



Key Intelligence Signals:
NOBELIUM Attacks Ukranian Allies in the European Region
Summary:
NOBELIUM is a Russian state-sponsored Cyber espionage group active and conducting cyber espionage operations since 2008. The threat actor is known by many other names, a few famous names are APT-29, Dukes, and Cozy Bears. The group has conducted cyber strikes globally, and they are operating solely to collect information and intelligence for the Russian government. In recent activity, the threat actor has been seen targeting diplomats and European governments who are Ukraine’s allies. Cybersecurity researchers have detected a new NOBELIUM campaign that utilizes targeted lures focused on individuals who have shown interest in the recent visit of the Ministry of Foreign Affairs of Poland to the U.S. The attackers have exploited the LegisWrite electronic system, which is a legitimate system for official document exchange within the European Union (EU). The campaign partially overlaps with a previous attack campaign that was uncovered by researchers in October 2022. In the observed phishing campaign, the attackers utilized malicious documents in their email lures. Once a victim opened the document, it led to a link that redirected them to download an infected HTML file. Further analysis suggests that the threat actor may have compromised a legitimate online library website based in EL Salvador in Central America to host the malicious HTML file and deliver additional malicious payloads. The HTML file was found to be using the ROOTSAW (aka Envyscout) dropper, which is commonly used to drop IMG or ISO files. In this instance, the HTML file dropped an ISO file that contained malicious .LNK and .DLL files.
Insights:
The cyber threat group NOBELIUM has been observed actively collecting intelligence on countries that are supporting Ukraine in the Russian-Ukrainian conflict. The use of lures related to the recent visit of Poland’s Ambassador to the United States in the attack campaign indicates that the attackers are closely monitoring geopolitical events and leveraging them to increase the chances of successful infection. This underscores the threat actor’s sophistication and highlights the need for vigilance in protecting against their tactics.
In the observed campaign malicious documents were weaponized by Envyscout dropper which needs a long chain of victim’s engagement to successfully compromise. The threat actor is still using it for quite some time which hints that the threat actor can compromise using old techniques.
The Play Ransomware has impacted the A&T group of companies in Poland.
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed from the dark forum that the A&T group of companies from Poland. (www[.]atglobalsolutions[.]eu)- The company had initially established itself in the Polish market and subsequently expanded its operations to include China, India, Thailand, Hong Kong, Taiwan, Malaysia, Lithuania, Germany, Luxembourg, the Netherlands, the United Kingdom, and Morocco. The ransomware group leaked A&T group of companies’ data on their dedicated leak site on 17th March 2023. According to Play Ransomware, the leaked data includes confidential private and personal information such as passports, contracts, and other sensitive materials.
Insights:
PLAY Ransomware has been active since at least mid-June 2022. The Ransomware encrypts files using the standard RSA-AES hybrid cryptosystem. Additionally, the ransomware executable has been heavily obscured using a variety of anti-analysis techniques that are uncommon in malware families. PLAY Ransomware uses double extortion against its victims.
To gain initial access to a company’s network, the PLAY Ransomware group makes use of a known valid account, exposed RDP servers, and unpatched Fortinet SSL VPN vulnerabilities. The PLAY employs living-off-the-land binaries (LOLBins) as part of its attacks, like the majority of contemporary ransomware. It employs Task Manager for Local Security Authority Server Service (LSASS) process dumping and credential cracking, as well as the remote tool WinSCP for data exfiltration.
Based on the victims’ list, PLAY ransomware is targeting predominately government and critical infrastructure organizations.
We observed that Play ransomware is targeting Microsoft Exchange servers in its operations through critical vulnerabilities (CVE-2022-41080 – CVSS 8.8 and CVE-2022-41082 – CVSS 8.8) which can lead to remote code execution and remote privilege escalation on the servers.
CYFIRMA Research team observed the sale of enterprise admin and database credentials of TOYOTA BRAZIL in the underground forums.
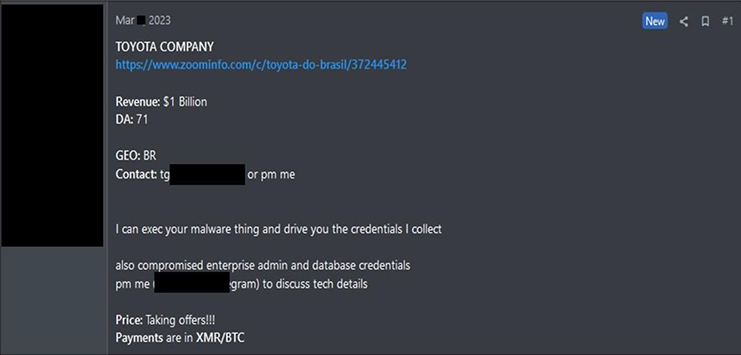
Source: Underground Forums