


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows
Introduction
CYFIRMA Research and Advisory Team has found Prey Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Prey Ransomware
Researchers have identified a new ransomware variant named Prey, a member of the MedusaLocker family. This malware uses a combination of RSA and AES encryption algorithms to lock user data and appends the “.prey35” extension to affected files.
During execution, it alters system configurations, replaces the desktop wallpaper, and drops an HTML ransom note named HOW_TO_RECOVER_DATA.html. Prey disables system recovery features and removes shadow volume copies to prevent file restoration. It is typically distributed through infected email attachments, malicious downloads, and exploit-based delivery methods, using standard MedusaLocker mechanisms to execute its encryption payload.
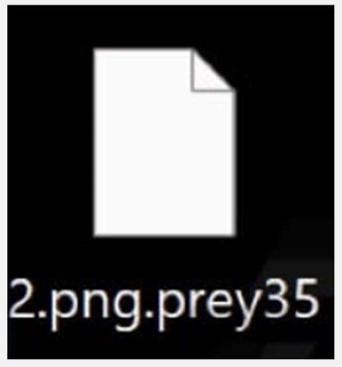
Screenshot of files encrypted by ransomware (Source: Surface Web)
The ransom note left by Prey specifies that the victim’s files have been encrypted and sensitive data exfiltrated. It clearly states that decryption is only possible through the attackers and warns that third-party tools or modifications can permanently damage the files. The message provides two contact emails sets a 72-hour deadline before the ransom increases. Victims are also informed that refusal to pay will lead to the public exposure of the stolen information, illustrating the data theft and extortion approach characteristic of this ransomware.
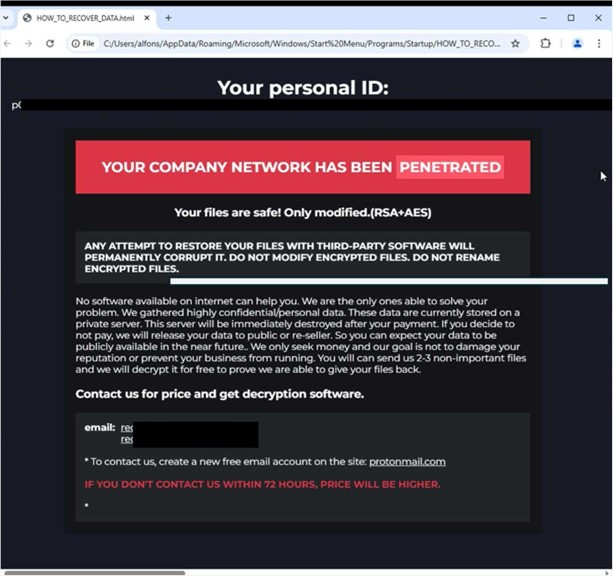
The appearance of Prey’s ransom note (HOW_TO_RECOVER_DATA.html) (Source: Surface Web)
The following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1129 | Shared Modules |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1134 | Access Token Manipulation |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
|
Defense Evasion |
T1027.005 |
Obfuscated Files or Information: Indicator Removal from Tools |
|
Defense Evasion |
T1027.009 |
Obfuscated Files or Information: Embedded Payloads |
| Defense Evasion | T1134 | Access Token Manipulation |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1518 | Software Discovery |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1090 | Proxy |
| Command and Control | T1571 | Non-Standard Port |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1489 | Service Stop |
| Impact | T1529 | System Shutdown/Reboot |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment indicates that Prey currently gains access primarily through social-engineering vectors (malicious attachments, trojanized downloads) that convince users to execute the payload. Once active, it encrypts files using RSA/AES, deletes local recovery artifacts (shadow copies, backups), establishes simple persistence, and drops a ransom note instructing victims to contact specific email addresses leveraging the threat of data disclosure to pressure payment (double-extortion rhetoric is present in the note).
Prey could evolve into a more capable and modular threat: operators may harden its encryption/key management to eliminate recoverable flaws, add robust C2 redundancy (Tor/IM proxies and encrypted beaconing), and expand lateral-movement tooling (credential theft, pass-the-hash, and exploit modules) to reach high-value assets faster. We assess a high likelihood of expanded double-extortion behavior (automated exfiltration pipelines and leak sites), a move toward a Ransomware-as-a-Service model or third-party affiliate network to increase scale, and greater use of living-off-the-land and fileless techniques plus sandbox/anti-debug checks to frustrate detection. Functionally, this would make Prey more evasive (process hollowing, polymorphic payloads), more persistent (service/backdoor installers and cloud-backup targeting), and more destructive to recovery options (targeted removal of on-host and cloud snapshots). These trajectories imply that defensive focus should shift toward robust offline/immutable backups, credential hygiene, network segmentation, and telemetry that catches early lateral movement and abnormal uses of native admin tools.
Sigma rule:
title: New RUN Key Pointing to Suspicious Folder tags:
– attack.t1547.001 logsource:
category: registry_set product: windows
detection: selection_target:
TargetObject|contains:
– ‘%tmp%’
Details|contains: ‘:\Users\’ selection_suspicious_paths_user_2:
Details|contains:
TargetObject|contains: ‘\Microsoft\Windows\CurrentVersion\RunOnce\’ Image|startswith: ‘C:\Windows\SoftwareDistribution\Download\’ Details|contains|all:
Image|endswith:
TargetObject|endswith: ‘SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Spotify’ Details|endswith: ‘Spotify.exe –autostart –minimized’
condition: selection_target and (selection_suspicious_paths_1 or (all of selection_suspicious_paths_user_* )) and not 1 of filter_main_* and not 1 of filter_optional_*
falsepositives:
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Trojan | Objectives: Credential theft, Financial Fraud, Data exfiltration | Target Technologies: Windows OS, Browsers| Target Industry: Finance sector (banking & crypto services) | Target Geography: Brazil
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “Maverick” is trending.
Overview of Maverick Malware
Researchers discovered a new Brazilian banking Trojan named Maverick, spread through WhatsApp using ZIP files containing a malicious shortcut that bypasses the platform’s security. Once installed, the malware ensures the victim is in Brazil by checking system settings and then hijacks WhatsApp accounts to propagate itself further. Maverick can take full control of infected machines, capturing screens, monitoring browser activity, logging keystrokes, controlling the mouse, blocking the screen when accessing banking websites, and displaying phishing overlays to steal credentials. It specifically targets 26 Brazilian banks, six cryptocurrency exchanges, and one payment platform. The Trojan operates stealthily in memory with minimal disk activity, leveraging PowerShell, .NET, and encrypted shellcode, and its development involved AI-assisted coding, particularly for certificate decryption and other functions, highlighting a sophisticated and highly targeted financial threat.
Attack Method
The infection begins when a user receives a ZIP over WhatsApp containing a malicious shortcut; opening it launches a memory-resident bootstrap that fetches further components from the attacker without dropping obvious files on disk. This initial stage is designed to run covertly and loads additional pieces directly into memory, limiting forensic traces and making the campaign harder to detect with simple file-scanning tools.
From there, the compromise splits into two distinct flows: one branch loads a banker module that stays resident to watch browsers and act when users visit targeted financial sites, while the other installs a WhatsApp automation module that takes over the victim’s session to spam their contacts and amplify the campaign. The messaging infector uses web automation tooling to instrument the user’s WhatsApp session and send the malicious lure, and the banking branch only activates the heavy credential-stealing logic when it recognizes a target site in the browser.
Persistence is intentionally lightweight: the malware writes a small startup launcher that reconstructs the in-memory bootstrap on reboot rather than storing the full payload on disk, because the operation depends on the attacker’s command server being reachable. The campaign also enforces strict geographic checks — time zone, locale and date format — so the intrusive banker functionality will only run on machines configured for Brazil, while all control traffic is protected and authenticated to prevent trivial download or replay by benign HTTP clients.
Following are the TTPs based on the MITRE Attack Framework for Enterprise
| Tactic | Technique ID | Technique name |
| Initial Access | T1566.001 | Phishing: Spearphishing Attachment |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command
Shell |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys /
Startup Folder |
| Defense
Evasion |
T1027 | Obfuscated Files or Information |
| Defense
Evasion |
T1027.004 | Obfuscated Files: Compile After Delivery |
| Defense
Evasion |
T1055 | Process Injection |
| Credential
Access |
T1056.001 | Input Capture: Keylogging |
| Credential
Access |
T1056.002 | Input Capture: GUI Input Capture |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1057 | Process Discovery |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1056.002 | Input Capture: GUI Input Capture |
| Collection | T1113 | Screen Capture |
| Command and
Control |
T1071.001 | Application Layer Protocol: Web Protocols |
| Command and
Control |
T1573 | Encrypted Channel |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| Impact | T1529 | System Shutdown/Reboot |
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that Maverick-like campaigns are likely to increase pressure on organizations and employees by blurring the line between personal and corporate digital spaces, as malware spreads through trusted messaging platforms and exploits familiar contacts. Employees may face higher risks of inadvertent data exposure or credential compromise, while organizations could see a rise in account takeovers that indirectly impact internal systems and workflows. The campaign’s modular and memory-resident nature suggests future variants could adapt quickly to new environments, targeting specific roles or departments, and amplifying social engineering attacks through hijacked communication channels. This evolution will likely demand heightened vigilance in monitoring unusual account behavior, managing digital trust among staff, and responding to rapidly propagating threats that bypass traditional endpoint protections.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rule:
rule Maverick_Suspicious_Domains_and_IPs
{
meta:
description = “Detects domains and IPs associated with Maverick malware” author = “CYFIRMA”
malware = “Maverick”
strings:
// Domains
$domain_1 = “sorvetenopote.com”
$domain_2 = “casadecampoamazonas.com”
// IP Addresses
$ip_1 = “77.111.101.169”
$ip_2 = “181.41.201.184”
condition:
any of ($domain*) or any of ($ip*)
}
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Please refer to the trending malware advisory for details on the following:
OceanLotus (APT32): Evolving Threats in the APAC Cyber Landscape
About the Threat Actor
OCEANLOTUS, also known as APT-C-00, SeaLotus, or Cobalt Kitty, is a sophisticated threat actor group believed to be affiliated with the Vietnamese government. The group has been active since at least 2013 and primarily operates in the Asia-Pacific (APAC) region. The group is known for using custom malware, spear-phishing campaigns, and advanced persistence techniques. Cyber Threat Intelligence (CTI) assesses that OCEANLOTUS is financially motivated, based on its consistent targeting of private sector entities. Its activities suggest a blend of espionage and economic objectives, making it a significant threat to both regional and international organizations.
Details on Exploited Vulnerabilities
| CVE ID |
Affected Products |
CVSS Score |
Exploit Links |
|
CVE-2017-11882 |
Microsoft Office |
7.8 |
link |
|
CVE-2020-0688 |
Microsoft Exchange software |
8.8 |
Link1, link2 |
|
CVE-2016-7255 |
Windows Server |
7.8 |
Link1, link2, link3, link4 |
|
CVE-2020-14882 |
Oracle WebLogic Server |
9.8 |
Link1, link2, link3 |
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Reconnaissance | T1589 | Gather Victim Identity Information |
| Reconnaissance | T1589.002 | Gather Victim Identity Information: Email
Addresses |
| Reconnaissance | T1598.003 | Phishing for Information: Spearphishing Link |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains |
| Resource Development | T1583.006 | Acquire Infrastructure: Web Services |
| Resource Development | T1585.001 | Establish Accounts: Social Media Accounts |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Resource Development | T1608.001 | Stage Capabilities: Upload Malware |
| Resource Development | T1608.004 | Stage Capabilities: Drive-by Target |
| Initial Access | T1189 | Drive-by Compromise |
| Initial Access | T1078.003 | Valid Accounts: Local Accounts |
| Initial Access | T1566.001 | Phishing: Spearphishing Attachment |
| Initial Access | T1566.002 | Phishing: Spearphishing Link |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1059.001 | Command and Scripting Interpreter:
PowerShell |
| Execution | T1059.003 | Command and Scripting Interpreter:
Windows Command Shell |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual
Basic |
| Execution | T1059.007 | Command and Scripting Interpreter:
JavaScript |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Execution | T1072 | Software Deployment Tools |
| Execution | T1569.002 | System Services: Service Execution |
| Execution | T1204.001 | User Execution: Malicious Link |
| Execution | T1204.002 | User Execution: Malicious File |
| Execution | T1047 | Windows Management Instrumentation |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry
Run Keys / Startup Folder |
| Persistence | T1543.003 | Create or Modify System Process: Windows
Service |
| Persistence | T1574.001 | Hijack Execution Flow: DLL |
| Persistence | T1112 | Modify Registry |
| Persistence | T1137 | Office Application Startup |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Persistence | T1505.003 | Server Software Component: Web Shell |
| Persistence | T1078.003 | Valid Accounts: Local Accounts |
| Privilege Escalation | T1078.003 | Valid Accounts: Local Accounts |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1068 | Exploitation for Privilege Escalation |
| Privilege Escalation | T1574.001 | Hijack Execution Flow: DLL |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1053.005 | Scheduled Task/Job: Scheduled Task |
|
Defense Evasion |
T1550.003 | Use Alternate Authentication Material: Pass the Ticket |
| Defense Evasion | T1218.005 | System Binary Proxy Execution: Mshta |
| Defense Evasion | T1218.010 | System Binary Proxy Execution: Regsvr32 |
| Defense Evasion | T1218.011 | System Binary Proxy Execution: Rundll32 |
| Defense Evasion | T1216.001 | System Script Proxy Execution: PubPrn |
| Defense Evasion | T1550.002 | Use Alternate Authentication Material: Pass the Hash |
| Defense Evasion | T1027.013 | Obfuscated Files or Information: Encrypted/Encoded File |
| Defense Evasion | T1027.016 | Obfuscated Files or Information: Junk Code Insertion |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1036.003 | Masquerading: Rename Legitimate Utilities |
| Defense Evasion | T1036.004 | Masquerading: Masquerade Task or Service |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1027.010 | Obfuscated Files or Information: Command Obfuscation |
| Defense Evasion | T1027.011 | Obfuscated Files or Information: Fileless Storage |
| Defense Evasion | T1078.003 | Valid Accounts: Local Accounts |
| Defense Evasion | T1055 | Process Injection |
|
Defense Evasion |
T1222.002 |
File and Directory Permissions Modification: Linux and Mac File and Directory Permissions Modification |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Defense Evasion | T1564.004 | Hide Artifacts: NTFS File Attributes |
| Defense Evasion | T1574.001 | Hijack Execution Flow: DLL |
| Defense Evasion | T1070.001 | Indicator Removal: Clear Windows Event Logs |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1078.004 | Valid Accounts: Cloud Accounts |
| Defense Evasion | T1070.006 | Indicator Removal: Timestomp |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Credential Access | T1552.002 | Unsecured Credentials: Credentials in Registry |
| Credential Access | T1003 | OS Credential Dumping |
| Credential Access | T1003.001 | OS Credential Dumping: LSASS Memory |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1135 | Network Share Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1078.003 | Valid Accounts: Local Accounts |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1049 | System Network Connections Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Discovery | T1046 | Network Service Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1018 | Remote System Discovery |
| Lateral Movement | T1021.007 | Remote Services: Cloud Services |
| Lateral Movement | T1570 | Lateral Tool Transfer |
| Lateral Movement | T1021.002 | Remote Services: SMB/Windows Admin Shares |
| Lateral Movement | T1072 | Software Deployment Tools |
|
Lateral Movement |
T1550.002 |
Use Alternate Authentication Material: Pass the Hash |
|
Lateral Movement |
T1550.003 |
Use Alternate Authentication Material: Pass the Ticket |
| Collection | T1560 | Archive Collected Data |
| Collection | T1056.001 | Input Capture: Keylogging |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1071.003 | Application Layer Protocol: Mail Protocols |
| Command and Control | T1571 | Non-Standard Port |
| Command and Control | T1102 | Web Service |
|
Exfiltration |
T1048.003 |
Exfiltration Over Alternative Protocol: Exfiltration Over Unencrypted Non-C2 Protocol |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
Latest Developments Observed
The threat actor is suspected of targeting government, defense, and research organizations across China and Southeast Asian nations. The group is assessed to be leveraging the Havoc Demon Remote Access Trojan (RAT), which establishes communication with its command-and-control (C2) server through DLL hollowing techniques and is executed using a callback mechanism via VEH (Vectored Exception Handling). The actor’s primary objective appears to be information theft, indicating a focus on espionage-oriented operations.
ETLM Insights
OceanLotus remains an active, politically motivated espionage group assessed to be aligned with Vietnamese state interests. The group has increasingly shifted its focus towards opportunistic supply-chain and software-dependency targeting, exploiting the weakest security links within interconnected ecosystems. OceanLotus is known for maintaining long periods of operational dormancy between campaigns, suggesting extensive reconnaissance and preparation prior to execution. This deliberate and patient approach underscores their emphasis on precision and impact.
Looking ahead, OceanLotus is expected to further refine its stealth and evasion capabilities, enhance operational security, and potentially increase collaboration with other regional or state-aligned threat actors to expand reach and sophistication. Organizations with exposure to Southeast Asia, or dependencies on regional technology suppliers, should anticipate continued and evolving targeting from this group.
YARA Rules
rule OceanLotus_Suspected_Campaign_Indicators
{
meta:
author = “CYFIRMA” date = “2025-10-16”
threat_actor = “OceanLotus / APT32”
strings:
$cve1 = “CVE-2017-11882” fullword ascii
$cve2 = “CVE-2020-0688” fullword ascii
$cve3 = “CVE-2016-7255” fullword ascii
$cve4 = “CVE-2020-14882” fullword ascii
$cve5 = “CVE-2020-0968” fullword ascii
$cve6 = “CVE-2021-40444” fullword ascii
$cve7 = “CVE-2021-44832” fullword ascii
$cve8 = “CVE-2021-45105” fullword ascii
$cve9 = “CVE-2021-22986” fullword ascii
/* IP addresses */
$ip1 = “50.63.202.51”
$ip2 = “127.0.0.1”
$ip3 = “204.79.197.200”
$ip4 = “46.105.57.169”
/* Domains */|
$d1 = “appointmentmedia.com” nocase
$d2 = “hosting-wordpress-services.com” nocase
$d3 = “toppaperservices.com” nocase
$d4 = “webmanufacturers.com” nocase
$d5 = “stablewindowsapp.com” nocase
/* Filenames and artifacts */
$f1 = “win32 exe” nocase
$f2 = “js:1428.js” nocase
$f3 = “spofer fortnite.exe” nocase
/* Hash / suspicious string */
$h1 = “c8a6d282adcf2a52127a70e2f9678585” fullword ascii
condition:
2 of ($cve*) or 2 of ($ip*) or
2 of ($d*) or 2 of ($f*) or 1 of ($h*)
}
Recommendations
Strategic
Management
Tactical
British Intelligence Highlights Chinese Cyber Activity Targeting UK Government Infrastructure
MI5, the British domestic intelligence agency, has issued a stark warning to UK politicians and their staff, highlighting espionage threats from China, Russia, and Iran aimed at undermining British democracy. The guidance, released after a high-profile espionage case against two men accused of spying for China collapsed, urges vigilance against “threat actors” using tactics like cyberattacks, online approaches by purported recruiters, donations masquerading as legitimate funding, or blackmail to influence decisions or gather sensitive information. MI5 advises politicians and businesses alike to track suspicious social interactions, secure digital data, conduct due diligence on new contacts, and report anything suspicious promptly.
Separately, intelligence sources revealed that Chinese hackers accessed UK government systems for over a decade, compromising sensitive and secret data, including confidential policy documents, private communications, and diplomatic cables. A significant breach involved a London data center sold to a China-aligned entity under the previous Conservative government, raising major security concerns. While top-secret information reportedly remained secure, former officials of the National Cyber Security Centre, emphasized China’s persistent cyber espionage as a serious threat to the UK’s economic prosperity and democratic institutions. The government denies that its most sensitive systems were compromised, but the issue has sparked parliamentary calls for an inquiry into the handling of the espionage case.
ETLM Assessment:
China continues to extend its cyber and influence operations beyond the United Kingdom, with increasing activity observed across Europe. These operations target critical infrastructure, political institutions, and key economic sectors to advance Beijing’s strategic interests and enhance its geopolitical leverage. China’s multifaceted approach – combining cyber espionage, economic coercion, and influence operations – poses an expanding threat to European sovereignty, data security, and policy independence. The pattern of coordinated activity highlights the need for stronger EU-wide cybersecurity frameworks, enhanced intelligence sharing, and more stringent scrutiny of foreign investments linked to state influence.
US Warns of ‘Catastrophic’ Hacks After Cyber Security Firm Breached by China
Seattle-based cybersecurity firm F5 revealed that state-sponsored hackers, most likely to be linked to Beijing, had long-term, persistent access to its networks for at least a year, stealing source code and customer data. The breach compromised the development environment for F5’s BIG-IP product suite, widely used by major global companies and US government agencies, as well as its engineering knowledge management platform. F5’s SEC filing stated that the hackers exfiltrated files containing portions of BIG-IP source code and information on undisclosed vulnerabilities, though no critical or remote code vulnerabilities were compromised, and there is no evidence to suggest tampering with the software supply chain. In response, the US Cybersecurity and Infrastructure Security Agency (CISA) issued an emergency directive, mandating federal civilian agencies to inventory F5 devices and apply updates by October 22, warning that the stolen data could enable hackers to identify zero-day vulnerabilities and develop targeted exploits. The warning states that nation-state hackers could exploit vulnerabilities in F5 products to gain access to credentials and tools that could allow them to move through a company’s network, steal sensitive data, and compromise entire systems.
ETLM Assessment:
The main concern about the hack of the BIG-IP source code is that the hackers could have found ways to infiltrate systems to surveil network traffic and manipulate or steal sensitive data that would be difficult to detect. In the past, Chinese state- sponsored actors, particularly the notorious APT41 group, have orchestrated multifaceted cyber operations resulting in the exfiltration of trillions of dollars’ worth of intellectual property from around 30 multinational companies in sectors like manufacturing, energy, and pharmaceuticals in 2022 alone. These efforts, described by the NSA as the greatest wealth transfer in history, involve persistent network intrusions and rapid data analysis, underscoring China’s unapologetic fusion of state intelligence and business ambitions to dominate global industries through cyber- enabled theft. As outlined in this previous CYFIRMA report, the Chinese state is geared to exploit vulnerabilities and thus is able to exploit holes in cyber security to much larger extent than any other actor in the world.
WorldLeaks Ransomware Impacts Mandom Corporation
Summary:
CYFIRMA observed in an underground forum that a company from Japan, Mandom Corporation (https[:]//www[.]mandom[.]co[.]jp//), was compromised by WorldLeaks Ransomware. Mandom Corporation is a Japanese company that specializes in the manufacturing, marketing, and sale of cosmetics, perfumes, and health-related products. It offers well-known brands such as Gatsby and Lucido-L, which are highly regarded in the men’s grooming market. While Mandom primarily focuses on personal care products for men, it also provides a variety of beauty and skincare products catering to women’s needs. The company’s product range includes hair styling, face and body care, skincare, and makeup, reflecting a comprehensive approach to personal grooming for both genders across Japan and Asia. The compromised data includes information related to information technology, marketing, product specifics, as well as confidential and other sensitive organizational data. The total volume of compromised data is approximately 622.2 gigabytes, comprising around 23,272 individual files.
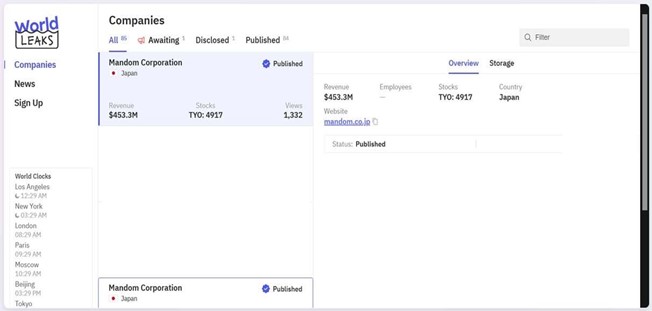
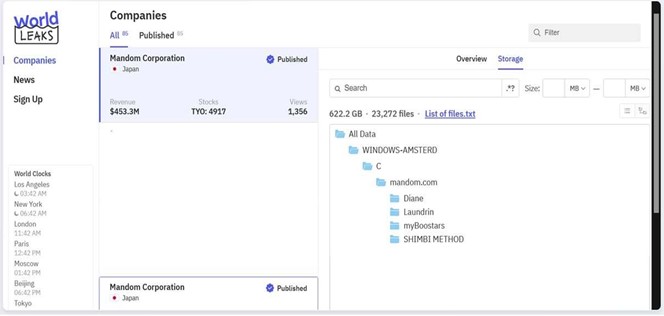
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, the WorldLeaks ransomware group represents a modern evolution of the ransomware ecosystem, shifting toward data exfiltration and extortion-centric tactics. Emerging from Hunters International in early 2025, WorldLeaks operates a hybrid model combining Extortion-as-a-Service (EaaS) with limited encryption-based campaigns, demonstrating the strategic adaptation of cybercriminals to defensive maturity in enterprises.
Rhysida Ransomware Impacts FURUNO Electric Co., Ltd.
Summary:
CYFIRMA observed in an underground forum that a company from Japan, FURUNO Electric Co., Ltd.(https[:]//www[.]Furuno[.]co[.]jp/), was compromised by Rhysida Ransomware. FURUNO Electric Co., Ltd. specializes in providing advanced electronic systems and products primarily for the marine, land, and aviation sectors. The company’s offerings include navigational equipment, radar systems, and communication devices designed to enhance safety and efficiency for professionals in these industries. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The exposed data comprises of highly confidential and sensitive information associated with the organization. The attackers have set the ransom demand at 15 Bitcoin (BTC).
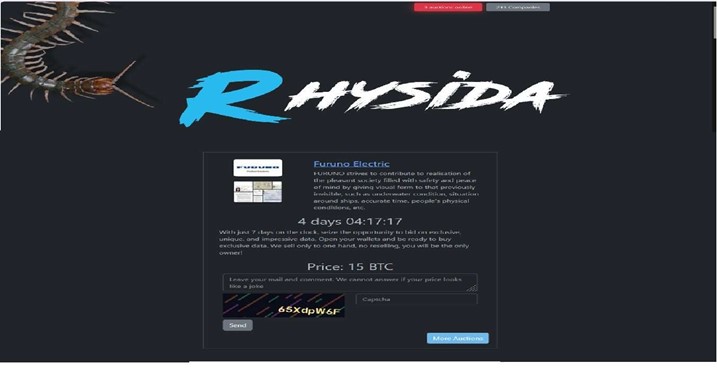
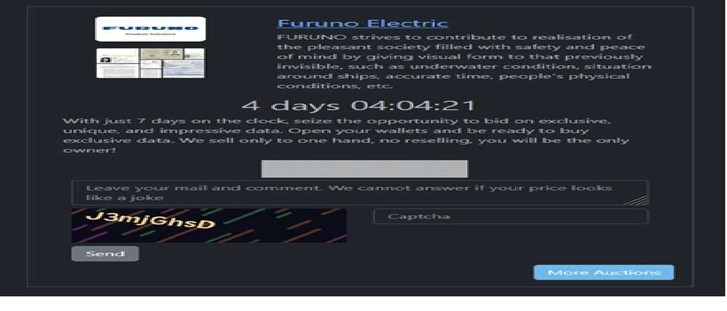
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Rhysida ransomware has emerged as a notable double-extortion threat leveraging both encryption and data theft, evolving rapidly in sophistication since its first appearance in 2023. The Rhysida case underlines the necessity of robust layered defenses, vigilant credential management, cross-sector threat monitoring, and proactive response capabilities. Organizations must not only strengthen prevention and detection controls but also ensure comprehensive incident response planning to mitigate operational, financial, and reputational risks associated with this aggressive, evolving ransomware actor.
Vulnerability in RSUPPORT RemoteCall Remote Support Program
Relevancy & Insights:
The vulnerability exists due to uncontrolled search path element.
Impact:
A local attacker can place a specially crafted .dll file and execute arbitrary code on the target system.
Affected Products:
https://jvn.jp/en/jp/JVN22713803/
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
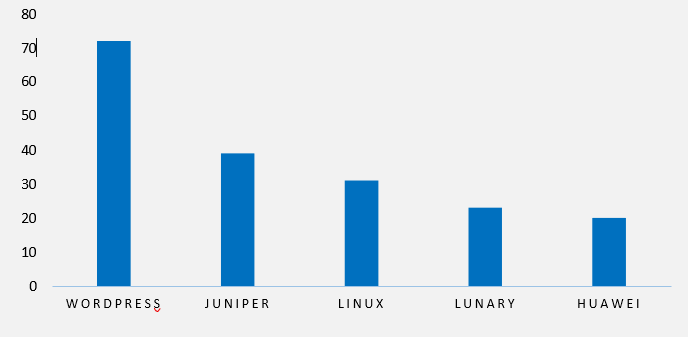
ETLM Assessment
Vulnerability in RSUPPORT RemoteCall Remote Support Program can pose significant threats to user privacy and organizational security. This can impact various industries globally, including technology, customer service, healthcare, and finance. Ensuring the security of RSUPPORT RemoteCall is crucial for maintaining the integrity and confidentiality of remote support sessions and sensitive client data. Therefore, addressing these vulnerabilities is essential to safeguarding remote access operations, customer assistance workflows, and cross-platform device management across different geographic regions and sectors.
Sinobi Ransomware attacked and published the data of the Sunbulah Group
Summary:
Recently, we observed that Sinobi Ransomware attacked and published the data of the Sunbulah Group (https[:]//www[.]sunbulahgroup[.]com/) on its dark web website. Sunbulah Group is one of the largest food manufacturing companies based in Saudi Arabia. Sunbulah Group specializes in producing and distributing a wide range of high-quality food products, including frozen pastries, frozen vegetables, processed meats, premium cheeses, and natural honey. The group operates multiple reputable brands such as Sunbulah, Alshifa, Sary, and Walima, with a presence in over 35 countries, primarily across the Middle East, Asia, Europe, and Africa. The data leak, following the ransomware attack, encompasses sensitive and confidential records originating from the organizational database.
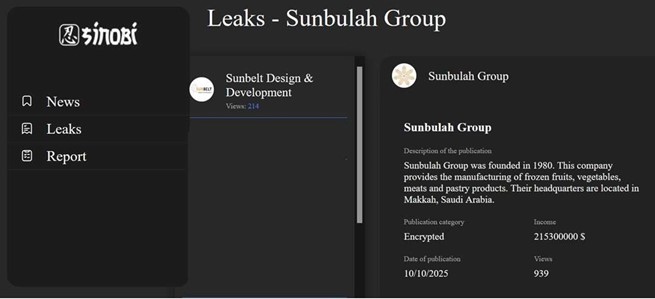
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Sinobi Ransomware represents a new, persistent threat in the ransomware landscape, capable of disruptive attacks on both enterprises and mid-sized organizations.
Kuwaiti Construction Firm Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that a threat actor “Kazu” is claiming to sell access to the internal network of a major Kuwaiti company operating in construction and mega-projects sector. The unnamed company is described as having over 12,000 employees.
The actor is offering access to the company’s Network Attached Storage (NAS) server for a price of $10,000.
According to the actor, the compromised NAS server contains a massive trove of data. The data allegedly for sale includes:
The authenticity of this access sale remains unverified at the time of reporting, as the claim originates solely from the threat actor.
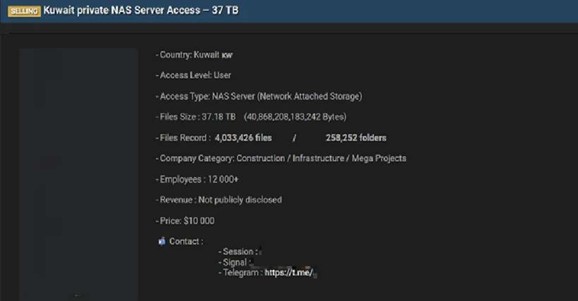
Source: Underground Forums
Creatorlink Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that a threat actor “AgSlowly” has claimed responsibility for a data breach targeting Creatorlink, a South Korean website building platform. The actor is offering the entire database for sale on a dark web forum. According to the actor, the compromised database is 231.9 MB and contains sensitive information from over 575,000 users. The allegedly exfiltrated data includes:
Personal Identifiable Information (PII):
Technical & Activity Data:
Platform-Specific Data:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
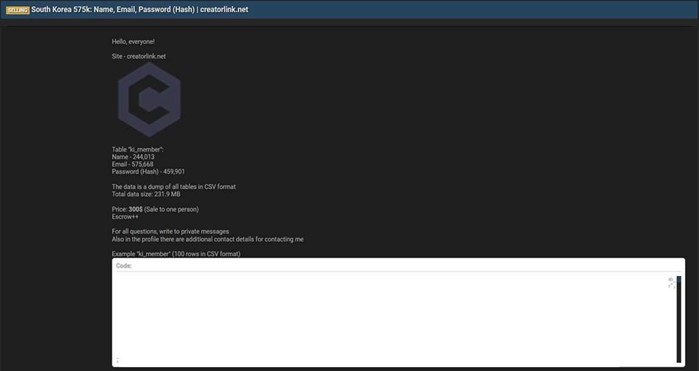
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously looking for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to gain access and steal valuable data. Subsequently, the stolen data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor “Kazu” has recently emerged as a notably active group engaged in data leak activities. Credible sources have tied the group to multiple security breaches involving unauthorized system access and attempts to sell stolen data on dark web marketplaces. The group’s ongoing operations illustrate the persistent and escalating cyber threats stemming from underground forums. These incidents reinforce the critical need for organizations to bolster cybersecurity through continuous monitoring, advanced threat intelligence, and proactive defense strategies to protect sensitive data and critical infrastructure.
Recommendations:
Enhance the cybersecurity posture by:
The CYFIRMA Research team observed that a threat actor claims to have breached Trans7, a major national private television station in Indonesia. In a post on a dark web forum, the actor announced they are in possession of a 1.1GB database belonging to the media company. The post included a warning to Trans7, threatening to expose the entire database if their demands are not met. The breach exposes a significant amount of sensitive personal information.
According to the actor, the compromised 1.1GB database contains a wide range of personally identifiable information (PII). The data categories allegedly include:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
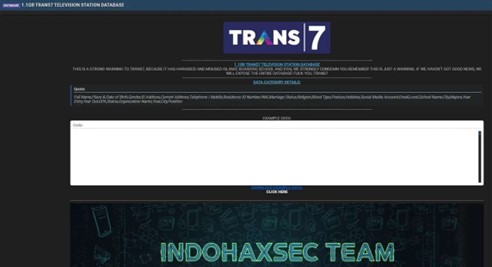
Source: Underground Forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
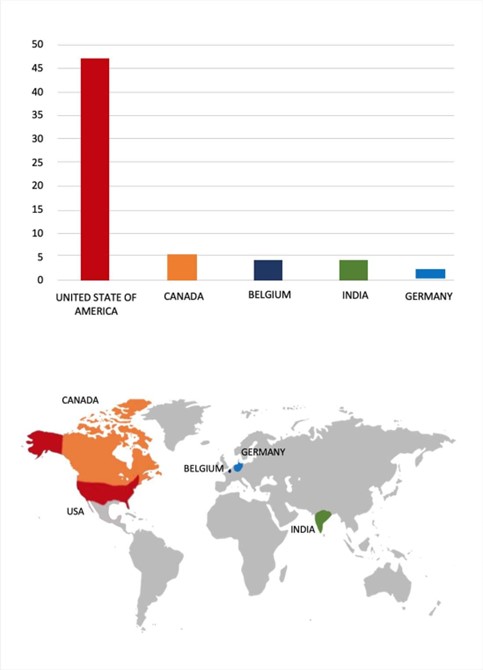
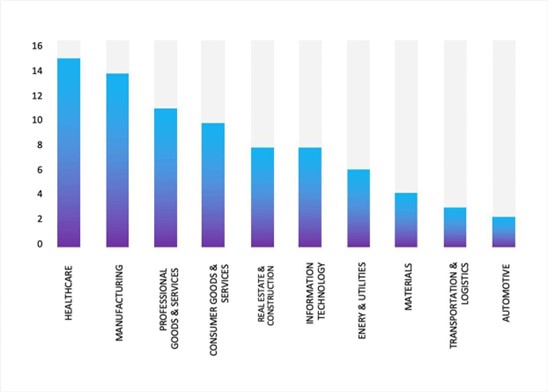
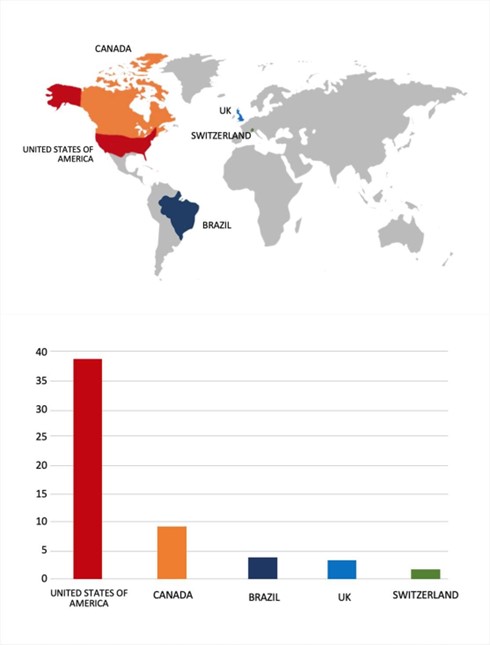
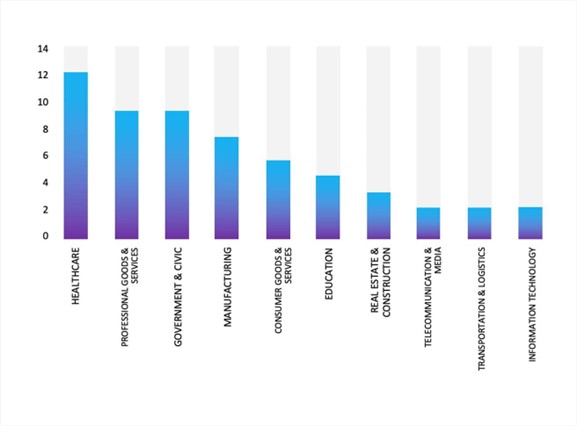
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
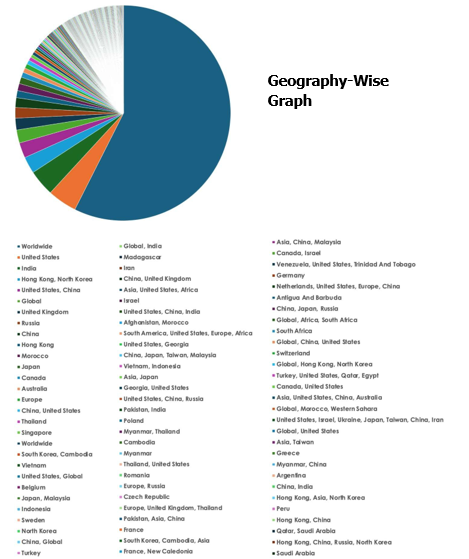

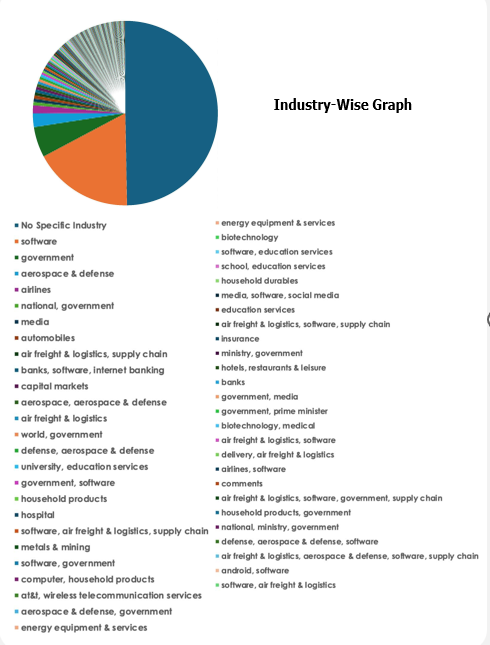
 For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.