



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Heda Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Heda Ransomware
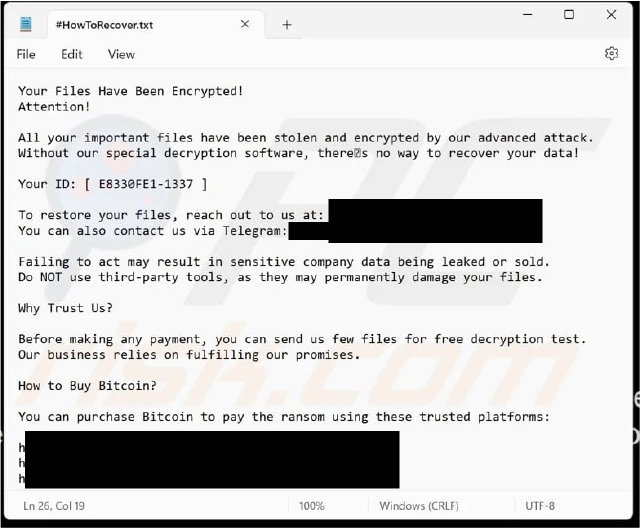
In early November 2024, researchers identified a new ransomware variant named Heda. This ransomware encrypts files on compromised systems, alters filenames, and modifies the desktop wallpaper. It also generates a ransom note in a text file titled “#HowToRecover.txt.” The ransomware renames files by appending the victim’s unique ID, an email address, and the “.Heda” extension to the original filenames.
Notably, Heda ransomware is identical to the previously known Sauron ransomware.
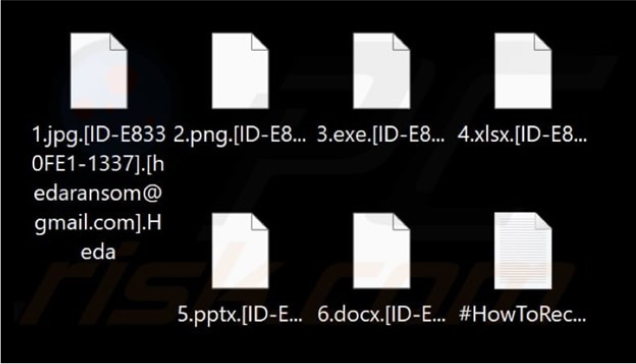
Heda’s ransom note informs victims that their critical files have been both encrypted and stolen, claiming that recovery is only possible with the attackers’ proprietary decryption tool. The note assigns a unique identifier to the victim and directs them to contact the attackers via email or Telegram for file restoration instructions.
The attackers threaten to leak or sell sensitive data if the victim fails to pay the ransom and caution against using third-party tools, warning that such actions could cause irreversible damage. Additionally, the note provides links to platforms where victims can purchase Bitcoin to facilitate the ransom payment.
Following are the TTPs based on the MITRE Attack Framework.
| Tactic | ID | Technique |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1129 | Shared Modules |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1134 | Access Token Manipulation |
| Privilege Escalation | T1574.002 | Hijack Execution Flow: DLL Side- Loading |
| Defense Evasion | T1027.002 | Obfuscated Files or Information : Software Packing |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1134 | Access Token Manipulation |
| Defense Evasion |
T1497 | Virtualization /Sandbox Evasion |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion |
T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion |
T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Credential Access |
T1003 | OS Credential Dumping |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1049 | System Network Connections Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1135 | Network Share Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Discovery | T1614 | System Location Discovery |
| Collection | T1005 | Data from Local System |
| Command and Control |
T1071 | Application Layer Protocol |
| Command and | T1573 | Encrypted Channel |
| Control | ||
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1529 | System Shutdown/Reboot |
Relevancy and Insights:
ETLM Assessment:
According to the assessment from CYFIRMA, the ransom note associated with Heda ransomware indicates a primary focus on targeting enterprises to maximize financial returns. This suggests that ransomware is likely to become a serious threat to developed nations, with industries such as Manufacturing, Healthcare, Hospitality, and Finance expected to be key targets due to their substantial ransom payment capacities and heavy reliance on critical data. Furthermore, the ransomware warns that non-compliance could lead to the exposure or sale of sensitive corporate information.
Sigma Rule
title: Shadow Copies Deletion Using Operating Systems Utilities tags:
– attack.defense-evasion
– attack.impact
– attack.t1070
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’ selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’ selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’ selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’ selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’ CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) fields:
– CommandLine
– ParentCommandLine falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand) level: high
(Source: Surface web)
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Information stealer
Objective: Data theft, Data Exfiltration
Target Technologies: Windows OS, Facebook Ads Manager
Active Malware of the Week
This week “NodeStealer” is trending.
NodeStealer
Researchers have uncovered new NodeStealer samples targeting Facebook Ads Manager accounts, a tool used to manage advertising campaigns on platforms like Facebook and Instagram. Originally discovered in 2023 as a Python-based infostealer aimed at Facebook Business accounts, NodeStealer has spent over a year stealing login credentials, cookies, and saved browser data. These latest variants expand the malware’s capabilities by focusing on Ads Manager, pilfering budget details, credit card information, and additional credentials. Using advanced techniques such as Windows Restart Manager to unlock browser databases, junk code obfuscation, and batch script-driven dynamic execution, the malware demonstrates a sophisticated evolution. Researchers believe its ultimate goal is to exploit compromised accounts for creating malicious ads, posing a growing threat to digital advertising platforms.
Attack Strategy
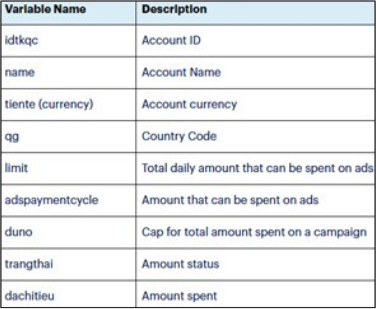
Researchers have identified NodeStealer samples designed to extract detailed information from Facebook Ads Manager accounts. By using cookies stolen from a victim’s machine, the malware generates an access token to log into adsmanager.facebook.com. With this token, it retrieves business details linked to the account through the Facebook Graph API and stores the data in a file named “data.txt” in the TEMP folder. The malware then gathers additional account details from the Ad Accounts endpoint, appending this information to the same file, showcasing its methodical data theft approach.
Avoiding Detection in Vietnam
The attackers behind the NodeStealer campaign targeting Facebook Ads Manager accounts appear to be Vietnamese, as some of the malware’s strings are in Vietnamese. However, they intentionally avoid victims in Vietnam by checking the country code through ipinfo and exiting the script if the code is “VN.” This tactic is common among cybercriminals to evade legal risks and reduce attention from local law enforcement.
Evolving Techniques of NodeStealer Windows Restart Manager
Some Python NodeStealer variants use Windows Restart Manager to unlock locked database files, enabling the malware to steal sensitive information. Typically used to minimize reboots during software updates, Restart Manager is exploited here to bypass file locks. The malware copies browser database files to a temporary folder, uses Sqlite3 to query data, and relies on the Restart Manager DLL to identify and terminate processes locking the files. By leveraging legitimate tools like Restart Manager, attackers evade detection and enhance their data extraction capabilities.
Credit card information theft
Some NodeStealer variants have added the ability to steal credit card information by targeting the “Web Data” files of browsers. These files, stored as SQLite databases, contain sensitive autofill data and saved payment methods. By querying the stolen databases with Python’s SQLite3 library, the malware extracts credit card details, including the cardholder’s name, card number, and expiration date, significantly expanding its scope for financial theft.
Persistence through run registry keys
Some NodeStealer variants have adopted a new persistence technique using the Windows Run registry key. Previously, the malware relied on the startup folder for persistence, a method still seen in some samples. However, newer variants now use the current user’s Run key in the registry, leveraging PowerShell to execute the malicious Python script, making the persistence mechanism stealthier and more resilient.
Junk code
Some NodeStealer variants include large amounts of junk code, likely added to inflate the file size and evade detection by systems that prioritize smaller files. These variants feature tens of megabytes of junk code, with the actual malicious script hidden within 3.9 to 6 million characters of filler, making analysis more challenging and time-consuming.
Dynamic generation via batch file
A newer NodeStealer variant found in the wild uses a batch file to generate and execute the Python infostealer. Unlike older samples that relied on batch files to download payloads from external sources, this variant embeds the entire payload within the batch file itself.
The batch script echoes the malicious Python code line-by-line into a separate file, simplifying deployment while avoiding external network activity.
Telegram still used for exfiltration
All analyzed NodeStealer samples continue to use Telegram for exfiltrating stolen data. The malware saves the pilfered credentials and victim information, such as public IP address, country, and hostname, into text files. These files are then compressed into a zip archive and sent to the attacker via Telegram, ensuring quick and covert data transfer.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that as NodeStealer continues to evolve, its reach and sophistication are expected to expand, intensifying the threat to both businesses and individuals. By targeting sensitive data from platforms like Facebook Ads Manager, the malware is likely to increase risks such as financial theft, personal data loss, and privacy breaches. The use of legitimate system tools and the embedding of malicious payloads in seemingly harmless files will complicate traditional security efforts, making detection and prevention more challenging. As NodeStealer increasingly leverages system processes, its attacks may become harder to spot, leaving many unaware until significant damage occurs. With the malware’s capabilities growing, targeted attacks are expected to rise, further escalating the challenges of online security and personal data protection.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
A Chinese APT group targeting critical industries in the US, the Asia-Pacific region, the Middle East, and South Africa
Summary:
Earth Estries, a highly sophisticated Chinese APT group has emerged as a significant threat in recent years. Since 2023, the group has primarily targeted critical industries, such as telecommunications, government agencies, and private-sector organizations across regions including the United States, Asia-Pacific, the Middle East, and South Africa.
Earth Estries uses a combination of exploiting known vulnerabilities in publicly exposed servers and deploying custom malware for long-term access. The group is known for its strategic, technical approach, utilizing N-day vulnerabilities (CVE-2023-46805 – CVSS 8.2, CVE-2024-21887-CVSS 9.1, CVE-2023-48788-CVSS 9.8, CVE-2022-3236-
CVSS 9.8, CVE-2021-26855-CVSS 9.8, CVE-2021-26857-CVSS 7.8, CVE-2021- 26858-CVSS 7.8, CVE-2021-27065-CVSS 7.8)to gain initial access, such as those in Ivanti VPN, Fortinet FortiClient, and Microsoft Exchange. Once inside, they employ living-off-the-land binaries for lateral movement and deploy malware like SNAPPYBEE (Deed RAT) and DEMODEX rootkit to maintain persistence. Additionally, Earth Estries uses cross-platform backdoors like MASOL RAT, which targets both Linux and Windows systems. A key tool in their arsenal is the GHOSTSPIDER backdoor, a highly modular and adaptable malware that allows attackers to dynamically load various components based on their objectives. This malware uses encrypted communications and custom protocols to evade detection and maintain secure communication with C&C servers. The group’s tactics also include sophisticated network obfuscation techniques, such as using distributed C&C infrastructure and encrypted communication channels through SoftEther VPN. Their victims span over 20 organizations in various sectors, including telecommunications, technology, government, and NGOs.
Earth Estries’ primary motivation is cyber espionage, which is focused on gathering sensitive information related to government operations, military intelligence, and corporate secrets. The group’s long-term objective appears to be the strategic infiltration of critical infrastructure, refining attack methods, and penetrating multiple levels of organizations, including secondary contractors and service providers. This persistent and evolving threat emphasizes the need for continued vigilance and proactive cybersecurity measures to defend against such advanced threats.
Relevancy & Insights:
Earth Estries, with a notable history of cyber espionage operations targets governments, telecommunications, and critical infrastructure. Their past attacks have focused on exploiting known vulnerabilities in widely used software and services, such as Microsoft Exchange (via ProxyLogon vulnerabilities) and Fortinet VPNs. These early campaigns established Earth Estries as a group skilled in long-term, stealthy operations, often compromising networks for years without detection. For instance, in their 2020 and 2021 campaigns targeting Southeast Asian governments, they employed tools like the MASOL RAT and DEMODEX rootkit to maintain access and exfiltrate sensitive data.
In more recent incidents, such as the 2023 attacks on telecommunications companies in Southeast Asia, Earth Estries escalated their use of modular backdoors, notably GHOSTSPIDER, which has a more sophisticated and multi-layered approach compared to previous malware.
This evolution reflects the group’s growing sophistication and ability to adapt their tools for specific targets and environments. Furthermore, their recent use of Cobalt Strike and overlapping C&C infrastructure with past incidents highlights their continued reliance on a mix of old and new techniques. The group’s shift towards cloud infrastructure, combined with its longstanding focus on exploiting supply chains and targeting vendor networks (as seen in recent attacks on consulting firms), indicates a strategic refinement in their operations. These patterns suggest that Earth Estries continues to build on its earlier methods, refining its tactics, tools, and infrastructure while maintaining its primary goal of espionage and data theft, specifically from high- value government and corporate entities.
ETLM Assessment:
Earth Estries is a Chinese advanced persistent threat (APT) group specializing in cyber espionage. They target high-value organizations and sectors, focusing on gathering intelligence and maintaining long-term access to compromised networks. Their geographic targets span the United States, Southeast Asia, the Middle East, South Africa, and the Asia-Pacific region. The group has primarily attacked government agencies, telecommunications, consulting firms, NGOs, and critical infrastructure, using sophisticated techniques to exploit vulnerabilities in widely-used technologies, including public servers, VPNs, and cloud environments. Earth Estries is adept at exploiting critical vulnerabilities like those in Ivanti Connect Secure VPN, Fortinet FortiClient EMS, and Microsoft Exchange, as well as leveraging public infrastructure flaws to gain access. Their malware arsenal includes tools like SNAPPYBEE, DEMODEX rootkit, MASOL RAT, and GHOSTSPIDER, all of which are used for surveillance, data exfiltration, and maintaining persistence within networks. Their tactics evolve with time, shifting towards more complex malware, like modular backdoors that operate across multiple platforms (Windows and Linux), and increasingly targeting cloud services and supply chains. The group’s ability to adapt to emerging threats and their ongoing use of highly obfuscated and stealthy methods make them a formidable player in cyber espionage. Looking ahead, Earth Estries will likely continue to focus on exploiting unpatched vulnerabilities, evolving their malware capabilities, and potentially collaborating with other APT groups. Organizations must strengthen defenses, patch vulnerabilities, and enhance threat detection to protect against these persistent, sophisticated attacks.
Strategic Recommendations
Tactical Recommendations
Operational Recommendations
| MITRE ATT&CK Tactics and Techniques | ||
| Tactics | ID | Technique |
| Execution | T1129 | Shared Modules |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side- Loading |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1218.011 | System Binary Proxy Execution: Rundll32 |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Credential Access | T1056 | Input Capture |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Collection | T1056 | Input Capture |
| Command and Control | T1071 | Application Layer Protocol |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Russia targets post-Soviet states
Researchers have published a report on a Russian cyberespionage campaign targeting organizations in Central Asia, East Asia, and Europe with two strains of custom malware dubbed “HATVIBE” and “CHERRYSPY.” The campaign has been linked to the Russia-aligned threat actor TAG-110, while its tactics overlap with previous operations by Russia’s Fancy Bear, an APT controlled by Russian intelligence.
Since the summer of this year, the espionage campaign has targeted governments, human rights groups, and educational institutions in eleven countries, including Kazakhstan, Kyrgyzstan, and Uzbekistan.
ETLM Assessment:
The behaviour of the Central Asian states shows a general conviction that Moscow is no longer able to play its role of an enforcer and more and more eyes are directed primarily towards Beijing and partly also towards Ankara. In Central Asia, it is Beijing in particular that is facing pressure from local governments to fill the security vacuum left by Moscow. An increasing number of Central Asian soldiers and police are being trained in China, and Russian weapons are increasingly being replaced by Chinese ones. The European Union is the main regional trading partner, followed by China and Russia is only third. Hence, the effort, which is clearly a classic case of state-driven espionage, is likely part of a broader Russian strategy to gather intelligence on geopolitical developments and maintain influence in post-Soviet states.
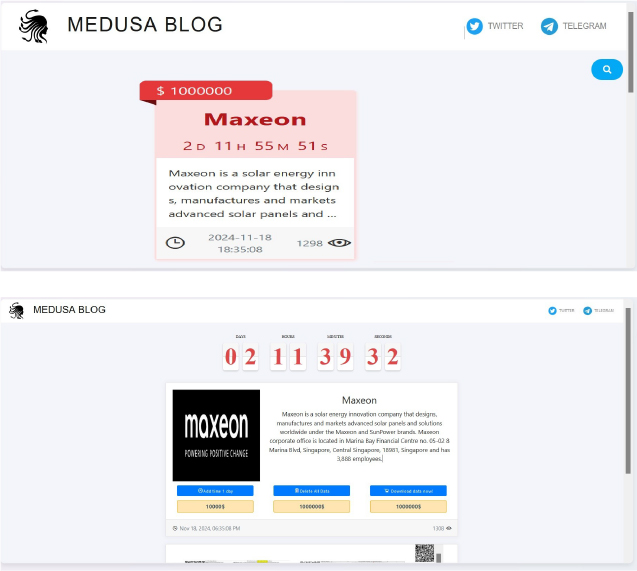
The Medusa Ransomware impacts Maxeon
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Singapore; Maxeon (https[:]//maxeon[.]com), was compromised by Medusa Ransomware. Maxeon is a solar energy innovation company that designs, manufactures and markets advanced solar panels and solutions worldwide under the Maxeon and SunPower brands. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway.
The compromised data encompasses a trove of sensitive and confidential records, originating from the organizational database. The compromised data has been listed for sale with an asking price of $1,000,000.
The following screenshot was observed published on the dark web:
Relevancy & Insights:
ETLM Assessment:
Based on recent assessments by CYFIRMA, Medusa ransomware continues to evolve as a significant threat within the cybersecurity landscape, characterized by its sophisticated tactics and aggressive extortion methods. Organizations are urged to implement robust cybersecurity measures, including regular updates, employee training on phishing awareness, and comprehensive incident response plans to mitigate risks associated with this evolving threat actor. Continuous monitoring of Medusa’s activities will be essential for understanding its impact on global cybersecurity efforts.
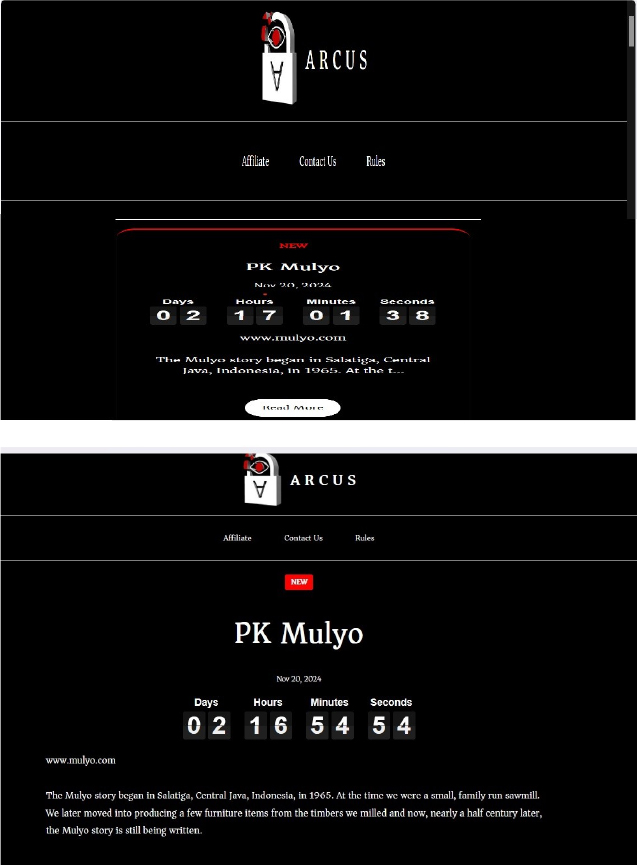
The ArcusMedia Ransomware impacts PK Mulyo
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Indonesia; PK Mulyo (www[.]mulyo[.]com) was compromised by ArcusMedia Ransomware. PK Mulyo is an Indonesian company specializing in furniture manufacturing. PK Mulyo manufactures furniture using both local and imported materials, such as teak, mahogany, oak, and maple. They produce a variety of furniture styles, ranging from classic to contemporary, with a focus on craftsmanship and design. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data encompasses a trove of sensitive and confidential records, originating from the organizational database.
The following screenshot was observed published on the dark web:
Relevancy & Insights:
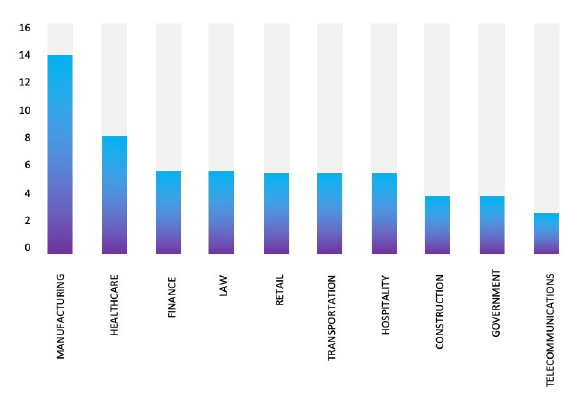
The Top 10 Industries, most affected by ArcusMedia Ransomware from 1st May 2024 to 27th November 2024 are as follows: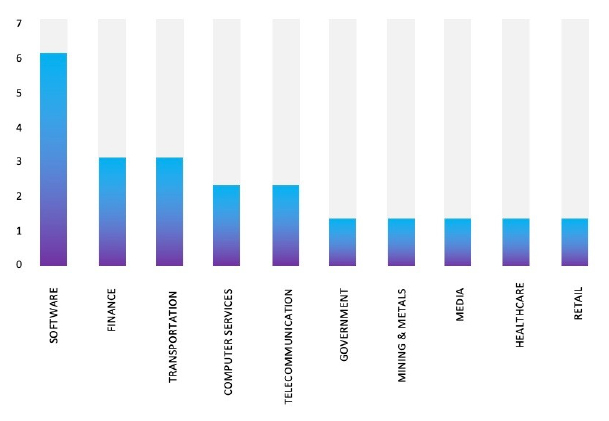
ETLM Assessment:
Based on recent assessments by CYFIRMA, ArcusMedia ransomware represents a significant new threat in the cybersecurity landscape, characterized by its sophisticated tactics and aggressive approach to extortion. Organizations are advised to enhance their cybersecurity defenses, including employee training on phishing awareness, regular updates to systems, and comprehensive incident response plans to mitigate risks associated with this evolving threat actor. Continuous monitoring of ArcusMedia’s activities will be essential for understanding its impact on global cybersecurity efforts.
Vulnerability in GLib2
Source
Vulnerability Type: Buffer Overflow
Summary:
The vulnerability allows a remote attacker to execute arbitrary code on the target system.
Relevancy & Insights:
The vulnerability exists due to an off-by-one error in gio/gsocks4aproxy.c when handling responses from the SOCKS4 proxy. A remote attacker can trick the victim into connecting to a malicious SOCKS4 proxy server, trigger an off-by-one error, and execute arbitrary code on the target system.
Impact:
Successful exploitation of this vulnerability may result in complete compromise of vulnerable systems.
Affected Products:
https[:]//www[.]suse[.]com/support/update/announcement/2024/suse-su- 20244051-1/
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
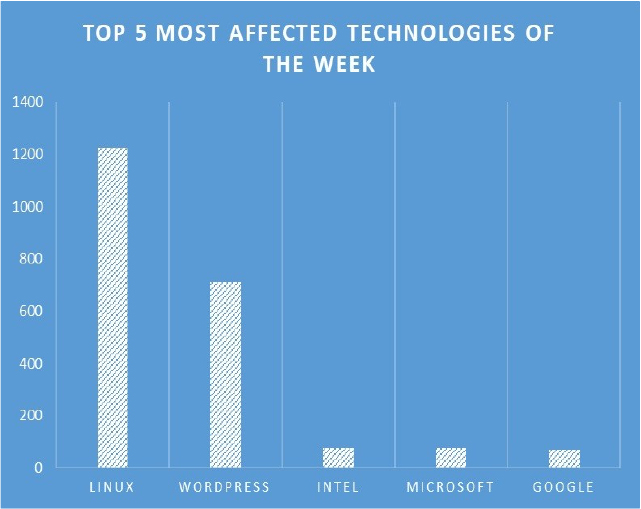
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment:
Vulnerability in GLib can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of GLib is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding the functionality of portable utility libraries, including data types, type conversions, string utilities, and file handling, across different geographic regions and sectors.
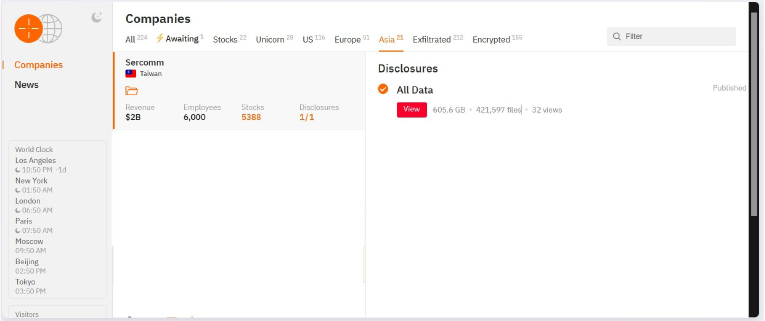
Hunters International Attacked and Published the Data of Sercomm
Summary:
Recently, we observed that Hunters International Ransomware attacked and published the data of Sercomm (www[.]sercomm[.]com) on its dark web website. Sercomm Corporation is a global leader in the telecommunications and broadband solutions industry. The company specializes in designing and manufacturing a wide range of broadband networking products, including 4G/5G customer premises equipment (CPE), Wi-Fi routers, mesh systems, small cells, and IoT devices. Their products are widely used in home networking, enterprise connectivity, and smart city applications. The data leak, following the ransomware attack, encompasses sensitive and confidential records, originating from the organizational database. The scale of the data exposure measures approximately 605.6 GB, comprising a total of 421,597discrete files.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, the Hunters International ransomware group is expected to continue targeting a wide range of industries globally, with a particular focus on the United States, Europe, and Asia. A recent attack on Sercomm, a leading Telecommunications company in Taiwan, highlights the significant threat this ransomware poses in the East Asian region. This incident highlights the growing risk to critical industries in the area and the importance of strengthening cybersecurity defenses against such sophisticated threats.
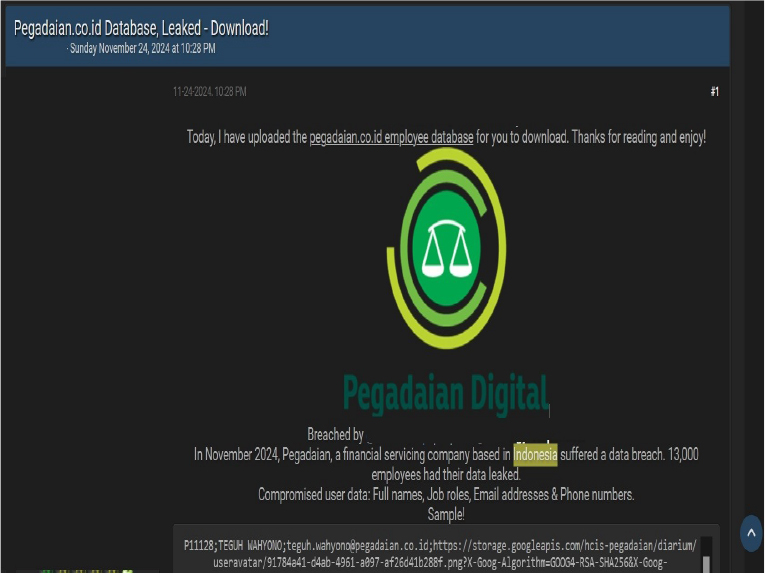
Pegadaian Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data sale related to Pegadaian (www[.]pegadaian[.]co[.]id) in an underground forum. Pegadaian is an Indonesian state-owned enterprise specializing in pawnbroking and financial services. The compromised data reportedly includes information on 13,000 employees, encompassing their full names, job titles, email addresses, and phone numbers. The data breach has been attributed to a threat actor known as “IntelBroker.”
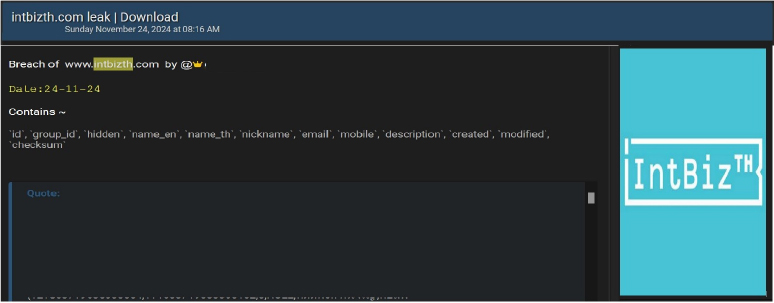
Intelligence Business (Thailand) Co., Ltd. (IntBizTH) Data Advertised on a Leak Site
Summary:
The database of Intelligence Business (Thailand) Co., Ltd. (IntBizTH)(http[:]//IntBizTH[.]com), a Thai business platform, has been leaked online. The breach exposes sensitive user information, highlighting potential risks to privacy and data security. This incident underscores the need for enhanced cybersecurity measures to protect users from exploitation.
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
IntelBroker acts as an “intelligence broker,” breaching organizations and selling their compromised data on underground forums. They have claimed responsibility for over 80 data leaks, affecting more than 400 organizations. Based on the available information, CYFIRMA’s assessment indicates that IntelBroker represents a significant threat in the cybercrime landscape due to its aggressive tactics and high-profile targets. Organizations must remain vigilant and proactive in their cybersecurity measures to protect against such evolving threats.
Recommendations: Enhance the cybersecurity posture by
The official platform http[:]//DubaiPulse[.]gov[.]ae, a critical hub for UAE government services, has reportedly been breached. The leaked database includes sensitive information, potentially affecting individuals and entities using the platform. This incident raises serious concerns about the security of government-managed digital platforms and underscores the urgent need for robust cybersecurity measures.The data breach has been attributed to a threat actor identified as “Henrymans0n”.
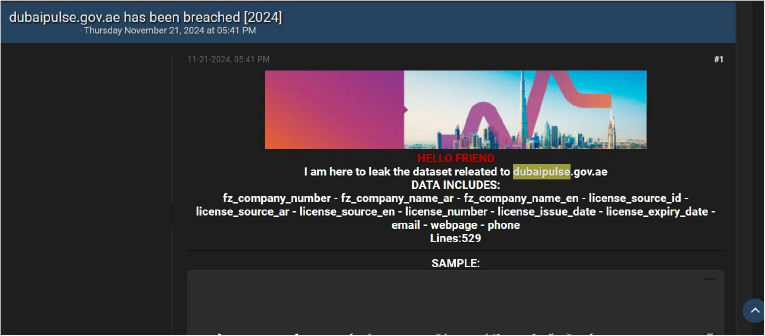
ETLM Assessment:
The “Henrymans0n” threat actor group has recently surfaced as a significant player in cybercrime, primarily driven by financial motives. Active in underground forums, the group has already targeted various sectors, including government, industrial conglomerates, retail, staffing, business consulting, banking, e-commerce, and electric utilities. This broad range of targets signals their intent to further expand their operations across additional industries on a global scale.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
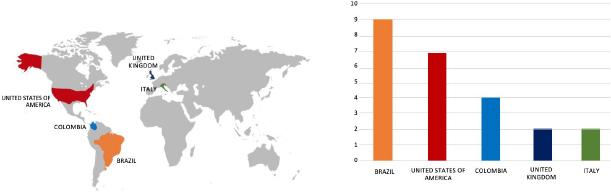
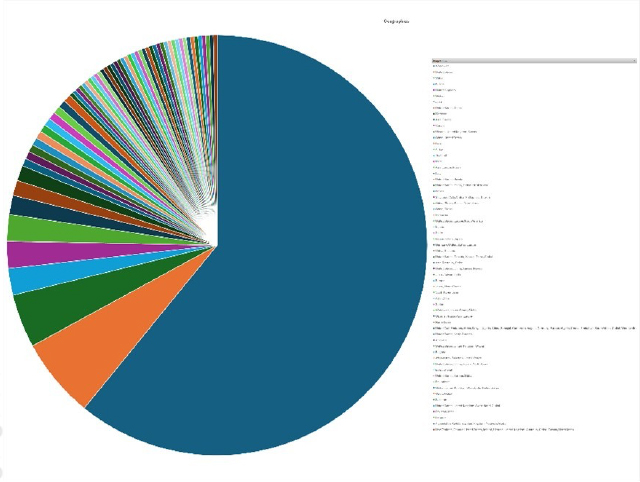
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.