Published On : 2024-04-26
Ransomware of the Week
CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found new Lethal Lock ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Lethal Lock ransomware
Researchers recently identified a new strain of ransomware known as Lethal Lock. This malicious software encrypts files on the victim’s system and adds its distinct “.LethalLock” extension to filenames. In addition to file encryption, Lethal Lock alters the victim’s desktop wallpaper and generates a ransom note named “SOLUTION_NOTE.txt”.
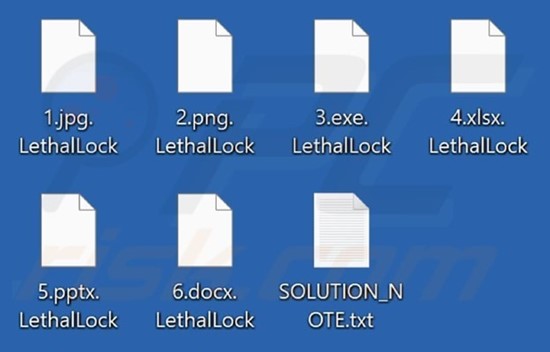
Screenshot of files encrypted by ransomware (Source: Surface Web)
The Lethal Lock ransomware ransom note threatens permanent data loss unless a hefty ransom of 25BTC is paid within 72 hours. It warns against attempting decryption or seeking help, claiming data will be sold on the dark web and decryption keys will be deleted if demands aren’t met. The note boasts of employing military-grade encryption algorithms, rendering victim files virtually inaccessible. The language suggests high confidence in the encryption’s robustness, emphasizing its complexity and mysterious nature.

Screenshot of Lethal Lock text file (Source: Surface Web)

Screenshot of Lethal Lock’s desktop wallpaper (Source: Surface Web)
Following are the TTPs based on the MITRE Attack Framework.
| Sr.
No |
Tactics |
Techniques/Sub-Techniques |
| 1 |
TA0002: Execution |
T1053: Scheduled Task/Job |
| T1059: Command and Scripting Interpreter |
| T1106: Native API |
|
2 |
TA0003:
Persistence |
T1053: Scheduled Task/Job |
| T1176: Browser Extensions |
| T1543.003: Create or Modify System Process:
Windows Service |
| T1547.001: Boot or Logon Autostart Execution:
Registry Run Keys / Startup Folder |
|
3 |
TA0004: Privilege Escalation |
T1053: Scheduled Task/Job |
| T1055: Process Injection |
| T1543.003: Create or Modify System Process:
Windows Service |
| T1547.001: Boot or Logon Autostart Execution:
Registry Run Keys / Startup Folder |
| T1548: Abuse Elevation Control Mechanism |
| 4 |
TA0005: Defense |
T1027: Obfuscated Files or Information |
|
Evasion |
T1036: Masquerading |
| T1055: Process Injection |
| T1070.004: Indicator Removal: File Deletion |
| T1112: Modify Registry |
| T1140: Deobfuscate/Decode Files or
Information |
| T1202: Indirect Command Execution |
| T1222: File and Directory Permissions
Modification |
| T1497: Virtualization/Sandbox Evasion |
| T1548: Abuse Elevation Control Mechanism |
| T1562.001: Impair Defenses: Disable or Modify
Tools |
| T1564.003: Hide Artifacts: Hidden Window |
|
5 |
TA0006:
Credential Access |
T1003: OS Credential Dumping |
| T1552.001: Unsecured Credentials:
Credentials In Files |
| T1555.003: Credentials from Password Stores:
Credentials from Web Browsers |
|
6 |
TA0007:
Discovery |
T1010: Application Window Discovery |
| T1012: Query Registry |
| T1018: Remote System Discovery |
| T1057: Process Discovery |
| T1082: System Information Discovery |
| T1083: File and Directory Discovery |
| T1087: Account Discovery |
| T1497: Virtualization/Sandbox Evasion |
| T1518.001: Software Discovery: Security
Software Discovery |
| 7 |
TA0008: Lateral
Movement |
T1080: Taint Shared Content |
| 8 |
TA0009:
Collection |
T1005: Data from Local System |
| T1115: Clipboard Data |
| T1185: Browser Session Hijacking |
| 9 |
TA0011:
Command and
Control |
T1071: Application Layer Protocol |
| T1095: Non-Application Layer Protocol |
|
10 |
TA0040: Impact |
T1485: Data Destruction |
| T1486: Data Encrypted for Impact |
| T1489: Service Stop |
| T1490: Inhibit System Recovery |
Relevancy and Insights:
- This ransomware specifically targets the widely used Windows Operating System, which is prevalent across numerous industries and organizations.
- The Ransomware places itself in “HKEY_LOCAL_MACHINE\ SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\” to manipulate the execution behaviour of the image. This registry key allows the ransomware to achieve persistence, silently execute alongside or instead of legitimate images, and maintain control over compromised systems, evading detection.
- Detect-Debug-Environment: Debugging environments are used by developers to analyze and troubleshoot This technique is used by the ransomware to determine whether it is operating in a debug environment. This feature aids the ransomware in avoiding analysis and detection attempts.
- The ransomware is making calls to the Windows Management Instrumentation (WMI) framework. WMI is a powerful tool used by many legitimate applications and services, but it can also be exploited by malware to execute commands, collect information, or perform system modifications
- If the victim fails to pay the ransom, their data will remain locked indefinitely. The perpetrators would then either sell the data to a third party on the Dark Web or trade it for more advanced tools to swiftly dismantle the victim’s organization.
ETLM Assessment:
- CYFIRMA’s assessment, relying on available information, suggests that Lethal Lock ransomware, with its demand for 25 bitcoins and intricate encryption methods, is likely to target economically developed nations like East Asia, South-East Asia, and the US, where organizations are more capable of meeting such demands. Considering the Tactics, Techniques, and Procedures, Lethal Lock exhibits a high level of sophistication and adaptability, indicating the potential for evolving strategies in future attacks. Vigilance and strong cybersecurity measures are essential to mitigate these threats effectively.
Sigma Rule
title: Delete shadow copy via WMIC threatname:
behaviorgroup: 18
classification: 0 mitreattack:
logsource:
category: process_creation product: windows
detection: selection:
CommandLine:
– ‘*wmic*shadowcopy delete*’ condition: selection
level: critical
(Source: Surface web)
IOCs:
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
- Implement competent security protocols and encryption, authentication, or access credentials configurations to access critical systems in your cloud and local
- Ensure that backups of critical systems are maintained which can be used to restore data in case a need arises.
MANAGEMENT RECOMMENDATIONS
- A data breach prevention plan must be developed considering, (a) the type of data being managed by the company; (b) the remediation process; (c) where and how the data is stored; (d) if there is an obligation to notify the local authority.
- Enable zero-trust architecture and multifactor authentication (MFA) to mitigate the compromise of credentials.
- Foster a culture of cybersecurity, where you encourage and invest in employee training so that security is an integral part of your organization.
TACTICAL RECOMMENDATIONS
- Update all applications/software regularly with the latest versions and security patches
- Add the Sigma rules for threat detection and monitoring which will help to detect anomalies in log events, identify and monitor suspicious activities.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence provided.
Trending Malware of the Week
Type: Trojan
Objective: Espionage, Stealing Banking Certificates & Keys Target Technology: Android OS
Target Geography: South Korea Target Industries: Banks
Active Malware of the Week
This week “SoumniBot” is trending
SoumniBot
Malware creators commonly use tools to impede code detection and analysis, and this applies to Android malware as well. For instance, droppers like Badpack and Hqwar are favored by malicious actors to discreetly distribute Trojan bankers or spyware on smartphones. However, researchers have identified a new malware called SoumniBot that specifically targets South Korean users. What distinguishes SoumniBot from others is its novel approach to evading analysis and detection: obfuscating the Android manifest, an unconventional technique in the world of malware.
Obfuscation of Android Manifest in SoumniBot Malware
The APK file format is essentially a ZIP archive, with the AndroidManifest.xml file located in the root directory. This manifest file provides essential details about an app’s components, permissions, and other metadata, assisting the operating system in accessing various entry points within the app. Similarly, analysts begin by examining the manifest to identify these entry points, which serve as the starting point for code analysis. The developers of SoumniBot likely targeted this process by researching the manifest parsing and extraction routine and discovering opportunities to obfuscate APKs effectively. SoumniBot employs several techniques to obfuscate its presence and thwart analysis.
Technique 1: Invalid Compression method value
The technique involves manipulating the Compression method field in APK files, specifically related to how manifests are unpacked. The standard unarchiving function in the libziparchive library only allows two Compression method values (0x0000 for uncompressed and 0x0008 for zlib compressed). However, the Android APK parser has an alternate implementation that incorrectly validates the Compression method field. If a value other than 0x0008 is encountered for the Compression method in the AndroidManifest.xml entry, the parser interprets the data as uncompressed, allowing the installation of the application. This method exploits a discrepancy in compression method validation, enabling malware like SoumniBot to evade detection during unpacking.
Technique 2: Invalid manifest size
The technique involves manipulating the size field of the AndroidManifest.xml entry within a ZIP archive. If the entry is stored uncompressed, the manifest file is copied from the archive unchanged, even if its size is stated incorrectly. The malware exploits this by stating a larger size for the archived manifest than its actual size, resulting in an overlay where additional content from the archive is appended to the unpacked manifest. Stricter manifest parsers would fail to read such files correctly, but the Android parser handles the invalid manifest without errors. Notably, Google’s official utility for analyzing APKs, apkanalyzer, cannot handle these files, and Google has been informed of this issue.
Technique 3: Long namespace names
The SoumniBot malware family utilizes a technique involving the use of very long strings as names for XML namespaces within the manifest. This causes the manifest to become unreadable for both humans and programs, potentially leading to memory allocation issues for programs attempting to process it. However, the manifest parser in the operating system (OS) completely ignores these namespaces, allowing the manifest to be processed without encountering errors despite its complexity and length.
Functionality and Behavior of SoumniBot Malware
Upon launch, the SoumniBot application initiates a request to a hardcoded server address to retrieve configuration parameters: mainsite (the mainsite server receives collected data) and mqtt (MQTT messaging functionality). These parameters are critical server addresses required for the malware’s operation. If the server fails to provide these parameters, default addresses stored within the code are used instead.
Following the parameter request, the application starts a malicious service. If this service fails to start or stops unexpectedly, the application retries every 16 minutes. Initially, when executed, the Trojan conceals its app icon to hinder removal and begins uploading data discreetly from the victim’s device to mainsite server every 15 seconds. This uploaded data typically includes the victim’s IP address, deduced country information, contact and account lists, SMS and MMS messages, and a victim’s ID generated using the trustdevice-android library. Additionally, the Trojan subscribes to messages from an MQTT server to receive the following specific commands for further actions:
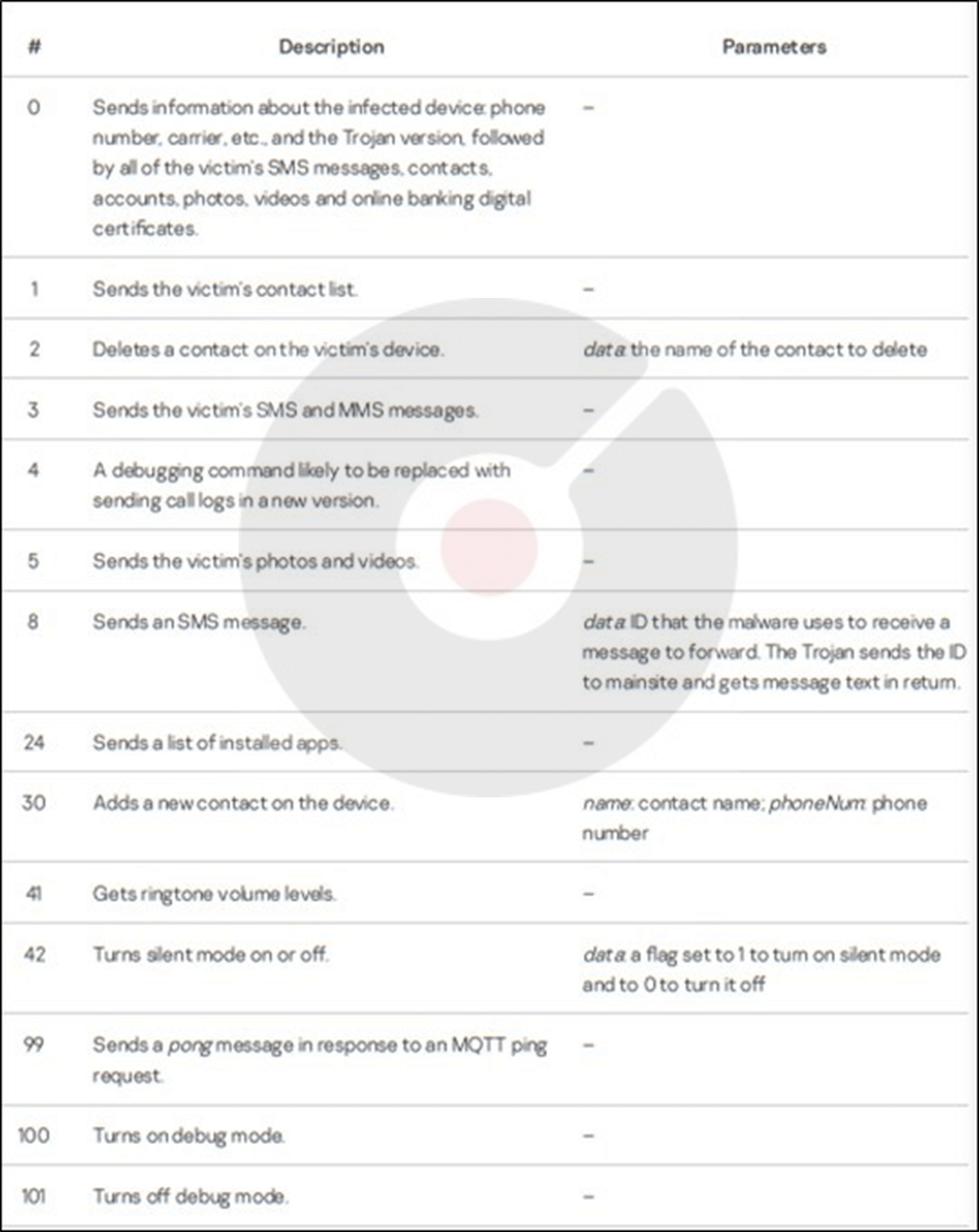
One notable command, specifically command number 0, involves searching external storage media for .key and .der files that contain paths to /NPKI/yessign. If found, the malware copies the directory containing these files into a ZIP archive and sends it to the command and control (C&C) server. These files typically represent digital certificates issued by South Korean banks to clients for online banking authentication and transaction confirmation. This approach is relatively uncommon for Android banking malware.
INSIGHTS
- SoumniBot represents an advanced form of Android malware distinguished by its utilization of unconventional obfuscation techniques and its focus on stealing South Korean online banking keys, a feature rarely observed in Android banking The malware employs sophisticated methods to evade detection, including manipulation of the Android manifest file and the use of extended XML namespace strings. These tactics demonstrate the evolving complexity of mobile malware.
- The capability of SoumniBot to steal South Korean online banking keys carries significant implications. By acquiring these keys, malicious actors can gain unauthorized access to victims’ bank accounts, enabling them to carry out financial transactions and potentially bypassing traditional bank authentication This poses a direct threat to users’ financial security.
- The success of SoumniBot in evading detection highlights the persistent challenge faced by security professionals in combating malware creators, who constantly seek new ways to infect devices discreetly. The developers of SoumniBot exploited insufficiently strict validations in the Android manifest parser code, allowing the malware to operate stealthily on infected devices. This underscores the importance of continuous improvement in detection mechanisms and security protocols to keep pace with evolving malware tactics.
ETLM ASSESSMENT
- From the ETLM perspective, CYFIRMA anticipates that the evolution of sophisticated malware like SoumniBot signals a challenging landscape for organizations and cybersecurity experts. As malware creators continue to exploit vulnerabilities in Android systems and employ advanced obfuscation techniques, the impact on organizations could become more severe. CYFIRMA believes that novel obfuscation techniques like those employed by SoumniBot will be adopted by other Android malware to evade detection in the future. The malware’s current targeting of South Korea, with an emphasis on stealing banking credentials and certificates, suggests that threats like SoumniBot could potentially broaden their scope to other regions and industries, leveraging similar tactics to target organizations in East Asia, Southeast Asia, Europe, the Americas, and beyond. Looking ahead, as malware tactics become more sophisticated, the impact on organizations could include financial losses, data breaches, and reputational damage.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
- Implement Mobile Device Management (MDM) policy to enhance corporate data security by monitoring, managing, and securing mobile devices such as laptops, smartphones, and tablets that are used in enterprises.
- Maintain an up-to-date inventory of all active software used within the organization and perform regular self-audit of workstations, servers, laptops, mobile devices to identify unauthorized/ restricted software.
- Configure organization’s intrusion detection systems (IDS), intrusion prevention systems (IPS), or any network defence mechanisms in place to alert on — and upon review, consider blocking connection attempts to and from — the external IP addresses and domains listed in the appendix.
MANAGEMENT RECOMMENDATIONS
- Secure your organization’s internet-facing assets with robust security protocols and encryption, including authentication or access credentials configuration, to ensure that critical information stored in databases/servers is always safe.
- Move beyond the traditional model of security awareness towards Improved Simulation and training exercises that mimic real attack scenarios, account for behaviors that lead to a compromise, and are measured against real attacks the organization receives.
- Incorporate a written software policy that educates employees on good practices in relation to software and potential implications of downloading and using restricted
TACTICAL RECOMMENDATIONS
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence provided.
- Use multi-factor authentication (MFA) to mitigate credential theft and prevent attacker access. Keep MFA always-on for privileged accounts and apply risk-based MFA for normal accounts.
- Enable Network traffic/security monitoring, security incident detection, notification, and alerting by leveraging SIEM solutions.
Weekly Intelligence Trends/Advisory
Weekly Attack Type and Trends
Key Intelligence Signals:
- Attack Type: Malware Implant, Ransomware Attacks, Vulnerabilities & Exploits, Data Leaks.
- Objective: Unauthorized Access, Data Theft, Data Encryption, Financial Gains,
- Business Impact: Data Loss, Financial Loss, Reputational Damage, Loss of Intellectual Property, Operational Disruption.
- Ransomware – BlackSuit Ransomware, RansomEXX Ransomware | Malware – SoumniBot
- BlackSuit Ransomware – One of the ransomware
- RansomEXX Ransomware – One of the ransomware
- Please refer to the trending malware advisory for details on the following:
- Behaviour –Most of these malwares use phishing and social engineering techniques as their initial attack vectors. Apart from these techniques, exploitation of vulnerabilities, defence evasion, and persistence tactics are being observed.
Threat Actor in Focus
Unveiling Forest Blizzard’s Exploitation Tactics: The GooseEgg
- Threat Actors: APT28
- Attack Type: Vulnerability & Exploits
- Objective: Espionage
- Target Technology: Windows
- Target Geographies: Ukrainian, Western European, USA
- Target Industries: Government, NGO, Education, Transportation sector
- Business Impact: Data Loss, Data exfiltration
Summary:
- Forest Blizzard, also known as STRONTIUM (APT28), is a Russian-based threat actor that primarily focuses on strategic intelligence gathering to support Russian government foreign policy Recent observations indicate that Forest Blizzard has employed a new malware called GooseEgg, which is a custom post-compromise tool. This tool is used to gain elevated access to target systems, steal credentials, and facilitate various malicious activities, including remote code execution, installing backdoors, and lateral movement within compromised networks.Forest Blizzard exploits CVE-2022-38028 (CVSS – 7.8) in Windows Print Spooler service using GooseEgg, which modifies a JavaScript constraints file to execute commands with SYSTEM-level permissions, allowing the actor to launch arbitrary executables or DLLs with elevated privileges. Windows-based systems are vulnerable to CVE-2022-38028 and associated with the Print Spooler service. Forest Blizzard employs sophisticated techniques to manipulate registry keys, create custom protocol handlers, and hijack symbolic links to redirect system processes and execute malicious code.
Forest Blizzard historically targeted government, energy, transportation, non- governmental organizations, media, information technology, sports organizations, and educational institutions primarily in the United States and Europe. In the observed activity, Forest Blizzard expanded its scope to encompass a broad spectrum of sectors, including government, energy, transportation, media, information technology, sports, and education, with a strategic focus on intelligence gathering. Specifically targeted geographies include entities in Ukraine, Western Europe, and North America. The exploitation of CVE-2022-38028 by Forest Blizzard poses significant risks to targeted organizations, leading to potential data breaches, credential theft, unauthorized access, and compromise of sensitive information. The actor’s activities can disrupt operations, compromise network integrity, and facilitate espionage activities aligned with Russian government interests. Organizations are urged to apply security updates and implement defensive measures to mitigate the threat posed by Forest Blizzard.
Relevancy & Insights:
- APT28, a Russian-based threat group, is known for its espionage activities aligned with Russian government interests. They exploit system vulnerabilities to gain unauthorized access, a tactic increasingly observed among threat actors. APT28’s use of customized malware like GooseEgg highlights their sophistication and adaptability in evading detection while escalating privileges and conducting further malicious activities within compromised networks. Understanding APT28’s tactics and motives is crucial for organizations to enhance their cybersecurity defences against such sophisticated
ETLM Assessment:
- APT28, also referred to as Fancy Bear and Forest Blizzard, is an advanced threat actor that systematically targets government, non-governmental, education, and transportation sector organizations across Ukraine, Western Europe, and North America. Exploiting the CVE-2022-38028 vulnerability and utilizing tools like GooseEgg, APT28 engages in sophisticated cyber espionage activities. Their objectives primarily revolve around gathering strategic intelligence to advance geopolitical interests, with a particular emphasis on exploiting vulnerabilities within critical infrastructure and high-value targets. The extensive scope of their targeting, spanning multiple industries and geographic regions, underscores the urgent need for proactive threat mitigation measures. Furthermore, CYFIRMA observed that along with APT28, Chinese threat actors like MISSION2025 and Stone Panda are also targeting CVE-2022-38028. Recently, the Cybersecurity and Infrastructure Security Agency (CISA) has added this particular vulnerability to its list of known vulnerabilities, emphasizing the importance of heightened vigilance and collaboration in defending against sophisticated cyber threats.
Recommendations:
- Employee Training and Awareness: It’s crucial to educate employees about the risks of phishing attacks, social engineering tactics, and the importance of cybersecurity hygiene. Regular training programs should be conducted to ensure that staff are well- informed and vigilant.
- Install the security updates released by Microsoft for the Print Spooler vulnerability (CVE-2022-38028) as soon as possible.
- Since the Print Spooler service is not required for domain controller operations, consider disabling it on domain controllers to mitigate the risk of exploitation.
- Implement credential hardening recommendations to defend against common credential theft techniques, such as securing LSASS access.
- Enable full automated mode for investigation and remediation in Microsoft Defender for Endpoint to allow immediate action on alerts and reduce alert volume.
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Major Geopolitical Developments in Cybersecurity
China used TikTok, AI, and big data to target Taiwan’s elections
- Taiwanese researchers issued a report on Chinese election meddling methods. Chinese operators cultivated TikTok influencers in Taiwan and elsewhere to spread specific disinformation, used government-related accounts and generative AI to push fake videos, and used third-party and other data to micro-target messages and influence campaigns to specific individuals, according to the report. China relies on a variety of conspiratorial themes in its messaging, such as that the United States is attempting to build bioweapons labs in Taiwan, that it is seeking to draw China into conflict, and that the United States is a poor ally because it’s on the verge of a civil
ETLM Assessment:
- China’s efforts in Taiwan provide a glimpse into tactics and techniques they could use on a global scale to undermine support for the Western institutions, inside and outside of the respective countries, both domestically in the West as well as in the regions where China intends to hold sway. Wider adoption of AI, and particularly large language models, could greatly improve the effectiveness of China’s disinformation campaigns, particularly when it comes to English-speaking countries. In the weeks leading up to the Taiwanese election, Chinese actors circulated on social media and through chain emails a 300-page e-book entitled “The Secret History of Tsai Jing-wen”, which contained scandalous and false claims that President Tsai (whose party included Beijing’s least preferred candidate William Lai) had gained power through sexual transactions. We have seen similar practices before, but the innovation has come in the form of videos on Instagram, YouTube, TikTok and other platforms, where credible AI-generated avatars – many of them posing as professional news anchors – read various juicy and scandalous revelations from the book. The book was thus primarily a script for the deepfakes, and it is quite possible that the book itself was “written” by AI. And such a process can be scaled up almost indefinitely today and similar tactics are to be expected to be employed in countries like the US in the coming election cycles.
US water treatment plants attacked by Russian hackers
- According to a recent report by researchers, a Russian military-affiliated hacking group infiltrated a Texas water treatment plant this winter, causing a system malfunction that forced a water tank to overflow, escalating concerns about the network security of similar U.S. facilities.
- The breach occurred at a water facility in Muleshoe near the New Mexico border and is the first known case perpetrated by Russia, joining Iran and China with the list of countries linked to similar incidents this year. Researchers are pointing towards Sandworm; a hacking operation that’s tied to Russia’s military intelligence directorate (GRU). Drinking water in the municipalities nearby was not affected, but there were related hacking attempts reported in other Texas towns.
ETLM Assessment:
- The Environmental Protection Agency and National Security Council urged US states last month to stay alert for Iranian and Chinese cyber threats targeting water sector infrastructure, however, the Russians have also joined the fray. Sandworm operatives have mainly focused on Ukrainian targets and have escalated their attacks since Russia’s invasion some two years ago, however, the group has a history of attacking the US and is notably linked to the crippling NotPetya cyberattacks from 2017 that impacted U.S. critical infrastructure.
- Drinking water and wastewater systems are an attractive target for cyberattacks because they are a lifeline critical infrastructure sector but often lack the resources and technical capacity to adopt rigorous cybersecurity practices. Moreover, there were further similar Russian-originated activities tracked by researchers, also tied to water system compromises in a French dam and Polish water utilities. Russia has been using these attacks as a tool of signaling in the international arena and is likely to double down on them in all NATO countries.
- The Russian campaign presents a significant proliferation risk for new cyber-attack concepts and methods. As the researchers note, continued advancements and in-the- wild use of the group’s information technology (IT) and OT cyber-attack capabilities have also likely lowered the barrier of entry for other state and non-state actors to replicate and develop their own cyber-attack programs.
Rise in Malware/Ransomware and Phishing
The BlackSuit Ransomware impacts the UPC Technology Corporation
- Attack Type: Ransomware
- Target Industry: Manufacturing
- Target Geography: Taiwan
- Ransomware: BlackSuit Ransomware
- Objective: Data Theft, Data Encryption, Financial Gains
- Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
- From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Taiwan; (www[.]upc [.]com[.]tw), was compromised by the BlackSuit Ransomware. UPC Technology Corporation manufactures and markets chemicals. The Company’s products include plasticizers and phthalic anhydride (PA). UPC also produces electrical chemicals and semiconductor materials. The Compromised data includes Business data (contracts, contacts, planning, presentations, etc), Employee data (passports, contracts, contacts, family details, medical examinations, etc), Product data (development, analysis, drawings, etc), Factories data (projects, reports, audits, etc), Production data (formulas, analysis, development, etc), Financial Data (audits, reports, payments, contracts, etc), Construction data (blueprints, planning, construction details, etc), and other data taken from shared and personal folders. The total size of the compromised data is 470GB.
The following screenshot was observed published on the dark web:
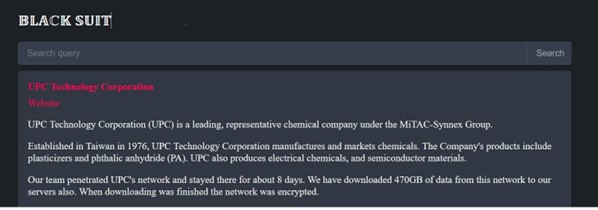
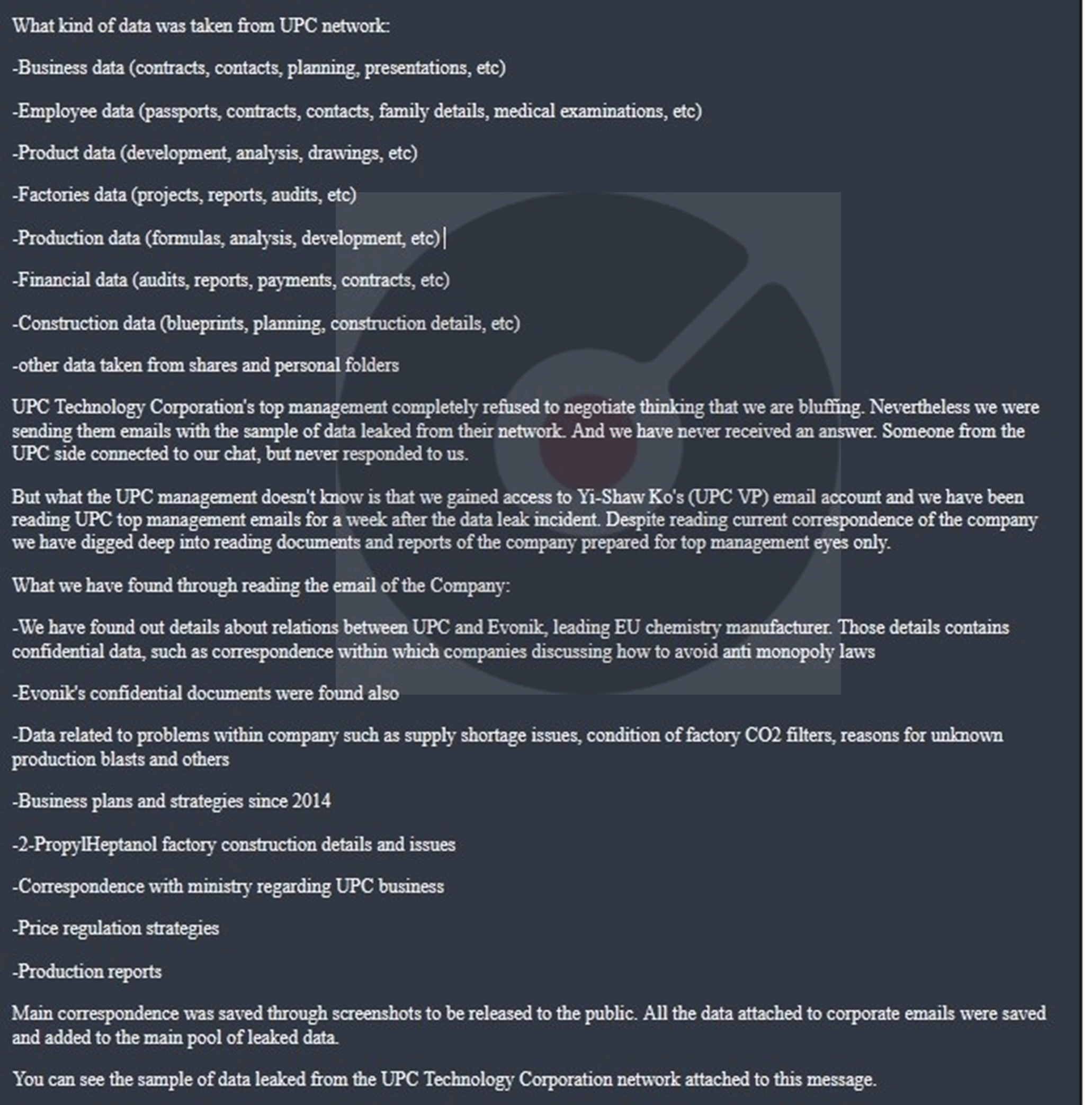
Source: Dark Web
Relevancy & Insights:
- The BlackSuit ransomware operation emerged in early May of 2023. The group is a multi-pronged extortion outfit, encrypting and exfiltrating victim data and hosting public data leak sites for those victims who fail to comply with their demands. The group is known for significant attacks against entities in the healthcare and education sectors, along with other critical industries. BlackSuit is a private operation in that there are no public affiliates. BlackSuit payloads contain many technical similarities to Royal ransomware payloads such as similar encryption mechanisms and command-line
- The group emerged with payloads that support both Windows and Linux operating systems. Payloads are delivered via phishing email or third-party framework (e.g., Empire, Metasploit, Cobalt Strike). The use of malicious torrent files has also been observed as a delivery vector for BlackSuit ransomware.
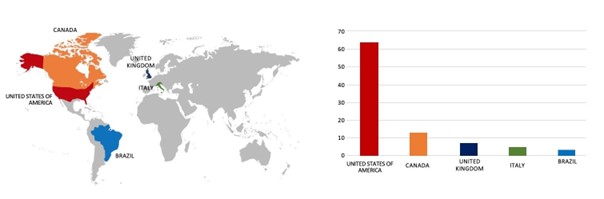
- The BlackSuit Ransomware group primarily targets countries such as the United States of America, Canada, the United Kingdom, Italy, and Brazil.
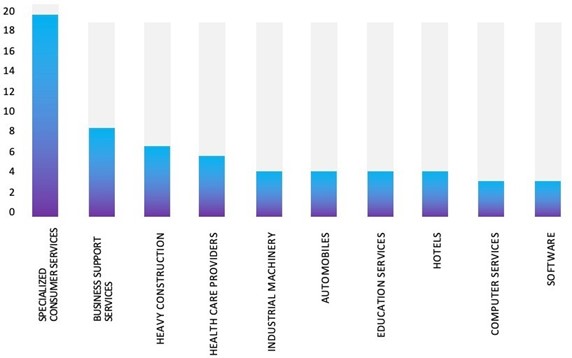
- The BlackSuit Ransomware group primarily targets industries, such as Specialized Consumer Services, Business Support Services, Heavy Construction, Health Care Providers, and Industrial Machinery.
- Based on the BlackSuit Ransomware victims list from 1st Jan 2023 to 24 April 2024, the top 5 Target Countries are as follows:
- The Top 10 Industries, most affected by BlackSuit Ransomware from 1 Jan 2023 to 24 April 2024 are as follows:
ETLM Assessment:
- BlackSuit Ransomware is a private ransomware/extortion Large enterprises and small to medium-sized businesses (SMBs) are targeted, though there does not appear to be any specific discrimination when it comes to industry or type of target. Similar to Royal, targeting of entities in the CIS (Commonwealth of Independent States) appears to be excluded. To date, BlackSuit targeting has favored those in the healthcare, education, information technology (IT), government, retail, and manufacturing industries. Based on the available information, CYFIRMA’s assessment indicates that BlackSuit Ransomware will continue to target various industries globally, with a significant emphasis on the United States, European, and Asian regions. The recent breach targeting UPC Technology Corporation, a leading manufacturing firm based in Taiwan, serves as a potential indicator of BlackSuit Ransomware’s inclination towards targeting organizations across Southeast Asia.
The RansomEXX Ransomware impacts the Asteco
- Attack Type: Ransomware
- Target Industry: Real Estate
- Target Geography: The United Arab Emirates (UAE)
- Ransomware: RansomEXX Ransomware
- Objective: Data Theft, Data Encryption, Financial Gains
- Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the United Arab Emirates (UAE); (www[.]asteco[.]com), was compromised by the RansomEXX Ransomware. Asteco is a real estate services firm based in the United Arab Emirates (UAE), with its headquarters in Dubai. It offers a wide range of real estate services including property management, valuation, research, investment consultancy, and sales and leasing brokerage. Asteco has been a prominent player in the UAE’s real estate market for several years, providing services to both individual clients and corporate entities. The compromised data contains highly confidential and sensitive information relevant to the organization. Altogether, the compromised data comprises 11.4 gigabytes.
The following screenshot was observed published on the dark web:
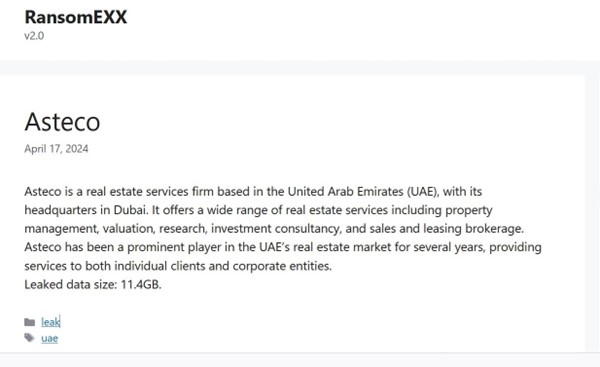
Source: Dark Web
Relevancy & Insights:
- RansomEXX (aka Defray, Defray777), a multi-pronged extortion threat, has been observed in the wild since late 2020. RansomEXX is associated with attacks against the Texas Department of Transportation, Groupe Atlantic, and several other large enterprises. There are Windows and Linux variants of this ransomware family, and they are known for their limited and exclusive targeting.
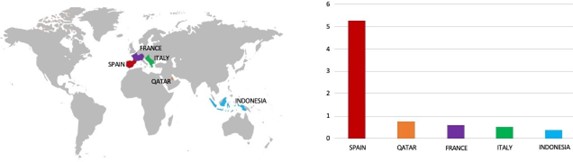
- RansomEXX Ransomware group primarily targets countries such as Spain, Qatar, France, Italy, and Indonesia.
- RansomEXX Ransomware group primarily targets industries, such as Recreational Services, Heavy Construction, Software, Accounting, and Telecommunications.
- Based on the RansomEXX Ransomware victims list from 1 Jan 2023 to 24 April 2024, the top 5 Target Countries are as follows:
- The Top 5 Industries, most affected by RansomEXX Ransomware from 1st Jan 2023 to 24 April 2024 are as follows:
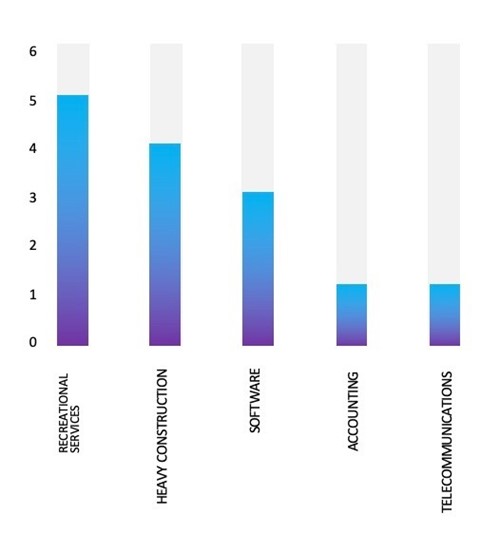
ETLM Assessment:
RansomEXX ransomware is known to target large enterprises and high-value targets. They have also been known to focus on those in the government, Informational Technology, and healthcare sectors as well as high-value manufacturing entities. RansomEXX ransomware targets its victims through phishing and spear phishing emails. They are also known to leverage exposed and vulnerable applications and services such as remote desktop protocol (RDP) and third-party frameworks (e.g., Vatet Loader, Metasploit, Cobalt Strike).
Based on CYFIRMA’s assessment, RansomEXX ransomware targets worldwide organizations. The attack on Asteco also highlights ransomware groups’ interest in Asian organizations that are financially strong in the region with exploitable vulnerabilities.
Vulnerabilities and Exploits
Vulnerability in Wazuh
- Attack Type: Vulnerabilities & Exploits
- Target Technology: Server application
- Vulnerability: CVE-2023-49275(CVSS Base Score 5)
- Vulnerability Type: NULL Pointer Dereference
Summary:
- The vulnerability allows a remote attacker to perform a denial of service (DoS) Relevancy & Insights:
- The vulnerability exists due to a NULL pointer dereference error in wazuh-
Impact:
- A remote attacker can pass specially crafted data to the application and perform a denial of service (DoS) attack.
Affected Products: https[:]//github[.]com/wazuh/wazuh/security/advisories/GHSA-4mq7- w9r6-9975
Recommendations:
- Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
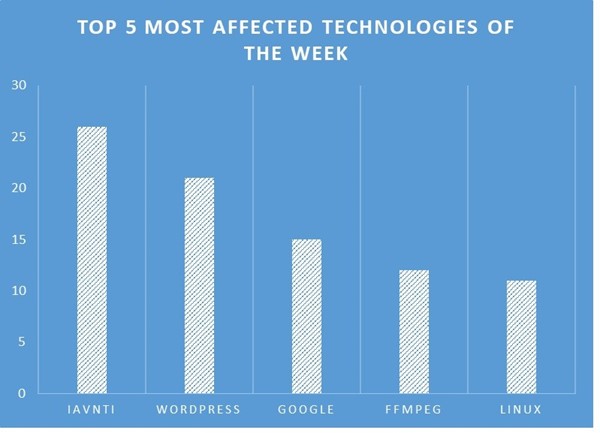
ETLM Assessment:
Wazuh, a critical server application for security monitoring and intrusion detection, plays a pivotal role across diverse sectors, including technology, finance, healthcare, and e- commerce. Vulnerabilities within Wazuh could have far-reaching implications, potentially disrupting operations and compromising security.
Latest Cyber-Attacks, Incidents, and Breaches
Darkvault Ransomware attacked and Published data of Agribazaar
- Threat Actors: Darkvault Ransomware
- Attack Type: Ransomware
- Objective: Data Leak, Financial Gains
- Target Technology: Web Application
- Target Geographies: India
- Target Industry: Agriculture and Agribusiness
- Business Impact: Operational Disruption, Data Loss, Financial Loss, Potential Reputational Damage
Summary:
- Recently we observed that Darkvault Ransomware attacked and Published data of Agribazaar on its darkweb website. AgriBazaar(www[.]agribazaar[.]com) is an online marketplace that operates under the aegis of StarAgri – one of Asia’s leading agri- solutions With a vision to create a holistic trading platform that will provide end-to-end services, StarAgri has launched AgriBazaar – a cutting-edge technology platform managed by top-of-the-line, experienced IT professionals. The result is a digital destination that will integrate fragmented agri-commodity trading securely and conveniently. StarAgri has been delivering integrated post-harvest solutions, including warehousing, collateral financing, and value-added services to enhance efficiency across the entire food supply chain. The breached data contains highly confidential and sensitive information about the organization.
Source: Dark Web
Relevancy & Insights:
- DarkVault is a self-proclaimed exclusive online community and ransomware operation that performs many illegal activities, including bomb threats, swatting, doxing, website defacing, malware creation, scams, spam, and various amounts of fraud. It’s probably a few individuals engaged in a bunch of cybercrimes.
ETLM Assessment:
- It appears that the DARKVAULT ransomware is quite new, as evidenced by its recent emergence and rapid targeting of nine victims within a short timeframe. However, despite its novelty, the sophistication of its operations, coupled with the geographical spread of its victims across four countries the US, India, Sri Lanka, and the UK, suggests a high level of organization and possibly prior experience in cybercrime. Additionally, the focus on Asian nations, as indicated by ongoing assessments by CYFIRMA, highlights a strategic shift towards regions with potentially lucrative financial targets. This trend underscores the evolving nature of cyber threats and the need for heightened vigilance and cybersecurity measures, particularly in vulnerable sectors and regions.
Data Leaks
Mineral Alam Abadi Group data advertised on a Leak Site
- Attack Type: Data Leak
- Target Industry: Mining
- Target Geography: Indonesia
- Objective: Data Theft, Financial Gains
- Business Impact: Data Loss, Reputational Damage
Summary:
- The CYFIRMA Research team observed a potential data leak related to Mineral Alam Abadi Group, {www[.]maagroup[.]co[.]id} in an underground Mineral Alam Abadi Group is the holding company of several companies engaged in Nickel Mining, Nickel Trading, Stone mining, Mining Investment, and Sea Transportation Services. The compromised data includes sensitive Employee data, encompassing Employee ID, Full Name, Barcode, Organization, Job Position, Job Level, Join Date, Resign Date, Employee Status, End Date, Sign Date, Email, Birth Date, Age, Birthplace, Citizen ID, Address, Residential Address, and other highly confidential information. The data breach has been attributed to a threat actor identified as ‘Sedapmalam’.
Source: Underground Forums
Askara Internal data advertised on a Leak Site
- Attack Type: Data Leak
- Target Industry: Manufacturing
- Target Geography: Indonesia
- Objective: Data Theft, Financial Gains
- Business Impact: Data Loss, Reputational Damage
Summary:
- CYFIRMA Research team observed a potential data sale related to PT. Askara Internal, {www[.]myrepublic[.]co[.]id} in an underground PT. Askara Internal is a company engaged in the procurement of a wide range of industrial needs, both goods and services. The compromised data contains sensitive Employee information, including Employee ID, Full Name, Barcode, Organization, Job Position, Job Level, Join Date, Resign Date, Employment Status, End Date, Sign Date, Email Address, Birth Date, Birthplace, Citizen ID, Residential Address, and other confidential and sensitive details. The data breach has been attributed to a threat actor identified as ‘Sedapmalam’.


Source: Underground Forums
Relevancy & Insights:
- Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
- Based on CYFIRMA’s assessment, the financially motivated threat actor known as ‘Sedapmalam’ poses a significant risk to organizations, as they are known to target any institution and profit from selling sensitive data on the dark web or underground The organizations targeted by ‘Sedapmalam’ typically have inadequate security measures in place, rendering them vulnerable to potential cyberattacks orchestrated by this threat actor.
Recommendations:
- Enhance the cybersecurity posture by Updating all software products to their latest versions is essential to mitigate the risk of vulnerabilities being exploited.
- Ensure proper database configuration to mitigate the risk of database-related
- Establish robust password management policies, incorporating multi-factor authentication and role-based access, to fortify credential security and prevent unauthorized access.
Other Observations
- CYFIRMA Research team observed a potential data leak related to BTC Cash. IntelBroker claims to have leaked the source code for BTC Cash from both private and public repositories.
Source: Underground forums
ETLM Assessment:
IntelBroker threat actor group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries, indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
- Attack Surface Management should be adopted by organizations, ensuring that a continuous closed-loop process is created between attack surface monitoring and security testing.
- Deploy a unified threat management strategy – including malware detection, deep learning neural networks, and anti-exploit technology – combined with vulnerability and risk mitigation processes.
- Incorporate Digital Risk Protection (DRP) in the overall security posture that acts as a proactive defence against external threats targeting unsuspecting customers.
- Implement a holistic security strategy that includes controls for attack surface reduction, effective patch management, active network monitoring, through next generation security solutions and ready to go incident response plan.
- Create risk-based vulnerability management with deep knowledge about each asset. Assign a triaged risk score based on the type of vulnerability and criticality of the asset to help ensure that the most severe and dangerous vulnerabilities are dealt with first.
MANAGEMENT RECOMMENDATIONS
- Take advantage of global Cyber Intelligence providing valuable insights on threat actor activity, detection, and mitigation techniques.
- Proactively monitor the effectiveness of risk-based information security strategy, the security controls applied and the proper implementation of security technologies, followed by corrective actions remediations, and lessons learned.
- Move beyond the traditional model of security awareness towards improved simulation and training exercises that mimic real attack scenarios, account for behaviours that lead to a compromised and are measured against real attacks the organization receives.
- Consider implementing Network Traffic Analysis (NTA) and Network Detection and Response (NDR) security systems to compensate for the shortcoming of EDR and SIEM solutions.
- Detection processes are tested to ensure awareness of anomalous Timely communication of anomalies and continuously evolved to keep up with refined ransomware threats.
TACTICAL RECOMMENDATIONS
- Patch software/applications as soon as updates are available. Where feasible, automated remediation should be deployed since vulnerabilities are one of the top attack vectors.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthen defences based on tactical intelligence provided.
- Deploy detection technologies that are behavioural anomaly-based to detect ransomware attacks and help to take appropriate measures.
- Implement a combination of security control such as reCAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart), Device fingerprinting, IP backlisting, Rate-limiting, and Account lockout to thwart automated brute-force attacks.
- Ensure email and web content filtering uses real-time blocklists, reputation services, and other similar mechanisms to avoid accepting content from known and potentially malicious sources.
Situational Awareness – Cyber News
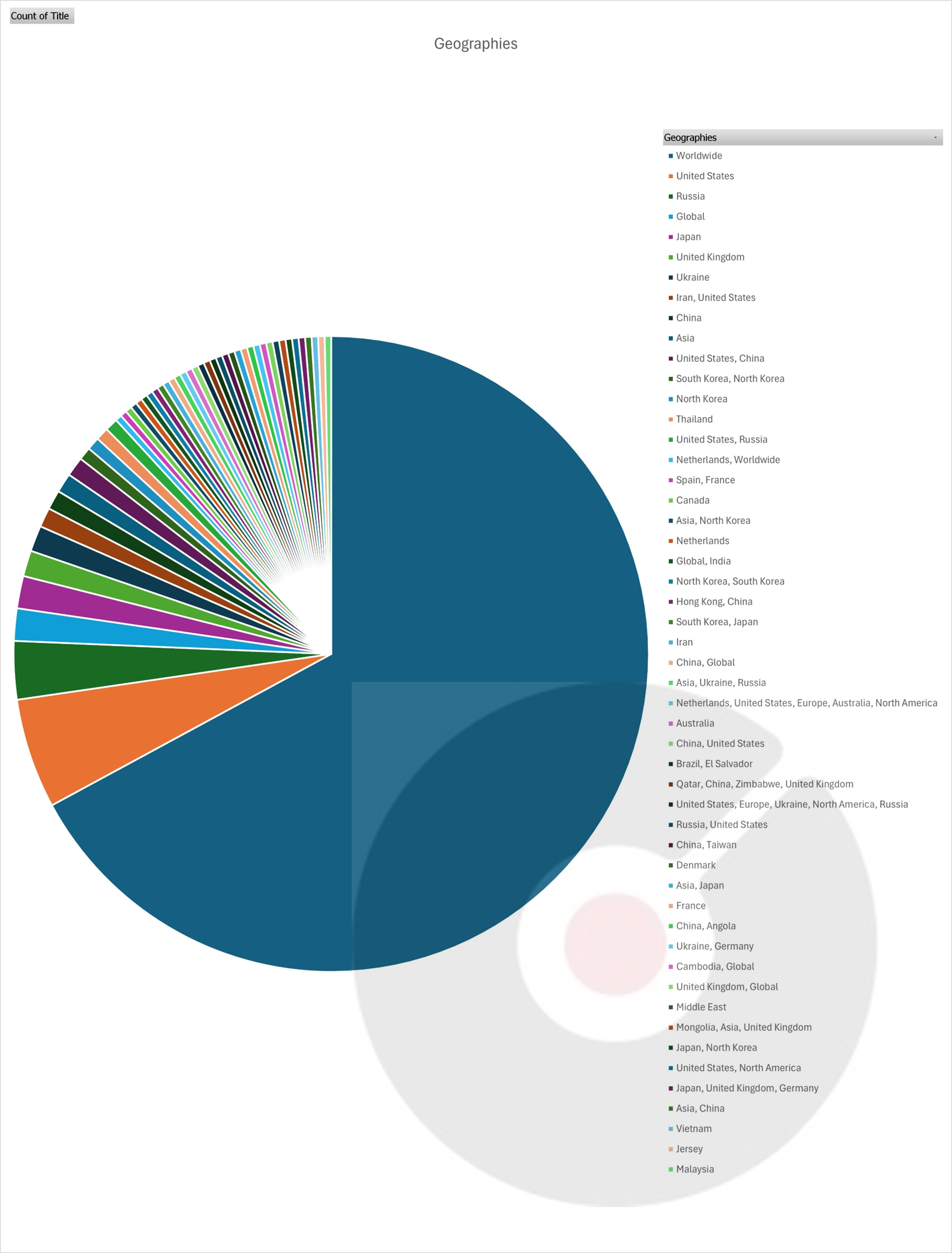
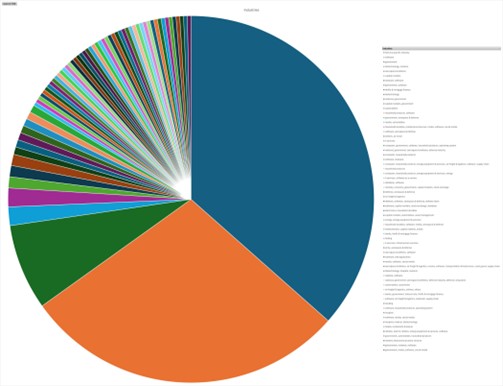
Please find the Geography – Wise and Industry – Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.






















