



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Diamond Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Diamond Ransomware
In late April 2024, researchers identified a new ransomware strain known as Diamond, also referred to as Duckcryptor.
Upon execution, the ransomware encrypts files on the system and appends the extension “.[[email protected]].duckcryptor” to their filenames.
Subsequently, the ransomware altered the desktop wallpaper and generated two ransom notes: “Duckryption_info.hta” and “Duckryption_README.txt”.

Screenshot of files encrypted by ransomware (Source: Surface Web)

Screenshot of Diamond ransomware’s ransom note (“Duckryption_info.hta”): (Source: Surface Web)

Screenshot of Diamond (Duckcryptor)’s desktop wallpaper: (Source: Surface Web)

Appearance of Diamond (Duckcryptor) ransomware’s text file “Duckryption_README.txt” (Source: Surface Web)
The ransom notes reveal that the ransomware targets both individuals and organizations, with the ransom amount adjusted based on the victim’s perceived ability to pay.
Additionally, the threat actors warn of repeated attacks on organizations if the ransom is not paid.
Following are the TTPs based on the MITRE Attack Framework
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002:Execution | T1047: Windows Management Instrumentation |
| T1053: Scheduled Task/Job | ||
| T1059: Command and Scripting Interpreter | ||
| 2 | TA0003: Persistence | T1053: Scheduled Task/Job |
| T1176: Browser Extensions | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| 3 | TA0004: Privilege Escalation | T1053: Scheduled Task/Job |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1548: Abuse Elevation Control Mechanism | ||
| 4 | TA0005: Defense Evasion | T1036: Masquerading |
| T1070.004: Indicator Removal: File Deletion | ||
| T1202: Indirect Command Execution | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1548: Abuse Elevation Control Mechanism | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1564.001: Hide Artifacts: Hidden Files and Directories | ||
| 5 | TA0006: Credential Access | T1003: OS Credential Dumping |
| 6 | TA0007: Discovery | T1010: Application Window Discovery |
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 7 | TA0009: Collection | T1005: Data from Local System |
| T1114: Email Collection | ||
| T1185: Browser Session Hijacking | ||
| 8 | TA0011: Command and Control | T1071: Application Layer Protocol |
| 9 | TA0040: Impact | T1486: Data Encrypted for Impact |
Relevancy and Insights:
ETLM Assessment:
Based on the available information, CYFIRMA’s assessment suggests that the Diamond (Duckcryptor) ransomware is likely to evolve in order to target more sophisticated environments. This evolution may involve leveraging system management tools and registry manipulation for persistence. The increased utilization of WMI calls and network behavior checks indicates a trend toward employing more advanced and evasive techniques, which poses significant risks globally. The ransomware’s clear intention, as stated in its ransom note, is to generate substantial profits, thus it will particularly target developed regions such as the US, UK, East Asia, Southeast Asia, etc. Vigilance and robust cybersecurity measures are essential for effectively mitigating these threats.
Sigma Rule
title: Drops script at startup location threatname:
behaviorgroup: 1
classification: 7 logsource:
service: sysmon product: windows
detection: selection:
EventID: 11 TargetFilename:
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.vbs*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.js*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.jse*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.bat*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.url*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.cmd*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.hta*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.ps1*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.wsf*’ condition: selection
level: critical
(Source: Surface web) Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Backdoor
Objective: Espionage, Data Exfiltration
Threat Actor: Turla (aka Snake)
Target Entities: Diplomats and Foreign Affairs Ministries
Target Geographies: Europe and Middle East
Target Technology: Web Servers & Mail Servers
Active Malware of the Week
This week “Lunar” is trending
Lunar
Researchers discovered two previously unknown backdoors, named LunarWeb and LunarMail, compromising a European ministry of foreign affairs (MFA) and its diplomatic missions, including diplomatic institutions of this MFA in the Middle East. LunarWeb, which targets servers, uses HTTP(S) for command and control (C&C) communications and mimics legitimate requests. LunarMail, targeting workstations, persists as an Outlook add- in and uses email for its C&C communications. Both backdoors utilize steganography to hide commands in images, evading detection. The Lunar toolset has likely been in use since at least 2020. Due to similarities in tactics, techniques, and procedures (TTPs) with past activities, researchers attribute these compromises to the Russia-aligned cyberespionage group Turla with medium confidence.
Technical Analysis
The analysis began with detecting a lunar loader decrypting and executing a payload from an external file on an unidentified server, leading to the discovery of a new backdoor named LunarWeb. Further analysis revealed LunarWeb deployed at a diplomatic institution of a European MFA. During another attack, simultaneous deployments of LunarWeb were observed at three diplomatic institutions of this MFA in the Middle East, occurring within minutes of each other. The attacker likely had prior access to the MFA’s domain controller and used it for lateral movement to related institutions within the same network.
Additionally, researchers identified a second backdoor, LunarMail, which uses a different method for command and control (C&C) communications. Following are the two observed Lunar backdoor compromise chains:

Stage 1 – Lunar Loader
The execution chain begins with a loader named LunarLoader, which uses the RC4 cipher to decrypt the path to the Stage 2 blob and read an encrypted payload. To ensure only one instance is active, it creates a mailslot with a unique name instead of using common synchronization objects. It derives a decryption key from the MD5 hash of the computer’s DNS domain name, which it verifies before decrypting the payload with AES-256, resulting in a PE file. LunarLoader allocates memory for the PE image, decrypts the name of an exported function, and runs this function in a new thread containing a reflective loader.
Using the DNS domain name for payload decryption acts as an execution guardrail, ensuring the loader only executes in the targeted organization, potentially hindering analysis if the domain name is unknown. LunarLoader can be standalone or part of trojanized open-source software. One observed case involved a trojanized AdmPwd, part of the Windows Local Administrator Password Solution (LAPS).
Stage 2 blob – Payload Container
The Stage 2 blob comprises four entries, including two unused strings, one being the base64-encoded version of freedom or death or freedom or death (yeah,we are alive), and 32-bit and 64-bit versions of the payload. While the purpose of the “freedom or death” string isn’t explicitly explained, it’s common for malware authors to include such strings for various reasons, such as tracking versions, distracting analysts, or as a signature.
Additionally, instead of a 32-bit payload, researchers found strings like “shit happens.” Two different backdoors were observed as payloads (LunarWeb and LunarMail), utilizing DLL names in the export directory with “e” suffixes indicating 64-bit versions.
LunarWeb
LunarWeb, the initial payload discovered, functions as a backdoor, communicating with its C&C server via HTTP(S) and executing received commands. Deployed exclusively on servers, it initializes by locating or creating its state file and decrypting strings related to communication using RC4 with a static key. It collects victim identification data to calculate a victim ID used in communications. After safety checks, including assessing its lifespan and C&C server accessibility, it enters a communication loop with a delay of a few hours, skipped on the first run. If safety conditions fail, LunarWeb self-removes, deleting its files but leaving potentially detectable traces of the Stage 1 loader’s persistence method.
Initial Server Compromise
The initial server compromise involving LunarWeb remains partially unclear, but an installation-related component was found on one compromised server: a compiled ASP.NET web page named system_web.aspx. This filename is a known indicator of compromise (IoC) associated with Hafnium, a China-aligned APT group, but researchers believe this might be a coincidence or a false flag. When requested, the system_web.aspx page appears as a benign Zabbix agent log but secretly expects a password in a cookie named SMSKey. This password, combined with a specific salt, derives an AES-256 key and IV to decrypt two embedded blobs, dropped as temporary files in a directory excluded from scanning.
While the exact password remains unknown, the file sizes match the Stage 1 loader and the Stage 2 blob containing the LunarWeb backdoor. The attacker, or an unknown component, renames and moves these temporary files to their final destinations and establishes persistence. The attacker had prior network access, used stolen credentials for lateral movement, and meticulously compromised the server without raising suspicion.
They copied two log files over the network, disguised as Zabbix agent logs, moved them to the IIS web directory as the system_web page, and sent a HEAD request with a password, resulting in the creation of two .tmp files. These files, containing Stages 1 and 2, were then moved to specific locations. Finally, to maintain access and execute their code, the attacker set up a Group Policy extension in the registry using the Remote Registry service.
LunarWeb Configuration and Operation
Configuration and State
LunarWeb’s configuration, likely manually changed in the source code, is hardcoded into the binary, varying between samples. This includes C&C servers, unreachability threshold, communication format, and backdoor lifespan. It maintains a 512-byte state structure, stored in a file, with three slots accessed by index. While the first two slots are unused, the third is utilized. State slots are encrypted using RC4 with a key.
Information Collection
LunarWeb gathers host computer information and sends it to the C&C server upon initial contact:
Communication
After initialization, LunarWeb communicates with its C&C server via HTTP(S), employing a custom binary protocol with encrypted content. It utilizes three URLs, each serving different purposes: one for initial contact, uploading host computer information, and two for receiving commands, each on a different server, referred to as command URLs. To conceal its C&C communications, LunarWeb mimics legitimate traffic by spoofing HTTP headers with genuine domains and commonly used attributes. It can also receive commands disguised within images, such as impersonating Windows services (Teredo, Windows Update). Victim identification is included in HTTP requests, either through randomly generated cookies or URL query parameters containing a victim ID. LunarWeb can also use an HTTP proxy server for C&C communications if necessary.
Receiving Commands
LunarWeb retrieves commands from the C&C server via a GET request to the command URL, with the request and response formats varying across five supported formats determined by a hardcoded value. Depending on the format, received data may require decoding with base64 or extraction from an image. Communication formats 0 and 1 decrypt data using RSA-4096, while formats 2, 3, and 4 utilize a more complex process involving
AES-256 decryption and zlib decompression. After decryption and decompression, the data forms a command package with a unique ID, compared to the last processed ID stored in the backdoor’s state. If different, the package is processed, and the last ID is updated.
Cryptographic operations are performed using a statically linked Mbed TLS library, utilizing two embedded RSA-4096 keys for encryption and decryption, as outlined in their GitHub repository.
Exfiltrating Data
Data undergoes zlib compression and AES-256 encryption, with a session key and IV derived from the data’s size, along with a hash-based message authentication code (HMAC). AES encryption involves generating a random 32-byte AES seed, encrypted using RSA-4096, then derived into a session key using SHA-256 hashing. Encrypted data, along with decryption and integrity metadata, is sent via POST requests to the C&C server, delayed by a sleep of 34 to 40 seconds. Command packages include an output URL for sending results, which could be the same or a different server. If output data exceeds 1.33 MB after compression, it is split into multiple parts of random size (384–512 KB).
Commands
LunarWeb possesses standard backdoor functionalities, enabling file and process operations and executing shell commands, including PowerShell and Lua code. It supports a variety of capabilities, including running reconnaissance commands to gather system and network information, user details, installed programs, and security settings. Notably, it can retrieve Zabbix configurations using a specific file path. Additionally, some commands may produce error messages referencing them as “tasks,” indicating incorrect formatting.
LunarMail
The second backdoor, LunarMail, is similar to LunarWeb but communicates through email with its C&C server. Unlike LunarWeb, LunarMail is intended for deployment on user workstations and persists as an Outlook add-in. It draws inspiration from LightNeuron, a Turla backdoor with a similar email-based communication method, although no code similarities were found between them. Other Turla backdoors with similar operations include the Outlook backdoor.
Malicious Document Delivery
In another compromise, an older malicious Word document was discovered, likely from a spear phishing email. Despite being a DOC file, it’s actually in DOCX format, which is a ZIP archive that can hold extra content. This document contains 32- and 64-bit versions of a Stage 1 loader and a Stage 2 blob containing the LunarMail backdoor. The installation is facilitated by a VBA macro executed on document opening. The macro calculates a victim ID from the computer name and informs its C&C server by pinging a specific URL with the ID. It then creates a directory and extracts the necessary files from the ZIP/DOCX content. Persistence is established via Outlook add-in registry settings, mimicking Gpg4win’s Outlook add-in, GpgOL. Once deployed, the Stage 1 loader appears in Outlook Add-Ins.
Initialization
During initialization, the backdoor decrypts encrypted strings, including a regex expression used as a filter to search for the email profile for C&C purposes. These strings are encrypted using RC4 with a static key. To interact with Outlook, the backdoor dynamically resolves the required Outlook Messaging API (MAPI) functions. Additionally, the backdoor creates a directory in the %TEMP% path on each run, serving as a staging directory for data exfiltration.
Configuration and State
Similar to LunarWeb, LunarMail’s configuration entries are hardcoded in the binary, encompassing conditions to locate an Outlook profile for C&C communications, default exfiltration settings, and the backdoor’s lifespan limit. Unlike LunarWeb, LunarMail maintains a single-state file that persists in %LOCALAPPDATA%\Microsoft\Outlook\outlk.share. This 668-byte structure is updated during execution, storing details such as the timestamp of the last command executed and the current staging directory. Subsequent runs replace the previous staging directory with a new one.
Information Collection
During its initial operation, the LunarMail backdoor gathers environmental variables and recipients’ email addresses from sent email messages. It also decrypts a batch file containing system information commands, though this file is not executed. In specific error scenarios, it collects the email addresses associated with available Outlook profiles.
Communication and Commands
The LunarMail backdoor operates within Outlook, utilizing the Outlook Messaging API (MAPI) to communicate with its command and control (C&C) server. It receives commands and exfiltrates data through email messages, demonstrating its stealthy operation within the email environment.
Profile Search
LunarMail initiates communication by searching for compatible Outlook profiles from Microsoft Exchange. These profiles must adhere to specific criteria, including having four default folders and containing the domain of the targeted institution in the email address. Profiles that match these conditions are further filtered based on a regex pattern to exclude legitimate institutional emails. Once a suitable profile is found, initial information is sent.
Subsequent communication involves searching the inboxes of potential profiles for emails containing commands. This dynamic approach eliminates the need for hardcoded profiles and complicates identification. Furthermore, commands can specify a particular profile to use, a setting that is retained in the backdoor’s state.
Receiving Commands
LunarMail identifies a profile containing commands by scrutinizing email messages and attempting to analyze their attachments. These attachments must adhere to strict criteria: being a single PNG image with a .png extension and a size of ≤10 MB. The backdoor then inspects the IDAT chunks of the PNG file, seeking specific components such as an AES seed, an exfiltration configuration, and command chunks. All these elements are zlib- compressed and encrypted, with RSA-4096 used for the former and AES for the latter two. It’s intriguing that these chunks must maintain the PNG format, complete with validated CRCs, resulting in a visually noisy yet technically valid image due to the encrypted and compressed content.
LunarMail employs the same cryptographic methods as LunarWeb, including the Mbed TLS library and two RSA-4096 keys. The structure of the decompressed exfiltration configuration mirrors LunarWeb’s command package metadata, detailing the destination for command outputs and employing an ID to prevent duplicate commands stored in state. Following decryption and decompression, LunarMail commands exhibit an identical structure to LunarWeb’s. Each parsed command is executed, with outputs stored in the staging directory for subsequent exfiltration. Significantly, emails that fail parsing for commands have their IDs cached to prevent redundant parsing. However, this cache isn’t retained between backdoor executions and is rebuilt each time. Successfully parsed emails are promptly deleted post-processing.
Commands
LunarMail offers a more streamlined set of command capabilities compared to LunarWeb. It can create files, initiate new processes, and, uniquely, capture screenshots and adjust the C&C communication email address. Unlike LunarWeb, it doesn’t feature distinct commands for executing shell or PowerShell commands, but it does support Lua scripts.
Upon execution, commands deposit their outputs into files within the staging directory.
Exfiltrating Data Preparation
LunarMail prepares data for exfiltration by embedding it into PNG images or PDF documents, determined by the attachment extension specified in the exfiltration configuration. PNG and PDF files are constructed using predefined content templates. For PNG files, LunarMail utilizes a template featuring the institution’s logo, suggesting prior familiarity with the compromised system. To create a PNG containing output files, LunarMail initiates by generating a random 32-byte AES seed for encryption.
Subsequently, it generates IDAT chunks containing data and integrates them into the PNG template. These chunks consist of:
Before compression and encryption, the output file name and content are structured alongside a magic string (001035) within the PNG chunks, ensuring adherence to PNG specifications. To complete the image, the IEND footer chunk is appended. Alternatively, LunarMail produces PDF files using an encrypted template, the content of which remains undisclosed. Output files with metadata are inserted into the PDF template, facilitating parsing and decryption. Once embedded, files staged for exfiltration are deleted, remaining temporarily in the staging directory until transmission.
Exfiltrating Data – Transmission
Prepared PNGs or PDFs, containing output files, are dispatched as email attachments to a controlled inbox, adhering to predefined configurations. Default settings dictate recipient, subject, message body, and attachment filename. Although the email content mirrors the language of the compromised institution, it appears translated due to unnatural phrasing.
Customized exfiltration configurations can override the default settings. HTML format may be employed for the email body, with PNGs embedded as images. Messages are flagged for deletion post-transmission, ensuring a discrete exfiltration process.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the emergence of sophisticated backdoors like LunarWeb and LunarMail signals a concerning trajectory in cyber threats, with cybercriminals constantly innovating to breach organizational defenses. As these threats become increasingly intricate, organizations face heightened risks to their digital security. The use of steganography to conceal commands within images underscores the evolving sophistication of malware techniques, posing challenges for traditional detection methods. Looking ahead, it’s evident that cybercriminals will continue refining their tactics and adapting to the evolving cybersecurity landscape. While Lunar is currently targeting specific regions like Europe and the Middle East, historical patterns indicate that threat actors like Turla have historically targeted a broader geographic scope, including Europe, Central Asia, and the Middle East. This suggests the potential for Lunar to expand its target geography in the future, posing a broader threat landscape for organizations.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Emerging Threat: Void Manticore’s Destructive Cyber Campaigns Targeting Israeli Organizations
Summary:
Void Manticore (aka Storm-842) is an Iranian state-sponsored threat actor known for conducting destructive attacks on Israeli organizations and leaking information through the online persona ‘Karma’ (sometimes written as KarMa). These operations often target sectors such as government, finance, and critical infrastructure, aligning with Iran’s broader offensive strategy. The group employs straightforward and efficient techniques aimed at causing rapid and significant damage. Their operations extend beyond Israel, with attacks also reported in Albania, where they use the persona ‘Homeland Justice’ to leak stolen data. In Israel, Void Manticore is notable for utilizing a custom wiper named BiBi, after Israeli Prime Minister Benjamin Netanyahu.
One common method Void Manticore uses to gain access to target systems is through internet-facing web servers like CVE-2019-0604, where they deploy web shells like the custom “Karma Shell.” This tool, disguised as an error page, can list directories, create processes, upload files, and manage services, using simple encryption methods like base64 and one-byte XOR for obfuscation. They have also been observed uploading a custom executable, do.exe, which checks for Domain Admin credentials. Upon successful authentication, it installs another web shell, reGeorge, indicating valid credentials. This suggests the initial access might be facilitated by another entity, possibly Scarred Manticore, a more sophisticated threat actor.
After gaining access, Void Manticore uses Remote Desktop Protocol (RDP) for lateral movement and SysInternal’s AD Explorer to gather information about the target network. On compromised hosts, they establish command and control (C2) channels using an OpenSSH client. These steps enable them to control the network environment and prepare for deploying destructive payloads. The group employs custom wipers to achieve their destructive goals. These wipers either selectively corrupt specific files within the system or destroy the system’s partition table, making all data on the disk inaccessible.
One notable tool in their arsenal is the CI Wiper, this wiper employs a legitimate driver, ElRawDisk, to interact directly with the disk, allowing it to wipe files, disks, and partitions. The use of ElRawDisk has been seen in other wipers associated with Iranian actors, indicating a shared methodology. Void Manticore’s activities extend beyond Israel, with attacks in Albania where they use the persona ‘Homeland Justice’ to leak stolen data. This dual approach combines psychological warfare with data destruction, amplifying the impact on targeted organizations. Their attacks often carry politically charged messages, as demonstrated by the custom BiBi wiper.
The collaboration between Void Manticore and Scarred Manticore highlights a sophisticated level of coordination, allowing Void Manticore to benefit from advanced capabilities and access to high-value targets. The observed handoff procedures between the two groups underscore a strategic alignment, enhancing Void Manticore’s effectiveness and reach.
Relevancy & Insights:
Void Manticore (also known as Storm-842) is an Iranian threat actor notable for its destructive campaigns and information leaks using the online persona ‘Karma’. Their operations show significant overlap with Scarred Manticore (Storm-861), indicating collaboration between the two groups. Instances where victims are transferred from Scarred Manticore to Void Manticore suggest a cooperative relationship spanning multiple operations in Israel and Albania. Void Manticore, believed to be affiliated with Iran’s Ministry of Intelligence and Security (MOIS), has conducted BiBi Wiper attacks in both Israel and Albania. The BiBi Wiper malware, initially used to cause data destruction, now includes a new version that deletes the disk partition table, making data restoration more difficult and extending downtime for the victims. This threat actor targets Israeli organizations as part of a broader Iranian intelligence strategy, aiming to disrupt critical sectors and cause significant operational setbacks.
ETLM Assessment:
Void Manticore, an Iranian threat actor affiliated with the Ministry of Intelligence and Security (MOIS), targets Israeli organizations and extends its reach to Albania. This group collaborates with Scarred Manticore, utilizing initial access and infrastructure provided by them. They aim for cyberespionage through destructive wiping attacks and influence operations, primarily focusing on government, finance, and critical infrastructure sectors. Void Manticore employs custom wipers for both Windows and Linux, including the BiBi Wiper, which now deletes disk partition tables to complicate data restoration and prolong downtime. Their tactics also involve manual deletion of files, ransomware, and leveraging Scarred Manticore’s prior compromises to enhance their disruptive operations. The involvement of this threat actor, along with others, raises serious concerns and may increase in the future due to conflicts and rising tensions in the Middle East. Additionally, a wide range of hack and leak personas have emerged, specifically targeting Israel, further complicating the threat landscape.
Recommendations:

IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
China intensifies its information war on the West
Over the past 24 months, the Chinese information operations have switched from pushing predominately pro-China content to more aggressively target US politics. It’s a part of a wider multibillion-dollar influence campaign by the Chinese government, which has used millions of accounts on dozens of internet platforms ranging from X and YouTube to more fringe ones, where Chinese operators have been trying to push pro-China content. It’s also been among the first to adopt cutting-edge techniques such as AI-generated profile pictures and video avatars. Over the past five years, the researchers who have been tracking the campaign have watched as it attempted to change tactics, using video, automated voiceovers, and most recently the adoption of AI to create profile images and content designed to inflame existing divisions.
ETLM Assessment:
There’s little doubt at this point that TikTok is censoring Americans’ videos on topics sensitive to Beijing, as well as providing lots of personal data on Americans (and Canadians, and everyone else) to the Chinese government. Canada’s intelligence agency recently warned citizens not to use TikTok due to privacy concerns. Meanwhile, TikTok is far from China’s only vector of information warfare. The country has flooded American social media with bots and human-operated accounts attempting to spread disinformation and divisive messaging.
Chinese hackers targeting the shipping industry
Researchers have published a report on activity observed in the last 6 months in which the Chinese hacking group Mustang Panda was deploying malware against the shipping industry in Europe. Researchers detected Korplug loaders utilized by Mustang Panda on computer systems belonging to cargo shipping companies based in Norway, Greece, and the Netherlands, including some that appeared to be aboard the cargo ships themselves.
ETLM Assessment:
While it is not clear why exactly is China targeting the shipping industry, it might be mapping the field and trying to insert cyber capabilities into critical infrastructure which it could activate in a crisis. In a conflict scenario (typically over Taiwan), China could use their pre-positioned cyber capabilities to wreak havoc in civilian infrastructure and deter coordinated Western military action.
The RansomHouse Ransomware impacts the Gantan Beauty Industry
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; (www[.]gantan[.]co[.]jp), was compromised by the RansomHouse Ransomware. Gantan Beauty Industry Co., Ltd. specializes in metal roofing solutions for both commercial and residential buildings. The company offers various products, including metal roofs, integrated gutters, and other roofing accessories. The compromised data includes sensitive and confidential information related to the organization. The total volume of compromised data is approximately 400 GB.
The following screenshot was observed published on the dark web:


Source: Dark Web
Relevancy & Insights:

ETLM Assessment:
RansomHouse ransomware is known to target large enterprises and high-value targets. RansomHouse ransomware targets its victims through phishing and spear phishing emails. They are also known to use third-party frameworks (e.g., Vatet Loader, Metasploit, Cobalt Strike). Based on the available information, CYFIRMA’s assessment indicates that RansomHouse ransomware will continue to target various industries globally, with a significant emphasis on the United States, European, and Asian regions. The recent breach targeting the Gantan Beauty Industry, a leading Construction firm based in Japan, serves as a potential indicator of RansomHouse ransomware’s inclination towards targeting organizations across the Asia Pacific.
The RansomHub Ransomware impacts the Chuo System Service Co., Ltd
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; (www[.]Chuoss[.]co[.]jp), was compromised by the RansomHub Ransomware. Chuo System Service Co., Ltd. (CSS) is a Japanese IT company specializing in the planning, design, development, and maintenance of business systems. They also provide medical package software solutions and offer services across various industries, including retail, banking, and gas utilities. The company is known for its custom IT solutions, such as warehouse management and ATM software. CSS emphasizes creating a fair and professional work environment to achieve high customer satisfaction. The compromised data contains sensitive and confidential information related to the organization. The total volume of compromised data is approximately 20 GB.
The following screenshot was observed published on the dark web:

Source: Dark Web
Relevancy & Insights:


ETLM Assessment:
The RansomHub group seems to be a recently emerged ransomware group, likely with roots in Russia. Due to the benefit it offers its affiliates and the strict controls it enforces, they could be vying for the leadership position amidst pressure from security forces to major players like LockBit and ALPHV. However, their ransomware strains appear to be just a revised version of an old sample for now. An interesting part is that this strain is also written in the Golang language. Based on CYFIRMA’s assessment, RansomHub Ransomware targets organizations worldwide. The attack on Chuo System Service Co., Ltd also highlights ransomware groups’ interest in organizations from the Asia Pacific, financially strong in the region with exploitable vulnerabilities.
Vulnerability in Mozilla Focus for iOS
Summary:
The vulnerability allows a remote attacker to perform a spoofing attack.
Relevancy & Insights:
The vulnerability exists due to incorrect processing of URLs with file scheme.
Impact:
A remote attacker can trick the victim into visiting a specially crafted webpage and spoof addresses in the location bar.
Affected Products: https[:]//www[.]mozilla[.]org/en-US/security/advisories/mfsa2024-24/
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.

ETLM Assessment:
Vulnerabilities in Firefox Focus can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of Firefox Focus is crucial for maintaining the privacy and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding online activities across different geographic regions and sectors.
LockBit3.0 Ransomware attacked and Published data of Thai Agri Foods Public Company Limited
Summary:
Recently we observed that LockBit3.0 Ransomware attacked and Published data of Thai Agri Foods Public Company Limited on its darkweb website. Thai Agri Foods Public Company Limited(www[.]thaiagri[.]com), headquartered in Thailand, is a prominent food processing company. The company specializes in the production of frozen and canned food products, using fresh ingredients such as seafood, fruits, and vegetables. They offer a wide range of products under several brands including Aroy- D, Savoy, Foco, Panchy, Little Chef, Uni Eagle, and Fuco. These products include coconut milk, sauces, curry pastes, canned fruits, juices, and ready-to-eat meals. TAF has customers in over 70 countries. The data leak, following the ransomware attack, encompasses a broad spectrum of sensitive and confidential information pertinent to the organization.



Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
Based on the available information, CYFIRMA’s assessment indicates that LockBit 3.0 ransomware will continue to target various industries globally, with significant emphasis on the United States, Europe, and Asia. The recent breach targeting Thai Agri Foods Public Company Limited, a leading agriculture and agribusiness firm in Thailand, serves as a potential indicator of LockBit 3.0 ransomware’s increased focus on organizations across Southeast Asia.
Centurion University Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data leak related to Centurion University, {www[.]cutm[.]ac[.]in} in the Telegram Channel. The hacktivist group known as “Hacktivist Indonesia” has publicly disclosed the complete database of Centurion University. The leaked data, made available on May 19, 2024, includes highly sensitive information about numerous applicants, students, and staff associated with the university. The breach, targeting the website of Centurion University (www[.]cutm[.]ac[.]in), has exposed a wide range of personal details. The compromised data encompasses IDs, names, campus affiliations, course details, gender, email addresses, mobile numbers, dates of birth, categories, nationalities, religions, Aadhar numbers, and detailed family information. Additionally, educational backgrounds, including scores and institutions from secondary to postgraduate education, and payment details are part of the exposed dataset.

Source: Telegram
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
According to CYFIRMA’s assessment, Hacktivist Indonesia is a cyber-attack group that has recently made headlines for targeting Indian government websites. The group has claimed it intends to attack 12,000 websites associated with various Indian governmental bodies. These attacks are primarily carried out using Distributed Denial- of-Service (DDoS) methods, which overwhelm servers with excessive traffic, causing disruptions in accessing online services. The targeted institutions lacked robust security postures and were susceptible to potential cyberattacks orchestrated by this threat actor.
Recommendations: Enhance the cybersecurity posture by
CYFIRMA Research team observed a potential data leak related to Sakaem Logistics (www[.]sakaemlogistics[.]com). Sakaem Logistics is a reputable auto transport company offering a range of vehicle shipping services across the United States and internationally. CyberNiggers threat actor group claims to have breached the CI/CD server of Sakaem Logistics, resulting in the leak of a substantial amount of the company’s source code.

Source: Underground forums
ETLM Assessment:
CyberNiggers threat actor group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
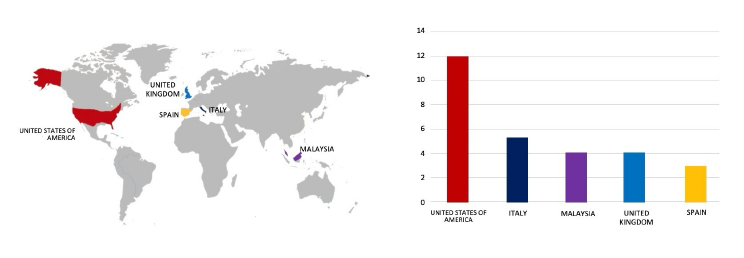
Please find the Geography – Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph

Industry-Wise Graph

For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.