CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This covers a variety of topics that can be pertinent to your company, including technology, geography, and industries.
Type: Ransomware
Target Technologies: Windows
Introduction
CYFIRMA Research and Advisory Team has found ChickenKiller Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
ChickenKiller Ransomware
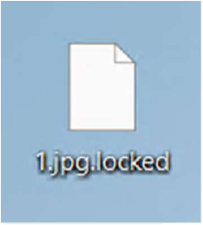
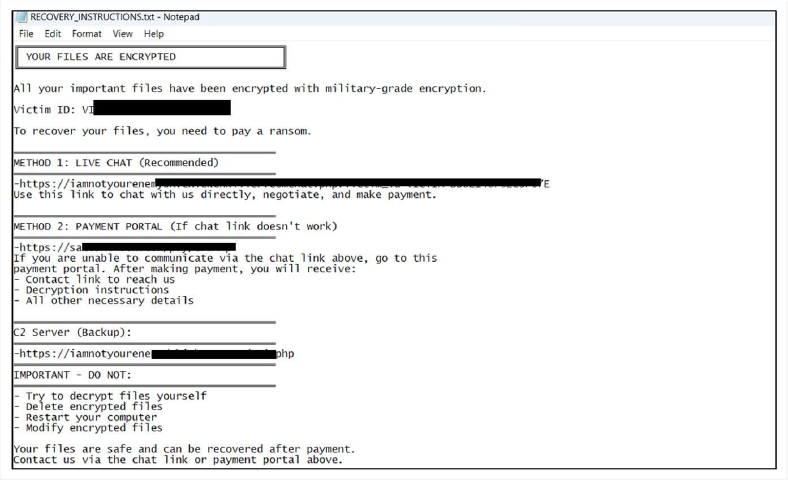
Researchers have identified ChickenKiller as a ransomware-type program designed to encrypt data and append the “.locked” extension to affected files During execution, the malware encrypts user files, prevents further access, and drops a ransom note titled “RECOVERY_INSTRUCTIONS.txt.” The sample with capability that once encryption has occurred, file restoration is less likely possible without the attackers’ decryption mechanism, and removing the malware only stops additional damage. As with similar ransomware families, recovery is best feasible through pre-existing backups stored separately from the infected system.
The ransom note accompanying ChickenKiller outlines that the victim’s data has been encrypted with “military-grade” methods and assigns a unique Victim ID. It directs victims to a live chat link or a secondary payment portal, both intended to facilitate negotiation and ransom payment. The message also issues strict warnings against modifying or deleting encrypted files, attempting manual decryption, or restarting the computer. Through these instructions, the operators attempt to control the victim’s actions and pressure payment while offering no guarantee of actual file recovery.
The following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Initial Access | T1091 | Replication Through Removable Media |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1053.002 | Scheduled Task/Job: At |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1106 | Native API |
| Execution | T1129 | Shared Modules |
| Execution | T1569.002 | System Services: Service Execution |
| Persistence | T1053.002 | Scheduled Task/Job: At |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Persistence | T1112 | Modify Registry |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Persistence | T1546.012 | Event Triggered Execution: Image File Execution Options Injection |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1053.002 | Scheduled Task/Job: At |
| Privilege Escalation | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Privilege Escalation | T1055.003 | Process Injection: Thread Execution Hijacking |
| Privilege Escalation | T1055.012 | Process Injection: Process Hollowing |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1546.012 | Event Triggered Execution: Image File Execution Options Injection |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055.003 | Process Injection: Thread Execution Hijacking |
| Defense Evasion | T1055.012 | Process Injection: Process Hollowing |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1564.004 | Hide Artifacts: NTFS File Attributes |
| Defense Evasion | T1620 | Reflective Code Loading |
| Discovery | T1012 | Query Registry |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1120 | Peripheral Device Discovery |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1518 | Software Discovery |
| Lateral Movement | T1091 | Replication Through Removable Media |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1568 | Dynamic Resolution |
| Command and Control | T1573 | Encrypted Channel |
| Impact | T1485 | Data Destruction |
| Impact | T1489 | Service Stop |
| Impact | T1490 | Inhibit System Recovery |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment indicates that ChickenKiller fits within the broader landscape of financially motivated ransomware operations, which continue to leverage file- encryption, data-locking mechanisms, and victim coercion as their primary means of extortion. In general, ransomware groups refine their tooling to maximize impact with minimal operator effort focusing on rapid encryption, automated payload deployment, and persistent communication channels for ransom negotiation. The goal remains consistent: disrupt business continuity enough to force payment while maintaining operational anonymity.
Going forward, threat actors behind campaigns like ChickenKiller can be expected to evolve by incorporating more efficient delivery methods, improved evasion techniques, and multi-layered extortion tactics. Their operations may also shift toward increasingly modular codebases, allowing quick adaptation to defensive countermeasures. As ransomware ecosystems grow more service-oriented, actors can diversify approaches including targeting smaller organizations with weaker defenses or using automated reconnaissance to tailor ransom demands, making the threat landscape progressively more dynamic and challenging for defenders.
Sigma rule:
title: Boot Configuration Tampering Via Bcdedit.EXE tags:
– attack.impact
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection_img:
– Image|endswith: ‘\bcdedit.exe’
– OriginalFileName: ‘bcdedit.exe’ selection_set:
CommandLine|contains: ‘set’ selection_cli:
– CommandLine|contains|all:
– ‘bootstatuspolicy’
– ‘ignoreallfailures’
– CommandLine|contains|all:
– ‘recoveryenabled’
– ‘no’
condition: all of selection_* fields:
– ComputerName
– User
– CommandLine falsepositives:
– Unlikely level: high
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Stealer| Objectives: Credential Theft, Data Exfiltration | Target Technologies: Windows OS| Target Industry: Financial Sector (Banks, Payment Services, Cryptocurrency Exchanges/Wallets) | Target Geography: Brazil
CYFIRMA collects data from various forums. We have identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week, “Eternidade” is trending.
Overview of Eternidade Malware
Eternidade Stealer is a recently identified malware that has gained attention for its quiet delivery, its ability to adapt to the victim’s system, and its region-specific targeting. It checks the operating system language and activates only on devices set to Brazilian Portuguese, displaying an error message and stopping execution on any other setting.
The operation relies on compromised WhatsApp accounts to send messages that appear genuine, convincing recipients to open files they believe were shared by trusted contacts. Once executed, the malware deploys several coordinated components that quietly collect user information, harvest contact lists, monitor on-device activity, and spread further through the victim’s own WhatsApp interactions. Its modular structure and use of common communication pathways allow it to blend in with normal device behaviour, making detection significantly more difficult.
A key characteristic of this campaign is its deliberate focus on specific environments and controlled activation. Eternidade Stealer is designed to operate only on systems that match the Brazil region and Portuguese language setting, while actively avoiding virtual machines or configurations that could expose its presence. It maintains a persistent connection to attacker-controlled infrastructure, periodically retrieving updated instructions to sustain access over time. Although the malware is tailored for Brazilian users, telemetry linked to its supporting infrastructure shows activity from multiple countries, hinting at a broader reach than originally intended. Overall, the campaign demonstrates how widely used messaging platforms can be weaponised to deliver sophisticated, socially engineered threats that seamlessly blend into everyday digital communication.
Attack Method
The Eternidade Stealer campaign is distributed through a WhatsApp-based worm, where attackers hijack WhatsApp on infected devices to send malicious attachments to victims’ contacts. Instead of relying on technical exploits, the attackers use a highly effective form of social manipulation, sending messages that appear to originate from trusted contacts. When the victim opens the attached file, a hidden execution sequence begins, reaching out to attacker-controlled servers to download the next-stage components. By delivering the initial payload through a familiar and credible communication channel, the operation significantly reduces suspicion and increases the likelihood of successful infection, particularly among Brazilian users.
Stealth Deployment Strategy
Upon execution, the malware proceeds to operate quietly in the background. Before enabling any harmful capabilities, it performs a series of system checks to ensure the device matches the intended target environment. The malware activates only on systems configured for Brazilian users and deliberately avoids virtual machines, analytical environments, and non-Brazilian language settings. Once this validation is complete, it retrieves multiple lightweight modules that each perform a specific role. These modules are transferred through ordinary network requests and distributed across shifting infrastructure, allowing the campaign to blend into routine device activity and evade standard security monitoring.
Data Theft and Persistence
With the full set of components in place, Eternidade Stealer initiates a structured data- collection process. It extracts WhatsApp contacts, monitors user activity, and identifies when financial or cryptocurrency applications are accessed, triggering specialized routines to capture additional information. All harvested data is transmitted to the attackers through their command-and-control channel. To maintain ongoing control, the malware keeps a persistent connection to its infrastructure, routinely retrieving updated instructions and re-establishing access after system restarts. This modular and adaptive design ensures sustained visibility, minimal detection, and long-term persistence on infected devices.
Following are the TTPs based on the MITRE Attack Framework for Enterprise
| Tactic | Technique ID | Technique Name |
| Initial Access | T1566.001 | Phishing: Spearphishing Attachment |
| Execution | T1204.002 | User Execution: Malicious File |
| Persistence | T1547 | Boot or Logon Autostart Execution |
| Privilege Escalation | T1055 | Process Injection |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Credential Access | T1555 | Credentials from Password Stores |
| Credential Access | T1556 | Modify Authentication Process |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1057 | Process Discovery |
| Collection | T1056 | Input Capture |
| Command & Control | T1105 | Ingress Tool Transfer |
| Command & Control | T1102 | Web Services |
| Command & Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
INSIGHTS
One of the most striking elements of the Eternidade Stealer campaign is how deeply it relies on human trust rather than technical force. By spreading through hijacked WhatsApp on infected devices the attackers position themselves inside personal conversations, allowing malicious files to arrive as if they were ordinary messages from friends, family members, or colleagues. This bypasses many of the psychological barriers users typically rely on when judging suspicious content. The campaign highlights how digital attackers increasingly exploit personal relationships and everyday communication habits, turning familiar interactions into effective delivery vehicles for harmful activity.
Another key insight from this operation is its careful selection of targets and deliberate effort to remain unnoticed by security analysts. Instead of activating universally, the malware limits itself to devices configured for Brazilian users, while refusing to run on systems that appear to belong to researchers or automated analysis tools. This level of selectivity reflects a disciplined strategy, where the attackers avoid unnecessary exposure and focus solely on environments most likely to yield valuable results. The combination of narrow targeting and selective activation creates an ecosystem where the campaign can continue functioning quietly without drawing early attention from cybersecurity communities.
Although the malware itself is designed to function primarily within Brazil, the infrastructure surrounding the campaign has attracted global interaction. Network records indicate that systems from numerous countries attempted to access the attacker’s resources, demonstrating how interconnected digital ecosystems unintentionally extend the footprint of a localised threat. This does not imply global targeting but instead reflects how modern communications, shared servers, and automated scanning tools create broader visibility. Such patterns show that even region-specific malware can produce signals far beyond its intended scope, making its operational presence detectable across a much wider landscape.
ETLM ASSESSMENT
From an ETLM perspective, CYFIRMA assesses that the Eternidade Stealer campaign reflects an emerging landscape in which organizations and employees may face increasingly personalized and socially engineered threats that blur the boundary between legitimate communication and malicious intent. As messaging applications continue to serve as primary channels for both professional and personal exchanges, adversaries are expected to exploit this inherent trust by distributing malware through compromised contacts and seemingly routine interactions. This shift elevates the likelihood of employees inadvertently contributing to the spread of infections, placing human behaviour at the forefront of organizational vulnerability. In this context, CYFIRMA anticipates that enterprises may become progressively more dependent on continuous Behavioral validation mechanisms not due to weaknesses in technical infrastructure, but because future attacks will be designed to mirror normal communication patterns. Over time, this trend may erode confidence in everyday digital engagement, compelling users to adopt greater caution even when interacting with familiar colleagues and trusted platforms.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rule
rule Eternidade_Stealer_IOCs
{
meta:
author = “CYFIRMA”
description = “Detects known IOCs associated with the Eternidade Stealer campaign”
strings:
/* ———- VBS Hashes */
$vbs_hash1 = “e1779d9810ad39a45759c856cc85f1148a8f6601”
$vbs_hash2 = “e3e24d57163e04ac16a93a698d4c8051473bccb4”
/* ———- WhatsApp Worm Hashes */
$wpy_hash1 = “8f3b5a0cecd4d50fc6eb52a627fe6a9179e71736”
$wpy_hash2 = “167cc2d716bfebc440f14ff1affe7f99b8556f2e”
/* ———- Payload Hashes */
$payload1 = “db5545b6136f1197fd5234695cdeff285a99208e”
$payload2 = “03944933d662f4e96d43750aa29bd287685c6007”
/* ———- Domains */
$d1 = “varegjopeaks.com/altor/teste_obscado.vbs” nocase
$d2 = “varegjopeaks.com/altor/whats.py” nocase
$d3 = “centrogauchodabahia123.com/altor/installer.msi” nocase
$d4 = “varegjopeaks.com/altor/installer.msi” nocase
$d5 = “itrexmssl.com/jasmin/altor/receptor.php” nocase
$d6 = “alentodolcevitad.com/admin.php” nocase
$d7 = “miportuarios.com” nocase
$d8 = “mazdafinancialsevrices.com” nocase
$d9 = “adilsonralfadvocaciad.com” nocase
$d10 = “domimoveis1.com.br” nocase
$d11 = “serverseistemasatu.com” nocase
/* ———- IP Addresses */
$ip1 = “103.84.176.107”
$ip2 = “104.21.48.41”
$ip3 = “162.120.71.56”
$ip4 = “185.169.234.139”
$ip5 = “83.229.17.71”
$ip6 = “140.99.164.172”
$ip7 = “174.138.187.2”
condition:
any of ($vbs_hash*) or any of ($wpy_hash*) or any of ($payload*) or any of ($d*) or
any of ($ip*)
}
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Behavior – Most of these malwares use phishing and social engineering techniques as their initial attack vectors. Apart from these techniques, exploitation of vulnerabilities, defense evasion, and persistence
tact
The Sandworm Playbook: APT44’s Persistent Cyber Campaigns
About the Threat Actor
The advanced persistent threat group APT44, also known as Sandworm, is believed to be behind the recent Petya ransomware attacks, an incident also referred to as ExPetr, PetrWrap, or NotPetya. The group’s activity was first noted in December 2016, when it targeted Ukrainian financial institutions and critical infrastructure. Dark-web sources suggest the group also operates under the names TeleBots, SandStorm, and Electrum, and is allegedly supported by the Russian government. APT44 maintains close associations with the BlackEnergy group, which was implicated in the 2015 power outages in Ukraine.
Details on Exploited Vulnerabilities
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2023-42793 | JetBrains TeamCity | 9.8 | Link |
| CVE-2020-1472 | Microsoft Windows domain controllers | 10.0 | Link1, link2 |
| CVE-2022-30190 | MSDT | 7.8 | link |
| CVE-2021-27065 | Microsoft Exchange Server | 7.8 | link1, link2 |
| CVE-2024-7344 | Howyar UEFI Application | 8.2 | – |
| CVE-2023-38831 | RARLAB WinRAR | 7.8 | link |
| CVE-2017-11882 | Microsoft Office | 7.8 | link |
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Reconnaissance | T1592.002 | Gather Victim Host Information: Software |
| Reconnaissance | T1595.002 | Active Scanning: Vulnerability Scanning |
| Reconnaissance | T1589.002 | Gather Victim Identity Information: Email Addresses |
| Reconnaissance | T1589.003 | Gather Victim Identity Information: Employee Names |
| Reconnaissance | T1590.001 | Gather Victim Network Information: Domain Properties |
| Reconnaissance | T1591.002 | Gather Victim Org Information: Business Relationships |
| Reconnaissance | T1598.003 | Phishing for Information: Spearphishing Link |
| Reconnaissance | T1593 | Search Open Websites/Domains |
| Reconnaissance | T1594 | Search Victim-Owned Websites |
| Resource Development | T1583 | Acquire Infrastructure |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains |
| Resource Development | T1583.004 | Acquire Infrastructure: Server |
| Resource Development | T1586.001 | Compromise Accounts: Social Media Accounts |
| Resource Development | T1584.004 | Compromise Infrastructure: Server |
| Resource Development | T1584.005 | Compromise Infrastructure: Botnet |
| Resource Development | T1587.001 | Develop Capabilities: Malware |
| Resource Development | T1585.001 | Establish Accounts: Social Media Accounts |
| Resource Development | T1585.002 | Establish Accounts: Email Accounts |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Resource Development | T1588.006 | Obtain Capabilities: Vulnerabilities |
| Resource Development | T1608.001 | Stage Capabilities: Upload Malware |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Initial Access | T1133 | External Remote Services |
| Initial Access | T1195 | Supply Chain Compromise |
| Initial Access | T1195.002 | Supply Chain Compromise: Compromise Software Supply Chain |
| Initial Access | T1199 | Trusted Relationship |
| Initial Access | T1078 | Valid Accounts |
| Initial Access | T1078.002 | Valid Accounts: Domain Accounts |
| Initial Access | T1566.001 | Phishing: Spearphishing Attachment |
| Initial Access | T1566.002 | Phishing: Spearphishing Link |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Execution | T1106 | Native API |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Execution | T1072 | Software Deployment Tools |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1204.001 | User Execution: Malicious Link |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1204.002 | User Execution: Malicious File |
| Persistence | T1098 | Account Manipulation |
| Persistence | T1554 | Compromise Host Software Binary |
| Persistence | T1136 | Create Account |
| Persistence | T1136.002 | Create Account: Domain Account |
| Persistence | T1543.002 | Create or Modify System Process: Systemd Service |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Persistence | T1133 | External Remote Services |
| Persistence | T1112 | Modify Registry |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Persistence | T1505.003 | Server Software Component: Web Shell |
| Persistence | T1505.001 | Server Software Component: SQL Stored Procedures |
| Persistence | T1078 | Valid Accounts |
| Persistence | T1078.002 | Valid Accounts: Domain Accounts |
| Privilege Escalation | T1098 | Account Manipulation |
| Privilege Escalation | T1543.002 | Create or Modify System Process: Systemd Service |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Privilege Escalation | T1078 | Valid Accounts |
| Privilege Escalation | T1078.002 | Valid Accounts: Domain Accounts |
| Defense Evasion | T1078 | Valid Accounts |
| Defense Evasion | T1078.002 | Valid Accounts: Domain Accounts |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1484.001 | Domain or Tenant Policy Modification: Group Policy Modification |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1562.002 | Impair Defenses: Disable Windows Event Logging |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1036.004 | Masquerading: Masquerade Task or Service |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location |
| Defense Evasion | T1036.008 | Masquerading: Masquerade File Type |
| Defense Evasion | T1036.010 | Masquerading: Masquerade Account Name |
| Defense Evasion | T1027.010 | Obfuscated Files or Information: Command Obfuscation |
| Defense Evasion | T1218.011 | System Binary Proxy Execution: Rundll32 |
| Defense Evasion | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Defense Evasion | T1055 | Process Injection |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers |
| Credential Access | T1539 | Steal Web Session Cookie |
| Credential Access | T1110 | Brute Force |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Credential Access | T1040 | Network Sniffing |
| Credential Access | T1003.003 | OS Credential Dumping: NTDS |
| Credential Access | T1003.001 | OS Credential Dumping: LSASS Memory |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1087.002 | Account Discovery: Domain Account |
| Discovery | T1087.003 | Account Discovery: Email Account |
| Discovery | T1040 | Network Sniffing |
| Discovery | T1018 | Remote System Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1049 | System Network Connections Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Lateral Movement | T1072 | Software Deployment Tools |
| Lateral Movement | T1570 | Lateral Tool Transfer |
| Lateral Movement | T1021.002 | Remote Services: SMB/Windows Admin Shares |
| Collection | T1213 | Data from Information Repositories |
| Collection | T1005 | Data from Local System |
| Collection | T1056.001 | Input Capture: Keylogging |
| Command and Control | T1132.001 | Data Encoding: Standard Encoding |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1571 | Non-Standard Port |
| Command and Control | T1572 | Protocol Tunneling |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1090 | Proxy |
| Command and Control | T1219 | Remote Access Tools |
| Command and Control | T1102.002 | Web Service: Bidirectional Communication |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1491.002 | Defacement: External Defacement |
| Impact | T1561.002 | Disk Wipe: Disk Structure Wipe |
| Impact | T1499 | Endpoint Denial of Service |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1489 | Service Stop |
Latest Developments Observed
The threat actor is conducting the BadPilot campaign on a global scale, targeting sectors such as energy, oil and gas, telecommunications, shipping, arms manufacturing, and various government organizations. They appear to be identifying and compromising numerous Internet-facing systems by exploiting vulnerabilities in ConnectWise ScreenConnect (CVE-2024-1709) and Fortinet FortiClient EMS (CVE-2023-48788). These attacks have primarily impacted Ukraine, Europe, and specific industries across Central and South Asia, as well as the Middle East.
ETLM Insights
The threat actor is believed to conduct high-impact cyber operations where destructive effects, intelligence collection, and strategic signalling outweigh any financial motivation. Their campaigns demonstrate a consistent focus on undermining national resilience, disrupting critical functions, and shaping geopolitical outcomes through cyber-enabled coercion.
Operationally, the actor is known to:
The actor’s behaviour reflects three core strategic drivers:
YARA Rules
rule APT_IOC_Detection
{
meta:
description = “Detects files or content referencing known malicious domains, IPs, and filenames”
author = “CYFIRMA” date = “2025-11-25”
strings:
// — Domains —
$d1 = “cache-pdf.com”
$d2 = “lollitop.cc”
$d3 = “aoldaily.com”
$d4 = “cyberazov.com”
// — Filenames & paths —
$f1 = “abuse-ransomware.csv”
$f2 = “index.php”
$f3 = “win32 exe” nocase
$f4 = “hrm3jvh9v.dll”
// — CVEs (sometimes embedded in exploit kits) —
$c1 = “CVE-2023-34362”
$c2 = “CVE-2024-38213”
$c3 = “CVE-2014-4114”
$c4 = “CVE-2019-19781”
$c5 = “CVE-2021-26858”
$c6 = “CVE-2021-26857”
$c7 = “CVE-2024-3094”
// — IP addresses —
$ip1 = “172.67.178.121”
$ip2 = “216.239.38.21”
$ip3 = “213.186.33.40”
$ip4 = “184.168.221.32”
$ip5 = “172.67.179.217”
$ip6 = “23.236.62.147”
$ip7 = “69.172.201.208”
condition:
any of ($d*) or any of ($f*) or any of ($c*) or any of ($ip*)
}
Strategic
Management
Tactical
US DOD heavy investment in AI-assisted hacking
According to media reports, the US Department of Defense is currently investing in AI- assisted hacking capabilities, spending more than 12 million dollars on a contract with Arlington-based offensive security startup. The company has also landed a $240,000 research contract with the US Navy. The contractor has reportedly received funding from the US intelligence community’s venture capital fund In-Q-Tel, as well as private venture capital. Twenty’s contracts awarded to a single offensive capability provider represent an unusual story in securing work for the U.S. Cyber Command. At the same time, U.S. Cyber Command has appointed Brig. Gen. Reid Novotny as its new Chief AI Officer. Novotny previously led intelligence and cyber operations for the National Guard Bureau. In an official statement, the command emphasized that it will use AI to bolster U.S. cyber capabilities by improving offensive AI-assisted capabilities and decision-making edges, while safeguarding national security and freedoms. This involves promoting “ethical AI development, rapidly deploying cutting-edge tools on a large scale, and building collaborations across the Department of Defense, private industry, and academic institutions.”
ETLM Assessment:
These recent developments formalize AI as a core pillar of U.S. cyber strategy amid rising global threats (e.g., from China or Russia). It reflects a proactive push to counter AI-enabled adversaries, but also underscores challenges like ethical dilemmas, talent shortages, and the need for cross-sector trust. The “Department of War” phrasing is a tongue-in-cheek nod to the DoD’s pre-1949 name, highlighting its warfighting roots in a modern context.
China’s APT24 deploys new stealthy downloader
Researchers have recently released a detailed report exposing an ongoing, multi-year cyber espionage campaign conducted by the Chinese state-sponsored advanced persistent threat actor known as APT24 (aka Bronze Atlas). Central to the group’s recent operations is a highly obfuscated first-stage downloader nicknamed “BADAUDIO,” which APT24 has actively employed and iteratively refined over the past three years. The malware is designed to evade detection by blending into normal audio-related network traffic and leveraging heavy code obfuscation, polymorphic behaviors, and anti-analysis techniques. According to the analysis, APT24’s tactics have noticeably evolved. Whereas earlier campaigns leaned heavily on so-called “strategic web compromises” (SWC) — the mass defacement or backdooring of legitimate but poorly secured websites to serve malware to broad visitor populations — the group has shifted toward far more precise and sophisticated infection vectors, with a clear geographic focus on Taiwan. Notable recent methods include repeated compromise of a prominent regional digital-marketing and advertising technology firm based in Taiwan, turning the company into an unwitting vector for supply-chain attacks against its downstream customers. There also were highly targeted spear- phishing campaigns that incorporate multi-layered social engineering, often combining personalized lures with forged identities and lookalike domains.
ETLM Assessment:
This pivot in this APT’s targeting reflects a broader trend among top-tier Chinese espionage actors: moving away from noisy, high-volume operations toward lower- signature, higher-precision intrusions that maximize intelligence value while minimizing the risk of detection and attribution.
Cl0p Ransomware Impacts Sumitomo Chemical Co., Ltd
Summary:
CYFIRMA observed in an underground forum that a company from Japan, Sumitomo Chemical Co., Ltd (https[:]//www[.]sumitomo-chem[.]co[.]jp/), was compromised by Cl0p Ransomware. Sumitomo Chemical Co., Ltd is a major Japanese chemical company and a global “innovative solution provider” that develops and supplies a wide range of chemical-based products supporting many industries and everyday life. It operates worldwide in sectors such as agrochemicals, electronics/IT materials, pharmaceuticals, and essential & green materials, under the corporate slogan “Creating What the Earth Needs Next.” The compromised data contains confidential and sensitive information belonging to the organization.
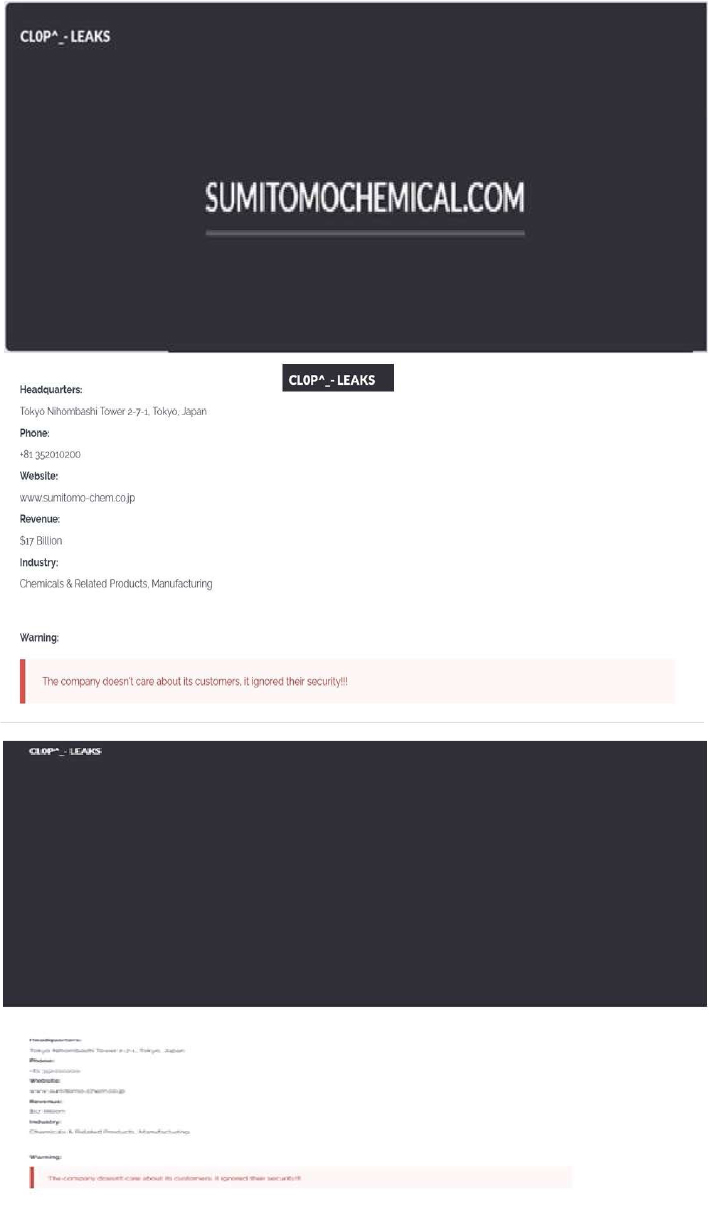
Relevancy & Insights:


ETLM Assessment:
According to CYFIRMA’s assessment, Cl0p ransomware remains one of the most significant and disruptive threats in the current cybercrime landscape, particularly evident through its unprecedented volume of attacks and innovative extortion tactics witnessed in 2025. The Cl0p campaign reinforces the urgent need for holistic security strategies: rapid vulnerability management, robust incident detection, thorough supply chain risk assessments, and strong contingency plans for data exfiltration scenarios.
Qilin Ransomware Impacts Cal-Comp Electronics Public
Summary:
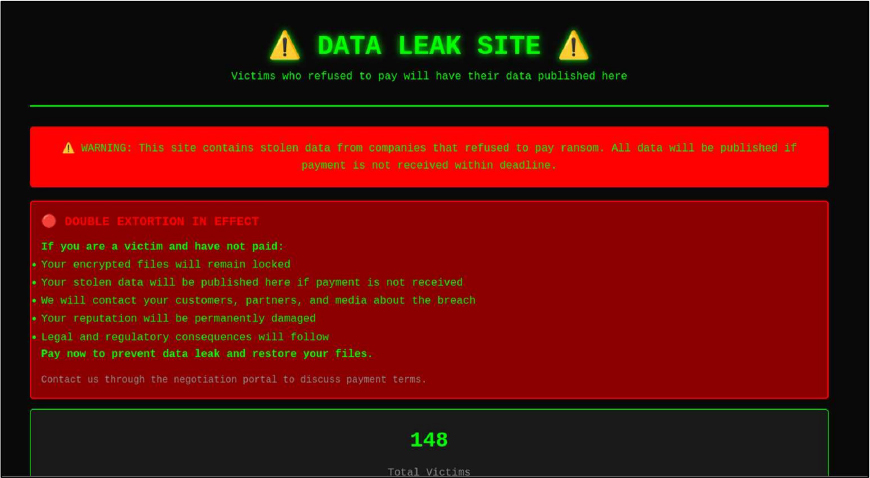
CYFIRMA observed in an underground forum that a company from Thailand, Cal- Comp Electronics Public (https[:]//www[.]calcomp[.]co[.]th/), was compromised by Qilin Ransomware. Cal-Comp Electronics (Thailand) Public Company Limited (CCET) is a leading electronics manufacturing services (EMS) company headquartered in Bangkok, Thailand. Cal-Comp Electronics Public specializes in OEM (Original Equipment Manufacturing) and ODM (Original Design Manufacturing) for a broad range of electronic products, including computer peripherals, telecommunications equipment, consumer electronics, and automation products. The compromised data contains confidential and sensitive information belonging to the organization.

Relevancy & Insights:

ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and a focus on speed and evasion, make it a particularly dangerous actor.
Vulnerability in SAP NetWeaver Enterprise Portal
Relevancy & Insights:
The vulnerability exists due to improper input validation.
Impact:
A remote non-authenticated attacker can send a specially crafted request and execute arbitrary JNDI commands on the target system.
Affected Products:
https[:]//support[.]sap[.]com/en/my-support/knowledge- base/security-notes-news/november-2025.html
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
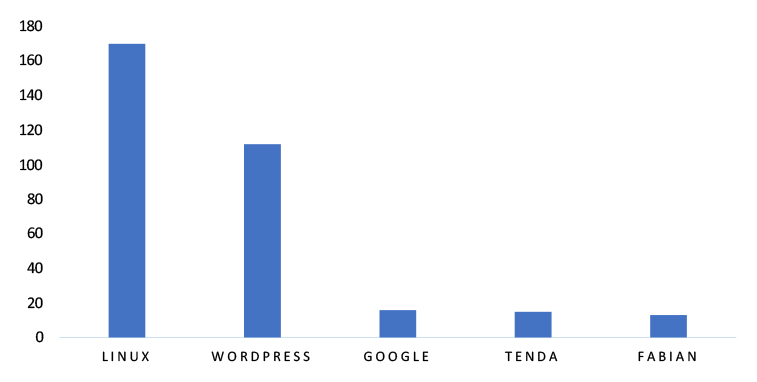
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerabilities in SAP NetWeaver Enterprise Portal can pose significant threats to user privacy and network security. This can impact various industries globally, including financial services, manufacturing, healthcare, and public sector organizations. Ensuring the security of SAP NetWeaver Enterprise Portal is crucial for maintaining the integrity and protection of critical business data, enterprise applications, and interconnected systems worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding business operations, remote system management, and real-time information distribution across different geographic regions and sectors.
Crypto24 Ransomware attacked and published the data of Bayu Buana Travel Service
Summary:
Recently, we observed that Crypto24 Ransomware attacked and published the data of the Bayu Buana Travel Service (www[.]bayubuanatravel[.]com) on its dark web website. Bayu Buana Travel Services is one of Indonesia’s leading travel agencies, offering complete travel solutions for both leisure and corporate customers. The company provides tour packages, ticketing, hotel booking, MICE services, and travel documentation assistance, and operates both as a travel agent and a publicly listed company. The Crypto24 ransomware group exfiltrated over 500 GB of data from Bayu Buana Travel Service’s internal network, comprising company documents, customer and project information, and other data from internal systems.

Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Crypto24 is a high-profile ransomware group known for rapid, high-volume data theft, fast encryption, and aggressive pressure tactics that combine classic ransom demands with sensitive data leaks.
Organizations in Asia have been primary targets, with attacks resulting in the exfiltration and exposure of terabytes of sensitive information. Recovery without payment is rarely feasible, underscoring the need for robust defense and backup strategies.
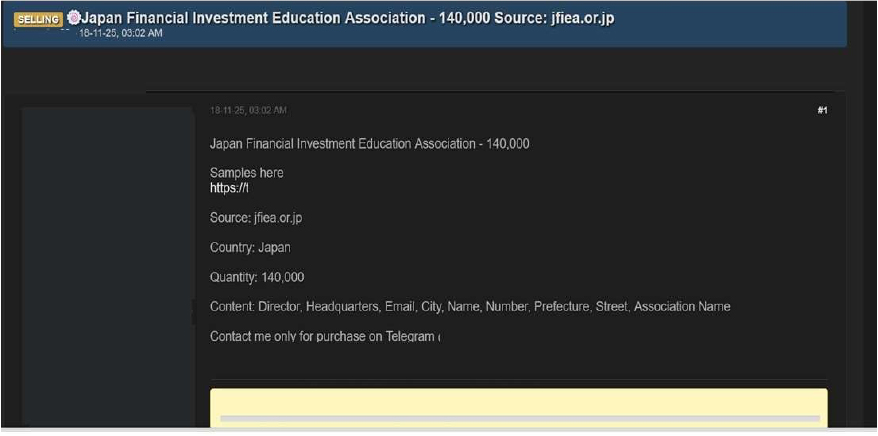
Japan Financial Investment Association (JFIEA) Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that a threat actor “Yeestge33” is claiming to be selling data allegedly stolen from the Japan Financial Investment Education Association (JFIEA), an organization dedicated to promoting financial literacy and investment education in Japan.
The actor posted the database for sale on a cybercrime forum, claiming it contains 140,000 records. The alleged source of the data is listed as the association’s official website, jfiea.or.jp.
According to the actor, the compromised data includes a wide range of personally identifiable information (PII) and organizational details.
The allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
Haravan Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that a threat actor “Spirigatito” has allegedly compromised and is selling the database of Haravan, a prominent Vietnamese omnichannel commerce platform. Haravan provides a software-as-a-service (SaaS) solution to manage sales for businesses across online and offline channels in Vietnam. The actor claims the breach includes 5,383,349 customer records and totals over 10 GB of data.
According to the actor, the allegedly compromised data includes:
The data samples provided indicate that these records contain personally identifiable information (PII) for Vietnamese customers using the Haravan platform.
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.

Relevancy & Insights:
Financially motivated cybercriminals are continuously looking for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to gain access and steal valuable data. Subsequently, the stolen data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor “Spirigatito” has recently emerged as a highly active group involved in data-leak operations. Multiple credible sources attribute a series of security breaches to this actor, including unauthorized system intrusions and efforts to sell stolen information on dark web marketplaces. The group’s continued activity underscores the persistent and evolving nature of cyber threats originating from underground communities. These incidents highlight the urgent need for organizations to strengthen their cybersecurity posture through continuous monitoring, robust threat-intelligence capabilities, and proactive defensive measures to safeguard sensitive data and critical infrastructure.
Recommendations: Enhance the cybersecurity posture by:
The CYFIRMA Research team observed that a threat actor “Sorb” claims to have compromised the systems of National Telecom Public Company Limited (NT), Thailand’s state-owned telecommunications enterprise. established in 2021 through the merger of CAT Telecom and TOT Public Company Limited, NT provides fixed-line telephony, mobile services, and international telecommunications infrastructure.
The actor is currently offering the alleged dataset for sale on a dark web forum for a price of $300.
According to the actor, the breach encompasses approximately 1,197,636 lines of data. A sample provided by the seller suggests the stolen database contains highly detailed customer and technical service logs.
The allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.

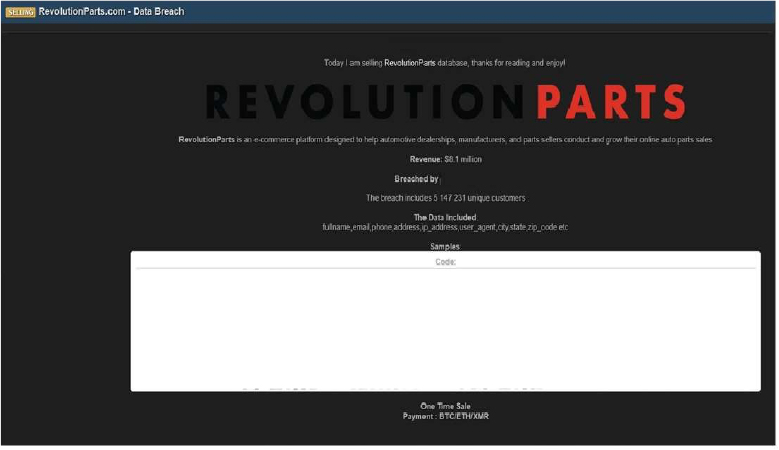
The CYFIRMA Research team observed that a threat actor “Spirigatito” claims to have breached RevolutionParts, an e-commerce platform designed to assist automotive dealerships, manufacturers, and parts sellers in growing their online sales. The actor has listed a database allegedly belonging to the company for sale on a cybercrime forum.
According to the post, the breach impacts a significant number of individuals. The actor asserts that the compromised database contains the personal information of 5,147,231 unique customers. The data is being offered for a “One Time Sale” payable in cryptocurrency (BTC, ETH, or XMR), suggesting the actor intends to sell the exclusive rights to the data to a single buyer.
The Data: According to the actor, the compromised database contains extensive Personally Identifiable Information (PII). The allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
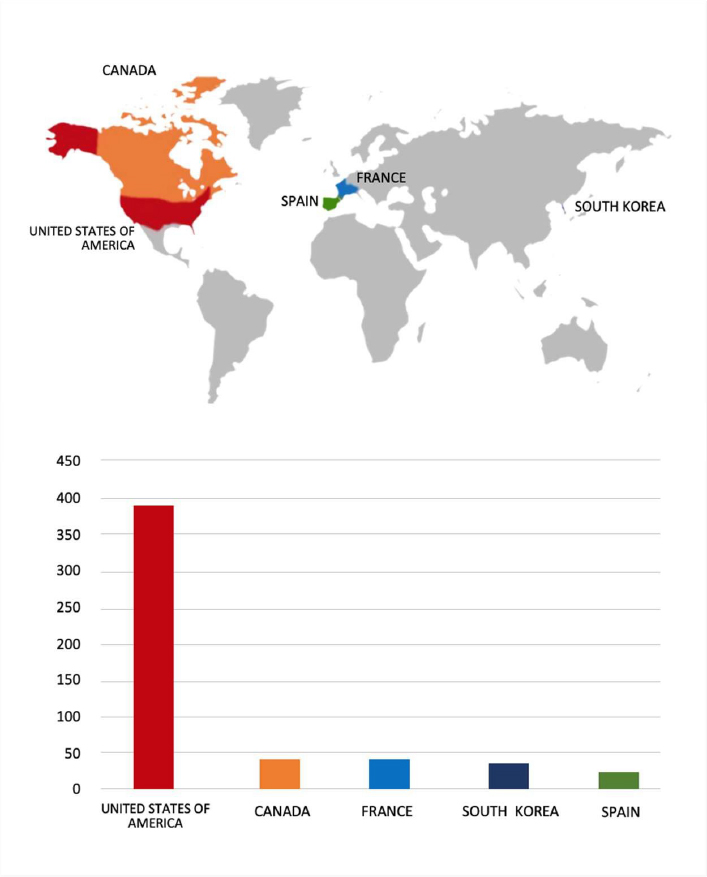
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.