



Key Intelligence Signals:
South Asia-based Bitter APT Targets Nuclear Energy Industry
In a recent observation, Bitter APT was found to target the Nuclear Industry in China. The threat actor is active since the year 2013 and is known for targeting Pakistan, Bangladesh Saudi Arabia, and China through well-crafted spear phishing emails. The tactics are similar to the previous campaigns that were active during the year 2021. In a recent attack, the threat actor applied a fresh layer of obfuscation to its malware to make it hard for analysts to detect. Phishing mail disguised to be from the Embassy of Kyrgyzstan was sent to Chinese recipients in Nuclear Energy Industry. Around 7 suspicious emails were detected, and a few were sent to entities in academia related to Nuclear Energy. Phishing emails tried to manipulate victims by inviting them to conferences related to their field. The phishing emails had attachments with RAR files that contained HTML Help (CHM) or Excel payload. An excel file leveraged Equation Editor exploits which led to the creation of two scheduled tasks, one performs fetching the second stage EXE payload using cURL and the second task performs execution of fetched EXE payload. In the CHM case, it also creates a scheduled task for the persistence and downloading of payloads for the next stage attack.
Nicely crafted social engineered email in this attack suggests that the threat actor had a good understanding of the working activities and responsibilities of the targeted individuals.
Recently, scientists working in nuclear research in the US were targeted by Cold River APT, a group based in Russia, using a phishing email that contained a password grabber. The nuclear sector continues to be a prime target for APT groups because it provides them with valuable intelligence and can help them gain an advantage over their adversaries.
The German intelligence agency BfV and the Republic of Korea’s National Intelligence Service have issued a joint advisory describing a spearphishing campaign by North Korea’s Kimsuky threat actor (also known as Thallium or Velvet Chollima).
The threat actor is going after experts on the Korean Peninsula and North Korea concerns with a malicious Chrome extension and malware-filled Android app. Analysts say that the attackers deceive their victims into installing the Chrome extension by sending them spearphishing emails. The extension can exfiltrate emails from the victim’s Gmail account once it is installed.
The APT is also using an Android Trojan called “FastViewer,” which was first observed in October 2022. The app is delivered via the Google Play console developer site for ‘internal testing only,’ and the victim’s device is supposedly added as a testing target. The advisory adds that since the technology exploited in this attack can be used universally, it can be used by foreign affairs and security think tanks around the world as well as unspecified people.
In other news, another North Korean threat actor known as Reaper or APT37 has been observed engaging South Korean targets. Researchers have observed APT37 conducting cyberespionage against individuals within South Korean organizations in February and March of this year. The gang disseminates the Chinotto PowerShell-based backdoor, giving the perpetrators full power and the ability to steal sensitive data from the victims.
According to researchers, Russia’s cyberwar on Ukraine has largely failed so far and Moscow is thus increasingly shifting focus towards the Western allies of Kyiv.
Russian actors are increasingly concentrated on attacking EU & NATO countries because Ukraine has proven to be a difficult target and cyberattack there have been largely replaced by kinetic strikes. The third quarter of 2022 saw a clear shift from a cyberwar focused on Ukraine to a high-intensity hybrid cyberwar across Europe, marking a turning point in cyberattacks linked to the conflict in Ukraine. With a growing emphasis on vital national infrastructure in sectors like aviation, energy, healthcare, banking, and public services, Russian hackers are primarily targeting Poland as well as the Baltic and Nordic countries and smaller nations that are seeking full EU membership, like Montenegro and Moldova. The cyber-attacks are often complemented by strong information warfare campaigns against both public and private institutions with the goal of weakening them and discrediting them alongside Ukraine itself.
Attacks against nations that back Ukraine’s cause have a clear connection to some recent events. For instance, a DDoS attack by Anonymous Russia against several Slovak government websites happened right after Slovakia decided to move its MiG-29 jet fighters to Ukraine.
Despite the failure of Russian cyberattacks to do any major damage to Western infrastructure so far, the US Cybersecurity and Infrastructure Security Agency (CISA) remains on guard against the possibility of a Russian cyber offensive, against the nuclear power sector. The agency has recently stated that a combination of effective defense, deterrence, and decisions by the Russian government itself have all contributed to the lack of effect on critical infrastructure. The agency also confirmed that it has yet not observed successful attacks on the United States from Russian state-backed actors and credited it to prepared defenses, increased vigilance, and successful cooperation of both government and industry in hardening the targets.
Russian hacktivist auxiliary groups have proven to be very active, but their attacks have so far only been on the level of annoyance. Hacktivists are mostly using DDoS attacks to briefly disable servers and interrupt services and engage in guerrilla cyber-harassment campaigns. The Russian groups span a variety of expertise levels and are frequently, though not always, linked to cybercriminal gangs. Given the tolerance and protection it gets from Moscow, criminal activity by Russian gangs has also continued at a high level, especially about ransomware attacks against inadequately protected organizations. This type of criminal activity might be described as privateering and has been on a steady rise in recent months.
CYFIRMA Research team observed the sale of database access of UK-based manufacturer Jabsco (www[.]jabsco[.]com) by the unknown threat actor. It is up for sale for USD 176,000.
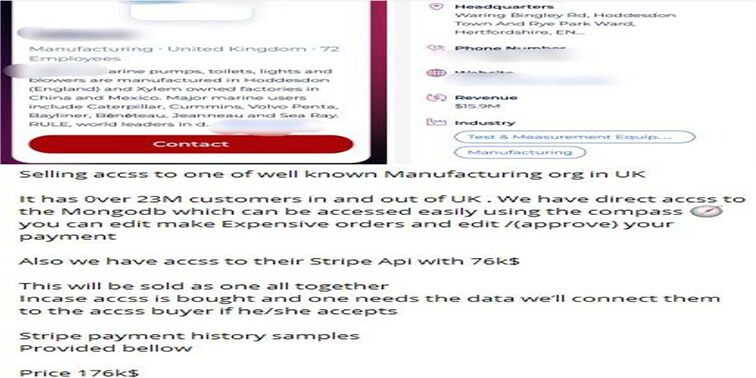
Source: Telegram