



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Hyena Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Hyena Ransomware
Researchers have identified a new ransomware strain named Hyena, linked to the MedusaLocker family. Hyena encrypts files, appending the “.hyena111” extension, and leaves a ransom note titled “READ_NOTE.html” while altering the desktop wallpaper.
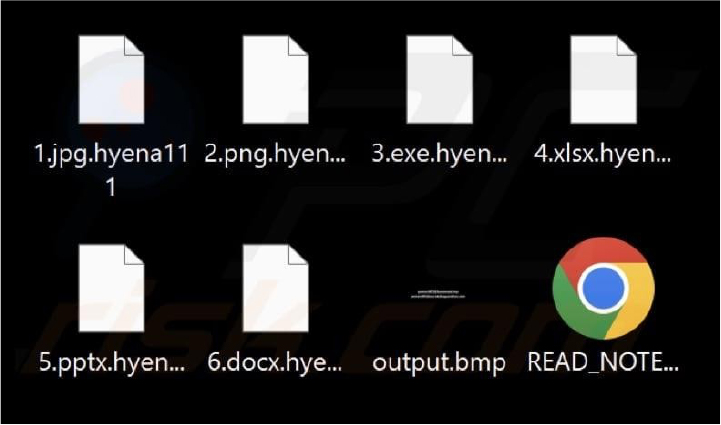
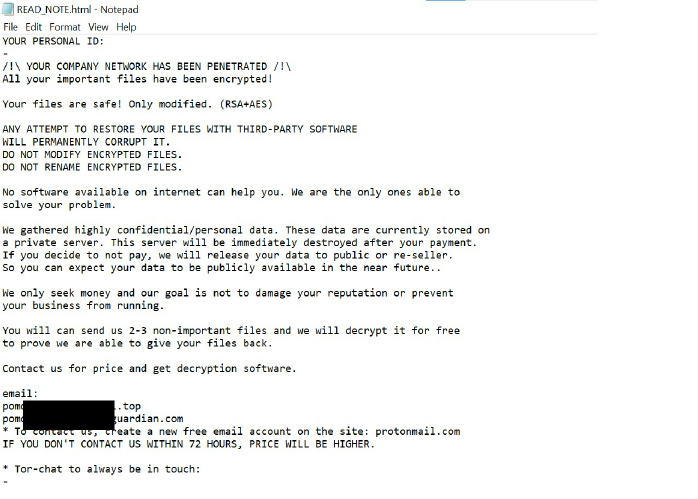
The ransom note informs victims that their network has been breached, and critical files are encrypted using RSA and AES algorithms. It warns against using third-party tools for file recovery, claiming such actions could lead to permanent data loss. The attackers also threaten to leak or sell confidential data if the ransom is not paid.
Victims are offered the chance to decrypt 2–3 non-essential files for free and are instructed to contact the attackers via provided email addresses or a Tor-based chat for negotiations. The note emphasizes that the ransom price will increase after 72 hours.
Following are the TTPs based on the MITRE Attack Framework
| Tactic | ID | Technique |
| Initial Access | T1091 | Replication Through Removable Media |
| Execution | T1059 | Command and Scripting Interpreter |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| PrivilegeEscalation | T1055 | Process Injection |
| PrivilegeEscalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| PrivilegeEscalation | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| CredentialAccess | T1056 | Input Capture |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1018 | Remote System Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1120 | Peripheral Device Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| LateralMovement | T1091 | Replication Through Removable Media |
| Collection | T1056 | Input Capture |
| Collection | T1074 | Data Staged |
| Commandand Control |
T1071 | Application Layer Protocol |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1573 | Encrypted Channel |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1496 | Resource Hijacking |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s analysis of available data reveals that MedusaLocker ransomware has been actively targeting diverse sectors including manufacturing, healthcare, finance, IT services and others since 2019. The emergence of Hyena ransomware, an advanced variant of MedusaLocker, suggests the adoption of enhanced evasion techniques aimed at expanding its reach to both individuals and enterprises. Projections indicate it will continue to impact key industries globally, highlighting the critical need for robust cybersecurity measures to effectively counter these evolving threats.
Sigma rule:
title: New RUN Key Pointing to Suspicious Folder tags:
– attack.persistence
– attack.t1547.001 logsource:
category: registry_set product: windows
detection: selection_target:
TargetObject|contains:
– ‘\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\’
– ‘\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce\’ selection_details:
– Details|contains:
– ‘:\$Recycle.bin\’
– ‘:\Temp\’
– ‘:\Users\Default\’
– ‘:\Users\Desktop\’
– ‘:\Users\Public\’
– ‘:\Windows\Temp\’
– ‘\AppData\Local\Temp\’
– ‘%temp%\’
– ‘%tmp%\’
– Details|startswith:
– ‘%Public%\’
– ‘wscript’
– ‘cscript’
filter_main_windows_update:
TargetObject|contains: ‘\Microsoft\Windows\CurrentVersion\RunOnce\’ Image|startswith: ‘C:\Windows\SoftwareDistribution\Download\’ Details|contains|all:
– ‘rundll32.exe ‘
– ‘C:\WINDOWS\system32\advpack.dll,DelNodeRunDLL32’
Details|contains:
– ‘\AppData\Local\Temp\’
– ‘C:\Windows\Temp\’
condition: all of selection_* and not 1 of filter_main_* falsepositives:
– Software using weird folders for updates level: high
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Information Stealer | Objectives: Data theft | Target Industries: Telecom, Healthcare, Banking, Marketing | Target Geographies: United States, Argentina, Colombia, Philippines | Target Technology: Windows OS
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “Lumma Stealer” is trending.
Lumma Stealer
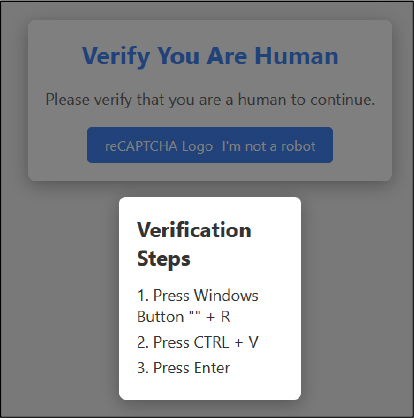
Researchers have identified a global malware campaign leveraging fake CAPTCHAs to deliver Lumma Stealer, a malware-as-a-service (MaaS) threat active since 2022. This campaign targets victims across industries such as telecom, healthcare, banking, and marketing, with notable activity in countries like the United States, Argentina, Colombia, and the Philippines. The attackers utilize various delivery methods, such as cracked software, Discord’s CDN, and fake CAPTCHA pages. The infection chain employs diverse techniques, including process hollowing and PowerShell one-liners. The campaign introduces new payloads, malicious websites leveraging malvertising, and sophisticated strategies to bypass security controls. Notably, attackers instruct victims to execute commands via the Windows Run command, effectively evading browser-based defenses. Additionally, the use of open-source snippets to bypass the Windows Antimalware Scan Interface (AMSI) further enhances the malware’s ability to remain undetected.
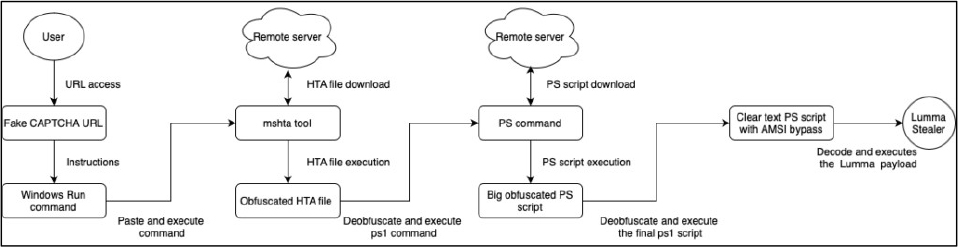
Attack Method
The infection process begins when a victim visits a website that redirects them to a fake CAPTCHA page. This deceptive CAPTCHA instructs the user to follow specific actions, initiating the next stage of the malware installation process. Since August 2024, Lumma Stealer has employed this tactic to trick users into running commands on their computers, effectively launching the infection. These fake CAPTCHAs are a sophisticated social engineering strategy, designed to make users unknowingly download and execute malware outside their browser. Even cautious users may fail to realize the implications of following these instructions. Executing the malware outside the browser also helps bypass browser-based security controls, making detection more challenging. In a recent campaign, the fake CAPTCHA instructs victims to open the Windows Run window using Windows+R, paste the clipboard’s content with CTRL+V, and press ENTER to execute it. This sequence, tailored for
Windows environments, is crucial for the malware’s deployment.
The website hosting the fake CAPTCHA uses a hidden JavaScript snippet to add a malicious command to the victim’s clipboard. This command utilizes the Windows tool mshta.exe to download and execute a file from a remote server. By leveraging mshta, a trusted Windows utility, attackers employ a technique known as LOLBIN to bypass security defenses by executing malicious code through legitimate system processes. Since the entire process occurs outside the browser, it effectively avoids detection by browser- based security measures.
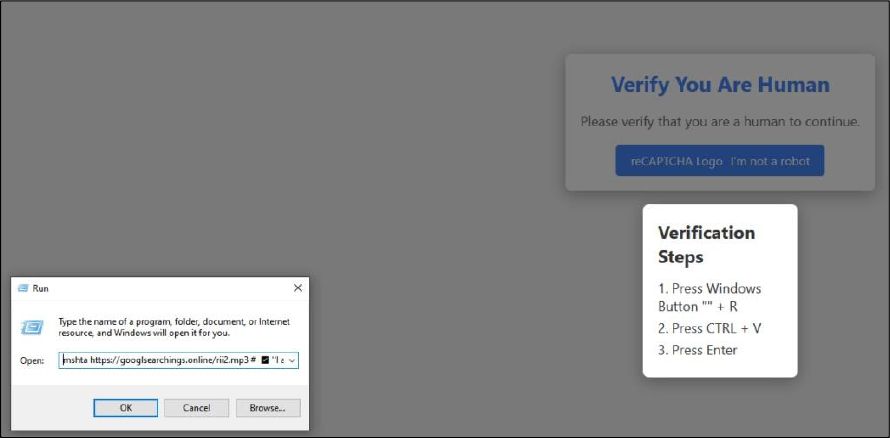
The observed payloads in this campaign disguise themselves with misleading file extensions like .mp3 or .accdb, but their contents reveal a mix of random data, malicious JavaScript, and incorrect file types. Once executed, the JavaScript invokes PowerShell to decode a base64-encoded data chunk, triggering the download and execution of a second-stage payload on the victim’s machine. This second-stage payload is an obfuscated PowerShell script that performs several tasks. It deobfuscates strings, generates a key (“AMSI_RESULT_NOT_DETECTED”), and uses base64 decoding with a multi- byte XOR operation to extract another PowerShell script. This script employs a clever evasion tactic by modifying the memory of the “clr.dll” module to bypass Windows Antimalware Scan Interface (AMSI), preventing its detection. Finally, the script decodes another base64 chunk into a PE file, which it loads and executes via reflection. This process ultimately delivers Lumma Stealer as the final payload.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that as Lumma Stealer continues to evolve, its ability to adapt to various attack vectors and exploit social engineering techniques could increase the difficulty for organizations to defend against it. The malware’s reliance on legitimate system processes and clever evasion tactics may allow it to bypass traditional security defenses, making it crucial for organizations to adopt broader, more comprehensive protection strategies. As the malware evolves, it could also expand its geographical reach, affecting organizations across different regions. Beyond direct financial or data losses, Lumma Stealer campaigns may erode trust within affected industries, especially as compromised credentials could facilitate secondary attacks, such as customer data breaches or supply chain disruptions. The continued growth of the malware-as-a-service model is likely to encourage similar threats, urging organizations to strengthen proactive and adaptive security measures through enhanced training, advanced detection tools, and cross-industry collaboration.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
PlushDaemon infiltrates the supply chain of a Korean VPN service.
Summary:
Recently, a sophisticated supply-chain attack was identified targeting a South Korean VPN provider. Attackers compromised the VPN’s installer, embedding a malicious backdoor alongside the legitimate software. This backdoor, known as SlowStepper, is a feature-rich tool with over 30 components designed for extensive cyberespionage activities.
The initial infection vector involved users downloading a ZIP archive containing the compromised installer from the VPN provider’s official website. Upon execution, the installer deployed both the legitimate VPN application and the SlowStepper backdoor. Persistence was achieved by adding a registry entry, ensuring the backdoor’s execution upon system startup.
SlowStepper operates through a multistage command-and-control (C&C) protocol utilizing DNS. It has the capability to download and execute numerous additional modules, primarily written in Python and Go, enhancing its espionage functionalities. These modules enable the malware to collect a wide range of data, including system details, running processes, installed applications, and network interfaces.
Furthermore, it can capture audio and video recordings, take photos, scan for documents, and extract information from various applications, including messaging platforms like WeChat and Telegram. Credential theft is also within its capabilities, posing significant risks to affected users.
The attackers’ primary method of initial access involves hijacking legitimate updates of applications by redirecting traffic to servers under their control. Additionally, they have been observed exploiting vulnerabilities in legitimate web servers to gain unauthorized access.
This campaign has been active since at least 2019, targeting individuals and entities across multiple regions, including mainland China, Taiwan, Hong Kong, South Korea, the United States, and New Zealand. The extensive toolkit and prolonged activity underscore the attackers’ commitment to developing a wide array of tools, making them a significant threat in the cyber landscape.
In response to the discovery, the compromised installer was promptly removed from the VPN provider’s website. However, users who downloaded the installer during the affected period are advised to conduct thorough security assessments to identify and remediate potential infections.
Relevancy & Insights:
The PlushDaemon threat actor group is a China-aligned sophisticated cyberespionage collective, primarily targeting East Asia, including South Korea, Taiwan, Hong Kong, and mainland China, with additional operations in the United States and New Zealand. The group is known for exploiting supply chain vulnerabilities and using trusted technologies such as VPNs and software updates to deploy malware. In one instance, they embedded a backdoor within a legitimate VPN installer.
Previously, PlushDaemon has taken advantage of web server vulnerabilities and DNS- based command-and-control (C&C) methods. Their toolkit consists of modular malware, reflecting the group’s adaptable and evolving tactics. With a focus on credential theft, data exfiltration, and surveillance, PlushDaemon’s operations demonstrate an ongoing refinement of their techniques.
ETLM Assessment:
PlushDaemon has a history of targeting across East Asia and beyond. Their operations often exploit trusted supply chains, allowing them to infiltrate networks with little chance of detection. The group is known for using sophisticated tactics, including modular malware and DNS-based command-and-control (C&C) techniques, to ensure long- term persistence and stealth.
They have frequently hijacked legitimate software updates or exploited vulnerabilities in web servers, tactics consistent with their past activity. PlushDaemon typically focuses on high-value targets in regions such as mainland China, South Korea, Taiwan, and Hong Kong, reflecting their strategic geopolitical interests.
Strategic Recommendations:
Tactical Recommendations:
Operational Recommendations:
| MITRE FRAMEWORK | ||
| Tactic | Tactic ID | Technique |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains |
| Resource Development | T1583.004 | Acquire Infrastructure: Server |
| Resource Development | T1608.001 | Stage Capabilities: Upload Malware |
| Resource Development | T1608.002 | Stage Capabilities: Upload Tool |
| Resource Development | T1588.001 | Obtain Capabilities: Malware |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Resource Development | T1588.003 | Obtain Capabilities: Code Signing Certificates |
| Resource Development | T1588.005 | Obtain Capabilities: Exploits |
| Initial Access | T1659 | Content Injection |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Initial Access | T1195.002 | Supply Chain Compromise: Compromise Software Supply Chain |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1059.006 | Command and Scripting Interpreter: Python |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1547.004 | Boot or Logon Autostart Execution: Winlogon Helper DLL |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| DefenseEvasion |
T1222.001 |
File and Directory Permissions Modification: Windows File and Directory Permissions Modification |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Name or Location |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1027.007 | Obfuscated Files or Information: Dynamic API Resolution |
| Defense Evasion | T1027.009 | Obfuscated Files or Information: Embedded Payloads |
| Defense Evasion | T1027.013 | Obfuscated Files or Information: Encrypted/Encoded File |
| Defense Evasion | T1553.002 | Subvert Trust Controls: Code Signing |
| Discovery | T1217 | Browser Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1120 | Peripheral Device Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1518 | Software Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1614 | System Location Discovery |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1016.002 | System Network Configuration Discovery: Wi-Fi Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Collection | T1560.002 | Archive Collected Data: Archive via Library |
| Collection | T1123 | Audio Capture |
| Collection | T1005 | Data from Local System |
| Collection | T1074.001 | Data Staged: Local Data Staging |
| Collection | T1113 | Screen Capture |
| Collection | T1125 | Video Capture |
| Command and Control | T1071.004 | Application Layer Protocol: DNS |
| Command and Control | T1132.001 | Data Encoding: Standard Encoding |
| Command and Control | T1573.001 | Encrypted Channel: Symmetric Cryptography |
| Command and Control | T1008 | Fallback Channels |
| Command and Control | T1105 | Remote File Copy |
| Command and Control | T1104 | Multi-Stage Channels |
| Command and Control | T1095 | Standard Non-Application Layer Protocol |
| Command and Control | T1090 | Connection Proxy |
| Command and Control | T1219 | Remote Access Tools |
| Exfiltration | T1020 | Automated Exfiltration |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
EU sanctions three GRU officers for cyberattacks against Estonia
The European Union imposed sanctions on three Russian nationals for orchestrating cyberattacks against Estonia in 2020. The EU identified the individuals as officers of the GRU’s 161st Specialist Training Center, also known as Unit 29155.
In a statement, the EU explained that the attacks provided unauthorized access to classified and sensitive data from multiple government ministries, including Economic Affairs and Communications, Social Affairs, and Foreign Affairs. As a result, thousands of confidential documents—containing business secrets, health records, and other critical information—were stolen, jeopardizing the security of the affected institutions. The EU also attributed other cyberattacks against its member states and partners, particularly Ukraine, to Unit 29155.
With the latest enforcement action, a total of 17 individuals and four entities are subject to asset freezes and travel bans, in addition to prohibiting E.U. people and entities from transacting with those listed.
ETLM Assessment:
Unit 29155 has previously been accused by the U.S. government and its allies of carrying out cyberattacks targeting government services, financial institutions, transportation systems, energy infrastructure, and healthcare sectors across NATO member states, the European Union, as well as countries in Central America and Asia.
Since at least early 2022, the group is believed to have actively disrupted efforts to provide aid to Ukraine. Within the cybersecurity community, this threat actor is tracked under various names, including Cadet Blizzard, Ember Bear, FROZENVISTA, Nodaria, Ruinous Ursa, UAC-0056, and UNC2589.
Notably, Korchagin and Denisov have been charged by the U.S. Department of Justice (DoJ) for their alleged roles in a conspiracy to commit computer intrusion and wire fraud, targeting Ukraine, the U.S., and 25 other NATO countries.
President Trump indicates new tariffs on computer chips and semiconductors
President Donald Trump said he would soon announce new tariffs on computer chips, repeating a campaign promise that if enacted could have deep impacts on the global tech industry and the geopolitical battle over AI with China.
“In the very near future we’re going to be placing tariffs on foreign production of
computer chips, semiconductors, and pharmaceuticals to return production of
these essential goods to the United States of America,” Trump said at a retreat of
House Republicans at his Doral golf resort in Miami.
Trump said he wanted the manufacturers of semiconductors and chips — which are used in many high-end consumer electronics and sophisticated AI-powered technology and research — to open factories in the United States and would use the threat of high taxes and tariffs to force them to relocate. “They’re not going to want to pay a 25, 50 or even 100 percent tax,” Trump said. “If you want to stop paying the taxes or the tariffs, you have to build your plant right here in America.”
ETLM Assessment:
The news comes on the back of the recent announcement of technical advancements by Chinese AI startup DeepSeek, shortly followed by a similar announcement from another Chinese company, Alibaba. These rattled tech stocks in the US and showed the world that semiconductor restrictions that the previous US administration placed on China are not working as intended and U.S. companies will need to intensify their efforts to maintain the country’s leadership in artificial intelligence.
The disruptions in the semiconductor market are going to be one of the most intense areas of strategic competition between the US and China and we should expect a lot of state-sponsored cyber activity in the field in the coming years.
The Lynx Ransomware Impacts Marukai
Summary
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; Marukai(www[.]marukai[.]com), was compromised by Lynx Ransomware. Marukai Corporation (d.b.a Tokyo Central) opened its business as one of the first international Japan-based retailers in the US market. Marukai offers a wide variety of imported Japanese goods such as food, health products, cosmetics, home furnishings, electric appliances, stationery, clothing, pottery, and many other specialty goods. The compromised data consists of confidential and sensitive information related to the organization.
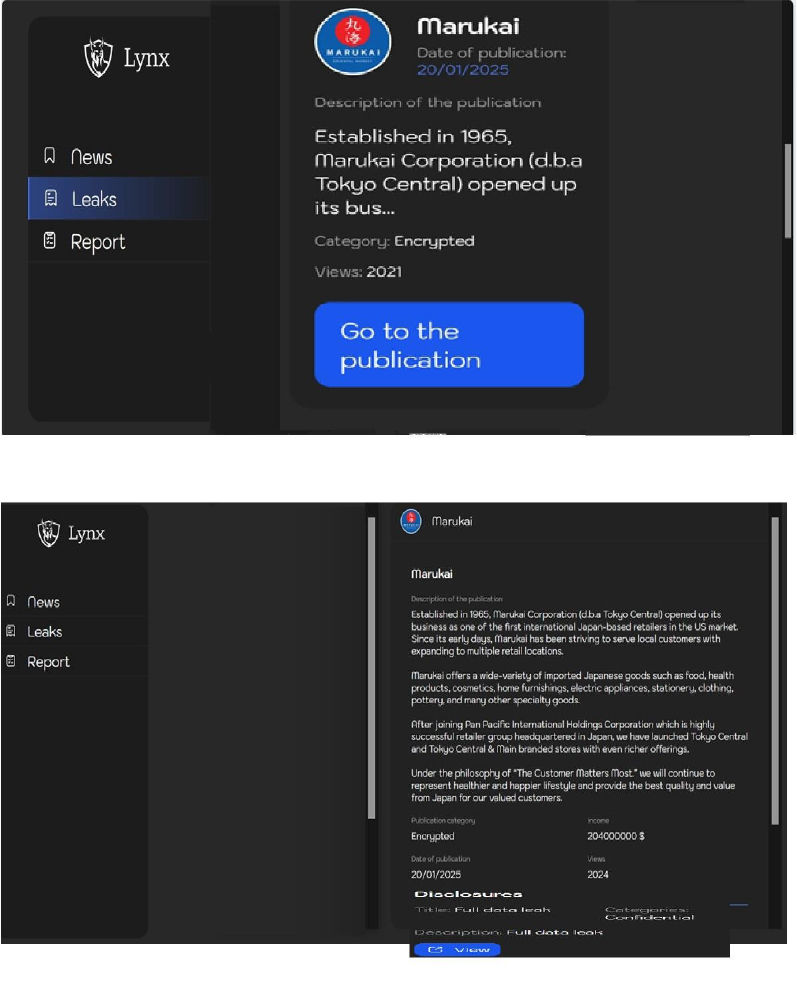
Relevancy & Insights:
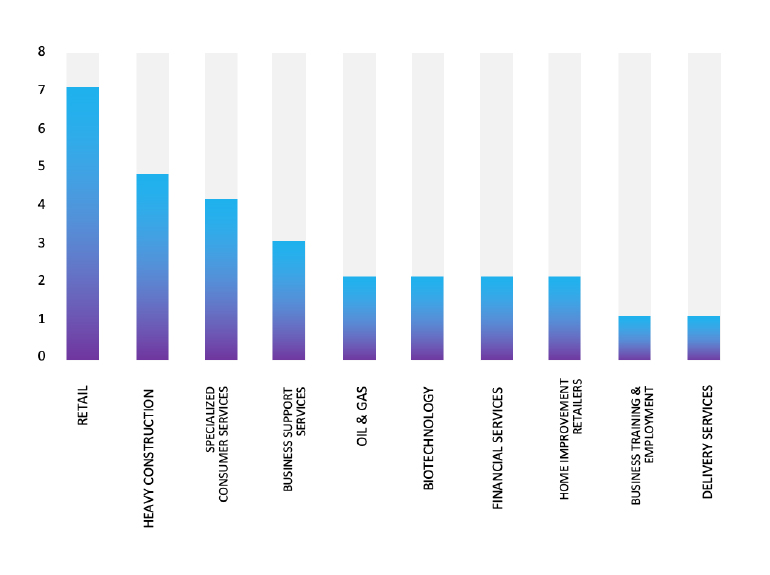
ETLM Assessment:
According to CYFIRMA’s assessment, Lynx Ransomware represents a significant threat in the evolving landscape of cybercrime. Its sophisticated techniques and aggressive tactics necessitate robust cybersecurity measures from organizations to mitigate risks associated with ransomware attacks. As this group continues to operate, ongoing monitoring and analysis will be crucial for understanding their methods and developing effective defenses against them.
The Hunters International Ransomware Impacts PetroVietnam Exploration Production Corporation
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Vietnam; PetroVietnam Exploration Production Corporation(www[.]pvep[.]com[.]vn), was compromised by Hunters International Ransomware. PetroVietnam Exploration Production Corporation (PVEP) is the upstream subsidiary of the Vietnam Oil and Gas Group (PetroVietnam), responsible for oil and gas exploration and production activities both domestically and internationally. The compromised data includes confidential and sensitive information belonging to the organization. The scale of the data exposure measures approximately 1.3 TB, comprising a total of 2,43,580 discrete files.
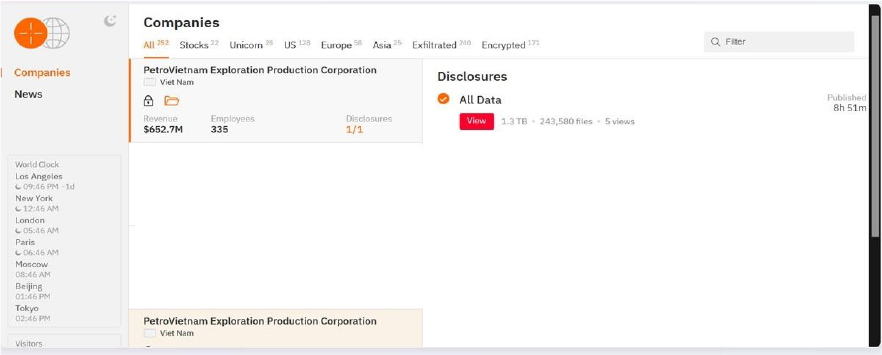
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Hunters International ransomware represents a significant threat within the ransomware landscape due to its sophisticated tactics and focus on double extortion strategies. Organizations are advised to enhance their cybersecurity measures by implementing robust backup solutions, conducting regular employee training on phishing awareness, and maintaining updated security protocols to mitigate risks associated with this evolving threat actor. Continuous monitoring of Hunters International’s activities will be essential for understanding its impact on global cybersecurity efforts.
Vulnerability in ArgoCD
Relevancy & Insights: The openshift.io/cluster-monitoring label is applied to all namespaces that deploy an ArgoCD CR instance, allowing the namespace to create a rogue PrometheusRule.
Impact: This issue can have adverse effects on the platform monitoring stack, as the rule is rolled out cluster-wide when the label is applied.
Affected Products: https[:]//access[.]redhat[.]com/security/cve/CVE-2024-13484
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
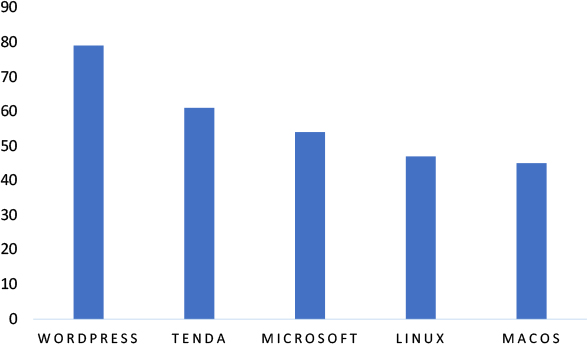
ETLM Assessment
Vulnerability in Argo CD can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of Argo CD is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding declarative continuous delivery processes for Kubernetes, whether used as a standalone tool or as part of a CI/CD workflow, across different geographic regions and sectors.
DragonForce Ransomware attacked and published the data of PT PINS Indonesia
Summary:
Recently, we observed that DragonForce Ransomware attacked and published the data of PT PINS Indonesia(www[.]pins[.]co[.]id) on its dark web website. PT PINS Indonesia is a subsidiary of PT Telkom Indonesia Tbk, focusing on the integration of devices and networks within the telecommunications and information technology sectors. The company offers a range of services, including Managed Mobility Services, Managed Machine-to-Machine (M2M) Solution Services, and Managed Customer Premises Equipment (CPE) Services. The ransomware attack resulted in a data leak containing confidential and sensitive organizational information. The total size of compromised data is approximately 362.14 GB.

Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, DragonForce represents a significant threat in the ransomware landscape due to its advanced operational methods and extensive use of modified ransomware tools. As it continues to target high-profile organizations globally, ongoing vigilance and proactive cybersecurity strategies will be essential for mitigating risks associated with this formidable threat actor.
Organizations should remain alert to the evolving tactics employed by groups like DragonForce to protect their sensitive data and maintain operational integrity.
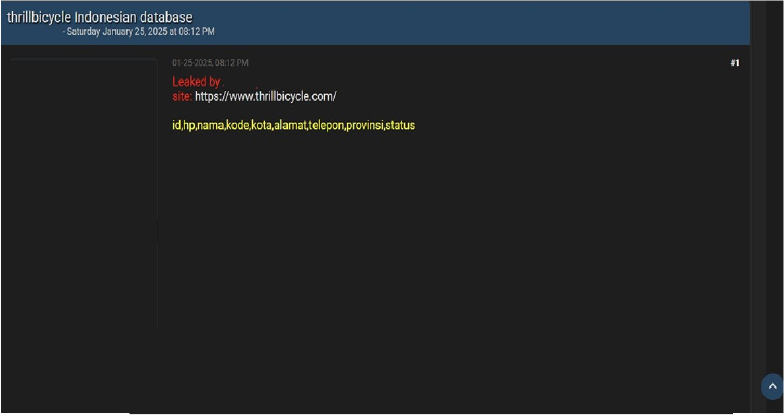
Thrill Bicycle Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data leak related to Thrill Bicycle (https://www[.]thrillbicycle[.]com) in an underground forum. Thrill Bicycle is a company specializing in the design and manufacture of bicycles tailored to the geometry of Asian riders. The leaked data includes ID, HP (phone number), name, code, city, address, telephone, province, and status. The breach has been linked to a threat actor identified as “AldzzXploit.”
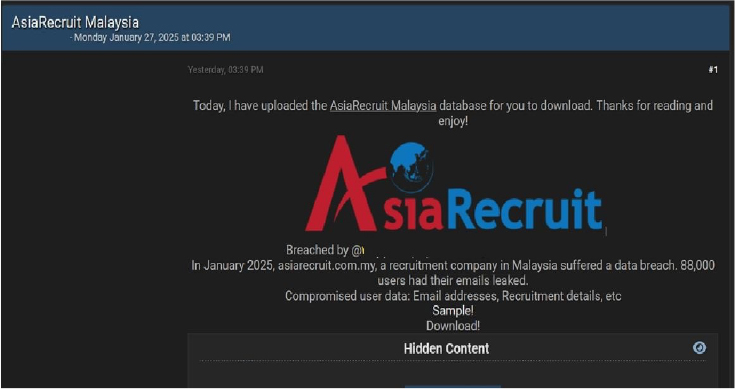
AsiaRecruit Malaysia Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data leak related to AsiaRecruit Malaysia (https[:]//www[.]asiarecruit[.]com[.]my) in an underground forum. Asia Recruit Malaysia is a premier recruitment agency with an expanding footprint across Asia. Serving a diverse range of industries, including Manufacturing, FMCG, Banking & Finance, IT, Oil & Gas, and Telecommunications, the agency has successfully placed countless professionals in roles across various sectors. The compromised user data includes email addresses, recruitment details, and other information. A total of 88,000 user emails have been leaked. The breach has been attributed to a threat actor known as “IntelBroker.”
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data.
Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
“IntelBroker” represents a significant threat within the cybersecurity landscape due to its sophisticated tactics and high-profile targets. Organizations are advised to implement robust security measures such as access control, regular patch management, and employee training to mitigate risks associated with such threat actors. Continuous monitoring of emerging threats like IntelBroker will be essential for effective incident response strategies in the evolving cyber threat environment.
Recommendations: Enhance the cybersecurity posture by:
The CYFIRMA Research team observed a data leak related to Wattpad (https[:]//www[.]wattpad[.]com/) in an underground forum. Wattpad is an online platform and community that enables users to read and publish original stories across various genres, including romance, teen fiction, and fan fiction. Wattpad has grown into a global hub for writers and readers. The platform boasts over 90 million monthly users and hosts more than 665 million story uploads. The compromised data includes the username, hashbcrypt, email, IP address, and other information, such as city, display name, or no additional details, along with the country. The breach has been attributed to a threat actor known as “CountySorter.”

The CYFIRMA Research team observed a data leak related to Tidtangstudio (https[:]//www[.]tidtangstudio[.]com/) in an underground forum. TIDTANG STUDIO is an architecture firm based in Bangkok, Thailand. They specialize in architectural and interior design, with a particular focus on the renovation of heritage buildings into hospitality spaces, such as hostels and hotels. The compromised data includes the ID, author, author email, author URL, IP address, date, amount, content, and other sensitive and confidential information. The breach has been attributed to a threat actor known as “Varun”.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
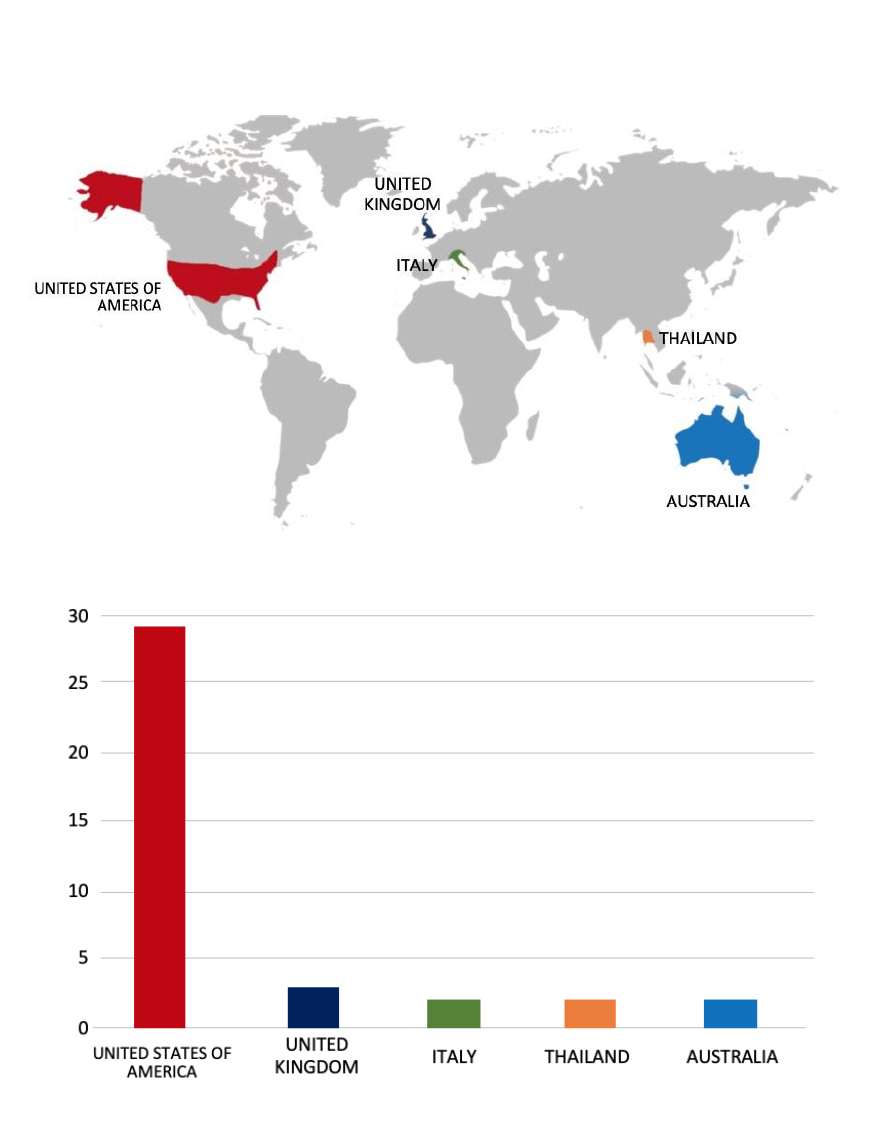
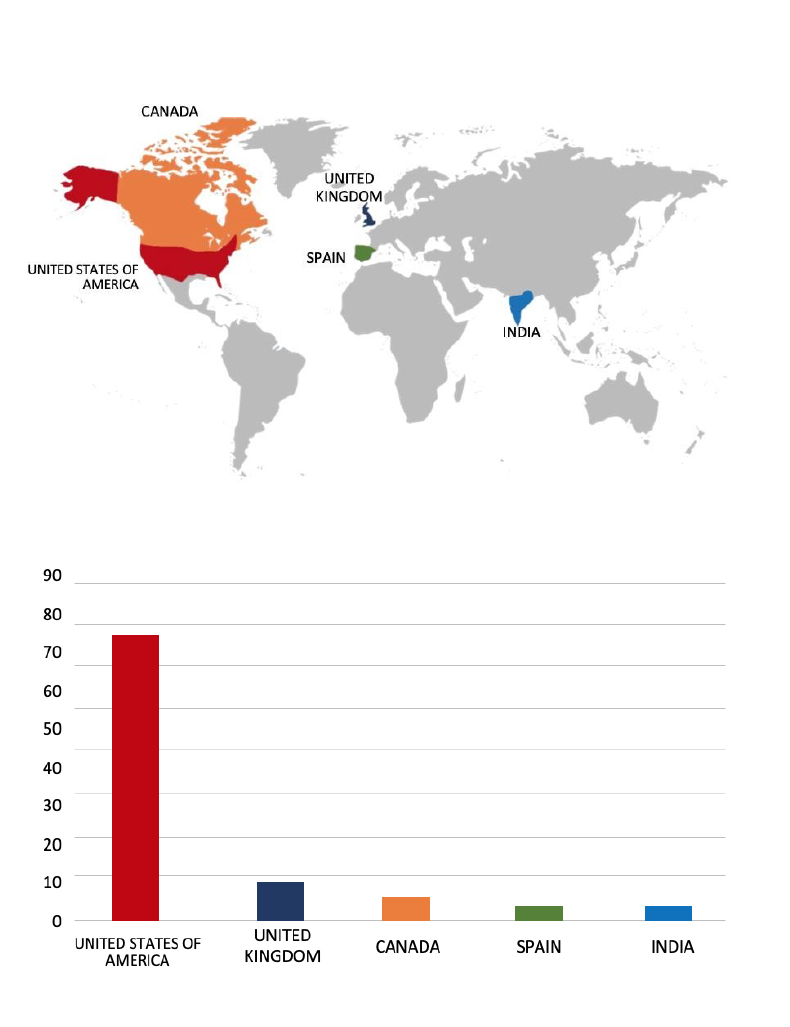
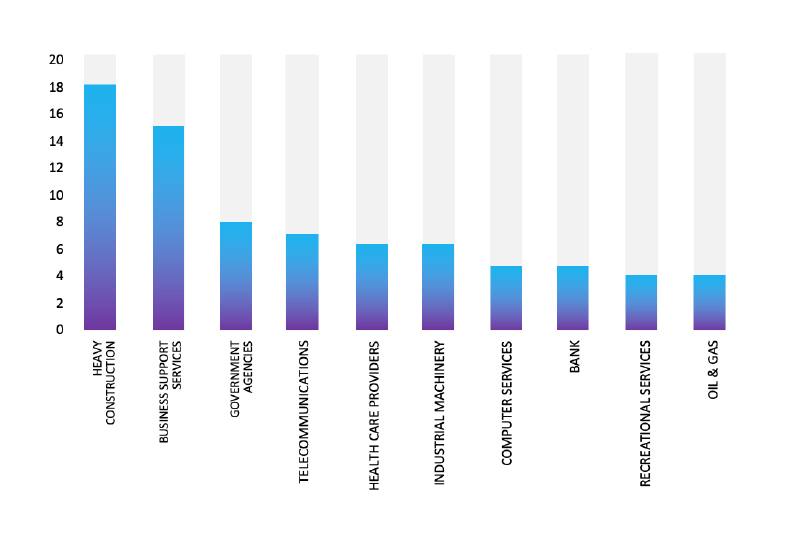
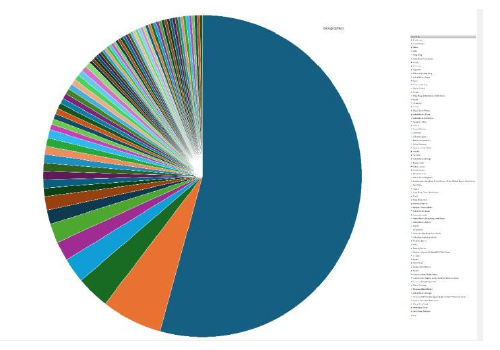
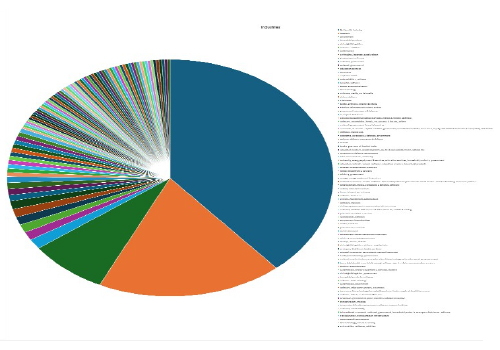
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.