



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
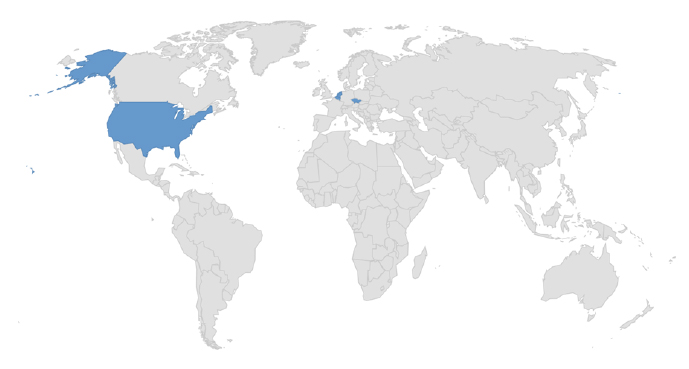
Target Geographies: Belgium, Czech Republic, Netherlands, United States
Target Industries: Finance, FMCG, Media & Internet, Transportation
Introduction
CYFIRMA Research and Advisory Team has found Donex ransomware while monitoring various underground forums as part of our Threat Discovery Process.
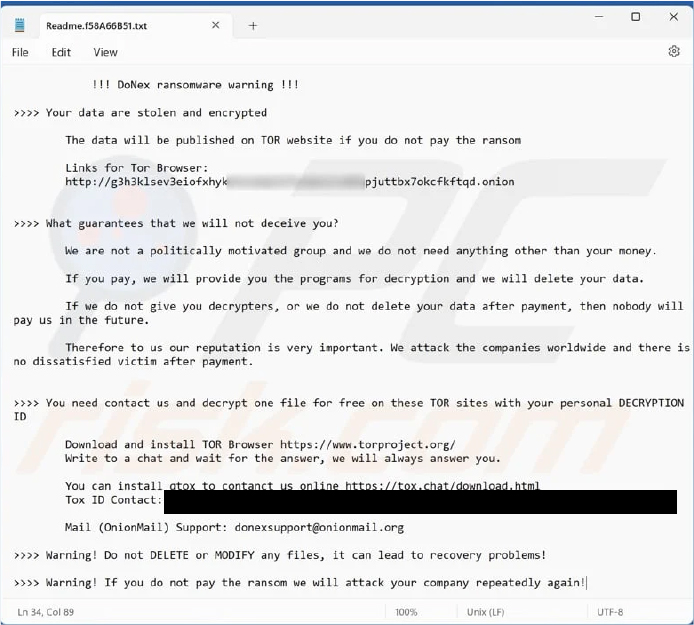
Donex ransomware
Donex ransomware was discovered in the beginning of March 2024. This ransomware encrypts data, adds a unique victim ID extension to filenames, and leaves a ransom note named “Readme.[victim’s_ID].txt” demanding payment for decryption.

Despite being a new entrant, the group has developed robust and sophisticated features that match those of established encryptors. These features include cleaning up attack- related files, restarting the machine, clearing event logs, discovering local and network files, and terminating processes that could disrupt the encryption of valuable files. Most of these functionalities leverage common Windows APIs for execution.
Flow of the Program
The ‘main’ function initiates by concealing the encryptor’s window via the ‘ShowWindow’ function, obtaining a handle to the ‘ConsoleWindowClass’. Subsequently, it proceeds to execute three primary functions, constituting the core of the encryptor.
Pre-Encryption Configuration
The setup begins by creating a mutex named ‘CheckMutex’ to ensure single-instance execution of the encryptor. Subsequently, the encryptor retrieves a pointer to the ‘IsWow64Process’ function using the ‘GetProcAddress’ function to locate its address within ‘kernel32.dll’. Once obtained, it calls the ‘IsWow64Process’ function pointer. If the return value is true, the encryptor then disables WoW64 file system redirection via the ‘Wow64DisableWow64FsRedirection’ call to ensure commands execute without file system redirection activated. Additionally, the encryptor reads the machine name and supported languages.
Before file manipulation, the encryptor must acquire a cryptographic context, which it does using the deprecated Windows functions ‘CryptAcquireContextA’ and ‘CryptGenRandom’. The reasons for the malware author’s choice of these outdated APIs remain unclear.
As one of the final setup steps, the encryptor modifies the default icon by updating the registry key ‘DefaultIcon’ with the value ‘C:\\ProgramData\\icon.ico’.
Prior to completing setup, the encryptor deletes all files in the recycle bins across each drive without displaying a confirmation dialog box.
Directory and File discovery
During file system discovery, the encryptor creates new threads using the standard ‘CreateThread’ method and passes a pointer to a function responsible for file and directory walking, service shutdown, or encryption.
A signalling object facilitates communication between threads, indicating when a thread needs to perform work, such as encrypting a discovered file. This is achieved through the ‘WaitForSingleObject’ function call, using a handle to a semaphore-backed object. Such inter-thread communication mechanisms are commonly employed in malware requiring frequent synchronization.
Thread One – TaskKiller
The thread endeavours to establish and execute a new bat file using the ‘WinExec’ function. This invokes the ‘cmd’ shell to execute the bat file. The command within the bat file utilizes the local ping utility with an echo request size of 2 on the loopback address (127.0.0.1) and the taskkill command to terminate a specified process.
Thread Two – Service Manager
This thread endeavours to obtain a handle to the service manager using the ‘OpenSCManager’ function to access the service manager database. As no machine name is specified, a NULL parameter is passed, obtaining a handle to the local machine’s service manager. The sample proceeds to manage a service from within its configuration block, initially checking the service’s status using the ‘OpenService’ and ‘QueryServiceStatusEx’ functions, storing the status information in a buffer. This buffer includes details such as the current state of the service. If the service is not in the ‘SERVICE_STOP’ or ‘SERVICE_STOP_PENDING’ state, the encryptor proceeds to stop the service via the ‘ControlService’ function, passing in a new state of ‘SERVICE_CONTROL_STOP’.
The thread then sleeps until the ‘dwWaitHint’ value, which is part of the service status, indicating the estimated time required for pending start, stop, pause, or continue operations in milliseconds. If successful, the thread closes the service handle, attempting up to 30 seconds.
Several processes are targeted for shutdown, including SQL servers, Excel, PowerPoint, Outlook, OneNote, Chrome, Firefox, etc.
After the creation of the first two threads, the file and directory discovery thread retrieve a list of logical drive strings using the ‘GetLogicalDriveStrings’ and ‘GetDriveType’ functions. This enables the acquisition of root path names, which are then passed to the file walking function executed in another thread.
Thread Three – File Walker
The file walking thread follows a straightforward process. Using the ‘FindFirstFile’ and ‘FindNextFile’ function calls, the encryptor obtains a handle to a file and iterates through all files from the top of the logical disk. The file handle contains data such as ‘cFileName’ and ‘dwFileAttributes’, which are used to identify potential filenames (‘.’) and determine whether the file is a directory or a regular file. Files earmarked for encryption are added to a list for handling during the encryption process.
Additionally, the encryptor utilizes ‘WNetOpenEnum’ and ‘WNetEnumResource’ to enumerate network shares, aiding in the discovery of files. This is a common API utilized by another ransomware.
The encryptor’s configuration includes a blacklist, whitelist of files or folders, and extensions.
Thread Four – Encryption
Prior to encryption, the Windows Restart Manager API is invoked to verify that the file to be encrypted is not locked by another process. This is achieved through the ‘RmStartSession’ and ‘RmGetList’ functions. Upon retrieval, the ‘OpenProcess’ and ‘TerminateProcess’ APIs are called to ensure file accessibility. Encryption is performed using the Salsa20/ChaCha20 algorithms.
Cleanup
Prior to shut down, the encryptor initiates cleanup tasks. It begins by obtaining a handle using the ‘OpenEventLog’ function and proceeds to clear the logs utilizing the ‘ClearEventLog’ functions. It targets the ‘Application’, ‘System’, and ‘Security’ logs for clearing. Subsequently, the local bat file ‘C:\\ProgramData\\1.bat’ is removed. Finally, it triggers an immediate system restart using the shutdown command with the ‘-r -f -t’ switch.
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1047: Windows Management Instrumentation |
| T1059: Command and Scripting Interpreter | ||
| T1106: Native API | ||
| T1129: Shared Modules | ||
| 2 | TA0003: Persistence | T1543.003: Create or Modify System Process: Windows Service |
| 3 | TA0004: Privilege Escalation | T1543.003: Create or Modify System Process: Windows Service |
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1027.005: Obfuscated Files or Information: Indicator Removal from Tools | ||
| T1027.009: Obfuscated Files or Information: Embedded Payloads | ||
| T1036: Masquerading | ||
| T1070.001: Indicator Removal: Clear Windows Event Logs | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1222: File and Directory Permissions Modification | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1564.003: Hide Artifacts: Hidden Window | ||
| 5 | TA0006: Credential Access | T1056: Input Capture |
| 6 | TA0007: Discovery | T1007: System Service Discovery |
| T1010: Application Window Discovery | ||
| T1016: System Network Configuration Discovery | ||
| T1018: Remote System Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1135: Network Share Discovery | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 7 | TA0009: Collection | T1056: Input Capture |
| T1119: Automated Collection | ||
| 8 | TA0011: Command and Control | T1090: Proxy |
| 9 | TA0040: Impact | T1485: Data Destruction |
| T1486: Data Encrypted for Impact | ||
| T1489: Service Stop | ||
| T1490: Inhibit System Recovery |
Relevancy and Insights:
ETLM Assessment:
Based on Cyfirma’s assessment, Donex ransomware is expected to evolve with enhanced evasion techniques and anti-analysis methods to evade detection by security solutions. Additionally, future variants may target specific industries or geographical regions, incorporating more sophisticated encryption algorithms and communication methods to maximize ransom collection. Organizations should remain vigilant, continuously update cybersecurity measures, and monitor threat intelligence for proactive defense against emerging ransomware threats.
Sigma Rule
title: Delete shadow copy via WMIC threatname:
behaviorgroup: 18
classification: 0 mitreattack:
logsource:
category: process_creation product: windows
detection: selection:
CommandLine:
– ‘*wmic*shadowcopy delete*’ condition: selection
level: critical
(Source: Surface web)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Backdoor
Objective: Espionage, Credential Stealing, Data Exfiltration
Threat Actor: Curious Serpens (aka Peach Sandstorm, APT33, Elfin, HOLMIUM, MAGNALIUM, REFINED KITTEN)
Target Technology: Windows OS, Browsers
Target Industries: Aerospace and Defense
Target Geography: United States
Active Malware of the Week
This week “FalseFont” is trending
Summary
Researchers have discovered the FalseFont backdoor, utilized by the suspected Iranian- affiliated threat actor known as Curious Serpens (aka Peach Sandstorm, APT33, Elfin, HOLMIUM, MAGNALIUM, and REFINED KITTEN). This espionage group has a notable history of targeting the aerospace and energy sectors, operating since at least 2013.
Across the Middle East, the United States, and Europe, Curious Serpens has engaged in espionage activities. FalseFont represents their latest tool, deployed through a deceptive recruitment process mimicking legitimate human resources software to trick victims into installing the backdoor.
FalseFont
The FalseFont backdoor, coded in ASP .NET Core, has been observed in the wild. It is packaged within a single native executable, sized at 182 MB. This executable not only houses the malware but also incorporates essential .NET components and libraries for its functionality. Moreover, FalseFont utilizes ASP.NET Core SignalR, an open-source web application library, to communicate with its command-and-control server (C2). Following are the capabilities of FalseFont:
Targeting Aerospace and Defense Job Applicants
The FalseFont backdoor is specifically aimed at job applicants within the aerospace and defense industries. It achieves this by disguising itself as a graphical user interface (GUI) for job application submissions to a U.S.-based aerospace company. While the GUI operates for user interaction, the malware’s main component runs in the background, establishing persistence and connecting to its command and control (C2) server.
Technical Analysis
The GUI Component
The FalseFont executable features a deceptive login interface, resembling an aerospace company’s login page. When a victim enters their credentials, the malware sends this information in JSON format via an HTTP POST request to the threat actor’s command and control (C2) server at 64.52.80[.]30 using TCP port 8080. Notably, the URLs for regular and guest logins differ.
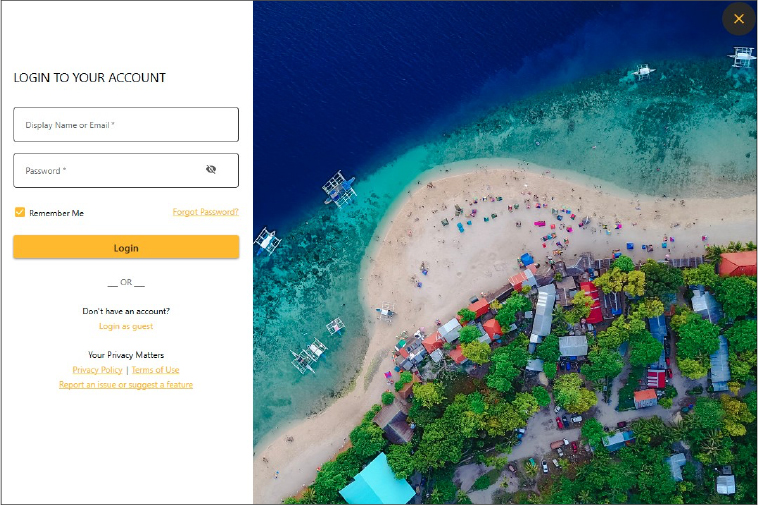
The FalseFont GUI features a “Remember Me” checkbox below the login fields. If selected, the victim’s username and password are saved to a file named data.txt under
%localappdata%. Upon subsequent launches of the application, if the data.txt file exists, the malware automatically sends login data to the C2 server. Upon successful response from the C2 server or if the file exists, the threat hides the login view and displays a resume collection page.
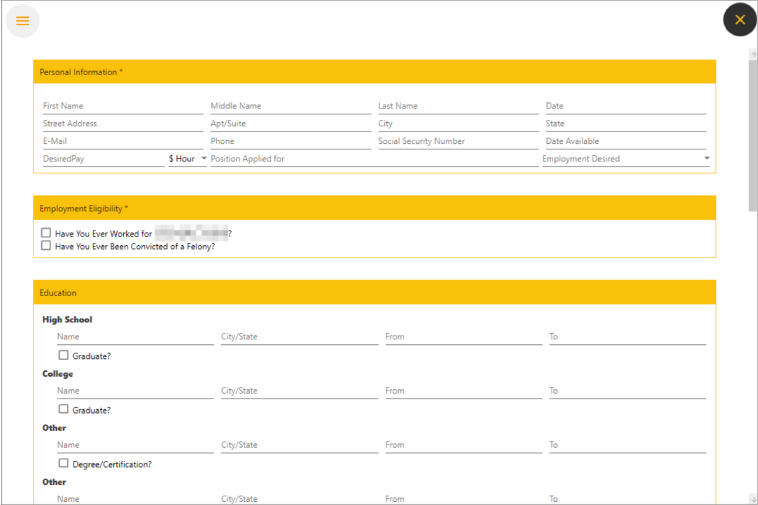
After a victim completes the fields, FalseFont converts the data into serialized JSON and transmits it to the C2 server’s IP address via a GET request. Upon receiving a response from the C2 server, the GUI displays the message “Your information has been registered, our colleagues will contact you.” Additionally, the resume data is stored in a file named data2.txt under %localappdata%.
The Backdoor Components Initialization
During initialization, FalseFont initiates an initial handshake with its C2 domain, transmitting the machine hostname, login username, and operating system details. Additionally, FalseFont supports command-line arguments such as “AppReset” and “AppUpdate,” signified by specific strings like:
These arguments inform the malware if the C2 server has requested a reset or update. Following this, FalseFont endeavors to create a mutex with the value 864H!NKLNB*x_H?5. If the mutex already exists and none of the specified arguments were received, the malware terminates.
Persistence
FalseFont drops three copies of itself into the infected machine,each utilizing unique pathways:
FalseFont ensures persistence by adding a new value to the registry CurrentVersion\Run key for all three copies.
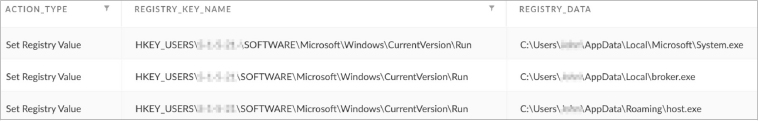
After startup, only the backdoor component of FalseFont runs, omitting the malware’s GUI. Furthermore, if values are already present in the Run key, FalseFont will modify the first existing key to execute the host.exe copy of FalseFont. The first instance to start up will create a mutex, terminating the other two instances.
Encoding and Encryption Scheme
FalseFont contains a hard-coded configuration within its code, aiming to obscure certain strings to impede analysis of its functionality. The malware’s strings are encoded in Base64 and encrypted using a hard-coded AES key.
Core Functionality
FalseFont possesses an array of commands received from the C2, empowering attackers to execute various activities, including:
FalseFont can receive commands from the C2 in two different ways:
These two methods facilitate interaction with FalseFont in distinct ways. The first method allows attackers to communicate with the backdoor through a predetermined set of commands executed periodically. Conversely, the second method, employing SignalR, permits attackers to transmit commands to the backdoor instantly, eliminating the need to wait for the backdoor to initiate a request first.
SignalR Client
SignalR, an ASP.NET library commonly utilized for chat applications, facilitates real-time content delivery from servers to clients. In contrast to querying a specific API endpoint periodically, attackers can employ SignalR to send commands to the FalseFont backdoor instantly. FalseFont utilizes SignalR’s default JSON-based text protocol. Messages sent from the attacker’s server are formatted in JSON and parsed by various handlers registered by the client (FalseFont). These messages consist of a name and additional parameters.
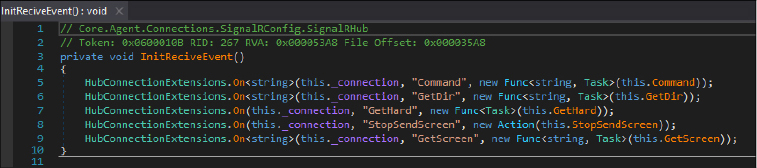
FalseFont registers five handlers using the HubConnectionExtensions.On method. Upon registration, the SignalR client awaits messages from the server. Upon receiving a message, the client checks if the message name matches one of five possible values. If there’s a match, the corresponding method is executed, with the message parameter passed in as an argument.
Credential Theft
Upon examining FalseFont’s credential theft functionality, it was discovered that upon receiving the command “CMD” with the parameter “pass” from the C2, FalseFont endeavors to pilfer credentials from popular web browsers. Moreover, it attempts credential theft by querying the Loginvault.db database.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the utilization of sophisticated techniques by threat actors like Curious Serpens, alongside the deployment of advanced malware such as FalseFont, poses significant future risks for organizations. As these threat actors continue to refine their tactics, organizations may face increased instances of credential theft, data breaches, and identity impersonation. For example, FalseFont’s ability to steal credentials from popular web browsers and query databases for sensitive information could result in widespread data compromises and financial losses for organizations. Looking ahead the impact of such attacks may escalate, with threat actors leveraging stolen credentials to perpetrate more targeted and damaging cyberattacks. This could include unauthorized access to sensitive systems, manipulation of critical data, and even extortion attempts against organizations.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
APT29 Launches First-Ever Campaign Targeting Political Parties in Germany
Summary:
In a recent observation, researchers discovered a campaign against political parties in Germany led by APT29. In late February 2024, researchers discovered APT29, a Russian-backed threat group linked to Russia’s Foreign Intelligence Service (SVR), targeting German political parties with a phishing campaign. This marks a significant shift as APT29 typically targets governmental and diplomatic entities. The operation employed a new backdoor variant known as WINELOADER, indicating a broadening operational focus. Phishing emails masquerading as invitations to a Christian Democratic Union (CDU) dinner reception were sent to victims, containing a link to a malicious ZIP file hosted on a compromised website. The ZIP file delivered the ROOTSAW dropper, which in turn deployed the WINELOADER payload. This activity is the first instance of APT29 targeting political parties, suggesting an expansion in their scope of interest. The WINELOADER backdoor, observed previously in January 2024, shares similarities with other APT29 malware families, implying a common developer. The targeting of political parties presents a potential threat to European and Western political organizations.
Relevancy & Insights:
Throughout the conflict between Russia and Ukraine, Germany has consistently denounced Russia’s aggression towards Ukraine. Germany has remained steadfast in its support for Ukraine, providing weapons, equipment, and substantial financial aid to bolster Ukraine’s security against Russian incursions. Given this support and Germany’s stance against Russian actions, it is conceivable that state-sponsored Russian threat actors may seek to target Germany’s political parties. By infiltrating political party systems, these actors could gather extensive intelligence, complementing information obtained from government departments. Understanding their objectives and strategic thinking is crucial in comprehending their motives and potential actions.
ETLM Assessment:
Renowned for its sophisticated tactics, APT29 employs diverse malware and occasionally develops new variants to bypass victim security measures, demonstrating a history of intricate attacks. Furthermore, its recent focus on a new industry within its target sector hints at potential plans to target additional political parties across various European nations. This is especially significant for nations strongly condemning Russia’s stance against Ukraine and providing robust support to Ukraine.
Recommendations:
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
AcidPour wiper used against Ukrainian Internet Providers
Researchers have discovered a new version of AcidRain, a wiper malware that was used against modems across Ukraine at the beginning of the Russian invasion in February 2022. The new strain has been dubbed “AcidPour” as the new version of the malware has advanced capabilities and destructive potential of the old version to now include Linux Unsorted Block Image (UBI) and Device Mapper (DM) logic, better targeting RAID arrays and large storage devices. The discovery of AcidPour coincides with the disruptions of four Ukrainian internet providers that began in mid-March. The longevity of the disruption suggests a more complex attack than a simple DDoS or nuisance disruption.
ETLM Assessment:
Russia is attacking Ukraine’s capacity to conduct self-defence holistically, and internet service disruptions are to be understood in this context in the same way as attacks on civilian infrastructure, but also the command-and-control capability of the armed forces of Ukraine. Ukraine is effectively utilizing civilian infrastructure in its defense, for example, using Google Meets to stream footage from drones or putting up 8000 cell phones connected to microphones on 6-foot poles around the country to detect incoming Russian drones. After the completion of the system, they can detect almost all Iran-supplied suicide drones and shoot the majority of them down using anti-aircraft guns, which is significantly cheaper and more sustainable than using surface-to-air rockets. This might be one of the reasons why the Russians targeted Ukrainian telecom providers with destructive cyber-attacks since mid-December.
The 8Base Ransomware impacts the Springfield Sign
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the United States of America; (www[.]springfieldsign[.]com), was compromised by the 8Base Ransomware. Springfield Sign is a full-service signage company that designs, manufactures, installs, and maintains professional custom signage. The compromised data includes Invoices, Receipts, Accounting documents, Personal data, Certificates, Employment contracts, a substantial volume of confidential information, Confidentiality agreements, Personal files, and other sensitive and confidential data.
The following screenshot was observed published on the dark web:

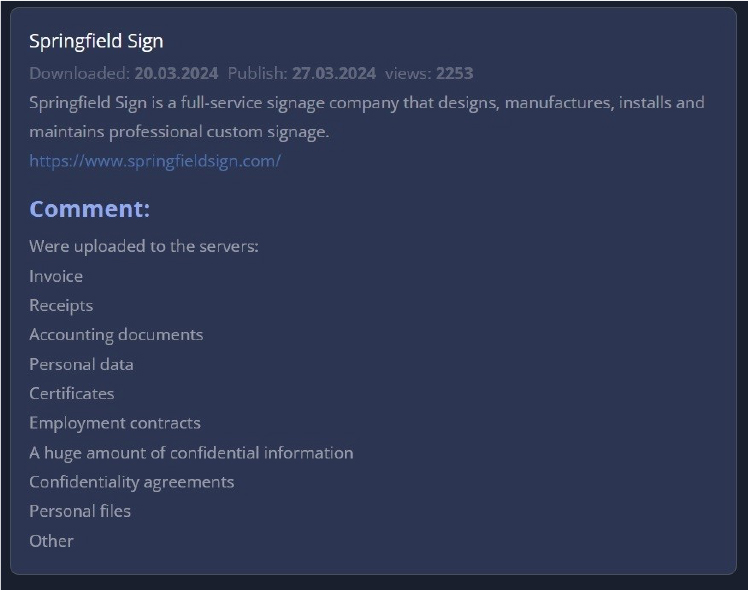
Source: Dark Web
Relevancy & Insights:
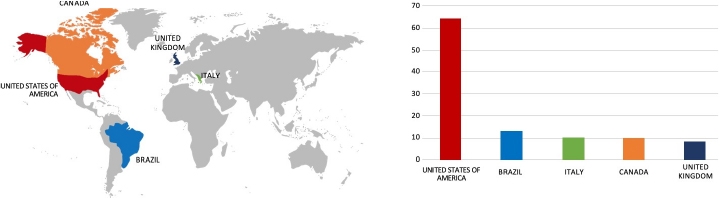
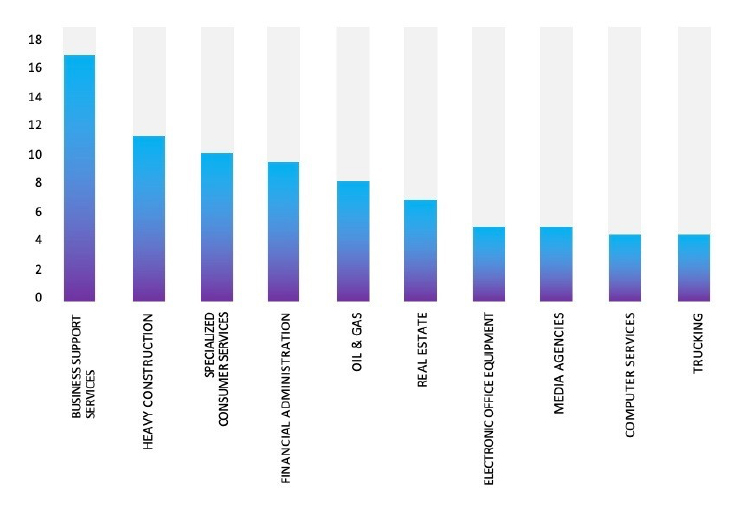
ETLM Assessment:
CYFIRMA’s evaluation underscores the ongoing and substantial global threat posed by the latest iteration utilized by the 8Base group. The recent attack on Springfield Sign, a manufacturing company based in the United States of America, serves as a stark reminder of the widespread risk associated with this specific ransomware.
Vulnerability in Grav
Summary:
The vulnerability allows a remote attacker to perform directory traversal attacks.
Relevancy & Insights:
The vulnerability exists due to input validation error when processing directory traversal sequences.
Impact:
A remote attacker can send a specially crafted HTTP request and upload arbitrary files on the system.
Affected Products: https[:]//github[.]com/getgrav/grav/security/advisories/GHSA-m7hx- hw6h-mqmc
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
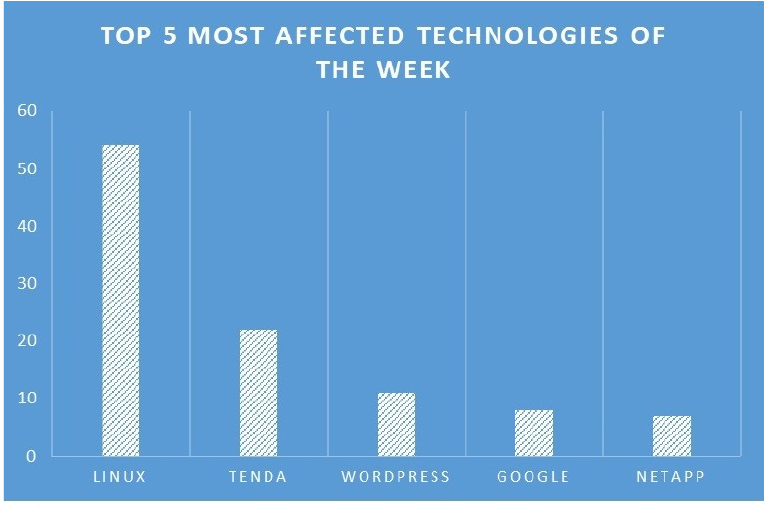
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
Rhysida ransomware claimed an attack on MarineMax
Summary:
The Rhysida ransomware group claims it was responsible for the cyberattack at a US luxury yacht dealer; MarineMax, earlier this month. MarineMax, Inc. (MarineMax) is a recreational boat and yacht retailer. It sells new and used recreational boats, including pleasure and fishing boats, and related marine products, including engines, trailers, parts, accessories, marine electronics, dock and anchoring products, boat covers, trailer parts and water sport accessories. More than $774 million worth of bitcoin has been demanded by Rhysida for the alleged stolen data, which includes the company’s customer databases, earnings reports, bank account transfers, balance sheets, and other financial records.
Relevancy & Insights:
Motivated by financial gains, Rhysida’s operators have been known to use phishing attacks as a means of gaining initial access, after which Cobalt Strike is used for lateral movement in infected machines. Numerous organizations have already been targeted by Rhysida since its emergence last May, with the most recent one being Chicago- based Lurie Children’s Hospital, which had all of its stolen data purportedly sold by the ransomware gang earlier this month, after the health provider’s failure to pay the $4 million ransom.
ETLM Assessment:
The Rhysida ransomware group emerged in May 2023 and has since set its sights on organizations across multiple sectors, including government, IT, manufacturing, healthcare, and education. Ongoing assessments by CYFIRMA from the current campaign indicate a strong likelihood of the Rhysida ransomware group persisting in its global operations, driven by the pursuit of substantial financial gains through ransomware activities.
SSML Carlo Bo data advertised on the Leak Site
Summary:
CYFIRMA Research team observed a potential data sale related to SSML Carlo Bo,
{www[.]ssmlcarlobo[.]it}. The Carlo Bo University for Linguistic Mediators (Istituto di Alti Studi SSML Carlo Bo) is an Italian institution with a presence in Milan (main office), Rome, Florence, Bologna and Bari. SSML Carlo Bo possesses a three-year course issuing a degree in Linguistic Mediation Sciences. The data for sale includes sensitive information such as ID, Enrolment Number, Password, Flag, Date, and other confidential data.
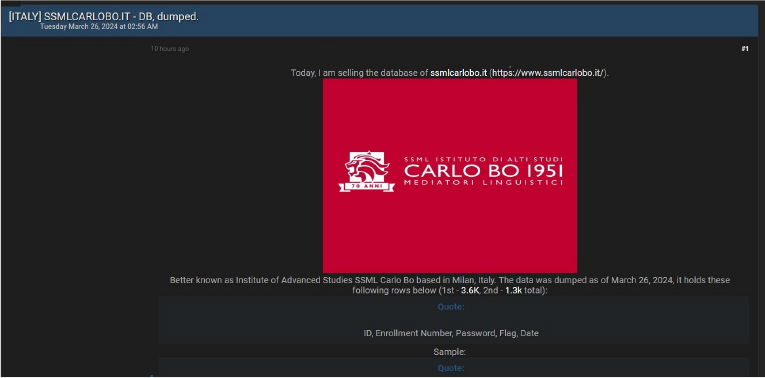
Source: Underground forums
Relevancy & Insights:
In the realm of cybersecurity, opportunistic cybercriminals driven by financial motives constantly scour the digital landscape for exposed and vulnerable systems and applications. A significant portion of these threat actors convene within underground forums, where discussions revolve around the exchange of stolen digital assets. Unlike ransomware or extortion groups, who often publicize their exploits, these perpetrators prefer to operate discreetly. They exploit unpatched systems or vulnerabilities in applications to illicitly gain access and pilfer valuable data. Subsequently, this stolen data finds its way into underground markets, where it is advertised, resold, and repurposed by other malicious actors to fuel their nefarious activities.
ETLM Assessment:
The cyber threat actor known as “N1k7′” holds a prominent position in the digital underworld, driven mainly by financial incentives. Presently, they are actively involved in the illegal trafficking of sensitive data, encompassing personally identifiable information (PII), financial records, and various other confidential datasets sourced from SSML Carlo Bo. CYFIRMA’s evaluation indicates that institutions within Italy lacking robust security measures and infrastructure are particularly vulnerable to potential cyber assaults orchestrated by this threat actor.
VNDirect and associated companies were attacked
Postal Insurance Corporation (PTI) reported a system attack starting from March 24, 2024, which affected their operations. VNDirect Securities, a company with a significant stake in PTI, also faced a similar attack along with its associated entities. IPA Investment Group and IPA Securities Investment Management Company (IPAAM) experienced website accessibility issues. Also, non-financial entities like Homefood Food Joint Stock Company encountered similar problems which are associated with VNDirect
The attack led to disruptions in VNDirect’s online trading system, prompting the Hanoi Stock Exchange (HNX) and Ho Chi Minh City Stock Exchange (HoSE) to suspend remote and online trading until the issue is fully resolved. VNDirect attributed the attack to an international organization but assured the safety of customer information and assets.
Despite assurances, investors could not access VNDirect’s online trading system by the end of the trading session. The company’s large dataset prolonged the reconnection process. VNDirect Securities, established in 2006, is a significant player in the market, ranking third in brokerage market share on HoSE in 2023.
Recommendations:
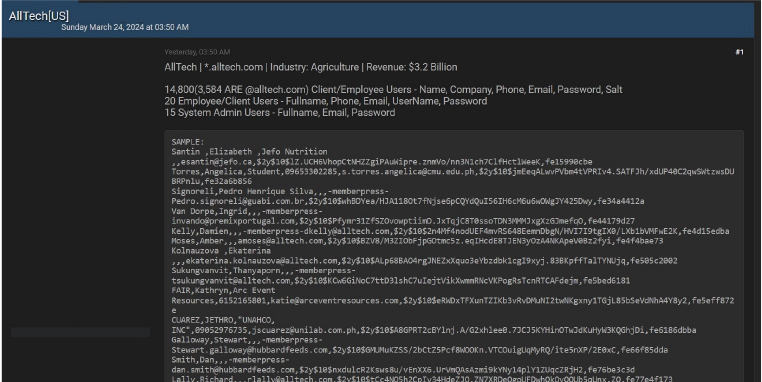
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS