


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware.
Target Technologies: Windows.
Introduction
CYFIRMA Research and Advisory Team has found RALEIGHRAD Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
RALEIGHRAD Ransomware.
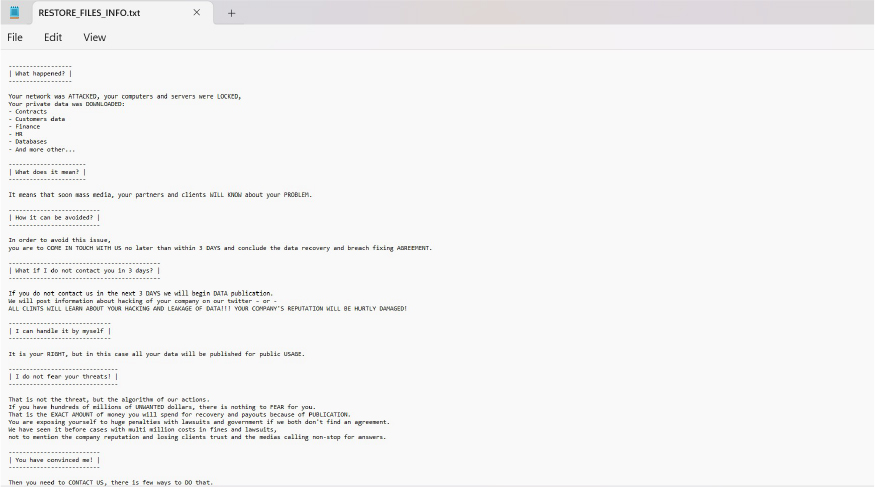
RALEIGHRAD is a newly identified ransomware strain that, upon execution, encrypts victim files and appends the “.RALEIGHRAD” extension.
Additionally, RALEIGHRAD generates a ransom note, “RESTORE_FILES_INFO.txt”.

A ransom note is dropped, informing the victim that a range of sensitive data— including contracts, customer records, financial documents, HR files, and databases— has been exfiltrated.
Victims are warned that the stolen information will be published if contact is not initiated within three days. The attackers instruct victims to communicate via the qTOX messaging app to begin ransom negotiations. In exchange for payment, the threat actors claim they will provide a decryption tool and delete the exfiltrated data from their servers.
Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1053 | Scheduled Task/Job |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1106 | Native API |
| Execution | T1569.002 | System Services: Service Execution |
| Persistence | T1053 | Scheduled Task/Job |
| Persistence | T1112 | Modify Registry |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Persistence | T1574 | Hijack Execution Flow |
| Privilege Escalation | T1053 | Scheduled Task/Job |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1574 | Hijack Execution Flow |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1574 | Hijack Execution Flow |
| Defense Evasion | T1620 | Reflective Code Loading |
| Discovery | T1012 | Query Registry |
| Discovery | T1033 | System Owner/User Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1087 | Account Discovery |
| Discovery | T1135 | Network Share Discovery |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1105 | Ingress Tool Transfer |
| Impact | T1486 | Data Encrypted for impact |
Relevancy and Insights:
ETLM Assessment:
Cyfirma’s assessment with available data suggests that RALEIGHRAD is likely to evolve into a persistent threat targeting enterprise environments reliant on Windows systems. Its use of qTOX for anonymity, WMI abuse, and sandbox evasion tactics reflects increasing sophistication. Future variants may introduce enhanced lateral movement and data exfiltration features. Given its data-leak extortion model and stealthy execution, RALEIGHRAD may transition into a ransomware-as-a-service (RaaS) model, placing organizations globally at heightened risk of data breaches and critical service disruptions.
Sigma rule:
title: Raccine Uninstall tags:
– attack.defense-evasion
– attack.t1562.001 logsource:
category: process_creation product: windows
detection: selection1:
CommandLine|contains|all:
– ‘taskkill ‘
– ‘RaccineSettings.exe’ selection2:
CommandLine|contains|all:
– ‘reg.exe’
– ‘delete’
– ‘Raccine Tray’ selection3:
CommandLine|contains|all:
– ‘schtasks’
– ‘/DELETE’
– ‘Raccine Rules Updater’ condition: 1 of selection*
falsepositives:
– Legitimate deinstallation by administrative staff level: high
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Information Stealer | Objectives: Data Theft, Data Exfiltration | Target Technologies: Windows OS, Browsers, Email Clients, FTP Clients | Target Industries: State and Local Government, Federal Government, High Tech, Finance, Manufacturing, Media and Entertainment | Target Geographies: United States, Brazil, Peru, the Netherlands, Turkey, Hungary
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “DarkCloud Stealer” is trending.
DarkCloud Stealer
Researchers uncovered a wave of attacks linked to DarkCloud Stealer, a threat that has been quietly promoted on underground forums since early 2023. While the stealer has cast a wide net across different sectors, government organizations appear to be its primary target. In the latest campaign, attackers used AutoIt scripting and file-sharing servers to bypass security tools and deploy the malware. These new AutoIt-based DarkCloud samples have been observed across various affected industries, including state and local government, federal government, high tech, finance, manufacturing, and media and entertainment. Geographically, the campaign has impacted victims in the United States, Brazil, Peru, the Netherlands, Turkey, and Hungary. DarkCloud’s layered structure and stealthy behavior make it particularly hard to spot, while its core strength lies in stealing sensitive information and establishing communication with attackers in the background.
Attack Method
Researchers have observed multiple variations of attack chains used to deliver DarkCloud Stealer, all following a similar pattern. These attacks typically begin with a phishing email, which either contains a compressed file (RAR archive) or a PDF. In some cases, the PDF tricks the victim into downloading a fake software update from a file- sharing site. Once opened, the RAR archive includes a hidden executable file designed to run in several steps. This file uses scripting to unpack and activate the final payload— DarkCloud Stealer—while keeping its actions concealed. The layered approach helps the malware evade detection and increases its chances of success, posing a significant threat to its targets.
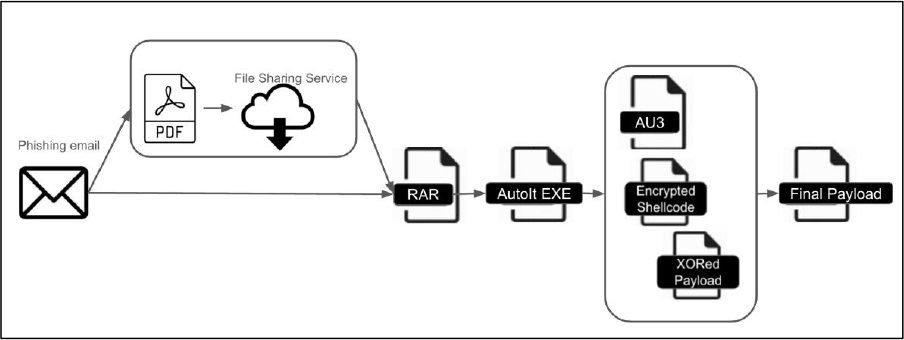
Technical Analysis
The attack begins with a phishing email containing a PDF crafted to mislead the victim. When opened, the PDF shows a fake pop-up warning that Adobe Flash
Player is outdated. If the victim clicks the “Download Flash” button, it redirects to a file-sharing site that delivers a compressed RAR archive. Inside the archive is an AutoIt compiled executable—a disguised program that quietly launches the next stage of the malware.

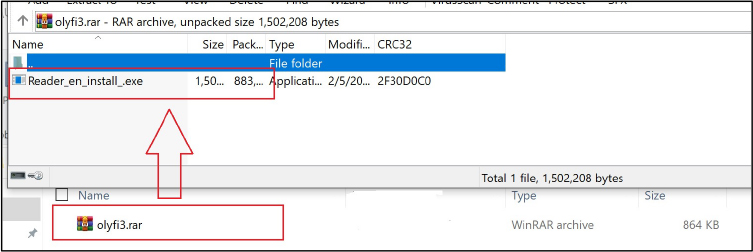
A key update in the latest variant of DarkCloud Stealer is its use of AutoIt-compiled executables to help deliver the malware. AutoIt is a legitimate tool often used for automating tasks on Windows, but in this case, attackers have cleverly repurposed it to hide their malicious activity. The AutoIt file doesn’t work alone—it’s bundled with two additional encrypted components, one acting as a shellcode and the other as a hidden payload.
Once activated, the script quietly unpacks and runs hidden code in the background. This multi-layered process includes decoding strings, injecting code into memory, and executing the final malware without raising suspicion. Interestingly, researchers noted signs that the attackers may be experimenting with more advanced obfuscation techniques, suggesting that future versions of the malware could be even harder to detect.
The final stage of the attack reveals the true purpose of DarkCloud Stealer. Identified by a clear signature within the code, this malware is built to quietly gather sensitive information from infected systems. It collects a wide range of data, including device names, user details, screenshots, saved browser passwords, email credentials, and contact lists—making it a powerful tool for stealing personal and workplace data.
Data Theft with Evasion and Persistence Tactics
The final DarkCloud payload is designed to harvest a wide range of sensitive data from infected systems. It targets saved usernames and passwords from browsers like Chrome and Firefox and also digs into email client profiles to extract login details. All this stolen information is bundled into a single file, ready to be sent back to the attackers’ server. Beyond login credentials, DarkCloud also looks for stored credit card data from popular browsers and retrieves FTP and SMTP credentials from related applications.
To avoid detection, the malware is equipped with several anti-analysis tricks. It checks for the presence of common monitoring tools like Wireshark, Process Monitor, and virtual environments such as VMware. It also uses junk code and fake API calls to confuse analysts. Additionally, DarkCloud tries to determine the infected device’s public IP address using online tools, likely to identify the victim’s location. To maintain its presence on the system, it creates a registry entry that ensures the malware runs every time the machine starts.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that DarkCloud Stealer is poised to become an even more disruptive threat as it advances, with future campaigns likely to feature stronger evasion tactics and broader targeting across sectors and geographies. As this stealer evolves, it may inspire the development of similar modular threats that are harder to detect and quicker to deploy, particularly through trusted platforms like file- sharing services. Its success could also fuel a growing underground market for plug-and- play malware, making it easier for low-skilled actors to launch sophisticated attacks. This trend points to an era where cybercrime becomes more accessible, scalable, and unpredictable posing a growing concern not just for organizations and individuals, but for digital ecosystems as a whole.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
SAP NetWeaver Under Fire: Chinese Threat Actors Launch Global Attacks via CVE-2025- 31324 (CVSS 9.8)
Summary:
Researchers have discovered that several China-linked threat actor groups— including UNC5221, UNC5174, and CL-STA-0048—have carried out coordinated cyber operations targeting a critical vulnerability, CVE-2025-31324 (CVSS 9.8), in SAP NetWeaver Visual Composer. This flaw, an unauthenticated file upload vulnerability, enables remote code execution, providing attackers with a powerful foothold into compromised systems.
Attackers leveraged mass scanning tools to identify vulnerable systems and uploaded webshells for persistent access. The campaign, focused on critical infrastructure, used an attacker-controlled server with an exposed directory to host reconnaissance results, listing over 1,800 SAP NetWeaver targets and confirming 581 successful compromises.
Post-exploitation activity involved the strategic deployment of two complementary webshells to maintain robust and resilient access.
The first, coreasp.js, was a feature-rich, encrypted webshell leveraging AES/ECB encryption with hardcoded keys(693e1b581ad84b87) and Java reflection for in- memory execution, allowing attackers to stealthily maintain persistent control while avoiding file-based detection.
The second, forwardsap.jsp, acted as a lightweight, fail-safe shell, enabling direct command execution via query parameter named cmdhghgghhdd—ideal for quickly re-establishing access if the primary shell was discovered or disabled. By combining both, attackers ensured operational redundancy: coreasp.js for stealth and extended control, and forwardsap.jsp for accessibility and resilience. Both were uploaded via the vulnerable /developmentserver/metadatauploader endpoint, granting attackers initial footholds and long-term backdoor access into SAP environments.
Compromised targets spanned essential sectors including energy, healthcare, and government services across the UK, the US, and Saudi Arabia. Attackers utilized the gained access for deep network reconnaissance, issuing thousands of remote commands aimed at identifying adjacent systems, internal IPs, and backup metadata. Techniques included using arp, parsing /etc/hosts, and probing for VMware ESXi-connected workloads. Unsegmented networks further increased the risk of lateral movement.
One actor used a reverse shell over TCP port 10443 and DNS beaconing to confirm exploitation success. Additional malware delivery chains were observed, including KrustyLoader—a Rust-based loader fetched from Amazon S3 buckets, designed to execute Sliver backdoors through encrypted, in-memory execution—and SNOWLIGHT, a loader that retrieves and executes a VShell RAT payload using memfd-based fileless techniques. Both malware strains performed environmental and anti-debugging checks, with staging and obfuscation routines designed for evasion and stealth.
The attackers leveraged widely-used cloud services and exposed enterprise systems to disguise malicious activity and evade detection. These operations are part of a broader strategy focused on achieving long-term, persistent access to critical infrastructure, with objectives likely tied to cyber espionage or potential disruption. SAP environments served as key entry points, enabling lateral movement into cloud identity systems and industrial control networks.
We detail the specific activities attributed:
Relevancy & Insights:
The threat actor behind this attack has previously employed sophisticated tactics, often leveraging zero-day vulnerabilities to infiltrate critical infrastructure. In earlier incidents, they used remote code execution (RCE) vulnerabilities to gain unauthorized access and maintain persistence within target systems, indicating a clear focus on espionage. The current attack, however, saw the exploitation of CVE-2025-31324 (CVSS 9.8), a remote code execution vulnerability in SAP NetWeaver Visual Composer, underscoring the actor’s advanced capabilities in identifying and exploiting high-impact flaws in widely used enterprise software.
Their main objective remains espionage, as evidenced by their history of targeting government organizations, financial sectors, and key industries in strategic geographies. Given the targeted nature of these attacks, industries involved in critical infrastructure, such as energy and telecommunications, should be particularly cautious.
ETLM Assessment:
In recent months, threat activity linked to China-nexus state-backed actors has escalated, with a notable campaign exploiting a critical vulnerability (CVE-2025- 31324) (CVSS 9.8) —a critical unauthenticated file upload vulnerability in SAP NetWeaver Visual Composer. This campaign is attributed to groups resembling UNC5221, UNC5174, and CL-STA-0048, all known for cyber-espionage operations aligned with Chinese strategic interests. These actors share overlapping tactics, infrastructure, and malware, pointing to coordination or shared tooling among units likely affiliated with state intelligence.
The attackers focused on high-value targets across the United Kingdom, the United States, and Saudi Arabia, with victim organizations in natural gas distribution, water utilities, oil and gas exploration, medical manufacturing, and governmental financial institutions. The primary attack surface was SAP NetWeaver, often poorly segmented from internal networks and connected to critical systems like VMware ESXi and cloud identities.
Post-compromise, the threat actors deployed encrypted webshells, then used malware loaders—KrustyLoader and SNOWLIGHT—to deliver Sliver and VShell implants. These techniques align with prior campaigns exploiting Ivanti and ConnectWise products. The use of in-memory malware, DNS beaconing, and reverse shells highlights their focus on stealth and persistence. Future operations will likely target similar enterprise platforms to sustain long-term espionage and strategic positioning.
Strategic Recommendations:
Tactical Recommendations:
Operational Recommendations:
|
MITRE FRAMEWORK |
||
| Tactic | ID | Technique |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Execution | T1059.007 | Command and Scripting Interpreter: JavaScript |
| Execution | T1059.006 | Command and Scripting Interpreter: Python |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1129 | Shared Modules |
| Persistence | T1543.002 | Create or Modify System Process: Systemd Service |
| Privilege Escalation | T1547.006 | Boot or Logon Autostart Execution: Kernel Modules and Extensions |
| Privilege Escalation | T1068 | Exploitation for Privilege Escalation |
| Privilege Escalation | T1055 | Process Injection |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Credential Access | T1003.008 | OS Credential Dumping: /etc/passwd and /etc/shadow |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1087 | Account Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1580 | Cloud Infrastructure Discovery |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1071 | Application Layer Protocol |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
A Major US steel manufacturer targeted by cyberattack
Nucor, a major steel manufacturer based in North Carolina and responsible for producing roughly a quarter of all raw steel in the U.S., has reported a cyberattack involving “unauthorized third-party access to certain information technology systems.” As a precaution, the company took some systems offline, resulting in production disruptions at several facilities. Nucor stated that it is “currently in the process of restarting the affected operations” and is “actively investigating the incident with the assistance of leading external cybersecurity experts.”
ETLM Assessment:
As CYFIRMA has warned in a recent report, U.S. President Trump’s tariffs carry significant geopolitical consequences. By tearing up trade agreements, the U.S. risks undermining its credibility as a global economic leader and straining alliances. Retaliatory tariffs from trading partners could further reduce U.S. exports, hitting manufacturers hard. In cyberspace, heightened tensions may increase the risk of cyberattacks, as trade wars spill into digital domains. The industries the U.S. government is trying to cushion off – where steel producers are the major example – can find themselves in the crosshairs of foreign threat actors.
Russian hackers targeting foreign governments and defense base
Researchers have uncovered a Russian cyberespionage campaign that leverages cross-site scripting (XSS) vulnerabilities in popular webmail platforms such as Roundcube, Horde, MDaemon, and Zimbra. One of these vulnerabilities, CVE-2024- 11182 in MDaemon, was exploited as a zero-day before being patched. The campaign is attributed to APT28, also known as Fancy Bear, a threat group linked to Russia’s military intelligence GRU.
The primary targets were governmental and defense organizations in Eastern Europe, though the researchers also observed attacks against government entities in Africa, Europe, and South America. The malware deployed in the campaign was designed to steal webmail credentials and exfiltrate contacts and email messages from compromised mailboxes.
ETLM Assessment:
The campaign bears all the hallmarks of a state-driven espionage campaign with a goal of providing the Russian government and defense establishment with strategic intelligence and possibly also intellectual property. There are likely many similar campaigns ongoing at the same time, primarily attacking the West and West-aligned governments and organizations around the globe.
The Qilin Ransomware Impacts CMIC CMO Co., Ltd.
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; CMIC CMO Co Ltd (www[.]cmic-cmo[.]com), was compromised by Qilin Ransomware. CMIC CMO Co., Ltd. is a subsidiary of the CMIC Group, a leading healthcare and pharmaceutical services provider headquartered in Tokyo, Japan. CMIC CMO specializes in Contract Development and Manufacturing Organization (CDMO) services, supporting pharmaceutical companies through various stages of drug development and manufacturing. The compromised data consists of confidential and sensitive information related to the organization. The total size of the compromised data is approximately 300 GB.
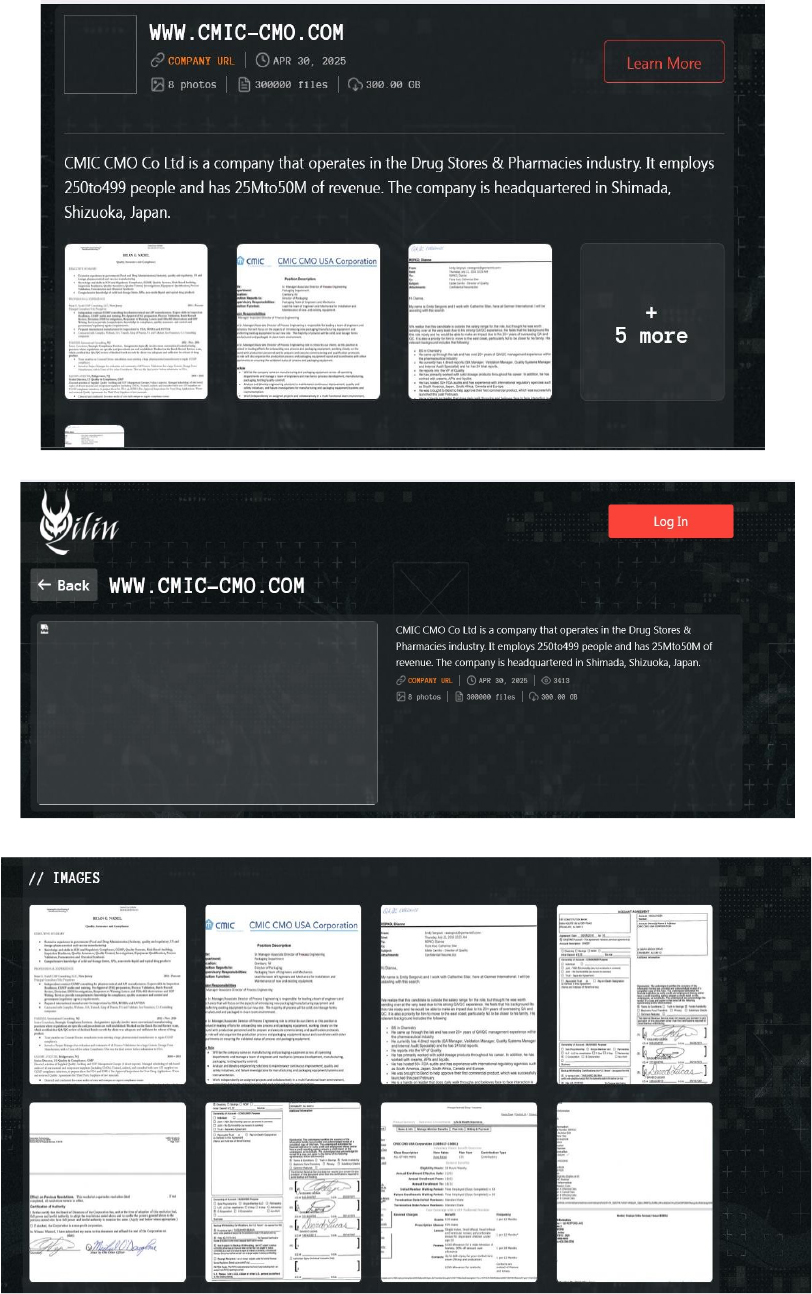
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and focus on speed and evasion, make it a particularly dangerous actor.
The BlackLock Ransomware Impacts TOHO CO., LTD.
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan, TOHO CO., LTD.(https[:]//www[.]toho[.]co[.]jp/), was compromised by BlackLock Ransomware. TOHO CO., Ltd. is a major Japanese entertainment company primarily engaged in film production, distribution, and theatrical stage productions. The compromised data consists of confidential and sensitive information related to the organization.

Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, BlackLock ransomware represents a rapidly growing and sophisticated threat in the ransomware ecosystem, distinguished by custom malware development, aggressive affiliate recruitment, and advanced operational security measures. Despite setbacks from security researchers exploiting vulnerabilities in their infrastructure, BlackLock continues to pose a significant risk to organizations worldwide across multiple sectors.
Vulnerability in Siemens OZW Web Servers
Relevancy & Insights: The vulnerability exists due to improper input validation in the exportDiagramPage endpoint. A remote unauthenticated attacker can pass specially crafted data to the application and execute arbitrary OS commands on the target system.
Impact: Successful exploitation of this vulnerability may result in complete compromise of the vulnerable system.
Affected Products: https[:]//cert-portal[.]siemens[.]com/productcert/html/ssa- 047424.html
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
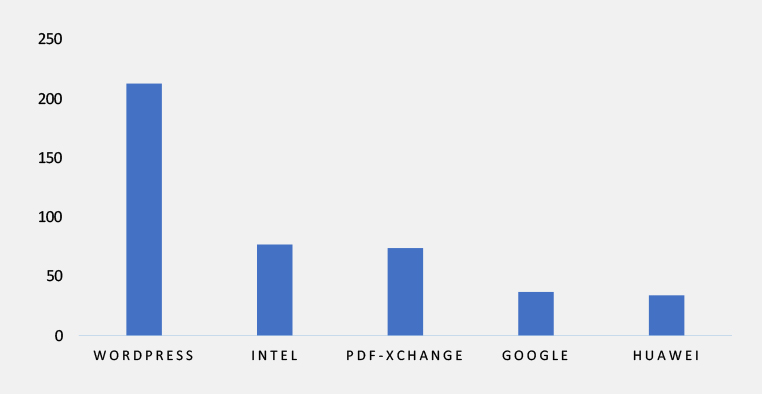
ETLM Assessment
Vulnerability in Siemens OZW Web Servers can pose significant threats to user privacy and security. This can impact various industries globally, including manufacturing, energy, and building automation. Ensuring the security of Siemens OZW Web Servers is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding building control systems, energy monitoring, and HVAC management processes across different geographic regions and sectors.
Everest Ransomware attacked and published the data of Khidmah
Summary:
Recently, we observed that Everest Ransomware attacked and published the data of Khidmah (https[:]//www[.]Khidmah[.]com/) on its dark web website. Khidmah is a comprehensive real estate services company based in Abu Dhabi, United Arab Emirates. The company provides a wide range of solutions, including property management, leasing and sales, facilities management, home maintenance, cleaning, landscaping, and pool maintenance. With its customer-focused approach, Khidmah caters to residential, retail, and commercial properties. The data leak resulting from the ransomware attack includes employees’ personal information, along with internal and confidential data. A total of 3,300 personal records have been compromised. The exposed data consists of User ID, Employee ID, First Name, Last Name, Middle Name, Gender, Email Address, Manager, Human Capital details, Department, Job Code, Division, Location, Time Zone, and other sensitive and confidential information.
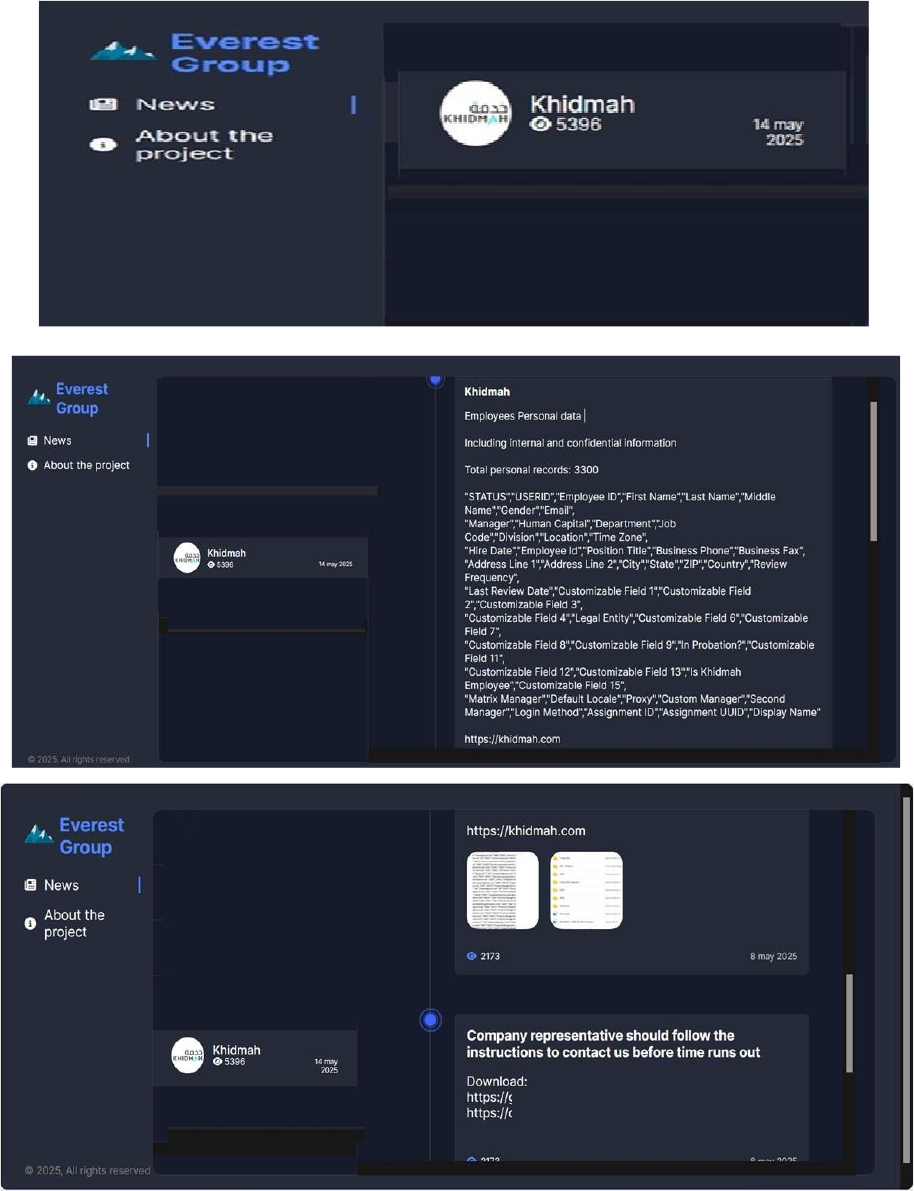
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Everest Ransomware remains a persistent and evolving threat in 2025. Despite the takedown of its leak site, the group continues to target new sectors, expand its operations as an initial access broker, and leverage data leak extortion as its primary tactic. Organizations should remain vigilant, strengthen access controls, monitor for lateral movement and Cobalt Strike activity, and ensure robust incident response capabilities to defend against Everest’s ongoing campaigns.
IM Co., Ltd Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data leak related to IM Co., Ltd. (https[:]//www[.]im-eng[.]jp/) in an underground forum. IM Co., Ltd is a Japanese manufacturing company specializing in the design and production of hydraulic cylinders and automotive components. Its service offerings include deep-hole machining, end processing, welding, and assembly. The leaked data includes confidential and sensitive information pertaining to the organization, with a total volume of approximately 1.88 GB. The breach has been attributed to a threat actor operating under the alias “BLF0ty.”
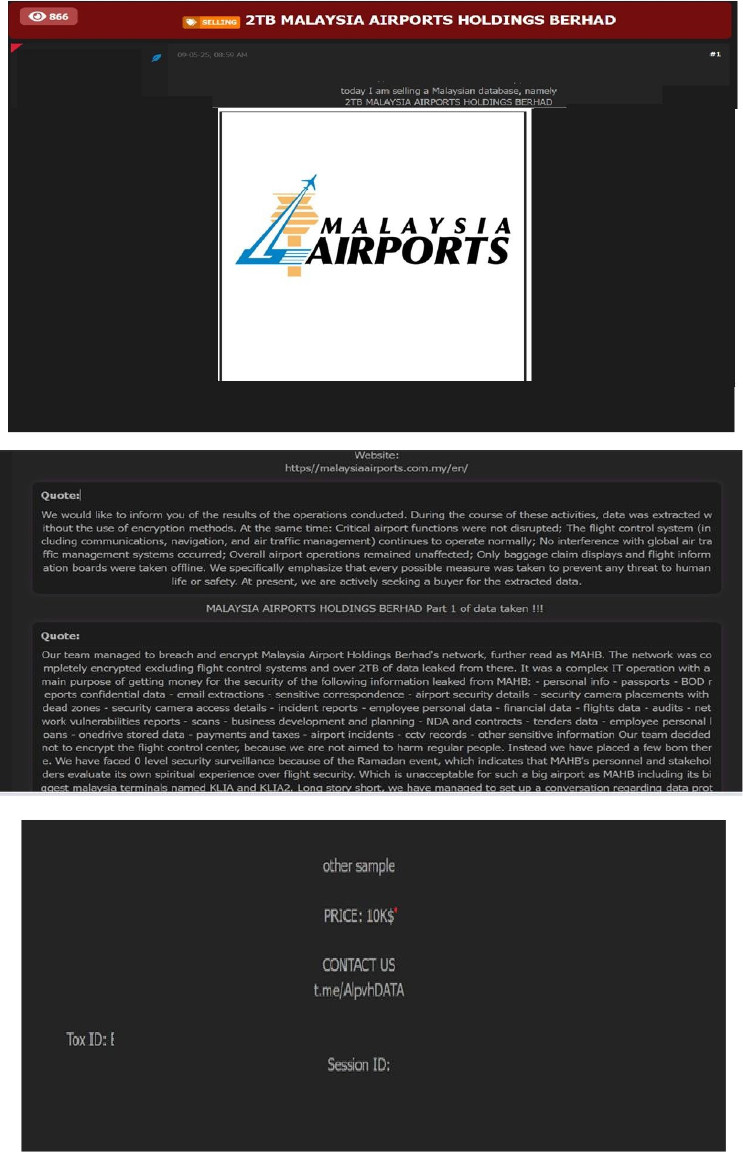
MALAYSIA AIRPORTS HOLDINGS BERHAD Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data sale related to MALAYSIA AIRPORTS HOLDINGS BERHAD (https[:]//www[.]malaysiaairports[.]com[.]my/) in an underground forum. Malaysia Airports Holdings Berhad (MAHB) is the primary operator of airports in Malaysia. MAHB oversees the management, operation, maintenance, and development of airports across the country and has expanded its operations internationally. The threat actor known as “Dedale” breached and encrypted the network of Malaysia Airports Holdings Berhad (MAHB), sparing only the flight control systems. Over 2TB of data was exfiltrated in what appears to have been a sophisticated cyberattack primarily aimed at extortion. The threat actor has demanded a ransom of $10,000 in exchange for the compromised data.
The leaked data includes a broad array of sensitive and confidential information, such as:
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor known as “Dedale” has been linked to multiple data breaches, with credible reports suggesting involvement in unauthorized system intrusions and attempts to sell stolen data on dark web forums. The emergence and ongoing activity of “Dedale” underscore the persistent and evolving nature of cyber threats originating from the dark web. These developments reinforce the urgent need for organizations to strengthen their cybersecurity posture through continuous monitoring, integration of threat intelligence, and proactive defense strategies to protect critical data assets.
Recommendations: Enhance the cybersecurity posture by:
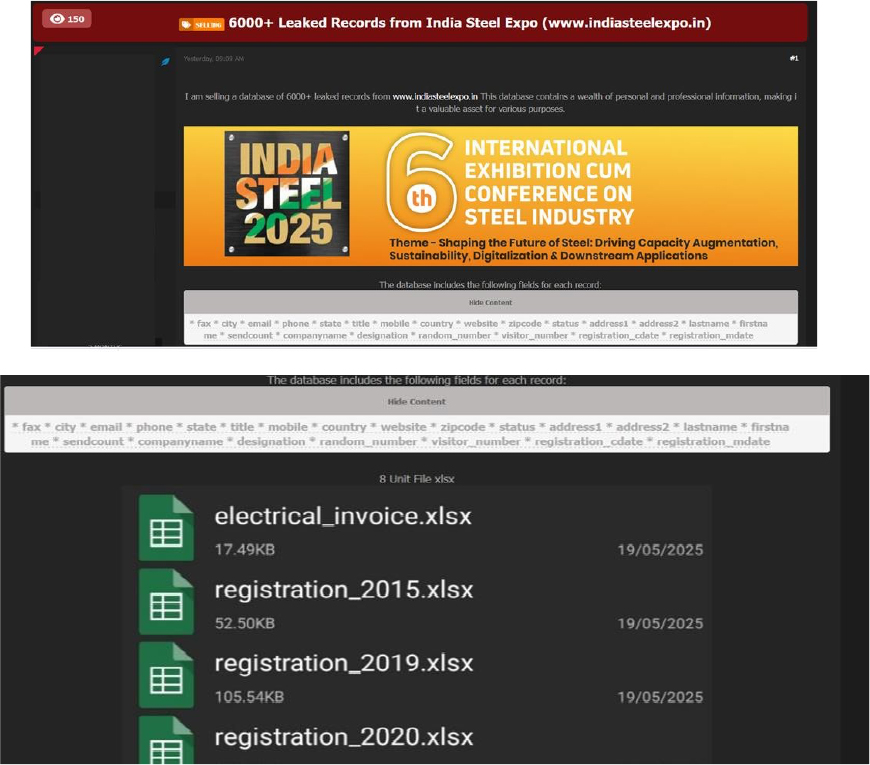
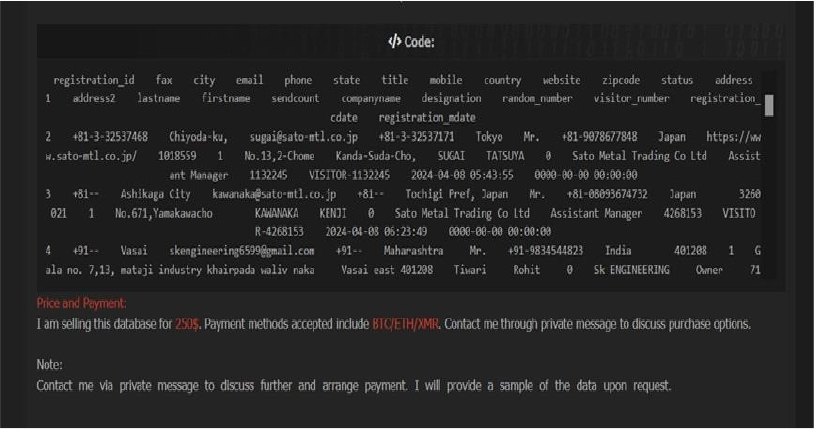
The CYFIRMA Research team observed a data sale related to India Steel Expo (https[:]//www[.]indiasteelexpo[.]in/) in an underground forum. The official website indiasteelexpo[.]in serves as the primary portal for India Steel 2025, the 6th International Exhibition and Conference on the steel industry. Jointly organized by the Ministry of Steel, Government of India, and the Federation of Indian Chambers of Commerce and Industry (FICCI), the event took place from April 24 to 26, 2025, at the Bombay Exhibition Centre (NESCO), Mumbai. The database contains a wealth of personal and professional information, making it a valuable asset for various purposes. The database being offered for sale contains the following fields for each record: Fax, City, Email, Phone, State, Title, Mobile Number, Country, Website, Zip Code, Status, Address, Last Name, First Name, Send Count, Company Name, Designation, Random Number, Visitor Number, Registration Date, along with other confidential information. The seller is asking $250 for the complete dataset.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
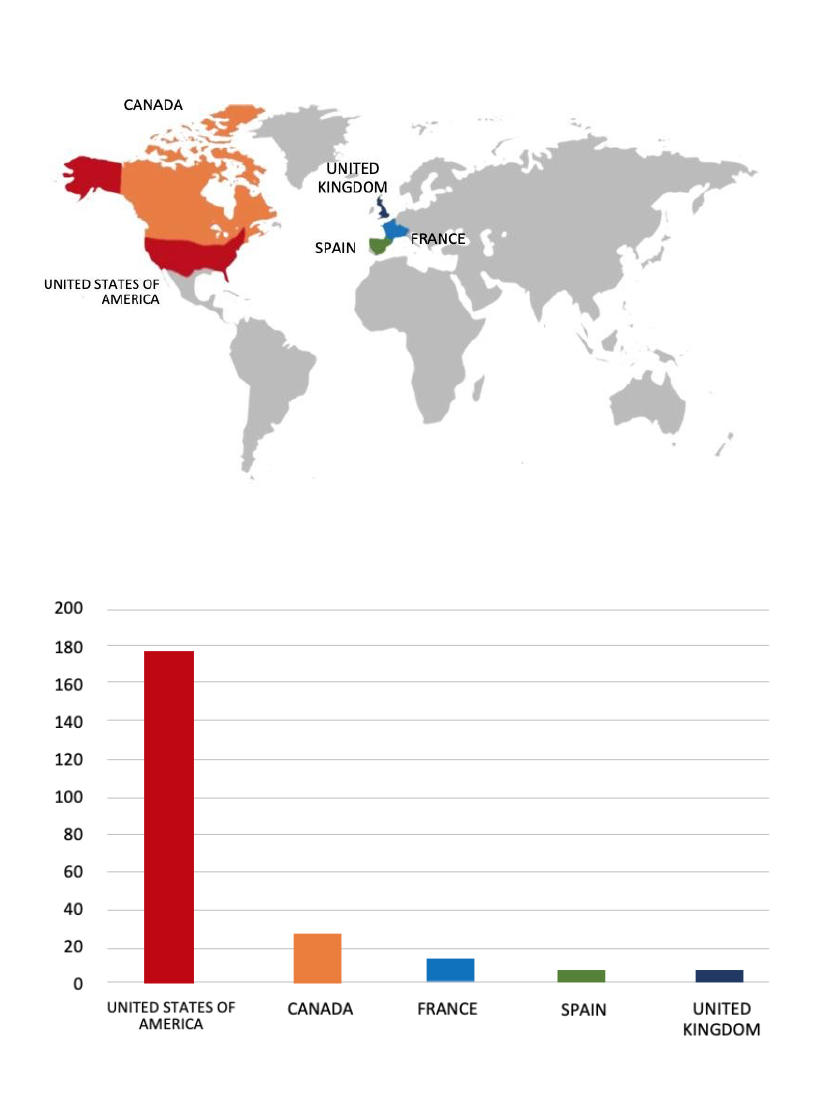
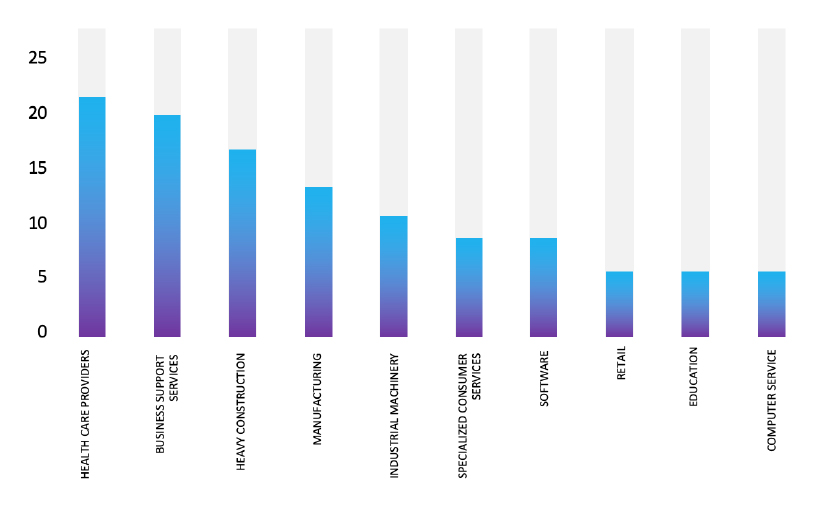
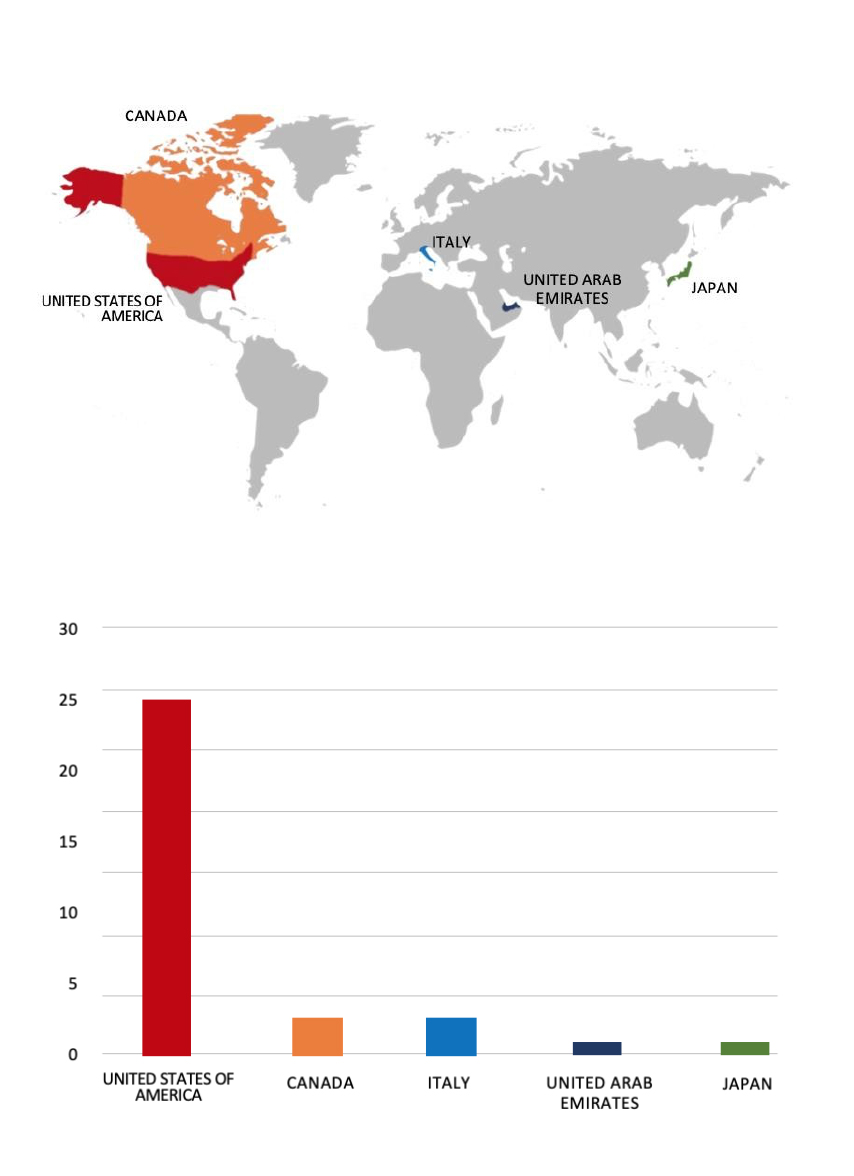
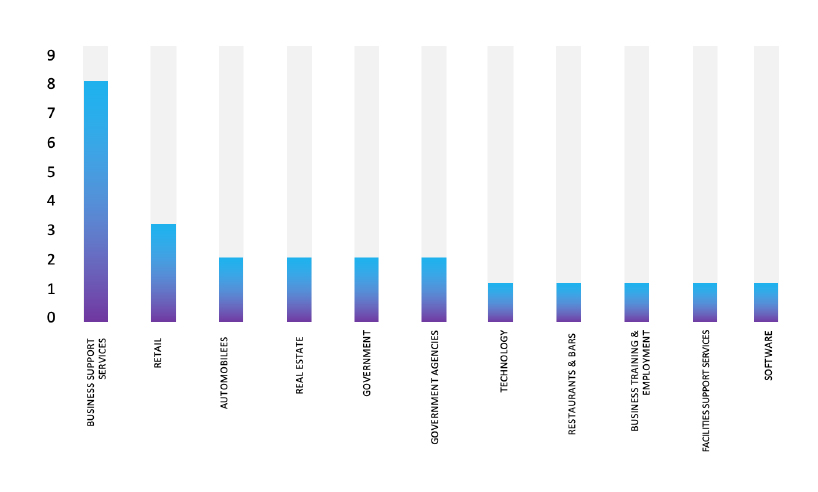
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.