



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Foxtrot Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Foxtrot Ransomware
Researchers have discovered a new ransomware variant named Foxtrot. This ransomware encrypts files, appends the “.foxtrot70” extension to the filenames, and generates a ransom note titled “How_to_back_files.html.” Further analysis revealed that Foxtrot is part of the MedusaLocker ransomware family.
By the ransom note it is clear that this ransomware variant targets companies rather than individuals.

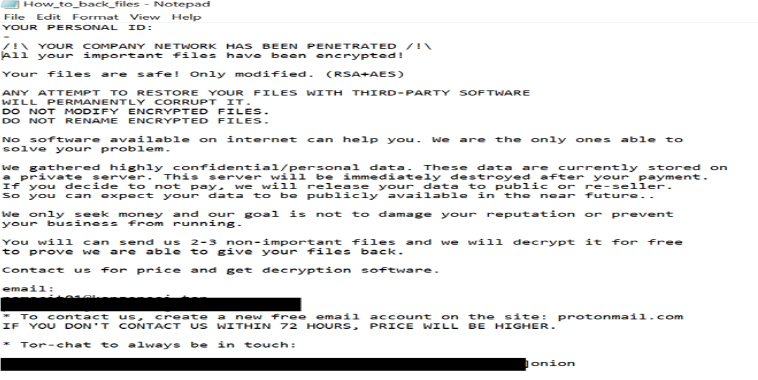
The ransom note states that all important files have been encrypted using a combination of RSA and AES encryption methods. It claims that the files are safe but emphasizes that they can only be restored by the attackers. The note warns against using third-party software to recover the files, stating that such attempts will permanently corrupt them.
Furthermore, the ransom note says that the attackers gathered highly confidential and personal data and will release it publicly if the ransom is not paid. They offer to decrypt a few non-sensitive files for free to prove their decryption capabilities.
Lastly, the note provides two contact emails and says that the ransom price will increase if cybercriminals are not contacted within 72 hours.
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0001: Initial Access | T1091: Replication Through Removable Media |
| 2 | TA0002: Execution | T1047: Windows Management Instrumentation |
| T1059: Command and Scripting Interpreter | ||
| T1129: Shared Modules | ||
| 3 | TA0003: Persistence | T1542.003: Pre-OS Boot: Bootkit |
| T1543.003: Create or Modify System Process: Windows Service | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 4 | TA0004: Privilege Escalation | T1134.004: Access Token Manipulation: Parent PID Spoofing |
| T1543.003: Create or Modify System Process: Windows Service | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1548: Abuse Elevation Control Mechanism | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 5 | TA0005: Defense Evasion | T1027.005: Obfuscated Files or Information: Indicator Removal from Tools |
| T1036: Masquerading | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1112: Modify Registry | ||
| T1134.004: Access Token Manipulation: Parent PID Spoofing | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1202: Indirect Command Execution | ||
| T1222: File and Directory Permissions Modification | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1548: Abuse Elevation Control Mechanism | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 6 | TA0006: Credential Access | T1056.001: Input Capture: Keylogging |
| 7 | TA0007: Discovery | T1012: Query Registry |
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1120: Peripheral Device Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| T1614: System Location Discovery | ||
| 8 | TA0008: Lateral Movement | T1091: Replication Through Removable Media |
| 9 | TA0009: Collection | T1056.001: Input Capture: Keylogging |
| T1074: Data Staged | ||
| 10 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1090: Proxy | ||
| 11 | TA0040: Impact | T1486: Data Encrypted for Impact |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s analysis, based on available data, indicates that MedusaLocker ransomware has been actively targeting a broad range of sectors—including manufacturing, healthcare, finance, IT services, and others since 2019. The projections suggest that Foxtrot, a more sophisticated variant of MedusaLocker, will likely utilize advanced evasion techniques to expand its reach, affecting both individuals and businesses. It is expected to continue targeting major industries globally. As a result, staying vigilant and adopting strong cybersecurity measures are essential to effectively mitigate these evolving threats.
SIGMA Rule:
title: Boot Configuration Tampering Via Bcdedit.EXE
tags:
– attack.impact
– attack.t1490
logsource:
category: process_creation
product: windows
detection:
selection_img:
– Image|endswith: ‘\bcdedit.exe’
– OriginalFileName: ‘bcdedit.exe’
selection_set:
CommandLine|contains: ‘set’
selection_cli:
– CommandLine|contains|all:
– ‘bootstatuspolicy’
– ‘ignoreallfailures’
– CommandLine|contains|all:
– ‘recoveryenabled’
– ‘no’
condition: all of selection_*
fields:
– ComputerName
– User
– CommandLine
falsepositives:
– Unlikely
level: high
(Source: SurfaceWeb)
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Remote Access Trojan (RAT)
Objective: Espionage, Data theft, Remote Access
Target Technologies: Windows OS, Browsers
Target Geography: Italy, Spain & Brazil
Active Malware of the Week
This week “SambaSpy” is trending.
SambaSpy
Researchers identified SambaSpy as a sophisticated Remote Access Trojan (RAT) that has gained attention for its targeted approach, primarily focusing on victims in Italy while also extending its reach to Spain and Brazil. This malware employs advanced techniques, blending malicious activities with legitimate-looking communications to evade detection effectively. SambaSpy exhibits a wide range of functionalities, including keystroke logging, credential theft from major browsers, and remote-control capabilities. As cybercriminals continue to refine their tactics, SambaSpy exemplifies the growing trend of region-specific cyber threats, raising significant concerns for organizations regarding the necessity for tailored cybersecurity strategies in response to this evolving landscape.
Features of SambaSpy
SambaSpy enhances its effectiveness as a Remote Access Trojan through a diverse set of functionalities designed for malicious intent. These features include:
Attack Strategy
Researchers discovered two slightly different infection chains associated with the malware, revealing distinct pathways through which it compromises targeted systems. This finding highlights the adaptability of the cyber threat and underscores the importance of understanding varied attack vectors in order to enhance cybersecurity measures.
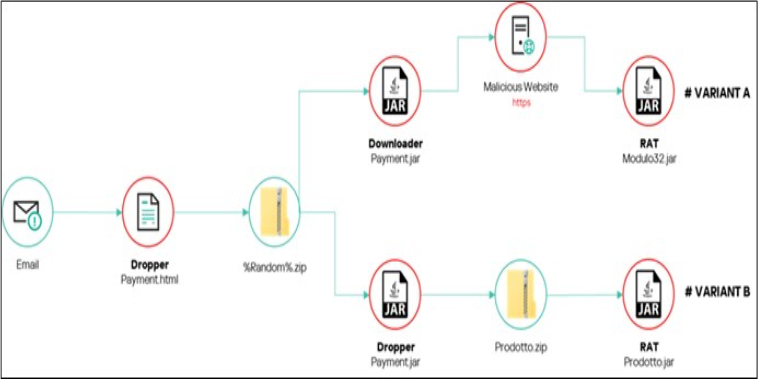
In the second case, which features a more elaborate infection chain. First, the victim receives an email from a German address. However, the email is written in Italian and is designed to appear as though it comes from a legitimate Italian real estate company, aiming to deceive the recipient.
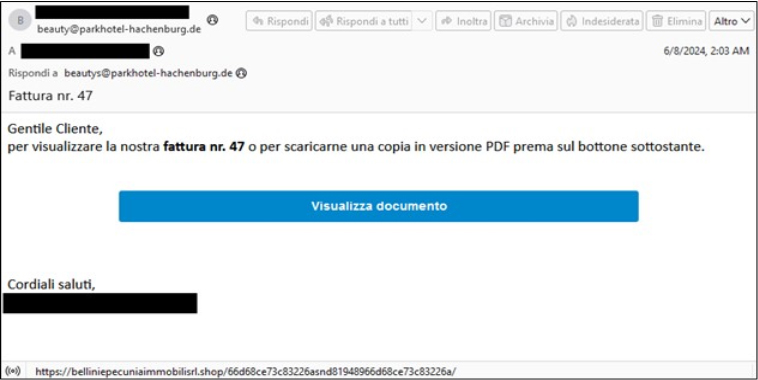
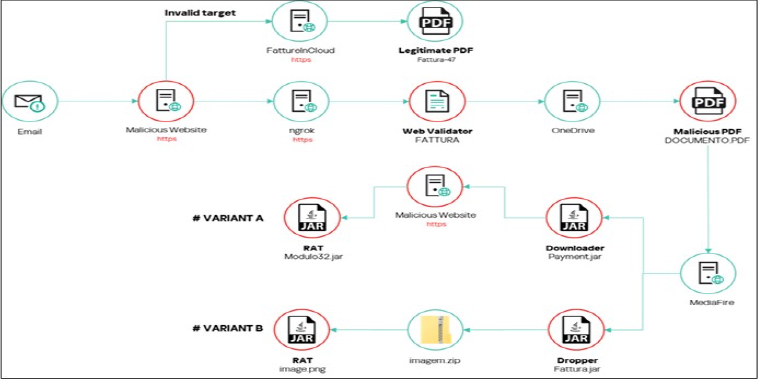
The email prompts the recipient to view an invoice by clicking on an embedded link, which redirects them to a malicious website. This site, according to researchers’ analysis and other sources, leads to FattureInCloud, a legitimate Italian cloud solution for managing digital invoices and quotes, where a valid invoice is displayed. While researchers couldn’t directly access this file, located a similar invoice on the urlscan.io website, as illustrated in the figure below.
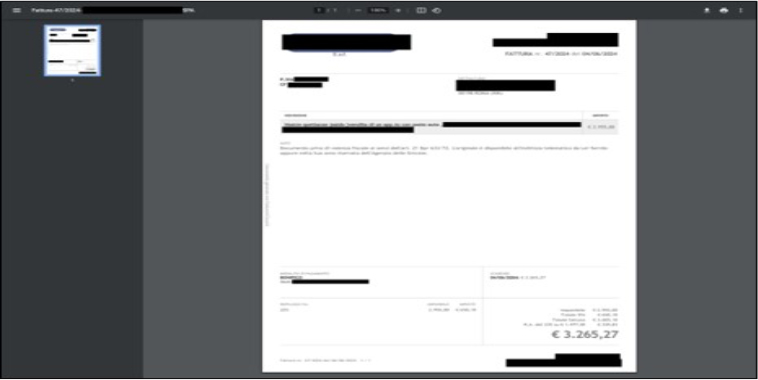
All the distribution campaigns appear to center around the legitimate invoice, with researchers noting a variety of malicious emails that exploit the brand of the company behind the invoice in their sender details, subjects, and content. Although being redirected to a legitimate resource initially seemed like a dead end, further analysis revealed that some users were redirected to a malicious web server hosted on ngrok. This server served an HTML page containing JavaScript code with comments in Brazilian Portuguese, which redirected users to a malicious OneDrive URL only if they were using Edge, Firefox, or Chrome with their language set to Italian. If users did not meet these criteria, they remained on the page. Users who meet the targeting criteria are directed to a PDF document hosted on Microsoft OneDrive, enticing them to click a hyperlink labeled “VISUALIZZA DOCUMENTO,” meaning “view document.” This link ultimately redirects to a malicious JAR file hosted on MediaFire, which functions as either a dropper or a downloader.
The downloader
The downloader performs checks to determine whether it is running in a virtual machine and verifies that the environment is set to Italian. If these conditions are not met, it exits. If all checks are passed, the downloader proceeds to download and execute the final payload.
The dropper
The dropper operates similarly to the downloader, but instead of downloading the malware, it contains the malicious payload embedded within the resources of the JAR file.
Loading plugins
The plugin loading mechanism is straightforward: a class is provided to the RAT and loaded using URLClassLoader to access a file previously downloaded to the disk. It then invokes the addURL() method within the loaded class.
Keylogging and Browser Credential Theft
SambaSpy employs the JNativeHook library to log every keystroke from the victim, sending each event to the command and control (C2) server upon key release. Additionally, it utilizes Java Abstract Window native libraries to steal or modify the victim’s clipboard content. The RAT is capable of stealing credentials from major browsers, including Chrome, Edge, Opera, Brave, Iridium, and Vivaldi.
Remote desktop control
SambaSpy features a custom remote-control system that utilizes the Java Abstract Window Library’s Robot class to manipulate the mouse and keyboard on the victim’s system. It also employs the GraphicsDevice class to enable screen display control for the attacker.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that SambaSpy’s impact on organizations could become increasingly significant as cybercriminals continue refining region-specific, stealthy attacks. As these targeted campaigns grow, organizations might face higher risks from phishing schemes that appear more legitimate, making it harder for employees to recognize threats. This could lead to increased incidents of credential theft, data breaches, and system compromises. Looking ahead, the malware’s ability to blend into legitimate platforms signals a future where attackers exploit trusted services more frequently, making traditional detection methods less effective. Organizations will need to adopt more proactive security measures that focus on behavioral analysis and regional threat intelligence to mitigate these evolving risks. Finally, as malware like SambaSpy becomes more modular and adaptable, organizations may struggle to keep up with its rapid evolution. Future attacks could see malware capable of dynamically changing its tactics, bypassing security updates, and continuing to compromise systems undetected.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Key Intelligence Signals:
UNC1860 and the Temple of Oats: Unveiling Iran’s Covert Influence in Middle Eastern Cyber Operations
Summary:
UNC1860 is a persistent Iranian state-sponsored cyber threat actor linked to Iran’s Ministry of Intelligence and Security (MOIS), characterized by its sophisticated tooling and passive backdoors that enable initial access and persistent infiltration of high-priority networks, particularly in the Middle East’s government and telecommunications sectors. Their operational parallels with other Iranian groups, such as Shrouded Snooper and APT34, suggest a collaborative approach to cyber operations, including providing initial access for destructive attacks. Notably, UNC1860 employs advanced techniques, such as a repurposed Windows kernel driver from legitimate software, to evade detection and maintain long-term access. Their arsenal includes GUI-operated malware controllers like TEMPLEPLAY and VIROGREEN, which facilitate remote access and control for third-party actors. The group’s use of web shells and passive implants, including STAYSHANTE and SASHEYAWAY, further supports stealthy operations, allowing for command execution without traditional C2 infrastructure. UNC1860 demonstrates a high level of sophistication in its coding practices, employing custom implementations of encryption and encoding to evade detection and maintain compatibility. Overall, UNC1860 is a formidable threat actor capable of adapting its strategies to meet evolving geopolitical objectives, posing significant risks to targeted networks in the region.
Relevancy & Insights:
UNC1860 has a history of targeting government and telecommunications sectors in the Middle East, often collaborating with other Iranian threat groups like APT34 to conduct disruptive operations. Previous attacks include the deployment of BABYWIPER against Israeli entities and ROADSWEEP in Albania, indicating a strategic motive of espionage and disruption rather than financial gains. The current incident shows similarities in tactics, techniques, and procedures (TTPs), with UNC1860 using custom malware like TEMPLEPLAY and VIROGREEN to establish initial access and maintain persistent footholds in targeted networks. This suggests a continued focus on high-value targets, such as governmental organizations and critical infrastructure, to support Iran’s geopolitical objectives. Entities in the Middle East, particularly those in the government and telecommunications sectors, need to be vigilant as they are at high risk. CYFIRMA assesses that UNC1860’s activities are likely aimed at gathering sensitive information and potentially enabling further disruptive operations, reflecting a persistent and evolving threat that aligns with Iran’s broader strategic goals in the region.
ETLM Assessment:
UNC1860 is a sophisticated Iranian state-sponsored threat actor, likely affiliated with Iran’s Ministry of Intelligence and Security (MOIS), known for its role as an initial access provider supporting espionage and disruptive operations. The group primarily targets government and telecommunications sectors across the Middle East, focusing on countries like Israel, Saudi Arabia, Qatar, and Iraq, and has also been linked to operations in Albania. UNC1860 exploits vulnerable technologies, particularly Microsoft SharePoint (CVE-2019-0604) and VPN servers, deploying advanced malware such as TEMPLEPLAY, VIROGREEN, and passive implants like TOFUDRV and TEMPLEDROP, which evade detection through sophisticated methods. The group collaborates with other MOIS-linked actors, like APT34, and has been involved in significant attacks, including those using BABYWIPER and ROADSWEEP. Given its adeptness in maintaining persistent access and its evolving toolkit, UNC1860 is expected to continue being a major threat in the region, capable of adapting its operations to support various strategic objectives ranging from espionage to network disruption. As tensions in the Middle East persist, UNC1860’s activities are likely to remain aligned with Iran’s geopolitical goals, posing a significant risk to regional stability.
Recommendations:
These recommendations aim to reduce the risk posed by UNC1860 and enhance organizational resilience against similar advanced persistent threats (APTs).
| MITRE ATT&CK Tactics and Techniques | ||
| Tactics | ID | Technique |
| Initial access | T1190 | Exploit Public-Facing Application |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1129 | Shared Modules |
| Privilege escalation | T1068 | Exploitation for Privilege Escalation |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Persistence | T1547.006 | Boot or Logon Auto start Execution: Kernel Modules and Extensions |
| Persistence | T1505.003 | Server Software Component: Web Shell |
| Defense evasion | T1036.005 | Masquerading: Match Legitimate Name or Location |
| Defense evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense evasion | T1218.011 | System Binary Proxy Execution: Rundll32 |
| Defense evasion | T1218.002 | System Binary Proxy Execution: Control Panel |
| Defense evasion | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Discovery | T1018 | Remote System Discovery |
| Discovery | T1135 | Network Share Discovery |
| Discovery | T1046 | Network Service Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Lateral Movement | T1021.001 | Remote Services: Remote Desktop Protocol |
| Lateral Movement | T1210 | Exploitation of Remote Services |
| Collection | T1005 | Data from Local System |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1573 | Encrypted Channel |
| Command and Control | T1090 | Proxy |
| Impact | T1485 | Data Destruction |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
US government disrupts Chinese botnet
The U.S. Department of Justice has revealed a court-sanctioned law enforcement operation that successfully dismantled a botnet network comprising over 200,000 consumer devices, such as routers, IP cameras, DVRs, and network-attached storage units. The Justice Department stated that the devices were compromised by hackers sponsored by the Chinese government, specifically working for Integrity Technology Group, a Beijing-based company also referred to in the private sector as Flax Typhoon. Researchers have identified the botnet, named “Raptor Train,” as having been used to target critical infrastructure in both the U.S. and Taiwan.
ETLM Assessment:
The court-authorized operation took control of the hackers’ computer infrastructure and, among other steps, sent disabling commands through that infrastructure to the malware on the infected devices. During the course of the operation, there was an attempt to interfere with the FBI’s remediation efforts through a distributed denial-of-service (DDoS) attack targeting the operational infrastructure that the FBI was utilizing to effectuate the court’s orders. The attack was ultimately unsuccessful in preventing the FBI’s disruption of the botnet. The case signifies another case of active defense on behalf of the U.S. government in tackling the issue of Chinese cyber-statecraft – China is the number one state sponsor of cyberattacks in the world.
Telegram‘s use banned in Ukraine for government and military use
Ukraine’s National Security and Defense Council (NSDC) has prohibited the use of the Telegram app on official devices used by government officials, military personnel, and employees at critical infrastructure sites. The NSDC pointed to national security risks, stating it has “credible information” that Russian intelligence could exploit the app to distribute malware and collect data to aid in missile strikes. Researchers note that Telegram remains the main platform for news sharing among most Ukrainians. The ban does not apply to personal devices or those who use the app for their official responsibilities.
ETLM Assessment:
The information of Telegram being compromised by the Russian intelligence agencies arrives on the back of the company’s founder Pavel Durov being arrested in France earlier in August. French prosecutors said they detained the Russian-born billionaire, who is now a French-Emirati citizen, as part of an investigation opened in July into the messaging app’s moderation of alleged criminal activity on the platform.
Founded in 2013, Telegram has rapidly gained popularity, approaching 1 billion users and becoming a key communication tool in conflict zones and humanitarian crises, such as the Russia-Ukraine war and the Israel-Hamas conflict.
Durov has adopted a largely hands-off approach to moderation, presenting the app as immune to government influence. However, some researchers have cautioned that this has led to Telegram becoming a hotspot for illicit activities and extremism. Known as the “Mark Zuckerberg of Russia” for co-founding the popular social media platform VKontakte, Durov left Russia in 2014 after reportedly refusing to comply with Moscow’s requests for access to data from Ukrainian users protesting against a pro-Russia government. In recent years, Durov has sought to distance himself and the app from Russia, however, many analysts point out the fact his private jet has been repeatedly returning to Russia anytime his business was in trouble and intelligence agencies are thus expecting his platform to be compromised by the Russian state and it is not only possible but also likely that Kremlin may still have ties to or influence over Telegram. This makes the app unsafe for official use and the Ukrainian move is expected to be followed by further governments in the future.
US to propose ban on auto technology from China and Russia
The U.S. Commerce Department is set to propose a ban on certain software and hardware from Chinese and Russian sources for connected vehicles. In a statement, the department cautioned that, in extreme circumstances, a foreign adversary could simultaneously disable or seize control of all vehicles operating in the United States, potentially leading to crashes or obstructed roadways. The Secretary of Commerce also highlighted the risk that China or Russia could exploit backdoor software to gather detailed location information on Americans. Reports indicate that this ban will not impact vehicles that have already been manufactured; instead, the software ban will apply to vehicles from the 2027 model year, while the hardware ban will take effect for the 2030 model year. Russia exports hardly any cars to the U.S., however, China is making moves to become the global leader in the EV industry, a goal that is well underway.
ETLM Assessment:
This year, the Five Eyes security officials warned against hacking campaigns by Volt Typhoon, a Chinese state-sponsored outfit. Beijing’s hackers were trying to position themselves in a way that could try to paralyze U.S. critical infrastructure in case of an eruption of conflict between the two countries over the issue of Taiwanese or Philippine waters. An attempt to induce societal panic in their adversary in case of conflict is an inherent part of Chinese military doctrine and targeting critical infrastructure on Guam could affect U.S. military operations in significant ways. The ban on Chinese EVs is a logical extension of the U.S.‘ fear of China deploying cyber time bombs in case of conflict.
The RansomHub Ransomware impacts the Vinati Organics
Summary:
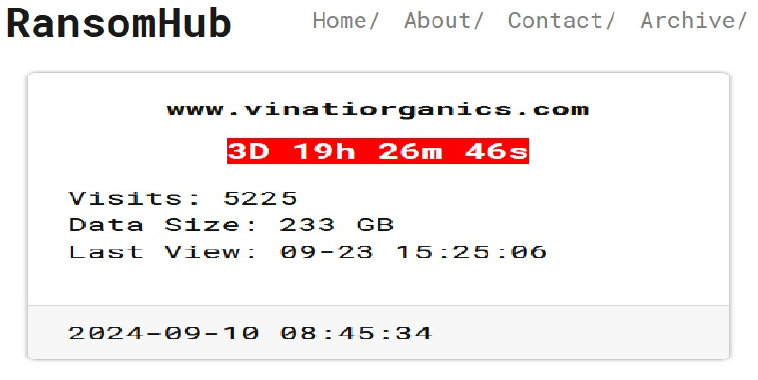
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from India; Vinati Organics (www[.]vinatiorganics[.]com), was compromised by the RansomHub Ransomware. Vinati Organics is a leading global producer of specialty chemicals and organic intermediaries, headquartered in India. The company specializes in manufacturing high-quality products like Iso Butyl Benzene (IBB), 2-Acrylamido-2-methylpropane sulfonic acid (ATBS), Iso Butylene(IB), and High Purity-Methyl Tertiary Butyl Ether( HPMTBE), which serve diverse industries, such as pharmaceuticals, agrochemicals, and water treatment across the US, Europe and Asia. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization. The total size of the compromised data is approximately 233 GB.
The following screenshot was observed published on the dark web:
Relevancy & Insights:
ETLM Assessment:
Based on recent assessments by CYFIRMA, RansomHub ransomware is expected to intensify its operations across various industries worldwide, with a notable focus on regions in the United States, Europe, and Asia. This prediction is reinforced by the recent attack on Vinati Organics, a prominent Manufacturing company from India, highlighting RansomHub’s significant threat presence in the South Asian region.
The Hunters International Ransomware Impacts the Bank Rakyat
Summary:
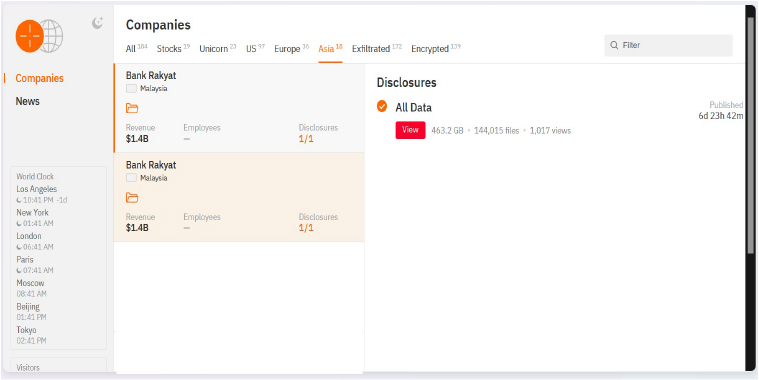
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Malaysia; Bank Rakyat (www[.]bankrakyat[.]com[.]my), was compromised by Hunters International Ransomware. Bank Rakyat is Malaysia’s largest Islamic cooperative bank. The bank primarily offers Islamic banking services, focusing on Shariah-compliant financial products, such as personal and home financing, credit and debit cards, and wealth management solutions. Bank Rakyat also offers specialized products like education financing, microfinancing, and various types of insurance (Takaful) plans. The compromised data encompasses a trove of sensitive and confidential records, originating from the organizational database. The scale of the data exposure measures approximately 463.2 GB, comprising a total of 1,44,015 discrete files.
The following screenshot was observed published on the dark web:
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, the Hunters International ransomware group is expected to continue targeting a wide range of industries globally, with a particular focus on the United States, Europe, and Asia. A recent attack on Bank Rakyat, a leading Finance company in Malaysia, highlights the significant threat this ransomware poses in the Southeast Asia region. This incident highlights the growing risk to critical industries in the area and the importance of strengthening cybersecurity defenses against such sophisticated threats.
Vulnerability in XenSource Xen
Summary:
The vulnerability allows a local user to perform a denial of service attack (DoS) on the target system.
Relevancy & Insights:
The vulnerability exists due to a deadlock within the vlapic_error() function.
Impact:
A buggy or malicious HVM or PVH guest can deadlock Xen and perform a denial-of-service attack.
Affected Products: https[:]//xenbits[.]xen[.]org/xsa/advisory-462.html
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
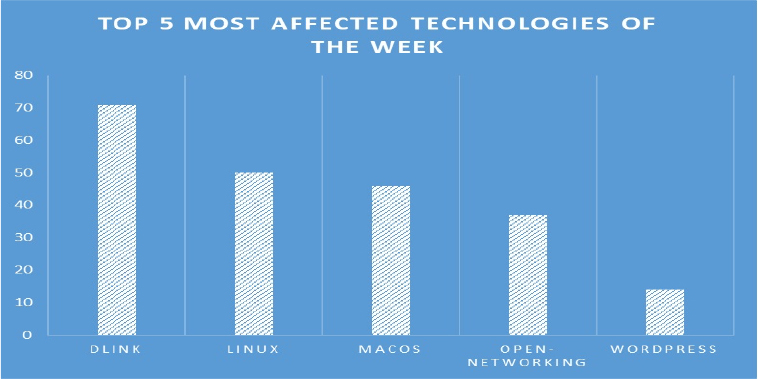
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment:
Vulnerability in Xen can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of Xen is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding virtualization activities that allow multiple operating systems to execute on the same hardware concurrently, across different geographic regions and sectors.
ValenciaLeaks Ransomware attacked and Published the data of the Duopharma Biotech
Summary:
Recently, we observed that the ValenciaLeaks Ransomware attacked and published data of Duopharma Biotech Berhad (www[.]duopharmabiotech[.]com) on its dark web website. Duopharma Biotech Berhad is a Malaysian-based investment holding company. The principal activities of its subsidiary are to carry out business as a manufacturer, distributor, importer, and exporter of pharmaceutical products and medicines. Duopharma exports to countries such as Vietnam, Ethiopia, Sudan, Southeast Asia, Papua New Guinea, Pakistan, Bangladesh, Sri Lanka, the Republic of Yemen, Singapore, and Hong Kong. Its range of products includes tablets, capsules, syrup, antibiotics, creams, haemodialysis solutions, sterile irrigation solutions, sterile powder injectables, small-volume injectables, dental cartridges, and eye drop preparations. The data leak, following the ransomware attack, encompasses sensitive and confidential information related to the organization. The total size of the data breached is approximately 25.7 GB.
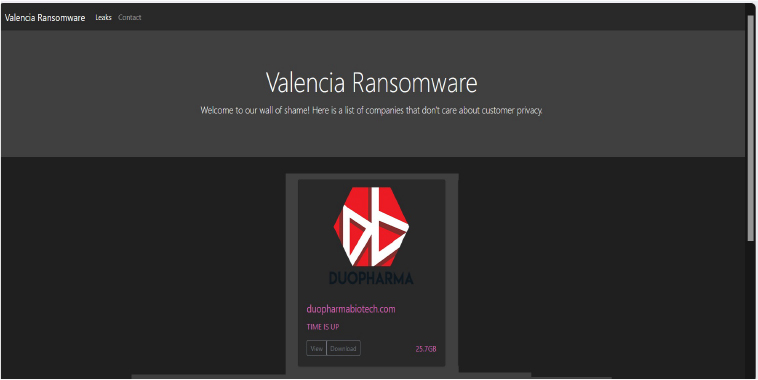
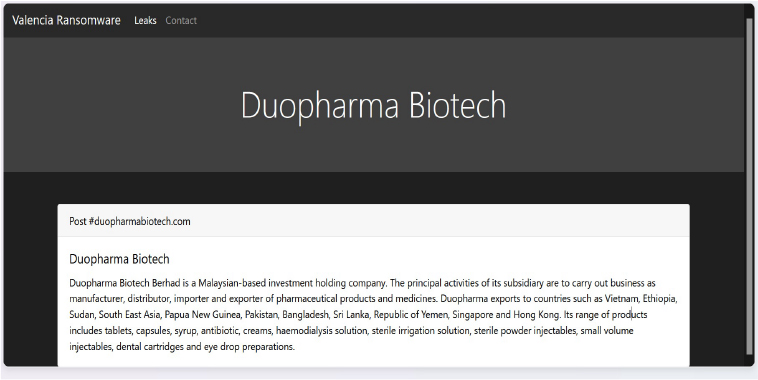
Relevancy & Insights:
ETLM Assessment:
ValenciaLeaks ransomware represents a growing threat in the cybersecurity landscape, utilizing sophisticated tactics and double-extortion strategies to maximize impact on organizations. Vigilance and proactive security measures are essential for mitigating the risks associated with this evolving threat.
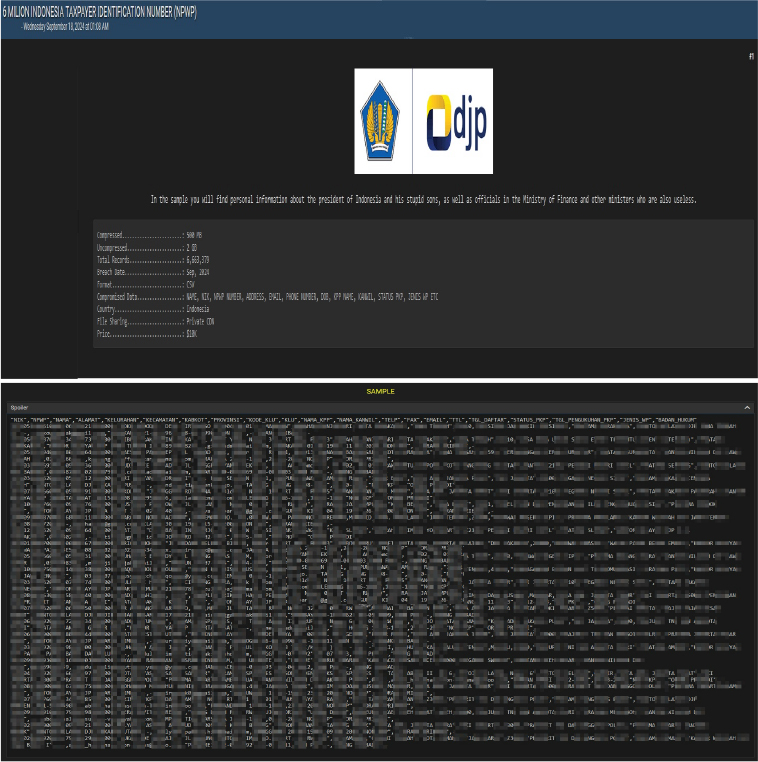
Indonesian Officials’ Data Advertised on a Leak Site
Summary:
A threat actor has claimed responsibility for leaking the personal information of high-ranking Indonesian officials, including the president and his family, on a dark web forum. The alleged data breach, which reportedly occurred in September 2024, exposed detailed personal information about the Ministry of Finance staff, and other cabinet members as well.
According to the threat actor’s post, the compromised data spans approximately 6.6 million records, which have been compressed into a 500 MB file. Once uncompressed, the data size increases to 2 GB and is available in CSV format. The stolen data allegedly includes sensitive information, such as names, national identification numbers, tax registration numbers, residential addresses, email addresses, phone numbers, dates of birth, tax office names, regional tax office details, tax status, and more.
The cybercriminal is reportedly selling the database for $10,000 via a private CDN, stating that the dataset includes highly classified information about the officials, which could have serious implications for the country’s government.
Chunghwa Telecom Data Advertised on a Leak Site
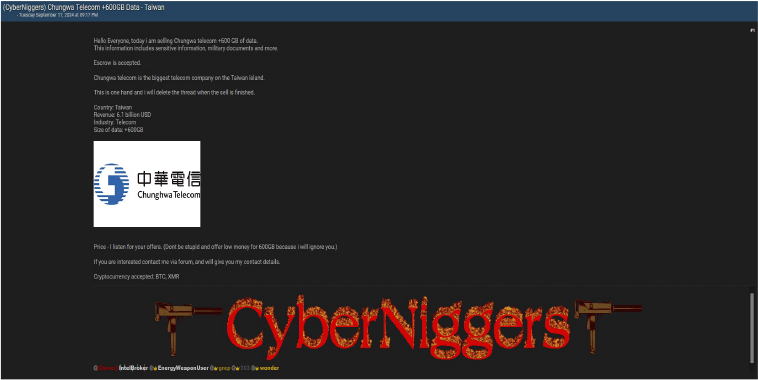
Summary:
A threat actor on a dark web forum has claimed to possess over 600GB of sensitive data, allegedly stolen from Chunghwa Telecom, Taiwan’s largest telecommunications company. The post asserts that the data contains classified documents, including sensitive information and military documents.
The threat actor emphasized that escrow services would be accepted for the transaction. However, they made it clear that they would only entertain serious offers and would ignore any low bids.
The threat actor has indicated that the listing will remain active until the sale is finalized, at which point the post will be deleted. Prospective buyers are encouraged to contact the threat actor via the forum, with payment being accepted in cryptocurrency, including Bitcoin (BTC) and Monero (XMR), ensuring anonymity for both parties. The data breach has been attributed to a threat actor identified as “303”.
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
Threat Actor “303” is driven primarily by financial motives, frequently targeting a broad spectrum of industries, such as healthcare, finance, manufacturing, and critical infrastructure. This actor poses a significant risk in the cybersecurity landscape, employing advanced techniques to facilitate data breaches and achieve financial gains through the exploitation of sensitive information. To defend against this evolving threat, organizations must maintain heightened awareness and adopt proactive cybersecurity measures.
Recommendations: Enhance the cybersecurity posture by
Oracle Corporation, a leading multinational computer technology company, has allegedly suffered a data breach impacting the personal details of its employees.
According to the post, the breach exposed sensitive employee details from a third-party source, affecting 4,002 records.
The compromised information includes employees’ first and last names, job titles, company names, email addresses, and their locations, spanning personal and corporate addresses from various cities, states, and countries. The breach also revealed the timestamps for when the emails were created and last verified. The data breach has been attributed to a threat actor identified as “888”.

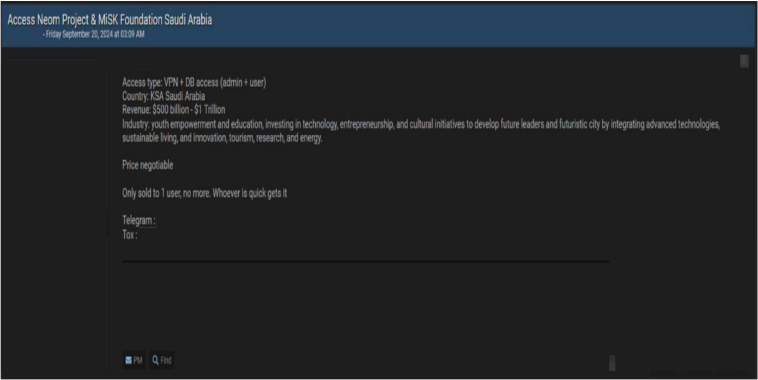
A threat actor claims to be offering access to the Neom Project and MiSK Foundation in Saudi Arabia. The access allegedly includes VPN and database privileges, both admin and user-level, to systems related to two of Saudi Arabia’s most significant initiatives.
According to the actor, the Neom Project, a futuristic mega-city initiative, and the MiSK Foundation, focused on youth empowerment, education, and technology investments, are both targets. These entities collectively represent industries, ranging from education and entrepreneurship to research, energy, and sustainable living. The revenue for these organizations is claimed to range between $500 billion and $1 trillion, reflecting their high economic importance.
ETLM Assessment:
The “888” threat actor group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries, indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
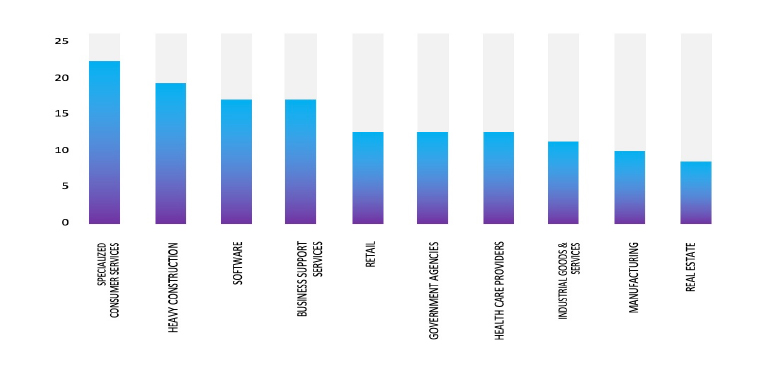
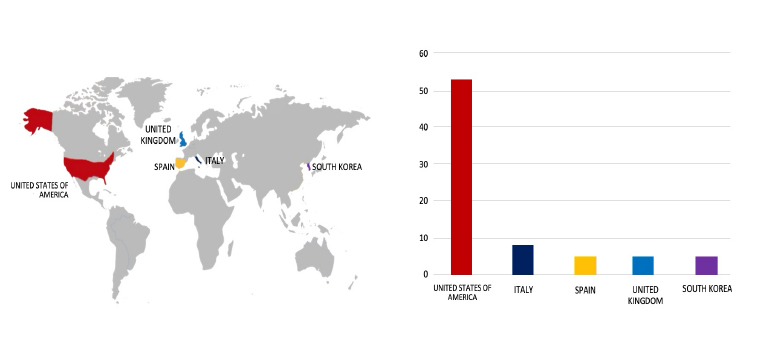
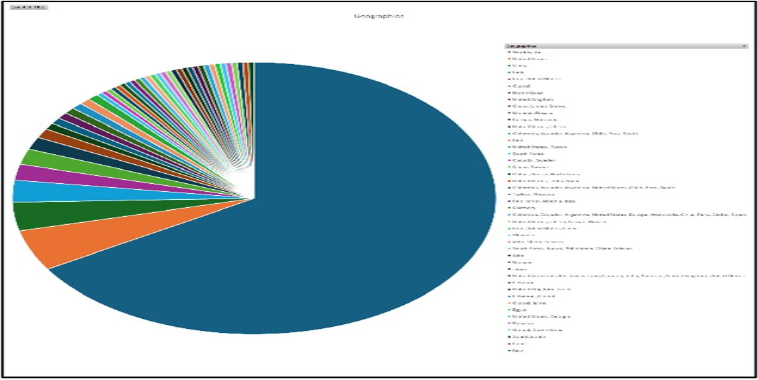
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
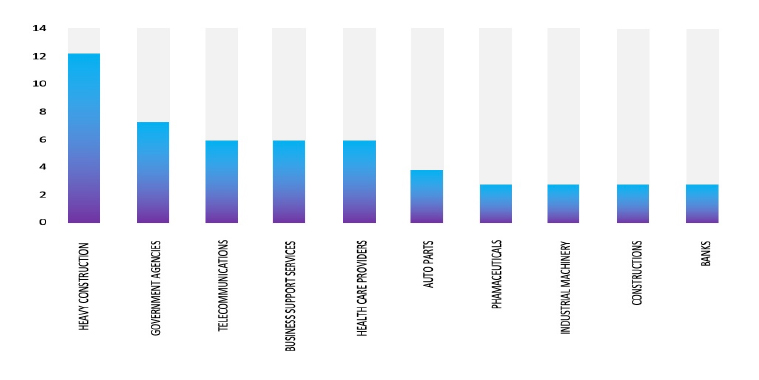
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.