature suggests ongoing development and the potential for targeting additional applications in the future.
INSIGHTS
- FjordPhantom’s strength in its modular architecture, allowing it to dynamically adapt and focus on different banking apps. This flexibility not only showcases the malware’s ability to tailor attacks to specific targets but also amplifies its potential impact, posing a versatile threat across a spectrum of financial institutions.
- FjordPhantom represents a targeted and financially motivated threat, specifically designed to exploit vulnerabilities in smartphones. This form of malicious software operates with a clear objective: stealing money by illicitly accessing banking applications. What makes it particularly insidious is its ability to deceive users, often disguising itself as enticing rewards or updates delivered through email, SMS, or messaging Once infiltrated, malware has the potential to induce significant disruptions for both end-users and financial institutions, allowing for unauthorized transactions and facilitating identity theft.
- The unique impact of FjordPhantom lies in its autonomous initiation of virtualization, embedding specific banking app APKs covertly and executing attacks seamlessly without user knowledge. The malware’s ability to inject additional code and its dynamic nature underscore its uniqueness, presenting a potent and evolving threat in the realm of Android banking malware.
ETLM ASSESSMENT
- From the ETLM perspective, CYFIRMA anticipates that FjordPhantom’s impact on organizations could evolve into a more formidable challenge. Given its sophisticated and adaptive nature, there’s a likelihood that the malware will continue to refine its tactics and expand its target scope across a broader array of banking Its autonomous initiation of virtualization and modular architecture suggest a potential for increasingly stealthy and targeted attacks. As FjordPhantom demonstrates ongoing development and the capability to inject additional code, future iterations may become even more adept at bypassing security measures, making detection and prevention more challenging. Organizations should brace for a continued and potentially heightened threat, necessitating a proactive and adaptive cybersecurity approach to counter the evolving strategies employed by FjordPhantom in the Android banking malware landscape.
STRATEGIC RECOMMENDATIONS
- Incorporate Digital Risk Protection (DRP) as part of the overall security posture to proactively defend against impersonations and phishing attacks.
- Maintain an up-to-date inventory of all active software used within the organization and perform regular self-audit of workstations, servers, laptops, mobile devices to identify unauthorized/ restricted software.
- Implement Mobile Device Management (MDM) policy to enhance corporate data security by monitoring, managing, and securing mobile devices such as laptops, smartphones, and tablets that are used in enterprises.
MANAGEMENT RECOMMENDATIONS
- Regularly reinforce awareness related to different cyberattacks using impersonated domains/spoofed webpages with end-users across the environment and emphasize the human weakness in mandatory information security training sessions.
- Provide your staff with basic cybersecurity hygiene training since many targeted attacks start with phishing or other social engineering techniques.
- Security Awareness training should be mandated for all company The training should ensure that employees:
- Avoid downloading and executing files from unverified
TACTICAL RECOMMENDATIONS
- Always listen to the research community and customer feedback when contacted about potential vulnerabilities detected in your infrastructure, or related compliance
- Use multi-factor authentication (MFA) to mitigate credential theft and prevent attacker access. Keep MFA always-on for privileged accounts and apply risk-based MFA for normal accounts.
- Enable network protection to prevent applications or users from accessing malicious domains and other malicious content on the internet.
Weekly Intelligence Trends/Advisory
Weekly Attack Type and Trends Key Intelligence Signals:
Attack Type: Malware Implant, Ransomware Attacks, Vulnerabilities & Exploits, DDoS, Data Leaks.
Objective: Unauthorized Access, Data Theft, Data Encryption, Financial Gains,
Business Impact: Data Loss, Financial Loss, Reputational Damage, Loss of Intellectual Property, Operational Disruption.
Ransomware –8Base Ransomware | Malware – FjordPhantom
8Base Ransomware – One of the ransomware
Please refer to the trending malware advisory for details on the following:
Malware – FjordPhantom
Behaviour –Most of these malwares use phishing and social engineering techniques as their initial attack vectors. Apart from these techniques, exploitation of vulnerabilities, defence evasion, and persistence tactics are being observed.
Threat Actor in Focus
Advanced Cyber Espionage Campaign: CL-STA-0002 Unveiled in Middle East, Africa and the US
- Threat Actors:CL-STA-0002
- Attack Type: Unknown
- Objective: Espionage
- Target Technology: Windows
- Target Geographies: Middle East, Africa and the S
- Target Industries: Education, Real estate, Retail, Non-profit organizations, Telecom companies & Governments
Business Impact: Data Loss, Data exfiltration
Summary:
In a recent cybersecurity study, researchers unveiled a new threat campaign orchestrated by a likely nation-state actor. This sophisticated actor has targeted a broad spectrum of sectors across the Middle East, Africa, and the United States, including government, education, real estate, retail, non-profits, and telecom companies. The actor’s distinctive tactics, techniques, and procedures (TTP) have been labelled as CL-STA-0002. The threat actor employed PowerShell snap-ins to extract data confidential emails from MS Exchange environments victim. To obfuscate their activities, they attempted to compress the extracted data into a .pst file using a command-line RAR tool.
The threat actor employed new malware tools in their campaigns. One such tool is named Agent Racoon, a .NET-based malware that establishes covert communication via DNS, utilizing a specific domain pattern. Despite lacking persistence, this malware is executed through scheduled tasks and features capabilities such as command execution, file operations, and encryption. It was first discovered in 2022.Another tool utilized by this threat actor is Ntospy. The Ntospy malware family employs a Network Provider DLL module to steal credentials during Windows authentication. It disguises itself as Microsoft Update Packages, maintains consistent file paths, and exhibits variations in code and compilation environments. Additionally, the threat actor employs Mimilite; a customized variant of Mimikatz. Mimilite is used for gathering credentials and sensitive information. It takes a decryption key as a command-line argument to decrypt its payload via a stream cipher. These tools collectively form a cluster of sophisticated and targeted cyber capabilities employed by the threat actor in their campaigns.
Relevancy & Insights:
- The observed threat actor’s behaviour is crucial for enhancing cybersecurity defences. The identification of advanced tools like Agent Raccoon and customized variants such as Mimilite provide a deep understanding of the adversary’s strategic sophistication. These might help security professionals recognize patterns, tactics, and techniques employed by threat actors, allowing for more targeted and effective defence Understanding the adept manipulation of familiar processes and exploitation of Windows authentication processes offers insights into potential vulnerabilities within an organization’s security infrastructure. This knowledge becomes a foundation for developing proactive defence measures, such as patching vulnerabilities, implementing robust access controls, and enhancing monitoring capabilities.
ETLM Assessment:
- The cybersecurity landscape evolves, with threat actors using tools like Agent Raccoon since August 2020, targeting diverse sectors. Customized versions of user-friendly tools like Ntospy and Mimikatz enable covert system compromise. As cybercriminals increasingly deploy obfuscated tools, such as Ntospy and Mimilite, the prevalence of complex multi-stage attacks is on the rise. This trend poses a significant challenge for organizations, demanding continuous enhancements in their threat detection and response capabilities. The historical context reveals a trajectory from early DLL exploits to the current sophistication of customized tools and covert communication channels. The Mimilite credential theft tool and the Agent Racoon backdoor represent contemporary threats, showcasing dynamic features and adaptability. Evolving tactics, such as disguising malware as updates and modifying source code, underscore the need for a forward-looking approach.Cyfirma assesses customized versions of Ntospy and Mimikatz, used by Cybercriminals, which will enhance their capabilities to compromise systems.
Recommendations:
- Conduct regular security audits to assess vulnerabilities and ensure that systems are resilient against evolving This includes reviewing scheduled tasks and update processes.
- Adopt a zero-trust approach to security, where no entity, whether internal or external, is trusted by default. Verify and authenticate all users and devices attempting to connect to the network.
- Promote and enforce encryption best practices, both for communication channels and file storage, to mitigate the risk of data breaches and enhance overall cybersecurity.
- Provide ongoing training for IT and security teams to stay abreast of the latest cyber threats and enhance their skills in responding to evolving attack techniques.
Indicators of Compromise
-
- Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Major Geopolitical Developments in Cybersecurity
British nuclear facility targeted by hackers
- The UK’s major nuclear fuel and waste processing facility; Sellafield, has been under acyber-attack since 2015 by actors supposedly linked to Russia and China. The first discovered attacks happened in 2015 and key personnel have repeatedly not reported the security breach to the UK nuclear regulator. The attacks were reported by national media citing sources in the British intelligence services and the nuclear watchdog ONR.
- The British government has denied that the networks at Sellafield were the victim of a successful cyber-attack by state actors. No evidence of an attack has also been seen by the nuclear authority, according to a statement. Sellafield is on the west coast of England, about 110 kilometers north of Liverpool. The site was once a nuclear power generation site, still processes spent fuel and nuclear waste, and is also home to British nuclear research. The site is also home to the world’s largest plutonium storage facility. According to the sources, experts discovered dormant malware hidden in the system in 2015 that could be used for espionage, data collection or an attack on the system and the sources suggested that foreign hackers may have accessed even the most classified information in Sellafield.
ETLM Assessment:
- While the exact scope of the attack is not clear, nuclear processing facilities as well as other critical infrastructure facilities like ports, commodity processing hubs, energy infrastructure or communications confront substantial risks from advanced threat actors. Data we have recently published on the logistics industry reveals a consistent pattern of attacks, with a clear emphasis on developed economies and major global logistics hubs. Although true that the detection of APT campaigns has declined, a correlation between the current geopolitical landscape and the most targeted countries remains evident.
EU warns member states of Russian cyber threat
- CERT-EU has warned the European Union that at least seven of the EU’s governments are being actively targeted by hackers of Russia’s military intelligence GRU. The report is singling out APT28 (also known as Fancy Bear) and its current spree of phishing campaigns using diverse decoy documents, including the meeting minutes of a subcommittee of the European Parliament and a report from a United Nations Special Committee as the bait. The warning was shortly followed by researchers reporting a spike in the group’s activity, targeting governmental organizations in Europe and North Among other methods, the group exploits the Microsoft Outlook vulnerability CVE-2023-23397.
ETLM Assessment:
-
- This recently reported activity is part of standard nation state cyber espionage efforts, with the attackers possibly trying to gain intelligence concerning next year’s EU and US elections, and possibly gain materials usable in information operations that could be used trying to influence those elections with the aim of boosting candidates deemed favourable by the Kremlin towards its long-term interests, like its war on Ukraine.
Rise in Malware/Ransomware and Phishing
GOLDMUND is Impacted by the 8Base Ransomware
- Attack Type: Ransomware
- Target Industry: Manufacturing
- Target Geography: Switzerland
- Ransomware: 8Base Ransomware
- Objective: Data Theft, Data Encryption, Financial Gains
- Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
- From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Switzerland, (www[.]goldmund [.]com), was compromised by 8Base Ransomware. Goldmund, the leading Swiss manufacturer of sound systems since 1978, offers a wide range of prestigious and high-precision home audio systems. The breached data encompasses invoices, receipts, accounting documents, personal information, certificates, employment contracts, a substantial volume of confidential data, confidentiality agreements, personal files, and other sensitive materials.
The following screenshot was observed published on the dark web:

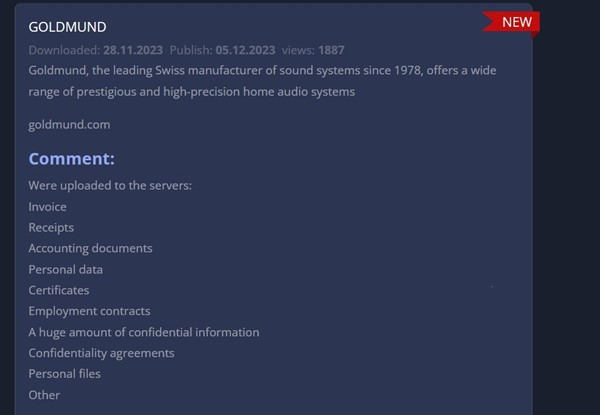
Source: Dark Web
Relevancy & Insights:
- The 8Base group’s identity, methods, and motivations largely remain a mystery. However, based on its leak site and public accounts, along with the group’s communications, researchers think the group’s verbal style is quite similar to that of RansomHouse; a group that typically purchases already compromised data or works with data leak sites to extort This has led to speculation that 8Base may be an offshoot of RansomHouse.
- We observe that the new variant used by the 8Base group includes features that can enable the attackers to establish persistence on victims’ systems, perform speedy encryption, and remove backup and shadow Furthermore, it includes advanced features, such as .NET profiler DLL loading vulnerability, API calls, and Cyrillic language, to avoid detection by security products.
- Based on the 8Base Ransomware victims list in 2023, the top 5 Target Countries are as follows:
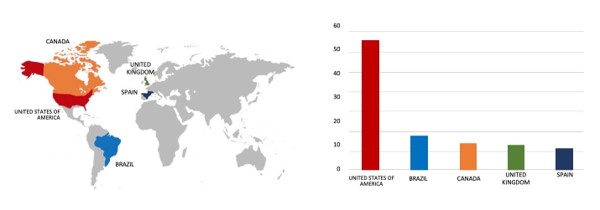
ETLM Assessment:
CYFIRMA’s evaluation reveals that the most recent iteration utilized by the 8Base group underscores the ongoing and substantial global threat that 8Base Ransomware poses to companies worldwide. The recent attack on GOLDMUND, a Swiss-based manufacturing company, serves as a stark reminder of the widespread risk associated with this specific ransomware.
Vulnerabilities and Exploits Vulnerability in MediaTek Chipset
- Attack Type: Vulnerabilities & Eploits
- Target Technology: Mobile firmware & hardware
- Vulnerability: CVE-2023-32850 (CVSS Base Score 4)
- Vulnerability Type: Integer Underflow
Summary:
The vulnerability allows a local application to execute arbitrary
Relevancy & Insights:
- In decoder, there is a possible out of bounds write due to an integer Impact:
- This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is needed for exploitation.
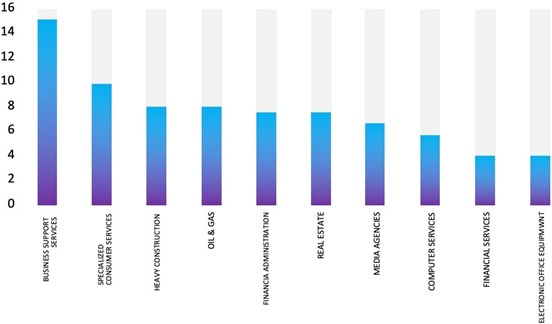
Affected Products: https[:]//corp[.]mediatek[.]com/product-security-bulletin/December-2023
Recommendations:
- Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this
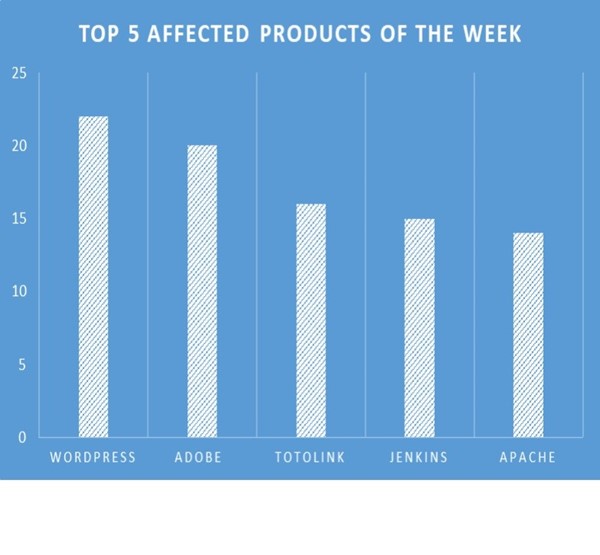
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products due to a range of vulnerabilities. The following are the top 5 most affected products.
Latest Cyber-Attacks, Incidents, and Breaches
Russian hackers exploiting Outlook bug to hijack Exchange accounts.
- Threat Actors: APT28(Fancy bear or Strontium)
- Objective: Data exfiltration
- Target Geographies: The United States, Europe, and the Middle East
- Target Industry: Government, Energy, Transportation and other critical infrastructure
- Business Impact: Operational Disruption
Summary:
- Today, Microsoft’s Threat Intelligence team issued a warning regarding the active exploitation by the Russian state-sponsored actor APT28 (also known as “Fancybear” or “Strontium”) of the CVE-2023-23397 Outlook vulnerability. This exploit is aimed at hijacking Microsoft Exchange accounts and illicitly acquiring sensitive information. The targeted entities encompass government, energy, transportation, and various essential organizations across the United States, Europe, and the Middle East. The tech giant also highlighted the exploitation of other vulnerabilities with publicly available exploits in the same attacks, including CVE-2023-38831 in WinRAR and CVE-2021-40444 in Windows MSHTML.
Relevancy & Insights:
- APT28 is a highly resourceful and adaptive threat group, the most effective defense strategy is to reduce the attack surface across all interfaces and ensure all software products are regularly updated with the latest security patches.
ETLM Assessment:
- Fancy Bear, also recognized as APT28, operates as a Russian cyber espionage group. This hacking collective leverages zero-day exploits targeting the Microsoft Windows operating system and Adobe Flash. Fancy Bear’s focal points encompass Eastern European governments and militaries, the nation of Georgia and the Caucasus, Ukraine, as well as security-related entities like NATO. In the ongoing campaign, they are actively capitalizing on the Outlook flaw CVE-2023-23397 to compromise Microsoft Exchange accounts and illicitly acquire sensitive data. According to CYFIRMA’s evaluation, the existence of the unpatched CVE-2023-23397 Outlook flaw poses a significate threat to Microsoft Exchange users in targeted areas.
Data Leaks
Prince Sultan Military Medical City (psmmc. med) Data Advertised in Leak Site
- Attack Type: Data Leaks
- Target Industry: Government
- Target Geography: Saudi Arabia
- Objective: Data Theft, Financial Gains
- Business Impact: Data Loss, Reputational Damage
Summary:
- CYFIRMA Research team observed a potential data leak related to Prince Sultan Military Medical City (psmmc. med) {www[.]psmmc[.]med[.]sa}. Prince Sultan Military Medical City (PSMMC) also known as Riyadh Armed Forces Hospital is in Riyadh City, the capital of Saudi Arabia, considered one of the most advanced centers in the Middle East. The breached data includes confidential and other sensitive information. The compromised data has a total size of 27 gigabytes.
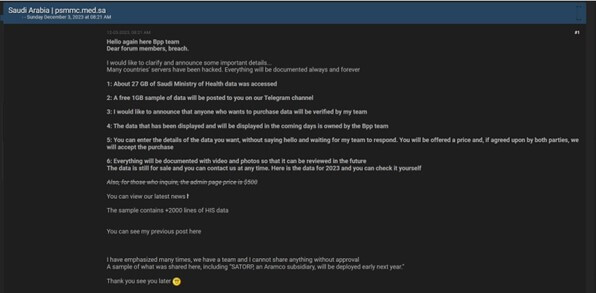
Source: Underground forums
Relevancy & Insights:
- Cybercriminals driven by financial motives and opportunistic goals actively seek outexposed and vulnerable systems and applications. Many of these attackers’ frequent underground forums where discussions revolve around buying and selling stolen digital assets. In contrast to other financially motivated groups, such as ransomware or extortion groups, who often publicize their attacks, these individuals prefer to operate discreetly. They exploit unpatched systems or vulnerabilities in applications and systems to gain unauthorized access and pilfer valuable data. The stolen data is subsequently promoted for sale within underground forums, being resold and repurposed by other attackers in their illicit activities.
ETLM Assessment:
- The Bpp team are financially motivated and claim to work “tirelessly to uncover weak protection in the security systems used by institutions and companies’” The Bpp team pose a significant to companies worldwide, and offer a service, so a customer can select a target The group exhibits refined business practices and efficiency, in their purchasing process which involves the negotiation of a price, and if mutually agreed upon, the transaction will proceed. Notably, the Bpp team underscores their commitment to transparency by documenting the entire process through video and photos, establishing a record for future reference.
Other Observations
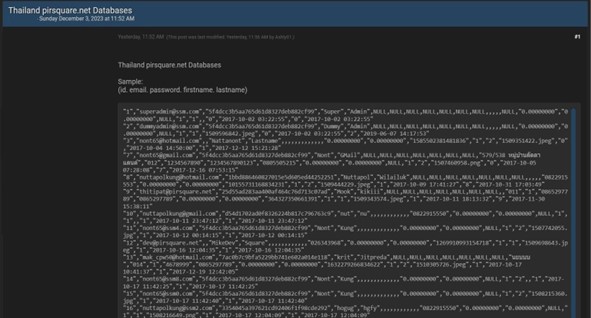
- CYFIRMA Research team observed a potential data leak related to Thailand Pi R Square, {www[.]pirsquare[.]net} Pi R Square is a software company that produces websites, e-ordering apps, game applications, and technology consultancy services. The compromised data includes identification details, email addresses, passwords, first names, last names, and other confidential information.
STRATEGIC RECOMMENDATIONS
- Attack Surface Management should be adopted by organizations, ensuring that a continuous closed-loop process is created between attack surface monitoring and security testing.
- Deploy a unified threat management strategy – including malware detection, deep learning neural networks, and anti-exploit technology – combined with vulnerability and risk mitigation processes.
- Incorporate Digital Risk Protection (DRP) in the overall security posture that acts as a proactive defence against external threats targeting unsuspecting customers.
- Implement a holistic security strategy that includes controls for attack surface reduction, effective patch management, active network monitoring, through next generation security solutions and ready to go incident response plan.
- Create risk-based vulnerability management with deep knowledge about each asset. Assign a triaged risk score based on the type of vulnerability and criticality of the asset to help ensure that the most severe and dangerous vulnerabilities are dealt with first.
MANAGEMENT RECOMMENDATIONS
- Take advantage of global Cyber Intelligence providing valuable insights on threat actor activity, detection, and mitigation techniques.
- Proactively monitor the effectiveness of risk-based information security strategy, the security controls applied and the proper implementation of security technologies, followed by corrective actions remediations, and lessons learned.
- Move beyond the traditional model of security awareness towards improved simulation and training exercises that mimic real attack scenarios, account for behaviours that lead to a compromised, and are measured against real attacks the organization
- Consider implementing Network Traffic Analysis (NTA) and Network Detection and Response (NDR) security systems to compensate for the shortcoming of EDR and SIEM solutions.
- Detection processes are tested to ensure awareness of anomalous Timely communication of anomalies and continuously evolved to keep up with refined ransomware threats.
TACTICAL RECOMMENDATIONS
-
- Patch software/applications as soon as updates are available. Where feasible, automated remediation should be deployed since vulnerabilities are one of the top attack vectors.
- Consider using security automation to speed up threat detection, improved incident response, increased the visibility of security metrics, and rapid execution of security
-
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthen defences based on tactical intelligence provided.
- Deploy detection technologies that are behavioural anomaly-based to detect ransomware attacks and help to take appropriate measures.
- Implement a combination of security control such as reCAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart), Device fingerprinting, IP backlisting, Rate-limiting, and Account lockout to thwart automated brute-force attacks.
- Ensure email and web content filtering uses real-time blocklists, reputation services, and other similar mechanisms to avoid accepting content from known and potentially malicious sources.













