Published On : 2023-04-28
Weekly Attack Type and Trends Key Intelligence Signals:
- Attack Type: Malware Implants, Ransomware Attacks, Vulnerabilities & Exploits, DDoS, and Data Leak
- Objective: Unauthorized Access, Data Theft, Data Encryption, Financial Gains, Payload Delivery, Cyber Espionage, and Data Destruction.
- Business Impact: Data Loss, Financial Loss, Reputational Damage, Loss of Intellectual Property, Operational Disruption
- Ransomware – BlackCat Ransomware | Malware – EvilExtractor
- BlackCat Ransomware – One of the ransomware groups.
- Please refer to the trending malware advisory for details on the following:
- Malware – EvilExtractor
- Behavior –Most of these malwares use phishing and social engineering techniques as their initial attack vector. Apart from these techniques, exploitation of vulnerabilities, defence evasion, and persistence tactics are being observed.
Threat Actor in Focus Chinese APT Daggerfly Targets Telecom Company in Africa
- Suspected Threat Actors: Daggerfly
- Attack Type: Unknown
- Target Geography: Africa
- Target Industry: Telecom
- Objective: Data Theft
- Target Technology: Windows Server
- Business Impact: Data loss, Reputational Damage, and Operational Disruption
Summary:
In a recent observation, it was found that a Chinese APT known as Daggerfly had targeted a telecom company based in Africa. The APT is also known by the names Evasive Panda and Bronze Highland and has been operating since 2014. The footprints of the campaign were first seen in November 2022, but it is reported that the attack is still active. Attribution to Daggerfly was made based on the technical revelations of an attack that happened in 2020 against the Indian government. The threat actor is seen employing the same loader and malware that was used against the Indian government. In this recent attack, the first sign of suspicious activity was the connection of AnyDesk to the Microsoft Exchange mail server, which was first seen in November 2020. The actor was also seen using the PlugX loader, MgBot modular malware framework, and exploiting the legitimate AnyDesk software. AnyDesk is a legitimate remote connection application, but it is currently in trend for exploitation by threat actors as remote access to compromised systems. Technical analysis of the malware revealed that it was purely deployed to gather information. The tools employed by the threat actor allowed them to fetch usernames-passwords for other parts of the victim system using ceeeb.dll, an info stealer on browsers that gave them information such as bookmarks and browsing history, and prsm.dll, which allowed the threat actor to capture audio from the infected system.
Insights:
Despite China’s significant contributions to Africa’s telecom industry, they have decided to target the telecom sector. There is a possibility that China might leverage the gathered information on the telecom industry in Africa to expand its market.
There has been an increase in the use of legitimate remote desktop softwares, particularly AnyDesk, as a means of unauthorized remote access. In addition to AnyDesk, various other remote desktop tools like TeamViewer, RuDesktop, ToDesk, and Ammy have also been exploited by APTs and ransomware groups such as Conti, DarkSide, and TA505.
Major Geopolitical Developments in Cybersecurity
A Chinese-speaking group is active against Taiwan, Japan, and South Korea
Chinese-speaking hacker group Genesis Day (also known as Teng Snake) has been targeting research and academic organizations in South Korea, Japan, and Taiwan according to researchers. The attacks started at the beginning of this year in South Korea and appear to be now targeting organizations in Japan and Taiwan with the intention of data exfiltration and cyber espionage According to researchers, as many as twelve South Korean research and academic websites were attacked.
The hackers boasted publicly that their first intended governmental target was the Korea Internet and Security Agency (KISA). The group also made unverified claims of cyberattacks against the US, Ukraine, Taiwan, Japan, and South Korea’s Ministry of Health and Defense Ministry. The researchers believe the group has no ties to the Chinese government but instead is composed of patriotic hacktivists, who are likely to conduct similar cyberattacks against countries deemed hostile to China according to the group’s view.
European air traffic control agency under attack
The European air traffic control agency, Eurocontrol, reports that it’s under cyberattack by Russian actors. Eurocontrol’s site has been targeted in what appears to be the familiar distributed denial-of-service attack type. Eurocontrol coordinates commercial traffic between 41 states, including the EU and their national air-traffic control entities. The outage reportedly jammed the agency’s communication systems and forced some smaller airlines to use older technology to manage flight schedules, including a fax-era backup system. According to the agency, there has been no impact on European aviation beyond the nuisance effect. Russian hacktivist group KillNet has claimed responsibility for the operation.
Other Observations
CYFIRMA Research team observed that the LockBit ransomware group put out an advertisement to hire an entry-level QA tester. This indicates groups focus on capability enhancement and new version development.
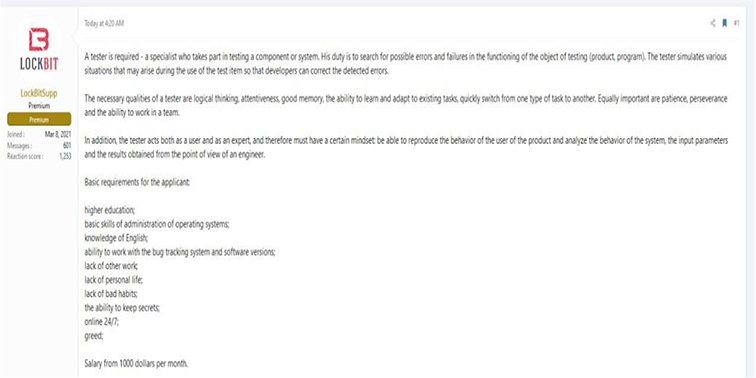
Source: Underground forum
STRATEGIC RECOMMENDATION
- Attack Surface Management should be adopted by organizations, ensuring that a continuous closed-loop process is created between attack surface monitoring and security testing.
- Deploy a unified threat management strategy – including malware detection, deep learning neural networks, and anti-exploit technology – combined with vulnerability and risk mitigation processes.
- Incorporate Digital Risk Protection (DRP) in the overall security posture that acts as a proactive defence against external threats targeting unsuspecting customers.
- Implement a holistic security strategy that includes controls for attack surface reduction, effective patch management, active network monitoring, through next generation security solutions and ready to go incident response plan.
- Create risk-based vulnerability management with deep knowledge about each asset. Assign a triaged risk score based on the type of vulnerability and criticality of the asset to help ensure that the most severe and dangerous vulnerabilities are dealt with first.
MANAGEMENT RECOMMENDATION
- Take advantage of global Cyber Intelligence providing valuable insights on threat actor activity, detection, and mitigation techniques.
- Proactively monitor the effectiveness of risk-based information security strategy, the security controls applied and the proper implementation of security technologies, followed by corrective actions remediations, and lessons learned.
- Move beyond the traditional model of security awareness towards improved simulation and training exercises that mimic real attack scenarios, account for behaviours that lead to a compromised, and are measured against real attacks the organization receives.
- Consider implementing Network Traffic Analysis (NTA) and Network Detection and Response (NDR) security systems to compensate for the shortcoming of EDR and SIEM solutions.
- Detection processes are tested to ensure awareness of anomalous events. Timely communication of anomalies and continuously evolved to keep up with refined ransomware threats.
TACTICAL RECOMMENDATION
- Patch software/applications as soon as updates are available. Where feasible, automated remediation should be deployed since vulnerabilities are one of the top attack vectors.
- Consider using security automation to speed up threat detection, improve incident response, increased the visibility of security metrics, and rapid execution of security checklists.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthen defences based on tactical intelligence provided.
- Deploy detection technologies that are behavioural anomaly-based to detect ransomware attacks and help to take appropriate measures.
- Implement a combination of security control such as reCAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart), Device fingerprinting, IP backlisting, Rate-limiting, and Account lockout to thwart automated brute-force attacks.
- Ensure email and web content filtering uses real-time blocklists, reputation services, and other similar mechanisms to avoid accepting content from known and potentially malicious sources.




