



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Locklocklock Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Locklocklock Ransomware
Researchers recently identified the “Locklocklock ransomware”, which encrypts files on infected systems and appends the extension “.locklocklock” to the filenames. Following encryption, it generates a ransom note titled “Readme-locklocklock.txt.”
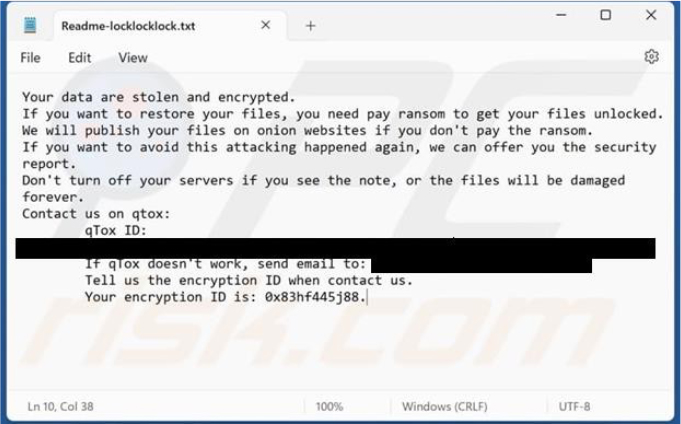
The Locklocklock ransomware ransom note informs victims that their data has been both encrypted and stolen. It demands a ransom payment to restore access to the files, threatening to publish the stolen data on Onion websites if the payment is not made. The note also offers a “security report” claiming to help prevent future attacks.
Victims are warned against shutting down servers while the note is displayed, as this could result in permanent file damage. Additionally, the note provides contact details, including an email address, for communication with the attackers.
Following are the TTPs based on the MITRE Attack Framework
| Tactic | ID | Technique/Sub-Technique |
| Execution | T1053 | Scheduled Task/Job |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1106 | Native API |
| Persistence | T1053 | Scheduled Task/Job |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| PrivilegeEscalation | T1053 | Scheduled Task/Job |
| PrivilegeEscalation | T1055 | Process Injection |
| PrivilegeEscalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| PrivilegeEscalation | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| PrivilegeEscalation | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1548 | Abuse Elevation Control Mechanism |
| DefenseEvasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Defense Evasion | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| CredentialAccess | T1003 | OS Credential Dumping |
| CredentialAccess | T1552.001 | Unsecured Credentials: Credentials In Files |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1087 | Account Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Collection | T1005 | Data from Local System |
| Collection | T1114 | Email Collection |
| Collection | T1115 | Clipboard Data |
| Collection | T1185 | Browser Session Hijacking |
| Collection | T1560 | Archive Collected Data |
| Commandand Control |
T1071 | Application Layer Protocol |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1496 | Resource Hijacking |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment suggests that Locklocklock ransomware is likely to intensify its global operations, with a particular emphasis on high-value sectors such as manufacturing, finance, and healthcare. These industries are appealing due to their reliance on critical data and infrastructure, coupled with the severe impact of operational disruptions. By leveraging advanced evasion techniques, persistent registry modifications, and recovery inhibition strategies, the ransomware is expected to exploit systemic vulnerabilities, maximizing its potential for financial and operational leverage.
Sigma Rule
title: Drops script at startup location threatname:
behaviorgroup: 1
classification: 7
logsource:
service: sysmon product: windows
detection: selection:
EventID: 11 TargetFilename:
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.vbs*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.js*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.jse*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.bat*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.url*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.cmd*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.hta*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.ps1*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.wsf*’
condition: selection
level: critical
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Remote Access Trojan (RAT) | Objectives: Espionage, Data theft| Threat Actor: TA397 | Target Technology: Windows OS | Target Organization: Defense sector | Target Geography: Turkey
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the Week
This week “WmRAT and MiyaRAT” is trending.
Summary
Researchers observed that the advanced persistent threat (APT) group TA397 targeted a Turkish defense organization using a lure related to public infrastructure projects in Madagascar. The attack employed a RAR archive containing an LNK file, which created a scheduled task on the victim’s system to retrieve additional payloads. In the final phase of the attack, TA397 manually delivered the WmRAT and MiyaRAT malware families, both designed for intelligence gathering and exfiltration. Researchers assess that these campaigns are likely focused on supporting the interests of a South Asian government.
TA397
TA397 is a prominent South Asian espionage-focused APT group known for targeting sectors such as government, energy, telecommunications, defense, and engineering across the EMEA and APAC regions. The group primarily uses scheduled tasks to communicate with staging domains and deploy malicious backdoors, allowing them to access sensitive information and intellectual property. Observed activity consistently falls within UTC+5:30 working hours, suggesting a defined operational window. WmRAT and MiyaRAT are two distinct malware families identified as actively used by TA397, with MiyaRAT being a more recent addition. MiyaRAT appears to be reserved for higher-value targets, as it has been deployed less frequently across campaigns. It is believed that both malware families were likely developed by the same developers.
Attack Method
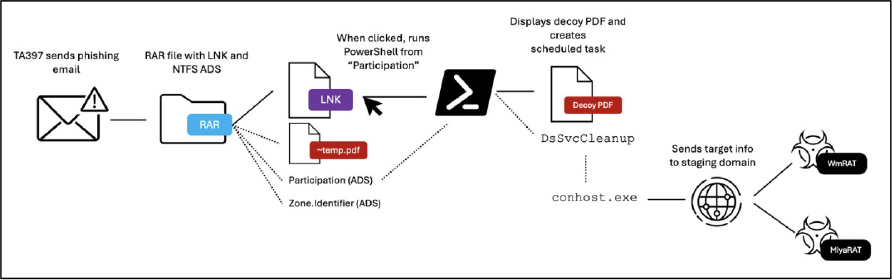
The TA397 campaign begins with attacks using spearphishing emails sent from a compromised government organization’s email account. These emails contained a RAR archive with various files, including an LNK file, a “~tmp.pdf” file, and two NTFS alternate data streams (ADS) named “Participation” and “Zone.Identifier.”
When the RAR file is opened, the target only sees the LNK file because the ADS are hidden by default in Windows’ built-in RAR extraction tool or WinRAR. Additionally, the PDF file has specific attributes (HSA) enabled, which misleads the user into thinking they’re opening a legitimate PDF file, as indicated by the “.pdf.lnk” extension. Since Windows hides the true file extensions by default, this trick is more convincing. However, if the RAR file is opened using 7-Zip, the user can view and extract the hidden NTFS ADS streams.
ADS are a feature of the NTFS file system in Windows, allowing additional data to be attached to files, with formats like RAR v5 supporting the inclusion of ADS streams. In this attack, the Zone.Identifier ADS stream, introduced in earlier Windows versions for security, records the origin of a file to assess its trustworthiness. It is automatically assigned to files downloaded via browsers and, when extracted from downloaded archives using Windows Explorer, the files inherit a Zone.Identifier stream pointing to the original archive’s source. While not critical to the attack’s success, this stream is useful for forensic analysis. In this case, the Zone.Identifier ADS reveals that the “~tmp.pdf” file is a legitimate document from the World Bank about a Madagascar infrastructure project.
The second ADS, called “Participation,” contained a base64-encoded PowerShell script, which was triggered when the LNK file ran, executing the script within the “~tmp.pdf” file. This opened the World Bank PDF lure while creating a scheduled task named “DsSvcCleanup” that attempted to send the target’s host information to the jacknwoods[.]com domain every 17 minutes. If a payload was retrieved, it was executed via a command prompt. Approximately 12 hours later, TA397 operators manually deployed the WmRAT and MiyaRAT payloads, starting with “anvrsa.msi,” which installed WmRAT as “anvrsa.exe.” When WmRAT failed to communicate, additional commands were issued to enumerate the system and exfiltrate data. Then, the “gfxview.msi” payload was executed to install MiyaRAT as “xrgtg.exe.”
WmRAT
WmRAT is a remote access trojan (RAT) written in C++ that utilizes sockets for communication and offers typical RAT features. It can collect basic host information, upload and download files, capture screenshots, obtain geolocation data, enumerate directories and files, and execute commands through cmd or PowerShell. The malware also generates numerous fake threads, likely to confuse researchers or responders analyzing the samples. Upon execution, it begins by copying timezone information using the GetDynamicTimeZoneInformation function and employs the standard method of using the Sleep function at various stages, including a dedicated function designed to trigger extended sleep periods.
The malware creates a thread that gathers basic host information such as username, hostname, and logical drives but does nothing with this data. This process is repeated 1,000 times, likely to overwhelm behavior logs or create noise in the environment. After this, another identical thread is created, continuing the same behavior. The malware then attempts to communicate with its command and control (C2) server, though initially failing due to an uninitialized socket. Later, it successfully initializes the socket and decrypts the C2 server address, academymusica[.]com. Once the C2 server is contacted, the malware checks connectivity by sending a request to microsoft[.]com before establishing a connection on port 47408. The malware receives a 4-byte value from the C2 server, swaps the endianness, and uses this value to determine which command to execute. Some notable supported commands include:
MiyaRAT
MiyaRAT, also written in C++, shares similar functionality with WmRAT. It begins by decrypting its hardcoded C2 server, using a method where it subtracts each character from the string “doobiedoodooziezzz” to decode the C2 domain, resulting in samsnewlooker[.]com. The malware also has a hardcoded port value, 56189, specifying the port it connects to. Uniquely, MiyaRAT implements its own version of the Mersenne Twister random number generator to determine sleep durations. After decoding the C2, MiyaRAT creates a global socket, which is initialized to communicate with the server.
Afterward, the malware gathers basic system information and sends it to the C2 along with the malware version, which is 3. This data is then encrypted using XOR with the byte value 0x43. The C2 can respond to commands that MiyaRAT supports:
TA397 Infrastructure and Domain Usage
TA397’s campaign infrastructure is split between implant and staging domains. The jacknwoods[.]com domain served as the staging domain for distributing WmRAT and MiyaRAT, while academymusica[.]com and samsnewlooker[.]com acted as C2 domains for each implant. The staging domain jacknwoods[.]com resolved to 185.244.151[.]84, registered with a Let’s Encrypt certificate and GoDaddy as the provider, reflecting patterns observed in previous TA397 campaigns. Notably, the IP is multi-tenanted and not controlled by TA397. The WmRAT C2, academymusica[.]com, resolved to 38.180.142[.]228, and the MiyaRAT C2, samsnewlooker[.]com, resolved to 96.9.215[.]155, likely belonging to the attackers.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that malware like WmRAT and MiyaRAT is expected to evolve significantly, with future versions becoming even more sophisticated and harder to detect. As these remote access tools become more advanced, threat actors such as TA397 will likely enhance their cyber espionage tactics, targeting sectors like defense, telecommunications, and energy. With geopolitical tensions increasing, state-sponsored groups are anticipated to launch more targeted and persistent attacks, leveraging malware-laced documents and spearphishing campaigns to compromise organizations. These attacks will seamlessly blend into routine operations, making them difficult to identify and mitigate. As malware continues to advance, employees could inadvertently become the weakest link, with their actions potentially facilitating access to sensitive data and systems. Over time, this could lead to more extensive data breaches, allowing threat actors to exfiltrate intellectual property, government secrets, and proprietary trade information, posing significant risks to both organizational security and national interests.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
Recommendations:
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Lazarus Group Enhances Its Infection Chain with a Combination of New and Existing
Malware
SUMMARY
The Lazarus group has evolved its attack methods, leveraging complex infection chains to target individuals in sensitive sectors such as aerospace, defense, and cryptocurrency, that involves delivering malicious software through fake job opportunities. This attack utilized archive files containing trojanized utilities like VNC software, which were delivered to multiple employees.
The infection process began with a trojanized version of TightVNC, disguised as a legitimate tool, used to prompt the victim to connect to a server. The malicious VNC software decrypted and extracted further malware, including a downloader, which was loaded into memory to facilitate additional attacks. One key malware component, Ranid Downloader, enabled the deployment of more malicious tools, such as MISTPEN and RollMid. MISTPEN was used to fetch additional payloads, some of which included a new Local Privilege Escalation (LPE) client variant.
Throughout the infection, the group employed a variety of techniques, including DLL side-loading and the use of legitimate software, to maintain persistence and evade detection. Another malware, CookieTime, was observed to facilitate lateral movement and the downloading of additional payloads on compromised systems. CookiePlus, a newer downloader, could retrieve DLLs or shellcodes and acted as a modular malware tool, enabling the continuous download of new malicious components from command-and-control servers.
The attack infrastructure mainly consisted of compromised web servers running PHP- based services. The persistent and evolving nature of the malware, especially the introduction of CookiePlus, highlights the group’s ongoing efforts to improve its attack techniques and evade security measures. The modular structure of the malware makes it difficult for defenders to track the full scope of an infection, as new plugins and payloads may be added over time.
Relevancy & Insights:
The Lazarus group’s past attacks, particularly those in the “DeathNote” campaign (also known as “Operation DreamJob”), provide key context for understanding their evolving tactics and techniques. Historically, this group has targeted sensitive sectors such as defense, aerospace, and cryptocurrency through social engineering tactics like fake job offers. These attacks often involved distributing malicious documents or trojanized tools, like remote access utilities (VNC or PuTTY), designed to convince targets to connect to controlled servers for “skills assessments.”
The current attack mirrors these past campaigns, maintaining the focus on social engineering through fake job-related archives. However, there is a significant shift in the methods used. In previous incidents, Lazarus relied heavily on infected documents or PDFs as the primary initial infection vector. This time, they employed compressed ISO files instead of ZIP archives to avoid detection by security systems. Inside these files, Lazarus continued to use trojanized VNC software but combined it with new tools like Ranid Downloader, MISTPEN, and CookieTime to enhance their persistence and payload delivery.
In terms of malware delivery, the group has evolved from using simpler trojans to deploying more sophisticated modular malware frameworks. In the past, Lazarus used tools like Mata and Gopuram Loader for persistent access. The current campaign introduces CookiePlus, a more advanced downloader, which is modular and capable of downloading both DLLs and shellcode, reflecting the group’s shift towards more flexible, persistent infection mechanisms.
The malware flow in the current incident is also more complex, with tools like CookieTime used to facilitate lateral movement across networks, and sophisticated payloads like RollMid and LPEClient delivered after initial access. This complexity demonstrates the group’s increasing sophistication and adaptability in evading detection and maintaining a foothold in targeted organizations, continuing the trend of adapting their methods for greater stealth and persistence seen in past attacks.
ETLM Assessment:
The Lazarus group, a state-sponsored threat actor from North Korea, is known for conducting sophisticated cyberattacks, including espionage, financial theft, and disruption of critical infrastructure. They target global industries, with a focus on defense, aerospace, cryptocurrency, and energy sectors. Their attack methods often involve social engineering, spear-phishing, and exploiting software vulnerabilities to gain access to sensitive systems.
Lazarus has evolved its malware toolkit over time. In recent campaigns, they have used a combination of new and old malware, including Ranid Downloader, MISTPEN, RollMid, CookieTime, and CookiePlus. These tools allow them to maintain persistence, deliver additional payloads, and evade detection. Earlier, they relied on trojanized remote access tools like VNC and PuTTY for infiltration. The group’s attacks target software vulnerabilities and social engineering exploits, such as fake job offers. The infrastructure of the Lazarus group used compromised web servers running WordPress as C2s for most of this campaign. Samples such as MISTPEN, LPEClient, CookiePlus, and RollMid used such servers as their C2. For CookieTime, however, only one of the C2 servers we identified ran a website based on WordPress. Additionally, all the C2 servers seen in this campaign run PHP-based web services not bound to a specific country.
Looking ahead, Lazarus is expected to continue adapting its tactics, focusing on improving malware modularity and stealth. With an ongoing interest in cryptocurrency theft and espionage, they will likely intensify their attacks on financial institutions and critical sectors, making advanced threat detection and proactive security measures essential for organizations in high-value industries.
Recommendations:
Strategic Recommendations:
Tactical Recommendations:
Operational Recommendations:
| MITRE FRAMEWORK | ||
| Tactic | ID | Technique |
| Execution | T1106 | Native API |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Privilege Escalation | T1548 | Abuse Elevation Control Mechanism |
| DefenseEvasion | T1036 | Masquerading |
| DefenseEvasion | T1497 | Virtualization/Sandbox Evasion |
| DefenseEvasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| CredentialAccess | T1056 | Input Capture |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1573 | Encrypted Channel |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
US considers a ban on Chinese-made TP-Link routers after large-scale telecom breach
Amid a year marked by prominent Chinese cyberattacks, the **Salt Typhoon campaign** has emerged as particularly alarming. This operation, attributed to a Chinese government-linked hacking group identified as “Salt Typhoon,” was disclosed in late September. The hackers breached at least eight major U.S. telecommunications networks, including AT&T and Verizon, specifically targeting the cellphones of high-profile government officials and politicians, such as President-elect Donald Trump and Vice President-elect J.D. Vance.
Adding to the concern, U.S. officials revealed that as of December, efforts to fully expel the hackers from most compromised systems remained unsuccessful, with no clear timeline for resolution. The implications extend beyond targeted individuals, with CISA and allied agencies from Australia, New Zealand, and Canada cautioning that the campaign’s scope goes beyond U.S. networks. The hackers have also likely accessed general phone call and text metadata for over a million Americans, signaling a potentially vast and pervasive breach.
ETLM Assessment:
The Biden administration’s response has been limited, including moves to ban Chinese telecom firms and allocate funds to replace Chinese equipment.
However, transitioning to a new administration complicates efforts as the authorities from the US Commerce, Defense, and Justice departments have each opened investigations into whether Chinese-manufactured TP-Link home routers pose a national security risk, and are considering banning the devices in the US. The company holds around 65% of the US market for routers for homes and small businesses, and the routers are used by the Defense Department and other Federal agencies.
CYFIRMA experts emphasize the need for stronger cybersecurity measures as international relations analysts discuss offensive counter-strategies. The incident reflects escalating cyber threats, underscoring vulnerabilities in private-sector-led U.S. cybersecurity defenses and the growing need for a unified, robust response to counter these adversarial provocations.
The Killsec Ransomware Impacts PT Pertamina
Summary
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Indonesia; PT Pertamina(www[.]pertamina[.]com), was compromised by Killsec Ransomware. PT Pertamina (Persero) is Indonesia’s state-owned oil and natural gas corporation, playing a crucial role in the country’s energy sector. The company operates across the entire energy value chain, including exploration, production, refining, and distribution of oil and gas. Pertamina is also actively involved in developing new and renewable energy sources, such as geothermal, solar, and biofuels, to support national energy security and sustainability. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization.
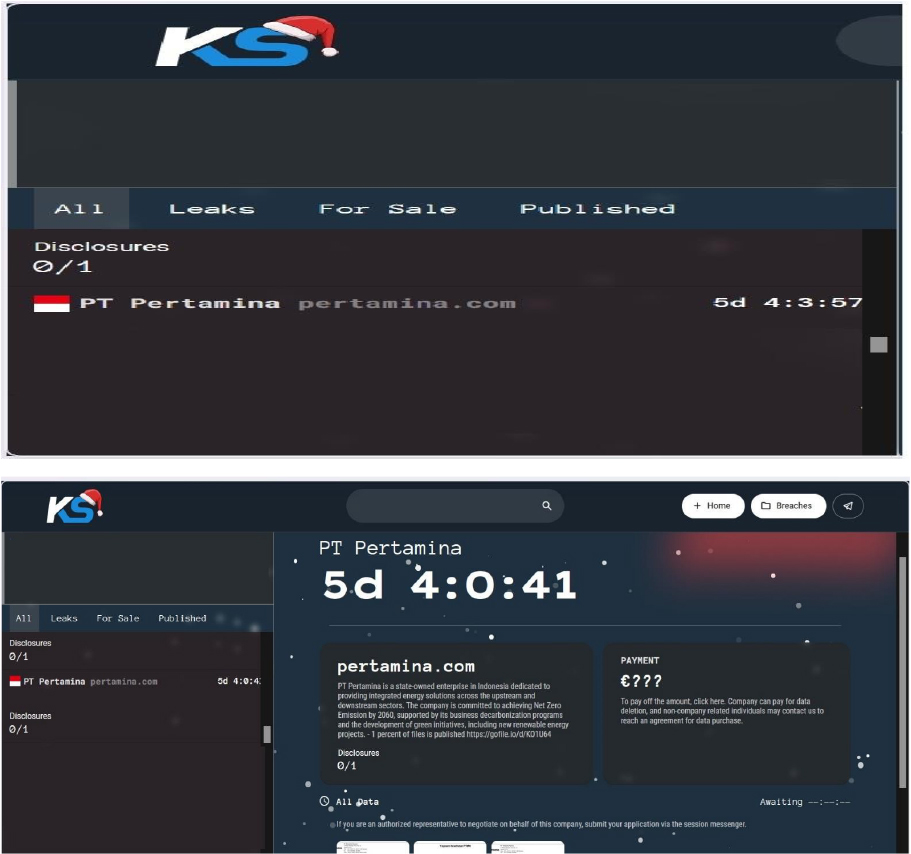
Relevancy & Insights:
ETLM Assessment:
The emergence and evolution of KillSec’s Ransomware-as-a-Service (RaaS) platform represents a concerning development in the cybercrime landscape. By lowering the technical barrier to entry, this RaaS model allows less skilled individuals to engage in sophisticated ransomware attacks, potentially leading to an increase in such incidents globally.
According to CYFIRMA’s assessment, the KillSec ransomware group is expected to continue targeting a wide range of industries worldwide. Their advanced tactics, such as exploiting website vulnerabilities and conducting credential theft, make them a significant threat to organizations with inadequate security measures in place.
The RansomHub Ransomware Impacts Hashem Contracting & Trading Corp
Summary
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Saudi Arabia; Hashem Contracting & Trading Corp (www[.]hashem-contracting[.]com), was compromised by RansomHub Ransomware. Hashem Contracting is a prominent construction and contracting company based in Saudi Arabia. The compromised data consists of confidential and sensitive information related to the organization. The total size of the compromised data is approximately 91GB.
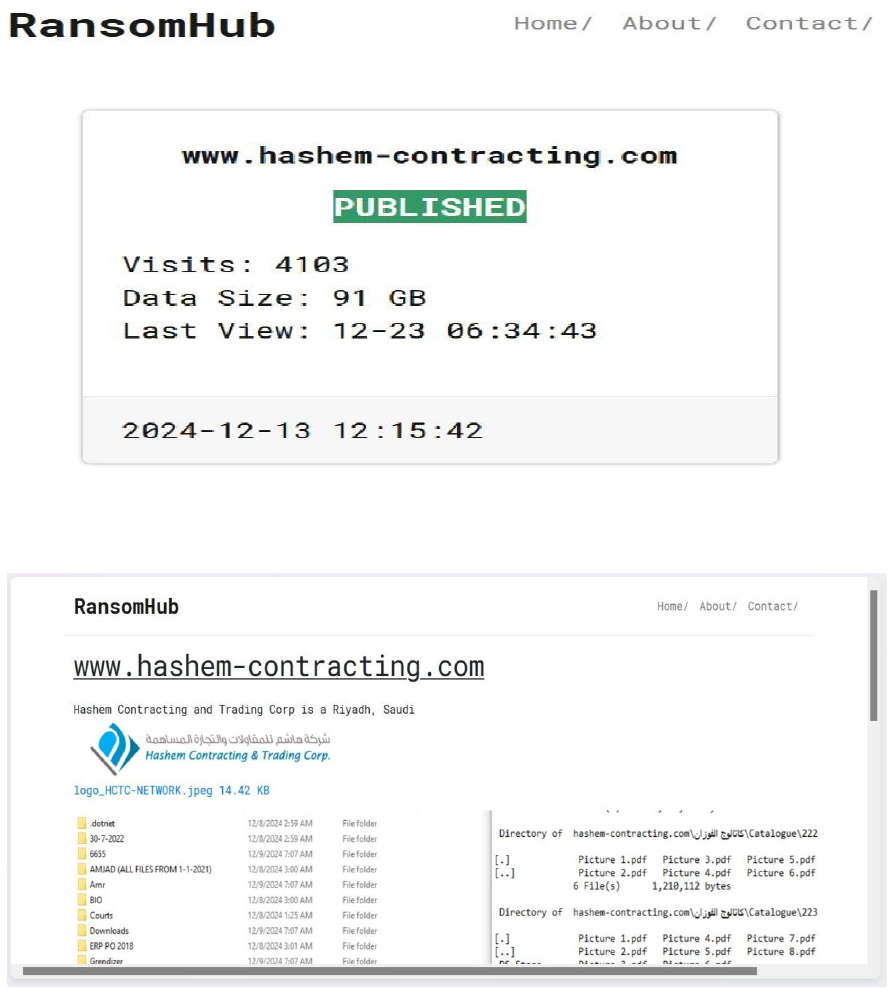
Relevancy & Insights:
ETLM Assessment:
Based on recent assessments by CYFIRMA, RansomHub ransomware is expected to intensify its operations across various industries worldwide, with a notable focus on regions in the United States, Europe, and Asia. This prediction is reinforced by the recent attack on Hashem Contracting & Trading Corp, a prominent Construction company from Saudi Arabia, highlighting RansomHub’s significant threat presence in the Middle East.
Vulnerability in LDAP Account Manager
Relevancy & Insights:
The vulnerability exists due to an input validation error when processing directory traversal sequences in mainmanage.php and confmain.php scripts.
Impact:
A remote user can modify configuration variables, including the log file path, and execute arbitrary PHP code on the system.
Affected Products:
https[:]//github[.]com/LDAPAccountManager/lam/security/advisories/GHSA-6cp9-j5r7- xhcc
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
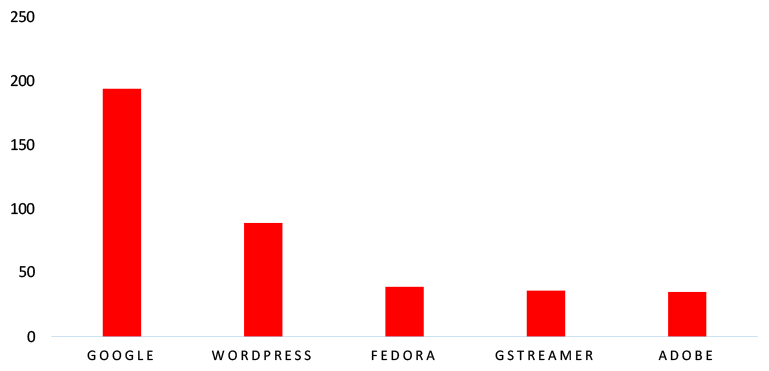
ETLM Assessment
Vulnerability in LDAP Account Manager can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of LDAP Account Manager is crucial for maintaining the integrity and protection of users’ data worldwide.
Therefore, addressing these vulnerabilities is essential to safeguarding account management activities in LDAP directories, providing a user-friendly and abstract view of directory structures, across different geographic regions and sectors.
8Base Ransomware Attacked and Published the Data of the ISEKI and CO., LTD
Summary
Recently, we observed that 8Base Ransomware attacked and published the data of ISEKI and CO., LTD (www[.]iseki[.]co[.]jp) on its dark web website. ISEKI & CO., LTD. is a leading Japanese manufacturer specializing in agricultural machinery, particularly known for its innovations in rice cultivation and other farming equipment. Iseki and Co. contribute to creating a prosperous society by providing products and services that delight customers. The data leak caused by the ransomware attack includes invoices, receipts, accounting records, personal data, certificates, employment contracts, a large volume of confidential information, confidentiality agreements, personal files, and other sensitive documents.

Relevancy & Insights:
ETLM Assessment:
8Base ransomware continues to pose a significant threat to organizations globally, particularly targeting SMBs across various sectors. Its double extortion tactics and sophisticated evasion techniques highlight the need for robust cybersecurity measures. Organizations are advised to implement strong email filtering, conduct regular security training for employees, and maintain updated backups to mitigate risks associated with this evolving threat actor. Continuous monitoring of emerging trends related to 8Base will be essential for effective incident response strategies.
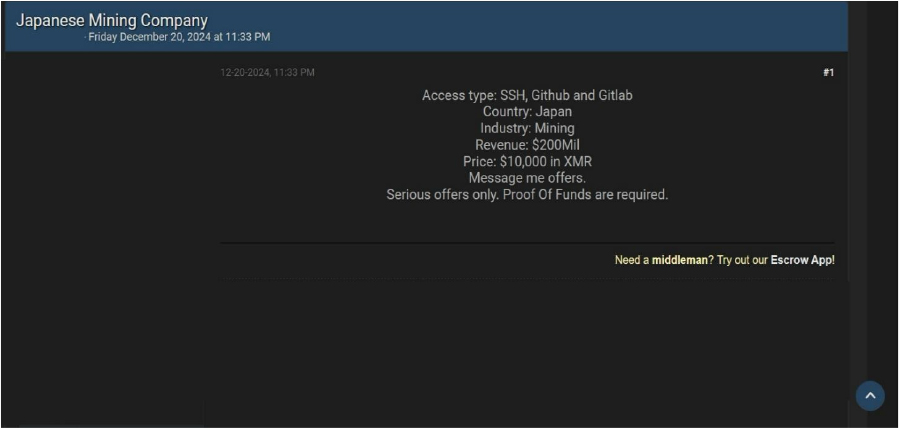
Japanese Mining Company Access Advertised on a Leak Site
Summary
The CYFIRMA Research team discovered an access sale involving a Japanese mining company on an underground forum. The access being sold includes SSH, GitHub, and GitLab credentials, with a listed price of $10,000 in XMR (Monero). The sale has been attributed to a threat actor known as “IntelBroker.”
The Ministry of Finance (MOF) Thailand Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data leak related to the Ministry of Finance (MOF) of Thailand in an underground forum. The Ministry of Finance (MOF) in Thailand is a pivotal cabinet ministry responsible for managing the nation’s public finances, taxation, treasury, government properties, and revenue- generating enterprises. It also oversees government monopolies and provides loan guarantees for governmental agencies, financial institutions, and state enterprises. The compromised data includes sensitive and confidential information related to the Ministry of Finance, available in XLSX, CSV, TXT, ZIP, 7Z, and PDF formats. The total size of the breached data amounts to 5.9 TB. The breach has been linked to a threat actor identified as “Ssuefddub.”
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data.
Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
“IntelBroker” represents a significant threat within the cybersecurity landscape due to its sophisticated tactics and high-profile targets. Organizations are advised to implement robust security measures such as access control, regular patch management, and employee training to mitigate risks associated with such threat actors. Continuous monitoring of emerging threats like IntelBroker will be essential for effective incident response strategies in the evolving cyber threat environment.
Recommendations: Enhance the cybersecurity posture by:
The CYFIRMA Research team observed a data leak related to 6ixpensary (https[:]//6ixpensary[.]io) in an underground forum. 6ixpensary is an online cannabis dispensary based in Toronto, Ontario, Canada. The platform specializes in the sale of various cannabis products, catering to both recreational and medicinal users.
The compromised data consists of an ID, username, email address, first name, last name, registration date, user nice name, display name, nickname, user role, hashed password, and activation key. The breach has been linked to a threat actor identified as “888.”
ETLM Assessment
The threat actor group “888” has gained notoriety in underground forums, emerging as a significant force in cybercrime, primarily motivated by financial gains. This group has already targeted a wide range of industries, including government, industrial conglomerates, retail, staffing, business consulting, banking, e-commerce, and utilities. Their diverse targeting patterns suggest that they plan to broaden their scope and potentially expand their attacks to additional industries worldwide in the future.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
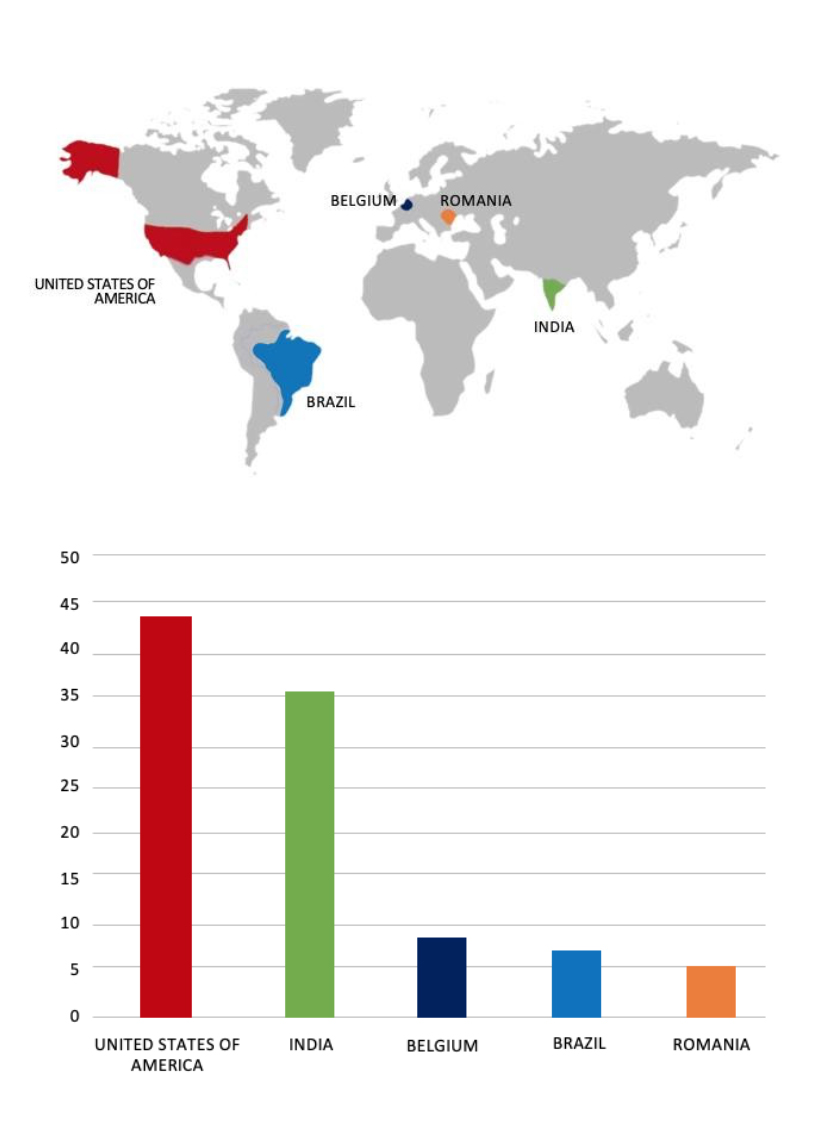
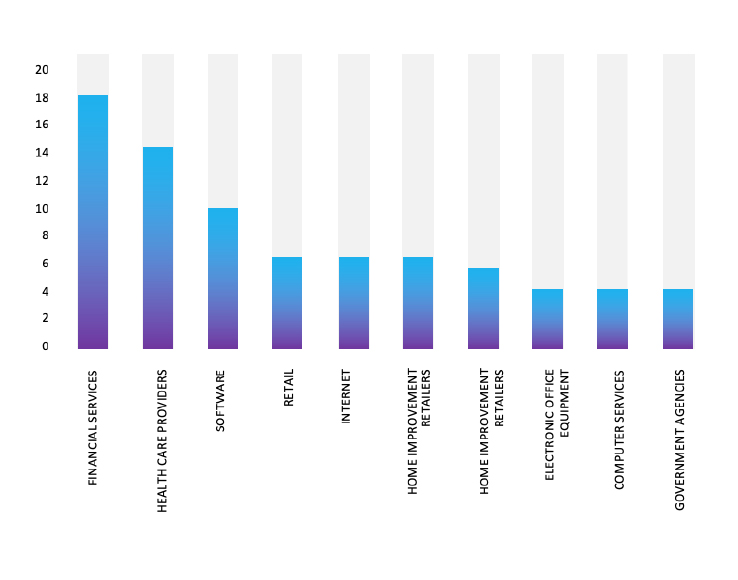
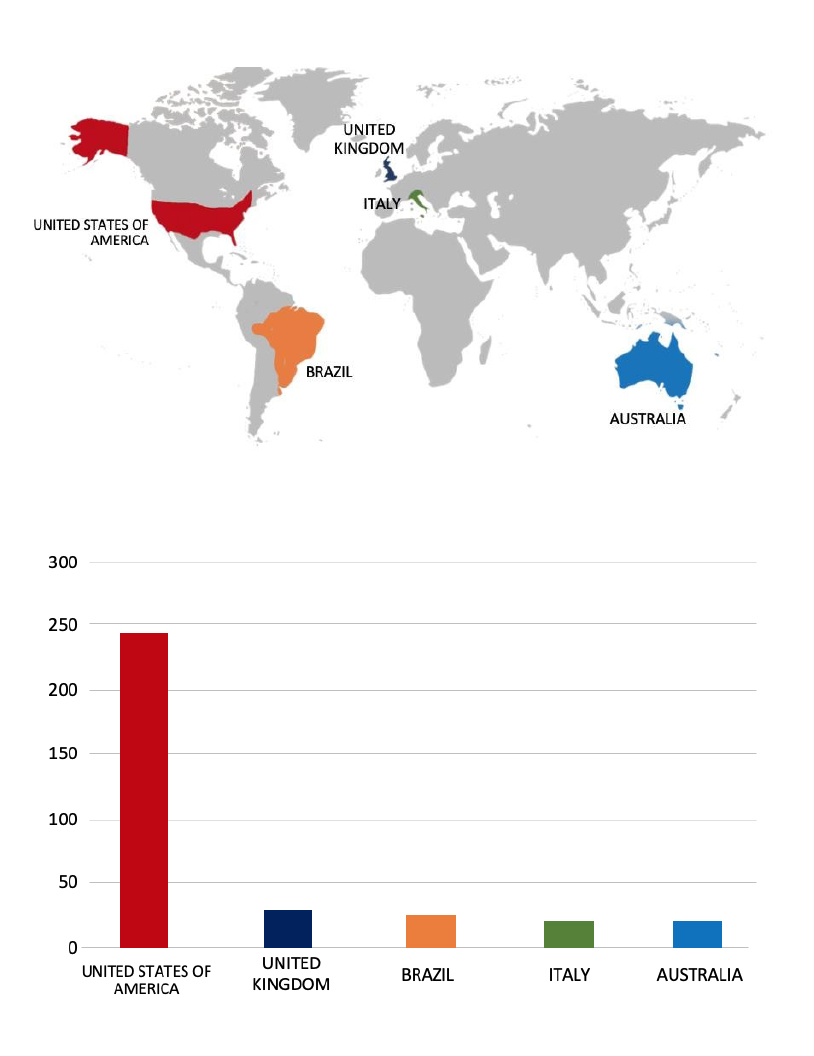
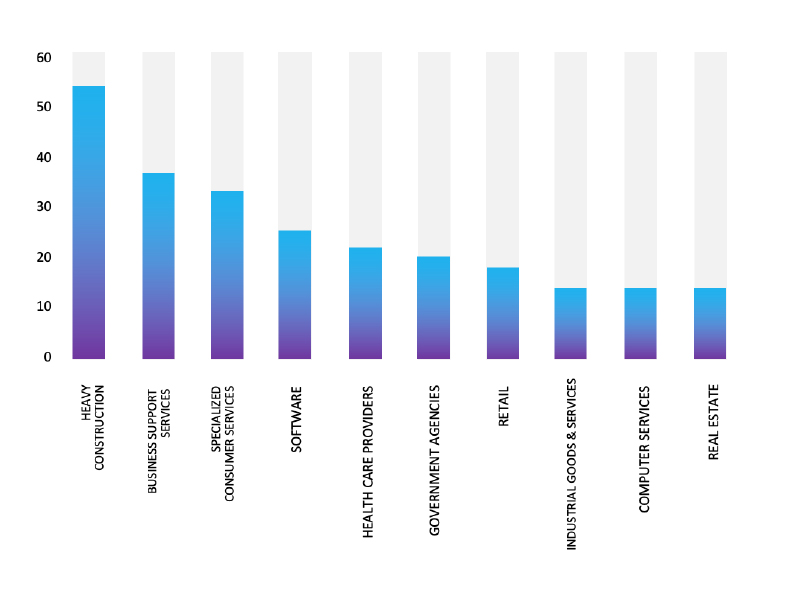
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.