



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
Target Geography: Canada, Poland, United States.
Target Industries: Construction, Law, Media & Internet, Manufacturing, Retail, Real Estate.
CYFIRMA Research and Advisory Team has found ransomware known as CryptBB while monitoring various underground forums as part of our Threat Discovery Process.
CryptBB, a recently wild-spread ransomware variant, is possibly written in the Delphi language. After encrypting the files, original file names were appended with an extension consisting of a random character string.
Upon the conclusion of the encryption process, this ransomware alters the desktop wallpaper and generates a ransom note with the title “[random_string].README.txt.”
It can be ascertained with high confidence that the threat actors are of Russian origin, publicly announcing themselves in support of the Russian Federation.

Screenshot of a Files Encrypted by CryptBB Ransomware. (Source: Surface Web)
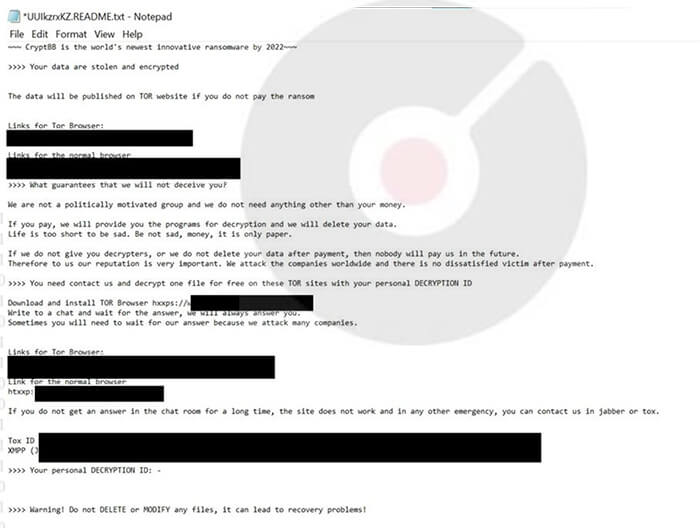
Screenshot of a ransom note by CryptBB Ransomware. (Dated: November 2022) (Source: Surface Web)
Researchers suggest that there is a possibility that the CryptBB ransomware may be based on or related to the LockBit 3.0 ransomware.
Screenshot of CryptBB’s desktop wallpaper. (Source: Surface Web)
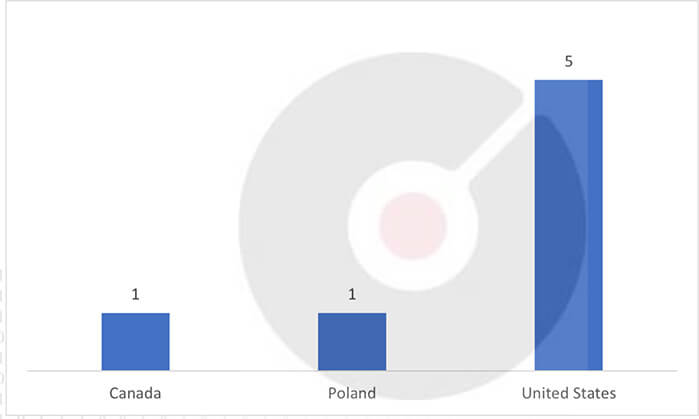
Countries Targetted by CryptBB Ransomware
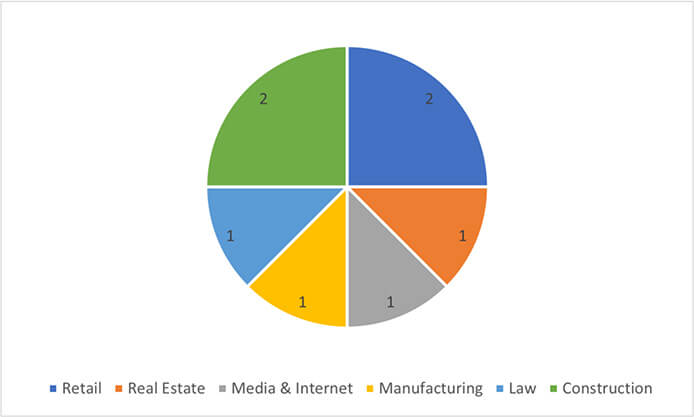
Industries Targeted by CryptBB Ransomware
There is a possibility that CryptBB may be separated from the LockBit group at the beginning of 2023.
CYFIRMA’s assessment, relying on the available information, suggests that the CryptBB ransomware might evolve further, adopting more advanced evasion methods. It could potentially broaden its scope to target various industries and regions. The capability to download and execute runtime modules increases the threat, allowing for the incorporation of new functionalities in upcoming versions. We will continue to monitor, and provide a more comprehensive assessment when further information becomes available.
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques / Sub-Techniques |
| 1 | TA0002: Execution | T1059: Command and Scripting Interpreter |
| T1129: Shared Modules | ||
| 2 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1027.002: Obfuscated Files or Information: Software Packing | ||
| T1036: Masquerading | ||
| 3 | TA0006: Credential Access | T1003: OS Credential Dumping |
| 4 | TA0007: Discovery | T1057: Process Discovery |
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1614: System Location Discovery | ||
| 5 | TA0009: Collection | T1005: Data from Local System |
| T1185: Browser Session Hijacking | ||
| 6 | TA0040: Impact | T1486: Data Encrypted for Impact |
Type: Trojan
Objective: Stealing Financial Information
Target Technology: Windows OS
Target Industries: Banking and Financial Sector
Target Geographies: Latin America (Brazil & Mexico)
This week “BBTok” is trending.
Researchers have recently uncovered an ongoing campaign in Latin America that is deploying a new version of the BBTok banking Trojan. This campaign employs a combination of Living Off the Land Binaries (LOLBins) in its infection chains, resulting in low detection rates. During their analysis, researchers identified server-side resources used by the threat actors in attacks targeting users in Brazil and Mexico. These server-side components are responsible for delivering malicious payloads, likely distributed through phishing links. Multiple iterations of these server-side scripts and configuration files were observed, revealing the evolving deployment methods of the BBTok banking Trojan over time.
The BBTok banking Trojan, initially discovered in 2020, was deployed in Latin America through fileless attacks. The banking Trojan has a wide set of functionalities, including enumerating and killing processes, keyboard, and mouse control, and manipulating clipboard contents. Alongside those, BBTok contains classic banking Trojan features, simulating fake login pages for a wide variety of banks operating in Mexico and Brazil. Since it was first publicly disclosed, the BBTok operators have adopted new TTPs, all while still primarily utilizing phishing emails with attachments for the initial infection. Recently, researchers have seen indications of banking Trojans distributed through phishing links and not as attachments to the email itself.
Following the fake interfaces, controlled by the BBTok banking Trojan, impersonate legitimate financial institutions. They skillfully manipulate unsuspecting users into divulging their personal and financial information. Victims are deceived into entering their security codes or token numbers, which are essential for bank account 2FA, allowing the BBTok attackers to conduct account takeovers. Moreover, in some cases, this deceptive tactic also tricks victims into providing their payment card numbers.
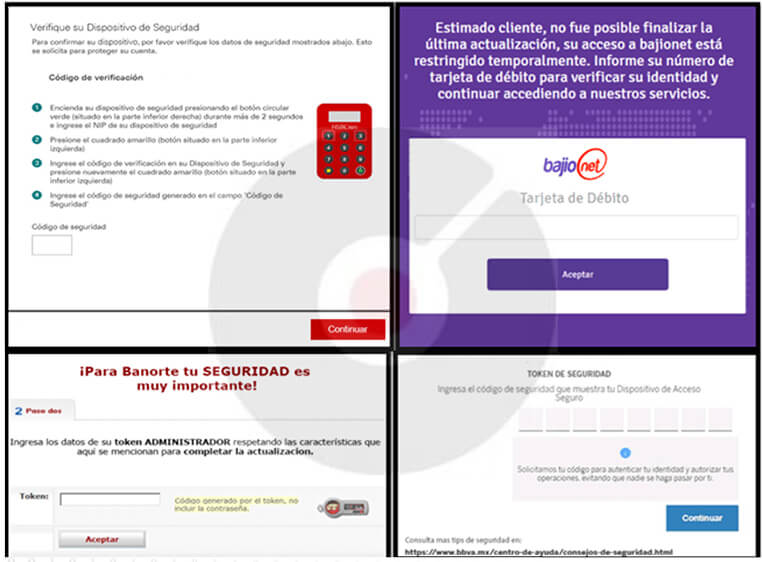
Fig: Fake interfaces embedded within the BBTok Banker
The BBTok banking Trojan creates fake versions of over 40 Mexican and Brazilian bank interfaces. It tricks victims into inputting their 2FA codes or payment card numbers. An analysis of the server-side code shows that the attackers continually update their methods to infect different Windows versions.
Researchers were able to identify a database of BBTok malware victims in Mexico, which contained more than 150 entries with victims’ information.
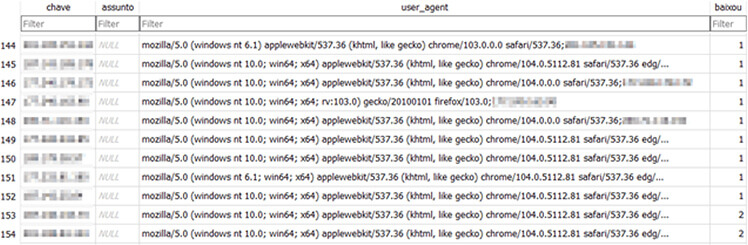
Fig: Database with victims’ information
From the ETLM Perspective CYFIRMA believes that BBTok may evolve to employ even more sophisticated evasion techniques, making it increasingly challenging for organizations to detect and mitigate the malware. This could lead to longer dwell times and more extensive data breaches. While BBTok has primarily targeted the banking sector, it may diversify its targets in the future. While primarily affecting Latin American countries, BBTok might expand its geographic reach, targeting organizations in other regions, which could impact a more diverse set of businesses.
Kindly refer to the IOCs Section to exercise controls on your security systems.
Key Intelligence Signals:
A new APT named AtlasCross launched Sophisticated Attack, using the Red Cross Blood Drive Template
Summary:
In a recent observation, a newly identified APT group known as ‘AtlasCross’ has emerged, targeting organizations through sophisticated phishing campaigns. This group employs deceptive emails impersonating the American Red Cross to distribute backdoor malware. Researchers have uncovered two previously unknown trojans, DangerAds and AtlasAgent, which are associated with AtlasCross’s attacks. Researchers said AtlasCross has a high level of sophistication and evasive tactics, making it challenging for researchers to pinpoint their origin. Researchers revealed that AtlasCross exhibits notable differences in execution flow, technology stack, attack tools, and objectives compared to known attackers. The attack chain begins with phishing emails, disguised as American Red Cross messages inviting recipients to participate in a “September 2023 Blood Drive.” These emails contain a macro-enabled Word document that, when activated, installs the DangerAds and AtlasAgent malware on Windows devices. DangerAds serves as a loader and system profiler, while AtlasAgent is the final payload, loaded once specific conditions are met. AtlasAgent is a custom C++ trojan with capabilities such as gathering host and process details, preventing multiple program launches, executing additional code, and downloading files from the attacker’s servers. AtlasCross maintains a narrow targeting scope, with DangerAds checking for specific strings in system usernames or domain names. Additionally, AtlasAgent communicates with its servers, receiving commands that are difficult for security tools to detect and thwart.
Relevancy & Insights:
New viruses like DangerAds and AtlasAgent can be more destructive due to their advanced evasion tactics, targeted nature, data exfiltration capabilities, persistence on compromised systems, and ability to evade security tools. Their complex payloads, exploitation of zero-day vulnerabilities, and potential to form botnets for large-scale attacks make them formidable threats.
ETLM Assessment:
Sophisticated attacks by groups like AtlasCross are becoming increasingly common due to their ability to evade traditional defenses. These attacks leverage social engineering tactics as initial access, making them easy, accessible, and effective. As cybercriminals continue refining their techniques, the frequency of such attacks is expected to go upwards as nation-state threat actors increasingly target nations with whom they have diplomatic tensions. Moreover, in modern warfare, cyberattacks are often initiated before conventional military operations, serving as the initial salvo in conflicts between nations.
Recommendations:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Trending Chinese Cyber-threats
In a recent report, the Chinese and North Korean government’s influence operations have been observed to have grown more effective over the past year. China-aligned social media networks have engaged directly with authentic users on social media, targeted specific candidates in content about US elections, and posed as American voters. Separately, China’s state-affiliated multilingual social media influencer initiative has successfully engaged target audiences in at least 40 languages and grown its audience to over 103 million. Chinese cyber operations this year have been focused on countries surrounding the South China Sea, where China presses territorial claims on countries like the Philippines, Vietnam or Indonesia as well as on the United States, with which China is in conflict over primacy in the region and global affairs as a whole.
ETLM Assessment:
Besides the aforementioned regions, Chinese cyber espionage has been increasingly targeting technical assets in the US defense industrial base with a special focus on satellites, telecommunications, on US infrastructure on the island of Guam, US critical infrastructure, and nations opposing China’s territorial claims in the South China Sea. All the mentioned industries are under perpetual threat of Chinese cyber penetration as China considers them as threats from a geopolitical perspective.
A shift in Russian cyber targeting
The State Service of Special Communications and Information Protection of Ukraine (SSSCIP) has published its observations of a distinct shift in the targets selected by Russian cyberespionage services. At least two of the major Russian intelligence services (the GRU and FSB) had previously shown a distinct preference for collecting against Ukraine’s electrical power infrastructure; however, both were observed shifting their focus on law enforcement agencies, and specifically on those units charged with collecting and analyzing evidence of Russian war crimes.
ETLM Assessment:
This activity shift is best explained as an early stage of an attempt to interfere with investigations into Russian war crimes and into preparing intelligence for future disinformation campaigns that are to be expected to attempt to discredit otherwise credible allegations, including those described by a recent UN fact-finding mission on the matter. There appears to be an ongoing wider cyber intelligence campaign by Russian security services, which also includes the recently disclosed compromise of systems at the International Criminal Court, which has charged Russian leaders including President Putin. The campaign is expected to last months and possibly years.
Clarion is Impacted by BlackCat Ransomware
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in the dark forum that a company from the United States of America, (www[.]clarion[.]com), was compromised by BlackCat Ransomware. Clarion is a manufacturer of multimedia systems, marine audio systems, smart access solutions, speakers, subwoofers, amplifiers, and more. The leak site associated with the BlackCat Ransomware alleges that the compromised data includes both engineering details of the company’s clients and various other sensitive information.
The following screenshot was observed published on the dark web:

Source: Dark Web
Relevancy & Insights:
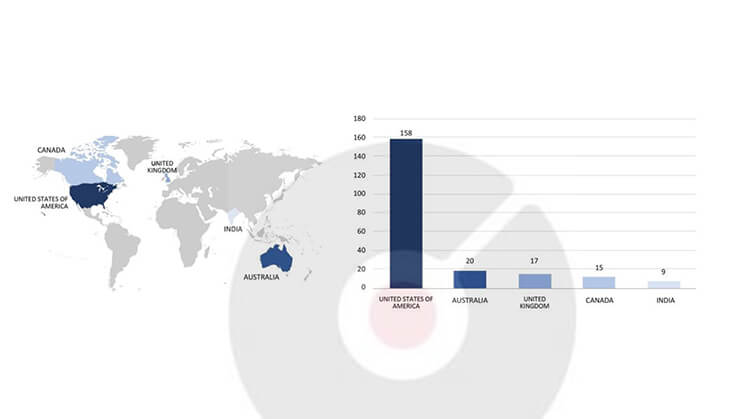
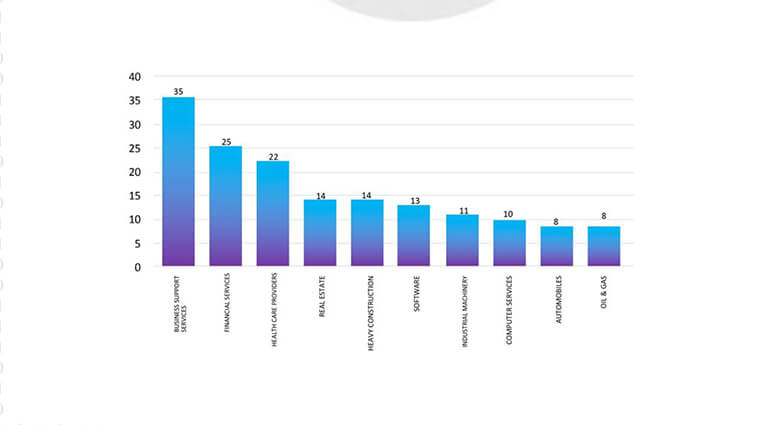
ETLM Assessment:
CYFIRMA’s evaluation remains steady: we expect the BlackCat Ransomware to persist in its focus on American businesses, as demonstrated in the accompanying graph, and possible continued targets to nations allied with the US. Nonetheless, recent events such as the Clarion attack underscore that even prominent manufacturing corporations are susceptible to potential targeting.
Vulnerability in Mitsubishi Electric GX Works3
Summary:
The vulnerability allows a local attacker to escalate privileges on the system.
Relevancy & Insights:
The vulnerability exists due to incorrect default permissions for files and folders that are set by the application.
Impact :
A local attacker can execute arbitrary code on the system with elevated privileges. Affected Products : https[:]//www[.]mitsubishielectric[.]com/en/psirt/vulnerability/pdf/2023-010_en.pdf
Recommendations:
Apply Security Updates : Mitsubishi Electric or the software vendor may release security patches or updates to address this vulnerability. Ensure that these updates are applied promptly.
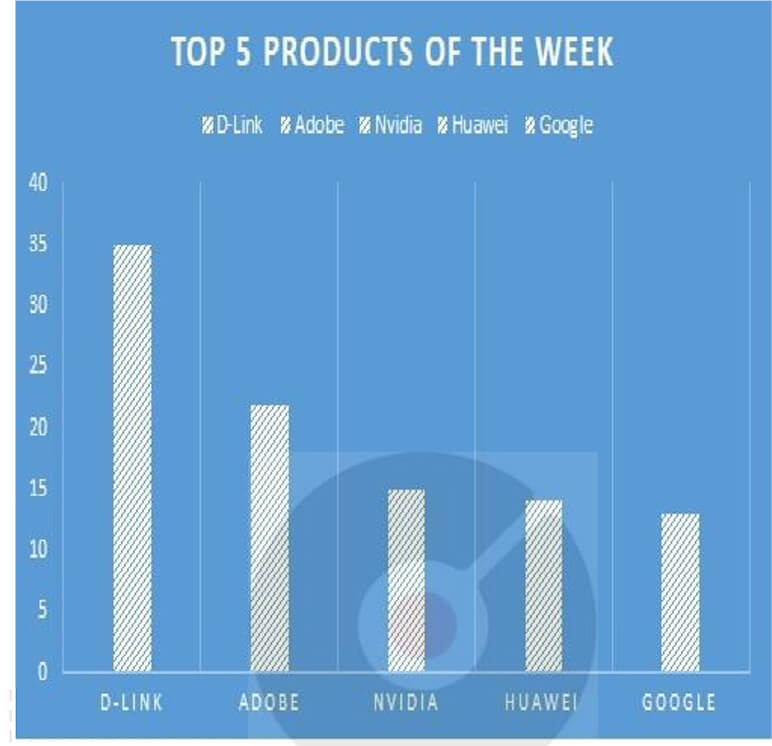
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products due to a range of vulnerabilities. The following are the top 5 products most affected.
Moldovan government websites are the focus of DDoS attacks.
Summary:
The Government of the Republic of Moldova has reported a surge in cyber-attacks targeting multiple websites over the past week. The Chisinau International Airport, the National Energy Regulatory Agency (ANRE), and the Ministry of Foreign Affairs and European Integration (MFAIE) have all fallen victim to a series of distributed denial-of- service (DDoS) attacks over the past week. The attacks involved a very large number of requests, usually from outside the country, which were aimed at blocking a server or a web platform. The government also advises private sector stakeholders to prioritize cybersecurity within their organizations, bolster corporate network defenses, and explore industry-specific recommended measures to safeguard web servers. The clarifications come after the Information Technology and Cybersecurity Service confirmed on Monday, September 25, the recording of a cyber-attack on the information sources of service providers in the field.
Relevancy & Insights:
Over the past week, the Government of the Republic of Moldova has observed a notable surge in cyber-attacks, primarily distributed denial-of-service (DDoS) attacks. These attacks specifically targeted critical websites.
ETLM Assessment:
CYFIRMA’s assessment suggests that Moldovan government websites are likely to face ongoing DDoS attacks, with the potential for escalation due to the significant operational disruption caused by such attacks, leading to substantial business repercussions.
LearningRx Data Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to LearningRx, {www[.]learningrx[.]com}. LearningRx is a brain training company with locations across the globe. LearningRx helps individuals and families sharpen their cognitive skills to help them think faster, learn easier, and perform better. The compromised data contains SQL-formatted information, including fields such as ID address, ID source, lead ID, center ID, session ID, prefix, first name, last name, suffix, age, date of birth, gender, area code, phone numbers, and other confidential information.
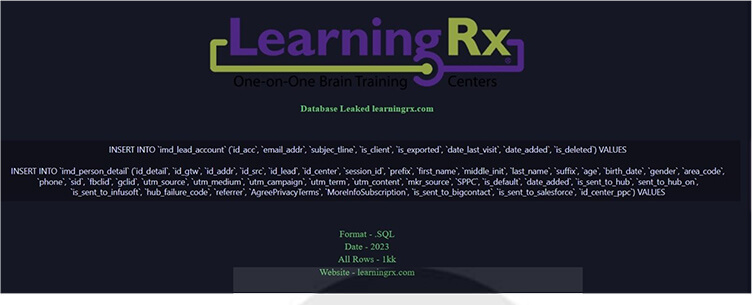
Source: Underground forums
Relevancy & Insights:
Opportunistic cybercriminals, motivated by financial gains, are continuously scouring the internet for exposed and vulnerable systems and software. Many of these attackers carry out their activities in secretive online communities, where they engage in discussions related to their illegal endeavors, including the trade of stolen digital assets. Unlike financially motivated groups such as ransomware or extortion gangs, who often publicize their attacks, these cybercriminals prefer to operate discreetly. They take advantage of unpatched systems or vulnerabilities in software and systems to gain unauthorized access and steal valuable data. Subsequently, the pilfered data is advertised for sale in underground forums, shared among fellow attackers, and repurposed for various illicit purposes.
ETLM Assessment:
The United States of America continues to rank among the top targets for cybercriminals worldwide. According to CYFIRMA’s assessment, U.S. institutions lacking strong security measures and infrastructure are likely to remain at a heightened risk of potential cyberattacks.
CYFIRMA Research team observed a potential data leak related to the ICT Billet, {www[.]ictbillet[.]com}. ICT Billet is an automotive service and collision repair provider, offering excellent bargains on a range of products, including LS and LT parts, LS engine swap kits, LT engine swap kits, LS engine components, LT engine components, and an extensive selection of premium aftermarket automotive merchandise. The data breach encompasses information in SQL format, including ID, Name, Email, Group, Phone, ZIP, Country, State/Province, Billing Address, Shipping Address, Date of Birth, Tax VAT Number, and various other sensitive details.
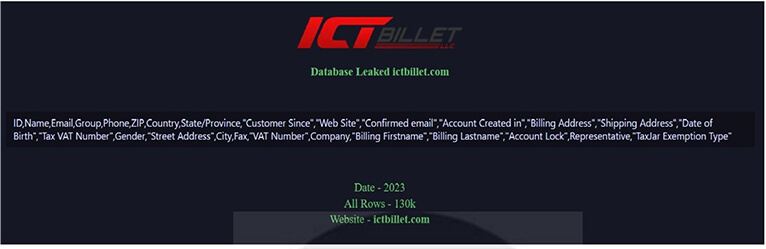
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS