


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows
Target Countries: Japan, USA, Germany
Target Industry: Financial Services, Employment Services, Media
Introduction
CYFIRMA Research and Advisory Team has found KaWaLocker Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
KaWaLocker Ransomware
Researchers have recently uncovered a new ransomware variant dubbed KaWaLocker, once infiltrated into a victim’s system, KaWaLocker quickly encrypts various file types and appends a randomly generated character string to each filename, making it difficult to identify or recover the original files. In affected directory, the ransomware drops a ransom note titled “!!Restore-My-file-Kavva.txt”, providing instructions on steps to be followed for ransom payment and gaining access to the data.
Screenshot of files encrypted by ransomware (Source: Surface Web)
The ransom note informs victims that their network has been compromised and files encrypted. It states that sensitive data such as manufacturing details, service credentials, customer and employee information, and financial records have been exfiltrated. Victims are threatened with data leaks on the dark web if demands are not met and warned that modifying the locked files or using third-party decryption tools can render them undecryptable. The ransom note cautions them against reaching out to law enforcement agencies.
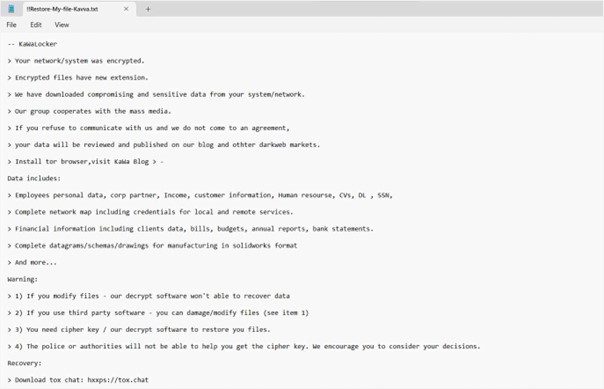
The appearance of KaWaLocker’s ransom note (““!!Restore-My-file-Kavva.txt “) (Source: Surface Web)
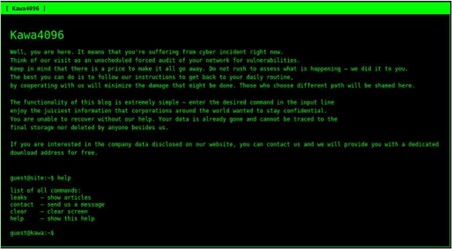
Screenshot of KaWaLocker’s Tor network website (Source: Surface Web)
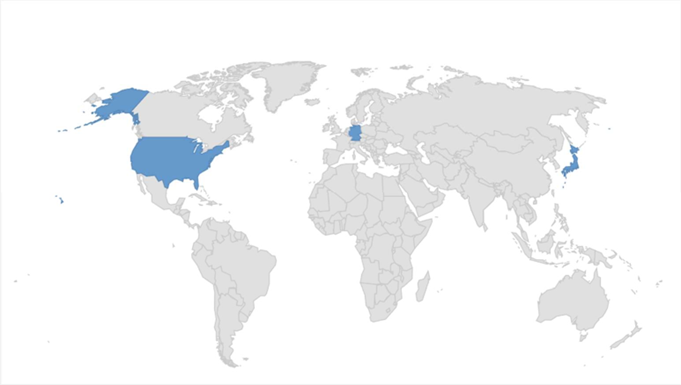
Targeted countries by Ransomware
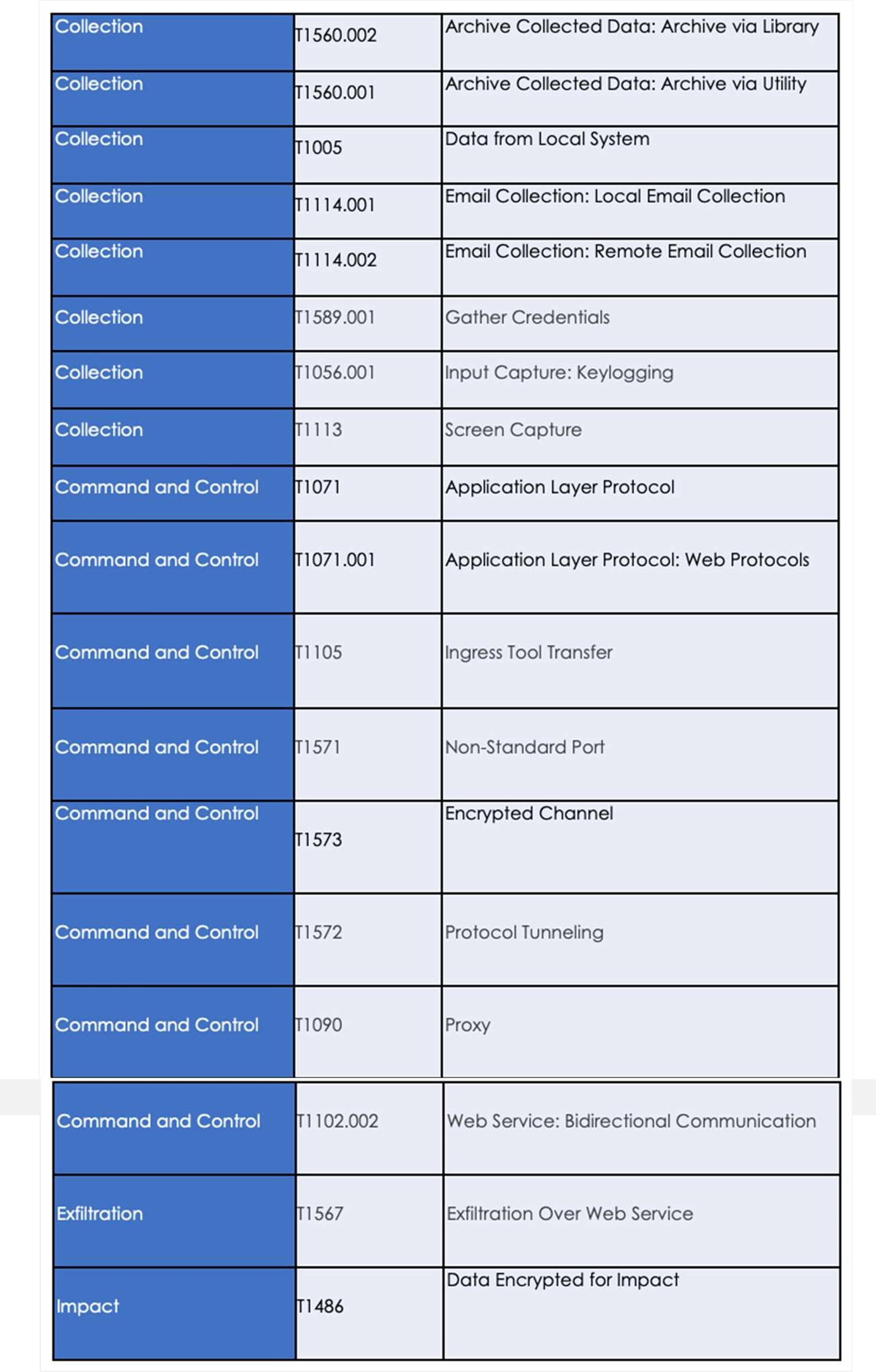
Following are the TTPs based on the MITRE Attack Framework
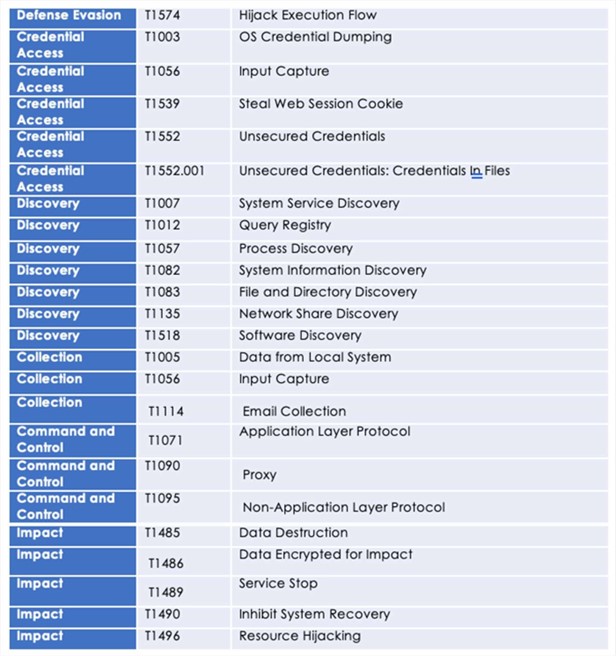
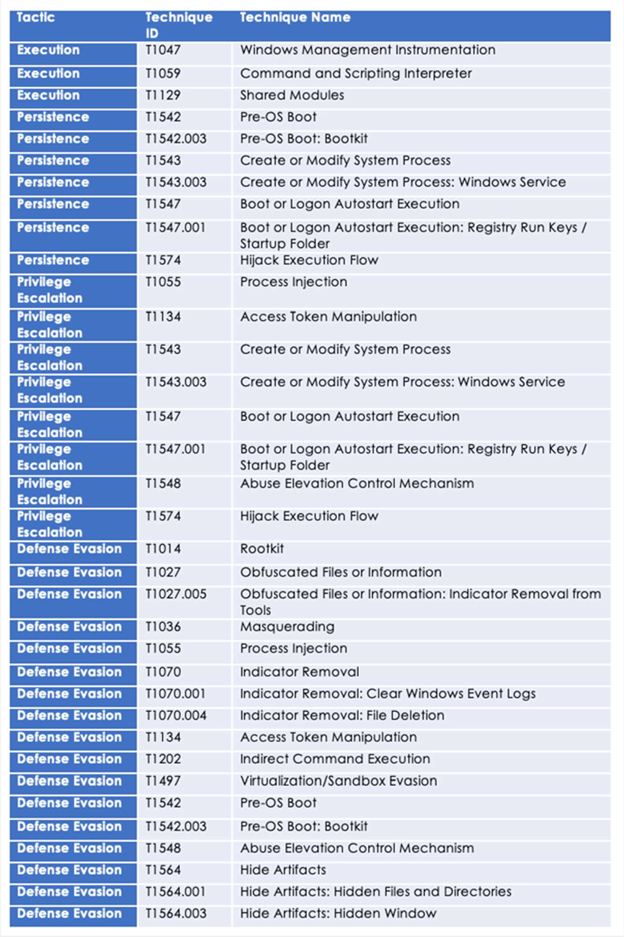
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s analysis of KaWaLocker, based on available data, indicates that it is emerging as a significant ransomware threat, particularly to high-value sectors such as Financial Services, Employment Services, Media, and other data-sensitive industries. While current activity has been observed in Japan, the United States, and Germany, its targeting behavior suggests likely expansion into additional regions especially those with critical infrastructure and valuable data assets. KaWaLocker’s deployment of both encryption and data exfiltration aligns with the growing trend of dual-impact extortion campaigns. Organizations in vital sectors are advised to enhance their cybersecurity readiness.
Sigma rule:
title: Shadow Copies Deletion Using Operating Systems Utilities
tags:
-defense-evasion
-impact
-t1070
-attack.t1490
logsource:
category: process_creation
product: windows
selection1_img:
-Image|endswith:
-‘\powershell.exe’
-‘\pwsh.exe’
-‘\wmic.exe’
-‘\vssadmin.exe’
-‘\diskshadow.exe’
OriginalFileName:
-‘PowerShell.EXE’
-‘pwsh.dll’
-‘wmic.exe’
-‘VSSADMIN.EXE’
-‘diskshadow.exe’
selection1_cli:
CommandLine|contains|all:
-‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
-‘delete’
selection2_img:
-Image|endswith: ‘\wbadmin.exe’
-OriginalFileName: ‘WBADMIN.EXE’
selection2_cli:
CommandLine|contains|all:
-‘delete’
-‘catalog’
-‘quiet’ # will match -quiet or /quiet selection3_img:
-Image|endswith: ‘\vssadmin.exe’
-OriginalFileName: ‘VSSADMIN.EXE’
selection3_cli:
CommandLine|contains|all:
-‘resize’
‘shadowstorage’
CommandLine|contains:
‘unbounded’
‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) fields:
-CommandLine
-ParentCommandLine
falsepositives:
-Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
-LANDesk LDClient Ivanti-PSModule (PS EncodedCommand)
level: high
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION:
MANAGEMENT RECOMMENDATION:
TACTICAL RECOMMENDATION:
Type: Information Stealer| Objectives: Stealing Sensitive Information, Data Exfiltration| Threat Actor: UAC-0226| Target Technologies: Windows OS, Browsers | Target Geography: Ukraine | Target Industries: Military, Law Enforcement Agencies, Government
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “GIFTEDCROOK” is trending.
About Malware GIFTEDCROOK
Researchers have identified that the cyber-espionage group UAC-0226 has significantly advanced its operations by evolving its malware, GIFTEDCROOK, from a simple browser- focused infostealer into a sophisticated intelligence-gathering tool. Developed in C/C++, GIFTEDCROOK is distributed through deceptive emails containing malicious Excel attachments. The latest versions are equipped with advanced evasion techniques to bypass traditional security measures without detection. Once executed, the malware rapidly extracts sensitive information, including credentials, browser sessions, cookies, and remote desktop configurations. This progression has positioned GIFTEDCROOK as a notable threat in recent campaigns, highlighting the increasing precision and complexity of modern cyber-espionage operations.
About Threat Actor UAC-0226
UAC-0226 is an espionage-focused threat group that targets Ukraine’s military and government sectors through tailored phishing campaigns, often using weaponized Excel files as initial entry points. UAC-0226 relies on two custom components: a reverse shell built on the .NET framework that incorporates adapted PowerShell scripts from publicly available code, and GIFTEDCROOK, a malware strain that captures sensitive browser information. This data is packaged using PowerShell scripts and discreetly sent through Telegram. To enhance delivery and evade detection, the group frequently hijacks legitimate webmail accounts, a tactic that underscores the value of closely monitoring email infrastructure. Despite using tools with modest technical complexity, UAC-0226 demonstrates a sharp focus on espionage goals, aligning with activity commonly attributed to nation-backed operations.
Attack Method Leveraged
The GIFTEDCROOK malware campaign begins with a targeted spear-phishing approach. Attackers send deceptive emails that appear to originate from legitimate locations within Ukraine, specifically spoofed to resemble official communications from Ukrainian-controlled cities. These emails often contain malicious PDF attachments disguised as urgent notices—often related to military obligations—prompting recipients to follow embedded links.
The links lead to a well-known cloud storage platform, where victims are tricked into downloading a malicious document. The document is designed to mislead the recipient into manually enabling macros by displaying distorted or unreadable content, creating a false impression that activation is necessary to view the information properly. Once macros are enabled, the document triggers the execution of a hidden malware payload.
The implant silently scans the system for files based on specific criteria such as type, size, and date of modification. It collects a wide range of sensitive data, including documents, spreadsheets, images, VPN configurations, and browser credentials from Chrome, Edge, and Firefox. The harvested files are compressed, encrypted, and split if needed before being exfiltrated via private Telegram channels. Finally, the malware erases itself from the system to eliminate forensic traces, ensuring the operation remains undetected.
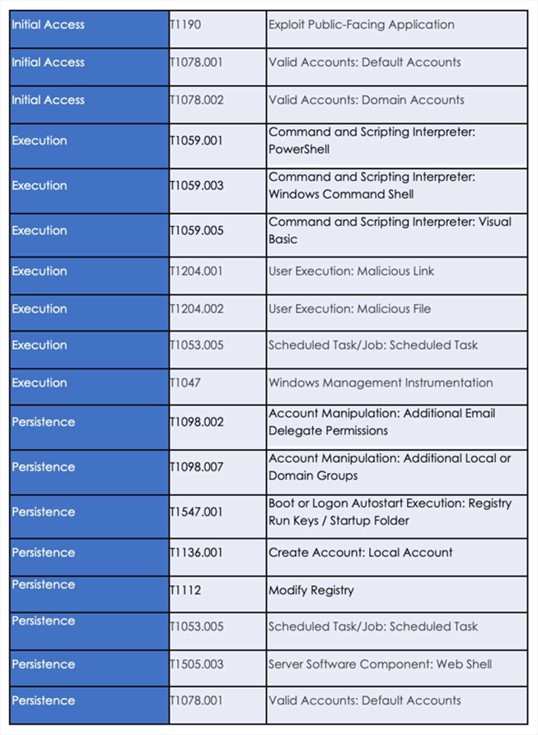
Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Initial Access | T1566.002 | Phishing: Spearphishing Link |
| Execution | T1203 | Exploitation for Client Execution |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Privilege Escalation | T1055 | Process Injection |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Credential Access | T1003 | OS Credential Dumping |
| Discovery | T1012 | Query Registry |
| Discovery | T1082 | System Information Discovery |
|
Command and Control |
T1071 |
Application Layer Protocol |
|
Command and Control |
T1095 |
Non-Application Layer Protocol |
|
Command and Control |
T1573 |
Encrypted Channel |
| Impact | T1485 | Data Destruction |
| Impact | T1496 | Resource Hijacking |
INSIGHTS:
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that as cyber-espionage malware like GIFTEDCROOK continue to evolve, their impact is poised to extend far beyond targeted organizations—reshaping digital trust, geopolitical dynamics, and everyday online interactions. As these attacks increasingly mimic official formats and exploit widely used platforms for delivery, users across society may grow more skeptical of routine online communications, including government notices, service updates, or shared documents. This erosion of trust could lead to slower digital adoption in critical sectors or reduce the effectiveness of genuine public outreach efforts. Additionally, we may see geopolitical tensions more frequently mirrored in cyberspace, where malware like GIFTEDCROOK becomes a tool for silent influence. Cyber operations could evolve into a preferred method for shaping narratives, gathering leverage, or destabilizing environments—without overt military engagement. These quieter, persistent digital intrusions could become standard features in international disputes, creating long-term uncertainty in both regional and global affairs. Finally, the continued success of these operations may prompt a shift in how public cloud services, file-sharing platforms, and communication tools are viewed. As threat actors abuse these trusted services to stage and deliver malicious content, there could be growing pressure on platform providers to implement stricter content validation or access controls, potentially reshaping how the internet functions for everyday users.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rule
rule GIFTEDCROOK_Infostealer
{meta:
description = “Detects GIFTEDCROOK Infostealer based on known strings and behaviors”
author = “CYFIRMA” date = “2025-07-01”
malware_family = “GIFTEDCROOK” threat_type = “Infostealer”
reference = “Internal Analysis / OSINT” strings:
$s1 = “GIFTEDCROOK” wide ascii
$s2 = “Crypto Wallets Found:” ascii
$s3 = “Collected browser credentials” ascii
$s4 = “Discord Token Grabber” ascii
$s5 = “System Information Collected” ascii
$s6 = “https://api.ipify.org” ascii
$s7 = “AppData\\Local\\Temp\\giftedcrook” wide
$s8 = “Mozilla\\Firefox\\Profiles” wide
$s9 = “Chrome\\User Data\\Default\\Login Data” wide condition:
uint16(0) == 0x5A4D and
(1 of ($s*) or all of ($s1, $s2, $s3))
}
STRATEGIC:
Management:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Tracking Educated Manticore: Alias of Charming Kitten/APT35
About the Threat Actor
Educated Manticore, also known as Charming Kitten, APT35, or Mint Sandstorm, is an Iranian state-sponsored threat actor active since at least 2014 and continuing operations through 2025. Researchers classified the group as a nation-state-based advanced persistent threat in December 2017, despite its lack of sophistication. It maintains close affiliations with Iran’s Islamic Revolutionary Guard Corps (IRGC) and demonstrates infrastructure and tactical overlaps with other Iranian threat clusters, including Rocket Kitten, Newscaster, NewsBeef, ITG18, and APT42.
Following are the TTPs based on the MITRE Attack Framework
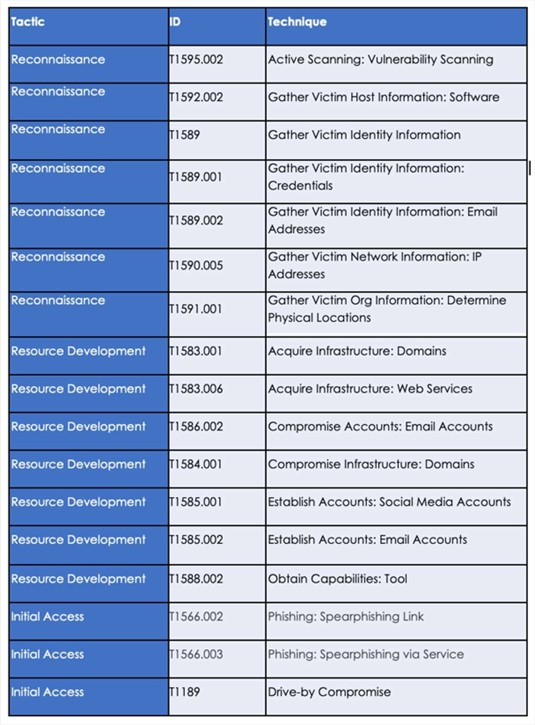
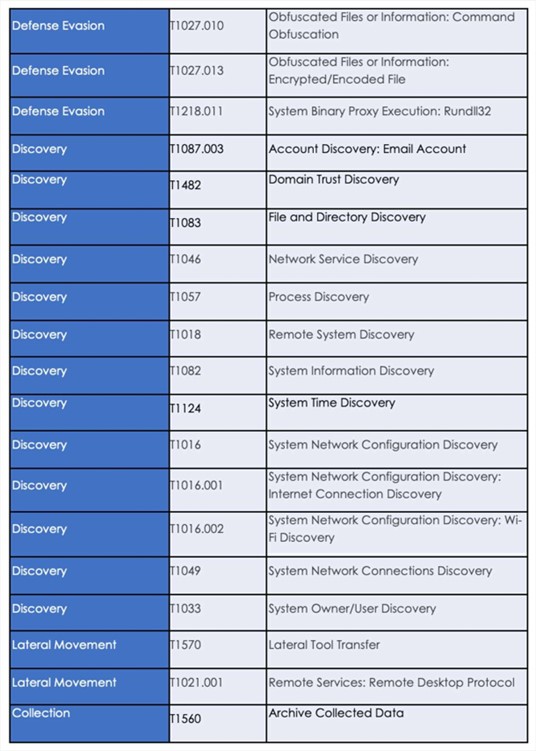
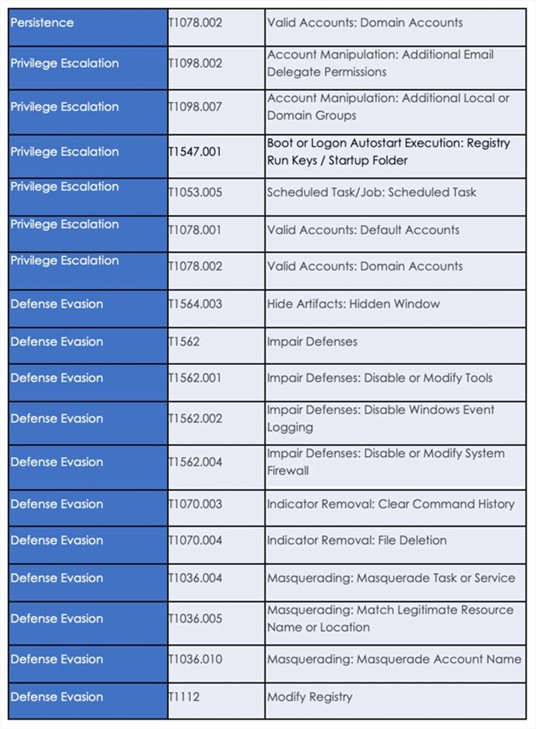
Latest Developments Observed
The threat actor is suspected of carrying out spear-phishing campaigns targeting Israeli journalists, prominent cyber security experts, and computer science professors from leading Israeli universities. Posing as fictitious assistants to technology executives or researchers, the threat actors are leveraging platforms such as Google emails/meet and WhatsApp messages. The motive appears to be credential harvesting, specifically capturing passwords and two-factor authentication (2FA) codes, and gaining unauthorized access to the victims’ accounts for espionage activities.
ETLM Insights
The threat actor and its affiliates are believed to be linked to Iran’s Islamic Revolutionary Guard Corps (IRGC), a highly influential entity that plays a central role in the country’s internal security, economic interests, and projection of power. The IRGC operates under the direct authority of Iran’s Supreme Leader.
This threat group primarily engages in cyberattacks and espionage operations targeting entities perceived as adversaries of Iran, executing highly targeted and strategic campaigns globally. Notably, the group is known to share its infrastructure with other domestic and international threat actors, indicating a collaborative approach aimed at amplifying the reach and impact of its operations.
Over time, the group has significantly advanced its tactics, techniques, and procedures (TTPs), positioning itself as one of the most prominent cyber threat entities within Iran. Its operations often involve multi-stage payloads and prolonged attack chains designed to evade detection, leveraging obfuscation and disguise to maintain persistence within compromised environments.
IOCs
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
YARA Rules
rule EducatedManticore_CharmingKitten_Generic
{
meta:
description = “Detects malware or artifacts linked to Educated Manticore / Charming Kitten (APT35)”
author = “CYFIRMA” date = “2025-07-01”
actor = “Educated Manticore / Charming Kitten / APT35” strings:
$s1 = “powershell -nop -w hidden -enc” ascii
$s2 = “System.Net.WebClient” ascii
$s3 = “Invoke-WebRequest” ascii
$s4 = “C:\\Users\\Public\\Documents\\BellaCiao.ps1” wide
$s5 = “New Document.docm” ascii
$s6 = “APT35_Phishing_Kitten” ascii
$s7 = “IranianHackers2020″ ascii wide condition:
uint16(0) == 0x5A4D and 3 of ($s*)
}
rule EducatedManticore_NetworkInfrastructure_Detection
{
meta:
description = ” Detects network infrastructure artifacts associated with Charming Kitten (APT35/Mint Sandstorm) operations ”
author = “CYFIRMA” date = “2025-07-01”
threat_actor = “Educated Manticore / Charming Kitten / APT35 / Mint Sandstorm”
confidence = “High”
strings:
// IP addresses
$ip1 = “185.130.226.71”
$ip2 = “45.12.2.158”
$ip3 = “45.143.166.230”
$ip4 = “91.222.173.141”
$ip5 = “194.11.226.9”
$ip6 = “195.66.213.132”
$ip7 = “146.19.254.238”
$ip8 = “194.11.226.29”
$ip9 = “194.11.226.46”
$ip10 = “194.61.120.185”
$ip11 = “2.56.126.230”
$ip12 = “194.11.226.5”
// Domains
$d1 = “conn-ectionor.cfd”
$d2 = “optio-nalynk.online”
$d3 = “ques-tion-ing.xyz”
$d4 = “sendly-ink.shop”
$d5 = “shaer-likn.store”
$d6 = “alison624.online”
$d7 = “bestshopu.online”
$d8 = “black-friday-store.online”
$d9 = “idea-home.online”
$d10 = “book-handwrite.online”
$d11 = “world-shop.online”
$d12 = “lenan-rex.online”
$d13 = “first-course.online”
$d14 = “reading-course.online”
$d15 = “make-house.online”
$d16 = “est5090.online”
$d17 = “zra-roll.online”
$d18 = “tomas-company.online”
$d19 = “clame-rade.online”
$d20 = “dmn-for-hall.online”
$d21 = “word-course.online”
$d22 = “clothes-show.online”
$d23 = “expressmarket.online”
$d24 = “loads-ideas.online”
$d25 = “sky-writer.online”
$d26 = “becker624.online”
$d27 = “adams-cooling.online”
$d28 = “stadium-fresh.online”
$d29 = “royalsoul.online”
$d30 = “live-message.online”
$d31 = “teammate-live.online”
$d32 = “wood-house.online”
$d33 = “ude-final.online”
$d34 = “city-splash.online”
$d35 = “door-black-meter.online”
$d36 = “prt-max.online”
$d37 = “albert-company.online”
$d38 = “human-fly900.online”
$d39 = “dmn-for-car.online”
$d40 = “good-student.online”
$d41 = “goods-companies.online”
$d42 = “pnl-worth.online”
$d43 = “ricardo-mell.online”
$d44 = “live-coaching.online”
$d45 = “wer-d.info”
$d46 = “spring-club.info”
$d47 = “all-for-city.info”
$d48 = “beta-man.info”
$d49 = “amg-car-ger.info”
$d50 = “cc-newton.info”
$d51 = “steve-brown.info”
$d52 = “connect-room.online”
$d53 = “live-gml.online”
$d54 = “roland-cc.online”
$d55 = “exir-juice.online”
$d56 = “yamal-group.online”
$d57 = “live-conn.online”
$d58 = “online-room.online”
$d59 = “platinum-cnt.info”
$d60 = “crysus-h.info”
$d61 = “lynda-tricks.online”
$d62 = “message-live.online”
$d63 = “white-life-bl.info”
$d64 = “meet-work.info”
$d65 = “prj-ph.info”
$d66 = “hrd-dmn.info”
$d67 = “ntp-clock-h.info”
$d68 = “work-meeting.info”
$d69 = “ph-crtdomain.info”
$d70 = “nsim-ph.info”
$d71 = “warning-d.info”
$d72 = “live-meet.cloud”
$d73 = “live-meet.blog”
$d74 = “live-meet.info”
$d75 = “live-meet.cfd”
$d76 = “live-meet.live”
$d77 = “network-show.online”
$d78 = “redirect-review.online”
$d79 = “arizonaclub.me”
$d80 = “backback.info”
$d81 = “cloth-model.blog”
$d82 = “cook-tips.info”
$d83 = “network-review.xyz”
$d84 = “socks.beauty”
$d85 = “gallery-shop.online”
$d86 = “network-game.xyz”
$d87 = “good-news.cfd”
$d88 = “network-show-a.online”
$d89 = “panel-network.online”
$d90 = “panel-redirect.online”
$d91 = “encryption-redirect.online”
$d92 = “thomas-mark.xyz”
$d93 = “rap-art.info”
$d94 = “anna-blog.info”
$d95 = “arrow-click.info”
$d96 = “best85best.online”
$d97 = “shadow-network.best”
$d98 = “good-news.fashion”
$d99 = “warplogic.pro”
$d100 = “cyberlattice.pro”
$d101 = “show-verify.xyz”
$d102 = “top-game.online”
$d103 = “suite-moral.info”
$d104 = “nice-goods.online”
$d105 = “crysus-p.info”
$d106 = “wash-less.online”
$d107 = “ptr-cc.online”
$d108 = “white-car.online”
$d109 = “live-content.online”
$d110 = “bracs-lion.online”
$d111 = “storm-wave.online”
$d112 = “course-math.info”
$d113 = “food-tips-blog.online”
$d114 = “white-life.info”
$d115 = “ph-work.info”
$d116 = “normal-dmn.info”
$d117 = “panel-meeting.info”
$d118 = “prj-pa.info”
$d119 = “ntp-clock-p.info”
$d120 = “nsim-pa.info”
$d121 = “pa-crtdomain.info”
$d122 = “infinit-world.info”
$d123 = “alex-mendez-fire.info”
$d124 = “reg-d.info”
$d125 = “everything-here.info”
$d126 = “healthy-lifestyle.fit”
$d127 = “alpha-man.info”
$d128 = “lesson-first.info”
$d129 = “master-club.info” condition:
any of ($ip*) or any of ($d*)
}
Recommendations:
Strategic
Management
Tactical
3. MAJOR GEOPOLITICAL DEVELOPMENTS IN CYBERSECURITY
Canada Bans China’s Surveillance Maker Over National Security Risks
The Canadian government has banned Chinese surveillance equipment maker Hikvision from operating in the country due to national security concerns. In an official statement, Canada’s Ministry of Innovation announced that following a National Security Review, the Government of Canada has ordered Hikvision Canada, Inc. to cease all operations and shut down its Canadian business as the government has determined that Hikvision’s continued presence would be harmful to Canada’s national security.
The government is also prohibiting all federal departments, agencies, and crown corporations from purchasing or using Hikvision products. Additionally, authorities are reviewing existing installations to ensure legacy Hikvision equipment is removed.
ETLM Assessment:
The company is partly owned by the Chinese government, and under China’s 2017 National Intelligence Law, Chinese firms are legally required to cooperate with intelligence agencies if asked. This means that even if Hikvision claims to operate independently, it could be compelled to share data or grant access to its equipment without disclosure.
Although there is no publicly confirmed evidence showing China has used Hikvision cameras for espionage in other countries, authorities view the risk as significant. Hikvision devices have a history of serious security vulnerabilities, including a critical flaw discovered in 2021 that allowed attackers to remotely take control of cameras. These weaknesses could potentially be exploited for surveillance or cyberattacks targeting sensitive Canadian networks.
Canada’s decision also reflects broader concerns about how the Chinese government uses Hikvision technology for domestic surveillance, particularly in regions such as Xinjiang, where cameras are deployed to monitor and track populations. This connection reinforces the perception that Hikvision is closely tied to China’s security apparatus.
By banning Hikvision and ordering the removal of its equipment from government networks, Canada is aligning with allies like the United States, the United Kingdom, and Australia, which have already imposed similar restrictions. Even without direct evidence of exploitation, the combination of Chinese state ownership, mandatory cooperation with Chinese intelligence, a track record of security flaws, and the company’s role in domestic surveillance led Canadian authorities to conclude that continuing to allow Hikvision devices posed an unacceptable risk to national security.
CISA warns of potential threats from Iran
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is urging organizations to remain alert for potential Iranian cyberattacks amid rising geopolitical tensions. In a joint advisory with the FBI, NSA, and Department of Defense Cyber Crime Center (DC3), CISA warned that Iranian-linked cyber actors could soon target U.S. networks and devices.
“Given the current geopolitical environment, Iranian-affiliated cyber actors may conduct near-term cyber operations against U.S. organizations,” the advisory stated. Companies in the Defense Industrial Base (DIB), especially those connected to Israeli defense and research firms, face heightened risk. Previously, hacktivists and groups tied to the Iranian government frequently exploited poorly secured U.S. networks and internet-connected devices to carry out disruptive attacks, as exemplified by the attacks on water utilities in the US during the previous tensions.
ETLM Assessment:
As the dust settles over the initial hot stage of the war between Israel and Iran, a parallel cyber conflict is unfolding—one that was previously largely overshadowed by the spectacle of missile strikes and air raids. Yet this digital battlefield is just as strategically significant. Both nations are using cyber operations to sabotage infrastructure, disrupt military planning, and undermine financial networks. While the physical war dominates headlines so far, the cyber war may prove more enduring, with long-term impacts on critical systems and civilian life that are less visible but strongly contributing to the efforts of both nations.
Iran’s cyberattacks have yielded mixed results, often with exaggerated or fabricated impacts to heighten psychological effects. Overhyping these incidents risks amplifying the attackers’ influence. Still, individual businesses could face serious consequences and should adopt ransomware prevention measures to mitigate risks.
Ukrainian Hackers Steal Data Related to Russian Electronic Warfare
Tens of gigabytes of secret data on Russia’s strategic electronic warfare systems has been hacked by the pro-Ukrainian hacker group. The hackers announced that they have obtained a large quantity of data on Russia’s EW systems, including technical specifications, diagrams, official correspondence, equipment setup methods, drawings, test reports, and functional information.
“We got more than just the external appearance. We see the internal logic, architecture, connections between nodes, we know who designed it, which companies supplied the units, which research institutes are responsible for the developments. … We received a number of important military developments along with protocols, engineering solutions and approvals from the Russian Ministry of Defence. In addition, we managed to establish the entire chain of enterprises involved in production and supply. … And it is also important that all the persons involved in the development and creation of these stations were identified. Upon completion of the operation, the RDK had their names, addresses, car numbers, places of work.”
The hacked documents also reveal that Russia exploits China’s satellites, apparently without China’s knowledge, as Russia uses civilian Chinese satellites to cover the calibration of its systems.
ETLM Assessment:
Russia has invested heavily in its EW systems to compensate for its relative lack of satellites, compared to the United States or China. The leak is likely to be a considerable setback, as it will enable Ukraine’s Western partners to develop effective countermeasures to Russia’s electronic warfare, which will effectively mean an important fusion of cyber and kinetic capabilities on the battlefield and further technological falling behind by Russia, which proved to be increasingly vulnerable to Western tech.
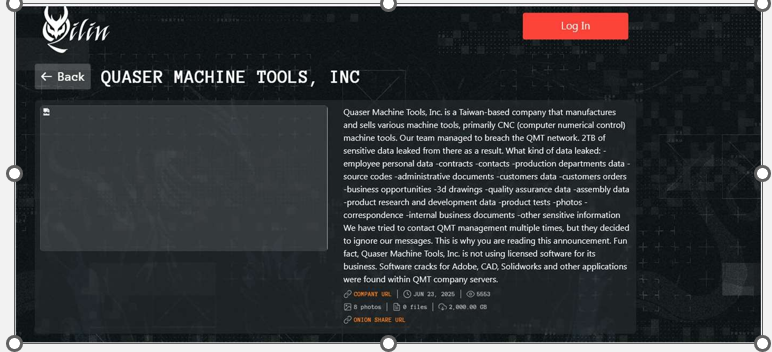
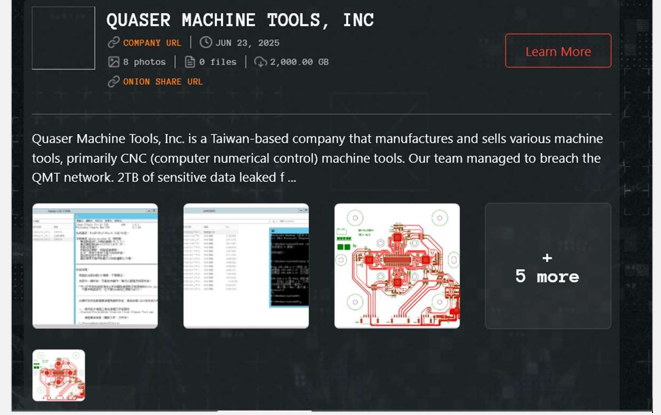
Qilin Ransomware Impacts the Quaser Machine Tools, Inc
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Taiwan, Quaser Machine Tools, Inc (https[:]//www[.]quaser[.]com/), was compromised by Qilin Ransomware. Quaser Machine Tools, Inc. is a Taiwan-based company that manufactures and sells various machine tools, primarily CNC (computer numerical control) machine tools. The compromised data includes employee personal information, employment contracts, contact details, production department records, source code, administrative documents, customer information, customer orders, business opportunity details, 3D drawings, quality assurance records, assembly data, product research and development files, product testing data, photographs, correspondence, internal business documents, and other sensitive information. The total volume of exposed data is approximately 2 terabytes.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and focus on speed and evasion, make it a particularly dangerous actor.
Lynx Ransomware Impacts Siamgas and Petrochemicals Public Company Ltd
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Thailand; Siamgas and Petrochemicals Public Company Ltd (https[:]//www[.]siamgas[.]com/), was compromised by Lynx Ransomware. Siamgas and Petrochemicals Public Company Ltd is a leading LPG distributor in Thailand and East Asia. The company operates in five countries: Thailand, China, Singapore, Malaysia, and Vietnam. The compromised data consists of confidential and sensitive information related to the organization.

Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Lynx ransomware has emerged as a significant threat in the cybersecurity landscape, leveraging advanced encryption and double extortion tactics to target small and medium-sized businesses. Its structured affiliate program and versatile ransomware toolkit make it a formidable force in the RaaS ecosystem.
Vulnerability in Zhiyuan OA
Relevancy & Insights: The vulnerability exists due to an input validation error when processing directory traversal sequences in the wpsAssistServlet interface.
Impact: A remote attacker can upload arbitrary files onto the system.
Affected Products:
https[:]//service[.]seeyon[.]com/patchtools/tp.html#/patchList?type=%E5%AE%89 %E5%85%A8%E8%A1%A5%E4%B8%81&id=1
Recommendations:
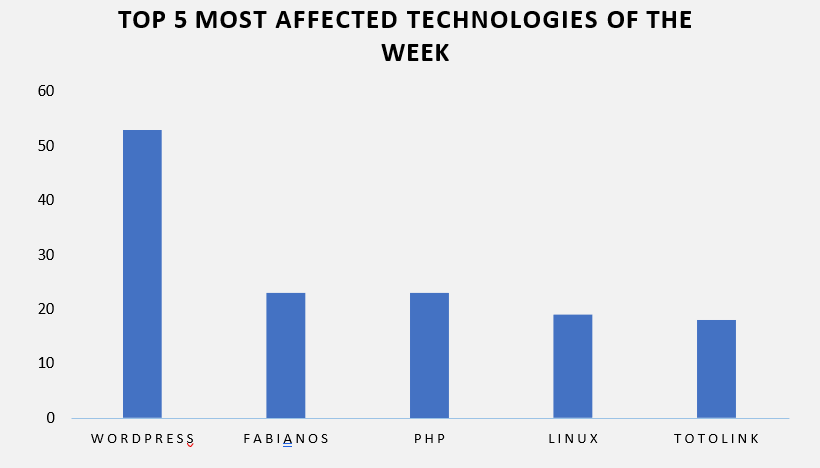
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment:
Vulnerability in the Zhiyuan OA platform can pose significant threats to user privacy and security. This can impact various industries globally, including government, education, healthcare, and enterprise sectors. Ensuring the security of the Zhiyuan OA platform is crucial for maintaining the integrity and protection of sensitive organizational data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding internal communication, workflow automation, and administrative operations across different geographic regions and sectors.
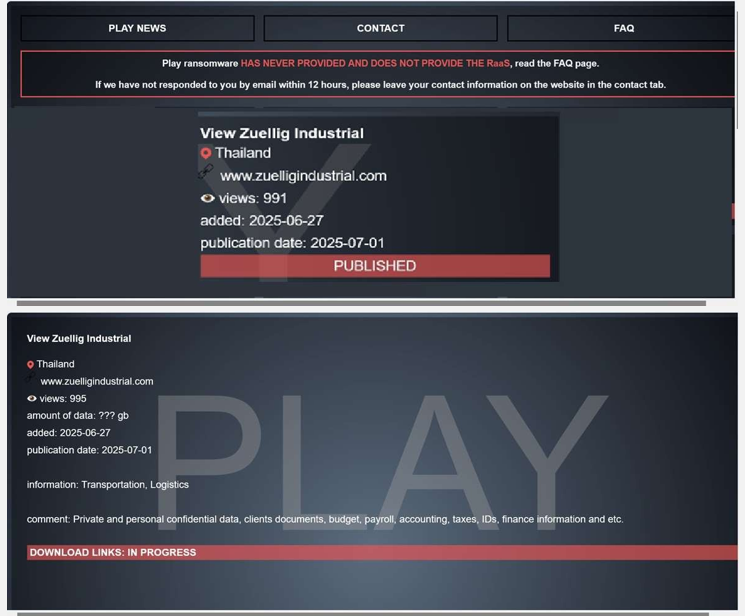
Play Ransomware attacked and published the data of the View Zuellig Industrial
Summary:
Recently, we observed that Play Ransomware attacked and published the data of the View Zuellig Industrial(www[.]zuelligindustrial[.]com) on its dark web website.
Zuellig Industrial is a leading B2B company based in Bangkok, Thailand, specializing in transportation, logistics, supply chain management, and storage solutions across the Asia-Pacific region. The company is focused on the marketing, sales, and distribution of technical products and value-added industrial solutions. Its portfolio includes automation and control systems, water treatment technologies, industrial chemicals, technical equipment, tools, and specialized solutions for the personal care and food industries. The data leak, following the ransomware attack, encompasses private and personal confidential data, clients’ documents, budget, payroll, accounting, taxes, IDs, finance information, etc.
Relevancy & Insights:
Recently, we observed a new Play ransomware variant targeting VMware ESXi virtual machines, marking the first Linux-based Play ransomware. The variant detects ESXi environments, shuts down virtual machines, and encrypts VM disks, configuration files, and metadata, appending the .PLAY extension to encrypted files. Ransom notes are left in root directories and displayed on ESXi login portals, increasing pressure on victims to pay.
ETLM Assessment:
According to CYFIRMA’s assessment, Play Ransomware continues to evolve as a significant threat within the cybersecurity landscape, marked by its innovative tactics and recent collaborations with other threat actors. Organizations are advised to enhance their cybersecurity measures by implementing robust defenses against phishing attacks, maintaining updated security protocols, and monitoring for unusual network activity to mitigate risks associated with this evolving threat actor. Continuous vigilance is essential as ransomware groups adapt their strategies and expand their operations.
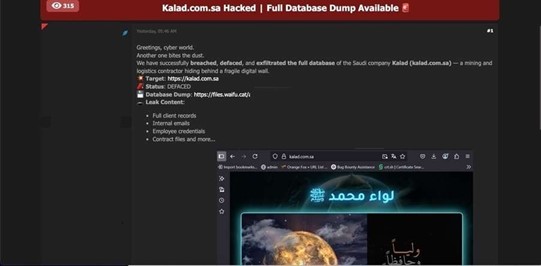
Saudi Mining & Logistics Firm Kalad’s Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data leak related to Saudi Mining & Logistics Firm Kalad(https://kalad[.]com.sa/) in an underground forum. A threat actor has allegedly breached Kalad, a company described as a mining and logistics contractor in Saudi Arabia. In a post on a cybercrime forum, the hacker claimed to have not only exfiltrated the company’s entire database but also defaced its official website, kalad[.]com[.]sa. The post included a screenshot of the defaced homepage as proof of the intrusion.
Kalad is allegedly a contractor in Saudi Arabia’s vital mining and logistics sector. Companies in this industry play a significant role in the Kingdom’s supply chain and economic infrastructure, making them potentially high-value targets for cyberattacks. The successful breach of such an entity could expose sensitive operational and commercial data, impacting its clients and business continuity.
The threat actor advertised a full database dump for download, which allegedly contains a wide range of sensitive information. The attacker also claimed the breach was accomplished using a “Zero-Day exploit.” The compromised data allegedly includes:
Source: Underground Forums
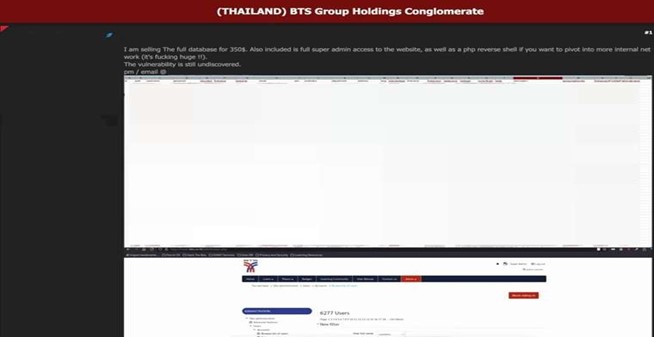
Thai Conglomerate BTS Group Holdings Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that a threat actor, “ByteToBreach”, has breached BTS Group Holdings, a major Thai conglomerate, and is offering stolen data for sale on a well-known hacking forum. The attacker claims to possess the complete database from ewet[.]bts[.]co[.]th, believed to be the company’s internal training or learning management portal. The dataset is being sold for $350, with the seller also offering “super admin” access to the site and a PHP reverse shell, potentially enabling deeper access into BTS Group’s internal network.
BTS Group Holdings plays a vital role in Thailand’s economy, primarily known for operating the BTS Skytrain and Bangkok BRT systems. The company also has substantial investments in media, real estate, and various service sectors, making it an attractive target for cybercriminals.
According to the leaked screenshots, the compromised system contains records for 6,277 users, with the exposed data allegedly including a broad range of personally identifiable information (PII). This information could be exploited for phishing attacks, identity theft, and other malicious purposes.
The threat actor provided screenshots showing the website’s administration panel and a large spreadsheet containing user data. An analysis of the images indicates the following information has allegedly been compromised:
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data.
Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor known as “ByteToBreach” has recently emerged as a highly active group specializing in data leaks. Verified reports link the group to multiple breaches involving unauthorized system access and the sale of stolen data on dark web marketplaces.
ByteToBreach’s ongoing activity highlights the evolving and persistent nature of cyber threats originating from the dark web. These incidents underscore the urgent need for organizations to strengthen their cybersecurity posture through continuous monitoring, effective use of threat intelligence, and proactive security measures to protect critical information assets.
Recommendations:
Enhance the cybersecurity posture by:
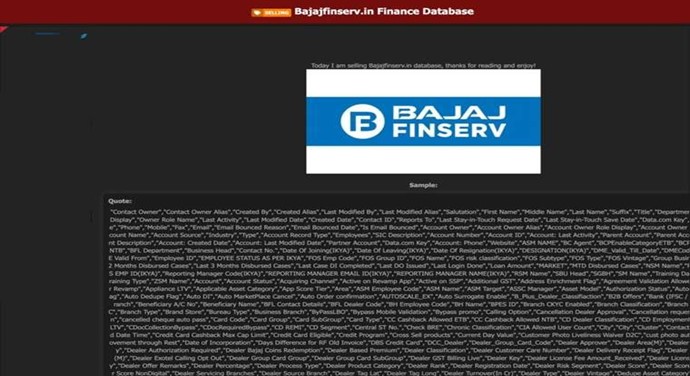
The CYFIRMA Research team observed that a threat actor has allegedly put the financial and personal data of Indian conglomerate Bajaj Finserv’s customers and employees up for sale on a dark web forum. Bajaj Finserv is a prominent non- banking financial services company in India, offering a vast portfolio of products, including loans, insurance, and wealth management to over 100 million customers. A breach of this magnitude could have significant consequences for the individuals whose data has been compromised.
The seller on the forum claims to possess a database containing information on 207,000 unique users. To substantiate their claim, the actor shared a sample of the data, which appears to contain an extensive amount of sensitive information. The potential leak includes a wide range of personal, financial, and internal company data, which could be exploited by malicious actors for phishing campaigns, identity theft, and other fraudulent activities. The scale and detail of the allegedly leaked information underscore the critical importance of robust cybersecurity measures for financial institutions.
The data, which is being sold for an undisclosed amount in Monero (XMR), allegedly includes numerous fields of customer and internal information. The exposure of such comprehensive data could lead to significant financial and reputational damage for the company and pose a serious privacy risk to its customers and employees.
While the company has not yet publicly addressed the alleged incident, the situation highlights the persistent threats facing large corporations that handle sensitive data.
Some of the allegedly leaked data points include:
Source: Underground Forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
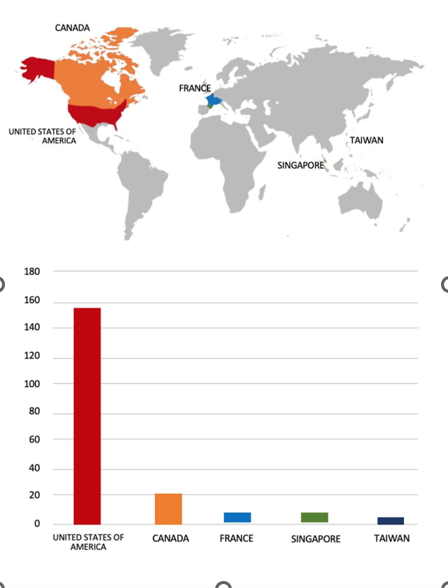
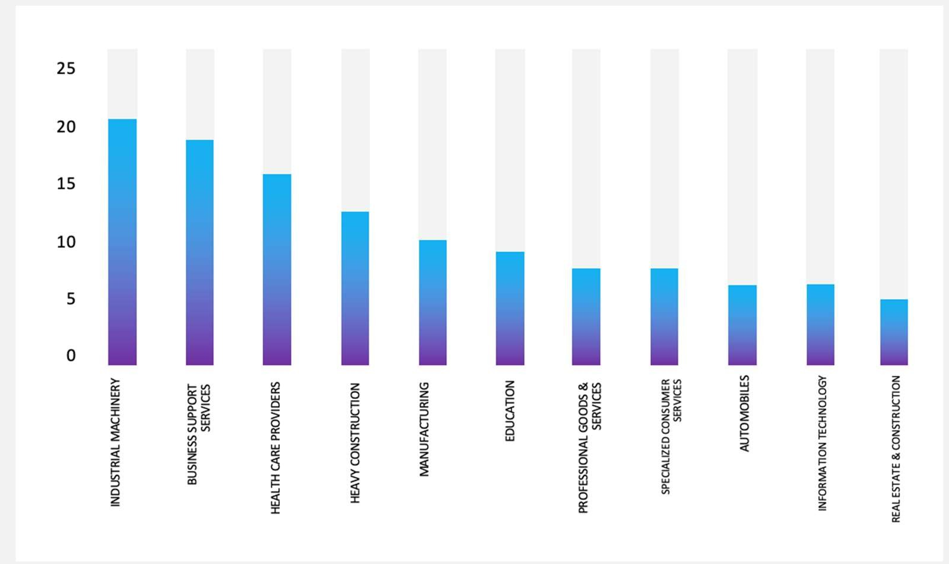
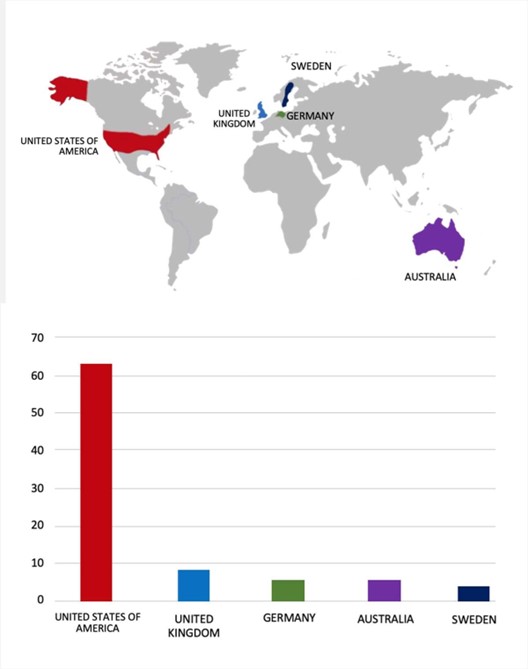
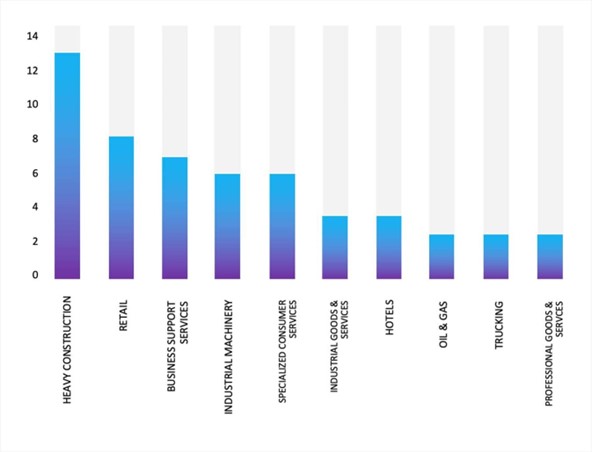
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
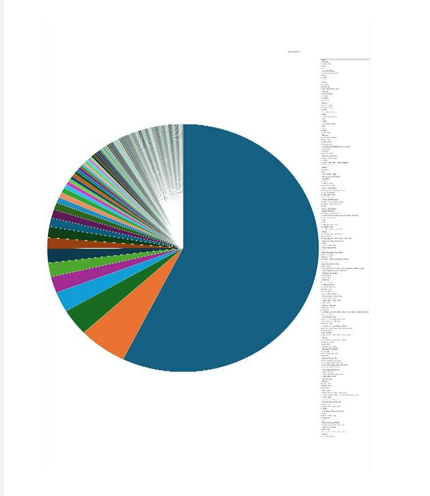
Industry-Wise Graph
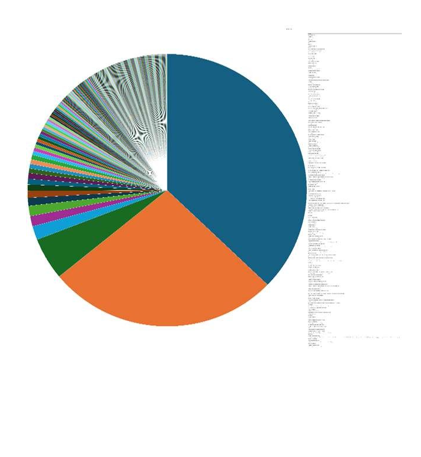
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.