



Key Intelligence Signals:
APT Gamaredon Abuses HoaxShell in Recent Campaign Against Ukraine
Summary:
According to researchers in recent observations, a new campaign by Gamaredon targeting multiple organizations in Ukraine has been detected. This ongoing espionage operation uses sophisticated techniques to deliver malware to the victim’s machines in Ukraine. The open-source tool Hoaxshell was abused for the technical attack. The attack vector is a spear-phishing email with an attachment that compromises the system through the installation of a WebShell. The WebShell includes features for executing remote commands and deploying additional payloads on an infected machine.
Gamaredon relies on the highly targeted distribution of weaponized documents that mimic official documents from Ukrainian government organizations and uses the Ukranian language for phishing mail. Several types of attachments were used to deliver malware, including .xlsx, .doc, .xlsm, and .docm, with .docm being the most prevalent. The decoy documents are portrayed as official government documents. Once the malicious document is opened, it executes a heavily obfuscated macro called “xdm,” which decodes and executes a second PowerShell script that reports back to the command-and-control server. This campaign is part of an ongoing espionage operation and has been observed as recently as February 2023. The use of obfuscated PowerShell and VBScript scripts in the infection chain makes it challenging to detect and prevent. The main file used to perform the next stage is coded in Python, while the WebShell is coded in pure PowerShell.
Insights:
Despite being exposed many times for using open-source tools like Hoaxshell for the advanced attack, APT continues to target with the same attack vector showing that the success rate is good.
According to Dutch military intelligence, Russia has recently tried to gather information to harm vital infrastructure in the Dutch portion of the North Sea. According to the agency, a Russian ship was discovered at an offshore wind farm in the North Sea as it was attempting to map out energy infrastructure. Before any sabotage attempt could be successful, the vessel was escorted out of the North Sea by Dutch marine and coast guard ships, but the ship has probably been able to gather data on this infrastructure.
According to a recent joint report by Dutch intelligence agencies MIVD and AIVD, Russia is undertaking activities which indicate preparations for disruption and sabotage, with the largest threat being posed towards water and energy supplies in the Netherlands. In recent months Russian cyber actors and intelligence were trying to uncover the workings of the energy system in the North Sea and according to Dutch authorities, Russia is interested in potential sabotage of the energy infrastructure in the Netherlands and more broadly in Europe. This is in line with the warnings CYFIRMA analysts have issued on the topic since the start of the Russian war on Ukraine in February 2022.
Researchers have observed a new threat actor that has been seen targeting shipping companies and medical laboratories in Asia with phishing emails. The APT has been dubbed Hydrochasma and appears to be interested in pharma industries connected with COVID-19 treatments or vaccines. The activity, which has been ongoing since October 2022 is mostly initiated by phishing messages containing resume-themed lure documents that, when launched, grant initial access to the machine.
Researchers did not notice any data being exfiltrated and the actor is not associated with any other known campaigns; however, the actor’s use of the tools they saw suggested that the purpose might be intelligence collection. However, the actor has been using off-the-shelf tools which have complicated the attribution of the attack, which was possibly the intention of the attacker in order to cover its tracks. Given the broad scope of the attack, the researchers suspect government involvement and an attempt to gain strategic intelligence.
According to researchers, APT37 (also known as “RedEyes” or “StarCruft”), a threat actor from North Korea, is disseminating a brand-new malware strain called “M2RAT” (ASEC). Recently, researchers discovered M2RAT being disseminated through phishing emails. The emails contain files that, when opened, will execute shellcode by taking advantage of an inherent flaw in the widely used in South Korean Hangul word processor. The victim’s computer will first receive a JPEG image download from the shellcode, which employs steganography to extract the M2RAT download code. The software is made to take screenshots and record keystrokes to steal data. Infected mobile devices will also be scanned for by M2RAT, and will likewise gain access to documents or audio recordings for the attacker. APT37 frequently targets journalists, North Korean defectors, and human rights advocates. The victims sometimes are unaware that they have been hacked because the threat actor targets individuals and personal devices rather than businesses with expensive protection systems.
In a fresh allegation, Chinese cybersecurity researchers have accused the West of politically motivated cyber-attacks against China. According to the Chinese, the hackers originated in North America and Europe and have been dubbed Against the West in China. The group has published sensitive Chinese information and databases more than 70 times since 2021, including stealing data from around 300 information systems. The list of victims includes the Hainan provincial government and China Southern Airlines.
The Chinese researchers claim the attacks to be political in nature and exclusively share their research with the Global Times, the vehemently nationalistic state-owned Chinese media publication in an attempt to spin the global narrative on government hacking in a more China-friendly light. The publication appears to be a part of China’s growing attempts to take control of the narrative on cyberattacks by pointing the finger in the other direction when it comes to cyber-attack attribution.
CYFIRMA Research team observed that AOL is web portal and online service provider in The United States of America suffered a data breach. This data leak contains First Name, Last Name, Email Address, Phone Number, Zip Code, and Customer ID.
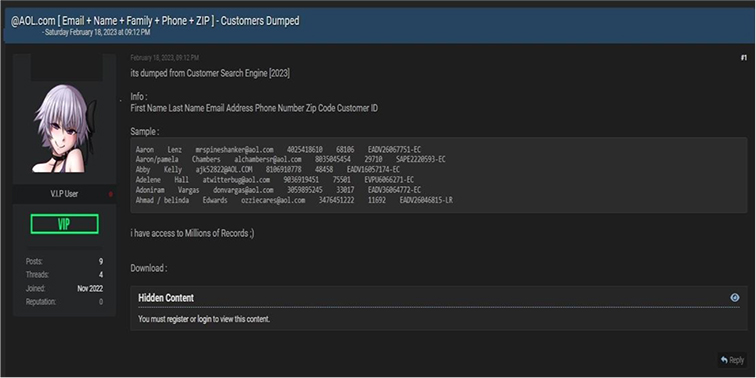
Source: Underground Forums
The Team also observed a potential data leak related to www[.]sttelemediagdc[.]com – ST Telemedia Global Data Centres (STT GDC), is a leading data centre service provider headquartered in Singapore. The Company offers data colocation, connectivity, hosting, and cloud storage services. This data leak contains data of 1,210 customers.
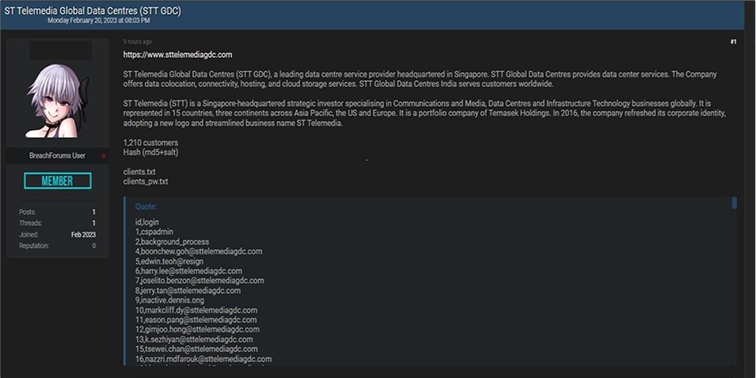
Source: Underground Forums