



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Target Industries: Accounting, Advertising & Marketing, Aerospace, Agriculture, Airlines, Apparel Retailers, Automobiles, Banks, Basic Resources, Business Services, Chemicals, Computer Services, Construction, Defense, Delivery Services, Electronic Equipment, Energy, Farming, Fishing & Plantations, Finance, Food & Beverage, Furniture, Government, Health Care, Hospitality, Industrial Goods & Services, Law, Manufacturing, Real Estate, Recreational Services, Retail, Semiconductors, Software, Specialized Consumer Services, Telecommunications, Transportation, Trucking and Utilities.
Target Geography: Australia, Canada, Czech Republic, Finland, France, Germany, Italy, Luxembourg, Mexico, Netherlands, Norway, Poland, Slovakia, South Africa, South Korea, Spain, Sweden, Switzerland, United Kingdom, United States.
Introduction
CYFIRMA Research and Advisory Team has found a Play Ransomware in the wild while monitoring various underground forums as part of our Threat Discovery Process.
Play
Play, also known as PlayCrypt, emerged as a ransomware threat in June 2022.
The Play ransomware group is thought to function as a closed unit, aiming to guarantee transaction confidentiality, as mentioned on their data leak website. Actors linked to Play ransomware follow a double-extortion approach, encrypting systems only after extracting data. The ransom notes from the group lack initial ransom demands or payment instructions; instead, victims are prompted to contact the threat actors via email.
To gain initial access to victim networks, the Play ransomware group exploits valid accounts and vulnerabilities in public-facing applications. They specifically target known vulnerabilities in FortiOS (CVE-2018-13379 and CVE-2020-12812) and Microsoft Exchange (CVE2022-41040 and CVE-2022-41082). Threat actors also use external facing services like Remote Desktop Protocol (RDP) and Virtual Private Networks (VPN).
The group uses tools such as AdFind for Active Directory queries and Grixba to check for a list of security files and processes. Additionally, they employ tools like GMER, IOBit, and PowerTool to disable anti-virus software and erase log files. In certain instances, Play ransomware actors are observed using PowerShell scripts to target Microsoft Defender.
For lateral movement and file execution, the threat actors leverage command and control (C2) applications like Cobalt Strike and SystemBC, along with tools like PsExec. Once inside a network, they actively search for unsecured credentials and use the Mimikatz credential dumper to gain domain administrator access. To identify additional privilege escalation paths, the group uses Windows Privilege Escalation Awesome Scripts (WinPEAS) and distributes executables through Group Policy Objects.
Compromised data is segmented, compressed using tools like WinRAR, and transferred via WinSCP to actor-controlled accounts. The files undergo encryption using AES-RSA hybrid encryption, with intermittent encryption applied to every other file portion of 0x100000 bytes. Notably, system files are exempt from this encryption process. Encrypted files receive a .play extension, and a ransom note named ReadMe.txt is dropped.
In the event of a refusal to pay the ransom, the actors threaten to publish exfiltrated data on their leak site accessible through the Tor network with an [.]onion URL. Victims are instructed to contact the Play ransomware group via an email address ending in @gmx[.]de, and ransom payments are expected in cryptocurrency to wallet addresses provided by the actors.
Tools Leveraged by Play Ransomware Actors
| Tool Name | Description |
| Mimikatz | Allows users to view and save authentication credentials such as Kerberos tickets. Play Threat actors have used it to add accounts to domain controllers. |
| WinPEAS | Used to search for additional privilege escalation paths. |
| WinRAR | Used to split compromised data into segments and to compress files into .RAR format for exfiltration. |
| WinSCP | Windows Secure Copy is a free and open-source Secure Shell (SSH) File Transfer Protocol, File Transfer Protocol, WebDAV, Amazon S3, and secure copy protocol client. Play ransomware actors have used it to transfer data from a compromised network to actor- controlled accounts. |
| Microsoft Nltest | Used by Play ransomware actors for network discovery. |
| Nekto | Used by Play ransomware actors for privilege |
| PriviCMD | escalation. |
| Process Hacker | Used to enumerate running processes on a system. |
| Plink | Used to establish persistent SSH tunnels. |
| AdFind | Used to query and retrieve information from Active Directory. |
| GMER | A software tool intended to be used for detecting and removing rootkits |
| IOBit | An anti-malware and anti-virus program for the Microsoft Windows operating system. Play have accessed IOBit to disable anti-virus software. |
| PsExec | A tool designed to run programs and execute commands on remote systems. |
| PowerTool | A Windows utility designed to improve speed, remove bloatware, protect privacy, and eliminate data collection, among other things. |
| PowerShell | A cross-platform task automation solution made up of a command-line shell, a scripting language, and a configuration management framework, which runs on Windows, Linux, and macOS. |
| Cobalt Strike | A penetration testing tool used by security professionals to test the security of networks and systems. Play ransomware actors have used it to assist with lateral movement and file execution. |
The PLAY ransomware has adopted a ransomware-as-a-service (RaaS) model recently, opening access to a broader spectrum of users, ranging from proficient hackers to less experienced cyber criminals.

Screenshot of files encrypted by Play Ransomware (source: surface web)

Fig: The ransom note of Play ransomware. (Source: Surface Web)
Recent observations:
Researchers have observed Play ransomware targeting ESXi environments for the first time in the evolving ransomware threat landscape.
Businesses commonly use ESXi environments to run multiple virtual machines (VMs). They often host critical applications and data and typically include integrated backup solutions.
Compromising these environments can significantly disrupt business operations and even encrypt backups, further reducing the victim’s capability to recover data.
The submitted sample of Play ransomware to the OSINT platforms indicates that it has successfully evaded security detections.
By the researchers analysis it is found that the Linux variant is compressed in a RAR file along with its Windows variant and is hosted at the URL, hxxp://108.[BLOCKED].190/FX300.rar.

The infection chain of the Linux variant of Play ransomware includes the use of several tools. (Source: SurfaceWeb)
The above figure illustrates the infection chain of this Play ransomware variant. The command-and-control (C&C) server hosts the common tools used in current Play ransomware attacks. This suggests that the Linux variant might utilize similar tactics, techniques, and procedures (TTPs).
Infection Routine of the Linux Variant of Play Ransomware
Similar to its Windows, the sample accepts command-line arguments, although their specific behaviours remain unknown.

Source: SurfaceWeb
The command-line arguments of the Windows and Linux variants of Play ransomware include commands for encrypting drives, files, and network shared resources.
The sample executes ESXi-related commands to verify it is operating in an ESXi environment before initiating its malicious routines. If it is not in an ESXi environment, the sample will terminate and delete itself. Once confirmed, a series of shell script commands are executed.
The following command, in particular, is responsible for scanning and powering off all VMs within the environment:
/bin/sh -c “for vmid in $(vim-cmd vmsvc/getallvms | grep -v Vmid | awk ‘{print $1}’); do vim- cmd vmsvc/power.off $vmid; done”
This command is responsible for setting a custom welcome message on the ESXi host:
/bin/sh -c “esxcli system welcomemsg set -m=\”
Upon executing the series of ESXi-related commands, the ransomware proceeds to encrypt various VM files, including VM disk, configuration, and metadata files. The VM disk file, in particular, contains crucial data such as applications and user data.

List of extensions to be encrypted (Source: SurfaceWeb)
Upon completion of the encryption process, the majority of files within the guest operating system, such as “ubuntu,” have their filenames appended with the extension “.PLAY.”

Files encrypted by the ransomware having the .PLAY extension. (Source:SurfaceWeb)
It will also place a ransom note in the root directory and display it on the ESXi client login portal.

The ransom note named PLAY_Readme.txt. (Source:SurfaceWeb)

The login portal of the affected ESXi server also displays the ransom note. (Source:SurfaceWeb)
Upon rebooting the ESXi system, the ransom note will also be displayed on the console as in below figure.

(Source:SurfaceWeb)
Uncovering the Link Between Prolific Puma and Play Ransomware
Researchers monitoring external activities linked to a suspicious IP address revealed that the URL used to host the ransomware payload and its tools is associated with another threat actor known as Prolific Puma.
Prolific Puma’s Activities
Prolific Puma is recognized for generating domain names using a random destination generator algorithm (RDGA). They offer a link-shortening service to other cybercriminals, enabling them to avoid detection while disseminating phishing schemes, scams, and malware.

Table 1: The different tools of Play ransomware resolve to several IP addresses. (Source: SurfaceWeb)

Table 2: The IP addresses hosting the Play ransomware resolves to different domains. (Source: SurfaceWeb)
Tables 1 and 2 illustrate the domains, especially DGAs, that resolve to the IP address associated with the Play ransomware toolkit. These domains are registered under various registrars. Our research shows that Prolific Puma typically uses three to four random characters in their registered domains. The domains listed in the tables match those associated with the IP address linked to Play ransomware.

Prolific Puma uses numerous registered domains. (Source: SurfaceWeb)

A shortened link generated by Prolific Puma matches the observed IP address linked to Play ransomware. (Source: SurfaceWeb)
To further confirm the connection between the two groups, researchers tested the Coroxy backdoor hosted at the same IP address. Black-box analysis revealed that the Coroxy backdoor connected to IP address 45[.]76[.]165[.]129, which also resolves to multiple domains linked to Prolific Puma.

The Coroxy backdoor employed by Play ransomware has been detected establishing a connection to the specified IP address. (Source: SurfaceWeb)

Different domains resolve to the IP address of the Coroxy backdoor connection. (Source: SurfaceWeb)
The IP address to which the Coroxy backdoor connects also resolves to various domains that match the registered domains of Prolific Puma. Upon further examination, the IP address includes “vultrusercontent.com,” aligning with the original IP. As shown in below picture.

A Shodan query of the IP address hosting Play ransomware reveals some details on its associated infrastructure. (Source: SurfaceWeb)
A comparison between the IP address hosting Play ransomware and another IP address linked to Prolific Puma reveals that both share the same autonomous system number (ASN). This indicates they are part of the same network and are managed by the same provider.

The IP address hosting the ransomware (left) and the IP address linked to Prolific Puma (right) exhibit similarities. (Source: SurfaceWeb)
Prolific Puma carefully selects its clients, preferring those deemed worthy of its services. The established reputation of the Play ransomware threat actors makes them likely candidates for Prolific Puma’s offerings. This suggests a potential collaboration between the two cybercriminal entities, with Play ransomware possibly seeking to improve its ability to bypass security measures through Prolific Puma’s services.

Countries targeted by Play Ransomware.
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0001: Initial Access | T1091: Replication Through Removable Media |
| T1190: Exploit Public-Facing Application | ||
| 2 | TA0002: Execution | T1059.004: Command and Scripting Interpreter: Unix Shell |
| T1129: Shared Modules | ||
| 3 | TA0003: Persistence | T1574.002: Hijack Execution Flow: DLL Side-Loading |
| 4 | TA0004: Privilege Escalation | T1055: Process Injection |
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 5 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1027.005: Obfuscated Files or Information: Indicator Removal from Tools | ||
| T1055: Process Injection | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 6 | TA0006: Credential Access | T1003: OS Credential Dumping |
| T1056: Input Capture | ||
| 7 | TA0007: Discovery | T1046: Network Service Discovery |
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1120: Peripheral Device Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 8 | TA0008: Lateral Movement | T1091: Replication Through Removable Media |
| T1570: Lateral Tool Transfer | ||
| 9 | TA0009: Collection | T1005: Data from Local System |
| T1056: Input Capture | ||
| 10 | TA0011: Command and Control | T1568.002: Dynamic Resolution: Domain Generation Algorithms |
| T1105: Ingress Tool Transfer | ||
| 11 | TA0040: Impact | T1486: Data Encrypted for Impact |
| T1489: Service Stop | ||
| T1491.001: Defacement: Internal Defacement |
Relevancy and Insights:
ETLM Assessment:
Based on available information, CYFIRMA’s assessment suggests that Play ransomware is set to become more aggressive, by targeting industries such as Finance, manufacturing, IT, and telecommunications sectors. Recent attacks show a strategic focus on industries with high-value data and critical operations, increasing the risk for Financial Institutions, Manufacturing, IT firms, and Telecom providers.
Additionally, Play ransomware is likely to expand its geographical reach, targeting previously overlooked regions such as East Asia, South East Asia etc. This is driven by the group’s evolving tactics, making it a significant threat globally. As Play ransomware continues to adapt, organizations worldwide must enhance their cybersecurity defenses to counter this growing and sophisticated threat.
Yara Rule
rule win_play_auto { strings:
$sequence_0 = { 0fb78d82feffff 2bc8 899570ffffff 014d84 }
// n = 4, score = 100
// 0fb78d82feffff | movzx ecx, word ptr [ebp – 0x17e]
// 2bc8 | sub ecx, eax
// 899570ffffff | mov dword ptr [ebp – 0x90], edx
// 014d84 | add dword ptr [ebp – 0x7c], ecx
$sequence_1 = { 02c1 c645c5ae 8845c3 b937030000 888556ffffff 8a45c7 c6852fffffff00 }
// n = 7, score = 100
// 02c1 | add al, cl
// c645c5ae | mov byte ptr [ebp – 0x3b], 0xae
// 8845c3 | mov byte ptr [ebp – 0x3d], al
// b937030000 | mov ecx, 0x337
// 888556ffffff | mov byte ptr [ebp – 0xaa], al
// 8a45c7 | mov al, byte ptr [ebp – 0x39]
// c6852fffffff00 | mov byte ptr [ebp – 0xd1], 0
$sequence_2 = { 8bd8 899d88fdffff 85db 0f8483040000 8a0b 80f9e9 7409 }
// n = 7, score = 100
// 8bd8 | mov ebx, eax
// 899d88fdffff | mov dword ptr [ebp – 0x278], ebx
// 85db | test ebx, ebx
// 0f8483040000 | je 0x489
// 8a0b | mov cl, byte ptr [ebx]
// 80f9e9 | cmp cl, 0xe9
// 7409 | je 0xb
$sequence_3 = { c83dad3c d92b e00c 9c 0d05f0657b 4e f30f7e05???????? }
// n = 7, score = 100
// c83dad3c | enter -0x52c3, 0x3c
// d92b | fldcw word ptr [ebx]
// e00c | loopne 0xe
// 9c | pushfd
// 0d05f0657b | or eax, 0x7b65f005
// 4e | dec esi
// f30f7e05???????? |
$sequence_4 = { 7f06 81c4ab000000 83c410 e8???????? 66f1 }
// n = 5, score = 100
// 7f06 | jg 8
// 81c4ab000000 | add esp, 0xab
// 83c410 | add esp, 0x10
// e8???????? |
// 66f1 | int1
$sequence_5 = { a1???????? 8945bc a1???????? 0f11855cffffff 894594 f30f7e05???????? 8b45f8 }
// n = 7, score = 100
// a1???????? |
// 8945bc | mov dword ptr [ebp – 0x44], eax
// a1???????? |
// 0f11855cffffff | movups xmmword ptr [ebp – 0xa4], xmm0
// 894594 | mov dword ptr [ebp – 0x6c], eax
// f30f7e05???????? |
// 8b45f8 | mov eax, dword ptr [ebp – 8]
$sequence_6 = { 91 ae 54 ce 3106 f77cf30f 7e05 }
// n = 7, score = 100
// 91 | xchg eax, ecx
// ae | scasb al, byte ptr es:[edi]
// 54 | push esp
// ce | into
// 3106 | xor dword ptr [esi], eax
// f77cf30f | idiv dword ptr [ebx + esi*8 + 0xf]
// 7e05 | jle 7
$sequence_7 = { 8955f4 8b460c 83ec08 8d0488 8945f8 8d45f4 }
// n = 6, score = 100
// 8955f4 | mov dword ptr [ebp – 0xc], edx
// 8b460c | mov eax, dword ptr [esi + 0xc]
// 83ec08 | sub esp, 8
// 8d0488 | lea eax, [eax + ecx*4]
// 8945f8 | mov dword ptr [ebp – 8], eax
// 8d45f4 | lea eax, [ebp – 0xc]
$sequence_8 = { 898d48fdffff 66898562fdffff 668985e6fcffff 66398d30fdffff 7634 66ff857cfcffff 8d0432 }
// n = 7, score = 100
// 898d48fdffff | mov dword ptr [ebp – 0x2b8], ecx
// 66898562fdffff | mov word ptr [ebp – 0x29e], ax
// 668985e6fcffff | mov word ptr [ebp – 0x31a], ax
// 66398d30fdffff | cmp word ptr [ebp – 0x2d0], cx
// 7634 | jbe 0x36
// 66ff857cfcffff | inc word ptr [ebp – 0x384]
// 8d0432 | lea eax, [edx + esi]
$sequence_9 = { 88852effffff 8b8548ffffff fec8 8855ad 88854dffffff 8d45e8 6689bd0cfeffff }
// n = 7, score = 100
// 88852effffff
// 8b8548ffffff
// fec8
// 8855ad
// 88854dffffff | mov
| mov
| dec
| mov
| mov
al byte ptr [ebp – 0xd2], al eax, dword ptr [ebp – 0xb8]
byte ptr [ebp – 0x53], dl byte ptr [ebp – 0xb3], al
// 8d45e8 | lea eax, [ebp – 0x18]
// 6689bd0cfeffff | mov word ptr [ebp – 0x1f4], di
condition:
7 of them and filesize < 389120
}
(Source: Surface web)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Information Stealer
Objective: Stealing sensitive information, Data exfiltration
Threat Actor: Void Banshee
Target Technologies: Windows OS, Browsers, Discord, Telegram, Steam, Crypto wallets, FileZilla
Target Geographies: North America, Europe, and Southeast Asia Exploited Vulnerability: CVE-2024-38112
Active Malware of the Week
This week “Atlantida” is trending
Summary
Void Banshee, an advanced persistent threat (APT) group, is exploiting a recently disclosed zero-day vulnerability CVE-2024-38112 (ZDI-CAN-24433) in the Microsoft MHTML browser engine to deploy an information stealer known as Atlantida. This zero-day vulnerability allows file access and execution via the disabled Internet Explorer using MSHTML. Void Banshee uses this exploit to infect machines with the Atlantida info-stealer, which targets system information and sensitive data like passwords and cookies from various applications. They lure victims with malicious zip archives disguised as book PDFs, distributed through cloud-sharing websites, Discord servers, and online libraries. Their attacks are primarily focused on North America, Europe, and Southeast Asia regions for information theft and financial gain.
Atlantida
Atlantida Stealer is an info-stealer malware with extensive capabilities, built from the open- source stealers NecroStealer and PredatorTheStealer. It targets sensitive information from various applications, including Telegram, Steam, FileZilla, various cryptocurrency wallets, and web browsers. This malware focuses on extracting stored sensitive and potentially valuable data, such as passwords and cookies, and can also collect files with specific extensions from the infected system’s desktop. Additionally, the malware captures the victim’s screen and gathers comprehensive system information. The stolen data is then compressed into a ZIP file and transmitted to the attacker via TCP.
Attack Method
The threat actor exploited CVE-2024-38112 to run malicious code by exploiting the MHTML protocol handler and x-usc directives within internet shortcut (URL) files. This method enabled them to access and execute files directly via the disabled Internet Explorer on Windows machines. The MHTML code execution vulnerability was utilized to infect users and organizations with Atlantida malware.
Internet Explorer used as an attack vector
Internet Explorer (IE) officially ended support on June 15, 2022, and has been disabled in later versions of Windows 10 and all versions of Windows 11. However, IE remnants still exist on modern Windows systems, though they are inaccessible to average users.
Attempting to open IE (iexplore.exe) instead launches Microsoft Edge. For those needing IE-specific functionality, Microsoft provides IE mode in Edge, operating within Edge’s sandbox for enhanced security. In this campaign, researchers discovered samples exploiting CVE-2024-38112. These samples could run files and websites through the disabled IE process by exploiting MSHTML. Using specially crafted .URL files containing the MHTML protocol handler and the x-usc directive, the APT group Void Banshee accessed and executed HTML Application (HTA) files through the disabled IE process.

Fig: Attack chain of the CVE-2024-38112 zero-day campaign (Source: Surface web)
Technical Analysis
Void Banshee used zip archives containing copies of book PDFs and malicious files disguised as PDFs in spearphishing links on online libraries, cloud-sharing sites, Discord, and compromised websites. Their PDF lures included textbooks and reference materials like “Clinical Anatomy,” indicating a focus on targeting highly skilled professionals and students. To exploit CVE-2024-38112, Void Banshee changed the default icon of an internet shortcut file to resemble a PDF, enticing victims to execute it.
Stage 1: Malicious internet shortcut (URL) file
The zero-day attack starts when the victim opens a URL shortcut file designed to exploit CVE-2024-38112. Researchers found a sample named “Books_A0UJKO.pdf.url,” which appears as a PDF book copy. The URL shortcut leverages the MHTML protocol handler and the x-usc! directive via the URL parameter. This exploit is similar to CVE-2021-40444, demonstrating the ongoing misuse of Windows protocol handlers. In this attack, CVE-2024- 38112 redirects victims by using the system-disabled IE to open a compromised website hosting a malicious HTML Application (HTA). Void Banshee crafted the URL string to open the target in Internet Explorer through the iexplore.exe process.
Stage 2: HTML file downloader
The internet shortcut file exploiting CVE-2024-38112 directs to an attacker-controlled domain where an HTML file initiates the HTA stage of the infection chain. This HTML file is crafted to control the window size of Internet Explorer, conceal browser information, and mask the download of the next infection stage. Void Banshee designed the HTML file to manipulate IE’s window size, making it less noticeable. When the URL is accessed via IE, it prompts the user to open or save the HTML application. This behavior is specific to IE, as HTA files are opened by default, unlike modern browsers. The attacker disguises the malicious HTA file by adding 26 spaces to its extension in “Books_A0UJKO.pdf.hta,” making it appear as a PDF file to the user.
Stage 3: HTA file and VBS downloader
The HTA file includes a Visual Basic Script (VBScript) that decrypts XOR-encrypted content with key 4 and then executes it via PowerShell. The script downloads an additional script from a compromised server using PowerShell commands (`irm` for Invoke- RestMethod and `iex` for Invoke-Expression) and creates a new process for this script using the Win32_Process WMI class.
Stage 4: PowerShell trojan downloader
The script first imports two functions: `GetConsoleWindow` from kernel32.dll to retrieve the console window handle and `ShowWindow` from user32.dll to set the window’s visibility. It uses the `Add-Type` cmdlet to define a type in the current PowerShell session. The script then retrieves and hides the console window using `GetConsoleWindow` and `ShowWindow` with a parameter of 0. This is a common technique for malware to operate without displaying a user interface. Next, the script creates a `System.Net.WebClient` object to download data from a malicious server. This data is loaded as a .NET assembly using `System.Reflection.Assembly.Load`, and the script executes the assembly’s entry point, running the code it contains.
Stage 5: .NET trojan loader
LoadToBadXml is a .NET Trojan loader obfuscated with Eziriz .NET Reactor. It decrypts XOR-encrypted payloads using a byte array key (3, 2, 2) and injects them into `C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe` using a common process injection technique. The process involves:
LoadToBadXml is a modified version of the shellcode injector from the Donut Loader open- source project.
Stage 6: Donut loader
Donut is an open-source, position-independent code that allows in-memory execution of VBScript, JScript, EXE, DLL files, and .NET assemblies. In this attack, Donut is used to decrypt and execute the Atlantida stealer within the memory of the `RegAsm.exe` process.
Stage 7: Atlantida stealer analysis
Upon execution, the malware initializes a ZIP file and sets up structures for writing files. It retrieves the “APPDATA” and “DESKTOP” paths using the SHGetFolderPathA API and stores them in a global variable. The malware takes a screenshot, saves it as “screenshot.jpeg,” and adds it to the ZIP archive.
To gather geolocation information, such as IP address, country, and zip code, it contacts its command-and-control (C&C) server over port 6666, storing this data in “Geo Information.txt” and appending it to the ZIP. It also collects system information like RAM, GPU, CPU, and screen resolution, saving it in “User Information.txt” and appending it to the ZIP archive.
The malware extracts credentials and sensitive files from various applications:
Finally, the malware compresses all collected data into a ZIP file and exfiltrates it to the attacker’s C&C server over TCP port 6655.

Fig: Example of Atlantida stealer’s collected data
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that as cyber threats continue to advance, the exploitation of legacy systems and outdated software, like Internet Explorer, will likely become more prevalent. This trend highlights a growing need for organizations to maintain comprehensive and up-to-date security measures that address not only current but also deprecated technologies. The successful use of CVE-2024-38112 and similar vulnerabilities in sophisticated attacks underscores the potential for increased targeting of such weaknesses in the future. Organizations can expect more targeted phishing campaigns and data breaches as attackers refine their tactics to exploit overlooked system components. To mitigate these risks, businesses must prioritize regular system updates, continuous vulnerability assessments, and robust employee training programs. Additionally, as attackers become more adept at using old technology as attack vectors, organizations will need to adopt a proactive approach to cybersecurity, ensuring that all potential entry points are secured against evolving threats.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
APT41: The Persistent Threat Behind Prolonged Cyber Espionage and Data Exfiltration
Summary:
APT41, an advanced persistent threat group with ties to Chinese state-sponsored espionage, has been actively conducting a prolonged and sophisticated cyber campaign targeting multiple industries across various regions. Known for their unique approach of utilizing non-public malware for both espionage and personal gain, APT41 has compromised organizations in the global shipping and logistics, media and entertainment, technology, and automotive sectors. The majority of these targeted entities are based in Italy, Spain, Taiwan, Thailand, Turkey, and the United Kingdom, reflecting the group’s broad geographical reach.
The initial phase of APT41’s attack involved deploying ANTSWORD and BLUEBEAM web shells to infiltrate systems and deliver the DUSTPAN dropper. This dropper executed the BEACON backdoor, establishing command-and-control communication with APT41’s infrastructure. This foothold allowed them to gain initial access and begin their operations. As they deepened their intrusion, APT41 escalated their tactics by deploying the DUSTTRAP dropper, which decrypted and executed malicious payloads in memory, leaving minimal forensic traces. They also engaged in hands-on keyboard activity, demonstrating their capability for direct and active manipulation of compromised systems.
To further their objectives, APT41 employed publicly available tools such as SQLULDR2 to extract data from databases and PINEGROVE to exfiltrate this data to Microsoft OneDrive. These tools enabled them to systematically export large volumes of sensitive information from the compromised networks, maintaining their presence and ensuring continuous data extraction.
APT41 has been infiltrating and maintaining unauthorized access to numerous networks since 2023, primarily for data extraction and espionage. Their activities highlight the significant resources and capabilities they possess, aiming to gather sensitive information over an extended period.
Relevancy & Insights:
APT41, also known as Double Dragon, is a Chinese state-sponsored espionage group known for its dual nature of conducting both state-sponsored espionage and financially motivated operations. Historically, APT41 has specialized in sophisticated software supply-chain attacks, compromising software development environments to inject malicious code and distribute it through normal software channels. They have also exploited vulnerabilities like the Log4j flaw to infiltrate U.S. state government networks. In the current incident, APT41 utilized ANTSWORD and BLUEBEAM web shells to deploy the DUSTPAN backdoor, leading to the execution of BEACON for command and control. They further leveraged DUSTTRAP for hands-on keyboard activity and PINEGROVE to exfiltrate sensitive data to OneDrive, also using SQLULDR to extract data from Oracle databases. APT41’s operations aim at both espionage and financial gains, frequently targeting sectors such as healthcare, high-tech, media, pharmaceuticals, and video games, across countries like the United States, the United Kingdom, and Japan. Their dual motives and extensive target range highlight the group’s persistent and growing threat to global cybersecurity.
ETLM Assessment:
APT41, also known as Double Dragon, Barium, Winnti, Wicked Panda, Wicked Spider, Bronze Atlas, and Red Kelpie, is a prolific Chinese state-sponsored espionage group active since 2012, uniquely combining state-sponsored espionage with financially motivated activities. They typically target countries such as Italy, Spain, Taiwan, Thailand, Turkey, and the United Kingdom, focusing on industries like global shipping and logistics, media and entertainment, technology, and automotive. APT41 exploits vulnerabilities in Internet-facing web applications, including SQL injection and directory traversal vulnerabilities, and notable zero-day vulnerabilities like those in USAHerds and Log4j. They have used malware such as ANTSWORD and BLUEBEAM web shells to execute DUSTPAN and BEACON backdoor for command-and-control communication, DUSTTRAP for hands-on keyboard activity, PINEGROVE for data exfiltration to OneDrive, and SQLULDR2 for exporting data from Oracle databases.
APT41’s operations are dual in nature, focusing on both espionage and financial gains, particularly within the video game industry. They quickly adapt to detections, often recompiling malware within hours. Given their ability to exploit new vulnerabilities rapidly and adapt their tactics, APT41 is expected to remain a significant threat, potentially connecting attacks across critical infrastructures to cause widespread disruption and economic impacts. Organizations in targeted sectors and countries should maintain vigilant and robust security measures to detect and respond to these evolving threats.
Recommendations:

IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Russia threatens the Olympic games
In the wake of the French government’s discussion to potentially send military trainers and even before the recent decision on the provision of Mirage 2000-5 jet fighters to Ukraine, France’s Ministry of Defense has recently warned of possible sabotage attacks by Russia on French military sites this year. Our analysts agree, moreover, we posit that during the Paris Olympics, Russia is likely to target civilian targets in France as well, in order to embarrass the government for President Macron’s repeated comments, in which he suggested NATO could deploy NATO troops in Ukraine. There has been a real stepping up of Russian activity in the intelligence and shadow sphere, intensifying Russian political war on NATO, as the freshly inaugurated president Putin reshuffles his government to include more macroeconomists, who will be needed for the long war Russia clearly intends to fight in the coming years.
As past Russian threats trying to prevent Europe from providing Ukraine with military aid were revealed as bluffs, the Western risk appetite grew. But circumstances change and since we are moving into an even more tense period than before, we should expect Russia to try to strike back in a covert way and to attack the confidence of the Western public.
ETLM Assessment:
Since events like the Olympic Games are at once bid by the host nation to accrue soft power and the focus of global attention, any embarrassing scandals, technical glitches, or unexpected blunders will be magnified as much by the legitimate media as Russian bots and trolls. In the current circumstances, with President Macron taking a hawkish stance on Russia and with Russian athletes banned from the Games, unless they can prove their opposition to the war (so far, only eight have), Moscow has plenty of incentives to attack the games. Hackers linked to the Russian intelligence services disrupted the opening ceremony of the 2018 Winter Olympics in South Korea, using a cyber-attack to shut down a significant portion of the digital infrastructure being used to hold and broadcast the event and French officials are bracing for more such cyber-attacks this year. At a minimum, Russia is preparing to target the Paris Olympics with information campaigns – or rather, these operations have already started.
Russian hackers disrupted heating services in Ukraine
Researchers have published a report on a new strain of ICS malware that disrupted a district energy company in Lviv, Ukraine this winter, resulting in a two-day loss of heating to 600 apartment buildings during sub-zero temperatures. According to researchers, the malware gained access to the ICS systems through an unknown vulnerability in an externally facing Mikrotik router. The adversaries did not attempt to destroy the controllers, instead they caused the controllers to report inaccurate measurements, resulting in the incorrect operation of the system and the loss of heating to customers. In this detail, the attack was similar to the famous US–Israeli hack of an Iranian nuclear facility in Natanz, using the Stuxnet malware.
ETLM Assessment:
Russia continues to use its mass in the Donbas and is making gradual and potentially important gains that could threaten important roads that help Ukraine resupply forces across the front. Nevertheless, the chance of a major Russian breakthrough appears increasingly slim. Russia’s war on Ukraine’s energy infrastructure, however, is causing havoc, with Ukraine reportedly losing half of its power generation, leading to some rolling black outs. This campaign is part of the Russian effort to bring Ukraine to submission by depriving its citizens of basic services.
The Hunters International Ransomware impacts the HOYA Corporation
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; (www[.]hoya[.]com), was compromised by the Hunters International Ransomware. HOYA Corporation is a Japanese multinational company that has been a leader in optical technology. HOYA is a major player in the eyeglass lens market, with advanced technologies aimed at providing superior vision correction solutions. Their products are distributed globally across 52 countries. The company initially specialized in optical glass but has since expanded into a diverse array of fields, including healthcare, information technology, and other high-tech areas. The breached data includes sensitive and confidential organizational information. The total size of the breached data is 2 TB.
The following screenshot was observed published on the dark web:
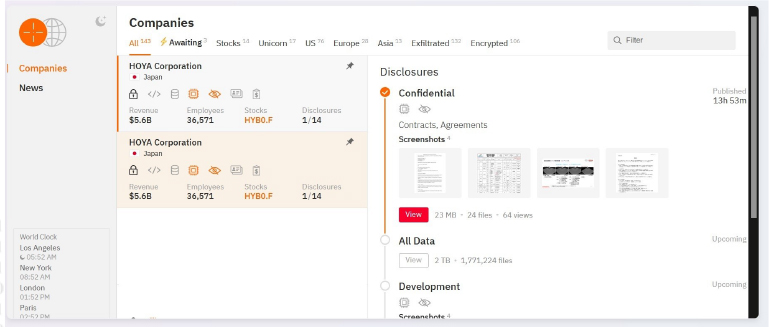
Source: Dark Web
Relevancy & Insights:


ETLM Assessment:
Based on the available information, CYFIRMA’s assessment indicates that Hunters International Ransomware will continue to target various industries globally, with a significant emphasis on the United States, European, and Asian regions. The recent incident involving an attack on HOYA Corporation, a prominent Manufacturing company in Japan, underscores the extensive threat posed by this ransomware strain in the Asia Pacific region.
The RansomHub Ransomware impacts GarudaFood
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Indonesia; (www[.]garudafood[.]com), was compromised by the RansomHub Ransomware. Garudafood is one of Indonesia’s leading food and beverage companies, which produces and sells a wide range of food and beverage products under several brand names, including Garuda, Gery, Chocolatos, Clevo, Prochiz, Okky, and Mountea. Their products range from biscuits, peanuts, pilus, and pellet snacks to confectionery, milk beverages, chocolate powder, cheese, and salad dressings. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization. The total size of the compromised data is approximately 10 GB.
The following screenshot was observed published on the dark web:

Source: Dark Web
Relevancy & Insights:


ETLM Assessment:
Based on recent assessments by CYFIRMA, RansomHub ransomware is expected to intensify its operations across various industries worldwide, with a notable focus on regions in the United States, Europe, and Asia. This prediction is reinforced by the recent attack on GarudaFood, a leading Food & Beverage firm in Indonesia, highlighting RansomHub’s significant threat presence in Southeast Asia.
Vulnerability in Sylius
Summary:
The vulnerability allows a remote attacker to gain access to potentially sensitive information.
Relevancy & Insights:
The vulnerability exists due to excessive data output by the application in the /api/v2/shop/adjustments/{id} endpoint.
Impact:
A remote attacker can enumerate valid adjustment IDs and retrieve order tokens.
Affected Products:
https[:]//github[.]com/Sylius/Sylius/security/advisories/GHSA-55rf-8q29- 4g43
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.

ETLM Assessment:
Vulnerability in Sylius can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of Sylius is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding eCommerce activities and custom solutions for mid-market and enterprise brands across different geographic regions and sectors.
Arcus Media Ransomware attacked and Published data of the Doodle Technologies
Summary:
Recently we observed that Arcus Media Ransomware attacked and published data of the Doodle Technologies (www[.]doodletech[.]ae) on its dark web website. Doodle Technologies, based in the UAE, is an IT support and services company. They offer a range of services including branding, digital marketing, and technology consultancy. Their expertise spans various domains such as IP Telephony, Structured Cabling, Wireless Networking, CCTV, Security Systems, and Time & Attendance Systems. Their services are diverse, covering cloud services, web development, IT infrastructure, and modern security solutions. They provide hybrid solutions combining Microsoft 365 and Cloud Mail, ensuring seamless communication and productivity for businesses. They also offer cloud services such as AWS and Azure hosting, cloud consulting, migrations, and dedicated server hosting. Doodle Technologies also specializes in mobile app development, offering custom solutions for iOS, Android, and cross-platform applications. Their approach focuses on enhancing customer engagement, accessibility, and brand visibility, and providing valuable data insights. The data leak, following the ransomware attack, encompasses sensitive and confidential information related to the organization.

Source: Dark Web
Relevancy & Insights:
Arcus Media is a relatively new ransomware group that has recently made headlines with its attacks on various organizations across different sectors. The group, which emerged in May 2024, operates on a Ransomware-as-a-Service (RaaS) model, allowing other cybercriminals to use their malware for attacks. They are known for using phishing emails to gain initial access and then deploying custom ransomware binaries to execute their attacks.
ETLM Assessment:
Based on the available information, CYFIRMA’s assessment indicates that Arcus Media Ransomware will continue to target various industries globally, with a significant emphasis on the United States, Europe, and Asia. The recent incident involving an attack on Doodle Technologies, a prominent information technology company located in the United Arab Emirates, underscores the extensive threat posed by this particular ransomware strain in the Middle East region.
Good Smile Company Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data sale related to Good Smile Company in an underground forum. A threat actor published a database on a dark web forum claiming that it belongs to Good Smile Company. Good Smile Company is a Japanese manufacturer of hobby products and scale figures. The alleged leak is 184,245 rows in total, and there is data from 76,474 unique users.
According to the forum post, the data is from 2024. The post also contains sample data from the leak, and the alleged data includes Customer ID, Customer Name, E-Mail, Nickname, Customer Group, Status, IP, Date Added, Gender, Login, Type, and Address.
The threat actor claims that this will be a one-time sale and only XMR will be accepted as a form of payment. No contact information is mentioned in the post and those interested are requested to reach out to the threat actor via forum PMs. The data breach is allegedly claimed by the threat actor “888”.

Source: Underground Forums
Universitas Indonesia data advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data leak related to Universitas Indonesia in an underground forum. A threat actor has claimed responsibility for a data breach at the Universitas Indonesia, which reportedly occurred in July 2024. The Universitas Indonesia, a prestigious institution located in Jakarta, is said to have had the personal information of 10,936 users compromised.
The leaked data allegedly includes Personal identification numbers (pencaker_id, no_regis, no_ktp), Full names (nama), Place and date of birth (tempat, tanggal_lahir), Gender (jk),Physical attributes (tinggi, berat),Residential information (provinsi, kota_kab, kecamatan, kelurahan, rt, rw, jalan),Contact information (telp, email),Educational background (pend, jurusan, tahun_lulus),Employment details (jabatan, pt, lokasi, gaji, peng_kerja, lamanya),Additional personal information (agama, status, umur).
The data also includes information about user status, language proficiency, and verification statuses, among other personal details. The threat actor has shared samples of the data to validate the breach.

Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
Based on CYFIRMA’s assessment, the financially motivated threat actor known as “888” poses a significant risk to organizations. This group is known to target any institution and profit from selling sensitive data on the dark web or underground forums. Organizations targeted by “888” typically have inadequate security measures, rendering them vulnerable to potential cyberattacks orchestrated by this threat actor.
Recommendations: Enhance the cybersecurity posture by
The CYFIRMA Research team observed a potential data sale related to Celcom Axiata Berhad(Malaysia). A threat actor has claimed to have obtained and is now offering for sale the user database of Celcom Axiata Berhad, dating from 2023 to 2024. Celcom Axiata Berhad, the oldest mobile telecommunications provider in Malaysia and a member of the Axiata group, merged with Digi to form CelcomDigi on December 1, 2022.
The leaked data purportedly includes 30 million user information such as addresses, city details, IC numbers, mobile numbers, names, postcodes, sources, and states. The threat actor has listed the price for this data at $10,000 in BTC (negotiable), also accepting USDT. The data breach is allegedly claimed by the threat actor “Sh1mo”.

Source: Underground forums
The CYFIRMA Research team observed a potential data sale related to a U Mobile (Malaysia). According to a post from a dark web forum, a Malaysian telecom company, U Mobile, has been allegedly breached. The threat actor states that their cyber-attack impacted 4 million people.
In the forum post, the threat actor stated the price for the alleged leak as $5000 BTC and included a Telegram link for contact information.
According to the threat actor, the alleged leak contains name, address, city, IC number, mobile number, postcode, and state information. A sample from the leaked data is also added to the forum post. The data breach is allegedly claimed by the threat actor “Sh1mo”.

Source: Underground forums
ETLM Assessment:
The Threat Actor group “Sh1mo” has become active in underground forums and emerged as a formidable force in cybercrime, primarily motivated by financial gains. The group has already targeted industries including Government, Industrial Conglomerates, Retail, Staffing, Business Consulting, Banks, E-Commerce, and Electric & Utilities. This activity indicates Sh1mo’s intention to expand its attack surface to other industries globally in the future.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph

Industry-Wise Graph

For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.