


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware.
Target Technologies: Windows OS.
Target Geography: Asia-Pacific
Introduction:
CYFIRMA Research and Advisory Team has found COOSEAGROUP Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
COOSEAGROUP Ransomware
Researchers have discovered a new ransomware strain called COOSEAGROUP. This ransomware encrypts victim data, renames affected files by appending a unique extension (such as .Cooseagroup), and generates a ransom note titled “README.TXT”.

Screenshot: File encrypted by ransomware (Source: Surface Web)
CYFIRMA’s assessment identifies COOSEAGROUP as a ransomware strain that encrypts victim data and appends a unique victim identifier followed by the “.Cooseagroup” extension to affected files, after which it generates a Chinese- language ransom note titled “README.TXT” stating that file decryption requires payment. The ransom note explicitly threatens the disclosure of sensitive and confidential data, including communications, databases, certificates, financial records, and employee information, if payment is not made, and applies time- based pressure by offering a reduced ransom if the attackers are contacted within 12 hours. Victims are instructed to communicate via the Session messenger, indicating the use of anonymized communication channels, and are discouraged from seeking third-party assistance such as law enforcement or recovery services, with warnings that manual decryption attempts may permanently damage the encrypted files. The note also claims limited decryption capability following payment as proof of functionality. Based on documented behavior, COOSEAGROUP operates using a ransomware model that combines file encryption with explicit data-leak extortion and coercive negotiation tactics; removal of the malware prevents further encryption but does not restore affected files, no free decryptor is available, and recovery is only possible through restoration from secure backups, if available.
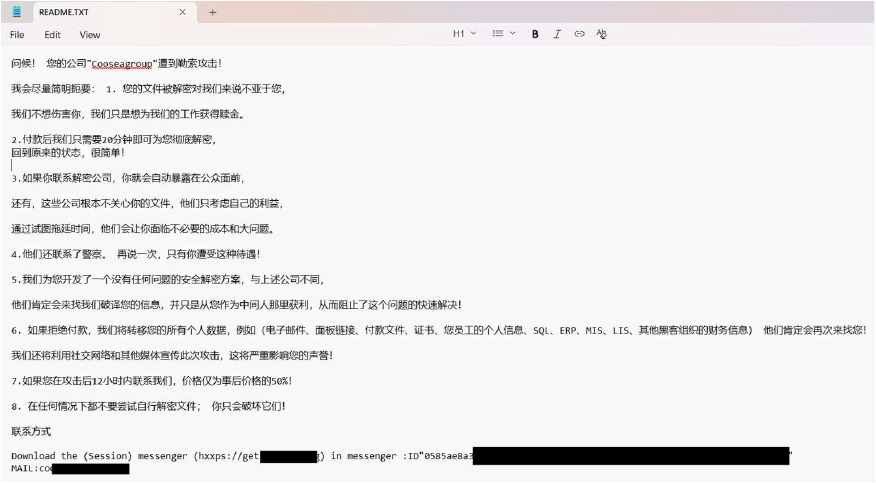
Screenshot: The appearance of COOSEAGROUP‘s ransom note “README.TXT” (Source: Surface Web)
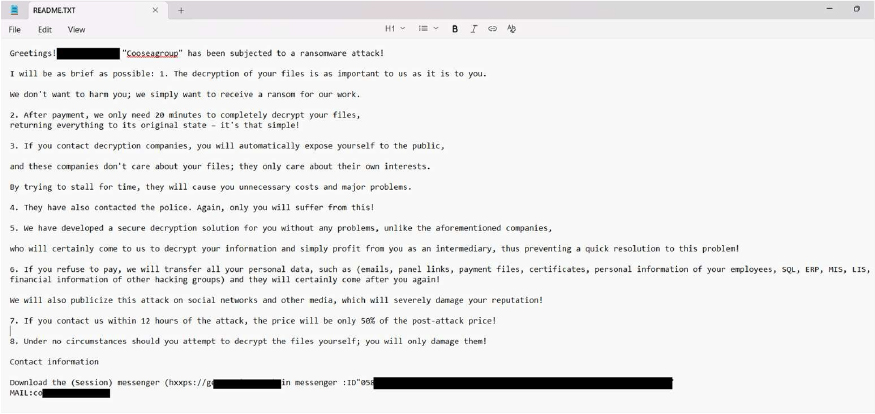
Screenshot: The appearance of COOSEAGROUP’s ransom note[English translated] “README.TXT” (Source: Surface Web)
The following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Persistence | T1112 | Modify Registry |
| Persistence | T1542 | Pre-OS Boot |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1547 | Boot or Logon Autostart Execution |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1134.004 | Access Token Manipulation: Parent PID Spoofing |
| Privilege Escalation | T1547 | Boot or Logon Autostart Execution |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1070 | Indicator Removal |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1134.004 | Access Token Manipulation: Parent PID Spoofing |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion | T1542 | Pre-OS Boot |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1564 | Hide Artifacts |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Credential Access | T1056 | Input Capture |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1614 | System Location Discovery |
| Collection | T1056 | Input Capture |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1074 | Data Staged |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1090 | Proxy |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1573 | Encrypted Channel |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment indicates that the COOSEAGROUP ransomware is likely to further advance its operations within a data-extortion–enabled ransomware model. The group’s use of file encryption combined with explicit data-leak threats, anonymized communication channels, and time-based ransom pressure reflects a structured extortion workflow focused on maximizing victim compliance. These characteristics align with established ransomware operating patterns in which reputational and operational impact are leveraged alongside encryption to increase payment likelihood. The absence of a free decryptor and the requirement for backup-based recovery reinforce the effectiveness of this approach against unprepared environments, supporting the likelihood of COOSEAGROUP maintaining sustained activity within the broader ransomware threat landscape.
Sigma rule:
title: COOSEAGROUP Ransomware Ransom Note Creation
description: Detects creation of the COOSEAGROUP ransomware ransom note README.TXT, indicating active ransomware impact.
date: 2025/12/17 tags:
– attack.impact
– attack.t1486 logsource:
product: windows category: file_event
detection: selection_filename:
TargetFilename|endswith: ‘\README.TXT’ selection_extension:
TargetFilename|contains: ‘.Cooseagroup’ condition: selection_filename or selection_extension
falsepositives:
– Legitimate README.TXT files created by software installers or developers level: high
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Information Stealer | Objectives: Credential Theft & Payment Fraud | Target Technology: Windows OS | Target Industry: Finance, Accounting, Treasury, Procurement, Legal, HR/Payroll & Executive Assistants | Target Geography: Russia
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week, “Phantom Stealer” is trending.
Overview of Operation Phantom Stealer
This activity represents a targeted phishing campaign aimed primarily at finance and accounting teams, using deceptive payment confirmation emails to exploit routine business workflows. The messages are written in formal Russian business language and are designed to appear as legitimate bank transfer notifications, encouraging recipients to open attached files without suspicion.
The attackers rely on carefully crafted attachments that bypass common email security checks and trick users into launching malicious content disguised as financial documents. Once opened, these files lead to silent compromise of the victim’s system, allowing the attackers to collect sensitive information and potentially enable financial abuse.
By imitating trusted financial communications and leveraging familiarity with routine payment processes, the campaign increases the likelihood of user interaction and successful compromise. This operation highlights how well-crafted social engineering, rather than complex technical exploits, continues to be a highly effective method for targeting organizations and exposing them to financial and data-related risks.
Attack Method
The infection chain begins with a Russian-language phishing email masquerading as a bank transfer confirmation from a legitimate financial or currency brokerage entity. The message targets finance-facing roles and leverages routine payment verification workflows to prompt user interaction. A ZIP archive is attached, named to resemble official banking documentation, reducing suspicion and increasing the likelihood of attachment execution.
Upon extraction, the archive delivers an ISO disk image that auto-mounts when opened, exposing its contents as a virtual drive. This technique enables the threat actor to bypass common email gateway and attachment scanning controls. The mounted ISO contains a single executable file presented as a payment-related document. Execution of this file initiates an in-memory loader that minimizes disk artifacts and delays detection.
The loader activates a secondary DLL component responsible for reconstructing the final Phantom Stealer payload directly in memory. Multiple evasion mechanisms are employed, including environment checks and obfuscated payload reconstruction using image-backed objects. Once deployed, Phantom Stealer initiates credential harvesting and data collection routines targeting browser-stored authentication data, cryptocurrency wallets, messaging application tokens, clipboard contents, and keystrokes. Stolen data is consolidated and exfiltrated via multiple outbound channels to ensure reliable data theft.
The following are the TTPs based on the MITRE Attack Framework for Enterprise
| Tactic (ID) | Technique ID | Technique Name |
| Initial Access | T1566.001 | Phishing: Spearphishing Attachment |
| Execution | T1204.002 | User Execution: Malicious File |
| Execution | T1059 | Command and Scripting Interpreter |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Persistence | T1053 | Scheduled Task/Job |
| Credential Access | T1555 | Credentials from Password Stores |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Credential Access | T1539 | Steal Web Session Cookie |
| Discovery | T1082 | System Information Discovery |
| Collection | T1115 | Clipboard Data |
| Collection | T1005 | Data from Local System |
| Collection | T1119 | Automated Collection |
| Exfiltration | T1567.002 | Exfiltration Over Web Service: Exfiltration to Cloud Storage |
| Exfiltration | T1048 | Exfiltration Over Alternative Protocol |
INSIGHTS
ETLM ASSESSMENT
From an ETLM perspective, CYFIRMA assesses that the increasing prevalence of phishing-driven intrusion campaigns reflects an evolving threat landscape marked by diminished visibility, heightened challenges in attribution, and the integration of malicious activity into routine business workflows. As these campaigns continue to advance, organizations may face prolonged periods of undetected compromise, thereby increasing exposure to covert financial fraud, credential exploitation, and unauthorized network access. Employees are increasingly targeted as indirect vectors, with routine actions such as opening attachments, handling financial documentation, or interacting with enterprise applications being leveraged to initiate malicious activity. Over time, these trends are likely to undermine traditional assumptions regarding trust, detection, and early warning, necessitating a reassessment of how security controls are enforced across users, applications, and operational contexts in environments where adversaries operate with a high degree of stealth and precision.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rule
rule Phantom_Stealer
{
meta:
author = “CYFIRMA” date = “2025-12-16”
strings:
$s1 = “27bc3c4eed4e70ff5a438815b1694f83150c36d351ae1095c2811c962591e1bf”
$s2 = “4b16604768565571f692d3fa84bda41ad8e244f95fbe6ab37b62291c5f9b3599”
$s3 = “60994115258335b1e380002c7efcbb47682f644cb6a41585a1737b136e7544f9”
$s4 = “78826700c53185405a0a3897848ca8474920804a01172f987a18bd3ef9a4fc77”
condition: any of ($s*)
}
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
o Rhysida Ransomware – One of the ransomware groups.
o Qilin Ransomware – One of the ransomware groups. Please refer to the trending malware advisory for details on the following:
o Malware – Phantom_Stealer Behavior – Most of these malwares use phishing and social engineering techniques as their initial attack vectors. Apart from these techniques, exploitation of vulnerabilities, defense evasion, and persistence tactics are being observed.
Blind Eagle (APT-C-36): Government-Focused Espionage Campaigns
About the Threat Actor
Since April 2018, a South America–based APT group known as Blind Eagle (APT-C-36) has conducted sustained, targeted attacks against Colombian government institutions and major organizations across sectors such as finance, petroleum, and professional manufacturing.
Details on Exploited Vulnerabilities
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2023-38831 | RARLAB WinRAR | 7.8 | Link |
| CVE-2024-43451 | Windows | 6.5 | – |
| CVE-2025-31324 | SAP NetWeaver Visual Composer Metadata Uploader | 9.8 | – |
| CVE-2023-39234 | GTKWave | 7.8 | – |
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Initial Access | T1566.001 | Phishing: Spearphishing Attachment |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Execution | T1204.002 | User Execution: Malicious File |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Privilege Escalation | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Defense Evasion | T1036.005 | Masquerading: Masquerade Task or Service |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Command and Control | T1571 | Non-Standard Port |
| Command and Control | T1105 | Ingress Tool Transfer |
Latest Developments Observed
Recent observations show that BlindEagle (APT-C-36) continues to target Colombian government entities, as seen in a September 2025 campaign against an agency under the Ministry of Commerce, Industry and Tourism (MCIT). The group has advanced its tradecraft by abusing compromised internal email accounts and employing multi-stage, fileless attack chains. It has also adopted the Caminho downloader to deploy an enhanced DCRAT payload, leveraging services like Discord and steganography to increase stealth and persistence.
ETLM Insights
Blind Eagle (APT-C-36) remains an active and persistent regional espionage threat actor, with ongoing operations continuing to prioritize Colombian government institutions and associated public-sector entities, and possibly suspected to expand its footprints to other geographical regions.
The threat actor continues to modernize its tradecraft, evidenced by a progressive shift toward modular, multi-stage execution chains, increased adoption of fileless and in-memory techniques, and the systematic abuse of legitimate platforms and cloud-based services to mask malicious activity. These developments indicate a deliberate emphasis on stealth, attribution resistance, and operational resilience, enabling the threat actor to persist within increasingly monitored and defended environments.
Looking forward, the threat actor is assessed to further refine its modular tooling, deepen its reliance on trusted third-party services, and expand stealth-focused persistence mechanisms. These evolutions will likely continue to support long- duration espionage operations against high-value and government-aligned targets, reinforcing the threat actor’s role as a strategic intelligence threat.
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
YARA Rules
rule BlindEagle_APT_C36_MultiCVE_Activity
{
meta:
description = “Detects Blind Eagle (APT-C-36) related artifacts leveraging multiple CVEs and known infrastructure”
author = “CYFIRMA”
threat_actor = “Blind Eagle / APT-C-36”
reference_cves = “CVE-2023-38831, CVE-2024-43451, CVE-2025-31324, CVE-2023-39234”
confidence = “Medium” date = “2025-12-18”
strings:
/* CVE Indicators */
$cve1 = “CVE-2023-38831” ascii
$cve2 = “CVE-2024-43451” ascii
$cve3 = “CVE-2025-31324” ascii
$cve4 = “CVE-2023-39234” ascii
/* IP Indicators */
$ip1 = “128.90.106.22” ascii
$ip2 = “128.90.107.21” ascii
$ip3 = “62.60.226.64” ascii
$ip4 = “128.90.115.28” ascii
$ip5 = “128.90.108.126” ascii
/* Domain Indicators */
$domain1 = “elyeso.ip-ddns.com” ascii
$domain2 = “republicadominica2025.ip-ddns.com” ascii
$domain3 = “upxsystems.com” ascii
$domain4 = “elfinindia.com” ascii
$domain5 = “occoman.com” ascii
/* Malware / File Indicators */
$mozi1 = “win32.exe” ascii
$mozi2 = “fikik.exe” ascii
$mozi3 = “exe:fikik.exe” ascii
$mozi4 = “8746bfa7f6ccddb8a2c6164ab4cfa06e.exe” ascii
condition:
any of ($cve*) or any of ($ip*) or any of ($domain*) or any of ($mozi*)
}
Recommendations Strategic
Management
Tactical
Venezuela blames the US for the cyberattack on the state-owned oil company
Venezuela’s state oil company, PDVSA, suffered a ransomware attack over the weekend that disrupted operations, forcing the suspension of oil cargo deliveries. PDVSA and the Venezuelan oil ministry accused the United States of orchestrating the incident, claiming it was carried out by “foreign interests in collusion with internal actors” aimed at undermining the country’s sovereign energy sector. The U.S. State Department has not commented on the allegations. Caracas routinely attributes domestic crises, including power outages, to U.S. sabotage–a pattern that persists amid escalating bilateral tensions, particularly following the U.S. seizure of a Venezuelan crude tanker and the U.S. administration’s imposition of a blockade on a sanctioned shadow fleet of tankers.
ETLM Assessment:
The enforcement mechanism of the blockade remains unclear, though it could involve U.S. naval or Coast Guard interdictions in international waters–similar to last week’s seizure of the sanctioned tanker Skipper (falsely flying a Guyana flag) off Venezuela’s coast. In the context of Venezuela’s recent blame of a PDVSA ransomware attack on U.S. “foreign interests,” potential American cyber operations could include disruptive actions against Venezuelan energy infrastructure, such as data wipers, supply chain compromises, or denial-of-service attacks to amplify economic pressure without direct kinetic force.
However, there is no public evidence or attribution of the U.S. government ever deploying ransomware in offensive cyber operations–ransomware remains overwhelmingly associated with criminal groups (e.g., from Russia, North Korea, or Iran) or occasional nation-state facilitation, while U.S. efforts focus on other tools of cyber statecraft.
Venezuela could leverage its strategic partnerships with Iran–whose cyber units have a proven track record of disruptive attacks on energy infrastructure (e.g., Shamoon wiper malware against Saudi Aramco in 2012)–to facilitate or proxy retaliatory operations targeting U.S. and allied oil refineries, pipelines, or grids, potentially using ransomware, data wipers, or supply-chain compromises to inflict economic damage.
Iranian hackers offer cash bounties for killing Israelis they doxed
The Iran-linked hacking group “Handala” has doxxed more than 200 Israeli academics, journalists, and defense officials, publicly releasing their photos, names, professional credentials, email addresses, locations, and phone numbers. The group has also announced $30,000 bounties on over a dozen individuals it identifies as engineers or technicians involved in Israel’s Patriot, Arrow, and David’s Sling air defense systems.
ETLM Assessment:
Widely attributed to Iran’s Ministry of Intelligence, Handala’s campaign blends psychological operations with real-world risks, compensating for Iran’s weakened conventional proxies by targeting civilian experts critical to Israel’s missile defenses — and signaling ongoing asymmetric retaliation amid heightened tensions.
Russian multiyear campaign targeting the energy sector revealed
Researchers have released a report detailing a multi-year Russian state-sponsored cyber campaign targeting global critical infrastructure, with a strong emphasis on the energy sector in Western countries. The activity is attributed with high confidence to Russia’s GRU (Main Intelligence Directorate), showing clear links to its notorious Sandworm group.
The campaign represents a major evolution in attacks on critical infrastructure, marked by a tactical shift: misconfigured network edge devices owned by customers have become the primary entry point, while exploitation of known vulnerabilities has decreased. According to the researchers, this adaptation achieves the same goals–stealing credentials and moving laterally into victims’ online services and infrastructure.
ETLM Assessment:
Russia’s military intelligence hackers appear to be preparing for potential escalation by quietly gaining persistent access to Western critical infrastructure– particularly energy networks–through low-profile compromises of misconfigured edge devices like routers and VPNs.This tactic allows stealthy credential harvesting and lateral movement into cloud services, enabling future disruption or sabotage with minimal detection risk, positioning them to “move in” rapidly during a conflict.
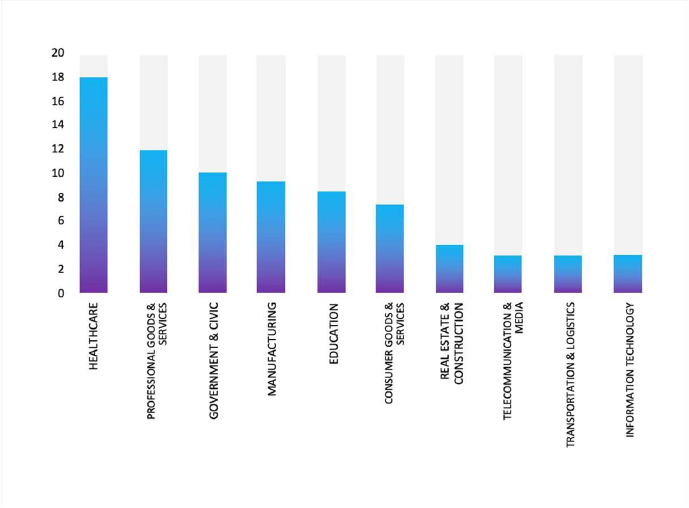
Rhysida Ransomware Impacts Yokosuka Gakuin
Summary:
CYFIRMA observed in an underground forum that a company from Japan, Yokosuka Gakuin (http[:]//yokosukagakuin[.]ac[.]jp/), was compromised by Rhysida Ransomware. Yokosuka Gakuin is a private co-educational institution located in Yokosuka, Kanagawa Prefecture, Japan. Established in 1950, the school operates at the elementary, junior high, and high school levels based on Christian founding principles. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. According to the samples provided by the actor, the allegedly compromised data includes:
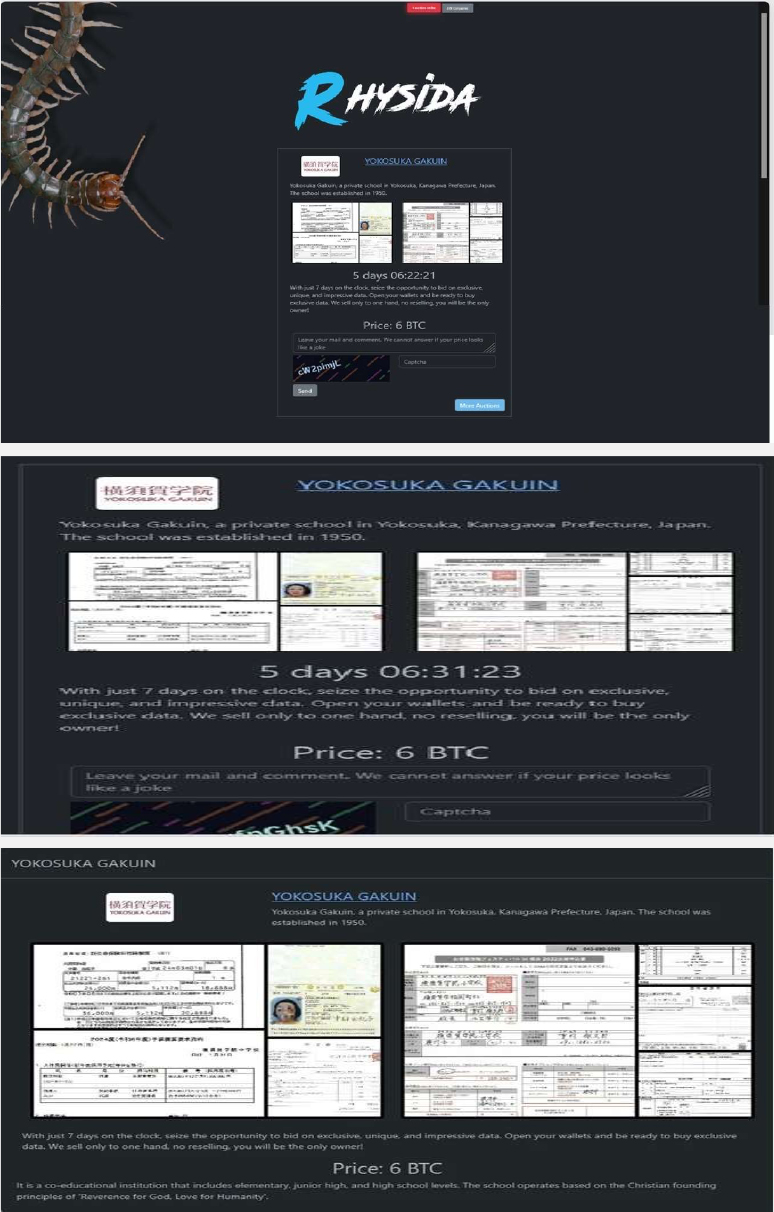
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Rhysida ransomware has emerged as a notable double-extortion threat leveraging both encryption and data theft, evolving rapidly in sophistication since its first appearance in 2023. The Rhysida case underlines the necessity of robust layered defenses, vigilant credential management, cross-sector threat monitoring, and proactive response capabilities.
Organizations must not only strengthen prevention and detection controls but also ensure comprehensive incident response planning to mitigate operational, financial, and reputational risks associated with this aggressive, evolving ransomware actor.
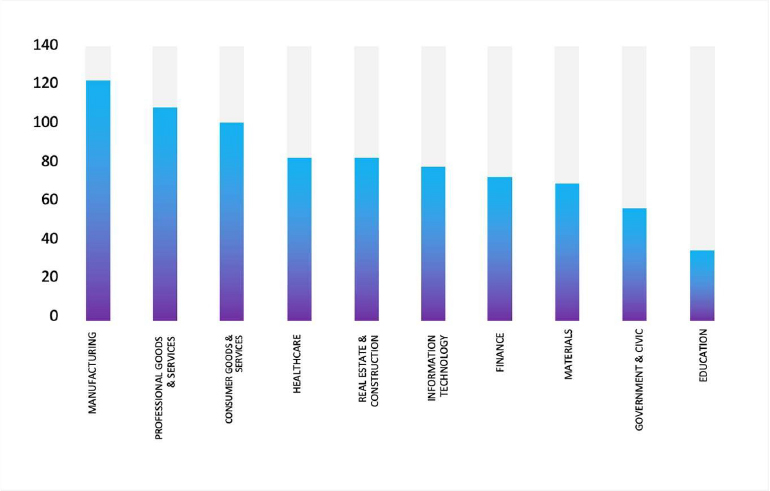
Qilin Ransomware Impacts Dacon Networks Pte Ltd
Summary:
CYFIRMA observed in an underground forum that a company from Singapore, Dacon Networks Pte Ltd (https[:]//www[.]dacon[.]com[.]sg/), was compromised by Qilin Ransomware. Dacon Networks Pte Ltd specializes in IT, voice, and video communication solutions based in Singapore, offering a range of products, including webcams and video conferencing systems. The compromised data contains confidential and sensitive information belonging to the organization.

Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and a focus on speed and evasion, make it a particularly dangerous actor.
Vulnerability in HPE OneView
Relevancy & Insights:
The vulnerability exists due to improper input validation. A remote non-authenticated attacker can send a specially crafted request and execute arbitrary code on the target system.
Impact:
Successful exploitation of this vulnerability may result in complete compromise of the vulnerable system.
Affected Products:
https[:]//support[.]hpe.com/hpesc/public/docDisplay?docLocale=en_US&docId= hpesbgn04985en_us
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.

ETLM Assessment
Vulnerability in HPE OneView can pose significant threats to user privacy and enterprise infrastructure security. This can impact various industries globally, including technology, finance, healthcare, manufacturing, and government sectors. Ensuring the security of HPE OneView is crucial for maintaining the integrity and protection of infrastructure management systems worldwide.
Space Bears Ransomware attacked and published the data of Right Power Technology Sdn Bhd
Summary:
Recently, we observed that Space Bears Ransomware attacked and published the data of Right Power Technology Sdn Bhd (https://www[.]rightpowerups[.]com[.]my/) on its dark web website. Right Power Technology Sdn Bhd stands as a leading producer and distributor of reliable, affordable, and efficient UPS systems. With over 20 years of experience, Right Power excels in delivering power protection solutions and maintenance services for critical mission facilities across the business, education, and commercial sectors. Right Power offers a comprehensive range of products, including Line Interactive Simulated Sinewave, True Online Sinewave, and Smart Pure Sinewave UPS systems. Additionally, we provide a full suite of heavy-duty and high-performance Industrial Automatic Voltage Regulators (AVRs), with capacities ranging from 800VA to 10,000KVA. The ransomware incident resulted in a data leak involving employees’ and clients’ personal information, financial documents, and other confidential and sensitive data.

Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Space Bears ransomware represents a significant threat in the evolving landscape of cybercrime. With its aggressive tactics, association with established ransomware operations like Phobos, and focus on double extortion, organizations are advised to bolster their cybersecurity measures to mitigate risks associated with such attacks. Continuous monitoring of this group’s activities will be essential for understanding their methods and potential impact on various sectors.
Thailand National Telecom Public Company Limited (NT) Data Advertised on a Leak Site
Summary: The CYFIRMA research team has identified claims by a threat actor using the alias “Sorb,” who alleges responsibility for a security breach involving National Telecom Public Company Limited (NT) in Thailand.
National Telecom Public Company Limited (NT) is a Thai state-owned telecommunications operator, established in 2021 following the merger of CAT Telecom and TOT Public Company Limited. The company provides fixed-line and mobile telephony services, as well as international telecommunications infrastructure, including international gateways, satellite systems, and submarine cable network connectivity.
According to the threat actor and the sample data shared, the allegedly compromised dataset contains approximately 1,197,636 records, including around 351,000 unique phone numbers. The exposed information reportedly includes:
The actor is reportedly offering the dataset for sale at an asking price of approximately USD 300.
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
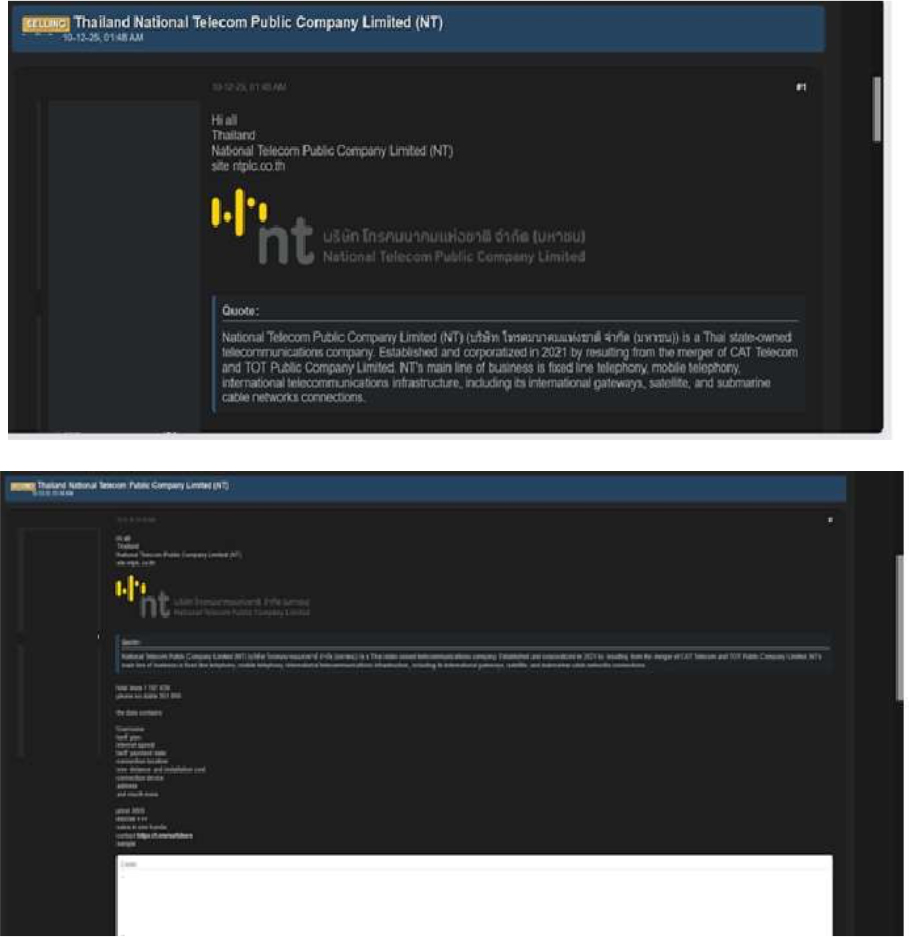
Source: Underground Forums
Voltras International Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team has observed that Voltras International, a prominent online booking platform and GDS aggregator based in Indonesia, has allegedly been compromised. A threat actor is currently selling a 30GB database claimed to be the company’s internal archive for $4,500. Voltras International serves as a major hub for numerous travel agencies in Southeast Asia, maintaining direct connections with airlines such as Garuda Indonesia, Emirates, and Singapore Airlines. The breach purportedly affects the company’s internal operations, specifically involving transaction records and agency financial details.
According to the actor, the compromised archive spans from 2019 to 2025 and contains sensitive financial documents. The allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
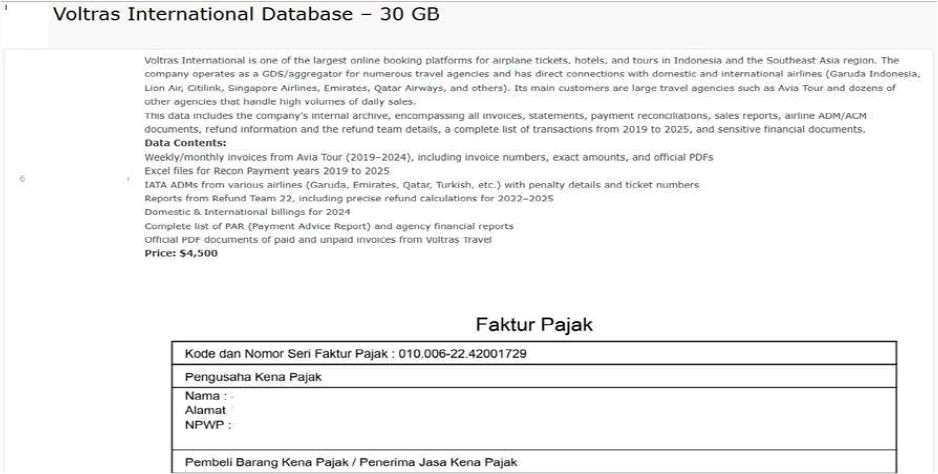
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously looking for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to gain access and steal valuable data. Subsequently, the stolen data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor referred to as “Sorb” is assessed to be a highly active and capable group primarily engaged in data-leak operations. Several credible sources have connected the actor to a range of security breaches involving unauthorized access to systems and the distribution or sale of stolen data on dark web marketplaces.
These activities highlight the persistent and rapidly evolving threat landscape driven by underground cybercriminal communities and underscore the importance for organizations to reinforce their cybersecurity posture through continuous monitoring, enhanced threat intelligence, and proactive defensive strategies to protect sensitive data and critical infrastructure.
Recommendations: Enhance the cybersecurity posture by:
The CYFIRMA Research team observed that Al-Ahli Saudi Football Club (Al-Ahli FC), a professional multi-sport club based in Jeddah and a prominent member of the Saudi Pro League, has allegedly suffered a significant data breach. The incident involves the unauthorized exfiltration of internal documents, which were subsequently leaked on a popular dark web forum. The party responsible for the leak claims to have obtained over 111 files from the club’s infrastructure and has signaled intentions to target other high-profile Middle Eastern football organizations and the Asian Football Confederation (AFC) database.
According to the actor, the allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.

Source: Underground Forums
The CYFIRMA Research team has identified that Play Ticket, a South Korean online ticketing and reservation platform, has allegedly been compromised, resulting in the exposure of significant user and order data. A threat actor on a cybercrime forum has listed a database for sale, claiming to contain approximately 210,000 records linked to the domain playticket.co.kr. The breach reportedly involves two separate files—one containing member details and another containing order history—offered for a low price of $150.
According to the actor, the compromised data spans over 64,000 member lines and 152,000 order lines. The allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
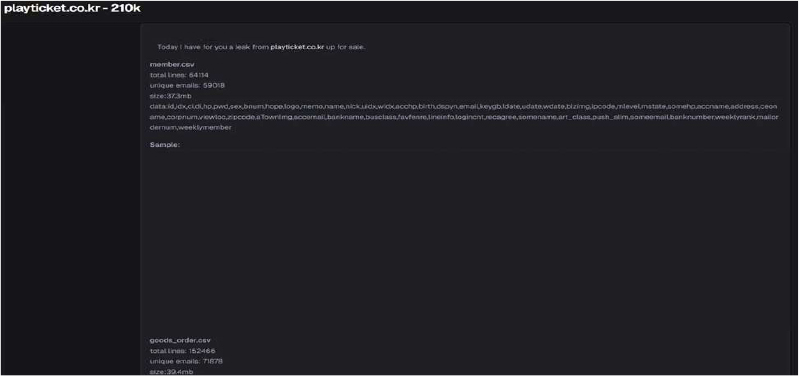
Source: Underground Forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
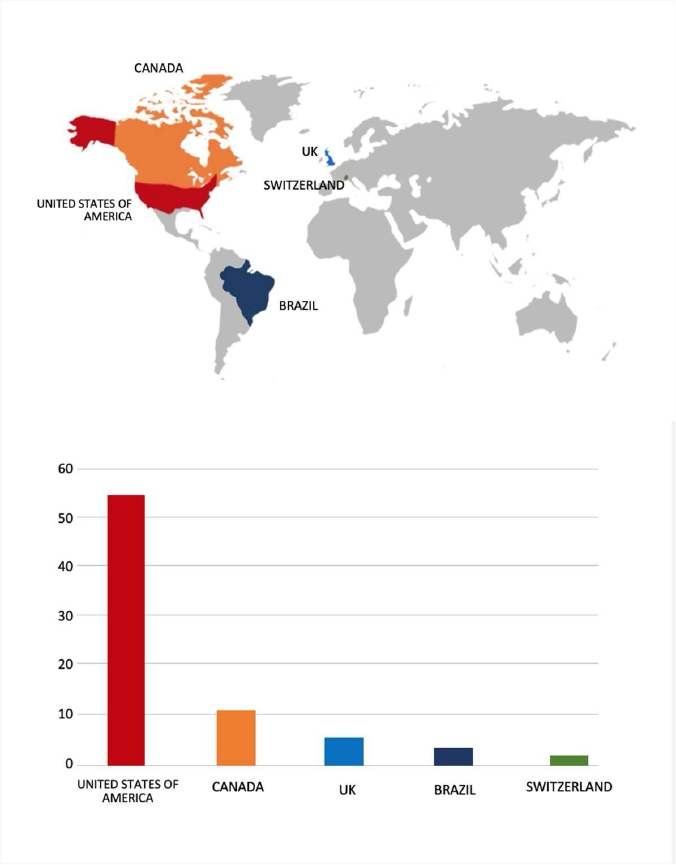
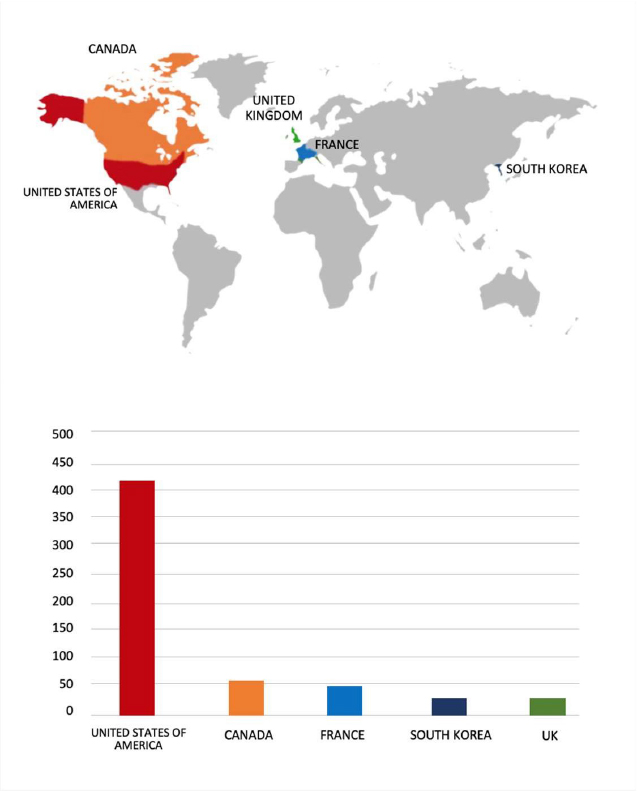
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
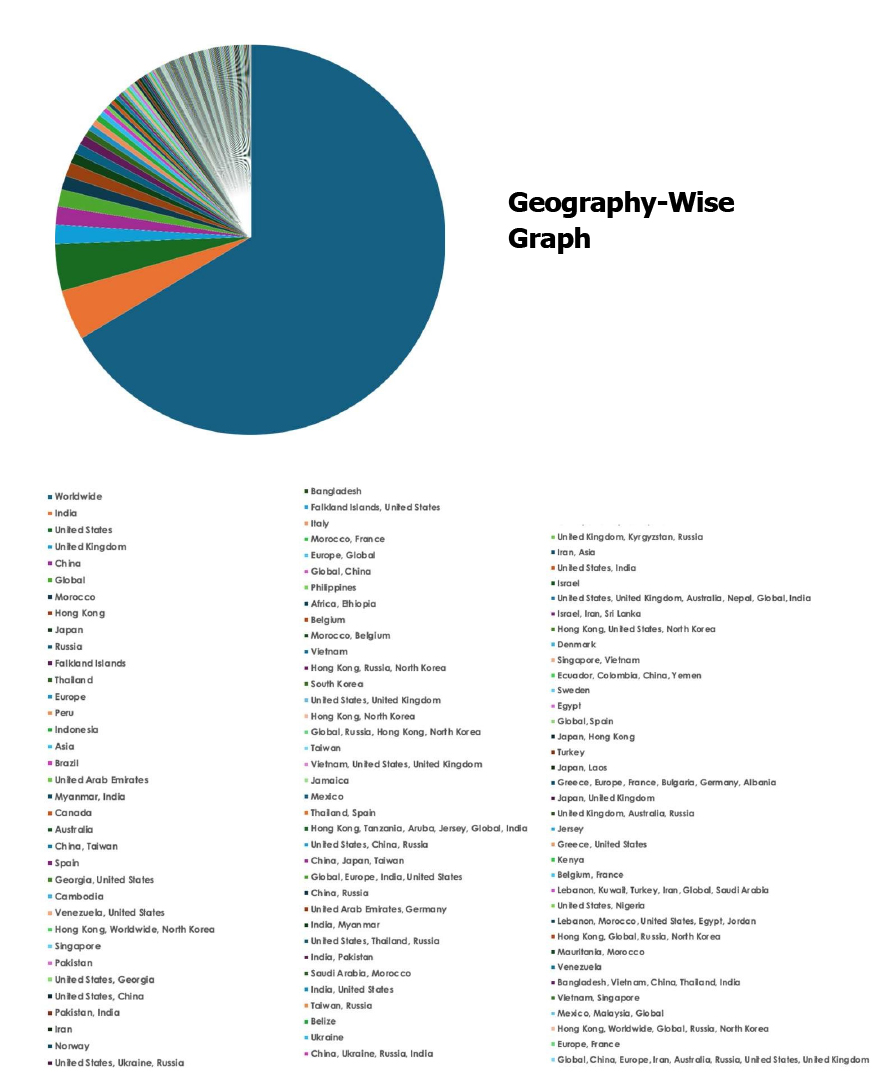

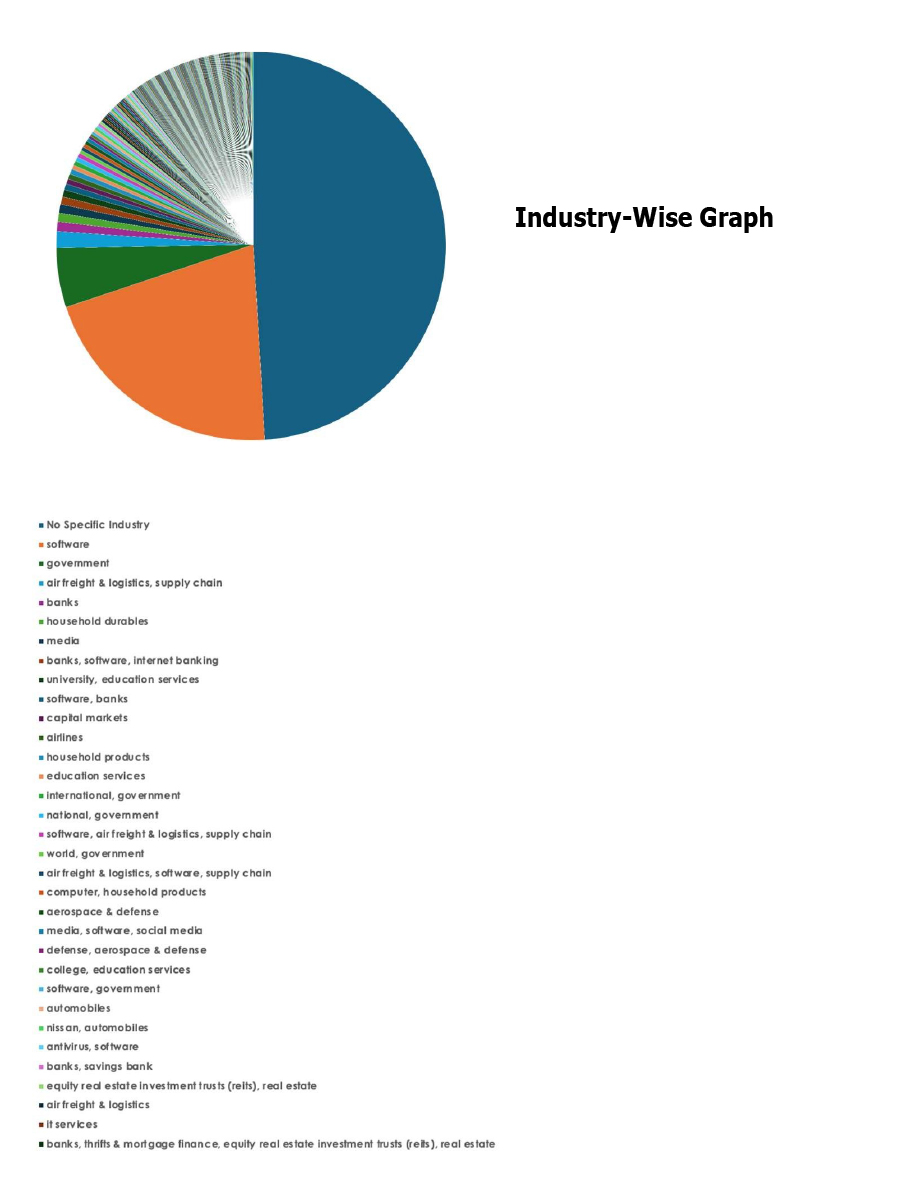

For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.