



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found AttackNew ransomware while monitoring various underground forums as part of our Threat Discovery Process.
AttackNew
Researchers have discovered a new ransomware named AttackNew, which is part of the MedusaLocker ransomware family. This ransomware encrypts files and appends a “.attacknew1” extension to their names, the number in the extension may varying by variant.
AttackNew also generates a ransom note titled “how_to_back.html,” indicating that it targets large organizations and employs double-extortion tactics.

Screenshot of files encrypted by this ransomware(Source: Surfaceweb)
The ransom note from AttackNew informs the victim that their company network has been breached, with files encrypted using RSA and AES algorithms. It warns against modifying the locked files or using third-party recovery tools, as this will make them irrecoverable.
The note also reveals that confidential and personal data was stolen from the network. If the ransom demands are not met, the stolen data will be leaked online or sold. They also state that the ransom amount will increase if contact is not established within 72 hours.
Victims can test the decryption process by sending three non-essential encrypted files before making a payment.
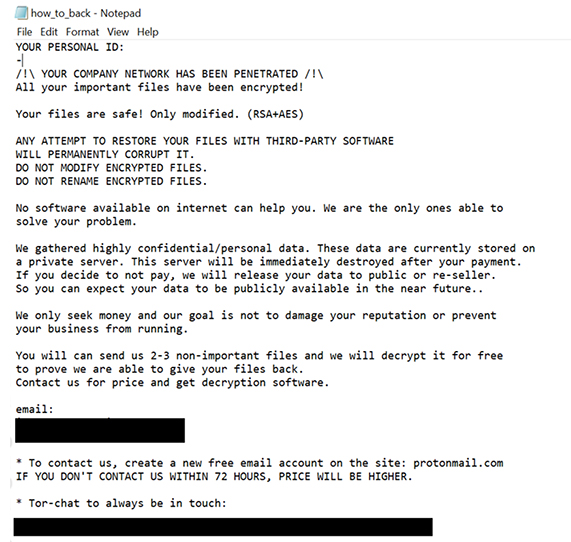
Screenshot of Text presented in AttackNew ransomware’s ransomnote (Source: SurfaceWeb)
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0001: Initial Access | T1091: Replication Through Removable Media |
| 2 | TA0002: Execution | T1129: Shared Modules |
| 3 | TA0003: Persistence | T1543.003: Create or Modify System Process: Windows Service |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 4 | TA0004: Privilege Escalation | T1055: Process Injection |
| T1134: Access Token Manipulation | ||
| T1543.003: Create or Modify System Process: Windows Service | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 5 | TA0005: Defense Evasion | T1027.005: Obfuscated Files or Information : Indicator Removal from Tools |
| T1036: Masquerading | ||
| T1055: Process Injection | ||
| T1134: Access Token Manipulation | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1202: Indirect Command Execution | ||
| T1222: File and Directory Permissions Modification | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1564.003: Hide Artifacts: Hidden Window | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 6 | TA0006: Credential Access | T1056.001: Input Capture: Keylogging |
| 7 | TA0007: Discovery | T1010: Application Window Discovery |
| T1012: Query Registry | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1120: Peripheral Device Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| T1614: System Location Discovery | ||
| 8 | TA0008: Lateral Movement | T1091: Replication Through Removable Media |
| 9 | TA0009: Collection | T1056.001: Input Capture: Keylogging |
| T1074: Data Staged | ||
| 10 | TA0011: Command and Control | T1071: Application Layer Protocol |
| 11 | TA0040: Impact | T1485: Data Destruction |
| T1486: Data Encrypted for Impact | ||
| T1489: Service Stop |
Relevancy and Insights:
ETLM Assessment:
Based on available information, CYFIRMA’s assessment suggests that the AttackNew ransomware, a variant of MedusaLocker, is likely to target economically developed regions, including the US, UK, Southeast Asia, Europe, and others, to maximize ransom demands. Given MedusaLocker’s history of consistently targeting industries such as Manufacturing, Finance, Healthcare, government and more due to their data sensitivity and financial capacity to pay substantial ransoms, there is medium confidence that AttackNew will continue this trend.
SIGMA Rule:
title: Suspicious desktop.ini Action tags:
– attack.persistence
– attack.t1547.009 logsource:
product: windows category: file_event
detection: selection:
TargetFilename|endswith: ‘\desktop.ini’ filter_generic:
Image|startswith:
– ‘C:\Windows\’
– ‘C:\Program Files\’
– ‘C:\Program Files (x86)\’ filter_jetbrains:
Image|endswith: ‘\AppData\Local\JetBrains\Toolbox\bin\7z.exe’ TargetFilename|contains: ‘\JetBrains\apps\’
filter_upgrade:
TargetFilename|startswith: ‘C:\$WINDOWS.~BT\NewOS\’ condition: selection and not 1 of filter_*
falsepositives:
– Operations performed through Windows SCCM or equivalent
– Read only access list authority level: medium
(Source: SurfaceWeb)
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Trojan
Objective: Stealing financial information, Remote Access Target Technology: Android OS
Target Industries: Financial Institutions, Cryptocurrency Exchanges Target Geographies: Italy and Spain
Active Malware of the Week
This week “Copybara” is trending.
Copybara
Researchers recently identified a new variant of Copybara, an Android malware family that first emerged in November 2021. This variant has been active since November 2023. This malware is primarily distributed through voice phishing (vishing) attacks, where victims receive phone instructions to install the malware. It then uses the MQTT protocol to communicate with its command-and-control (C2) server and exploits Android’s Accessibility Service to gain granular control over the infected device. This variant of Copybara was developed using B4A, a legitimate framework typically used for creating Android applications. Copybara frequently impersonates popular financial institution apps in Italy and Spain, and it downloads phishing pages that imitate cryptocurrency exchanges and global financial institutions, using legitimate logos and names to trick victims into entering their credentials, which are then stolen. Some versions of Copybara have even been found impersonating Google Chrome and an IPTV application, further highlighting the malware’s adaptability and widespread targeting tactics.

Fig: Logos of financial institutions impersonated by Copybara.
Technical Analysis
The exact method used to lure victims into downloading this specific variant remains unknown. However, once the application is launched, a message screen crafted by the attacker prompts the user to enable the Accessibility Service permission. Although this feature is intended to aid users with disabilities, it can give attackers extensive control over the device if activated. If Copybara is installed and permission is not granted, the malware continuously displays notifications and toast messages to pressure the user into enabling the service.

Fig: Copybara launch screen without the accessibility permission enabled (Left), Copybara after the Accessibility Service feature is enabled (Right)
Once the Accessibility Service is enabled, Copybara restricts access to certain settings, preventing the user from uninstalling the malware. In the background, Copybara’s behavior is guided by its configuration, which directs it to download phishing pages from the C2 server. The C2 server responds with a ZIP file containing fake login pages that imitate popular cryptocurrency exchanges and financial institutions. These phishing pages are crafted to trick users into entering their sensitive information.
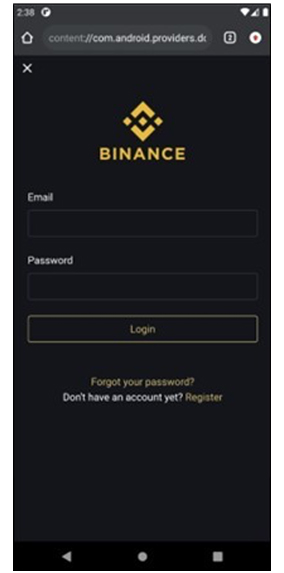
Fig: Copybara phishing page designed to look like a popular cryptocurrency exchange.
Finally, the application establishes a connection to an MQTT server on port 52997 and subscribes to the “commands_FromPC” queue. This allows Copybara to receive and process up to 59 supported commands sent by the C2 server.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that as online banking and digital payments rapidly advance, especially in regions like Asia, the threat landscape for mobile malware like Copybara is set to expand significantly. The increasing reliance on mobile devices for both professional and financial activities makes employees particularly vulnerable to sophisticated social engineering attacks, such as vishing. As a result, organizations that do not enhance their cybersecurity training and mobile security protocols will face increased risks of data breaches and financial losses. Moreover, the growing popularity of digital payment methods, including wallets and QR code payments, offers new avenues for malware like Copybara to exploit, potentially leading to widespread financial fraud and a loss of trust in emerging digital financial systems. To effectively combat these evolving threats, organizations will need to adopt a proactive and comprehensive cybersecurity strategy that addresses both technological vulnerabilities and the human element.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
New Insights into Attacker Infrastructure Revealed by Moon Peak Malware from North Korean Actors “UAT-5394” Likely Kimsuky
Summary:
A new remote access trojan (RAT) named “Moon Peak,” is based on the Xeno RAT malware and appears to be developed by a North Korean threat group designated UAT-5394 (Kimsuky). This RAT has evolved from an earlier variant of Xeno RAT and shows some similarities to the tactics, techniques, and procedures (TTPs) used by the North Korean APT group Kimsuky. UAT-5394 has previously used Quasar RAT but has transitioned to Moon Peak, indicating either a rebranding within Kimsuky or a distinct North Korean group adopting Kimsuky’s methodologies.
Research has revealed that UAT-5394 employs sophisticated infrastructure for staging and testing Moon Peak, including the use of Command and Control (C2) servers for malicious activities and VPN nodes for accessing and managing their operations.
The UAT-5394 activity over the past two months shows the interconnections between the several servers used by this threat actor.
Since June 11, 2024, UAT-5394 has transitioned from using legitimate cloud storage to managing its own infrastructure, including remote access and Command and Control (C2) servers, payload-hosting sites, and test virtual machines, likely to evade potential disruptions from cloud providers. A key server, 95[.]164[.]86[.]148, initially served as a Moon Peak C2 server before being accessed for Remote Desktop Protocol (RDP) connections and transitioning to manage another C2 server, 167[.]88[.]173[.]173. This server, which frequently changed operating systems, was under UAT-5394’s control between June 30 and July 8, 2024, and hosted Moon Peak v2 malware. During this period, the server was also accessed by other IP addresses used for testing Moon Peak implants. Following this, 104[.]194[.]152[.]251 emerged as a new Moon Peak C2 server, replacing previous domains and IPs, with further testing and setup conducted on 91[.]194[.]161[.]109, the latest C2 server. This server, operational by July 16, 2024, hosts various malicious artifacts and scripts used to deploy and test Moon Peak malware, indicating ongoing development and operational refinement by UAT-5394.
The analysis of UAT-5394’s Moon Peak campaign reveals that the threat actors have extensively used virtual machines (VMs) to test and refine their malware and infection chains. VMs with IPs 45[.]87[.]153[.]79 and 45[.]95[.]11[.]52 have been utilized to interact with various Moon Peak C2 servers over multiple ports since July 2, 2024, while a third VM, 80[.]71[.]157[.]55, has been used both for testing and for RDP access to C2 servers. The Moon Peak malware has shown a significant evolution from its Xeno RAT origins, with each variant incorporating incremental obfuscations and changes to evade detection and ensure compatibility with specific C2 server versions. This evolution reflects the threat actors’ ongoing efforts to enhance their malware’s stealth and functionality. Initial Moon Peak versions, based on Xeno Rat’s open-source code, have been progressively modified by UAT-5394, leading to the creation of distinct Moon Peak variants, as evidenced by the differences between Moon Peak v1 and v2. Understanding Xeno Rat’s architecture—comprising a client stub, main server component, and plugins—provides context for the observed modifications and strategic evolution of Moon Peak malware.
Relevancy & Insights:
UAT-5394, known for its North Korean affiliation, has a history of conducting cyber- espionage operations targeting high-value sectors. Past attacks have involved sophisticated phishing campaigns and the deployment of various RATs, including Quasar RAT and earlier variants of Xeno RAT. These campaigns are aimed at infiltrating government, defence, and high-tech organizations, aligning with North Korea’s strategic interests in gathering sensitive information and leveraging espionage for political and economic gains.
The current use of “Moon Peak,” an evolved version of Xeno RAT, represents a significant escalation in their tactics. Moon Peak’s advanced features and custom Command and Control (C2) infrastructure indicate a shift towards more resilient and stealthy operations. This evolution correlates with their historical pattern of continually adapting malware to evade detection and increase operational effectiveness.
ETLM Assessment:
UAT-5394, a North Korean threat actor, primarily targets East Asian countries, with a focus on South Korea, and spans various strategic sectors, including government, defence, technology, and finance. Initially leveraging cloud services, they have shifted to using custom-built infrastructure and virtual machines for testing and deploying their malware. UAT-5394’s current primary tool is “Moon Peak,” an advanced remote access trojan (RAT) derived from Xeno RAT, showcasing significant evolution with sophisticated obfuscation and custom Command and Control (C2) protocols. Previously, they employed Quasar RAT and earlier Xeno RAT variants, reflecting a trend towards increasingly resilient and evasive malware. The threat landscape indicates that UAT-5394 will continue to advance its tactics, introducing more complex malware and expanding its target scope beyond East Asia. Organizations must remain vigilant as UAT-5394 is likely to enhance their malware’s stealth and operational capabilities, making ongoing adaptation and robust cybersecurity measures crucial.
Recommendations:
MITRE ATT&CK Tactics and Techniques
| Tactics | ID | Technique |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Discovery | T1046 | Network Service Discovery |
| Discovery | T1082 | System Information Discovery |
| Lateral Movement | T1021.001 | Remote Services: Remote Desktop Protocol |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| Command and control | T1071 | Application Layer Protocol |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Chinese hackers exploiting a zero-day at home-office devices
Researchers have uncovered a zero-day vulnerability being actively exploited in the SD-WAN management platform, Versa Director. Versa has responded by releasing a patch, urging users to upgrade to version 22.1.4 or later. This flaw enables attackers to execute code by uploading Java files camouflaged as PNG images.
During their investigation, the researchers identified a custom-built web shell designed to leverage this vulnerability, which they have linked to the Chinese threat actor Volt Typhoon. Global telemetry analysis revealed that the actor-controlled small- office/home-office devices and exploited this zero-day vulnerability against four U.S. victims and one non-U.S. victim, primarily within the Internet service provider (ISP), managed service provider (MSP), and information technology (IT) sectors this past summer.
ETLM Assessment:
This spring, U.S. Secretary of State Antony Blinken traveled to Beijing in the latest of a series of high-level meetings between Chinese and U.S. leadership to ease tensions after China complained about the movement of US Navy ships in international waters around Taiwan. That followed last year’s campaigns in the South China Sea regions by other Chinese actors like the Volt Typhoon. Its hacking campaigns have been focused on the countries surrounding the South China Sea, where China presses territorial claims on countries like the Philippines, Vietnam or Indonesia, as well as on the United States, with which China is in conflict over primacy in the region and global affairs as a whole. Guam; a US territory in the Western Pacific that is home to significant US military bases, has allegedly been targeted. Chinese hackers have been lately mainly focusing on the defense industrial base, successfully compromising the networks of contractors to the Pentagon’s U.S. Transportation Command 20 times in a single year, while many other incursions have probably never been found. As we have warned in an earlier report, given the increasingly assertive Chinese posturing, it was likely that Beijing’s hackers were trying to position themselves in a way that could try to paralyze
U.S. critical infrastructure in case of an eruption of conflict between the two countries over the issue of Taiwanese or Philippine waters. An attempt to induce societal panic in their adversary in case of conflict is an inherent part of Chinese military doctrine and targeting of critical infrastructure on Guam could affect U.S. military operations in a significant way.
Seattle airport under cyber attack
Over the weekend, the Port of Seattle, which oversees Seattle-Tacoma International Airport, experienced a cyberattack that disrupted websites, email, and phone services. The airport advised passengers to arrive early and check-in online, as “technical issues” were affecting terminal screens displaying flight information. While the TSA confirmed that security operations remain unaffected, at least one airline is manually sorting over 7,000 checked bags that missed their flights due to the incident.
ETLM Assessment:
At the time of writing, not much is known about the attack, however in our report last year we had warned that the logistics industry, being a critical part of the infrastructure, confronts substantial risks from advanced threat actors. A correlation between the current geopolitical landscape and the most targeted countries remains evident. Moreover, Russia seems to be increasingly employing privateering actors, motivated by financial gains to put distance between Moscow and the global food insecurity. Such a trend is expected to continue as privateers are offered ever more leniency in the eyes of the Kremlin, the more global instability, the better the attention is deflected from its persecution of Ukraine, with fewer resources.
4. Rise in Malware/Ransomware and Phishing
The RansomHub Ransomware impacts the General Secretariat of the Military Service Council (Saudi Arabia)
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Saudi Arabia; the General Secretariat of the Military Service Council (Saudi Arabia), was compromised by the RansomHub Ransomware. The General Secretariat of the Military Service Council in Saudi Arabia is a governmental entity responsible for overseeing policies and regulations related to military personnel. It addresses matters such as recruitment, training, career progression, and the welfare of the armed forces. The council ensures the effective management of military human resources, enhancing the operational readiness and professional development of Saudi Arabia’s defense forces. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization. The total size of the compromised data is approximately 140GB.
The following screenshot was observed published on the dark web:
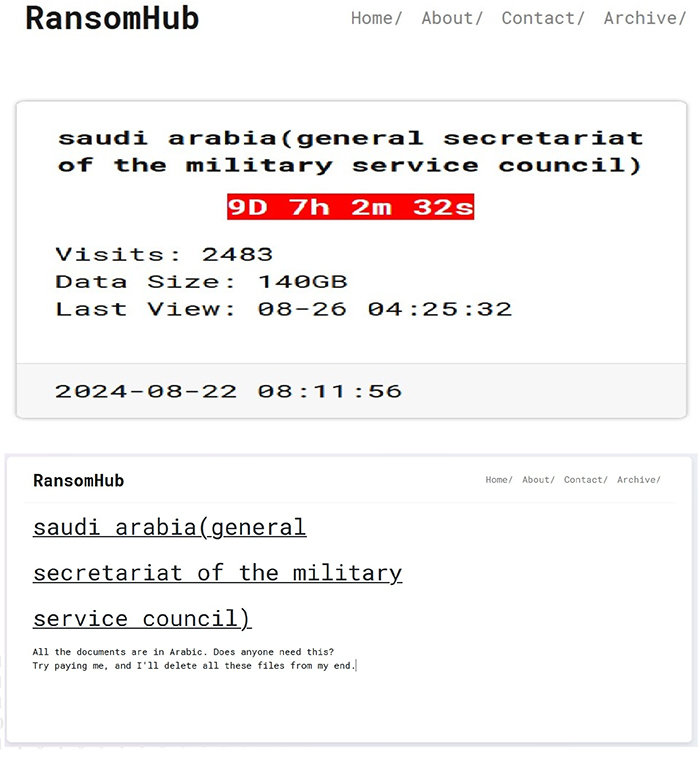
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
Based on recent assessments by CYFIRMA, RansomHub ransomware is expected to intensify its operations across various industries worldwide, with a notable focus on regions in the United States, Europe, and Asia. This prediction is reinforced by the recent attack on the General Secretariat of the Military Service Council from Saudi Arabia, highlighting RansomHub’s significant threat presence in the Middle East.
The KillSec Ransomware impacts Level SuperMind
Summary: From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from India; Level SuperMind (https[:]//level[.]game/), was compromised by the KillSec Ransomware. Level SuperMind is a wellness and fitness technology company in India. It focuses on enhancing mental and physical health through a mobile application that integrates neuroscience-backed routines. The app is designed to improve users’ overall well-being by offering a variety of features, including meditation sessions, journaling, workouts, yoga practices, and sleep stories. It emphasizes emotional intelligence and mindfulness, aiming to foster clarity, focus, memory, and creativity in users. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes Full names, Email addresses, Passwords, Device information, IP addresses, Geolocation, Payment details, and Operational data. The asking price for this compromised data is $25,000, with a special discount of $5,000 available for payments made within 24 hours.
The following screenshot was observed published on the dark web:
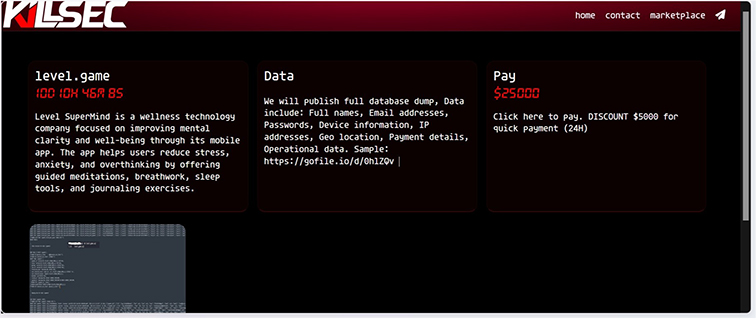
Source: Dark Web
Relevancy & Insights:
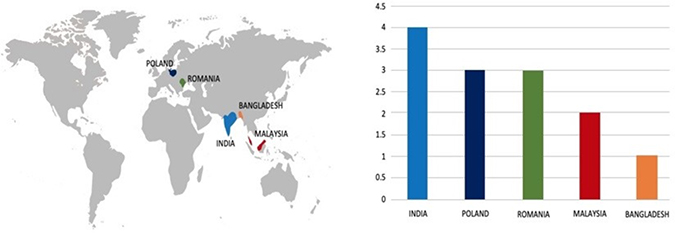
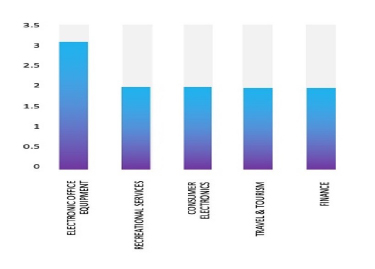
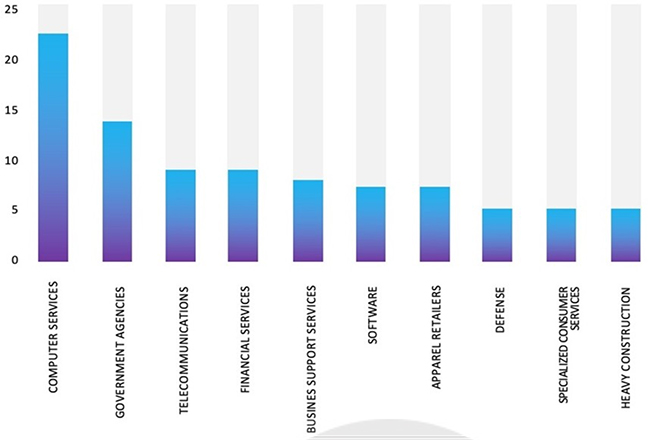
According to CYFIRMA’s assessment, the KillSec ransomware group is expected to continue targeting a wide range of industries worldwide. Their advanced tactics, such as exploiting website vulnerabilities and conducting credential theft, make them a significant threat to organizations with inadequate security measures in place.
Vulnerability in Versa Director ETLM
Summary:
The vulnerability allows a remote user to compromise a vulnerable system.
Relevancy & Insights:
The vulnerability exists due to insufficient validation of files during file upload.
Impact:
A remote authenticated user can upload a malicious file and execute it on the server.
Affected Products:
https[:]//versa-networks[.]com/blog/versa-security-bulletin-update-on- cve-2024-39717-versa-director-dangerous-file-type-upload-vulnerability/
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
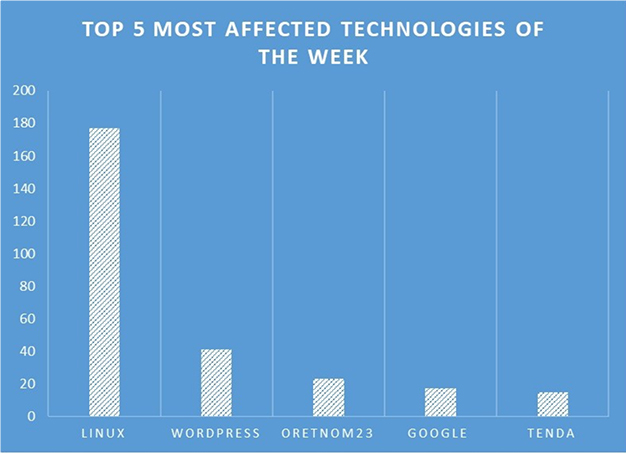
ETLM Assessment:
Vulnerability in Versa Director can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of Versa Director is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding the creation, automation, and delivery of network and security services using Versa WAN edge software, FlexVNF. This includes routing, advanced connectivity, and SD-WAN management across different geographic regions and sectors.
Fog Ransomware attacked and Published data of Hi-P International
Threat Actors: Fog Ransomware
Attack Type: Ransomware
Objective: Data Leak, Financial Gains Target Technology: Web Application Target Industry: Manufacturing
Business Impact: Operational Disruption, Data Loss, Financial Loss, Potential Reputational Damage
Summary:
Recently we observed that Fog Ransomware attacked and published data of Hi-P International(www[.]hi-p[.]com) on its dark web website. Hi-P International Group is a leading global manufacturer specializing in integrated electro-mechanical solutions across various industries, including telecommunications, lifestyle, computing, and automotive. Hi-P International Group excels in precision tooling, plastic molding, metal stamping, and electronic manufacturing services (EMS). They also provide services in industrial and product design, tool design, secondary operations, and supply chain management. The data leak, following the ransomware attack, encompasses sensitive and confidential information related to the organization. The total size of the compromised data is 22 GB.
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Fog Ransomware is likely to continue its global campaign, targeting a wide range of industries, with a heightened focus on the United States, Europe, and Asia. A recent attack on Hi-P International, a leading manufacturing company reflects the broader risk Fog presents to organizations worldwide, especially in regions where cyber threats are escalating.
Indonesian House of Representatives (DPR RI) Data Advertised on a Leak Site
Attack Type: Data Leak
Target Industry: Government
Target Geography: Indonesia
Objective: Data Theft, Financial Gains
Business Impact: Data Loss, Reputational Damage
Summary:
The CYFIRMA Research team observed a potential data sale related to the Indonesian House of Representatives (DPR RI)( www[.]dpr[.]go[.]id) in an underground forum. A threat actor claims to be selling a large database allegedly linked to the Indonesian House of Representatives (DPR RI). According to the actor’s announcement, the database includes details of 107 million users, with records dating to August 2024.
The database, described in the announcement, contains sensitive data fields, such as identity card numbers and personal transaction information. The threat actor is asking for $100,000 for the full database, with escrow services available for secure transactions. The data breach has been attributed to a threat actor identified as “Xobijahabi”.

Source: Underground Forums
Indonesian Ministry of Transportation data advertised on a Leak Site
Attack Type: Data Leak
Target Geography: Indonesia Target Industry: Government
Objective: Data Theft, Financial Gains
Business Impact: Data Loss, Reputational Damage
Summary:
The CYFIRMA Research team observed a potential data leak related to the Indonesian Ministry of Transportation(dephub)(www[.]dephub[.]go[.]id) in an underground forum. A threat actor known as “SILKFIN AGENCY” claims to have breached the Indonesian Ministry of Transportation’s official platform on August 20, 2024. This website manages the ministry’s Personnel Information System, which handles the administrative and personnel data of over 14,000 employees.
According to the actor, the compromised data includes sensitive information, such as employee IDs, birthdates, names, job titles, and more. The actor alleges that this data was extracted from the system, raising concerns about the security and privacy of the ministry’s staff.
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
According to CYFIRMA’s assessment, the threat actor known as ” Xobijahabi” poses a serious risk to organizations due to its financial motivations and ability to exploit vulnerable institutions. This actor is notorious for infiltrating organizations with weak security measures and profiting by selling stolen sensitive data on the dark web or underground forums. The typical targets of ” Xobijahabi” are institutions with inadequate cybersecurity defenses, making them particularly susceptible to the sophisticated cyberattacks orchestrated by this threat actor.
Recommendations: Enhance the cybersecurity posture by Updating all software products to their latest versions is essential to mitigate the risk of vulnerabilities being exploited. Ensure proper database configuration to mitigate the risk of database-related attacks. Establish robust password management policies, incorporating multi-factor authentication and role-based access, to fortify credential security and prevent unauthorized access.
The CYFIRMA Research team observed a potential data leak related to a Vietnamese IT Firm BPOTech. A threat actor has alleged that BPOTech, a company with over a decade of experience in providing IT services to Japanese firms, has suffered a data breach. The post, published on a dark web forum, claims that more than 20 million lines of data, including SQL files, have been leaked.
The threat actor’s post sheds light on the broader context of the Japanese IT industry, which is grappling with a severe shortage of human resources and rising labor costs, exacerbated by the country’s declining birthrate and aging population. As a solution, many Japanese firms have turned to offshore hiring, particularly in Asian countries like Vietnam, where labor costs and recruitment expenses are lower than in Japan. It seems that this “offshore hiring” is the motive behind the alleged breach.
Source: Underground forums
The CYFIRMA Research team observed a potential data sale related to SenangPay, Malaysia. In a dark web forum post, a threat actor has claimed responsibility for a data breach involving SenangPay, a prominent Malaysian payment solutions provider.
SenangPay is known for its payment solution catering to both online and offline transactions. The post alleges that the threat actor has obtained a vast amount of sensitive personal and financial information from the company’s systems.
The threat actor claims to have breached SenangPay, obtaining files that purportedly contain personally identifiable information (PII). The allegedly exposed data contains:
Names
Malaysian ID numbers Phone numbers
Email addresses
Business registration details Malaysian bank BIN numbers.
The breach is said to involve three SQL files, each containing extensive datasets:
Main SenangPay App SQL File: Comprising 97 tables out of the original 99, excluding two tables that allegedly contain non-essential API callback data.
Backup of SenangPay App SQL File: A backup version mirroring the contents of the main SQL file.
SQL File Related to SenangPay Zakat: Specific details regarding transactions and other data related to Zakat payments processed through SenangPay.
The threat actor is demanding 2 BTC for the data, offering to facilitate the transaction through escrow and giving priority to SenangPay. Interested parties can contact the seller directly via direct message on the forum.

Source: Underground forums
ETLM Assessment:
The “MantaProtocol” threat actor group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries, indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
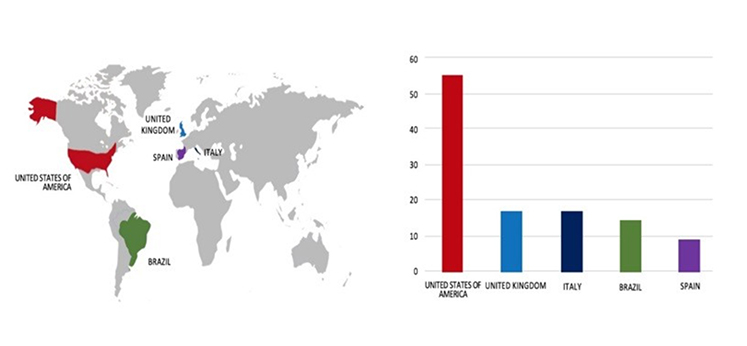
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.