



Ransomware of the Week
CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware,
Target Technologies: MS Windows.
Introduction
CYFIRMA Research and Advisory Team has found a new SophosEncrypt ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Relevancy:
The Ransomware primarily focuses on the widely used Windows Operating System, which is extensively utilized across various industries and organizations.
SophosEncrypt:
SophosEncrypt is a recent entrant in the ransomware arena, available through the ransomware-as-a-service (RaaS) business model. It has already been employed in malicious attacks by threat actors.
The ransomware encryptor is written in Rust and uses the ‘C:\Users\Dubinin\’ path for its crates.
Its capabilities and design seem to harken back to older, more traditional ransomware variants.
Researchers analyzed various samples of this ransomware and discovered that one of the samples displayed extraordinary capabilities beyond its primary function of file encryption, which is quite uncommon for ransomware.
The sample exhibits functionalities more akin to a general-purpose remote access trojan (RAT) rather than a typical contemporary ransomware executable. Alongside file encryption and ransom note generation, it demonstrates capabilities such as keyboard driver hooking for keystroke logging and system profiling through WMI commands.
Additionally, it checks the system’s language settings and declines to run if the language is set to Russian.
The other known sample exhibits fewer non-ransomware functionalities.
Both samples also contain a hardcoded IP address, associated with Cobalt Strike and crypto mining attacks on internet-facing computers for over a year.
Upon analyzing the most recent version of the malware (version 0.0.9), researchers discovered that it incorporates a Rust AES encryption library and employs AES-256 encryption in cipher-block-chaining (CBC) mode.
Upon execution, the encryptor prompts the affiliate to input a token linked to the victim, typically obtained from the ransomware management panel.
When a token is entered, the encryptor will verify if the token is valid. Once a valid token is provided, the encryptor will request further details from the ransomware affiliate, which will be used during the device encryption process.
The requested information includes a contact email, jabber address, and a 32-character password, which researchers believe is utilized as part of the encryption algorithm.
Before the encryption process, the program presents the attacker with various options to choose from.
After generating the encryption key but before attempting to encrypt files, the malware:
Once the encryption process is completed, each encrypted file adopts a new format, containing the original filename along with the entered token, provided email, and the ‘Sophos’ extension. Additionally, the ransomware generates a ransom note named information.hta for each folder after encrypting files. This note is automatically launched and contains information about the victim’s files, an explanation of the situation, and the contact details entered by the affiliate before initiating the encryption process.
The Ransomware includes a list of folders and file extensions that avoid encrypting, as well as a list of processes it terminates.
Folders to skip: ‘Boot’ ‘FRST’, ‘KVRT_Data’, ‘KVRT2020_Data’, ‘PerfLogs’, ‘AdwCleaner’, ‘ProgramData’, ‘$Recycle.Bin’, ‘$RECYCLE.BIN’, ‘MSOCache’, ‘Documents and Settings’, ‘Recovery’, ‘System Volume Information’, ‘SYSTEM.SAV’, ‘$Windows.~WS’, ‘$WINDOWS.~WS’, ‘Thumbs’, ‘Pagefile’, ‘Hyberfil’, ‘$WinREAgent’, ‘Program Files’, ‘Program Files (x86)’, ‘$WINDOWS.~BT’, ‘Thumbs.db’, ‘Windows.old’, ‘windows.old’, ‘Windows.old.000’, ‘windows.old.000’, ‘AppData’, ‘dev’.
File extensions to skip: ‘regtrans-ms’, ‘tmp’, ‘ps1’, ‘joker’, ‘ini’, ‘dll’, ‘inf’, ‘ico’, ‘bat’, ‘lnk’,
‘com’, ‘ani’ ‘adv’, ‘cpl’, ‘cur’, ‘rom’, ‘deskthemepack’, ‘diagcab’, ‘diagcfg’, ‘diagpkg’, ‘drv’,
‘log’, ‘hlp’, ‘icl’, ‘icns’, ‘ics’, ‘idx’, ‘ldf’, ‘mod’, ‘mpa’, ‘msc’, ‘msp’, ‘theme’, ‘wpx’, ‘lock’, ‘mkp’,
‘ocx’, ‘msu’, ‘nls’, ‘msstyles’, ‘nomedia’, ‘prf’, ‘rtp’, ‘scr’, ‘shs’, ‘spl’, ‘themepack’, ‘key’, ‘hta’, ‘faust’, ‘Devos’, ‘sophos’, ‘sys’.
Processes to kill: ‘Oracle.exe’, ‘Ocssd.exe’, ‘Dbsnmp.exe’, ‘Synctime.exe’, ‘Agntsvc.exe’, ‘Isqlplussvc.exe’, ‘Xfssvccon.exe’, ‘Mydesktopservice.exe’, ‘Ocautoupds.exe’, ‘Encsvc.exe’, ‘Firefox.exe’, ‘Tbirdconfig.exe’, ‘Mydesktopqos.exe’, ‘Ocomm.exe’, ‘Dbeng50.exe’, ‘Sqbcoreservice.exe’, ‘Excel.exe’, ‘Infopath.exe’, ‘Msaccess.exe’, ‘Mspub.exe’, ‘Onenote.exe’, ‘Outlook.exe’, ‘Powerpnt.exe’, ‘Steam.exe’, ‘Thebat.exe’, ‘Thunderbird.exe’, ‘Visio.exe’, ‘Winword.exe’, ‘Wordpad.exe’, ‘Notepad.exe’, ‘Utweb.exe’, ‘Ut.exe’, ‘Sql.exe’.
The encryption method used by the malware varies based on the file size. For files smaller than 6.4 megabytes, it creates a new file, encrypts the data in chunks using AES-256 in CBC mode, and appends the result to the new file while deleting the original. For larger files, it modifies the original file by replacing its content with encrypted data in chunks and appends the SHA256 of the key at the end.
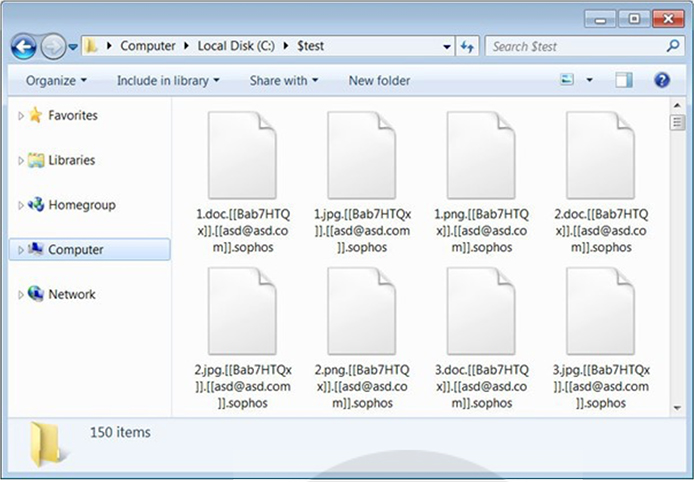
Screenshot of files encrypted by SophosEncrypt Ransomware. (Source: Surface Web)
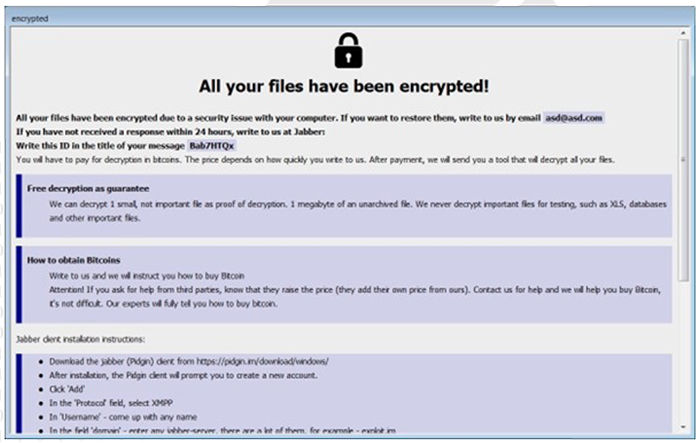
Screenshot of Ransomnote by SophosEncrypt Ransomware. (Source: Surface Web)
The ransomware possesses the ability to alter the Windows desktop wallpaper, prominently featuring the ‘Sophos’ brand that it is impersonating. It’s important to note that this wallpaper is entirely created by the threat actors and has no affiliation with the legitimate Sophos cybersecurity company. Ransomware uses this customized wallpaper as part of its strategy to further intimidate and deceive victims during the attack.
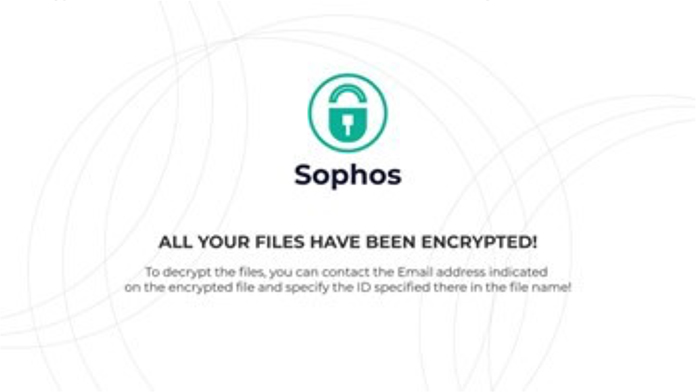
SophosEncrypt wallpaper (Source: Surface Web)
Insights:
Following are the TTPs based on MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1047: Windows Management Instrumentation |
| T1129: Shared Modules | ||
| 2 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1027.005: Obfuscated Files or Information: Indicator Removal from Tools | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1497.001: Virtualization/Sandbox Evasion: System Checks | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| 3 | TA0006: Credential Access | T1056: Input Capture |
| 4 | TA0007: Discovery | T1012: Query Registry |
| T1016: System Network Configuration Discovery | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1087: Account Discovery | ||
| T1497.001: Virtualization/Sandbox Evasion: System Checks | ||
| T1518: Software Discovery | ||
| 5 | TA0009: Collection | T1056: Input Capture |
| T1213: Data from Information Repositories | ||
| 6 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1071.001: Application Layer Protocol: Web Protocols | ||
| 7 | TA0040: Impact | T1486: Data Encrypted for Impact |
| T1490: Inhibit System Recovery |
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Spyware
Objective: Espionage, Data Exfiltration Target Technology: Android
Threat Actor: APT41 (aka Winnti, BARIUM, or Double Dragon)
Active Malware of the Week
This week “WyrmSpy and DragonEgg” is trending.
WyrmSpy and DragonEgg
Researchers have identified two sophisticated Android spyware, WyrmSpy, and DragonEgg, which are associated with the prominent Chinese threat group APT41, also known as Winnti, BARIUM, or Double Dragon, which has been predominantly associated with exploiting web-facing applications and traditional endpoint devices. Both WyrmSpy and DragonEgg appear to have sophisticated data collection and exfiltration capabilities, concealing these functions within additional modules that are downloaded after installation. WyrmSpy disguises itself as a default operating system app, while DragonEgg pretends to be a third-party keyboard or messaging application.
APT41’s connection with WyrmSpy and DragonEgg
DragonEgg and WyrmSpy are linked to each other through the use of overlapping Android signing certificates. Some versions of WyrmSpy introduced unique signing certificates that were later observed in use by DragonEgg developers. WyrmSpy played a crucial role in attributing both malware to APT41 by revealing a connection between their command-and- control (C2) infrastructure and Chengdu 404 (a Chinese company). A subdomain, “vpn2.umisen[.]com,” was used by APT41 from 2014 to 2020, and its resolving IP address matches with 14 samples analyzed by researchers, indicating their association.
Additionally, a WHOIS record for “umisen[.]com” from 2015 and 2016 lists one of the individuals mentioned in the indictment as the domain registrant, providing further evidence of APT41’s involvement.
Attack Strategy
The targeting strategy of WyrmSpy and DragonEgg differs significantly. WyrmSpy disguises itself mainly as a default Android system app, initially used for displaying notifications. Later variations of the malware are found in apps pretending to be adult video content, the “Baidu Waimai” food delivery platform, and Adobe Flash. On the other hand, DragonEgg has been detected in apps claiming to be third-party Android keyboards and messaging applications like Telegram.
Researchers have not yet come across any samples of these malware in the wild, and they believe they are distributed to victims through social engineering campaigns with moderate confidence. Google has confirmed that, as of the current detection measures, no apps containing this malware are available on Google Play.
Technical analysis of WyrmSpy and DragonEgg WyrmSpy
Once installed and launched, Wyrmspy utilizes known rooting tools to gain elevated privileges on the device and carry out surveillance tasks as instructed by its command-and- control (C2) servers. These tasks involve uploading log files, photos, and obtaining the device’s location using the Baidu Location library.
While additional modules from the C2 infrastructure were not accessible during the discovery, it is highly likely that a secondary payload is employed by the malware to execute further surveillance functions. This is supported by the permissions acquired by WyrmSpy, which are not utilized in the app’s code, indicating capabilities to exfiltrate additional data like SMS and audio recordings.
Furthermore, configuration files used by the malware also reinforce this assumption, with references to “AudioRecord” and “Files” being set to true or false based on the received commands.
Data Collection by WyrmSpy
Communications with C2 and configuration files
WyrmSpy operates based on commands received from its C2 and configuration files, determining its actions on the compromised device and the data it gathers. It remains uncertain whether these commands are automated or require direct human interaction, as the server-side code is inaccessible from the C2. The configuration files are created and populated by WyrmSpy on startup and form the basis of the behavior on an infected device. As the malware interacts with the device and receives instructions from its C2, it modifies the configuration files accordingly.Other configuration files contain details about the C2, metadata, and identifiers initially collected about the infected device. A file named “ManifestFile.json” is obtained from the C2, specifying C2 beaconing intervals, lists of files for upload and download, as well as a list of shell commands to execute on the device.
Rooting the device
WyrmSpy utilizes popular rooting tools like KingRoot11 and IovyRoot/IvyRoot12. It can also disable SELinux on compatible Android versions to access data that might otherwise be inaccessible. In cases where the included rooting tools fail to work or are not present, and if the device is not already rooted, the malware communicates with the C2 infrastructure, providing the model and kernel version of the infected device.
The C2 responds with a filename, which the malware uses to download additional rooting binaries from the C2 infrastructure if they exist for the specified device.
DragonEgg
DragonEgg, similar to WyrmSpy, relies on additional payloads to fully implement its surveillance capabilities. It acquires a payload named “smallmload.jar” from the C2 infrastructure or bundled within the APK to execute additional functionalities. Like WyrmSpy, DragonEgg requests extensive permissions for services not directly related to its core app.
To avoid detection and access valuable device data, APT41 disguises its surveillance activities by trojanizing legitimate chat apps like Telegram. By concealing surveillance functionality within fully-functional apps, the threat actor can maintain a low profile while the app is running on the device or being analyzed by researchers. Messaging apps typically request access to sensitive device data, making it easier for the malware to remain unnoticed during its operations.
DragonEgg uses “smallmload.jar” as a secondary payload to load a “forensics program (T1 version)” tertiary module, a term commonly used by Chinese-speaking defense or software development firms for surveillance tools. Unfortunately, at the time of analysis, DragonEgg’s command-and-control (C2) infrastructure was offline, preventing researchers from obtaining the “T1” forensics tool loaded by the core application.
Data Collection by DragonEgg
INSIGHTS
Indicators of Compromise
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Weekly Attack Type and Trends Key Intelligence Signals:
Threat Actor in Focus
Cryptocurrency-Focused North Korean Cyber Group UNC4899 Targets Supply Chain in Recent Attack
Summary:
Recently researchers discovered a compromised supply chain affecting a US-based software solutions entity. It was found the threat actor behind the attack has connections with North Korea and has a history of attacking cryptocurrency firms. They are known by the name UNC4899. The attack began with a sophisticated spear- phishing campaign aimed at JumpCloud; a zero-trust directory platform, used for identity and access management. The compromise impacted fewer than five customers and less than ten devices. UNC4899 is believed to be a part of the Reconnaissance General Bureau (RGB); a cryptocurrency-focused element within the Democratic People’s Republic of Korea (DPRK). The attackers gained initial access by inserting malicious code into JumpCloud’s commands framework, deploying a lightweight Ruby script that downloaded and executed a second-stage payload. The attackers used various backdoors, including FULLHOUSE.DOORED and STRATOFEAR, to establish persistence and communicate with command and control (C2) servers. TIEDYE, a related backdoor, was also identified. Researchers observed UNC4899 using VPN providers, such as ExpressVPN and NordVPN, to obscure their source addresses. However, due to operational security mistakes, they occasionally exposed their true IP addresses, revealing connections to North Korea. UNC4899’s targeting shows a strong interest in the cryptocurrency field, with overlaps in tactics and infrastructure observed among multiple North Korean groups, under the RGB umbrella.
Insights:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Government of Norway was targeted by a zero-day attack.
Norway continues its investigation of the zero-day attack, which was suffered by twelve of its ministries, all of whom share a common ICT platform. Governmental bodies using a different platform, namely The Prime Minister’s Office, the Ministry of Defense, the Ministry of Justice, and the Ministry of Foreign Affairs, were not affected in the attack. The attack has as of writing not yet been attributed to a specific threat actor, however, analysts are pointing out Russia, which has a recent track record of cyberattacks against neighbors of Norway, which is at odds with NATO’s expansion in the region (Norway is a founding member of the treaty). Norway is also Europe’s largest oil producer, effectively displacing Russian hydrocarbons in EU imports, after the start of the Russian attack on Ukraine, of which Norway is a strong supporter. The zero-day itself is tracked as CVE-2023-35078, an authentication bypass vulnerability afflicting all supported versions of Ivanti’s EPMM mobile device management software (formerly known as MobileIron Core)..
Russian breaches defense industry in Ukraine and Eastern EU
Rise in Malware/Ransomware and Phishing
Centennial Management is Impacted by Play Ransomware
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in the dark forum that a company from the United States of America, (www[.]centennialinvestments[.]com), was compromised by Play Ransomware. Centennial Management Corp is a full-service real estate management company with vast experience in all aspects of property management, particularly affordable housing. The data that has been compromised includes confidential and personal information, such as client and employee documents, IDs, contracts, financial records, tax information, and more.
The following screenshot was observed published on the dark web:

Source: Dark Web
Insights:
Vulnerabilities and Exploits
Vulnerability in AXIS A1001
Summary:
The vulnerability allows a remote attacker to execute arbitrary code on the target system.
Insights:
The vulnerability exists due to a boundary error within the Open Supervised Device Protocol (OSDP). A remote attacker on the local network can pass specially crafted data to the application, trigger a heap-based buffer overflow and execute arbitrary code on the target system.
Impact :
Successful exploitation of this vulnerability may result in the complete compromise of vulnerable systems.
Affected Products:
https[:]//www[.]axis[.]com/dam/public/1b/21/5f/cve-2023-21406-en-US- 407245[.]pdf
Latest Cyber-Attacks, Incidents, and Breaches
SiegedSec Hacktivist Asserts Responsibility for Targeting NATO and Exposing Confidential Documents.
Summary:
The cyber-activist collective known as “SiegedSec” initiated a cyber offensive against NATO, asserting that they successfully infiltrated its COI portal. As a result of the breach, they have exposed a substantial cache of sensitive documents intended for NATO nations and partners. The leaked data includes comprehensive details, such as full names, email addresses, phone numbers, office addresses, and ranks of at least 70 NATO officials. SiegedSec has risen as a substantial cyber menace, motivated by a combination of hacktivism and personal interests. As per SiegedSec’s claim, the motive behind the NATO hack is the alleged violation of human rights by NATO.
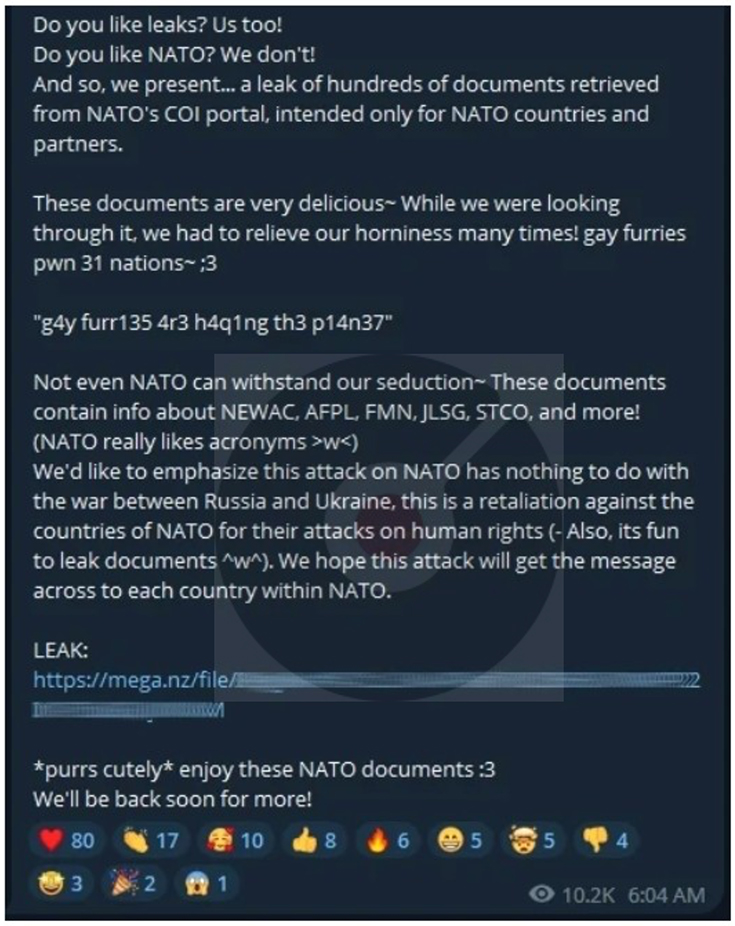
Source: Telegram Channel
Insights:
The purported assault on NATO’s COI portal represents a concerning escalation in SiegedSec’s methods. Their modus operandi frequently involves pilfering and disclosing confidential data from reputable and widely recognized companies or organizations to attract attention and obtain free publicity.
Data Leaks
DBA Tecnologia Data Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to DBA Tecnologia,
{www[.]dbatecnologia [.]com.[br]}. DBA Tecnologia is a company that operates in the Machinery industry. The company is headquartered in Brazil. The data that was exposed consists of sensitive information in SQL format, totalling 6GB in size.

Source: Underground forums
Insights:
There are constantly vigilant cybercriminals driven by financial motives, who actively seek out exposed and vulnerable systems and applications. Most of these attackers operate in clandestine online communities, engaging in discussions and trading stolen digital assets. Unlike ransomware or extortion groups that often publicize their attacks, these attackers prefer to work discreetly. They exploit unpatched systems or vulnerabilities in applications to gain unauthorized access and pilfer valuable data. The stolen information is subsequently advertised, sold, and repurposed by other attackers for their own malicious purposes.
CYFIRMA Research team observed a potential data leak related to RRG Group, {www[.]rrg-group[.]com}. RRG Group is a company that operates in the Automotive industry. The company is headquartered in England. The data released to the public comprises a customer database, containing customers’ IDs, first names, last names, gender, date of birth (DOB), nationality, marital status, number of dependents, occupations, employment status, and various other sensitive details.
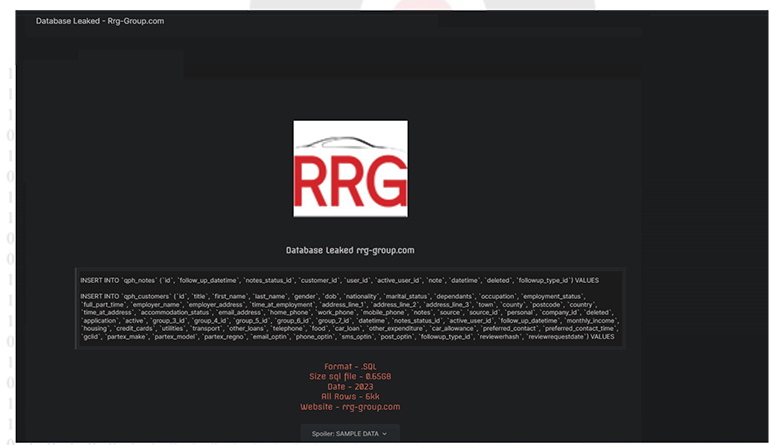
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS