



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows
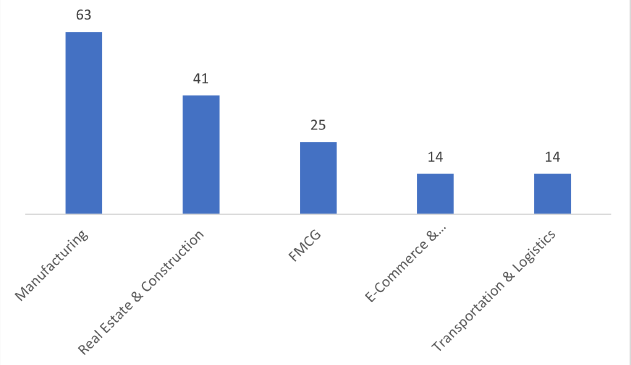
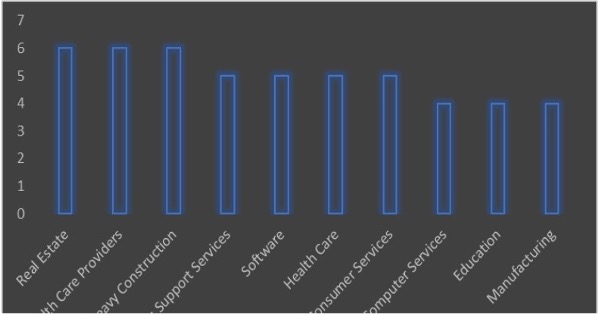
Target Industries: Accounting, Advertising & Marketing, Aerospace, Agriculture, Airlines, Apparel Retailers, Automobiles, Banks, Basic Resources, Business Services, Chemicals, Computer Services, Construction, Defense, Delivery Services, Electronic Equipment, Energy, Farming, Fishing & Plantations, Finance, Food & Beverage, Furniture, Government, Health Care, Hospitality, Industrial Goods & Services, Law, Manufacturing, Real Estate, Recreational Services, Retail, Semiconductors, Software, Specialized Consumer Services, Telecommunications, Transportation, Trucking and Utilities.
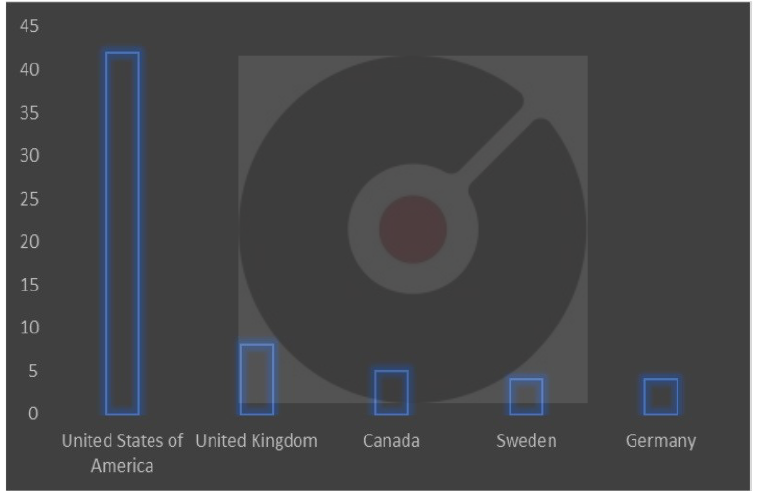
Target Geography: Australia, Canada, Czech Republic, Finland, France, Germany, Italy, Luxembourg, Mexico, Netherlands, Norway, Poland, Slovakia, South Africa, South Korea, Spain, Sweden, Switzerland, United Kingdom, United States.
Introduction
CYFIRMA Research and Advisory Team has found a Play Ransomware in the wild while monitoring various underground forums as part of our Threat Discovery Process.
Play
Play, also known as PlayCrypt, emerged as a ransomware threat in June 2022.
The Play ransomware group is thought to function as a closed unit, aiming to guarantee transaction confidentiality, as mentioned on their data leak website. Actors linked to Play ransomware follow a double-extortion approach, encrypting systems only after extracting data. The ransom notes from the group lack initial ransom demands or payment instructions; instead, victims are prompted to contact the threat actors via email.
To gain initial access to victim networks, the Play ransomware group exploits valid accounts and vulnerabilities in public-facing applications. They specifically target known vulnerabilities in FortiOS (CVE-2018-13379 and CVE-2020-12812) and Microsoft Exchange ( CVE2022-41040 and CVE-2022-41082). Threat actors also use external-facing services like Remote Desktop Protocol (RDP) and Virtual Private Networks (VPN).
The group uses tools such as AdFind for Active Directory queries and Grixba to check for a list of security files and processes. Additionally, they employ tools like GMER, IOBit, and PowerTool to disable anti-virus software and erase log files. In certain instances, Play ransomware actors are observed using PowerShell scripts to target Microsoft Defender.
For lateral movement and file execution, the threat actors leverage command and control (C2) applications like Cobalt Strike and SystemBC, along with tools like PsExec. Once inside a network, they actively search for unsecured credentials and use the Mimikatz credential dumper to gain domain administrator access. To identify additional privilege escalation paths, the group uses Windows Privilege Escalation Awesome Scripts (WinPEAS) and distributes executables through Group Policy Objects.
Compromised data is segmented, compressed using tools like WinRAR, and transferred via WinSCP to actor-controlled accounts. The files undergo encryption using AES-RSA hybrid encryption, with intermittent encryption applied to every other file portion of 0x100000 bytes. Notably, system files are exempt from this encryption process. Encrypted files receive a .play extension, and a ransom note named ReadMe.txt is dropped.
In the event of a refusal to pay the ransom, the actors threaten to publish exfiltrated data on their leak site accessible through the Tor network with an [.]onion URL. Victims are instructed to contact the Play ransomware group via an email address ending in @gmx[.]de, and ransom payments are expected in cryptocurrency to wallet addresses provided by the actors.
Tools Leveraged by Play Ransomware Actors
| Tool Name | Description |
| Mimikatz | Allows users to view and save authentication credentials such as Kerberos tickets. Play Threat actors have used it to add accounts to domain controllers. |
| WinPEAS | Used to search for additional privilege escalation paths. |
| WinRAR | Used to split compromised data into segments and to compress files into .RAR format for exfiltration. |
| WinSCP | Windows Secure Copy is a free and open-source Secure Shell (SSH) File Transfer Protocol, File Transfer Protocol, WebDAV, Amazon S3, and secure copy protocol client. Play ransomware actors have used it to transfer data from a compromised network to actor- controlled accounts. |
| Microsoft Nltest |
Used by Play ransomware actors for network discovery. |
| Nekto / | Used by Play ransomware actors for privilege |
| PriviCMD | escalation. |
| Process Hacker |
Used to enumerate running processes on a system. |
| Plink | Used to establish persistent SSH tunnels. |
| AdFind | Used to query and retrieve information from Active Directory. |
| GMER | A software tool intended to be used for detecting and removing rootkits |
| IOBit | An anti-malware and anti-virus program for the Microsoft Windows operating system. Play have accessed IOBit to disable anti-virus software. |
| PsExec | A tool designed to run programs and execute commands on remote systems. |
| PowerTool | A Windows utility designed to improve speed, remove bloatware, protect privacy, and eliminate data collection, among other things. |
| PowerShell | A cross-platform task automation solution made up of a command-line shell, a scripting language, and a configuration management framework, which runs on Windows, Linux, and macOS. |
| Cobalt Strike | A penetration testing tool used by security professionals to test the security of networks and systems. Play ransomware actors have used it to assist with lateral movement and file execution. |
In a recent development, the PLAY ransomware has adopted a ransomware-as-a-service (RaaS) model, opening access to a broader spectrum of users, ranging from proficient hackers to less experienced cyber criminals. This shift is anticipated to lead to a notable surge in incidents involving this ransomware.
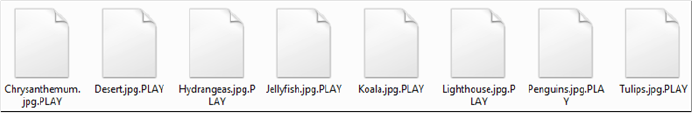
Screenshot of files encrypted by Play Ransomware (source: surface web)
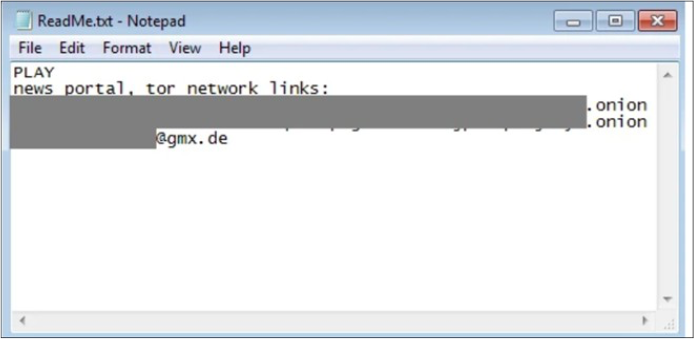
Fig: The ransom note of Play ransomware. (Source: Surface Web)
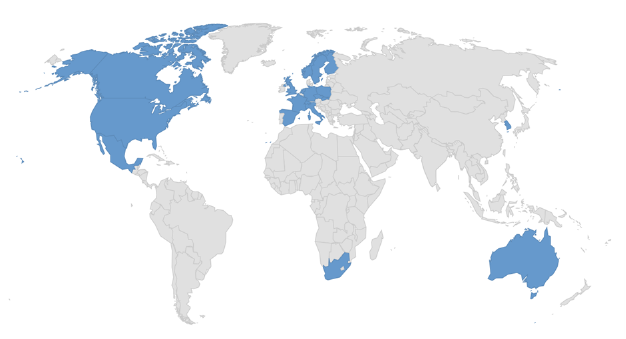
Countries targeted by Play Ransomware.
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0001: Initial Access | T1091: Replication Through Removable Media |
| T1190: Exploit Public-Facing Application | ||
| 2 | TA0002: Execution | T1129: Shared Modules |
| 3 | TA0003: Persistence |
T1574.002: Hijack Execution Flow: DLL Side- Loading |
| 4 | TA0004: Privilege | T1055: Process Injection |
| Escalation | T1574.002: Hijack Execution Flow: DLL Side- Loading | |
| 5 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1027.005: Obfuscated Files or Information: Indicator Removal from Tools | ||
| T1055: Process Injection | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 6 | TA0006: Credential Access | T1003: OS Credential Dumping |
| T1056: Input Capture | ||
| 7 | TA0007: Discovery | T1057: Process Discovery |
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1120: Peripheral Device Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 8 | TA0008: Lateral Movement | T1091: Replication Through Removable Media |
| 9 | TA0009: Collection | T1005: Data from Local System |
| T1056: Input Capture | ||
| 10 | TA0040: Impact | T1486: Data Encrypted for Impact |
Relevancy and Insights:
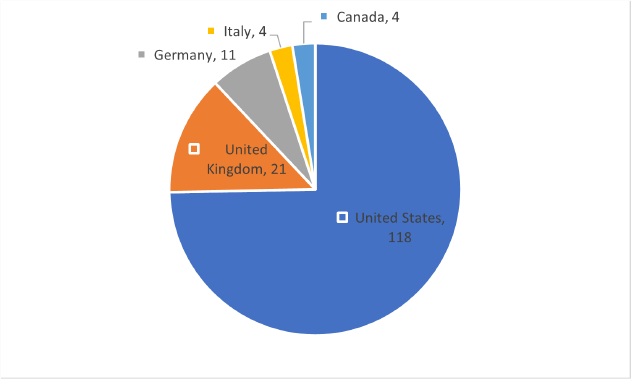
ETLM Assessment:
CYFIRMA’s assessment based on available information suggests that, in the future, the PLAY ransomware, now operating as a RaaS, is likely to cause a widespread increase in cyber-attacks. This shift enables a wide range of users, from skilled hackers to beginners, to use ransomware, potentially leading to more incidents. The group’s tactics like exploiting vulnerabilities in popular applications and using various tools to disable security measures will continue. As this ransomware becomes more accessible, cybersecurity challenges may escalate, necessitating increased vigilance and proactive measures to counter potential threats.
Yara Rule
rule win_play_auto { strings:
$sequence_0 = { 0fb78d82feffff 2bc8 899570ffffff 014d84 }
// n = 4, score = 100
// 0fb78d82feffff | movzx ecx, word ptr [ebp – 0x17e]
// 2bc8 | sub ecx, eax
// 899570ffffff | mov dword ptr [ebp – 0x90], edx
// 014d84 | add dword ptr [ebp – 0x7c], ecx
$sequence_1 = { 02c1 c645c5ae 8845c3 b937030000 888556ffffff 8a45c7 c6852fffffff00 }
// n = 7, score = 100
// 02c1 | add al, cl
// c645c5ae | mov byte ptr [ebp – 0x3b], 0xae
// 8845c3 | mov byte ptr [ebp – 0x3d], al
// b937030000 | mov ecx, 0x337
// 888556ffffff | mov byte ptr [ebp – 0xaa], al
// 8a45c7 | mov al, byte ptr [ebp – 0x39]
// c6852fffffff00 | mov byte ptr [ebp – 0xd1], 0
$sequence_2 = { 8bd8 899d88fdffff 85db 0f8483040000 8a0b 80f9e9 7409 }
// n = 7, score = 100
// 8bd8 | mov ebx, eax
// 899d88fdffff | mov dword ptr [ebp – 0x278], ebx
// 85db | test ebx, ebx
// 0f8483040000 | je 0x489
// 8a0b | mov cl, byte ptr [ebx]
// 80f9e9 | cmp cl, 0xe9
// 7409 | je 0xb
$sequence_3 = { c83dad3c d92b e00c 9c 0d05f0657b 4e f30f7e05???????? }
// n = 7, score = 100
// c83dad3c | enter -0x52c3, 0x3c
// d92b | fldcw word ptr [ebx]
// e00c | loopne 0xe
// 9c | pushfd
// 0d05f0657b | or eax, 0x7b65f005
// 4e | dec esi
// f30f7e05???????? |
$sequence_4 = { 7f06 81c4ab000000 83c410 e8???????? 66f1 }
// n = 5, score = 100
// 7f06 | jg 8
// 81c4ab000000 | add esp, 0xab
// 83c410 | add esp, 0x10
// e8???????? |
// 66f1 | int1
$sequence_5 = { a1???????? 8945bc a1???????? 0f11855cffffff 894594 f30f7e05???????? 8b45f8 }
// n = 7, score = 100
// a1???????? |
// 8945bc | mov dword ptr [ebp – 0x44], eax
// a1???????? |
// 0f11855cffffff | movups xmmword ptr [ebp – 0xa4], xmm0
// 894594 | mov dword ptr [ebp – 0x6c], eax
// f30f7e05???????? |
// 8b45f8 | mov eax, dword ptr [ebp – 8]
$sequence_6 = { 91 ae 54 ce 3106 f77cf30f 7e05 }
// n = 7, score = 100
// 91 | xchg eax, ecx
// ae | scasb al, byte ptr es:[edi]
// 54 | push esp
// ce | into
// 3106 | xor dword ptr [esi], eax
// f77cf30f | idiv dword ptr [ebx + esi*8 + 0xf]
// 7e05 | jle 7
$sequence_7 = { 8955f4 8b460c 83ec08 8d0488 8945f8 8d45f4 }
// n = 6, score = 100
// 8955f4 | mov dword ptr [ebp – 0xc], edx
// 8b460c | mov eax, dword ptr [esi + 0xc]
// 83ec08 | sub esp, 8
// 8d0488 | lea eax, [eax + ecx*4]
// 8945f8 | mov dword ptr [ebp – 8], eax
// 8d45f4 | lea eax, [ebp – 0xc]
$sequence_8 = { 898d48fdffff 66898562fdffff 668985e6fcffff 66398d30fdffff 7634 66ff857cfcffff 8d0432 }
// n = 7, score = 100
// 898d48fdffff | mov dword ptr [ebp – 0x2b8], ecx
// 66898562fdffff | mov word ptr [ebp – 0x29e], ax
// 668985e6fcffff | mov word ptr [ebp – 0x31a], ax
// 66398d30fdffff | cmp word ptr [ebp – 0x2d0], cx
// 7634 | jbe 0x36
// 66ff857cfcffff | inc word ptr [ebp – 0x384]
// 8d0432 | lea eax, [edx + esi]
$sequence_9 = { 88852effffff 8b8548ffffff fec8 8855ad 88854dffffff 8d45e8 6689bd0cfeffff }
// n = 7, score = 100
// 88852effffff
// 8b8548ffffff
// fec8
// 8855ad
// 88854dffffff | mov
| mov
| dec
| mov
| mov
al byte ptr [ebp – 0xd2], al eax, dword ptr [ebp – 0xb8]
byte ptr [ebp – 0x53], dl byte ptr [ebp – 0xb3], al
// 8d45e8 | lea eax, [ebp – 0x18]
// 6689bd0cfeffff | mov word ptr [ebp – 0x1f4], di
condition:
7 of them and filesize < 389120
}
(Source: Surface web)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Stealer
Objective: Information Stealing, Data exfiltration
Target Technology: Windows & macOS, Browsers (Chrome, Firefox)
Active Malware of the Week
This week “JaskaGO” is trending.
JaskaGO
A new and advanced malware strain named JaskaGO, developed in the Go programming language, has been identified as a serious threat to both Windows and macOS operating systems. This malware is particularly concerning because traditional antivirus solutions currently have low detection rates, making it a stealthy adversary. The use of Go, known for its simplicity and cross-platform capabilities, is a growing trend in malware development. Despite the common belief in the security of macOS, JaskaGO highlights the misconception that it is immune to malware, emphasizing the ongoing risk for both Windows and macOS users.
The first JaskaGo sample was observed in July 2023, initially targeted Mac users by masquerading as well-known applications (such as “Capcut_Installer_Intel_M1.dmg” and “Anyconnect.exe”) with deceptive file names. This malware employs a common strategy of deploying under the guise of legitimate software, especially on pirated application web pages. As the threat evolved, dozens of new samples have emerged, now impacting both macOS and Windows systems. Its low detection rate by antivirus engines underscores its adaptability and the ongoing challenge of identifying and preventing its spread.
Attack method
The malware, upon its first execution, cleverly generates a deceptive message box featuring a fake error message alleging a missing file. This strategic approach aims to mislead the user, creating the impression that the malicious code has encountered a failure in execution.
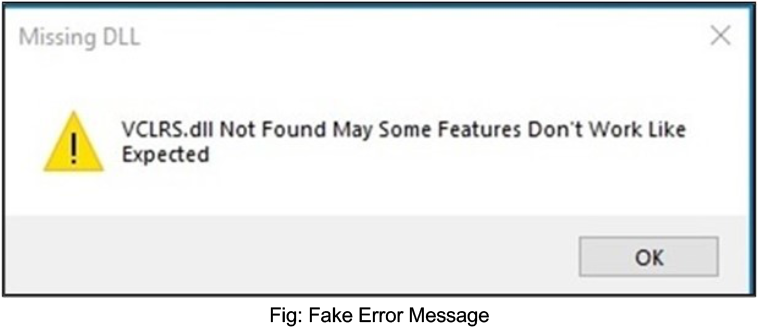
The malware performs comprehensive checks to ascertain whether it is running on a virtual machine (VM). These checks involve examining general machine information, including criteria such as the number of processors, system up-time, available system memory, and MAC addresses. Notably, the presence of MAC addresses linked to popular VM software like VMware or VirtualBox serves as a crucial indicator. Furthermore, on Windows systems, the malware searches for VM-related traces in both the registry and file system. If the malware identifies that it is operating within a virtual environment, it proceeds to randomly execute one of the following commands:
Upon bypassing VM detection, JaskaGO proceeds to gather information from the victim and establishes a connection to its command-and-control server for subsequent actions. The malware consistently queries its command-and-control server, anticipating instructions. Possible commands include:
Stealer
JaskaGO comes with powerful data exfiltration features, storing gathered information in a designated folder and then sending the compressed data to the malware’s threat actor when ready.
Browser stealer
JaskaGO, by default, is capable of stealing information from Chrome and Firefox browsers, but it can be customized to target other browsers as well. The collected browser information comprises:
Crypto currency stealer
The malware scans for crypto wallet extensions within the “Local Extension Settings” folder of the browser’s extension directory. Moreover, it has the capability to receive a specified list of wallets to search for and subsequently upload to the server.
Files
The malware has the capability to receive a designated list of files and folders for exfiltration.
Persistence Mechanisms in JaskaGO: Windows and macOS
Windows
In the Windows version, JaskaGO ensures persistence through two methods. First, it creates a service and initiates its execution. Additionally, it employs an unconventional yet effective approach by generating a Windows Terminal profile, specifically the file “C:\users$env: UserName\AppData\Local\Packages\Microsoft.WindowsTerminal_*\LocalState\settings.jso n.” This file is configured to run automatically upon a Windows reboot, initiating a PowerShell process to execute the malware.
macOS
On macOS, JaskaGO employs a multi-step process to establish persistence within the system. It begins by attempting execution with root privileges, followed by the systematic disabling of the Gatekeeper security feature using the command “spctl –master- disable.”This action aims to bypass security checks and facilitate unhindered operation. The malware then duplicates itself, adopting a naming format like “com.%s.appbackgroundservice,” where %s is replaced by a randomly generated string, enhancing its obfuscation on the system. Finally, based on successful root access, the malware creates either the LaunchDaemon “/Library/LaunchDaemons/Init.plist” or LaunchAgent “/Library/LaunchAgents/service.plist” to ensure automatic execution during system startup, deeply embedding itself into the macOS environment.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the evolving sophistication of threats like JaskaGO signals a persistent challenge for organizations in safeguarding their systems. As cybercriminals continue to leverage advanced techniques and cross- platform capabilities, the impact on organizations could extend beyond data compromise to potential disruptions in critical operations. The cross-platform nature of JaskaGO suggests that future malware may increasingly target multiple operating systems, demanding comprehensive security solutions that can effectively counter threats on various fronts. The potential for more intricate data-stealing capabilities poses a heightened risk to sensitive information, necessitating organizations to bolster their defenses against evolving attack vectors. Additionally, the reliance on command- and-control servers highlights the importance of continuous monitoring and threat intelligence integration to stay ahead of cyber adversaries. The impact of advanced threats like JaskaGO could extend to financial losses, reputational damage, and operational disruptions.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
❍
Threat Actor UAC-0050 Attacks Ukrainian Region by Employing RemcosRAT
Summary:
In a recent observation, Ukraine’s Government Computer Emergency Response Team; CERT-UA, detected a widespread email campaign with the subject, “Debts under the Kyivstar contract.” The email contained an attachment, “Subscriber’s debt.zip,” which holds a password-protected RAR archive split into two parts. Within this RAR archive lies a similarly named password-protected document, “Subscriber Debt.doc,” containing a potentially malicious macro. Activating the macro downloads and executes malicious executables such as “GB.exe” via explorer.exe, using the SMB protocol. This file is an SFX archive housing a BATCH script aimed at retrieving and launching “wsuscr.exe” from bitbucket. Encrypted via SmartAssembly .NET, this executable intends to decrypt and initiate the RemcosRAT remote control program. Correspondingly, emails labeled “SBU request” contained a “Documents.zip” attachment, housing “Request.rar,” which includes “Request.exe.” Execution of these files may lead to RemcosRAT infection. Moreover, apart from the typical UAC-0050 server placement within Shinjiro, the RemcosRAT management servers were identified within AS44477 (STARK INDUSTRIES SOLUTIONS LTD).
Relevancy & Insights:
In the first week of December, another phishing campaign attributed to UAC-0050 containing emails titled “judicial claims” and “debts” attached with password-protected RAR archives was identified targeting the Ukranian region. Opening these archives and executing the enclosed files potentially infected the computer with RemcosRAT or MeduzaStealer. It is interesting to note that the threat actor used already compromised accounts to send phishing emails and tactics used in the previous campaign, which are almost similar to the tactics used in the recent campaign.
ETLM Assessment:
UAC-0050; a threat actor possibly linked to Russia, has consistently targeted Ukraine with repeated attacks. In a single month, Ukrainian CERT identified two distinct campaigns by UAC-0050 aimed at the Ukrainian region. These attacks are believed to be part of cyber espionage aiding Russia in the ongoing conflict. The likelihood of these attacks persisting and intensifying, further favouring Russia in the ongoing conflict with Ukraine, is evident.
Recommendations:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
NSA’s look at 2023 in review
ETLM Assessment:
The People’s Republic of China (PRC) has emerged as the pacing challenge to the United States and as a competitor with both the intent and ability to reshape the international order to fit its own designs. The PRC, an adversary that is unique in the scope, scale, and sophistication of the threat it poses, has stated its desire to become one of the world’s leading powers and the cyberspace has been forming an advance guard of China’s designs for world order, a trend that is posed to continue in 2024. By NSA’s admission, Russia remains an acute threat and continues to threaten regional security and global stability through its disregard of international norms and its willingness to use its weapons to target civilians and critical infrastructure. We’ve witnessed numerous telling examples of this during Russia’s invasion of Ukraine. Both China and Russia have also deployed information operations, intended to weaken democratic institutions around the world, a threat that will be most acute in 2024 with important presidential elections scheduled in the USA and in Taiwan.
China’s hackers exploiting SOHO routers
Volt Typhoon, an APT working on behalf of Beijing, has been found actively exploiting vulnerabilities in small office/home office routers produced by Cisco, Netgear and Fortinet. The routers are at their end-of-life, outdated and no longer supported. Volt Typhoon’s activity exploiting these devices in the KV-botnet was also used earlier this year to attack U.S. infrastructure in Guam as we have reported earlier this year. According to researchers, the activity suggests battlespace preparation and staging for further infrastructure attacks against US targets.
ETLM Assessment:
Commonwealth Capital is Impacted by the BianLian Ransomware
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Singapore; (www[.]commonwealthcapital[.]asia), was compromised by BianLian Ransomware. Commonwealth Capital Pte Ltd (CCPL) is a Singapore-based investment company with a F&B portfolio from end-to-end manufacturing, logistics to retail services. Focusing on the food vertical value chain, CCPL portfolio of companies engage in Barramundi farming, in-house production of meat, bakery, ice cream & ready-to-eat products. It operates state-of-the-art warehousing and logistics services for food retailers and manages over 300 retail points in 13 countries. The compromised data encompasses a wide range of sensitive information, totalling 2TB in size. This includes financial records, human resources data, confidential information belonging to clients and partners, non-disclosure agreements, proprietary recipes, and various trade secrets. Additionally, internal, and external email correspondences, SQL databases, and other forms of confidential data have been compromised. The extent of the breach poses a significant threat to the privacy and security of the affected individuals and organizations.
The following screenshot was observed published on the dark web:
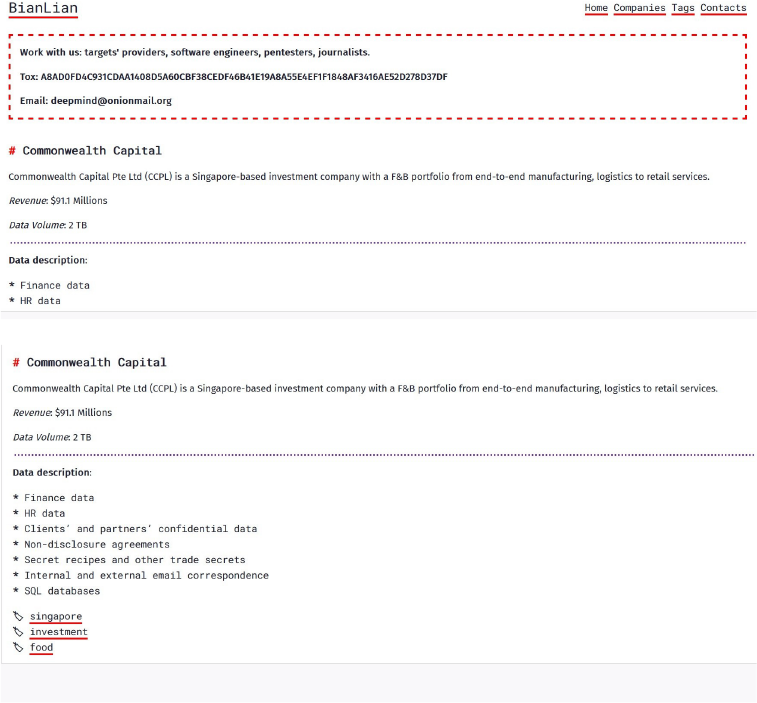
Source: Dark Web
Relevancy & Insights:
Vulnerability in Engelsystem
Summary:
Engelsystem prior to v3.4.1 performed insufficient validation of user supplied data for the DECT number, mobile number, and work-log comment fields.
Relevancy & Insights:
The values of those fields would be displayed in corresponding log overviews, allowing the injection and execution of Javascript code in another user’s context.
Impact:
This vulnerability enables an authenticated user to inject Javascript into other user’s sessions. The injected JS will be executed during normal usage of the system when viewing, e.g., overview pages.
Affected Products: https[:]//github[.]com/engelsystem/engelsystem/security/advisories/GHSA-p5ch-rrpm-wvhm
Recommendations:
Monitoring and Detection: : Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
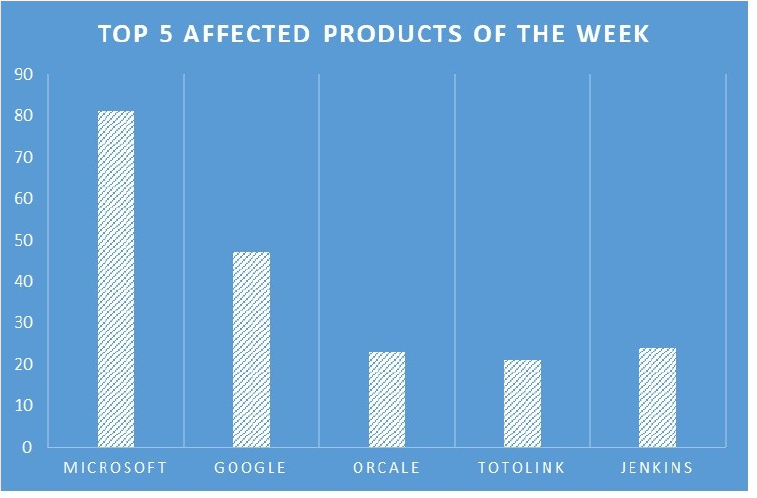
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products, due to a range of vulnerabilities. The following are the top 5 most affected products.
FalseFont Malware Targets Defence Contractors Worldwide
Summary:
The APT33 hacking group from Iran has recently introduced a novel malware known as FalseFont, with a noticeable increase in activity reported by Microsoft in December 2023. Our recent observations reveal that the Iranian APT33 has deployed this newly developed backdoor malware, targeting the global Defense Industrial Base (DIB). The DIB sector, which encompasses over 100,000 companies and subcontractors, is confronted with an elevated risk. Given its crucial role in the development of military weapons systems, these entities are attractive targets for cyber espionage.
Initiated in February 2023, the FalseFont campaign represents a continuation of a series of attacks. During this period, Peach Sandstorm, a subgroup of APT33, conducted extensive password spray attacks against thousands of global organizations. FalseFont; a tailor-made backdoor, facilitates remote access to compromised systems. This tool empowers its operators with extensive control, enabling file execution and transfer to command-and-control servers. First detected in early November 2023, FalseFont signifies a significant evolution in Peach Sandstorm’s tradecraft, posing a notable threat in the realm of cyber espionage.
Relevancy & Insights:
APT33, aka Peach Sandstorm, Refined Kitten, or Holmium, is an Iranian cyber espionage group active since at least 2013. It is considered a high-risk threat due to its sophisticated use of malware, complex social engineering, and targeted attacks against high-value organizations. The gang primarily targets organizations in the United States, Saudi Arabia, and South Korea. It appears to be particularly interested in the aerospace and energy sectors.
ETLM Assessment:
The Iranian government-sponsored espionage group, APT33, focuses its efforts on targeting organizations in the United States, Saudi Arabia, and South Korea. According to CYFIRMA assessments from the ongoing campaign, it is particularly essential for entities situated in nations with adversarial relations with Iran to exercise heightened caution against phishing attacks and social engineering tactics.
FIC and Shuttle Inc Data Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to FIC and Shuttle, {www[.]fic[.]com[.]tw} and {www[.]shuttle[.]com}. First International Computer, Inc. (FIC) a world leader in the design and production of electronic devices, now is focusing its core business on building automation systems, tablet PCs, and wireless communication devices. Shuttle Inc. is a Taiwan-based manufacturer of motherboards, barebone computers, complete PC systems, and monitors. The data available for sale comprises sensitive details such as names, phone numbers, gender, birthdates, addresses, email addresses, passwords, and other confidential information.
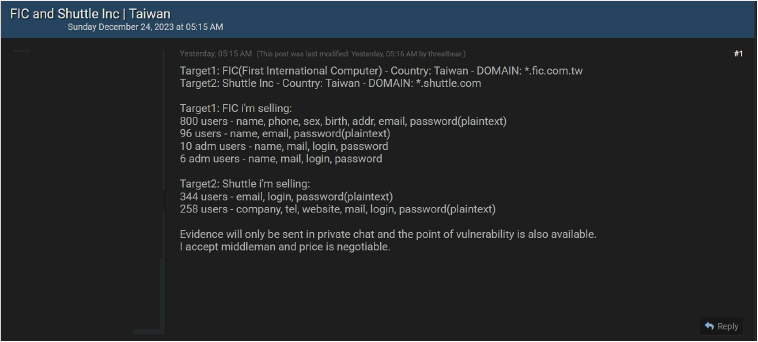
Source: Underground forums
Relevancy & Insights:
Cybercriminals driven by financial motives are opportunistic and consistently seek out exposed and vulnerable systems and applications. This particular breed of attackers predominantly operates within underground forums, engaging in discussions related to their illicit activities and participating in the trade of stolen digital goods. In contrast to other financially motivated groups, such as ransomware or extortion groups that often publicize their exploits, these attackers prefer to keep a low profile. Their modus operandi involves exploiting unpatched systems or vulnerabilities in applications and systems to gain unauthorized access and pilfer valuable data. The stolen data is subsequently advertised for sale within these clandestine forums, where it may be further resold and repurposed by other cybercriminals for their malicious activities. This covert approach allows them to quietly profit from their illicit endeavors without drawing undue attention.
ETLM Assessment:
CYFIRMA’s assessment highlights that financially motivated cybercriminals find Taiwan and other advanced economies in Asia to be appealing targets. Consequently, CYFIRMA perceives a persistent and ongoing threat to companies in technologically advanced nations, particularly Taiwan. Industries such as manufacturing remain susceptible to the intentions of financially motivated threat actors who are likely to continue their targeting activities in these sectors. This underscores the importance of heightened cybersecurity measures for organizations operating in technologically advanced regions, as they remain prime targets for cyber threats aimed at financial gains.
CYFIRMA Research team observed a potential data leak related to Lendenclub, {www[.]Lendenclub[.]com}. LenDenClub is the fastest-growing peer-to-peer platform in India. Listing only pre-verified loans, LenDenClub offers investors a convenient medium to browse thousands of loans to earn better than fixed deposits, mutual funds, etc. The compromised data encompasses a range of sensitive information, including but not limited to user credentials such as ID, password, and last login details.
Additionally, the exposed data includes indicators of account privileges like ‘is_superuser,’ as well as personal details like user ID, first name, middle name, last name, gender, mobile number, mobile number verification status, email, email verification status, date of birth (DOB), marital status, Aadhar number, PAN (Permanent Account Number), occupation, gross annual income, and various other confidential pieces of information. The compromise of such extensive and private details poses a significant threat to the affected individuals’ privacy and security.

Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS