



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
Targeted Geography: Austria, Australia, China, France, Netherlands, United Kingdom, United States.
Targeted Industries: Business Services, Construction, Education, Furniture, Healthcare Services, Home Improvement Retailers, Hotels, IT, Manufacturing, Metals & Mining, Real Estate.
CYFIRMA Research and Advisory Team has found an update of INC/INC. Ransom ransomware while monitoring various underground forums as part of our Threat Discovery Process.
INC ransomware strain emerged at the end of July of 2023. The ransomware will encrypt the files and append them with the “.INC” extension.
The initial access methods of ransomware can vary, with observed techniques encompassing spear-phishing emails and the targeting of vulnerable services. This targeting extends to the exploitation of CVE-2023-3519(CVSS-9.8) in Citrix NetScaler. Once initial access is achieved, a diverse range of Living off the Land Binaries (LOLBINs) is employed for ongoing internal reconnaissance and lateral movement. The tools used in ransomware operations consist of:
The ransomware payloads support multiple command-line arguments. Commands supported by Inc ransomware include:
Argument : Function
–file : Target a file directly for encryption (path)
–dir : Target a directory for encryption (path)
–sup : Stop using process
–ens : Encrypt network shares
–lhd : Local hidden drives (encrypt hidden boot and recovery volumes)
–debug : Output console-style debug logging
In case the threat actor excludes the utilization of command-line arguments, the payload will directly encrypt the local device’s data, encompassing all accessible volumes and files.
Copies of the ransom notes are generated in both .TXT and .HTML formats, designated as “INC-README.TXT” and “INC-README.HTML,” respectively.
Every victim receives a unique personal ID within their ransom notes, which they are expected to use when visiting the payment site.
It’s important to note that the ransomware seems to try to erase Volume Shadow Copies (VSS).
The ransomware payloads contain the following debug strings. C:\source\INC Encryptor\Release\INC Encryptor.pdb

Files Encrypted by INC Ransomware(Source: Surface web)
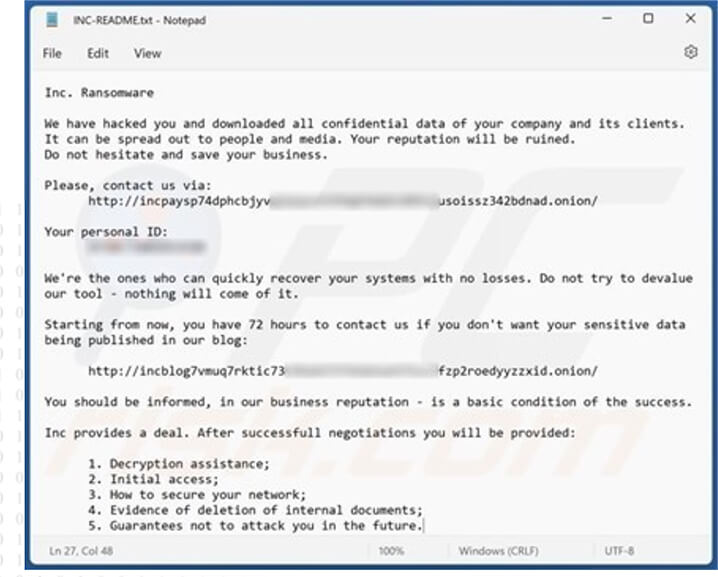
INC Ransomware Note (source: surface web)
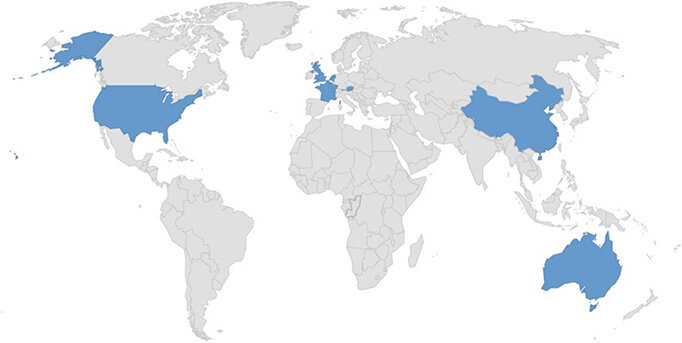
Countries Targeted by INC Ransomware
Based on available information, CYFIRMA’s assessment asserts that INC ransomware is likely to continue focusing on Windows OS systems, with a strong emphasis on propagating through USB drives, sophisticated user interaction capabilities, and flexibility in its encryption methods. Its primary aim seems to be disrupting critical sectors, with the United States being a potential primary target.
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0001: Initial Access | T1091: Replication Through Removable Media |
| T1190: Exploit Public-Facing Application | ||
| 2 | TA0002: Execution | T1059: Command and Scripting Interpreter |
| T1129: Shared Modules | ||
| T1569.002: System Services: Service Execution | ||
| 3 | TA0003: Persistence | T1574.002: Hijack Execution Flow: DLL Side-Loading |
| 4 | TA0004: Privilege Escalation | T1574.002: Hijack Execution Flow: DLL Side-Loading |
| 5 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1036: Masquerading | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1222: File and Directory Permissions Modification | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 6 | TA0006: Credential Access | T1056: Input Capture |
| 7 | TA0007: Discovery | T1082: System Information Discovery |
| T1083: File and Directory Discovery | ||
| T1120: Peripheral Device Discovery | ||
| 8 | TA0008: Lateral Movement | T1091: Replication Through Removable Media |
| 9 | TA0009: Collection | T1056: Input Capture |
| 10 | TA0011: Command and Control | T1090: Proxy |
| 11 | TA0040: Impact | T1486: Data Encrypted for Impact |
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
Type: Information Stealer
Objective: Credentials & Data Theft
Target Technology: Windows OS
This week “ExelaStealer” is trending.
In 2023, the InfoStealer market is competitive with established players like RedLine, Raccoon, and Vidar holding a significant market share. Researchers discovered that ExelaStealer is a recent addition to the crowded landscape of information stealers targeting Windows systems. These malware types are designed to capture sensitive data. Despite the prevalence of such infostealers, ExelaStealer’s emergence highlights the potential for new players to establish themselves in this space.
ExelaStealer is an open-source InfoStealer primarily written in Python, but it can incorporate resources from other languages like JavaScript. This tool allows threat actors to steal sensitive data from Windows-based systems, including passwords, credit card information, cookies, session data, and key logs.
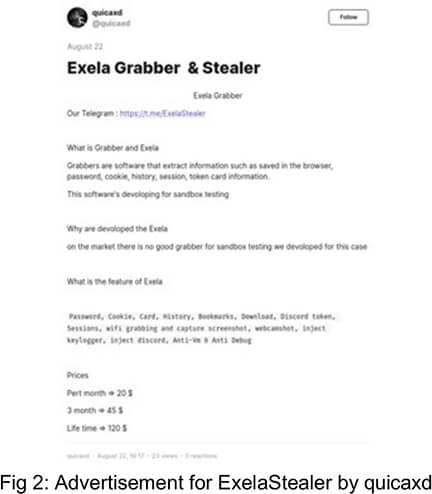
ExelaStealer: Dark Web Ads and Prices
ExelaStealer is advertised on the Dark Web, offering both open-source and paid versions. The advertisements provide valuable insights into its capabilities. These ads seem to be posted by “quicaxd,” the primary contact for ExelaStealer. The pricing includes $20 for one month of use, $45 for three months, and a lifetime subscription for $120.
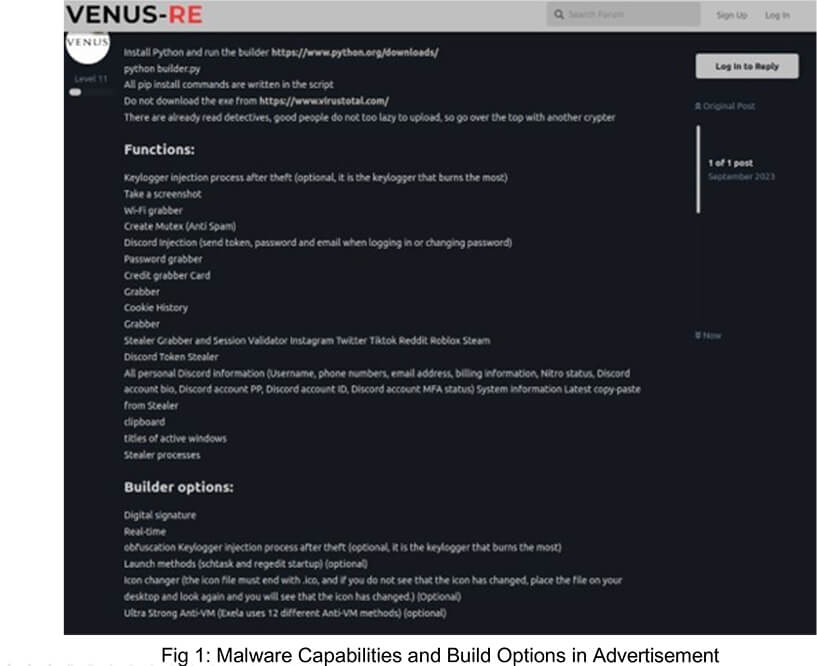
ExelaStealer’s active Telegram channel allows users to access both the paid and open- source versions via GitHub repository.
Researchers observed that the binaries analyzed appeared to be linked to a specific campaign, a conclusion further supported by the presence of a decoy document.
Regrettably, the initial infection vector was unclear, but it could have been initiated through various means, including phishing, watering holes, or other malware distribution.
The binary “sirket-ruhsat-pdf.exe” serves as the initial stage for deployment. Its primary functions include launching the “sirket-ruhsat-pdf.exe” executable and displaying a decoy PDF document named “BNG 824 ruhsat.pdf” to the user. Both of these files are deposited into the root of the C: Drive.
The “sirket-ruhsat-pdf.exe” attempts to find a compatible PDF viewer and open the decoy document,The PDF is a copy of a Turkish vehicle registration certificate for a Dacia Duster. which is entirely benign and serves as a visual distraction.
From the ETLM perspective, CYFIRMA expects that the future of info-stealers, like ExelaStealer is likely to involve increased sophistication, broader target diversity across industries, and the integration of multifaceted capabilities. Cybercriminals are currently in the process of expanding the capabilities of the Exela stealer beyond its current functionalities. By incorporating these new capabilities, it will become an even more formidable and versatile tool in the arsenal of fraud-related actors, heightening the risks associated with its usage. In today’s tech-driven world, where cyber threats are constantly evolving and becoming smarter, staying one step ahead is crucial to ensuring the security of your data and systems.
Indicators of Compromise
Kindly refer to the IOCs Section to exercise controls on your security systems.
Key Intelligence Signals:
Threat Actors Weaponize Malicious Script to Mine Cryptocurrency
Summary:
In a recent observation, many unknown threat actors were observed employing malicious scripts. In April of this year, the FBI issued an advisory warning about a series of cyberattacks targeting government, law enforcement, and non-profit organizations. These attacks involve the deployment of multiple types of malwares on victims’ devices. The primary objectives of the attackers are to harness company resources for cryptocurrency mining, steal sensitive data through keyloggers, and establish unauthorized backdoor access to computer systems. Upon investigation of the indicators of compromise identified in the FBI’s April report, previously undisclosed malicious scripts were discovered in August. These scripts attempted to manipulate Windows Defender, with one script disabling the security software and another attempting to add specific files to its exceptions list. The attackers also gained administrator privileges and renamed folders associated with security solutions to avoid detection. Further investigation revealed that the scripts aimed to mine Monero cryptocurrency on the infected devices. The malware collected keystrokes through a keylogger and established a backdoor connection to a command-and-control server. Over 10,000 attacks on more than 200 users worldwide have been recorded since May 2023, with a focus on the B2B sector, affecting various types of organizations in countries including Russia, Saudi Arabia, Vietnam, Brazil, Romania, and sporadically in the United States, India, Morocco, and Greece.
Relevancy & Insights:
The menace encompasses a combination of various malware, such as cryptocurrency miners and keyloggers, targeting a diverse set of victims. Neither the FBI, nor Kaspersky has publicly attributed this campaign to a specific cyberthreat group.
ETLM Assessment:
The cryptocurrency market, valued at $1.28 trillion, presents an appealing opportunity for hackers to target cryptocurrency traders and wallets. It’s clear that if malicious scripts, which primarily infiltrate systems by exploiting vulnerabilities in servers and computers, fall into the hands of threat actors with the objective of financial gains, they will use them extensively to steal cryptocurrency. As the cryptocurrency market continues to expand, the risk to the cryptocurrency owners facing various types of cyber-attacks by financially motivated threat actors will also increase in the future.
Recommendations:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Five Eyes warn of AI-enabled Chinese Espionage
The Five Eyes countries of Australia, Canada, New Zealand, the United Kingdom and
the United States have made an unprecedented step of publicly campaigning for industry and academic help on the issue of Chinese cyber and AI enabled IP theft. The chiefs of counterintelligence have made an unusually open appearance on American TV program 60 Minutes (CBS), where they publicly aired their concerns in an unprecedented joint appearance. The U.S. FBI Director Christopher Wray said the “unprecedented” joint call was meant to confront the “unprecedented threat” China poses to innovation across the world. According to the officials, China is stealing secrets in various sectors, from quantum technology and robotics to biotechnology and artificial intelligence to defense and manufacturing. The U.S. has long accused China of intellectual property theft and the issue has been a key sore point in U.S.-China relations. But this is the first time the Five Eyes members have joined publicly to call out China on it.
ETLM Assessment:
Such espionage is nothing new, especially coming from China. The warnings expressed are an echo of warnings issued by Cyfirma in the report on Chinese IP theft with the addition of new threats posed by AI-assisted data theft efforts. However, what the Five Eyes find particularly unsettling, is the use of artificial intelligence in these campaigns, given its potential to amplify and augment the threat. Chinese hackers have been mainly focusing on the defense industrial base, successfully compromising the networks of contractors to the Pentagon’s U.S. Transportation Command, 20 times in a single year, while many other incursions have probably never been found. Some researchers are also worried China is trying to position itself in a way it could try to paralyze U.S. critical infrastructure in case of eruption of conflict between the two countries over the issue of Taiwan.
Iranian hackers active among Middle East tensions
Iran’s OilRig threat group (also known as APT34) has conducted an eight-month intrusion campaign against a rival Middle Eastern government, according to recently published research. Iranian hackers stole files and passwords and, in one case, installed a PowerShell backdoor (dubbed PowerExchange), that was used to monitor incoming mails sent from an Exchange Server, to execute commands sent by the attackers in the form of emails, and surreptitiously forwarded results to the attackers. The researchers have not specified the specific government and entity targeted in this campaign, but OilRig has historically targeted Saudi Arabia, Israel, the United Arab Emirates, Iraq, Jordan, Lebanon, Kuwait or Qatar, as the Iranian government has security interest in virtually every country in the region.
ETLM Assessment:
There are likely similar campaigns by other Iranian actors pursuing the same goals of data exfiltration for the purpose of espionage. The cyber realm has been taking the form of the vanguard of geopolitical statecraft with the Middle East serving as the hotbed of both geopolitics and subsequently innovation and use of cyber intelligence collection, cyber warfare and integration of cyber warfare with kinetic means of conflict.
Hacktivism and influence operations continue to dominate the cyber side of the Hamas- Israel war
Opportunistic nuisance-level hacktivism remains a defining feature of cyber operations in the Hamas-Israel confrontation. Influence operations compete for accountability for the explosion that occurred at Gaza’s Al Ahli Hospital. The US Intelligence Community has tentatively concluded that the explosion appears to have been an accident caused by a Palestinian Islamic Jihad missile that malfunctioned and was fired from Gaza into Israel. That was Israel’s stance soon after the event. However, Hamas’s assertions that the explosion was caused by an Israeli airstrike are still widely believed and shared among Islamist and larger Arab circles, where they have sparked this week’s wave of protests. Most hacktivism stirred by the conflict has been carried out with Hamas’ benefit in sight. Private-sector players operating in Israel appear to have focused on gathering and analyzing information, especially when it comes to identifying and finding captives abducted during the early Hamas strikes.
ETLM Assessment:
Israel will seek to eliminate the threat posed by the Palestinian militant group for good, but that will require extensive bombing followed by boots-on-the-ground fighting in the Palestinian territory itself. This will cause very high collateral damage and civilian casualties in the Gaza strip, which could draw in other adversaries, including Hezbollah, al-Qaeda or even Iran. The cyberspace part of the conflict is likely just in its beginning and we are likely to see a spike in the activity of Iranian APTs attacking countries that support Israel. Russia might throw its weight behind some of the activity as well, as intensification of the conflict suits its interest, driving attention from its war in Ukraine and consuming resources that could otherwise help its western neighbor.
Simpson Strong-Tie is Impacted by Black Basta Ransomware
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in the dark forum that a company from The United States of America, (www[.]strongtie[.]com), was compromised by Black Basta Ransomware. Simpson Strong-Tie is the world leader in structural engineering solutions and deeply dedicated to a mission of helping people design and build safer, stronger structures. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. This compromised data includes highly confidential and sensitive information pertaining to the organization, totaling around 71.5 GB.
The following screenshot was observed published on the dark web:
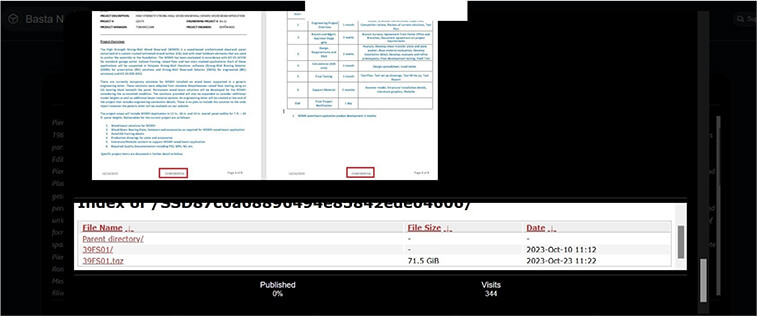
Source: Dark Web
Relevancy & Insights:
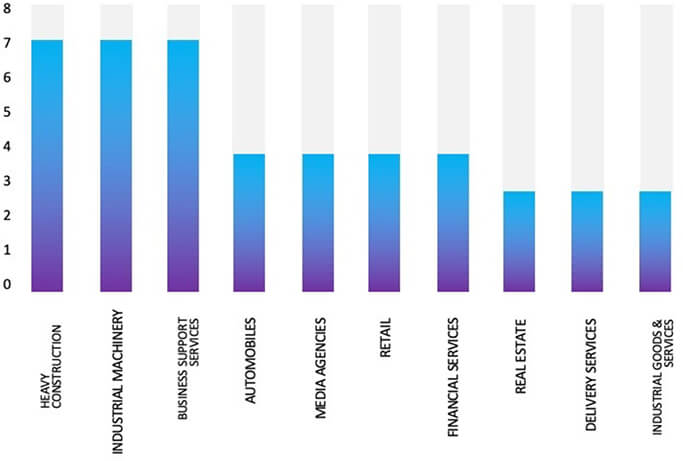
ETLM Assessment:
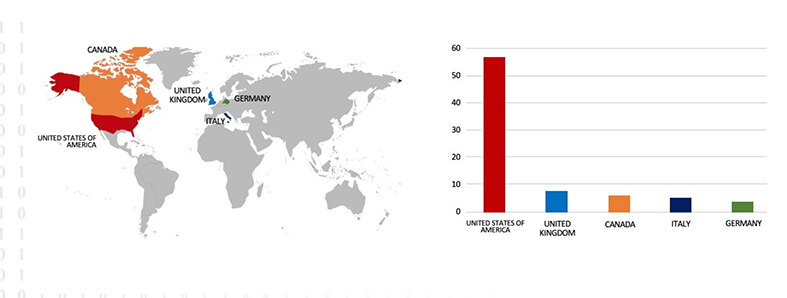
CYFIRMA’s assess Basta Ransomware will continue to prioritise American businesses and their associated entities that store substantial volumes of Personally Identifiable Information (PII).
Vulnerability in OMRON CX-Designer: 3.740
Summary:
The vulnerability allows a remote attacker to gain access to sensitive information.
Relevancy & Insights:
The vulnerability exists due to insufficient validation of user-supplied XML input. A remote attacker can pass a specially crafted XML code to the affected application and view contents of arbitrary files on the system or initiate requests to external systems.
Impact:
Successful exploitation of the vulnerability may allow an attacker to view contents of arbitrary files on the server or perform network scanning of internal and external infrastructure.
Affected Products:
https://www[.]fa[.]omron[.]co[.]jp/product/security/assets/pdf/en/OMSR- 2023-011_en.pdf
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
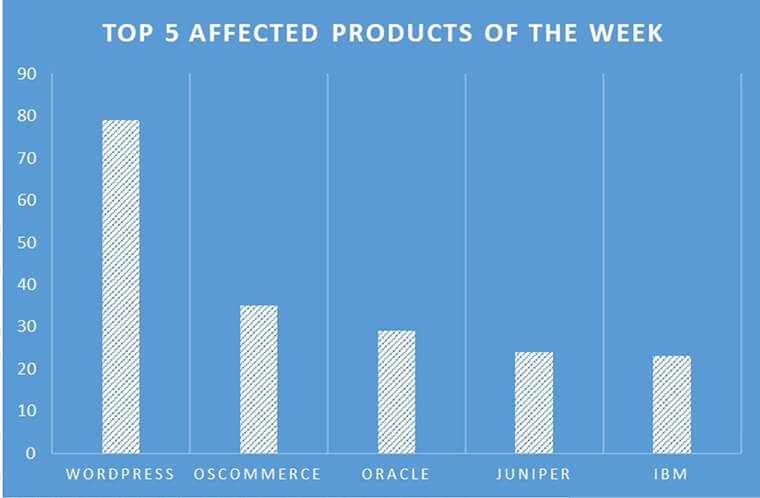
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products due to a range of vulnerabilities. The following are the top 5 most affected products.
Cyber Attacks Target the Websites of the Czech Police, Interior Ministry, and Airport.
Summary:
Relevancy & Insights:
CYFIRMA’s assesses the motivation behind the recent attacks on the Czech Interior Ministry, the police, Prague airport and the increase in other cyber-attacks against Czech institutions. They are mainly attributed to the Czech republic’s on-going support for Ukraine. CYFIRMA has observed similar such attacks against other NATO members, and therefore, we assess the Crimea Platform international summit held in Prague would have served as further encouragement to pro-Russian threat actors.
ETLM Assessment:
CYFIRMA assesses other NATO countries that play host to similar summits are at an increased risk of DDoS attacks from pro-Russian Hacktivists groups.
Toumei Data Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to Toumei,
{www[.]toumei[.]co[.]jp}. Toumei Co Ltd is a company that operates in the telecommunications industry. The data that has been compromised includes usernames, email addresses, and a range of other sensitive information. The overall data size amounts to 8 gigabytes.
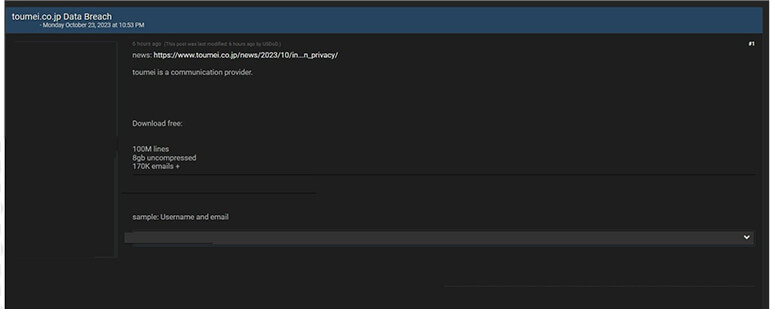
Source: Underground forums
Relevancy & Insights:
Cyber perpetrators motivated by financial gains persistently search for susceptible and
inadequately protected systems and software applications. A significant number of these illicit actors operate within hidden online communities, engaging in discussions related to cybercrime and the illicit trade of pilfered digital assets. Distinguishing themselves from other financially motivated groups such as ransomware or extortion collectives, who often publicize their attacks, these cybercriminals prefer to maintain a low-profile presence. Exploiting unpatched systems or vulnerabilities in software and hardware, they gain unauthorized access and abscond with valuable information. Subsequently, they advertise the stolen data on secretive forums, where it is either resold or repurposed by other malevolent entities for their own unlawful agendas.
ETLM Assessment:
CYFIRMA assess financially motivated cybercriminals consider Japan and other developed economies in Asia a primary target. Therefore, CYFIRMA considers there to be a continual and on-going risk to companies in technologically advanced nations, such as Japan. Telecommunications and other industries will continue to be targeted by financially motivated threat actors.
CYFIRMA Research team observed a potential data leak related to Moodle,
{www[.]moodle[.]com}. Moodle is a learning platform designed to provide educators, administrators, and learners with a single robust, secure, and integrated system to create personalized learning environments. The breached data consists of session details, emails, password hashes, and other confidential information in SQL format, with a total data size of 3 gigabytes.
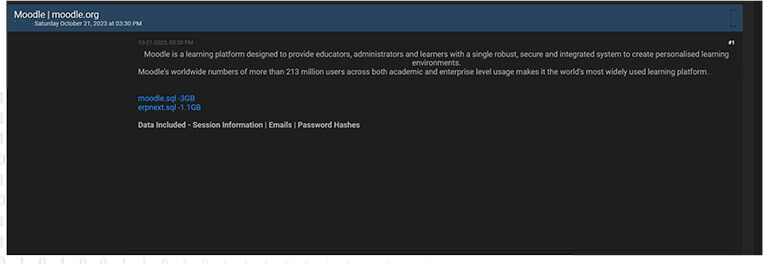
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS