



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
Target Geography: Australia, Austria, Chile, Canada, France, Germany, Italy, United States, United Kingdom, Netherlands, Spain, Switzerland.
Target Industry: Business Services, Consumer Services, Education, Food & Beverage, Government, Manufacturing, Software.
CYFIRMA Research and Advisory Team has found a new ransomware known as Rhysida while monitoring various underground forums as part of our Threat Discovery Process.
Relevancy: From the onset of its operation, the ransomware has targeted various industries, recent victims include:
This ransomware specifically targets the widely used Windows Operating System, which is prevalent across numerous industries and organizations.
Rhysida is a recently emerged ransomware family, written in C++.
The team presents itself as a “cybersecurity team” aiming to assist their targets by identifying vulnerabilities in their systems and emphasizing the potential consequences of these security issues. Ransomware is deployed through diverse methods, and one of the common approaches involves leveraging phishing campaigns.
The group adopts a similar approach to modern-day multi-extortion groups by coercively warning victims of potential public distribution of the exfiltrated data, aiming to pressure them into compliance.
When executed, the ransomware initiates a cmd.exe window, scanning through all files on local drives. Once the files are encrypted, the ransomware appends the “.rhysida” extension to them. The ransom notes generated by the ransomware are created as PDF documents with the name
“CriticalBreachDetected.pdf” and are saved within the affected folders on the targeted drives.
Victims receive instructions to reach out to the attackers through a TOR-based portal, using the unique identifier provided in the ransom notes. The ransomware exclusively accepts BTC (Bitcoin) payments and guides victims on purchasing and utilizing BTC through the victim portal. To facilitate authentication and communication, victims are prompted to provide additional information through a form on the payment portal, using their unique ID.
The Ransomware payloads employ the ChaCha20 encryption algorithm for encrypting files., which is much faster than more commonly used algorithms employed by ransomware operators.
The Rhysida developers leveraged the functionality of the open-source library called LibTomCrypt to construct the encryption modules within the ransomware’s payload. After successfully encrypting files using the Chacha20 encryption algorithm, the authors employed RSA-4096-OAEP to encrypt the Chacha20 keys.
When keys get encrypted with RSA, the authors use the CHC hash as entropy for the cipher IVs.
Upon execution, Rhysida excludes files with the following extensions from encryption:
.bat, .bin, .cab, .cmd, .com, .cur, .diagcab, .diagcfg, .diagpkg, .drv, .dll, .exe, .hlp, .hta, .ico, .lnk, .ocx, .ps1, .psm1, .scr, .sys, .ini, Thumbs.db, .url, .iso
Rhysida excludes the following directories:

Screenshot of a Ransom note of Rhysida Ransomware. (Source: Surface Web)
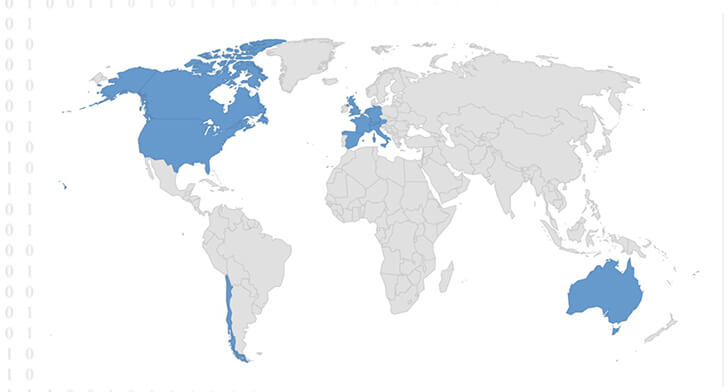
Countries Targetted by Rhysida Ransomware.
Insights:
Following are the TTPs based on MITRE Attack Framework.
| Sr. No. | Tactics | Techniques/Sub-Techniques |
| 1 | TA0001: Initial Access | T1566: Phishing |
| 2 | TA0002: Execution | T1059: Command and Scripting Interpreter T1129: Shared Modules |
| 3 | TA0003: Persistence | T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| 4 | TA0004: Privilege Escalation | T1055: Process Injection T1055.003: Process Injection: Thread Execution Hijacking T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| 5 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information T1027.005: Obfuscated Files or Information: Indicator Removal from Tools T1036: Masquerading T1055: Process Injection T1055.003: Process Injection: Thread Execution Hijacking T1497: Virtualization/Sandbox Evasion T1564: Hide Artifacts T1564.004: Hide Artifacts: NTFS File Attributes T1620: Reflective Code Loading |
| 6 | TA0007: Discovery | T1010: Application Window Discovery T1057: Process Discovery T1082: System Information Discovery T1083: File and Directory Discovery T1497: Virtualization/Sandbox Evasion T1518.001: Software Discovery: Security Software Discovery |
| 7 | TA0009: Collection | T1005: Data from Local System T1119: Automated Collection |
| 8 | TA0011: Command and Control | T1071: Application Layer Protocol T1071.001: Application Layer Protocol: Web Protocols |
| 9 | TA0040: Impact | T1486: Data Encrypted for Impact |
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
Type: Trojan
Objective: Stealing Banking Credentials & Financial Information Stealing
Target Geography: U.S, U.K, Germany, Austria, and Switzerland
Target Industry: Banking sector Target
Technology: Android
Active Malware of the Week
This week “Anatsa” is trending.
Researchers have discovered a new mobile malware campaign targeting online banking customers in the United States, United Kingdom, Germany, Austria, and Switzerland. The campaign utilizes an Android banking trojan called ‘Anatsa’ and the attackers are distributing their malware via the Play Store, Android’s official app store, and already have over 30,000 installations via this method alone.
The malware campaign involved malicious apps disguised as PDF viewers, office suites and productivity tools. Despite removals by Google, new droppers were consistently uploaded by the attackers. The dropper apps fetched Anatsa payload from GitHub, pretending to be text recognizer add-ons. Anatsa then collected sensitive financial data through phishing overlays and keylogging, targeting nearly 600 banking apps worldwide. The trojan automated fraudulent transactions using the stolen information, making detection by anti-fraud systems challenging. Stolen funds were converted to cryptocurrency and transferred through a network of money mules, with a portion kept by the mules as revenue and the remainder sent to the attackers.
In March 2023, Researchers discovered a new campaign by the Anatsa malware after a six-month break. The campaign involved a dropper application disguised as a PDF reade on the Google Play Store. Once installed, the dropper would request a download URL from a GitHub page, obtaining the payload that masqueraded as an add-on. This technique was consistent with previous campaigns by Anatsa.
After the initial dropper posing as a PDF viewer was reported and removed from the Google Play Store, the attackers persisted and released another dropper in the form of a PDF viewer one month later. This indicated a continuation of the same campaign, with the payloads still disguised as add-ons. The observed selection of disguises for these malicious applications confirms the ongoing trend we notice on Google Play. Following the restriction of the “REQUEST_INSTALL_PACKAGES” permission, droppers tend to mimic applications associated with file management.
The actors behind the Anatsa campaign were able to release multiple droppers on the Google Play Store, even after some were reported and removed. Despite the removal of certain droppers, the attackers quickly released new ones, with a turnaround time of a few days to a couple of weeks. Additionally, at the time of writing, a new Anatsa dropper had been discovered and was still online. The speed and persistence of the attackers in publishing new droppers demonstrate their determination to continue the distribution campaign.
During the Anatsa campaign, each dropper released on the Google Play Store was updated after its initial publication, likely to add additional malicious functionality. The actors behind the campaign employed multiple developer accounts to publish several apps simultaneously, with only one acting as the malicious dropper while the others served as backups. This tactic enabled the attackers to maintain long-running campaigns and minimize the time required to publish new droppers and continue the distribution of the malware.
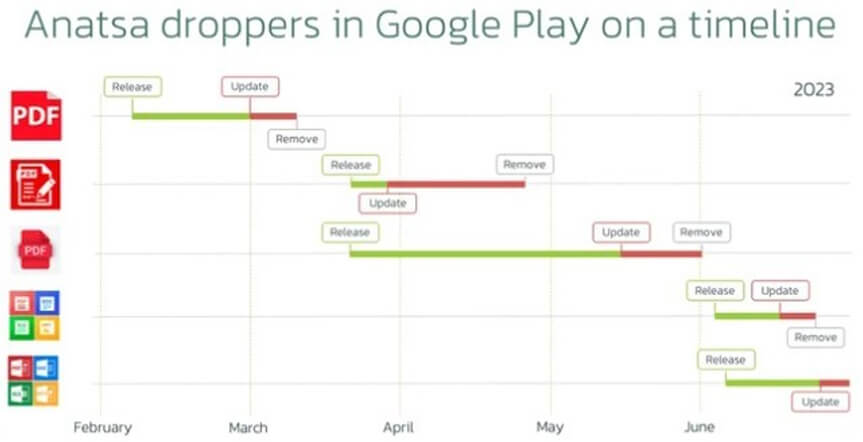
The Anatsa malware campaign begins by distributing the payload through malicious apps on the Google Play Store. Victims are led to these apps through deceptive advertisements that appear less suspicious as they direct users to the official store.
Once infected, Anatsa collects sensitive information using overlay attacks and keylogging, including credentials, credit card details, and payment information. This data is then used by the attackers to engage in Device-Takeover Fraud (DTO) and perform transactions on behalf of the victims. The fact that the transactions are initiated from the same device used by the targeted bank customers makes it challenging for banking anti-fraud systems to detect fraudulent activity.
Researchers monitoring the Anatsa malware campaign since 2020 and has observed changes in the attackers’ focus and target lists over time. In the latest iteration of the campaign, there is a strong emphasis on targeting banking institutions in the DACH region, particularly in Germany. This is reflected in the regions where the distribution droppers are released. However, Anatsa remains active in the US and UK as well. The target list has expanded to include more than 90 new applications compared to the previous year, with additions from countries such as Germany, Spain, Finland, South Korea, and Singapore.
While the droppers may not be distributed in all these countries, it indicates the attackers’ plans to potentially target those regions and gain insights into the internal structure of banking applications. Additionally, the targeting of significant minorities in these countries cannot be ruled out as a potential motive.
Indicators of Compromise
Kindly refer to the IOCs Section to exercise controls on your security systems.
1. Weekly Attack Type and Trends
Chinese APT Camaro Dragon aka Mustang Panda Strikes Health Care Industry
Summary:
A recent cyber-attack on a European hospital revealed that the observed malicious activity was likely unintended and resulted from the widespread propagation of Camaro Dragon’s self-propagating malware through USB drives. Camaro Dragon, a Chinese- based espionage threat actor, primarily targets Southeast Asian countries and associated foreign entities. The threat actor’s tactics, techniques, and procedures (TTPs) and resources bear resemblance to those of other Chinese threat actors, namely Mustang Panda and LuminousMoth. During the recent campaign, multiple updated versions of the malware toolset were identified, featuring similar capabilities for spreading via USB. These tools, named WispRider and HopperTick, are linked to other recently discovered tools, attributed to the same threat actor, including a Go- based backdoor known as TinyNote and a malicious router firmware implant called HorseShell. These tools share infrastructure and operational objectives. The primary variant of the malware, WispRider, has undergone significant revisions. In addition to its backdoor functionalities and USB-propagation abilities through the HopperTick launcher, the payload incorporates additional features. Notably, it includes a bypass mechanism for SmadAV, a popular antivirus solution in Southeast Asia. The malware also utilizes DLL-side-loading techniques, using components from security software such as G-DATA Total Security, as well as two prominent gaming companies, Electronic Arts and Riot Games.
Insights:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
North Korean hackers eavesdropping on individuals in South Korea
Ukrainian hackers break into Russian radio broadcasts to sow panic
Ukrainian cyber auxiliaries have recently been increasingly targeting Russian radio broadcasts in cyber-enabled information operations, inserting messages; exploiting the chaos in informational space in the recent mutiny by part of the Russian military. The Russian-army-supported and armed private military company Wagner under the leadership of businessman Yevgeny Prigozhin with ties to the Kremlin has mutinied taken over a large Russian military command building and even staged several hundred-kilometer drives towards the Russian capital, during which it shot down multiple aircraft, operated by the Russian army. The pro-Ukranian hacks preceded the mutiny, however, the hackers were also able to exploit the chaos in the informational space, created by a lack of coordinated response by the Russian government and inserted a message that Russia had declared full mobilization and martial law in response to a large-scale invasion of Russia. The operation gained enough traction to draw an official denial from Kremlin spokesman; Dmitry Peskov.
Intel report on a Russian foreign intelligence run threat actor
Researchers have recently published an intel report, profiling NOBELIUM, currently known as Midnight Blizzard, which is an APT run by SVR – the Russian Foreign Intelligence Service. According to the intel, this actor targets government agencies, non-governmental organizations, and diplomatic personnel in an intelligence-gathering operation. The actor is sophisticated enough to utilize diverse initial access methods, ranging from stolen credentials to supply chain attacks, exploitation of on-premise environments to laterally move to the cloud, exploitation of service providers’ trust chain to gain downstream customers, as well as ADFS malware known as FOGGYWEB and MAGICWEB.
Update on a recent Chinese state-sponsored hack
Researchers have recently provided details on the vulnerability found in Barracuda’s Email Security Gateway (ESG) which is suspected to be perpetrated by UNC4841, a known and aggressive and highly skilled actor conducting targeted activity most likely on behalf of the Chinese government. The actor has recently been focusing on targets in the United States, Norway, Taiwan, and Poland, mostly attacking academic institutions, defense industrial bases, and governmental organizations in an attempt at cyber-espionage-enabled data exfiltration. In the past, the threat actor also exhibited a sustained focus on scientific research, energy entities, and public health data.
Hill International is Impacted by Play Ransomware
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in the dark forum that a company from The United States of America, (www[.]hillintl[.]com), was compromised by Play Ransomware. Hill International provides program and project management, construction management, cost engineering and estimating, quality assurance, inspection, scheduling, risk management, and claims avoidance to clients involved in major construction projects worldwide. The data breach includes sensitive and confidential information such as private and personal data, documents related to clients and employees, financial records, technical documentation, passports, identification cards, tax information, financial details, and more.
The following screenshot was observed published on the dark web:
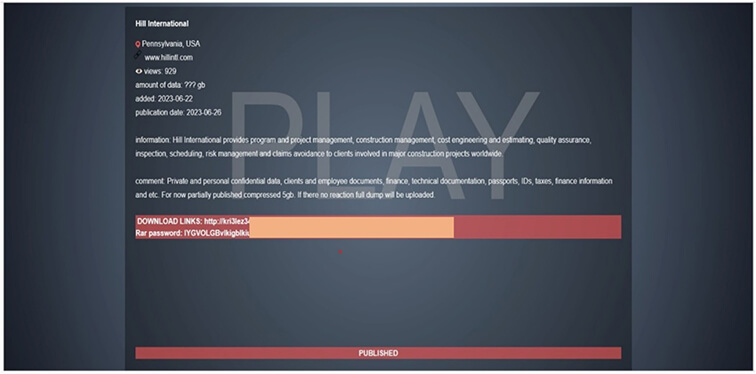
Source: Dark Web
Insights:
Vulnerability in DataEase
Summary:
DataEase could allow a remote authenticated attacker to bypass security restrictions, caused by improper authorization validation.
Insights:
The vulnerability exists due to improper access restrictions in the application deletion interface.
Impact:
A remote user can bypass implemented security restrictions and delete the application.
Affected Products: https[:]//github[.]com/dataease/dataease/security/advisories/GHSA- 4c4p-qfwq-85fj
Fort Worth, Texas Experiences Issues Due to Cyber Attack
Summary:
We have recently witnessed hackers successfully infiltrating a municipal website in Fort Worth, Texas, specifically designed to handle maintenance orders for various departments, such as transportation, public works, parks, and property management. The data that was leaked comprises various attachments, including photographs, spreadsheets, invoices documenting completed work, staff emails, PDF documents, and other relevant materials. The data leak encompasses an approximate size of 180GB in total. The attack has been attributed by officials to a threat actor group identified as SiegedSec. The data has been leaked by the group on their telegram channel SiegedSec. The threat actor is a self-proclaimed “hacktivist” group that emerged in February 2022. The group seems to be driven by the sheer enjoyment of the experience and the desire to gain recognition, by publicly ridiculing organizations that have inadequate information security measures in place. Evidently, the threat actors have acquired login details to infiltrate the website. Among the potential techniques employed are credential stuffing (testing stolen credentials or databases), phishing (sending deceptive links or attachments), password spraying (attempting common passwords), keylogging (recording keystrokes), or brute force (a method of systematically guessing passwords through trial and error).
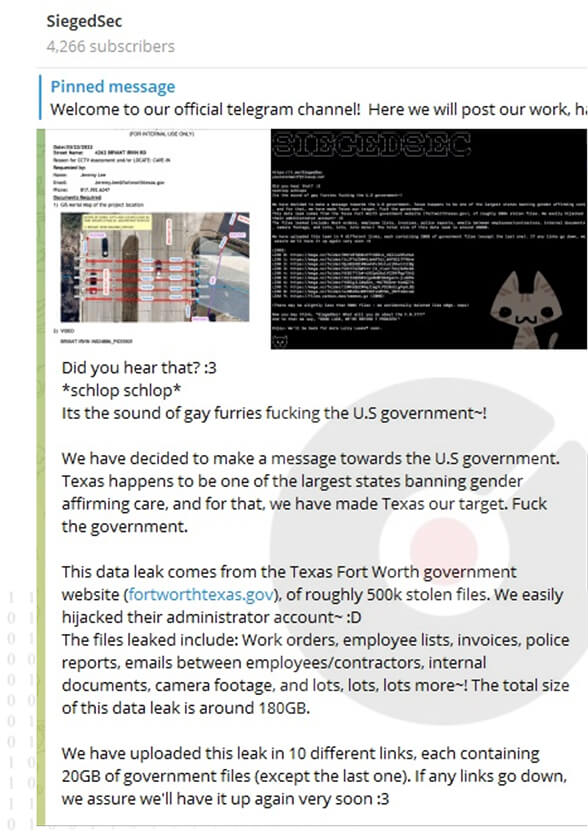
Source: Telegram channel
Insights:
The threat actor demonstrates a high level of proficiency in web attacks, as evidenced by their recent targeting of the Cauca government and the Colombian police’s website. Their capabilities are destructive in web attacks, indicating their ability to compromise websites and consistently leak substantial portions of database files.
SignifyCRM’s Data Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to SignifyCRM, {www[.]signifycrm[.]com}. SignifyCRM is a comprehensive Software-as-a-Service (SaaS) that users will find easy to use and can greatly improve sales and customer service operations. It has earned the trust of numerous client organizations that include industry leaders. The compromised data comprises various sensitive information, such as user IDs, first names, last names, usernames, emails, passwords, mobile phone numbers, office phone numbers, and other confidential details. The total size of the compromised data amounts to approximately 1.7 gigabytes (GB).
Source: Underground forums
Insights:
Financially driven cybercriminals are perpetually seeking out exposed and susceptible systems and applications, leveraging opportunistic tactics. Most of these attackers frequent underground forums, engaging in discussions and illicit transactions involving stolen digital assets. In contrast to ransomware or extortion groups, who often publicize their attacks, these individuals prefer to operate discreetly. By exploiting unpatched systems or vulnerabilities in applications, they infiltrate and pilfer valuable data.
Subsequently, this stolen data is advertised, resold, and repurposed by other attackers in their own malicious endeavors.
CYFIRMA Research team observed a potential data leak related to Hyperface, (www[.]hyperface[.]co). Hyperface is a modern transaction credit platform founded in 2021 and headquartered in India. The exposed data encompasses a wide range of sensitive and confidential information, stored in SQL format, with a cumulative size of 3.5 GB.
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS